Disciplined Software Engineering Lecture 13 Software Engineering Institute












































- Slides: 51

Disciplined Software Engineering Lecture #13 Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 Sponsored by the U. S. Department of Defense Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 1

Design Verification, Part 2 This is the second lecture on design verification. It covers • trace tables -symbolic execution -case checking • mathematical program verification • program proofs Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 2

Trace Tables Trace tables are similar to execution tables, but more general. Trace tables examine general program behavior rather than verifying individual cases. Trace tables use • symbolic execution • case checking Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 3

Symbolic Execution - 1 In symbolic execution • the program is represented symbolically • program behavior is examined analytically Symbolic execution can produce quite general verifications. Symbolic execution is not always practical. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 4

Symbolic Execution - 2 In symbolic execution, the approach is to • assign algebraic symbols to the program variables • restate the program as one or more equations in these symbols • analyze the behavior of these equations Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 5

Symbolic Execution - 3 Some questions to ask are • does the program converge on a result? • how does the program behave for both normal and abnormal input values? • does the program always produce the desired results? Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 6

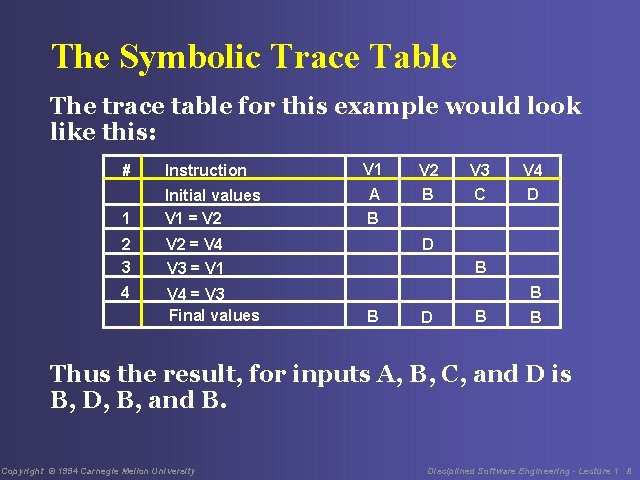
Symbolic Execution Example Given the following simple program segment begin V 1 = V 2 = V 4 V 3 = V 1 V 4 = V 3 end What would be the result for various values of V 1, V 2, V 3, and V 4? Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 7

The Symbolic Trace Table The trace table for this example would look like this: # Instruction 1 Initial values V 1 = V 2 2 3 V 2 = V 4 V 3 = V 1 4 V 4 = V 3 Final values V 1 A V 2 B V 3 C V 4 D B B B D B B Thus the result, for inputs A, B, C, and D is B, D, B, and B. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 8

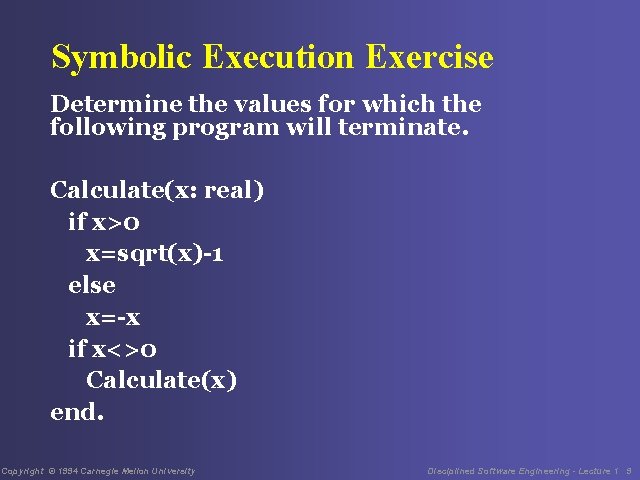
Symbolic Execution Exercise Determine the values for which the following program will terminate. Calculate(x: real) if x>0 x=sqrt(x)-1 else x=-x if x<>0 Calculate(x) end. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 9

Exercise Result - 1 The variables can be represented by x 1 and x 2. The equation for the result of each cycle is if x 1>0: x 2 = sqrt(x 1) -1 if x 1 <= 0: x 2 = -x 1 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 10

Exercise Result - 2 For x 1 = 0, the program terminates on the first cycle. For x 1 = 1, the program terminates on the first cycle. For x 1 = -1, the program terminates on the second cycle. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 11

