Dissecting complex codereuse attacks with ROPMEMU Mariano Graziano





![CHALLENGES [C 1] Verbosity CHALLENGES [C 1] Verbosity](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-25.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-26.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-27.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-28.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-29.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-30.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-31.jpg)
![CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-32.jpg)




- Slides: 52

Dissecting complex code-reuse attacks with ROPMEMU Mariano Graziano Cisco Talos

whoami § Security researcher at Cisco Talos § Ph. D. from Telecom Paris. Tech/Eurecom § Hackademic § Malware analysis / Memory forensics / Mitigations

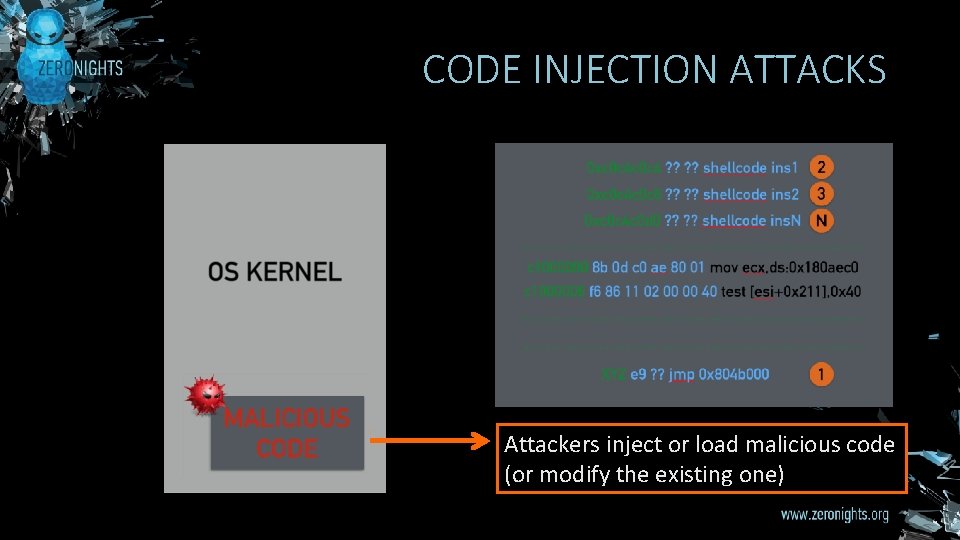
CODE INJECTION ATTACKS

CODE INJECTION ATTACKS

CODE INJECTION ATTACKS Attackers inject or load malicious code (or modify the existing one)

