Digital Signature and Authentication Protocol FOR BIM CSCL

Digital Signature and Authentication Protocol FOR BIM - CSCL
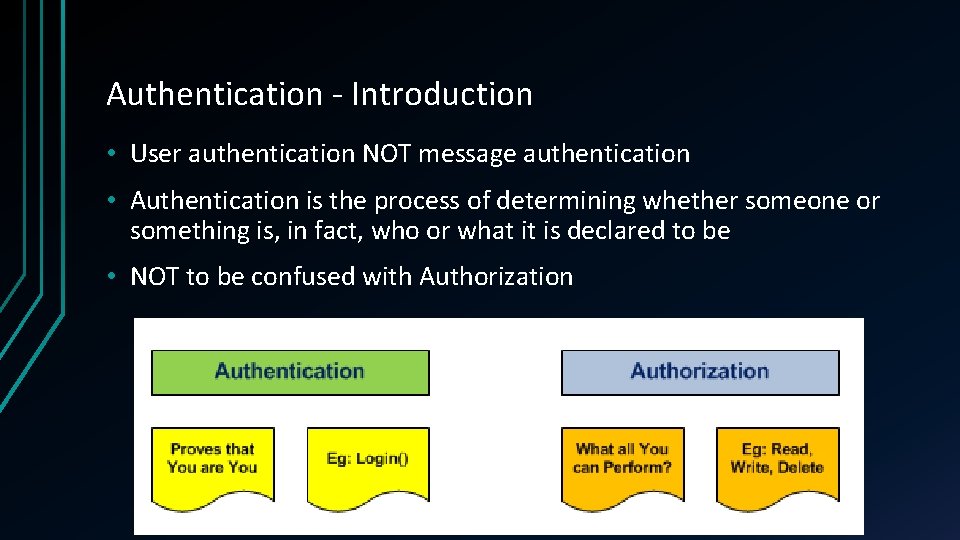
Authentication - Introduction • User authentication NOT message authentication • Authentication is the process of determining whether someone or something is, in fact, who or what it is declared to be • NOT to be confused with Authorization

Authentication Process • Consists of two steps • Identification step: Presenting an identifier to the security System • Verification step: Presenting or generating authentication information that confirms the binding between the entity and the identifier

Means of Authentication • What the entity knows (such as passwords or secret information) • What the entity has (such as a badge or card) • What the entity is (such as fingerprints or retinal characteristics) • Where the entity is (such as in front of a particular terminal)

Requirements in authentication System 1. The set A of authentication information is the set of specific information with which entities prove their identities. 2. The set C of complementary information is the set of information that the system stores and uses to validate the authentication information 3. The set F of complementation functions that generate the complementary information from the authentication information. That is, for f €F, f: A C. 4. The set L of authentication functions that verify identity. That is, for l€ L, l: A x C { true, false }. 5. The set S of selection functions that enable an entity to create or alter the authentication and complementary information.

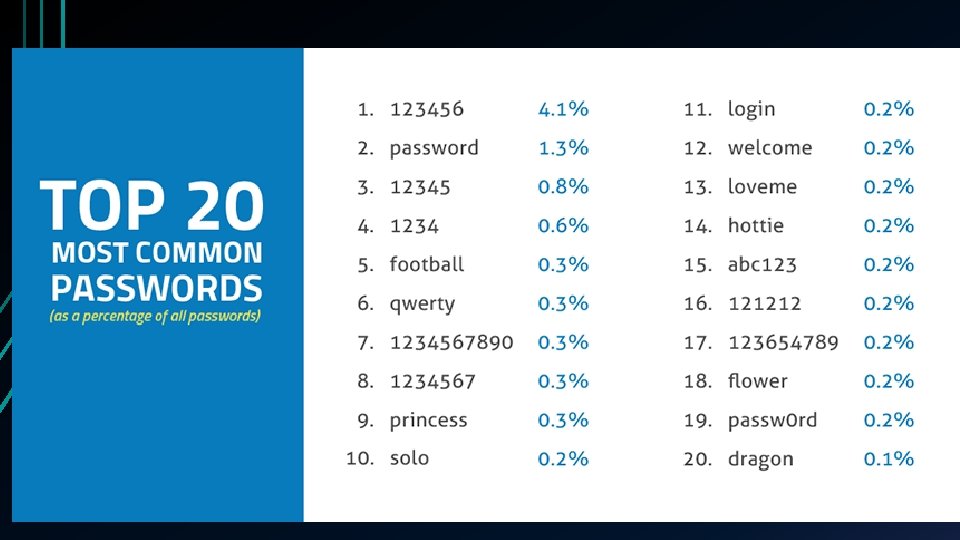
Password • A password is information associated with an entity that confirms the entity's identity. • a string of alpha-numeric characters that allows access to a computer, interface, or system. • An example of an authentication mechanism based on what people know • The simplest password is some sequence of characters. In this case, the password space is the set of all sequences of characters that can be passwords. • More the password space more secure is password
Attacking Password • The simplest attack against a password-based system is to guess passwords. • A dictionary attack is the guessing of a password by repeated trial and error. • Trying all the strings in a pre-arranged listing, typically derived from a list of words such as in a dictionary • The dictionary may be a set of strings in random order or (more usually) a set of strings in decreasing order of probability of selection.

