DNS Domain name server DNS a server to













- Slides: 22

DNS

• Domain name server DNS – a server to translate IP aliases to addresses • As you know, IP (internet protocol) works by providing every Internet machine with a unique address – as humans, we tend not to be able to remember lengthy strings of numbers so its easier for us to name our machines – DNS allows us to reference machines by name and still use IP • DNS servers exist across the Internet (globally) • DNS requests use UDP (user datagram protocol) and typically communicate over port 53 to DNS servers

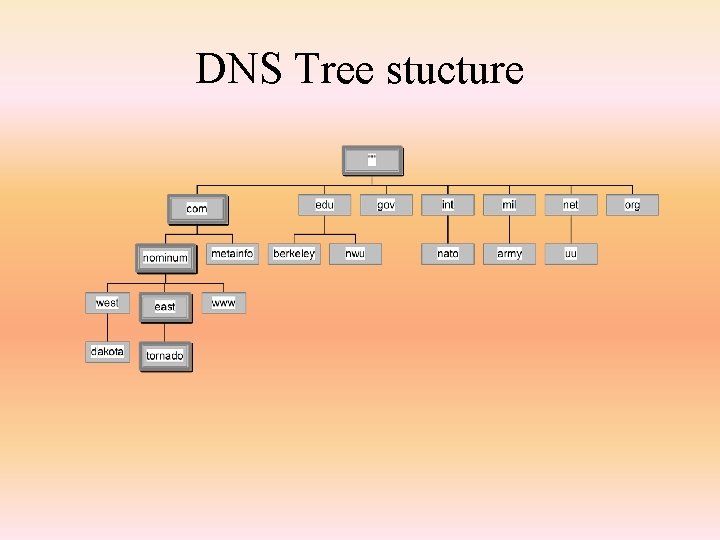
How DNS Works • The structure of DNS’s is tree-like – when you want to translate an IP alias to address, you ask your local DNS to perform the lookup of the given domain • if that information is not available locally, the DNS asks its nearest neighbor DNS, which will be one level higher • if that DNS does not have the information, it asks its next nearest neighbor (again, one level higher) • ultimately, if no DNS has the information on the path up the tree, you get an error – the precise location of a domain name in this hierarchy is known as a fully qualified domain name (FQDN) or absolute domain name • If the alias has subdomains that are not known by the responding DNS, then it forwards the request to the domain’s DNS • A DNS can act as a server to translate IP aliases and/or a cache which can merely cache previous lookups and respond if available

DNS Tree stucture

Example • A fully qualified domain name might be – myhost. subnet 1. example. com • here, the domain name is example. com • the subdomain or subnet name is subnet 1 • and the host name is myhost

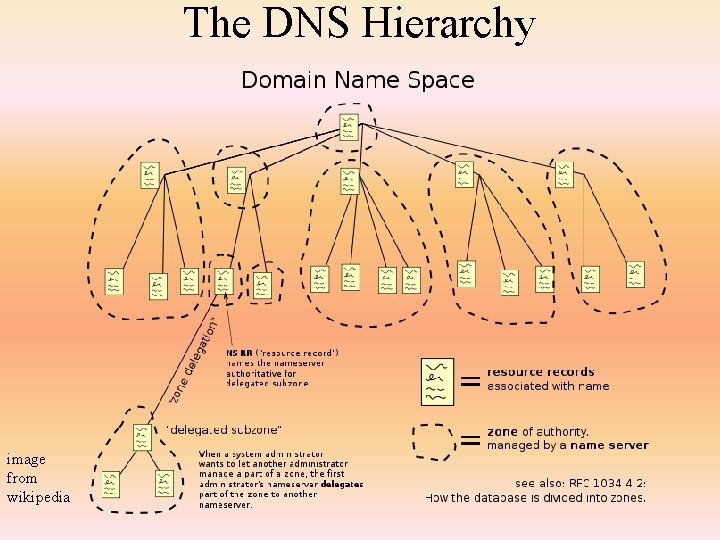
The DNS Hierarchy image from wikipedia

DNS Zone • As shown on the previous slide, the DNS hierarchy is divided into zones • What is a zone? – it represents an area of the Internet that is in one administered space – that is, there is a unit whose job is to administer that zone • as an example, it. nku. edu is administered by IT while cs. nku. edu is administered by the computer science department, so these represent separate zones – it just so happens that IT administers the it. nku. edu and the nku. edu zones • these zones are not administered by other organizations on the Internet though so they are separate from say uk. edu and uc. edu

