Disciplined Software Engineering Lecture 12 Software Engineering Institute






























- Slides: 41

Disciplined Software Engineering Lecture #12 Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 Sponsored by the U. S. Department of Defense Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 1

Design Verification Design verification is covered in 2 lectures. This lecture addresses • the reasons for design verification • state machine correctness • execution tables • proof by induction The next lecture covers • trace tables • mathematical program verification • program proofs Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 2

Need for Design Verification - 1 As you work to improve your personal software process, you will likely find it hard to significantly reduce the numbers of design defects you make. By using checklists and taking increased care, you can improve the yield of your code reviews. To improve the yield of design reviews, you need to use disciplined verification methods. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 3

Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 4

Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 5

Need for Design Verification - 2 An orderly approach to design verification is essential because • many common design defects are caused by overlooked conditions • what seem like unlikely situations become more likely with high-powered computing systems • conditions that were not possible with an initial program version may be induced by later modifications Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 6

Need for Design Verification - 3 By following a structured design verification procedure, you are more likely to • see overlooked conditions • identify rarely exposed risks • recognize possible future exposures By recording data on your design reviews, you can simplify later design inspections. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 7

Using Design Verification - 1 Design verification methods should be used • during design reviews • during design inspections Your design verification methods should focus on the defect types that have caused you the most trouble in test. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 8

Using Design Verification- 2 The topics covered in this and the next lecture were selected because they address the design defect categories that caused me the most trouble • state machine structures • loop constructs I would use additional verification methods for the following defect types if they were available • pointers • interfaces Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 9

Design Verification Topics The design verification topics covered in this and the next lecture are • verifying state machine correctness • execution tables • proof by induction • trace tables • mathematical program verification Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 10

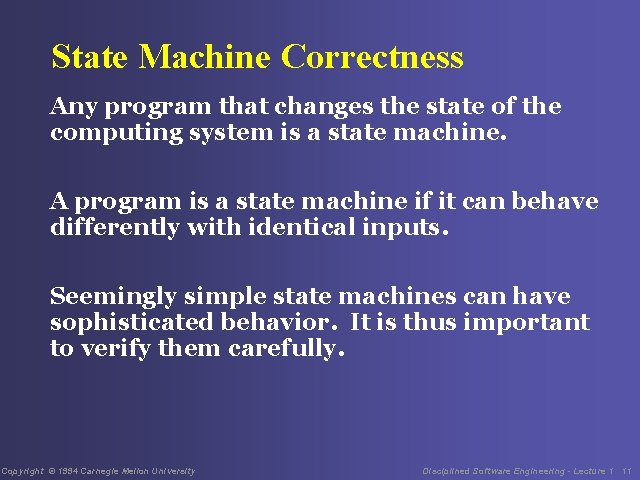
State Machine Correctness Any program that changes the state of the computing system is a state machine. A program is a state machine if it can behave differently with identical inputs. Seemingly simple state machines can have sophisticated behavior. It is thus important to verify them carefully. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 11

State Machine Verification The steps in state machine verification are to • check to ensure the state machine has no hidden traps or loops • check that the set of all states is complete and orthogonal • check that the set of all transitions from every state are complete and orthogonal After verifying state machine correctness, ensure that the program performs the intended application functions. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 12

Hidden Traps or Loops - 1 To check for hidden traps and loops • construct the state template • construct a state machine diagram • determine if any exit states are unreachable from any other states If any states cannot reach an exit state, this is not a proper state machine. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 13

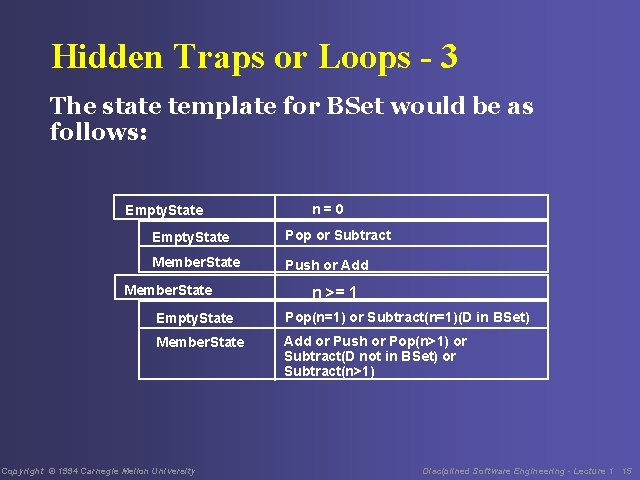
Hidden Traps or Loops - 2 Example: consider an object BSet as follows • 2 states: Empty. State, Member. State • 4 methods: Push, Pop, Add, Subtract • Push adds a member to BSet • Pop removes a member from BSet • Add adds a member to BSet if it does not already contain an identical member • Subtract removes a member from BSet if it contains an identical member Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 14

