DNSSEC CZ NIC Pavel Tma pavel tumanic cz



- Slides: 13

DNSSEC CZ. NIC Pavel Tůma pavel. tuma@nic, cz 7. 5. 2009 1

What's wrong with DNS? DNS protocol is 30 years old 1983 RFC, 1984 first implementation DNS is vulnerable to spoofing! Serious effects of abuse Phishing / pharming Information spoofing Eavesdropping Known … … but thought too complex and time consuming 2

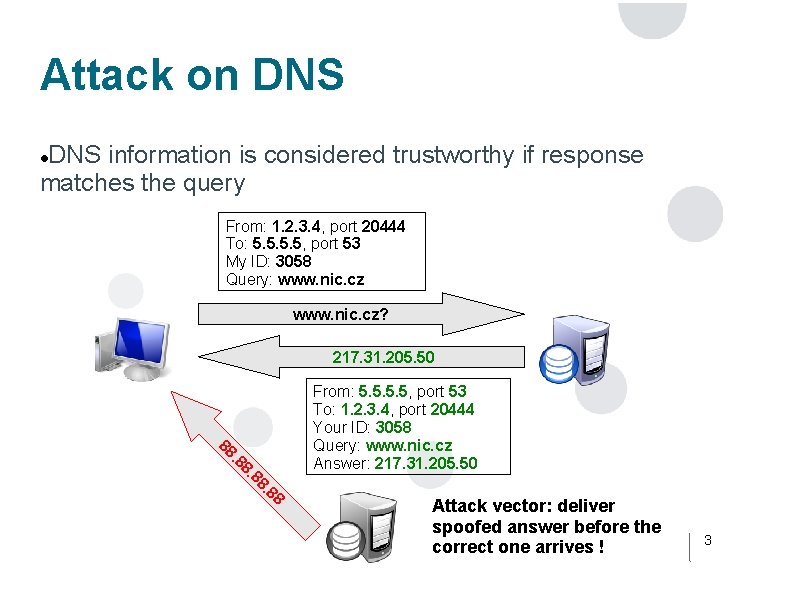
Attack on DNS information is considered trustworthy if response matches the query From: 1. 2. 3. 4, port 20444 To: 5. 5, port 53 My ID: 3058 Query: www. nic. cz? 217. 31. 205. 50 8 8 8. . 8 88 From: 5. 5, port 53 To: 1. 2. 3. 4, port 20444 Your ID: 3058 Query: www. nic. cz Answer: 217. 31. 205. 50 Attack vector: deliver spoofed answer before the correct one arrives ! 3

Attack on DNS Security measures: Port + Transaction ID DNS vulnerability case (Kaminski, August 2008) Port and Transaction ID predictability Time-to-live (TTL) irrelevant (querying random domain names) Compromised within seconds! Solution: full randomization (patches for all implementations) Servers patched. . . … but all of them are still vulnerable! 4

Attack on DNS Brute force attack Theoretically 4. 2 millions of Port and Tr. ID combinations Average DNS message size is 120 bytes 1. 1 million of combinations per second via 1 Gbps Querying random domains … Matter of time Lab testing 3 nodes over 1 Gbps LAN Common server grade hardware Compromised between 1: 01 and 10: 40! 5