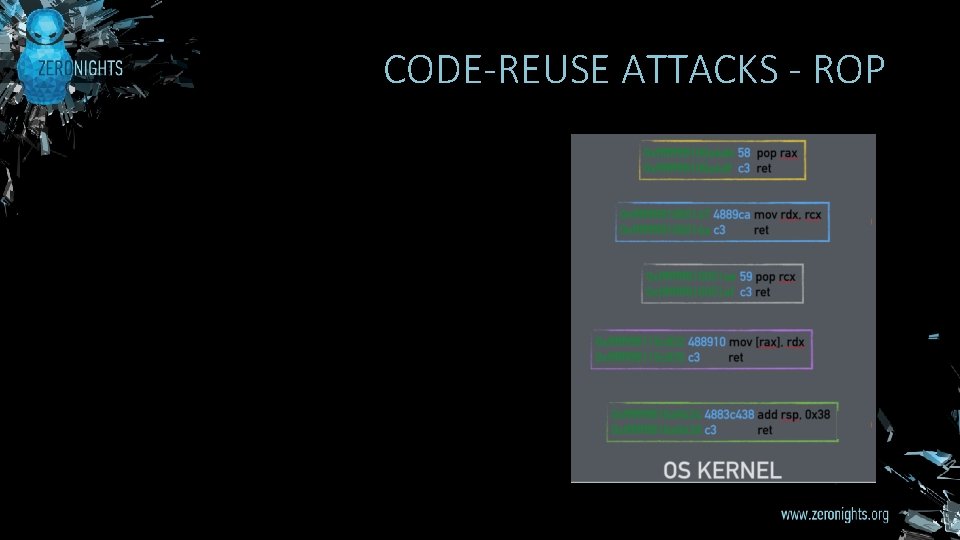
CODE-REUSE ATTACKS - ROP

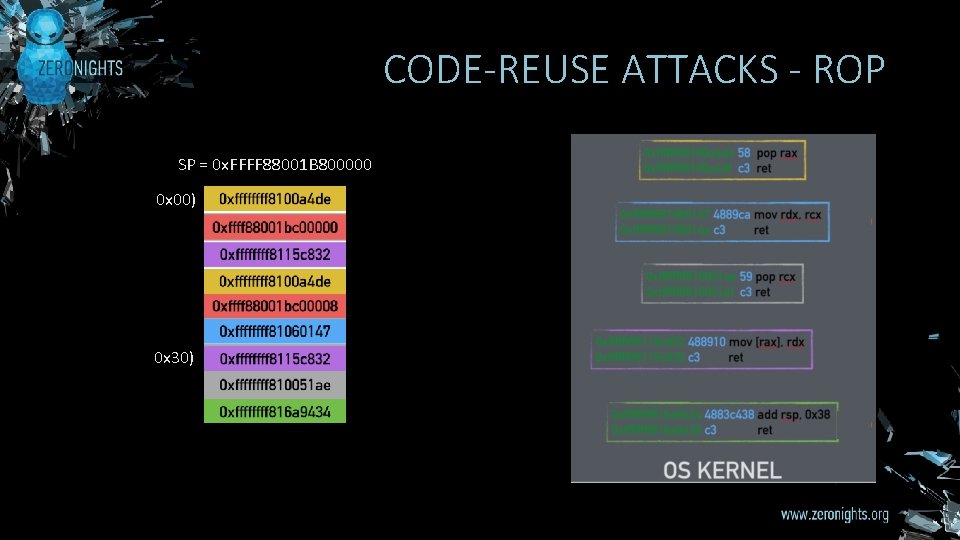
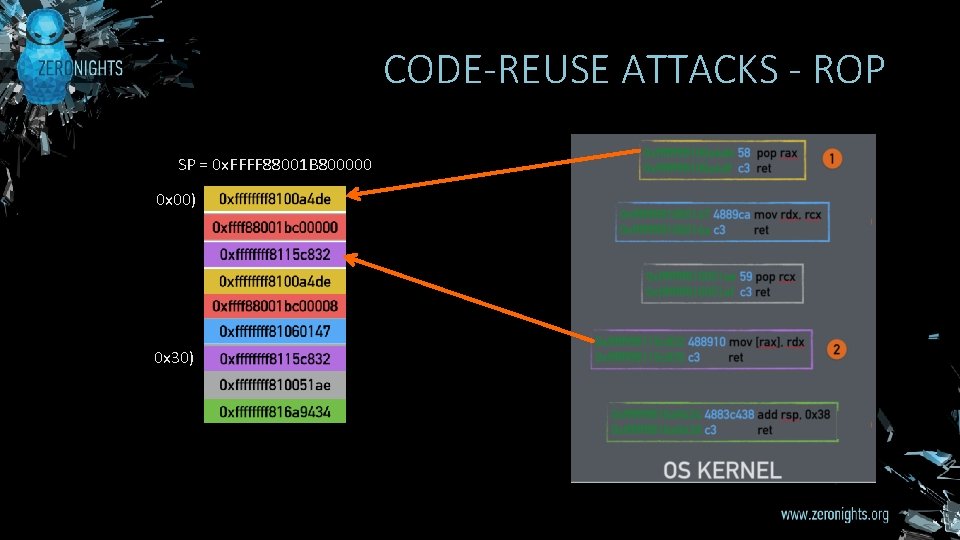
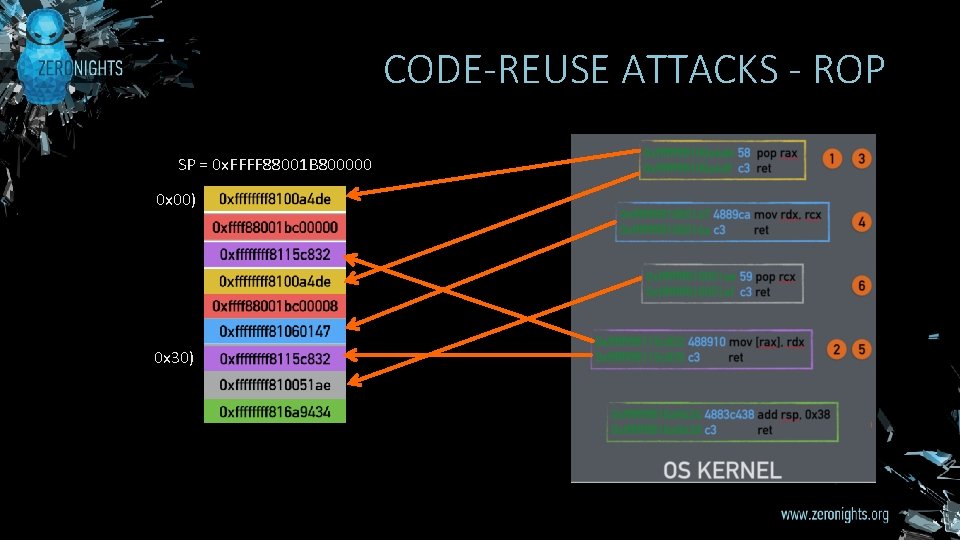
CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

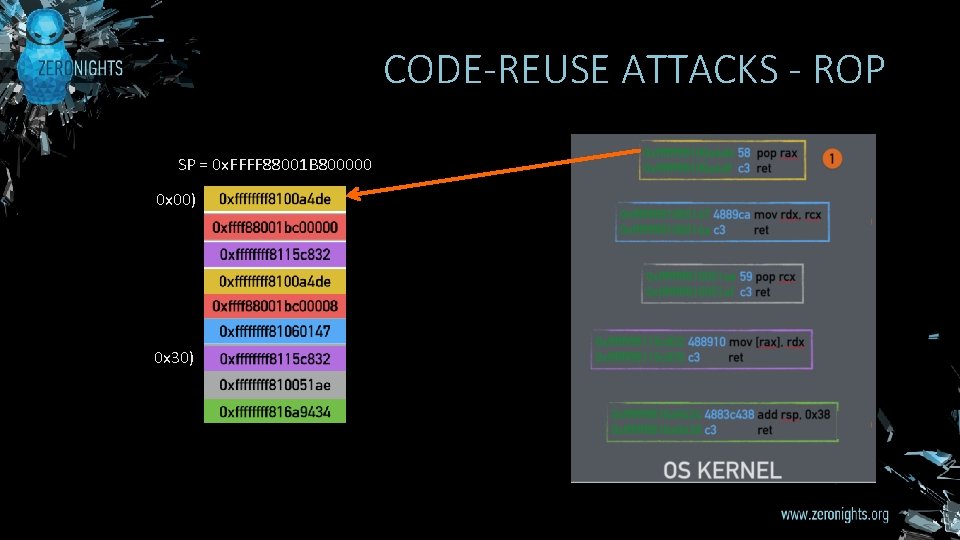
CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

