Digital Investigation Process 1 Introduction 2 Digital investigation





































- Slides: 44

Digital Investigation Process

1. Introduction 2. Digital investigation process model - physical model - staircase model - evidence flow model - sub phase model 3. Scaffloding or stages of Digital investigation 4. Handling a digital crime scene - fundamental principles of handling a digital crime scene - preparing to handle digital crime scenes - surveying the digital crime scene. 5. Preserving the digital crime scene 6. Modus operandi, motive and technology - modus operandi - relation between modus operandi and technology - motive and technology - concurrent technologies used in computer crime

Introduction

• The main goal of any case investigation is – to find & present the truth. • The DE can decide the decision of person’s life. • It is important to use – trusted methodologies & techniques to ensure correct DI.

DI Process Model

• DI process model, - describes, how DI can be conducted - to solve investigative challenges, - within the particular technical computing environments.

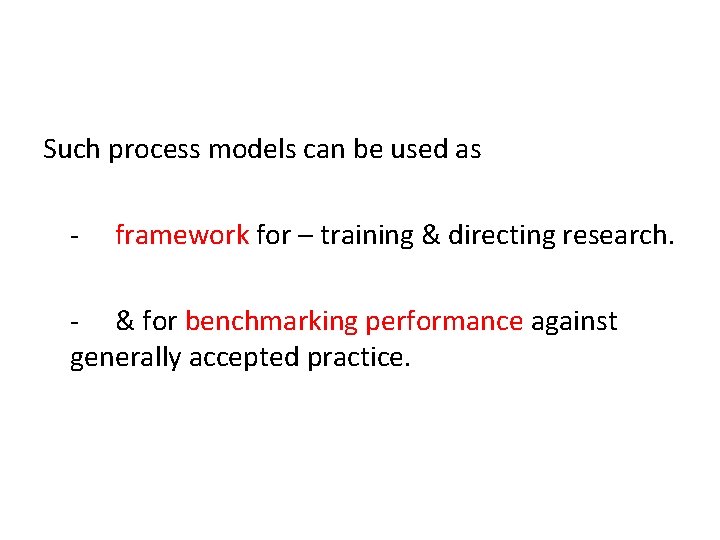
Such process models can be used as - framework for – training & directing research. - & for benchmarking performance against generally accepted practice.

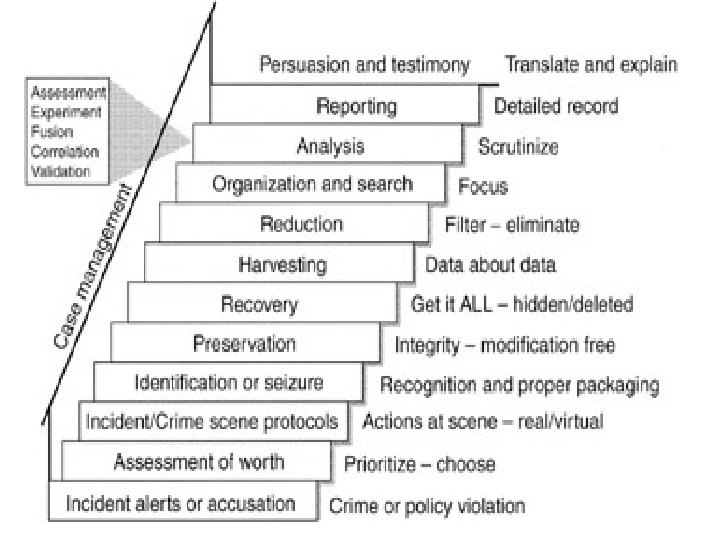
• Figure below shows, stepwise view of DI process model -

Fig. DI process model

• Certain process models address issues, that are important to consider when conducting a DI.

The most common steps for conducting a complete & competent DI are – 1. 2. 3. 4. 5. Preparation Survey/identification Preservation Examination & analysis presentation

1. Preparation Steps 1. Generate a plan of action, to conduct an effective DI. 2. Obtaining supporting resources & materials • For ex. Preparing a search warrant, preparing organization to deal with future consequences & incidents, etc.

2. Survey/Identification Steps – 1. Find sources of DI. for ex. At crime scene, within an organization or on the internet. 2. Identify them, with the real scenario.

3. Preservation Steps – 1. Preventing changes within/of digital evidence, when they are in custody or under examination. - (may cause, due to evidence dynamics) for ex. - isolating the system on the network - securing relevant log files. - collecting Volatile data. for ex. preserving hard drives, emails, mobile devices etc.

