Distributed Authentication in Kerberos Using Public Key Cryptography

Distributed Authentication in Kerberos Using Public Key Cryptography Marvin A. Sirbu (sirby@cmu. edu) John Chung-I Chuang (chuang+@cmu. edu) Carnegie Mellon University Pittsburgh, Pennsylvania 15213 A Review By Benjamin Lai

Presentation Overview Background The Proposed PKDA Protocol Conclusion

Background Kerberos is an authentication protocol Features a separate Authentication Server (known as KDC – Key Distribution Centre) and Ticket Granting Service (TGS) KDC keeps a symmetric key for all principals in the realm Possible attack would be on the KDC for all symmetric keys – and the subsequent key-recovery is expensive

The PKDA Protocol - 1 Stands for “Public key based Kerberos for Distributed Authentication” Proposed to solve the security weaknesses of the KDC Certificate Authority (CA) replaces the KDC as the trusted intermediary Elimination of the KDC and TGS – the client authenticates directly with the application server
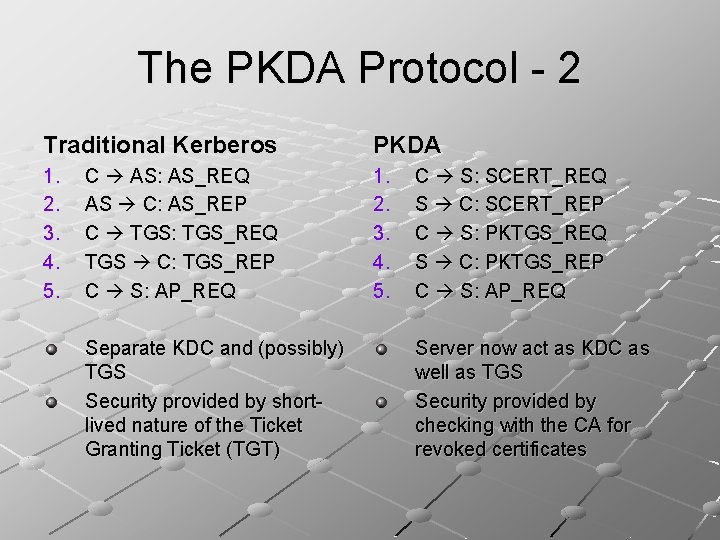
The PKDA Protocol - 2 Traditional Kerberos PKDA 1. 2. 3. 4. 5. C AS: AS_REQ AS C: AS_REP C TGS: TGS_REQ TGS C: TGS_REP C S: AP_REQ Separate KDC and (possibly) TGS Security provided by shortlived nature of the Ticket Granting Ticket (TGT) C S: SCERT_REQ S C: SCERT_REP C S: PKTGS_REQ S C: PKTGS_REP C S: AP_REQ Server now act as KDC as well as TGS Security provided by checking with the CA for revoked certificates
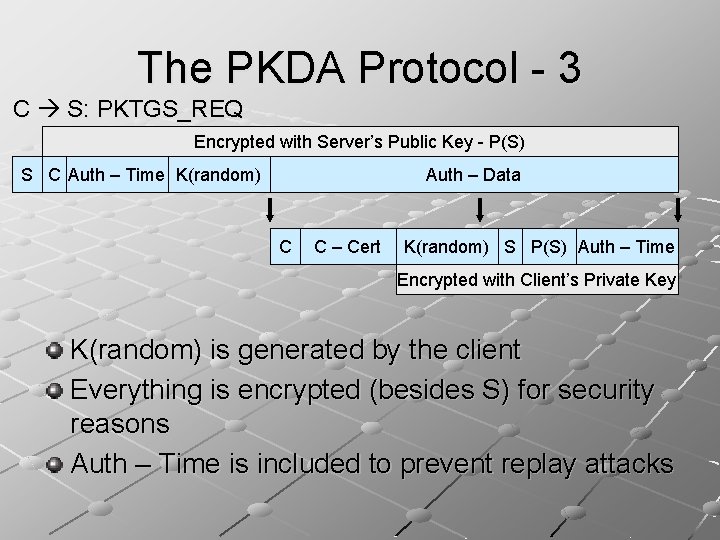
The PKDA Protocol - 3 C S: PKTGS_REQ Encrypted with Server’s Public Key - P(S) S C Auth – Time K(random) Auth – Data C C – Cert K(random) S P(S) Auth – Time Encrypted with Client’s Private Key K(random) is generated by the client Everything is encrypted (besides S) for security reasons Auth – Time is included to prevent replay attacks
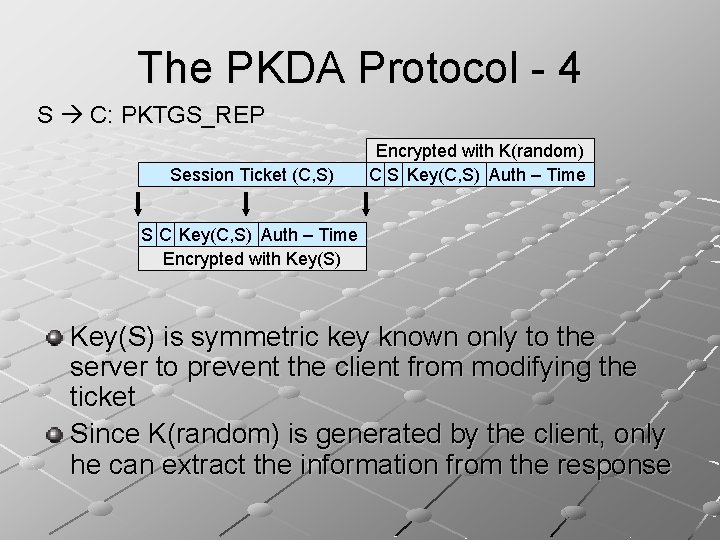
The PKDA Protocol - 4 S C: PKTGS_REP Session Ticket (C, S) Encrypted with K(random) C S Key(C, S) Auth – Time S C Key(C, S) Auth – Time Encrypted with Key(S) is symmetric key known only to the server to prevent the client from modifying the ticket Since K(random) is generated by the client, only he can extract the information from the response

Conclusion In Traditional Kerberos KDC poses a big security weakness PKDA was proposed to eliminate such security weakness. ? “The solution to a problem is itself another problem. ” What are the potential problems that are foreseeable in the PKDA authentication scheme?
- Slides: 8