Countering Password guessing •

Password Aging • Guessing of passwords requires that access to the complement, the complementation functions, and the authentication functions be obtained. • If none of these have changed by the time the password is guessed, then the attacker can use the password to access the system. • Password aging is the requirement that a password be changed after some period of time has passed or after some event has occurred. • Password aging is a mechanism you can use to force users to periodically change their passwords
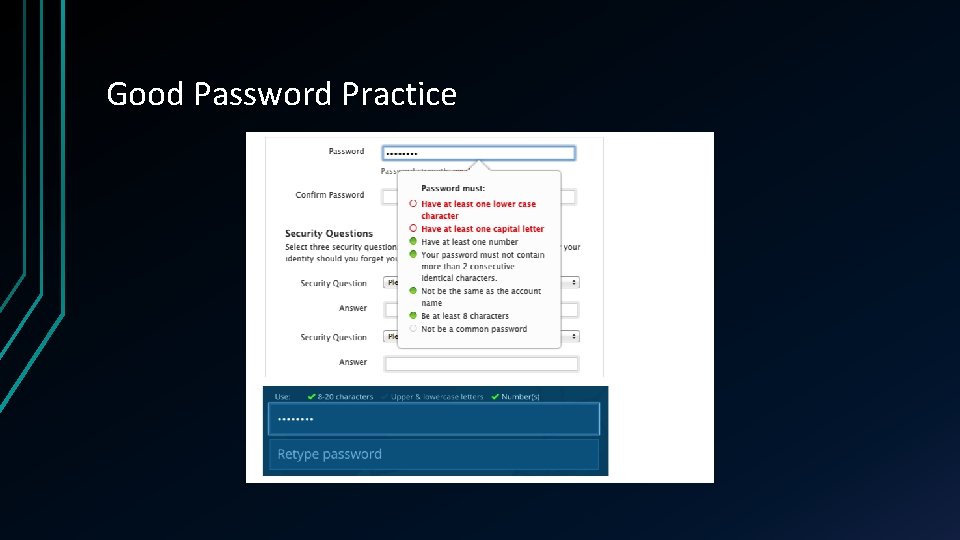
Good Password Practice

Challenge Response System • Passwords have the fundamental problem that they are reusable. • Vulnerable to replay attack • Challenge–response authentication is a family of protocols in which one party presents a question ("challenge") and another party must provide a valid answer ("response") to be authenticated. • Mathematical Definition: Let user U desire to authenticate himself to system S. Let U and S have an agreed-on secret function f. A challenge-response authentication system is one in which S sends a random message m (the challenge) to U, and U replies with the transformation r = f(m) (the response). S validates r by computing it separately.
Biometric • Biometrics is the measurement and statistical analysis of people's unique physical and behavioral characteristics • The technology is mainly used for identification and access control, or for identifying individuals • When a user is given an account, the system administration takes a set of measurements that identify that user to an acceptable degree of error. • Whenever the user accesses the system, the biometric authentication mechanism verifies the identity • False match rate (FMR, also called FAR = False Accept Rate) and False non-match rate (FNMR, also called FRR = False Reject Rate) are major performance metrics

Biometric: Types • Biometric identifiers are often categorized as. Physiological characteristics • Behavioral characteristics • • Physiological characteristics are related to the shape of the body. • Eg: fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina and odour/scent • Behavioral characteristics are related to the pattern of behavior of a person • Eg: typing rhythm, gait, and voice • Since biometric identifiers are unique to individuals, they are more reliable in verifying identity than token and knowledge-based methods; however, the collection of biometric identifiers raises privacy concerns about the ultimate use of this information.