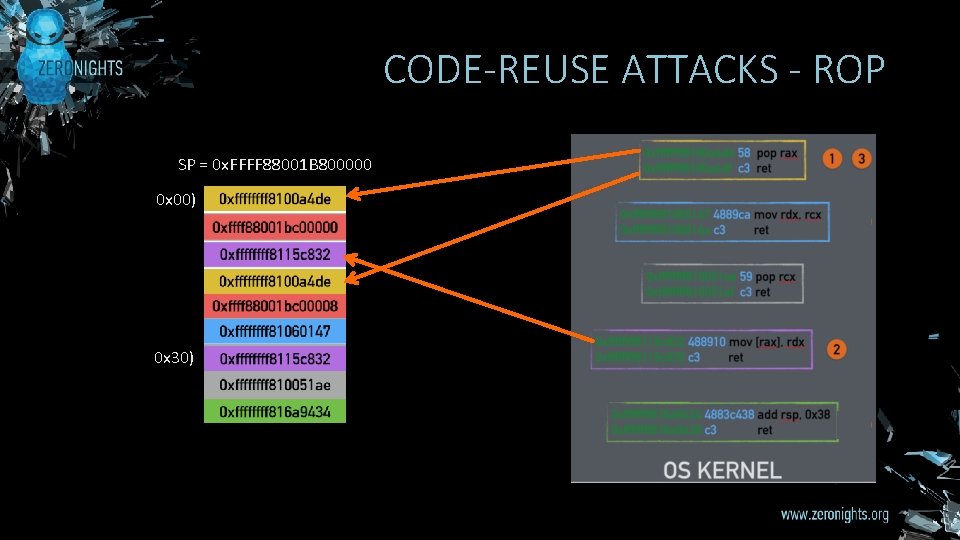
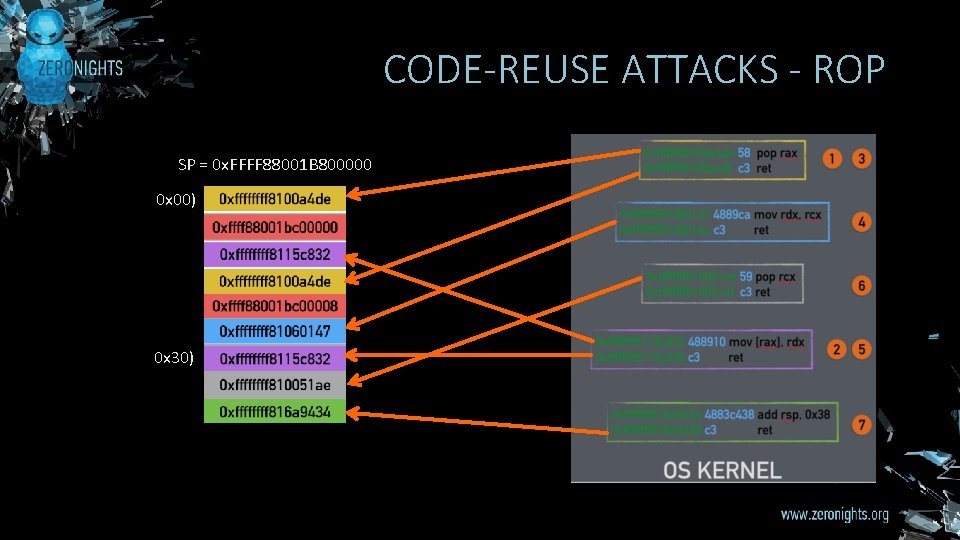
CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

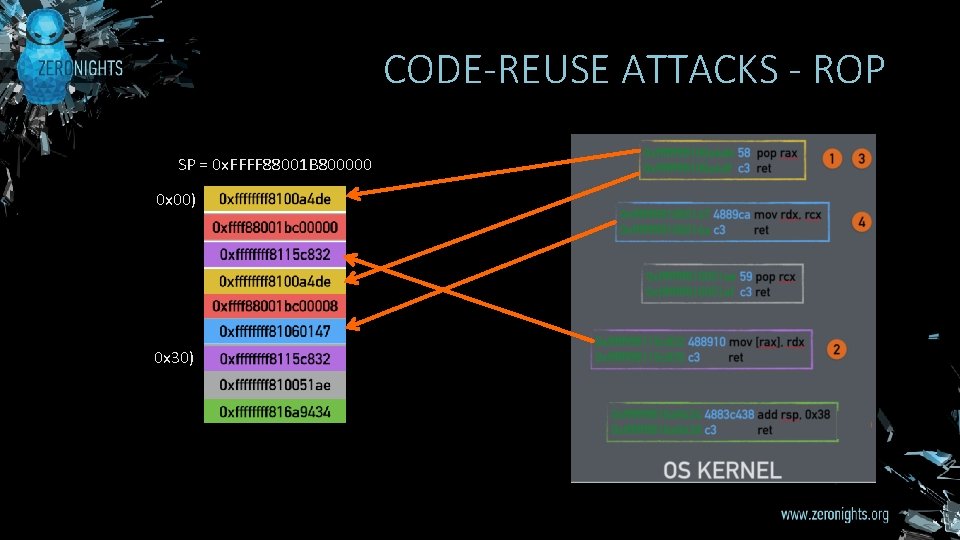
CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