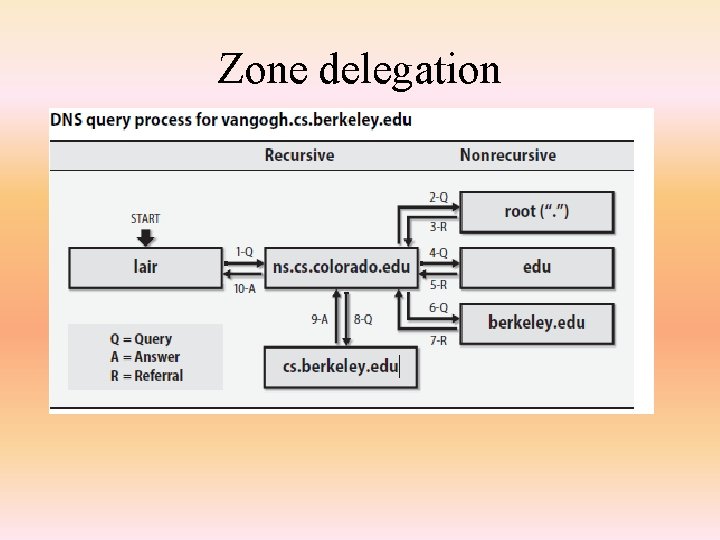
Delegation • All name servers read the identities of the root servers from a local config file or have them built into the code. • The root servers know the name servers for com, net, edu, fi, de, and other top-level domains • Farther down the chain, edu knows about colorado. edu, berkeley. edu, and so on. • Suppose we want to look up the address for the machine vangogh. cs. berkeley. edu from the machine lair. cs. colorado. edu.

Zone delegation

Types of Name Servers • • Authoritative name server Caching only server Recursive server Non recursive server

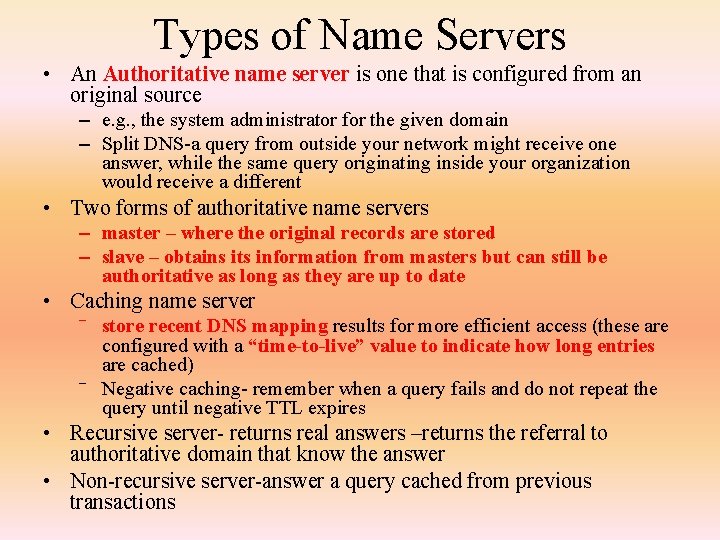
Types of Name Servers • An Authoritative name server is one that is configured from an original source – e. g. , the system administrator for the given domain – Split DNS-a query from outside your network might receive one answer, while the same query originating inside your organization would receive a different • Two forms of authoritative name servers – master – where the original records are stored – slave – obtains its information from masters but can still be authoritative as long as they are up to date • Caching name server ‾ store recent DNS mapping results for more efficient access (these are configured with a “time-to-live” value to indicate how long entries are cached) ‾ Negative caching- remember when a query fails and do not repeat the query until negative TTL expires • Recursive server- returns real answers –returns the referral to authoritative domain that know the answer • Non-recursive server-answer a query cached from previous transactions

DNS Database • It has two entries • Parser commands – Commands embedded in zone files to make them more readable – GENERATE, INCLUDE, TTL • Resource records