Hidden Traps or Loops - 3 The state template for BSet would be as follows: Empty. State n=0 Empty. State Pop or Subtract Member. State Push or Add Member. State n >= 1 Empty. State Pop(n=1) or Subtract(n=1)(D in BSet) Member. State Add or Push or Pop(n>1) or Subtract(D not in BSet) or Subtract(n>1) Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 15

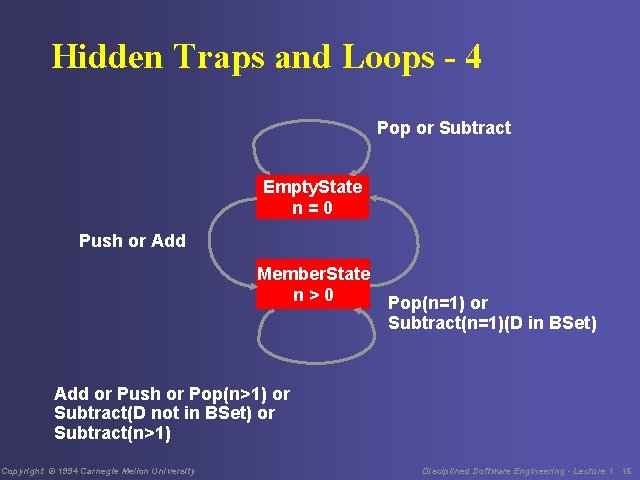
Hidden Traps and Loops - 4 Pop or Subtract Empty. State n=0 Push or Add Member. State n>0 Pop(n=1) or Subtract(n=1)(D in BSet) Add or Push or Pop(n>1) or Subtract(D not in BSet) or Subtract(n>1) Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 16

Hidden Traps or Loops - 5 It is thus clear that this state machine has no hidden traps or loops. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 17

All Possible States - 1 A common problem is to overlook some state machine state. Examples are initial states, empty states, error states, and so forth. Examine all possible conditions of the state parameters to ensure they are either included or truly impossible. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 18

All Possible States - 2 Checking the BSet example: • Empty. State has n = 0 • Member. State has n > 0 • since n cannot be < 0, this covers all cases To ensure that none of the n > 0 states should be distinct, check to see if any of them exhibit different behavior from the others. A check of the state template or state diagram shows that all n>0 states behave identically. Added states are thus unnecessary. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 19

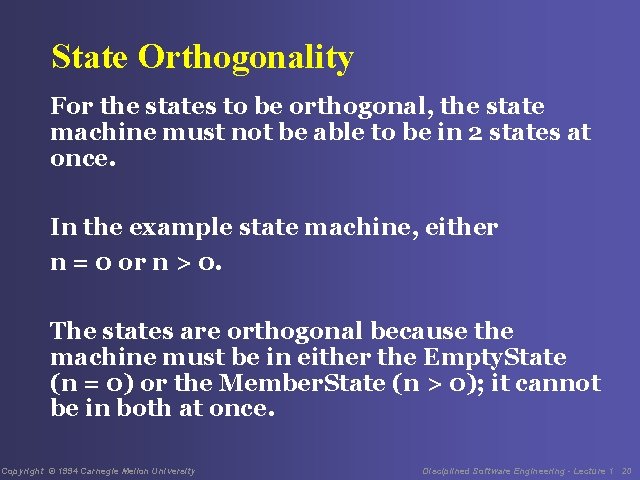
State Orthogonality For the states to be orthogonal, the state machine must not be able to be in 2 states at once. In the example state machine, either n = 0 or n > 0. The states are orthogonal because the machine must be in either the Empty. State (n = 0) or the Member. State (n > 0); it cannot be in both at once. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 20