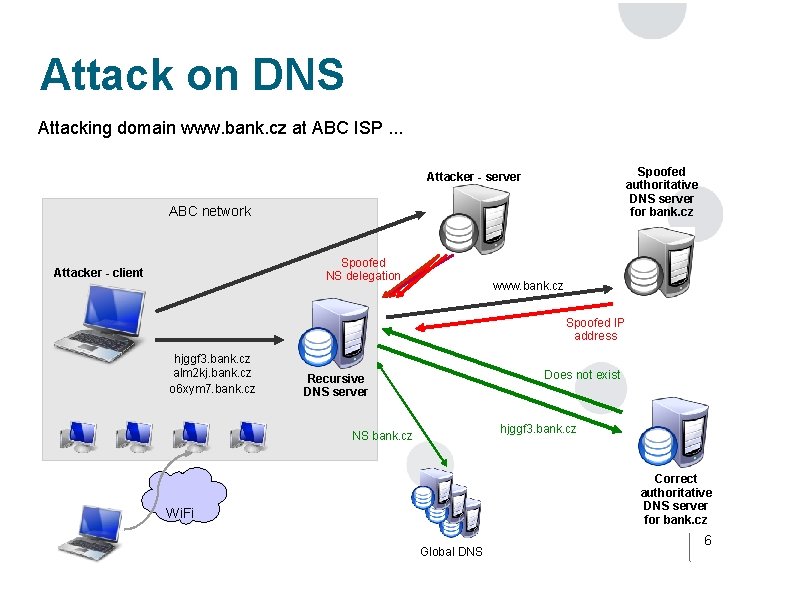
Attack on DNS Attacking domain www. bank. cz at ABC ISP. . . Spoofed authoritative DNS server for bank. cz Attacker - server ABC network Spoofed NS delegation Attacker - client www. bank. cz Spoofed IP address hjggf 3. bank. cz alm 2 kj. bank. cz o 6 xym 7. bank. cz Does not exist Recursive DNS server hjggf 3. bank. cz NS bank. cz Correct authoritative DNS server for bank. cz Wi. Fi Global DNS 6

DNSSEC Asymmetric cryptography within DNS data digitally signed by private key DNS server contains Data itself Digital signature Public key Chain of trust – like with SSL Public key hash stored within superior authority Superior authority = Lower level domain somedomain. cz ->. cz 7

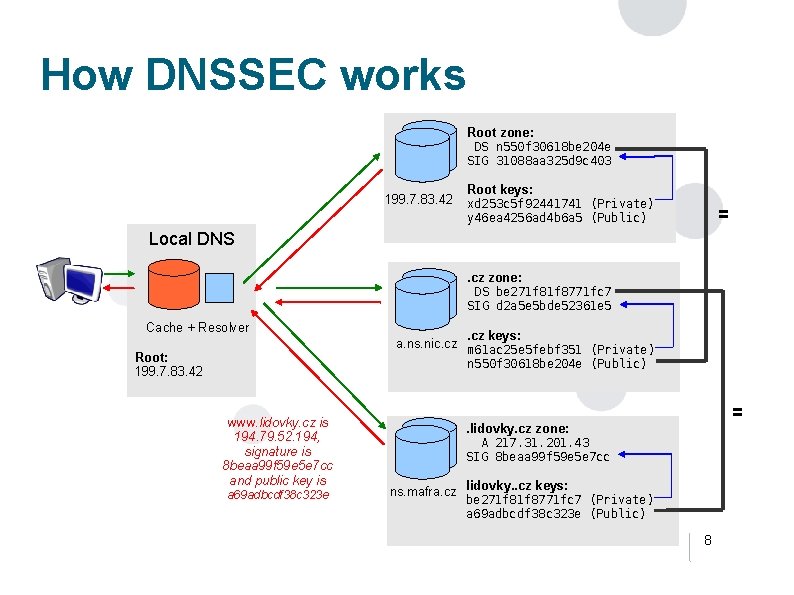
How DNSSEC works Root zone: DS n 550 f 30618 be 204 e SIG 31088 aa 325 d 9 c 403 199. 7. 83. 42 Root keys: xd 253 c 5 f 92441741 (Private) y 46 ea 4256 ad 4 b 6 a 5 (Public) = Local DNS. cz zone: DS be 271 f 8771 fc 7 SIG d 2 a 5 e 5 bde 52361 e 5 Cache + Resolver Root: 199. 7. 83. 42 . cz keys: a. ns. nic. cz m 61 ac 25 e 5 febf 351 (Private) n 550 f 30618 be 204 e (Public) www. lidovky. cz is 194. 79. 52. 194, signature is 8 beaa 99 f 59 e 5 e 7 cc and public key is a 69 adbcdf 38 c 323 e = . lidovky. cz zone: A 217. 31. 201. 43 SIG 8 beaa 99 f 59 e 5 e 7 cc ns. mafra. cz lidovky. . cz keys: be 271 f 8771 fc 7 (Private) a 69 adbcdf 38 c 323 e (Public) 8

. CZ implementation Only 8 DNSSEC enabled TLDs FRED free registry software (fred. nic. cz) EPP (extended) over TCP/SSL interface Zone generation every 30 minutes DNSSEC implementation goals Support sharing between domains Support multiple keys for easy key exchange Free registration (feature not service) 9