Common Example • Fingerprints • Voices • Eyes: Retina and iris • Faces • Keystroke dynamic • Gait
Fingerprint • Capacitive technique is used rather than optical
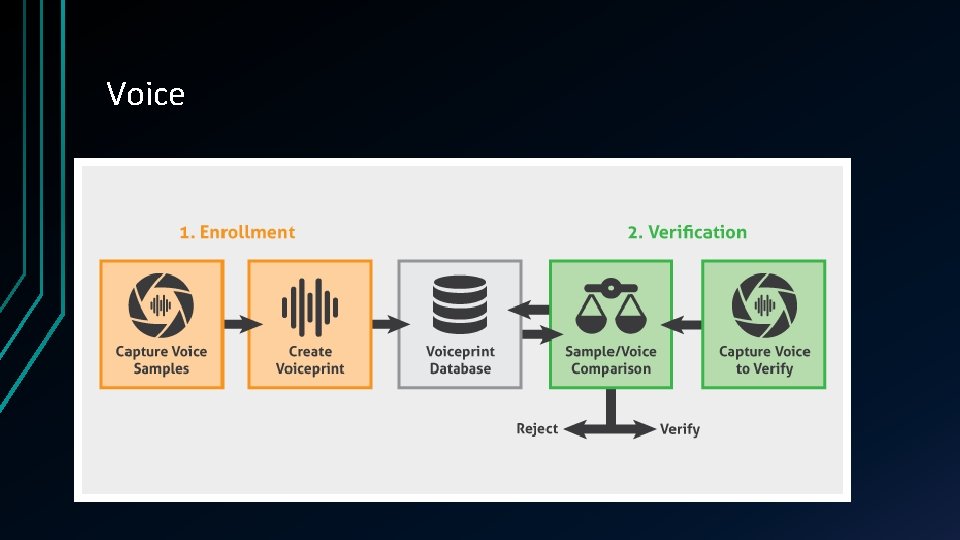
Voice

Eye

Retina & Iris: Similarities • Low false accept and false reject rates • High reliability because no two people have the same iris or retinal pattern • Rapid verification of the biometric • Strong protection against some spoofing attacks as the capillaries in the iris and retina decompose too rapidly to use a amputated eye to gain access

Retina & Iris: Difference • Retinal scan measurement accuracy can be affected by disease; iris fine texture remains remarkably stable • Retinal scanning requires close proximity to an eyepiece, such as looking into a microscope; iris capture is a normal photograph process and can be performed at a distance • Retinal biometrics are complex and have seen low commercial acceptance; Iris scanning is widely accepted as a commerciallyviable modality • Retinal scanning is considered to be invasive, iris is not considered invasive.

Face • A facial recognition system is a technology capable of identifying or verifying a person from a digital image or a video frame from a video source. • There are multiples methods in which facial recognition systems work, but in general, they work by comparing selected facial features from given image with faces within a database. • Simple camera is enough so not that much hardware cost

Key-stroke dynamic • Keystroke dynamics is a behavioural biometrics which captures the typing rhythms of users and then authenticates them based on the dynamics captured • Can be used as dynamics authorization

Location as authentication • Location can be use as authentication • GPS, IP address and network terminal can be used to track location

Digital Signature • A digital signature is a mathematical scheme for presenting the authenticity of digital messages or documents. • A valid digital signature gives a recipient reason to believe that the message was created by a known sender (authentication) • that the sender cannot deny having sent the message (non-repudiation) • that the message was not altered in transit (integrity). •

