DIGITAL SIGNATURES and AUTHENTICATION PROTOCOLS Chapter 13 Digital



![SOLUTION: TIMESTAMP 1. 2. 3. 4. 5. A IDA||IDB KDC 2. KDC EKA[ KS||IDB||T||EKB[KS||IDA||T] SOLUTION: TIMESTAMP 1. 2. 3. 4. 5. A IDA||IDB KDC 2. KDC EKA[ KS||IDB||T||EKB[KS||IDA||T]](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-13.jpg)




![SYMMETRIC-KEY (one-way auth. ) 1. A IDA||IDB||N 1 2. KDC EKA[KS||IDB||N 1||EKB[KS||IDA]] 3. 3. SYMMETRIC-KEY (one-way auth. ) 1. A IDA||IDB||N 1 2. KDC EKA[KS||IDB||N 1||EKB[KS||IDA]] 3. 3.](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-19.jpg)

![PUBLIC-KEY (one-way auth. ) Send A’s public key to B A M||EKRA[H(M)]||EKRAS[T||IDA||KUA] B PUBLIC-KEY (one-way auth. ) Send A’s public key to B A M||EKRA[H(M)]||EKRAS[T||IDA||KUA] B](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-21.jpg)

![VERIFY -1 (s’) w= mod q u 1 = [H(M’)w] mod q u 2 VERIFY -1 (s’) w= mod q u 1 = [H(M’)w] mod q u 2](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-25.jpg)
- Slides: 27

DIGITAL SIGNATURES and AUTHENTICATION PROTOCOLS - Chapter 13 • Digital Signatures • Authentication Protocols • Digital Signature Standard

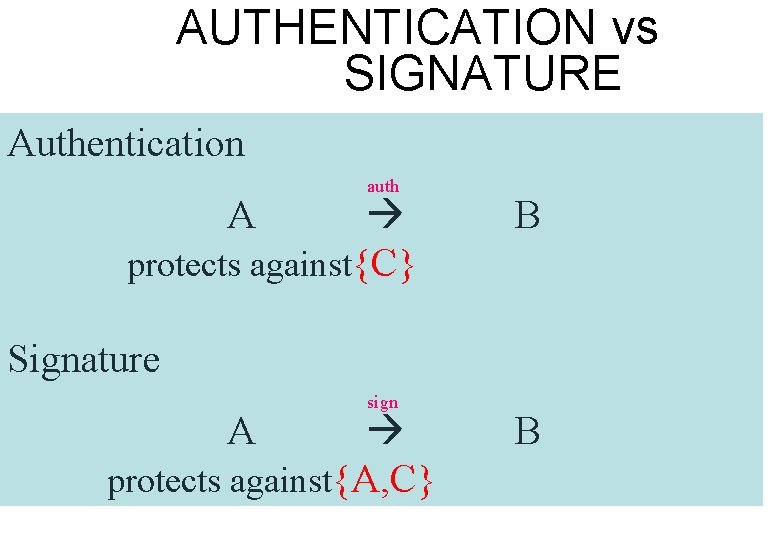
AUTHENTICATION vs SIGNATURE Authentication auth protects against{C} A B Signature sign protects against{A, C} A B