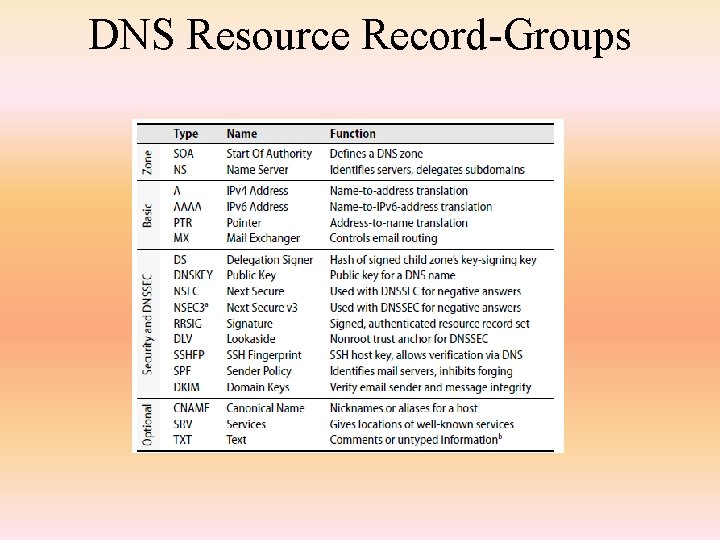
DNS Resource Records • The DNS stores its mapping information as resource records, which contain the following fields – name (the fully qualified name, may use * wildcards to represent all subdomains of a given domain) – time to live in sec -that is, how long the record is valid – class –specify the network type • IN for the Internet, which is the default • HS for Hesiod, a directory service used locally by some sites • CH, used internally by name servers to identify themselves – type of record (IPv 4 addresses, IPv 6 addresses, type of database records, certificate records, DHCP identifier, key records or key types (for encryption), PTRs, email address of the domain’s administrator, and other information) – Example • google. com. 300 IN A 209. 85. 171. 100 • google. com. 345600 IN NS ns 1. google. com

DNS Resource Record-Groups • Zone infrastructure records -identify domains and their name servers. • Basic records -map between names and addresses and route mail. • Security records- add authentication and signatures to zone files. • Optional records- provide extra information about hosts or domains

DNS Resource Record-Groups

BIND • The Berkeley Internet Name Domain – this is the common tool used in Linux/Unix, Windows to implement a DNS – Three flavours-BIND 4, BIND 8, BIND 9(BIND 10 under development) • BIND uses process named, which is the program in Linux for resolving IP addresses – bind’s configuration file is typically stored in /etc/named. conf • we will primarily be editing and working with this file – other bind resources are usually found in the /var/named directory • If you choose to implement just a caching DNS then you would find the configuration file in /etc/named. caching-namserver. conf instead

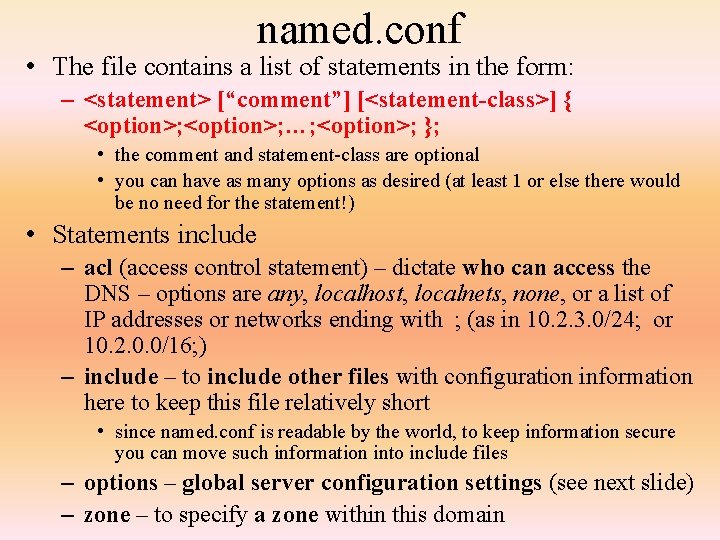
named. conf • The file contains a list of statements in the form: – <statement> [“comment”] [<statement-class>] { <option>; …; <option>; }; • the comment and statement-class are optional • you can have as many options as desired (at least 1 or else there would be no need for the statement!) • Statements include – acl (access control statement) – dictate who can access the DNS – options are any, localhost, localnets, none, or a list of IP addresses or networks ending with ; (as in 10. 2. 3. 0/24; or 10. 2. 0. 0/16; ) – include – to include other files with configuration information here to keep this file relatively short • since named. conf is readable by the world, to keep information secure you can move such information into include files – options – global server configuration settings (see next slide) – zone – to specify a zone within this domain