Common component of Digital Signature • A digital signature scheme typically consists of 3 algorithms; • A key generation algorithm that selects a private key uniformly at random from a set of possible private keys. The algorithm outputs the private key and a corresponding public key. • A signing algorithm that, given a message and a private key, produces a signature. • A signature verifying algorithm that, given the message, public key and signature, either accepts or rejects the message's claim to authenticity.
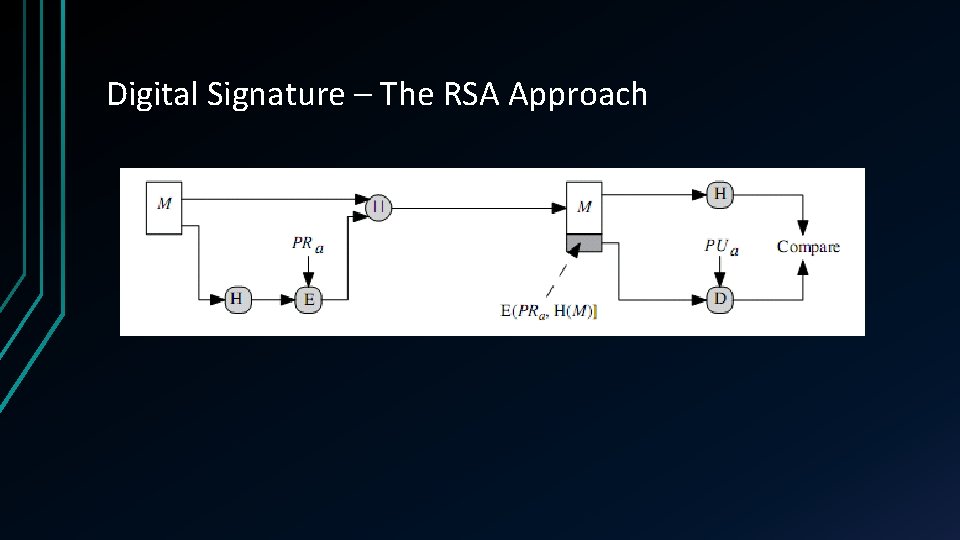
Digital Signature – The RSA Approach
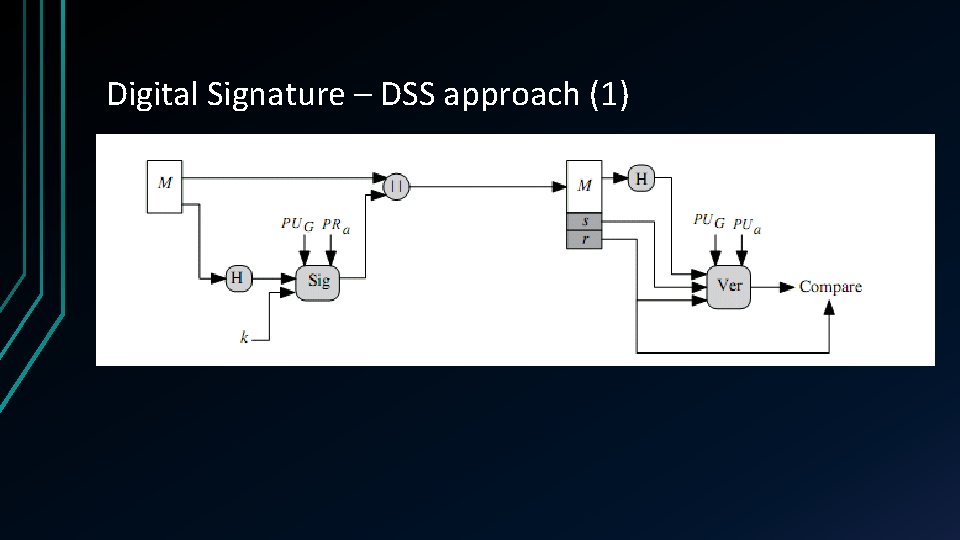
Digital Signature – DSS approach (1)
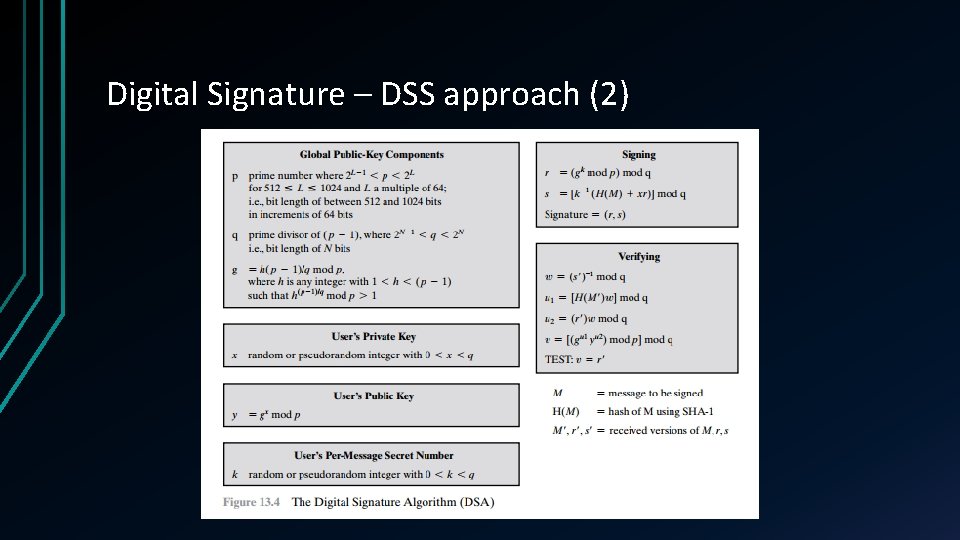
Digital Signature – DSS approach (2)
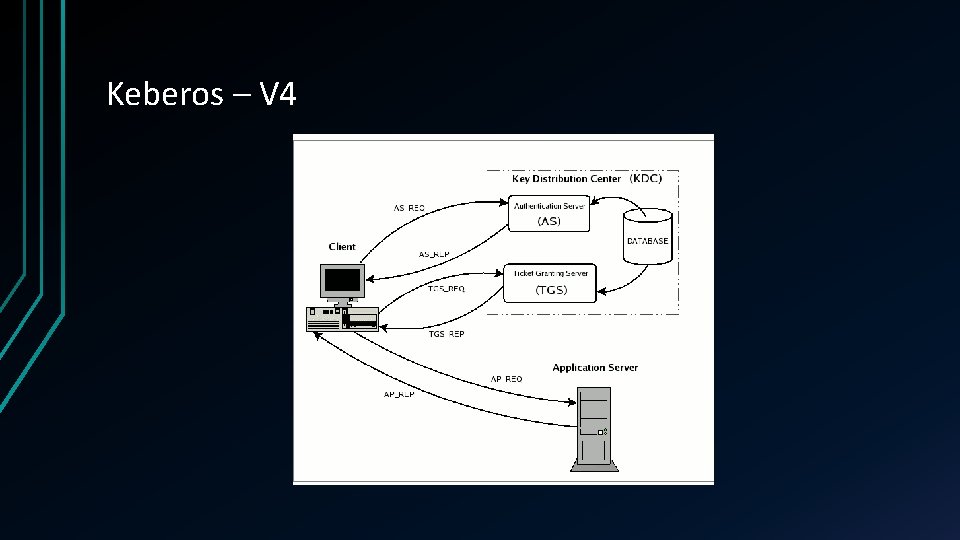
Keberos – V 4