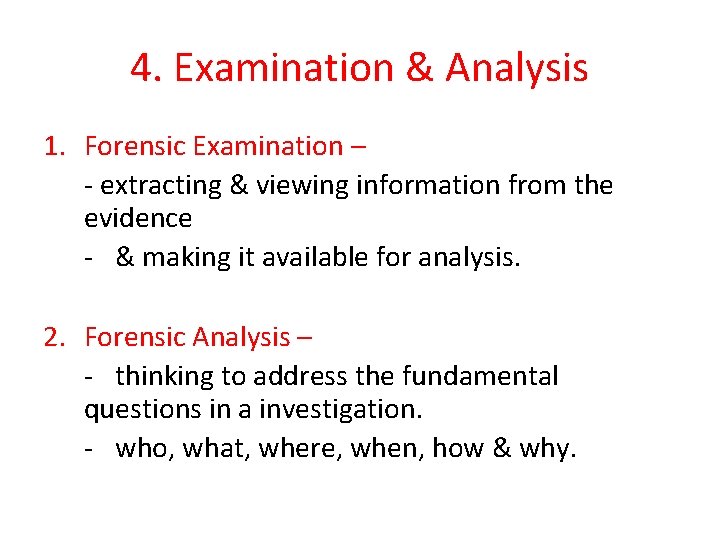
4. Examination & Analysis 1. Forensic Examination – - extracting & viewing information from the evidence - & making it available for analysis. 2. Forensic Analysis – - thinking to address the fundamental questions in a investigation. - who, what, where, when, how & why.

5. Presentation Steps – 1. Reporting of - findings or results of DEs, - in a manner, which satisfies the context of the investigation. - whether it is – legal, military, corporate or any other.

Various Models 1. Physical Model 2. Staircase Model 3. Evidence Flow Model 4. Sub Phase Model

1. Physical Model

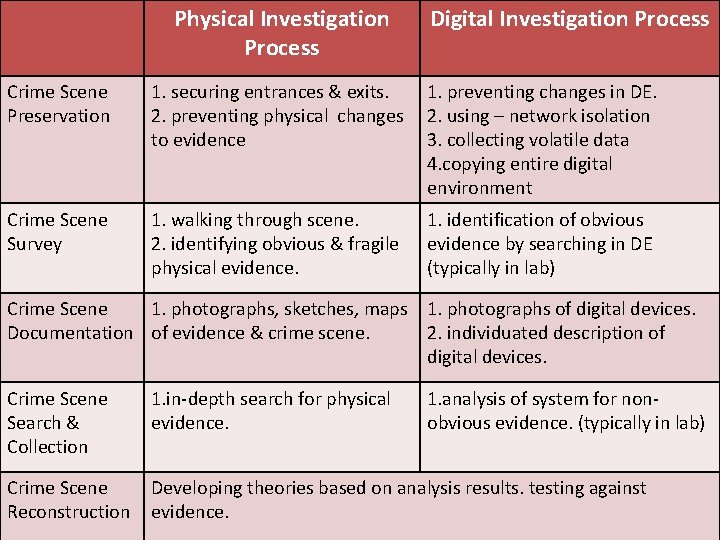
• This model relates – - physical investigation process - with, digital investigation process. 1. 2. 3. 4. 5. Crime Scene Preservation Crime Scene Survey Crime Scene Documentation Crime Scene Search & Collection Crime Scene Reconstruction

1. Crime Scene Preservation Physical Investigation Process - securing entrances & exits. - preventing physical changes to evidence. Digital Investigation Process - preventing changes in DE. - using – network isolation - collecting volatile data - & copying entire digital environment

2. Crime Scene Survey Physical Investigation Process - walking through scene. - identifying obvious & fragile physical evidence. Digital Investigation Process - identification of obvious evidence by searching in DE (typically in lab)

3. Crime Scene Documentation Physical Investigation Process - photographs, sketches, maps of evidence & crime scene. Digital Investigation Process - photographs of digital devices. - individuated description of digital devices.

4. Crime Scene Search & Collection Physical Investigation Process - in-depth search for physical evidence. Digital Investigation Process - analysis of system for non-obvious evidence. (typically in lab)

5. Crime Scene Reconstruction - Developing theories based on analysis results. & - testing against evidence.

Physical Investigation Process Digital Investigation Process Crime Scene Preservation 1. securing entrances & exits. 2. preventing physical changes to evidence 1. preventing changes in DE. 2. using – network isolation 3. collecting volatile data 4. copying entire digital environment Crime Scene Survey 1. walking through scene. 2. identifying obvious & fragile physical evidence. 1. identification of obvious evidence by searching in DE (typically in lab) Crime Scene 1. photographs, sketches, maps 1. photographs of digital devices. Documentation of evidence & crime scene. 2. individuated description of digital devices. Crime Scene Search & Collection 1. in-depth search for physical evidence. 1. analysis of system for nonobvious evidence. (typically in lab) Crime Scene Reconstruction Developing theories based on analysis results. testing against evidence.

