Digital Signatures The Alice Bob Show Chapter XX

Digital Signatures (The Alice & Bob Show, Chapter XX) Herman G. Meyer III Nov. 18, 2004

Overview • • • Purpose of a Signature Security Concepts Drawbacks of a Signature Email Cryptography Solutions

Do you read what you sign?

Purpose of a Signature • • Signify Intent Authentication and Approval Security Ceremony

Security Concepts • • Confidentiality (for your eyes only) Integrity (unchanged) Identification and Authentication (not forged) Non-repudiation (undeniable)

Drawbacks of a Signature • Lifting • Forgery • Document Alteration

Email • Plain Text • No Authentication (most, not all) • Can’t be trusted. I can prove it.
Cryptography • Symmetric • Asymmetric

Symmetric • Both users must have the same secret key • The Key Sharing Problem • n*(n-1)/2 keys needed for complete confidence • Using less than n*(n-1)/2 keys for n people, you lose identification of source

Asymmetric • Public Key Cryptography • Each user has a pair of complimentary keys (one private, one public) • n*2 keys needed (n key pairs) • Public key may be distributed freely • Either key encrypts – Complement needed to decrypt

Solutions/ More Problems • • • Digital Signatures Hashing Problem Key Problems Certificates PKI Confidentiality
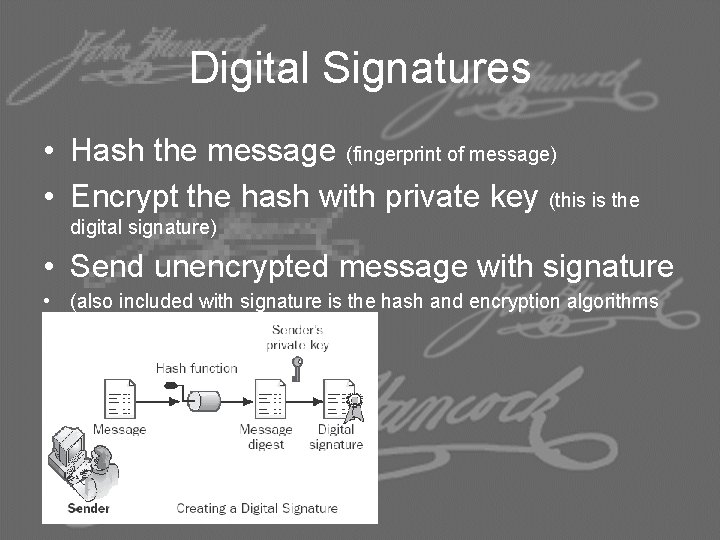
Digital Signatures • Hash the message (fingerprint of message) • Encrypt the hash with private key (this is the digital signature) • Send unencrypted message with signature • (also included with signature is the hash and encryption algorithms used)

Digital Signatures (cont. ) • • Recipient can read the message Message can be verified as unchanged Sender can be verified as correct Method – Rehash the message – Use senders public key to decrypt the signature – Compare rehash with decrypted signature

Hashing Problem • If two messages have the same hash, then they have the same signature • Effectively, the signer has signed everything with the same hash • Solution – Use a good hashing algorithm • MD 5 collision has one known collision

Key Problems • How do we know the public key we are using to validate the message belongs to the sender? • What if the true senders private key is compromised?

Key Solution • Digital IDs • Contents – – – Identifying information (Name, address, etc) Public Key Valid Date Range Certificate Number Signature & Digital ID info of a Certification Authority • Certificate Chain • Public Key Infrastructure

Public Key Infrastructure • PKI • Hardware, software, peoples, policies, and procedures required to issue and manage digital certificates – Corporate – Do. D – Educational

Public Key Infrastructure (cont. ) • Revoking Certificates now possible

Confidentiality • The nested safe method • Encrypt message (not just message digest) with receiver’s public key • Then encrypt result using own private key • The result is that both sender and receiver are assured no one else could have read the true contents

Ethics • Phishing / Social Engineering

Summary • Handwritten signatures are unreliable • Digital signatures provide solutions but create new problems • The new problems can be solved

Now, how do we prove the date… • Sign • Date July 4, 1776 . .

References • http: //www. rsasecurity. com/rsalabs/node. asp? id=2182 • http: //www. snopes. com/music/artists/vanhalen. htm • http: //www. microsoft. com/mspress/books/sampchap/6429/0 -73561877 -3. gif • http: //www. safescrypt. com/safecert/doc/PKI_Basics. pdf • http: //www. abanet. org/scitech/ec/isc/dsg-tutorial. html • Digital Signatures, RSA Press, ohan Atreya, Benjamin Hammond, Stephen Paine, Paul Starret, Stephen Wu, Mc. Graw-Hill, 2002 • Introduction to the Public Key Infrastructure for the internet, Messaoud Benantar, Prentice Hall, 2002 • Understanding Digital Signatures, Gail L. Grant, Mc. Graw-Hill, 1998 • The New Turing Omnibus, A. K. Dewdney, Henry Holt & Co. , 1993
- Slides: 23