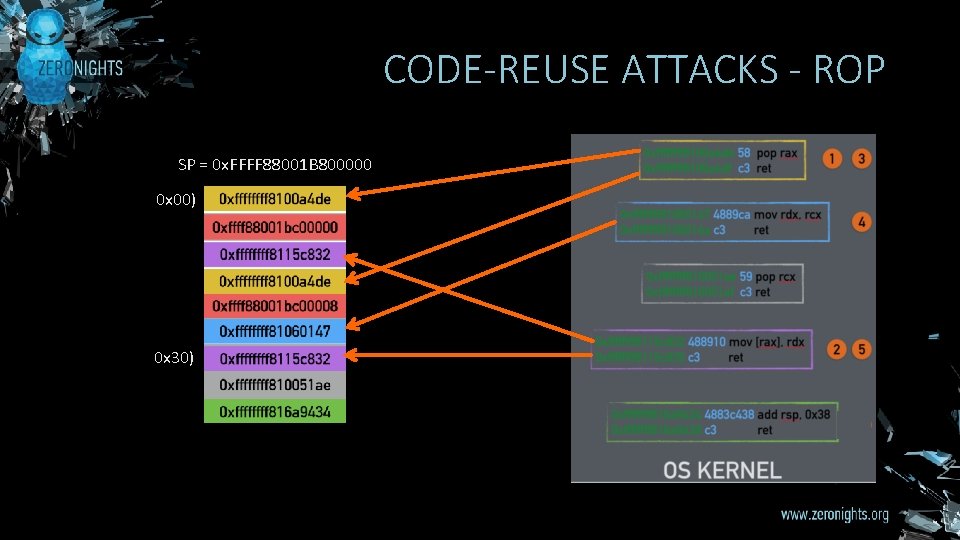
CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30)

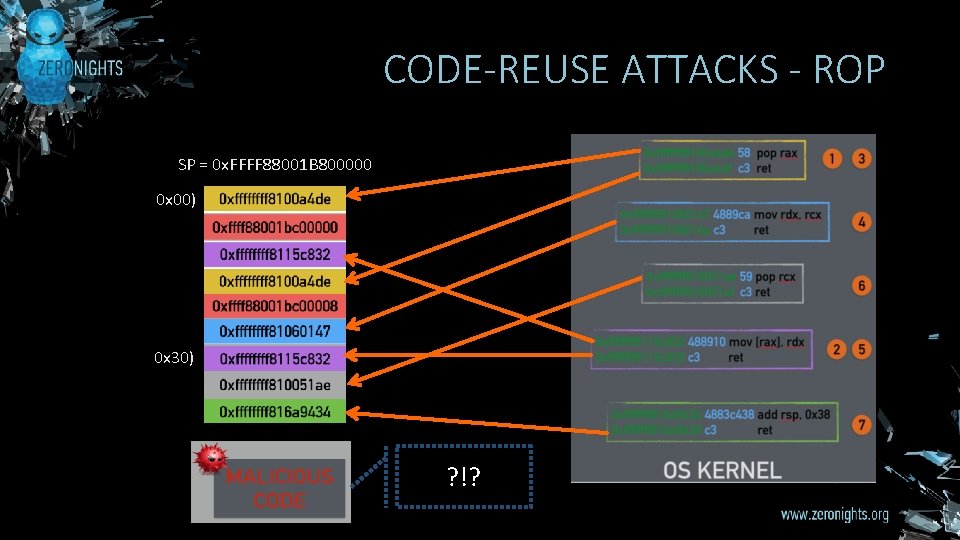
CODE-REUSE ATTACKS - ROP SP = 0 x. FFFF 88001 B 800000 0 x 00) 0 x 30) ? !?

MOTIVATION HW and OS countermeasures forced ROP adoption

MOTIVATION HW and OS countermeasures forced ROP adoption § Persistent ROP rootkit – Vogl et al. [NDSS 14] § ROP as an obfuscation technique (malware in the wild) § All existing tools cope with injected code § No tools to dissect ROP payloads

ROP ROOTKITS

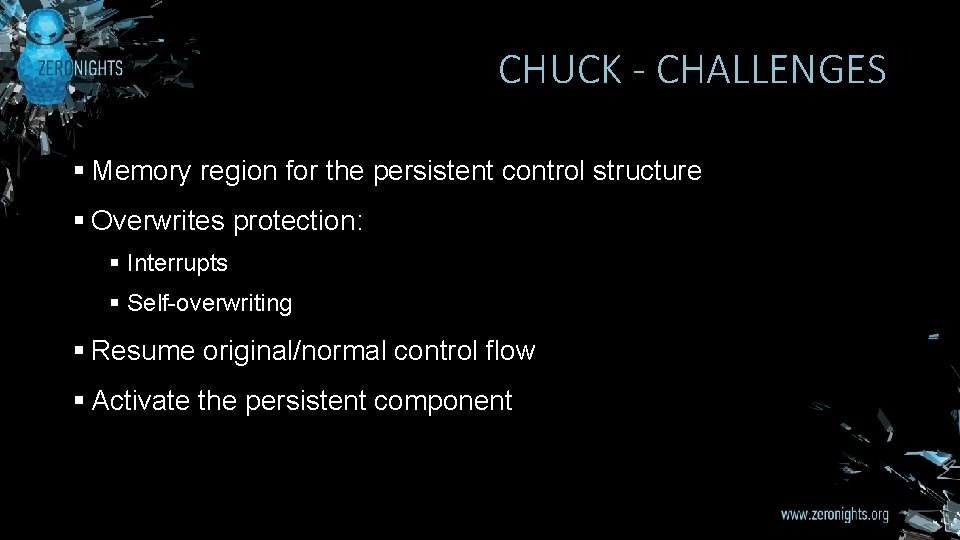
CHUCK - CHALLENGES § Memory region for the persistent control structure § Overwrites protection: § Interrupts § Self-overwriting § Resume original/normal control flow § Activate the persistent component