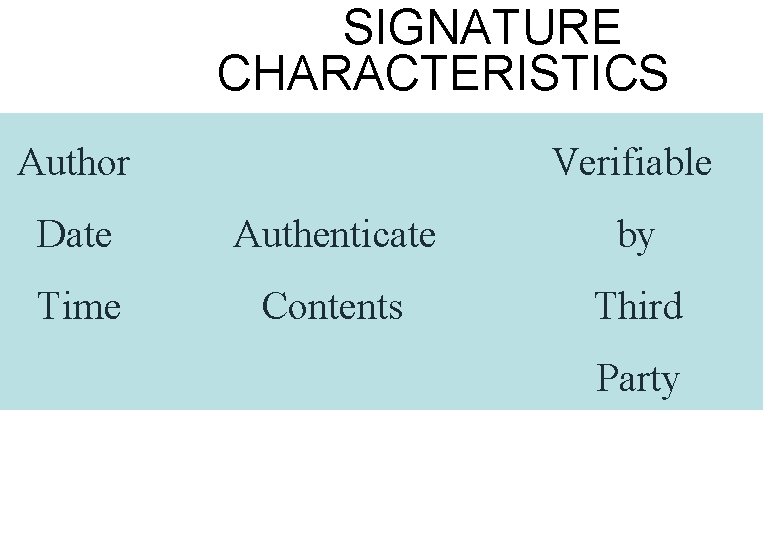
SIGNATURE CHARACTERISTICS Author Verifiable Date Authenticate by Time Contents Third Party

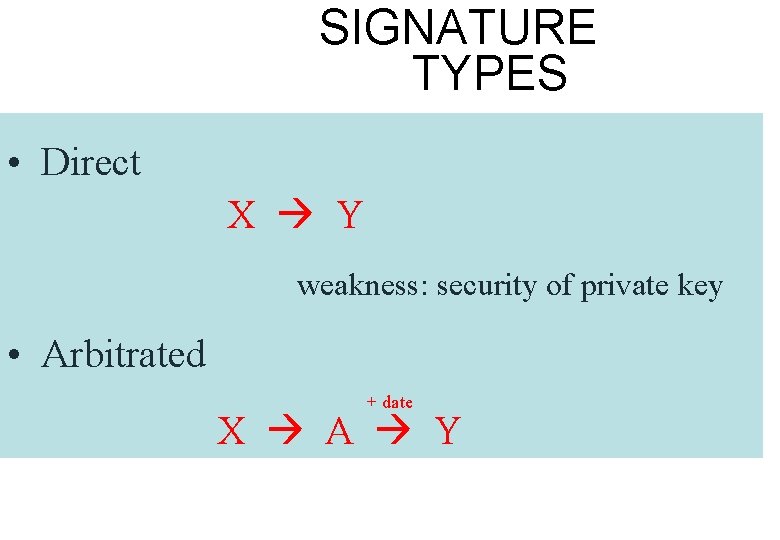
SIGNATURE TYPES • Direct X Y weakness: security of private key • Arbitrated + date X A Y