Exercise Result - 3 Working backwards • for x 2 to be 1, x 1 would have to be 4 • for x 2 to be 4, x 1 would have to be 25 • for x 2 to be 25, x 1 would have to be 676 • for x 2 to be 676, x 1 would have to be 458329 • and so forth Thus, the program terminates for input values of + or - 1, 4, 25, 676, 458329, etc. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 12

Exercise Result - 4 For other large positive or negative values of x 1, the value of x 2 will converge to a nonzero number between -1 and +1. What happens for non-zero values between 1 and +1? Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 13

Exercise Result - 5 Pick x 1=a, a very small number • x 2=sqrt(a)-1, a negative number • next, x 2 is made positive • in 2 more cycles, x 2 is approximately sqrt(a)/2, or slightly larger than a For small x 1, the value of x 2 thus gradually grows larger than x 1. The value of x 2 will thus not reach 0 but will converge on some number less than 1. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 14

Exercise Result - 6 When the value converges, x 1 = x 2 = x and the result would be given by the equation sqrt(x) - 1 = -x the solution to this equation is x = [3 - sqrt(5)]/2 = 0. 381966 Thus, the program will end up cycling between the values of + and - 0. 381966. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 15

Symbolic Execution Advantages Symbolic proofs can be general. Symbolic proofs typically involve less work than other methods. Symbolic proofs are less error prone than executing test cases. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 16

Symbolic Execution Disadvantages Symbolic execution is hard to use except for algorithmic and substitution problems. Symbolic execution proofs are manual and thus error prone. Symbolic execution is difficult to use with complex logic. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 17

Case Checking - 1 Case checking involves the following steps 1. Examine the program and determine the various categories of program behavior. 2. For these categories, identify the cases to be checked. 3. Check the cases to ensure that they cover all possible situations. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 18

Case Checking - 2 4. Using trace tables, either alone or with symbolic execution or proof by induction, examine program behavior for each case. 5. Once every case has been verified, program behavior has been verified. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 19

Trace Table Example - 1 The Clear. Spaces program requirements • clears the leading and trailing spaces from a character string • leaves the imbedded spaces in place • produces a state value 0 for an empty string • produces a state value 1 for a 1 space string • produces a state value 2 for a 2 or more space string • produces a state value 3 for a string containing non-space characters. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 20

Trace Table Example - 2 The portion of Clear. Spaces for removing trailing spaces is Clear. Spaces(var Input: string; State: int) Length = length(Input) if Length > 0 repeat(until State=3 or Length=0) if Input[Length-1] = ‘ ‘ Length = Length - 1 if State < 2 State=State+1 else State = 3 until State=3 or Length=0 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 21

Trace Table Example - 3 To define the cases for trailing spaces, establish the following conventions 1. A message string is a string starting and ending with a non-space character. 2. An input string will consist of m message characters and t trailing spaces 3. m is either >0 or 0 4. t is either >0 or 0 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 22

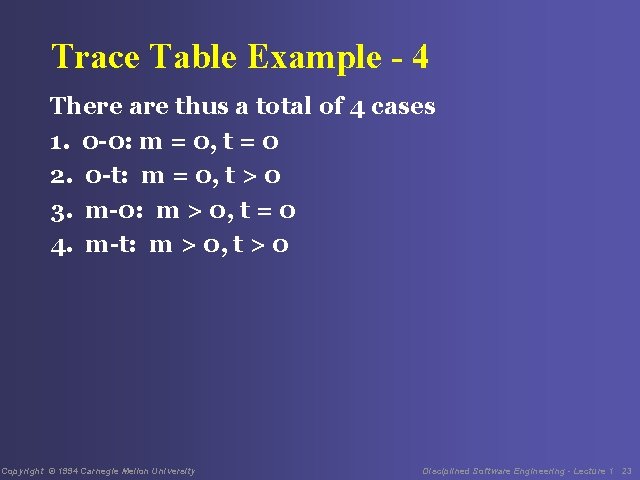
Trace Table Example - 4 There are thus a total of 4 cases 1. 0 -0: m = 0, t = 0 2. 0 -t: m = 0, t > 0 3. m-0: m > 0, t = 0 4. m-t: m > 0, t > 0 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 23

Trace Table Example - 5 The strategy is to verify program behavior with each case, using whatever method is most appropriate. 1. Check the 0 -0 case by itself, using an execution table. 2. Check the other cases, using proof by induction. 3. Do each proof with a trace table, using the execution table method described in lecture 12. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 24