Mutual Authentication

One-way authentication

Arbitrated Digital Signature • Involves used of a arbiter Validate any signed message • Then dated and sent to recipient • • Require suitable level of trust in arbiter • Can be implemented using public or private key algorithm • Arbiter may or maynot see message

Direct digital Signature

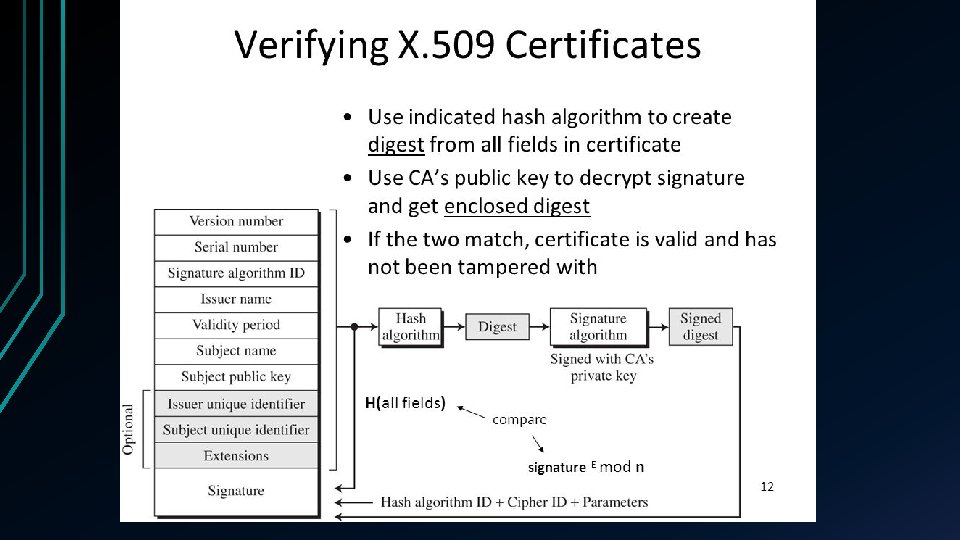
Digital certificate • AKA public key certificate, or identity certificate • is an electronic document used to prove the ownership of a public key. • The certificate includes information about • • • the key, the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). • If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject.

- Slides: 37