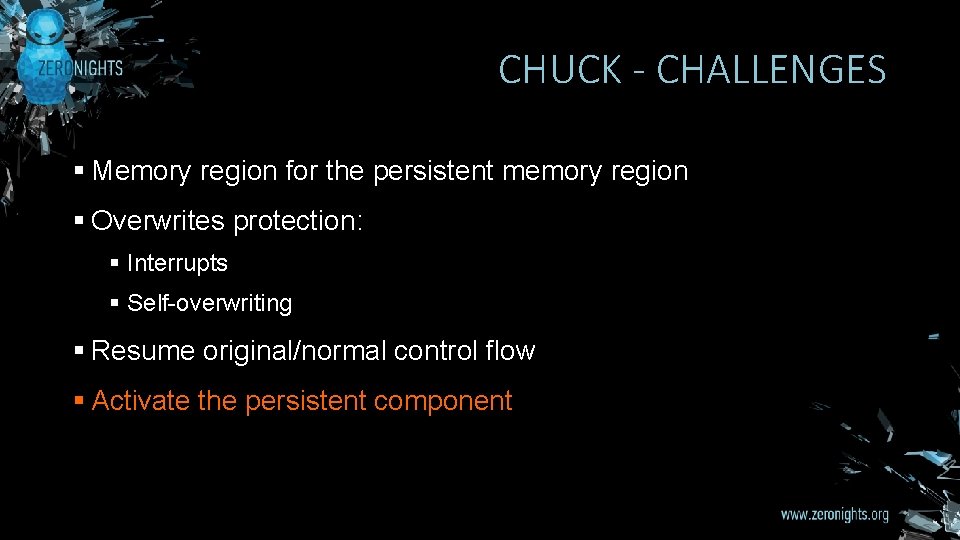
CHUCK - CHALLENGES § Memory region for the persistent memory region § Overwrites protection: § Interrupts § Self-overwriting § Resume original/normal control flow § Activate the persistent component

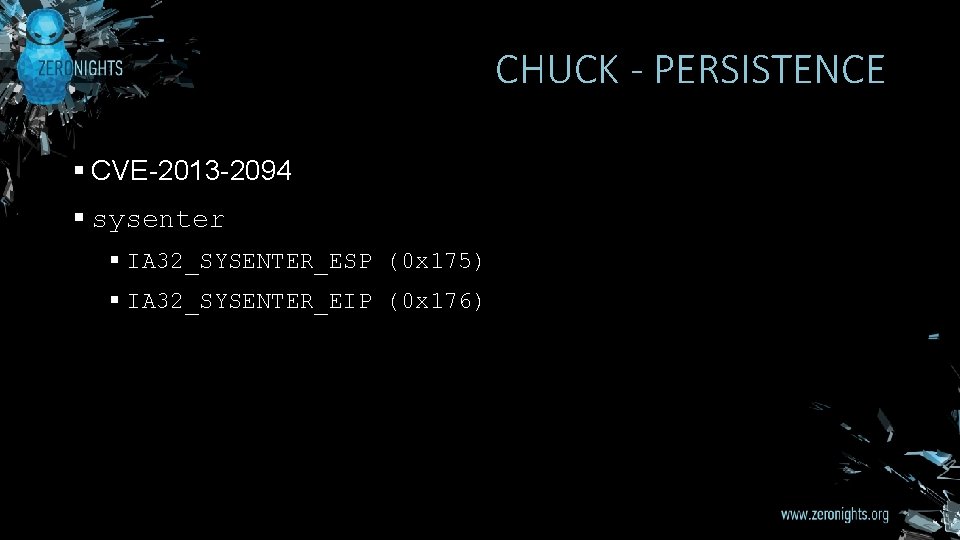
CHUCK - PERSISTENCE § CVE-2013 -2094 § sysenter § IA 32_SYSENTER_ESP (0 x 175) § IA 32_SYSENTER_EIP (0 x 176)

CHUCK - PERSISTENCE § CVE-2013 -2094 § sysenter § IA 32_SYSENTER_ESP (0 x 175) – Copy chain § IA 32_SYSENTER_EIP (0 x 176) - ret

CHUCK § Po. C 1: § LPE: CVE-2013 -2094 § OS: Ubuntu Server 3. 8 with secure boot § Hooks: § sys_read § sys_getdents § Chains: § Copy chain (persistent) § Dispatcher chain § Payload chain 1 https: //www. sec. in. tum. de/persistent-data-only-malware/
CHALLENGES
![CHALLENGES C 1 Verbosity CHALLENGES [C 1] Verbosity](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-25.jpg)
CHALLENGES [C 1] Verbosity
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-26.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values C 3 Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-27.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values C 3 Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-28.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining [C 4] Conditional branches
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values C 3 Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-29.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining [C 4] Conditional branches [C 5] Return to functions
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values C 3 Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-30.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining [C 4] Conditional branches [C 5] Return to functions [C 6] Dynamically generated chains
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values C 3 Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-31.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining [C 4] Conditional branches [C 5] Return to functions [C 6] Dynamically generated chains [C 7] Stop condition
![CHALLENGES C 1 Verbosity C 2 Lack of immediate values C 3 Stack based CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based](https://slidetodoc.com/presentation_image_h/0a331aecfddf08a5d5149468a105386b/image-32.jpg)
CHALLENGES [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining [C 4] Conditional branches [C 5] Return to functions [C 6] Dynamically generated chains [C 7] Stop condition

- Lu et al. – ACSAC 12 - Yadegari et al. – S&P 15 [C 1] Verbosity [C 2] Lack of immediate values [C 3] Stack based instruction chaining [C 4] Conditional branches [C 5] Return to functions [C 6] Dynamically generated chains [C 7] Stop condition CHALLENGES - Stancill et al. – RAID 13 - Lu et al. – ACSAC 12