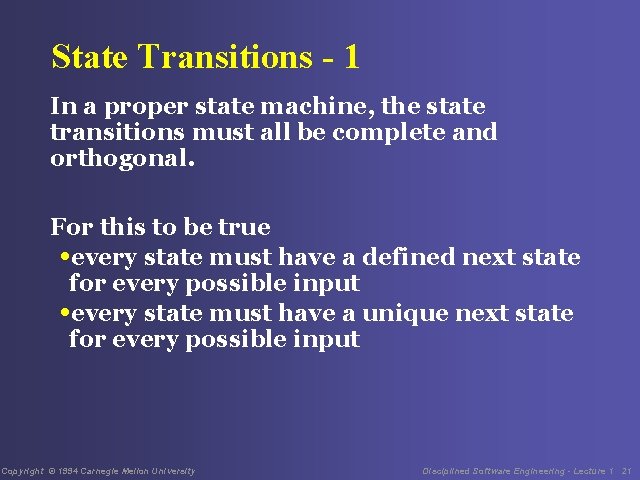
State Transitions - 1 In a proper state machine, the state transitions must all be complete and orthogonal. For this to be true • every state must have a defined next state for every possible input • every state must have a unique next state for every possible input Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 21

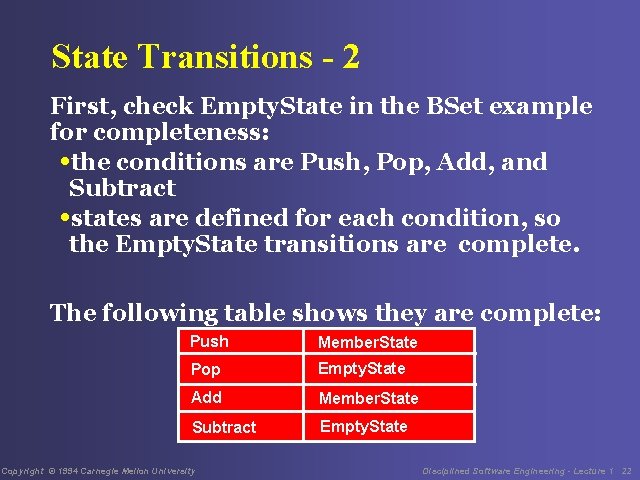
State Transitions - 2 First, check Empty. State in the BSet example for completeness: • the conditions are Push, Pop, Add, and Subtract • states are defined for each condition, so the Empty. State transitions are complete. The following table shows they are complete: Push Member. State Pop Empty. State Add Member. State Subtract Empty. State Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 22

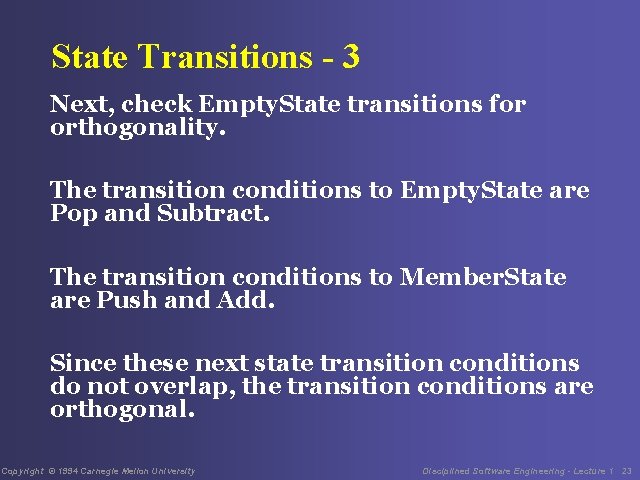
State Transitions - 3 Next, check Empty. State transitions for orthogonality. The transition conditions to Empty. State are Pop and Subtract. The transition conditions to Member. State are Push and Add. Since these next state transition conditions do not overlap, the transition conditions are orthogonal. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 23

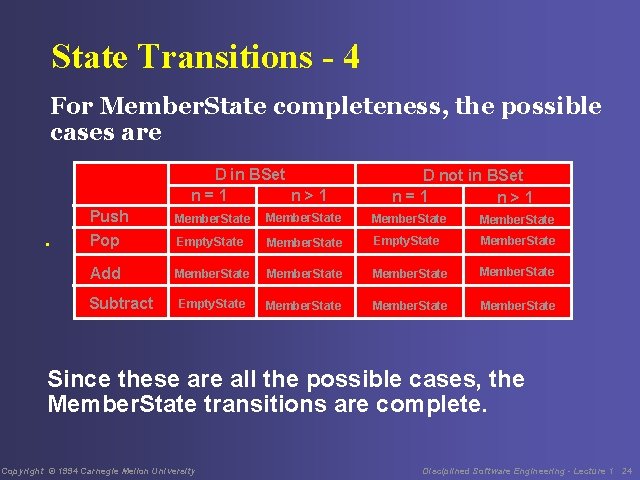
State Transitions - 4 For Member. State completeness, the possible cases are D in BSet n=1 n>1 D not in BSet n=1 n>1 Push Pop Member. State Empty. State Member. State Add Member. State Empty. State Member. State Subtract Since these are all the possible cases, the Member. State transitions are complete. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 24