Verifying Program Correctness These methods are based on treating programs as mathematical theorems. They are particularly useful during design and design review. Because program verification often involves sophisticated reasoning, it is important to check your work carefully. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 25

Correctness Verification The correctness verification approach is to • identify all the program cases. • use trace tables to evaluate all the conditions the program must satisfy for every case • use proof by induction where appropriate The program is verified if all the conditions are satisfied for every case. While this verification approach works with most design constructs, only loops are described in this lecture. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 26

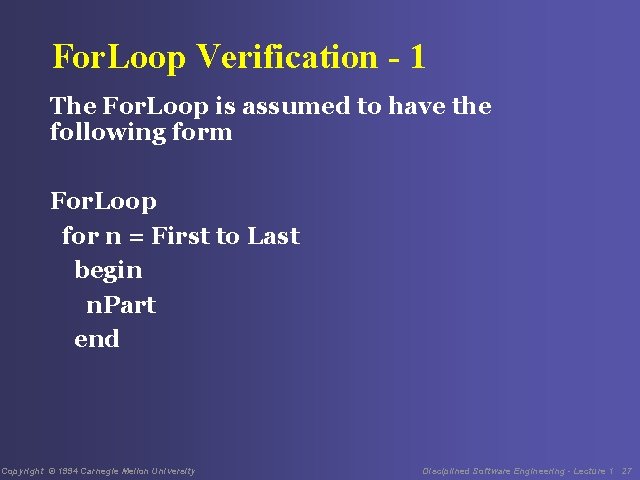
For. Loop Verification - 1 The For. Loop is assumed to have the following form For. Loop for n = First to Last begin n. Part end Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 27

For. Loop Verification - 2 The for-loop conditions require that the answer to the following question be true Does For. Loop = First. Part+Second. Part+. . . +Last. Part Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 28

For. Loop Example - 1 Verify that the following program produces the factorial of n. factorial(n) begin x=1 for i=1 to n x = x*i return = x end Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 29

For. Loop Example - 2 First, identify the cases. The cases are for n = 1 and for n > 1. For n = 1 For. Loop = 1! = 1 First. Part+Second. Part+. . . =First. Part = 1*1=1 The case for n = 1 is thus valid. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 30

For. Loop Example - 3 For n > 1, say 3 For. Loop = 3! = 6 First. Part+Second. Part+Third. Part = 1*1*2*3 =6 The case for n = 3 is thus true. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 31

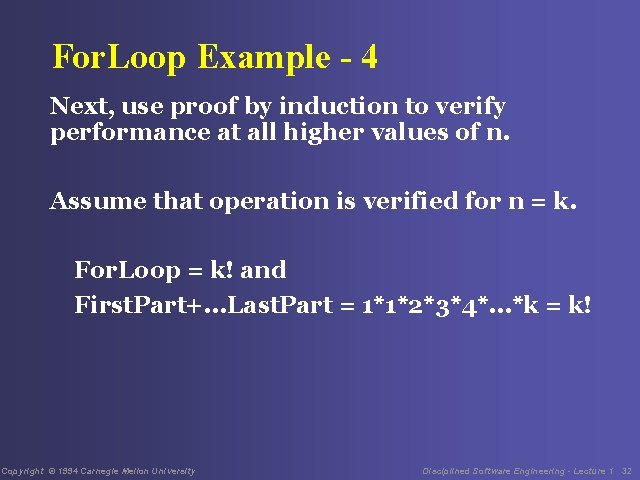
For. Loop Example - 4 Next, use proof by induction to verify performance at all higher values of n. Assume that operation is verified for n = k. For. Loop = k! and First. Part+. . . Last. Part = 1*1*2*3*4*. . . *k = k! Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 32

For. Loop Example - 5 Now, for k+1 For. Loop = k!*(k+1) = (k+1)! First. Part+. . . Last. Part = 1*1*2*3*4*. . . *k*(k+1) = (k+1)! The program is thus valid for k+1 so, by induction, it is valid for all values of n => 1. You should next check to find any k values on your system where this is not true. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 33

While. Loop Verification - 1 The While. Loop is assumed to have the following form While. Loop while While. Test begin Loop. Part end Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 34

While. Loop Verification - 2 Question 1. Is loop termination guaranteed for any argument of While. Test? Question 2. When While. Test is true does While. Loop = Loop. Part followed by While. Loop? Question 3. When While. Test is false does While. Loop = identity? Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 35