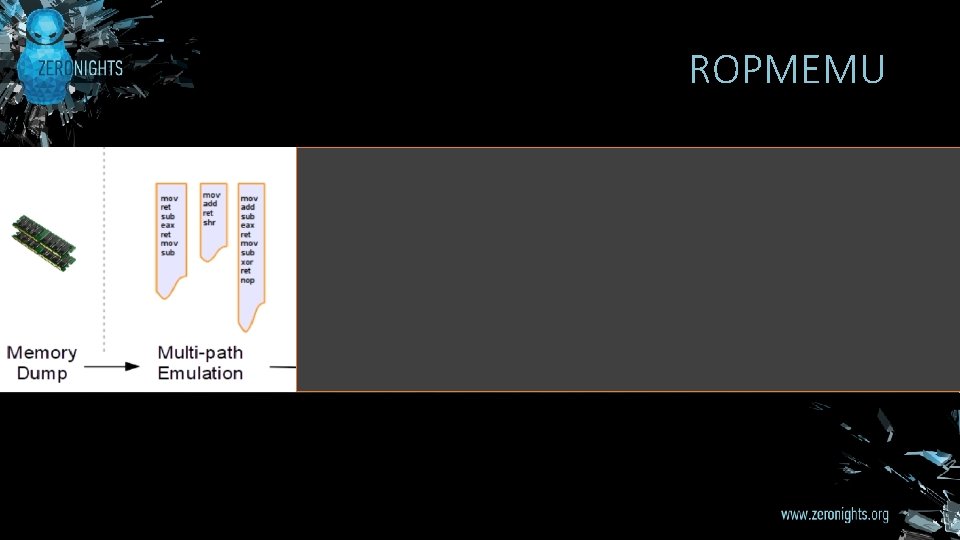
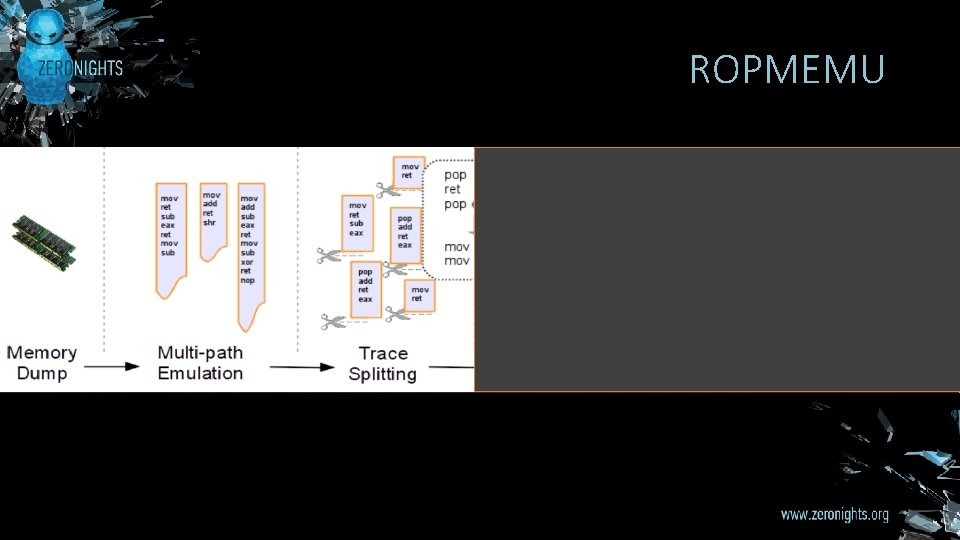
APPROACH § ROPMEMU framework adopts many techniques: § Memory forensics § Code emulation § Multi-path exploration § CFG recovery § Compiler transformations

IMPLEMENTATION § Volatility plugins (ropemu and unchain) depend on: § Capstone § Unicorn § nasm § Standalone scripts (bash and python): § GDB python § pygraphviz