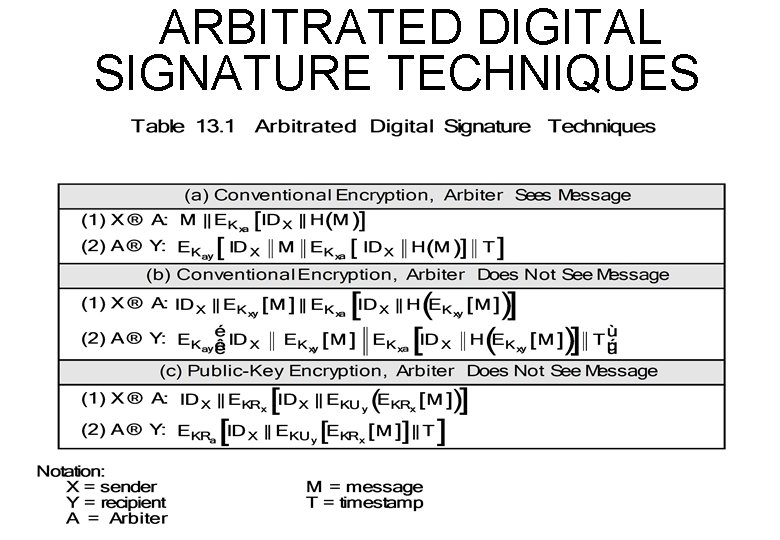
ARBITRATED DIGITAL SIGNATURE TECHNIQUES

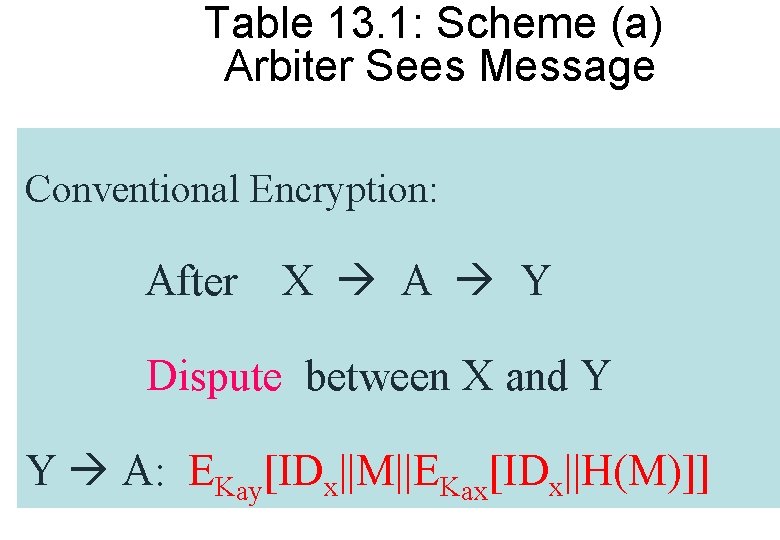
Table 13. 1: Scheme (a) Arbiter Sees Message Conventional Encryption: After X A Y Dispute between X and Y Y A: EKay[IDx||M||EKax[IDx||H(M)]]

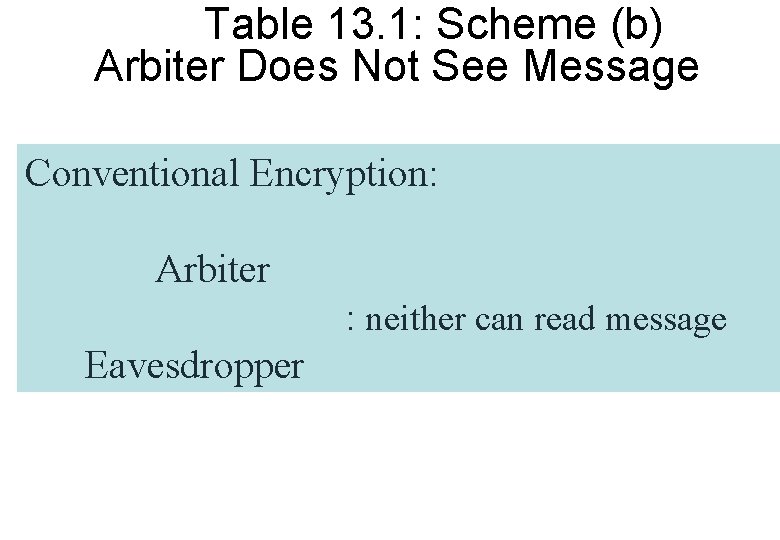
Table 13. 1: Scheme (b) Arbiter Does Not See Message Conventional Encryption: Arbiter : neither can read message Eavesdropper

Table 13. 1: Scheme (c) Arbiter Does Not See Message Public-Key (double) Encryption: advantages: 1. No information shared before communication 2. if KRx compromised date is still correct 3. message secret from Arbiter and Eavesdropper