Options • allow-query, allow-recursion – you provide previously defined acls here to indicate who can query or recurse with this DNS or who is disallowed access (blackhole) • forwarders, forward – list of DNS’s that we should forward a request onto and how we should forward (first or only) • listen-on – specify a particular machine or subnet that we will only listen to, e. g. , listen-on {10. 2. 3. 0/24; }; would force us to only listen on the 10. 2. 3 subnet – defaults to listen to any incoming IP address • notify – used to specify whether and which slaves to notify for updates

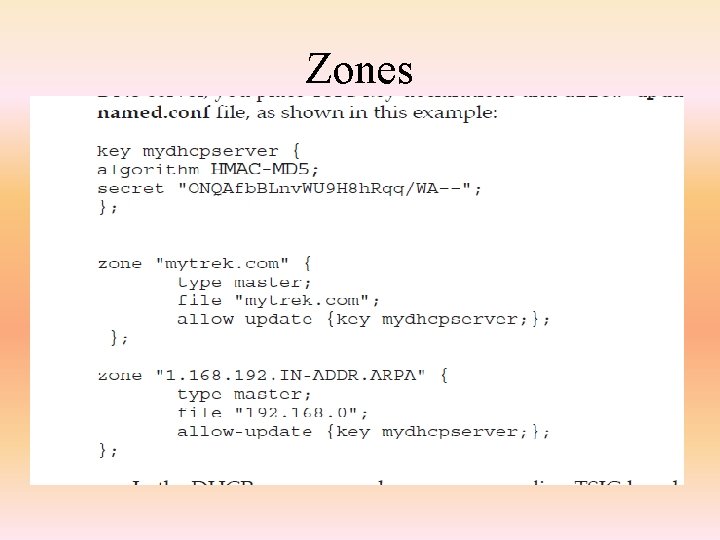
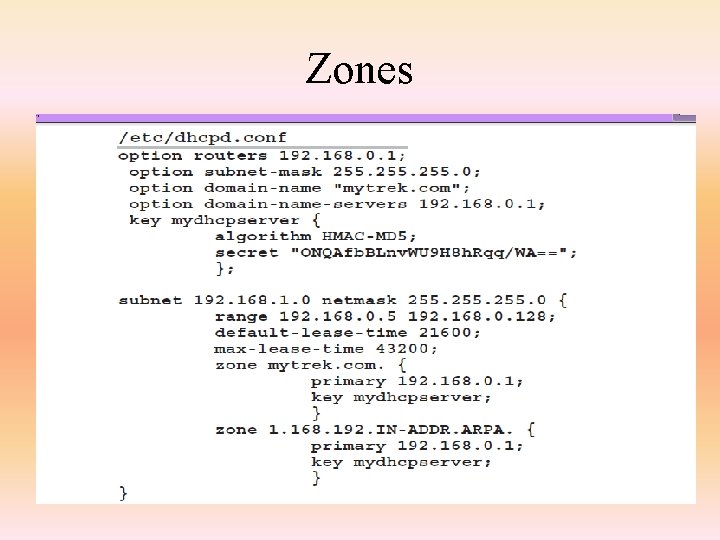
Zones • The zone statement defines the characteristics of a given zone (subdomain) – you can define multiple zones here • The format of the zone statement is – zone <name> <class> { <option>; …; <option>; }; • class is optional – the zone name is extended to the domain name, so for instance if the domain name is example. com and the zone is sales. then we have the subdomain sales. example. com – zone options are largely the same as the previous options but also include • allow-transfer – which slaves can obtain info • allow-update – the masters which can update this DNS • masters – list of DNS’s that are masters – only used if the type of this DNS is slave • type – delegation-only, forward, hint, master, slave

Zones

BIND configuration examples • The localhost zone • A small security company that use split DNS • The experts: isc. org, The Internet Systems Consortium

Zones