DIGITAL WATERMARKS THE WAY TO PROTECT MULTIMEDIA FILES
















- Slides: 23

DIGITAL WATERMARKS THE WAY TO PROTECT MULTIMEDIA FILES By: Vladimir Novikov

Digital Watermarking? Allows users to embed SPECIAL PATTERN or SOME DATA into digital contents without changing its perceptual quality. n When data is embedded, it is not written at HEADER PART but embedded directly into digital media itself by changing media contents data n Watermarking is a key process for the PROTECTION of copyright ownership of electronic data. n

Features of Watermarking n Invisible/Inaudible n Information is embedded without digital content degradation, because of the level of embedding operation is too small for human to notice the change. n Inseparable n The embedded information can survive after some processing, compression and format transformation. n Unchanging data file size n Data size of the media is not changed before and after embedding operation because information is embedded directly into the media.

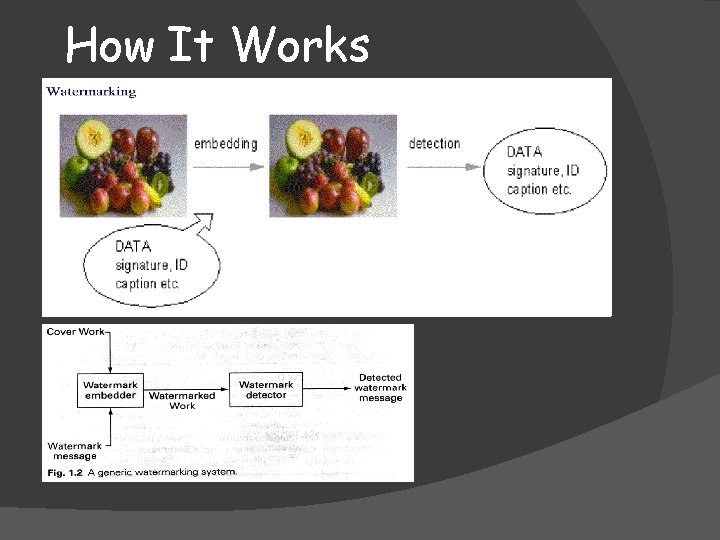
How It Works

CLASSIFICATION OF WATERMARK n According to Human Perception n According to Robustness n n Invisible Visible Fragile Semi fragile Robust According to types of Document n n Text Image Audio Video

CLASSIFICATION BY “HUMAN PERCEPTION”

Visible Watermark Logo or seal of the organization which holds the rights to the primary image, it allows the primary image to be viewed, but still visible it clearly as the property of the owning organization. Overlay the watermark in such a way that makes it difficult to remove, if the goal of indicating property rights is to be achieved.

Visible Watermark Image with watermark Watermark

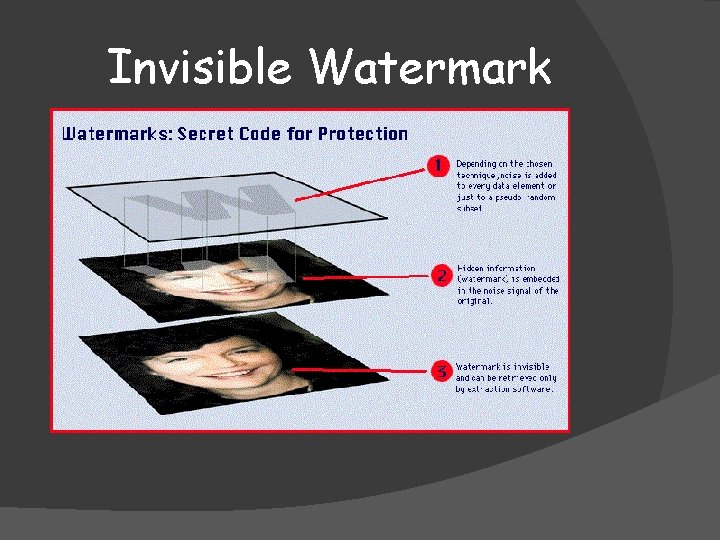
Invisible Watermark Embedding level is too small to notice Can be retrieved by extraction software Applications: Authentication Copyrighting Etc…

Invisible Watermark

CLASSIFICATION BY “ROBUSTNESS”

Fragile/Semi Fragile/Robust A watermark is called fragile if it fails to be detected after the slightest modification. A watermark is called semi-fragile if it resists beginning transformations but fails detection after malignant transformations. A watermark is called robust if it resists a designated class of transformations.