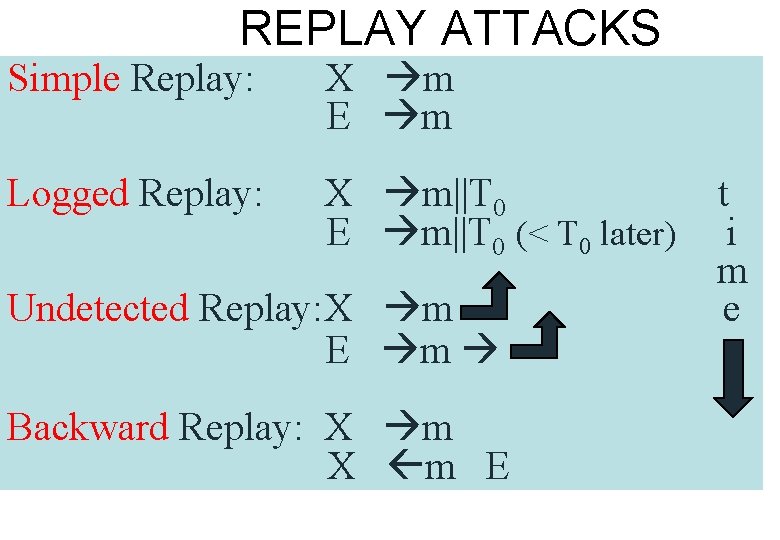
REPLAY ATTACKS Simple Replay: X m E m Logged Replay: X m||T 0 E m||T 0 (< T 0 later) Undetected Replay: X m E m Backward Replay: X m E t i m e

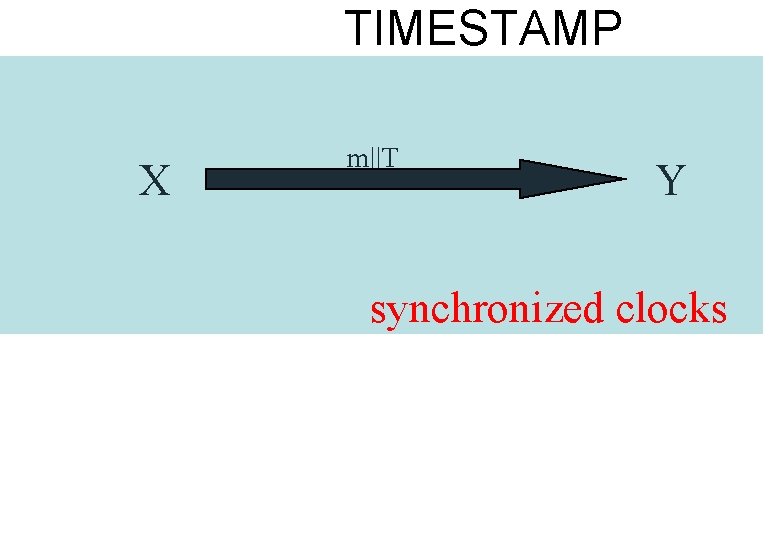
TIMESTAMP X m||T Y synchronized clocks

CHALLENGE/RESPONSE Use NONCE: X X N m||N Y Y handshake required

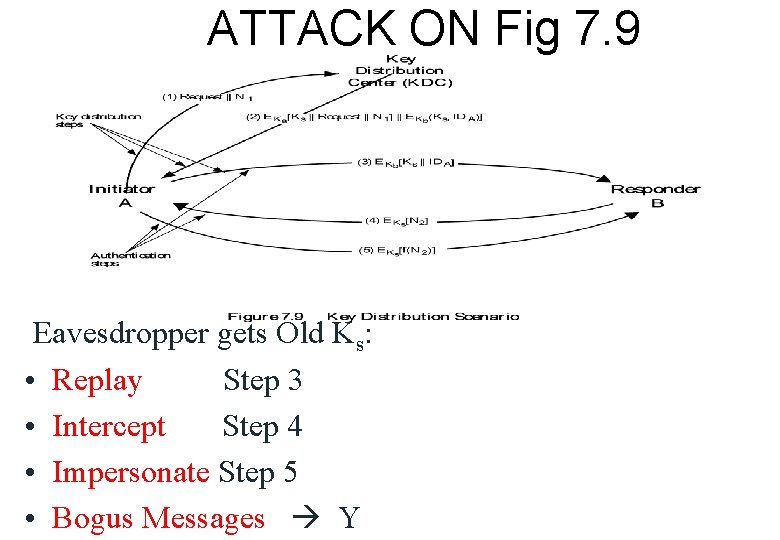
ATTACK ON Fig 7. 9 Eavesdropper gets Old Ks: • Replay Step 3 • Intercept Step 4 • Impersonate Step 5 • Bogus Messages Y
![SOLUTION TIMESTAMP 1 2 3 4 5 A IDAIDB KDC 2 KDC EKA KSIDBTEKBKSIDAT SOLUTION: TIMESTAMP 1. 2. 3. 4. 5. A IDA||IDB KDC 2. KDC EKA[ KS||IDB||T||EKB[KS||IDA||T]](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-13.jpg)
SOLUTION: TIMESTAMP 1. 2. 3. 4. 5. A IDA||IDB KDC 2. KDC EKA[ KS||IDB||T||EKB[KS||IDA||T] ] A 3. A EKB[KS||IDA||T] B 4. B EKS[N 1] A 5. A EKS[f(N 1)] B