While. Loop Example - 1 Use the first part of a program to reduce a floating point number to standard form. • Exp is a positive integer • Mant is to be made a positive non- zero number with one digit before the decimal point. Normalize. Real(Mant, Exp, Neg. Ex) while Mant >= 10 do Mant = Mant/10 if Neg. Ex then Exp=Exp-1 else Exp = Exp + 1 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 36

While. Loop Example - 2 Since the value of Exp is not material, there are 3 cases of interest. Each of these cases is examined for Neg. Ex true and Neg. Ex false. 1. Mant <10 2. Mant = 10 3. Mant > 10 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 37

While. Loop Example - 3 Question 1. Is loop termination guaranteed for any argument of While. Test? Case 1. Mant < 10, the while test fails immediately, so the loop terminates. Case 2. Mant = 10, the while test will fail after one cycle, thus terminating the loop. In both cases, this happens regardless of the value of Neg. Ex. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 38

While. Loop Example - 4 Question 1, continued Case 3. Mant > 10, can be shown by induction • Mant = k*10**n, where 1 <= k < 10 • when n = 1, the test fails after 1 cycle • if the test is true for some value n=m then after m cycles, Mant = k • thus for n=m+1, after m cycles, Mant = k*10 and the While. Test will fail in one more cycle Since the value of Neg. Ex does not affect the result, question 1 is satisfied for all n => 1. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 39

A While. Loop Example - 5 Question 2. When While. Test is true does While. Loop = Loop. Part followed by While. Loop? Case 1. Mant < 10, is not pertinent since While. Test is never true. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 40

A While. Loop Example - 6 To examine the other cases, check that this program gives the same result as While. Loop (the check is described in the next foil). Mant = Mant/10 if Neg. Ex then Exp=Exp-1 else Exp = Exp + 1 while Mant >= 10 do Mant = Mant/10 if Neg. Ex then Exp=Exp-1 else Exp = Exp + 1 Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 41

A While. Loop Example - 7 Question 2 - continued For case 2. Mant = 10, the value of Neg. Ex is immaterial • While. Loop has one cycle, leaving Mant = 1 • Loop. Part followed by While. Loop starts with Mant = 10, Loop. Part leaves value 1, and While. Loop leaves the same value 1 Since both give the same result, the answer is true. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 42

While. Loop Example - 8 Question 2 - Continued Case 3. Mant > 10, can be shown by induction. • Mant = k*10**n, where 1<=k<10 • when n = 1, While. Loop would take one cycle and the While. Loop following the Loop. Part would take none • when n > 1 the While Loop following Loop. Part would take one less cycle with the same result Question 2 is thus satisfied for all cases. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 43

While. Loop Example - 9 Question 3. When While. Test is false does While. Loop = identity? Case 1. Mant < 10 is the only case where While. Test is false. Since, in this case the program is not executed, the conditions are left undisturbed which is the definition of identity. Question 3 is thus satisfied. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 44

Repeat. Until Verification - 1 Repeat. Until has the following form Repeat. Until begin Loop. Part Until. Test end Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 45

Repeat. Until Verification - 2 Repeat-until verification is satisfied if the answers to the following 3 questions are true. Question 1. Is loop termination guaranteed for any argument of Until. Test? Question 2. When the Until. Test after Loop. Part is false, does Repeat. Until = Loop. Part followed by Repeat. Until? Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 46

Repeat. Until Verification - 3 Question 3. When Until. Test after Loop. Part is true, does Repeat. Until = Loop. Part? The repeat-until verification follows the same logical format as While. Loop verification so no example is given. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 47

Comments on Program Verification - 1 If done correctly, these verification methods are quite general and can guarantee program correctness. The verification methods are tricky and require skill. While you should attempt to use these methods, when in doubt, check with a trace table or an execution table. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 48

Comments on Program Verification - 2 With practice, you can do program verification quite rapidly. The careful examination of all possible cases will quickly reveal most defects. The loop termination test is critical because endless loops are hard to identify with other methods. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 49

Lecture #13 Assignment Start work on the final report. Update the process used to develop the midterm report and use it to develop the final report. Turn in the updated process, the plan for the work, the actual data for the work, and the final report. Consult the report specifications in Appendix D. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 50

Messages to Remember from Lecture 13 1. There are many powerful verification techniques. 2. Experiment with these techniques, find the ones that are most effective for you, and use them. 3. The time you spend verifying designs will be repaid many times by the testing time you save. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 51