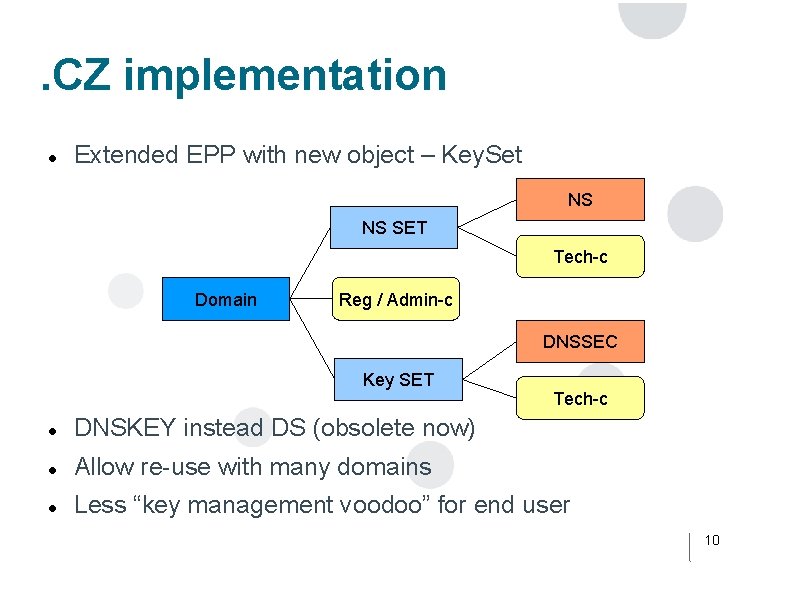
. CZ implementation Extended EPP with new object – Key. Set NS NS SET Tech-c Domain Reg / Admin-c DNSSEC Key SET Tech-c DNSKEY instead DS (obsolete now) Allow re-use with many domains Less “key management voodoo” for end user 10

. CZ implementation Zone signing using Bind native tools – processed in SW HSM (various vendors) testing failed Low level of support & bugs BIND development version Working on CUDA acceleration Huge increase in zone size, from 40 MB to 180 MB Caused problems Bandwidth – 19 secondary locations Memory Solved with reusing signatures – based on ldns tools 11

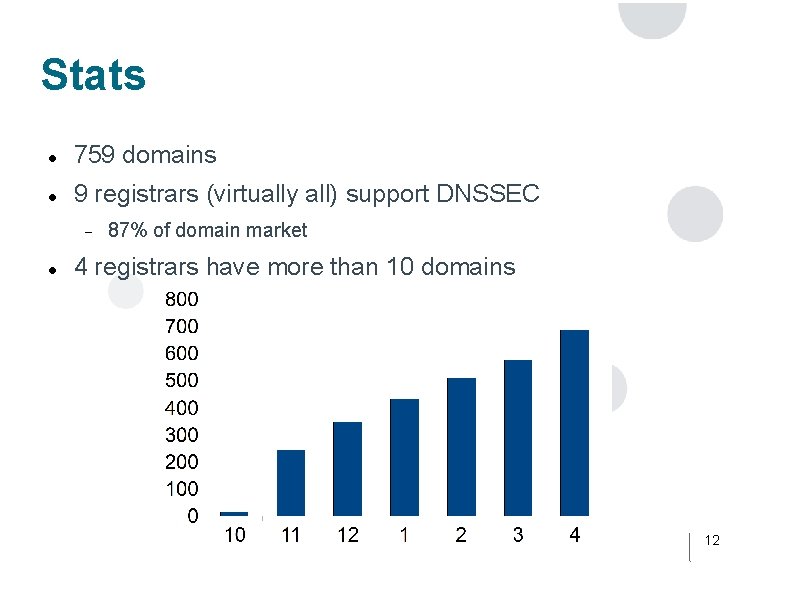
Stats 759 domains 9 registrars (virtually all) support DNSSEC 87% of domain market 4 registrars have more than 10 domains 12

Questions? Thank you DNSSEC Pavel Tuma pavel. tuma@nic. cz http: //www. nic. cz 13