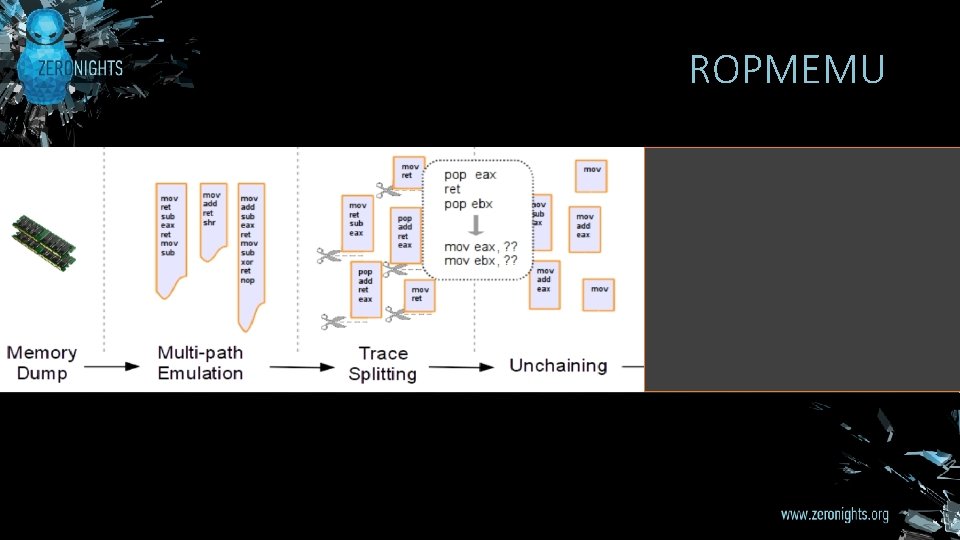
ROPMEMU

ROPMEMU

DEMO 0 x 01

ROPMEMU

DEMO 0 x 02

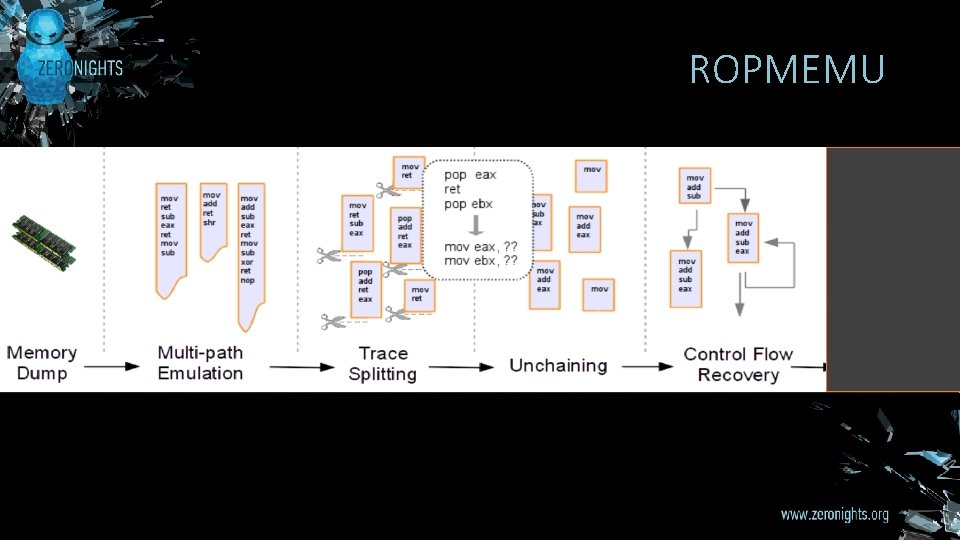
ROPMEMU

DEMO 0 x 03

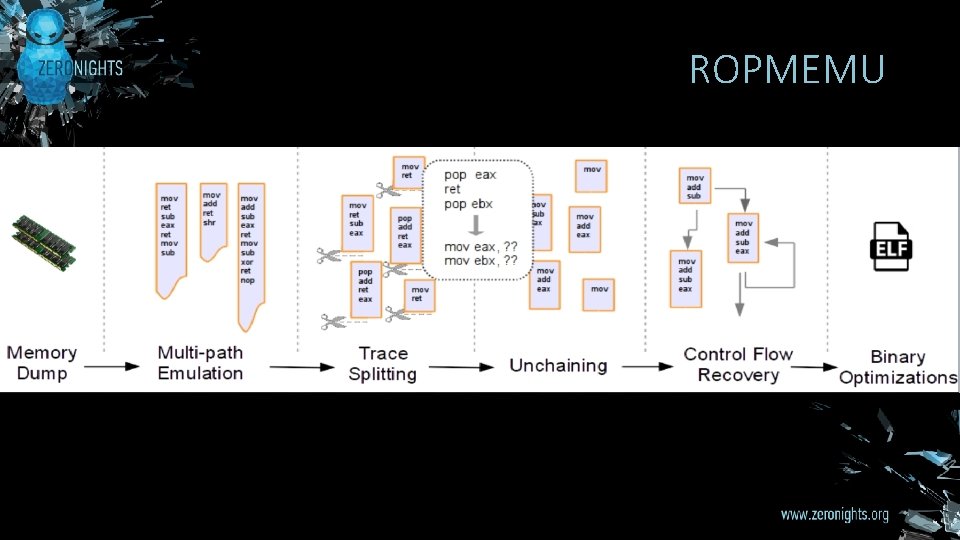
ROPMEMU

ROPMEMU

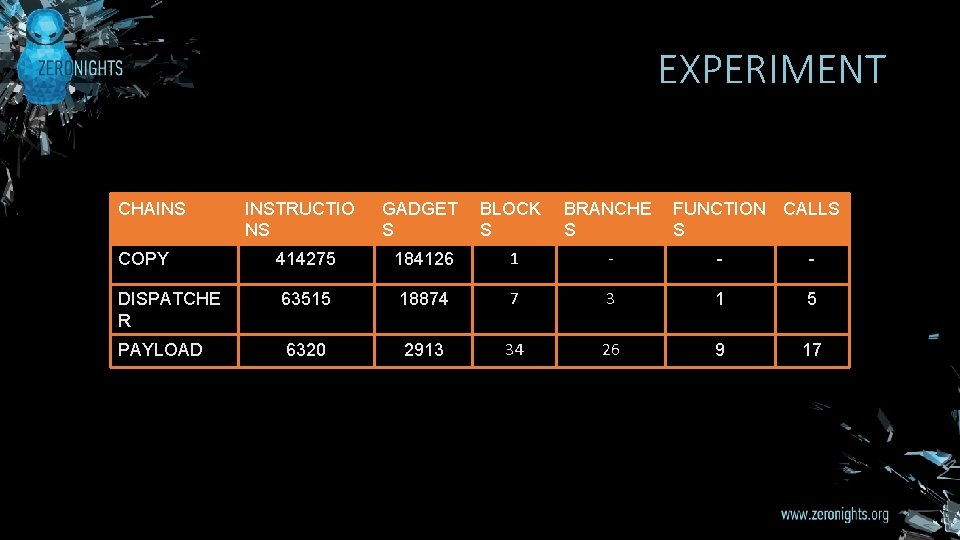
EXPERIMENT CHAINS INSTRUCTIO NS GADGET S BLOCK S BRANCHE S FUNCTION CALLS S COPY 414275 184126 1 - - - DISPATCHE R 63515 18874 7 3 1 5 PAYLOAD 6320 2913 34 26 9 17