CLOCK ATTACKS To counteract: Suppress – Replay attacks: 1. Check clocks regularly use KDC clock 2. Handshaking via Nonce

AN IMPROVED PROTOCOL over Fig 7. 9 To counteract suppress-replay attacks: • A IDA|| NA B • B IDB||NB||EKB[IDA||NA||TB] KDC • KDC EKA[IDB||NA||KS||TB]||EKB[IDA||KS||TB]||NB 4. A 5. 6. EKB[IDA||KS||TB]||EKS[NB] No clock synch. TB only checked by B A B

AUTHENTICATION SERVER - no secret key distribution (public key) • AS 3. A IDA||IDB EKRAS[IDA||KUA||T]||EKRAS[IDB||KUB||T] AS A EKRAS[IDA||KUA||T]||EKRAS[IDB||KUB||T]||EKUB[EKRA[KS||T]] B Problem: Clock Synch.

ALTERNATIVE NONCE PROTOCOL 1. A 2. KDC 3. A 4. B 5. KDC B 6. B 7. A IDA||IDB EKRauth[IDB||KUB] EKUB[NA||IDA] IDB||IDA||EKUauth[NA] KDC A B KDC EKRauth[IDA||KUA]||EKUB[EKRauth[NA||KS||IDA||IDB]] EKUA[EKRauth[NA||KS||IDA||IDB]||NB] EKS[NB] A B

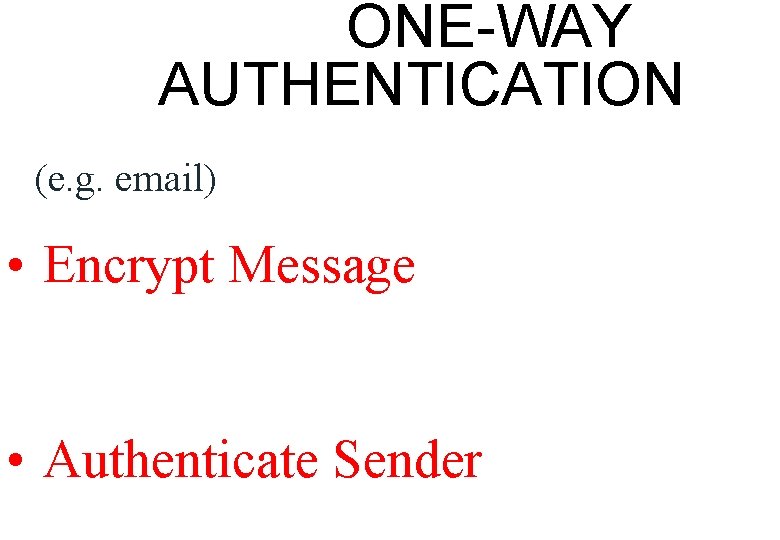
ONE-WAY AUTHENTICATION (e. g. email) • Encrypt Message • Authenticate Sender
![SYMMETRICKEY oneway auth 1 A IDAIDBN 1 2 KDC EKAKSIDBN 1EKBKSIDA 3 3 SYMMETRIC-KEY (one-way auth. ) 1. A IDA||IDB||N 1 2. KDC EKA[KS||IDB||N 1||EKB[KS||IDA]] 3. 3.](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-19.jpg)
SYMMETRIC-KEY (one-way auth. ) 1. A IDA||IDB||N 1 2. KDC EKA[KS||IDB||N 1||EKB[KS||IDA]] 3. 3. A EKB[KS, IDA]||EKS[M] KDC A B