CLASSIFICATION BY “DOCUMENT”

Text/Image/Audio watermarking refers to embedding watermarks in an text/image/audio in order to protect the image from illegal copying and identify manipulation.

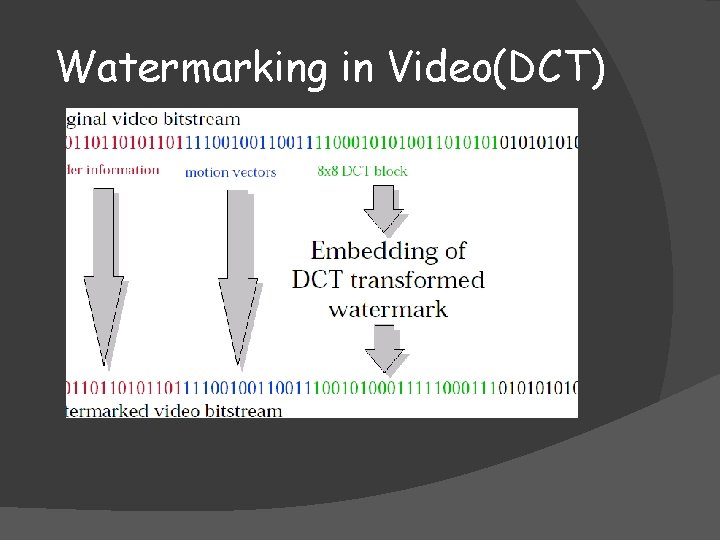
Video Watermarking Video watermarking refers to embedding watermarks in a video sequence in order to protect the video from illegal copying and identify manipulation Algorithm for video watermarking n DFT n DCT n DWT n Watermarking in I-frame.

Discrete Cosine Transformation DCT convert images from spatial-domain to frequencydomain to decorrelate pixels The discrete cosine transform (DCT) helps to separate the image into parts of differing importance (with respect to the image's visual quality). The DCT is similar to the discrete Fourier transform § Remember that JPEG breaks an image into 8 x 8 units So for DCT n = 8 For example: 256 gray-scale image each pixel is stored as a value between 0 – 255 0 = black pixel 255 = white pixel Value between are shades of gray

Amplitude Wave Transforms Frequency

DCT: One Dimensional The general equation for a 1 D (n data items) DCT is defined by the following equation: where n = total no. of data item p = pixel F = coefficients f(i)= is the intensity of the i th pixel

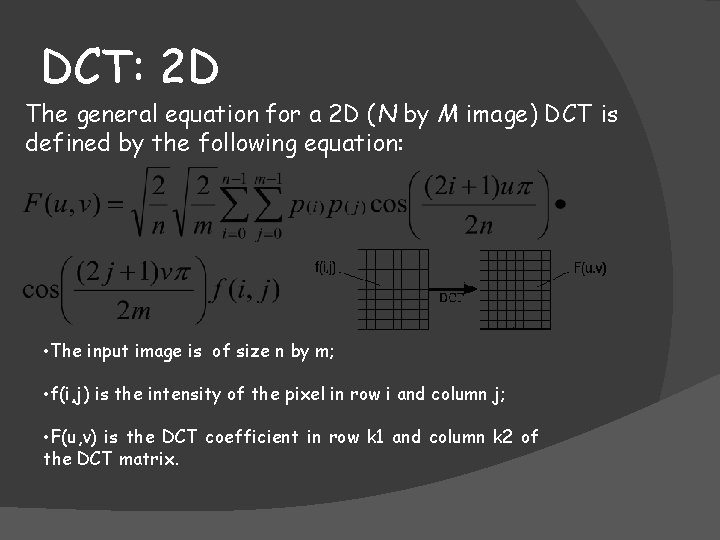
DCT: 2 D The general equation for a 2 D (N by M image) DCT is defined by the following equation: • The input image is of size n by m; • f(i, j) is the intensity of the pixel in row i and column j; • F(u, v) is the DCT coefficient in row k 1 and column k 2 of the DCT matrix.

Watermarking in Video(DCT)

Frequency Domain n Watermarking signal to embed n Host signal n Frequency components(using DCT) n Embedding n Extraction = watermared singal

Purpose of Watermarking n n n Copyright Protection Fingerprinting Copy Protection Broadcasting Monitoring Data Authentication

THANK YOU FOR YOUR ATTENTION!