State Transitions - 5 For Member. State orthogonality, there must be no overlap between the transitions. • the transitions from Member. State to Empty. State occur when: Pop(n=1) or Subtract(n=1) and (D in BSet) • the transitions from Member. State to Member. State occur when: Add + Push + Pop(n>1) + Subtract(D not in BSet) + Subtract(n>1) As is clear from the previous chart, these two cases have no condition in common and are thus orthogonal. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 25

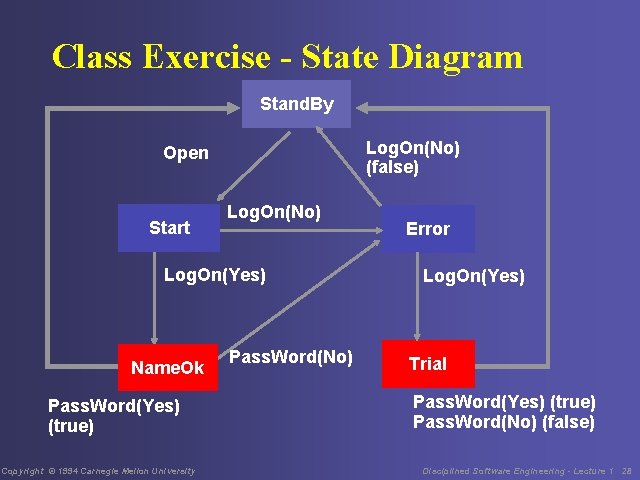
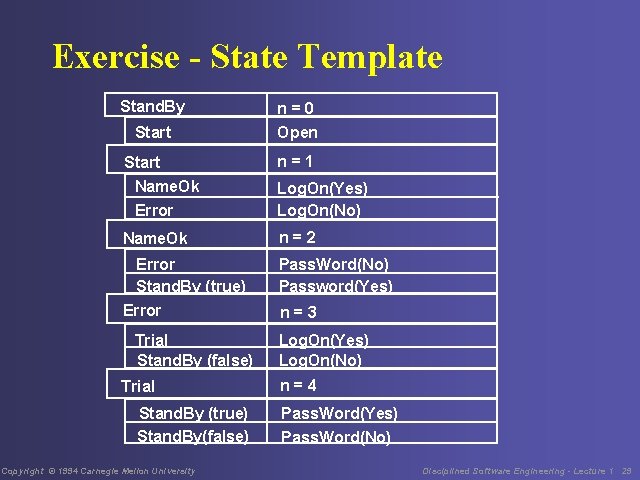
Class Exercise - 1 The Sign. On object is to have the following methods • Open - initiates a sign-on procedure • Log. On - requests a name • if the name is correct, Pass. Word requests the password • if the Pass. Word is correct, Sign. On terminates with the value true • if there is any error, the program starts again at Log. On • for any two errors, Sign. On terminates with the value false Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 26

Class Exercise - 2 Construct the Sign. On state template and state diagram. Check for hidden traps and loops. Check the states for completeness and orthogonality. Check the transitions for completeness and orthogonality. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 27

Class Exercise - State Diagram Stand. By Log. On(No) (false) Open Start Log. On(No) Log. On(Yes) Name. Ok Pass. Word(Yes) (true) Copyright © 1994 Carnegie Mellon University Pass. Word(No) Error Log. On(Yes) Trial Pass. Word(Yes) (true) Pass. Word(No) (false) Disciplined Software Engineering - Lecture 1 28

Exercise - State Template Stand. By Start n=0 Open Start Name. Ok Error n=1 Name. Ok n=2 Error Stand. By (true) Error Pass. Word(No) Password(Yes) Trial Stand. By (false) Trial Stand. By (true) Stand. By(false) Copyright © 1994 Carnegie Mellon University Log. On(Yes) Log. On(No) n=3 Log. On(Yes) Log. On(No) n=4 Pass. Word(Yes) Pass. Word(No) Disciplined Software Engineering - Lecture 1 29