PUBLIC-KEY (one-way auth. ) Use Figs 11. 1 b, c, and d or A EKUB[KS]||EKS[M] B M||EKRA[H(M)] B or A
![PUBLICKEY oneway auth Send As public key to B A MEKRAHMEKRASTIDAKUA B PUBLIC-KEY (one-way auth. ) Send A’s public key to B A M||EKRA[H(M)]||EKRAS[T||IDA||KUA] B](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-21.jpg)
PUBLIC-KEY (one-way auth. ) Send A’s public key to B A M||EKRA[H(M)]||EKRAS[T||IDA||KUA] B

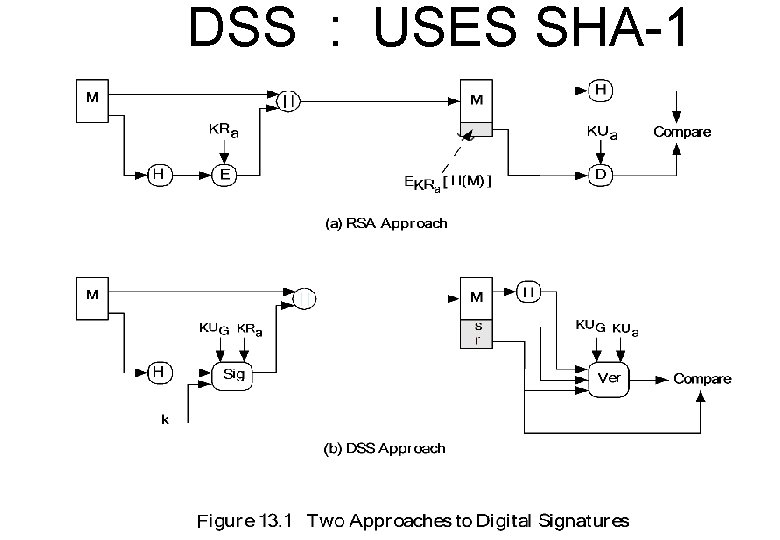
DSS : USES SHA-1 Signature YES Encryption NO Key-Exchange NO