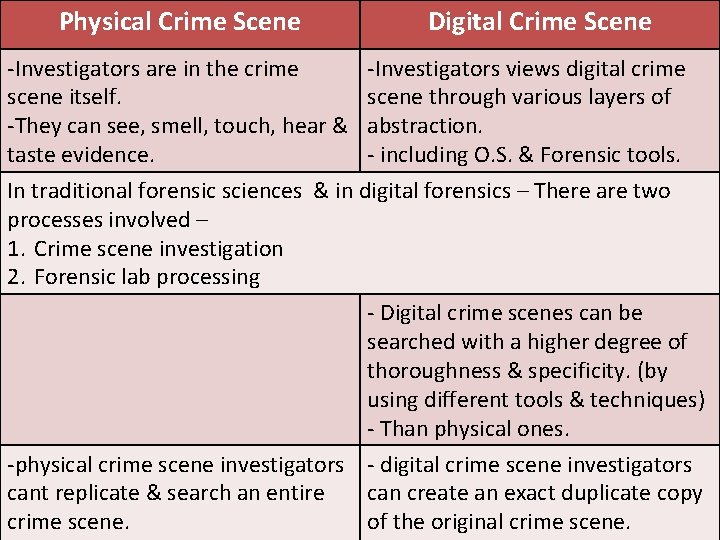
• Digital & Physical Crime Scenes are compared on following basics

Physical Crime Scene Digital Crime Scene -Investigators are in the crime -Investigators views digital crime scene itself. scene through various layers of -They can see, smell, touch, hear & abstraction. taste evidence. - including O. S. & Forensic tools. In traditional forensic sciences & in digital forensics – There are two processes involved – 1. Crime scene investigation 2. Forensic lab processing - Digital crime scenes can be searched with a higher degree of thoroughness & specificity. (by using different tools & techniques) - Than physical ones. -physical crime scene investigators - digital crime scene investigators cant replicate & search an entire can create an exact duplicate copy crime scene. of the original crime scene.

2. Staircase Model


• Digital investigators & forensic examiners follows several steps from bottom to top - in a systematic, determined manner - to reveal true facts. • Every step has relationship with the next step. • i. e. results of previous step can be used as an input of next step. • Unique methods & tools employed in each step of investigation.

Various steps involved in the staircase model are 1. Incident alerts or accusation 2. Identification of crime or seizure. 3. Preservation 4. Recovery 5. Harvesting. 6. Reduction 7. Focus 8. Search 9. Analysis 10. Report 11. Persuasion & Testimony

• Staircase model could be simplified by treating – – Recovery – Harvesting – Reduction – Organization & – Search As subcomponents of the examination step.

3. Evidence Flow Model

• Describes – flow of information; in a digital investigation. • From the moment, digital investigators are alerted until the investigation reaches its conclusion. • Appropriate controls can be implemented at each step of the process, to handle – evidentiary data – Written reports or – Communications, relating to the investigation.

• This model – - Prevents information leakage & - Maintains the authenticity & integrity of digital evidence. • This is a general model, - Which can be applied to any environment & technology.

Steps involved in – The Evidence Flow Model 1. Awareness 2. Authorization 3. Planning 4. Notification 5. Search/identity 6. Collection 7. Transport 8. Storage 9. Examination 10. Hypothesis 11. Presentation 12. Proof/defense.

4. Sub phase Model

• Beebe & Clark concluded that – “most investigative process models are too high level & - don’t address the – more concrete/complete principles of investigation”

• For this – a multi-tired framework is created by - Taking the steps common in other models - & adding sub phases with defined objectives - to help investigators implement each step properly.

• This model mainly focuses on – - evidence collection & analysis phase

Main Steps In – Subphase Model 1. 2. 3. 4. 5. 6. Preparation Incident response Data collection Data analysis Findings presentations & Incident closure

• File system analysis provides – • Three objectives-based sub phases (SEE). - survey - extract & - examine.

Objectives Of File System Analysis 1. 2. 3. 4. 5. 6. 7. Reduce the amount of data to analyze. Recover deleted files. Find relevant hidden data. Recover relevant ASCII and non-ASCII data. Recover relevant email & attachments. Recover printed documents. Recover relevant “personal organizer’s” data (e. g. Calendar, address book etc. )

• The analysis of digital evidence is more commonly viewed as • a separate process that involves hypothesis testing & • event reconstruction among other things.