Execution Tables - 1 An execution table is an orderly way to trace program execution. • it is a manual check of the program flow • it starts with initial conditions • a set of variable values is selected • each execution step is examined • every change in variable values is entered • program behavior is checked against the specification Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 30

Execution Tables - 2 The advantages of execution tables are • they are simple • they give reliable proofs The disadvantages of execution tables are • they only check one case at a time • they are time consuming • they are subject to human error Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 31

Execution Table Procedure To use an execution table • identify the key program variables and enter them at the top of the trace table • enter the principal program steps • determine and enter the initial conditions • trace the variable values through each program step • for repeating loops, additional execution table steps for each additional loop cycle • for long loops, group intermediate steps if their results are obvious Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 32

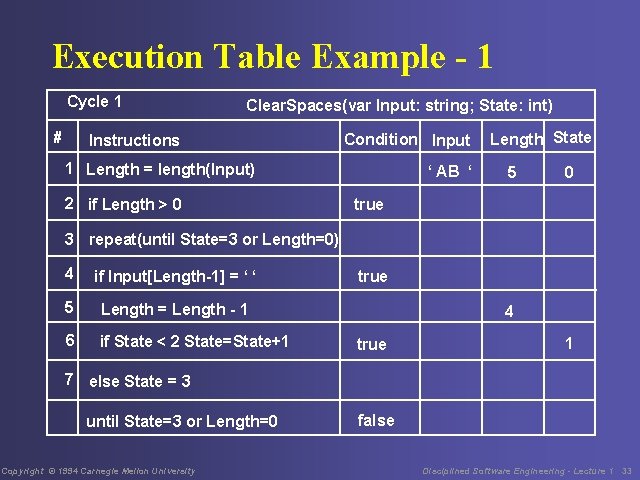
Execution Table Example - 1 Cycle 1 # Clear. Spaces(var Input: string; State: int) Instructions Condition Input 1 Length = length(Input) 2 if Length > 0 ‘ AB ‘ Length State 5 0 true 3 repeat(until State=3 or Length=0) 4 if Input[Length-1] = ‘ ‘ 5 Length = Length - 1 6 if State < 2 State=State+1 true 4 true 1 7 else State = 3 until State=3 or Length=0 Copyright © 1994 Carnegie Mellon University false Disciplined Software Engineering - Lecture 1 33

Execution Table Example - 2 3 cycles are required before the until condition is satisfied. Just as with a test case, the execution table will only prove the case for this specific variable combination. Carefully check the initial conditions to ensure they are set by the program. Double check the execution table for errors and omissions. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 34

Proof by Induction This method applies to Boolean functions with integer parameters. It states if f(n) is true for n = k and if • when n = z where z > k • and f(z) is true • you can show that f(z+1) is true then f(n) is true for all values of n larger than k Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 35

Proof by Induction Example: for i=1 to Limit do xyz If • you can show that this is true for Limit = 1 and • it is true for some arbitrary larger value z and • you can then show it would be true for z+1 • then it is true for all positive values of Limit Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 36

A Proof by Induction Technique If • you have a design element using variable x • you verify that it works for x = k Next • assume it works for some larger value x = z • try to find a value of z where program behavior would be improper at z + 1 If you cannot, the proof is completed. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 37

Factorial Example - 1 Prove that the following program produces N! Factorial(N) F=1 for i = 1 to N F = F*i return = F Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 38

Factorial Example - 2 Pick k = 1 and show that when N=1, F = N! • since 1 factorial is 1, this is correct Next, assume that when N = z, F = z! Finally, find any value of z where F(z) = z! and F(z+1) <> (z+1)! Such cases would only occur when • the computing number system was exceeded • computing capacity was exceeded Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 39

Assignment #12 Read Chapter 12 in the text. Continue developing program 10 A. If you have time, start working on the Final Report, R 5. The specifications for R 5 can be found in Appendix D. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 40

The Messages to Remember from Lecture 12 1. Your design review yield will significantly improve if you use disciplined design review methods. 2. The time spent verifying designs will be more than repaid by the testing time saved. 3. Practice verification techniques and select the most effective for finding the defects you most commonly find in testing. Copyright © 1994 Carnegie Mellon University Disciplined Software Engineering - Lecture 1 41