DSS : USES SHA-1

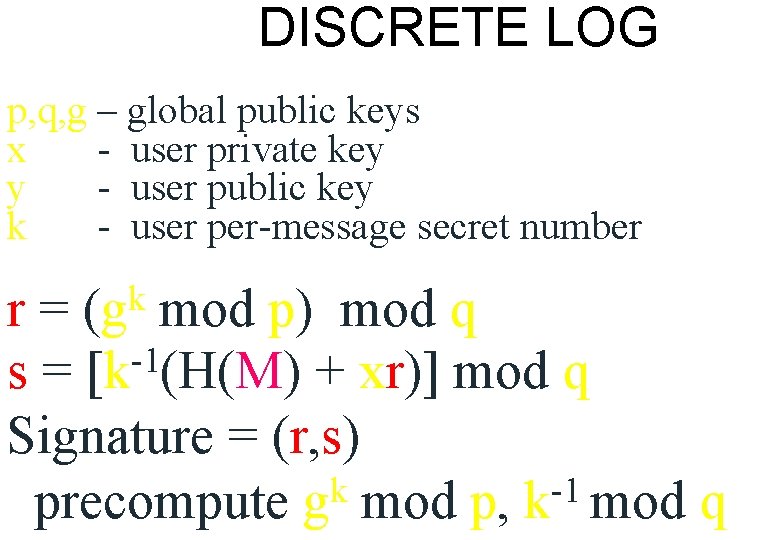
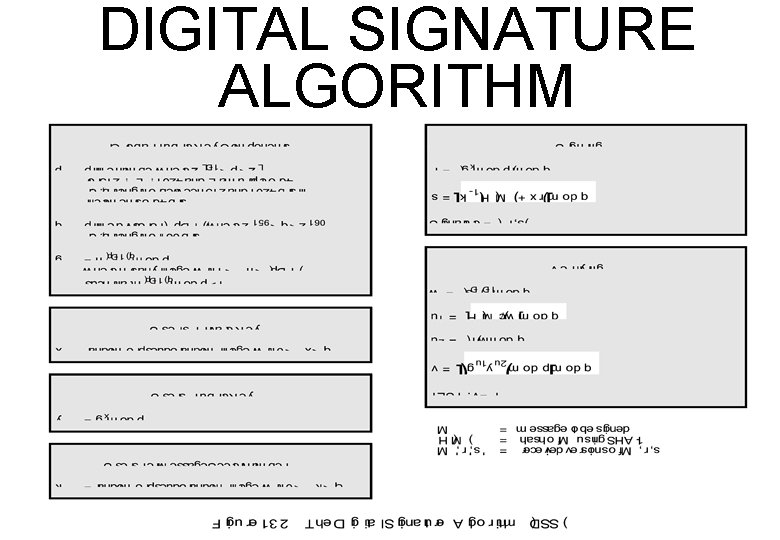
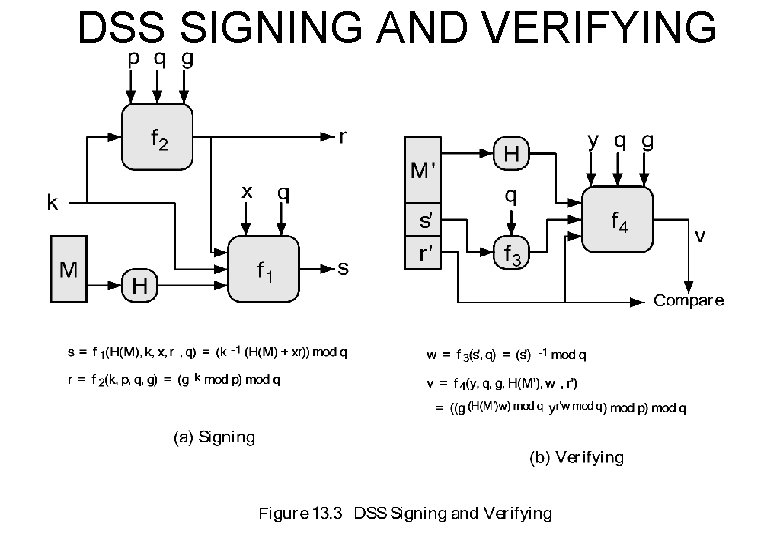
DISCRETE LOG p, q, g – global public keys x - user private key y - user public key k - user per-message secret number k (g r= mod p) mod q -1 s = [k (H(M) + xr)] mod q Signature = (r, s) k -1 precompute g mod p, k mod q
![VERIFY 1 s w mod q u 1 HMw mod q u 2 VERIFY -1 (s’) w= mod q u 1 = [H(M’)w] mod q u 2](https://slidetodoc.com/presentation_image_h2/d2bfc6d880e8ac54befa3ec0619e66bd/image-25.jpg)
VERIFY -1 (s’) w= mod q u 1 = [H(M’)w] mod q u 2 = (r’)w mod q v = [(gu 1. yu 2) mod p] mod q where y = gx mod p v = r’ ? y = gx is one-way: x y YES y x NO

DIGITAL SIGNATURE ALGORITHM

DSS SIGNING AND VERIFYING