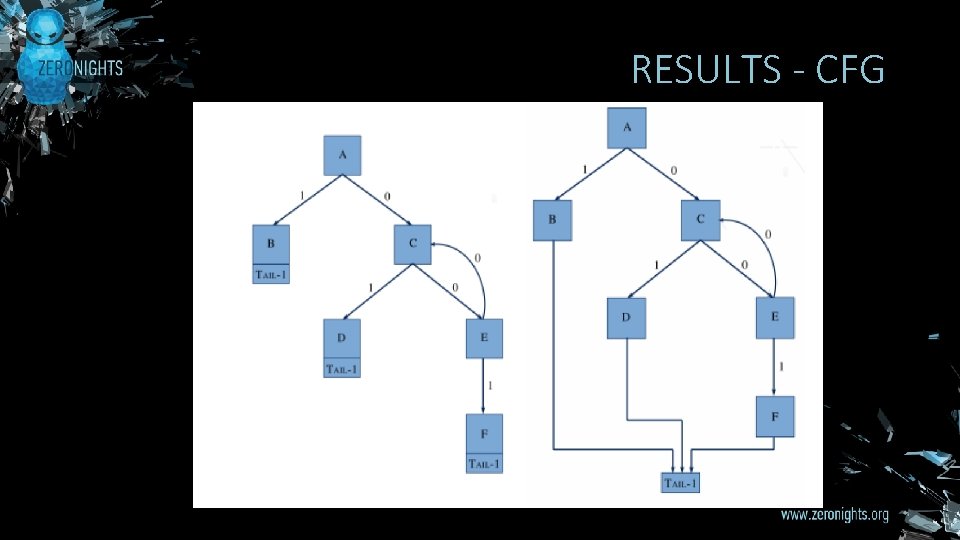
RESULTS - CFG

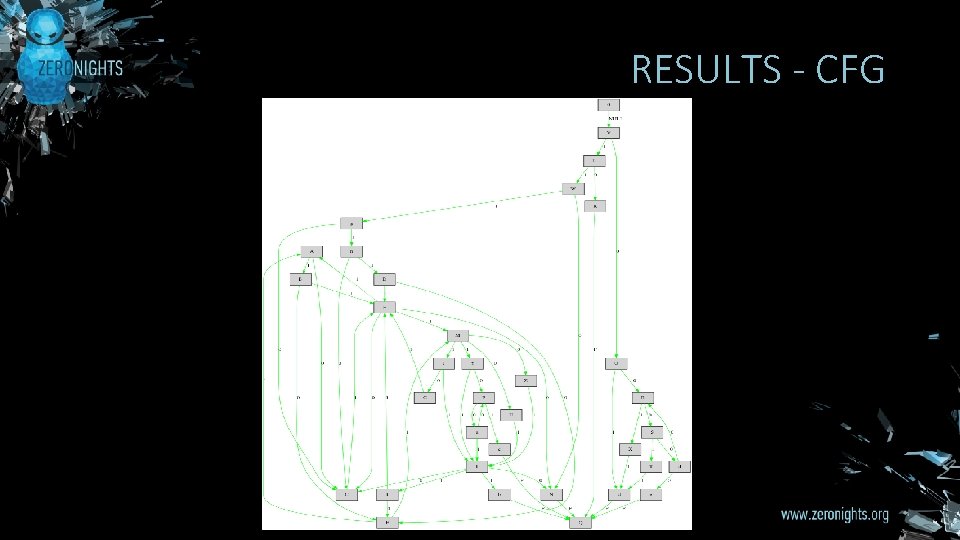
RESULTS - CFG

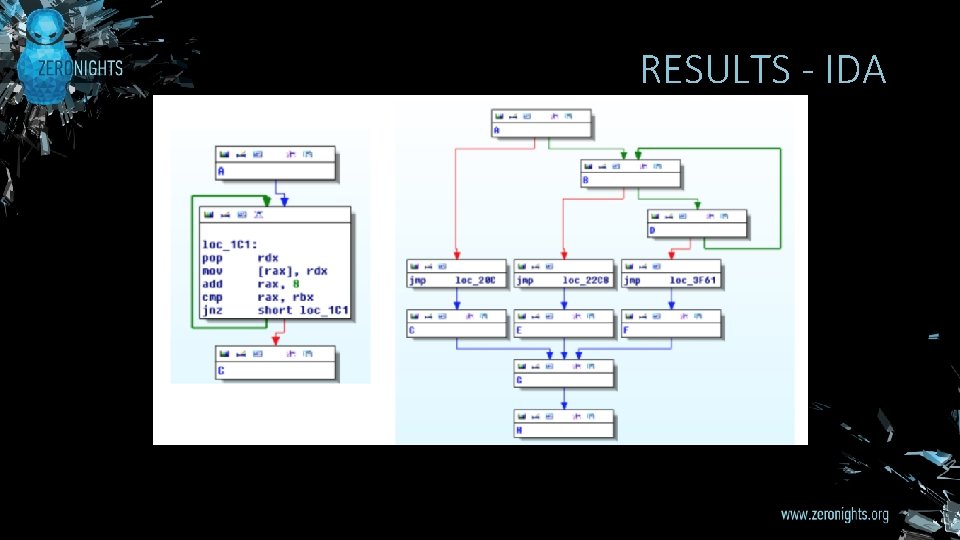
RESULTS - IDA

DEMO 0 x 04

LIMITATIONS § Prone to anti-acquisition § Prone to anti-emulation § Lack of completeness on arbitrary inputs

CONCLUSIONS § Source code: https: //github. com/vrtadmin/ROPMEMU § First public tool to analyze code-reuse payloads § Tested on the most complex public threat

QUESTIONS? Mariano Graziano @emd 3 l magrazia@cisco. com