Digital certificates One concern with the public key

Digital certificates • One concern with the public key approach: must ensure that you are encrypting to the correct person’s public key v Otherwise, you can only encrypt/decrypt to those key handed to you • A solution: digital certificates (or certs) • A form of credentials (like a physical passport) • Included with a person’s public key to verify that a key is valid 1
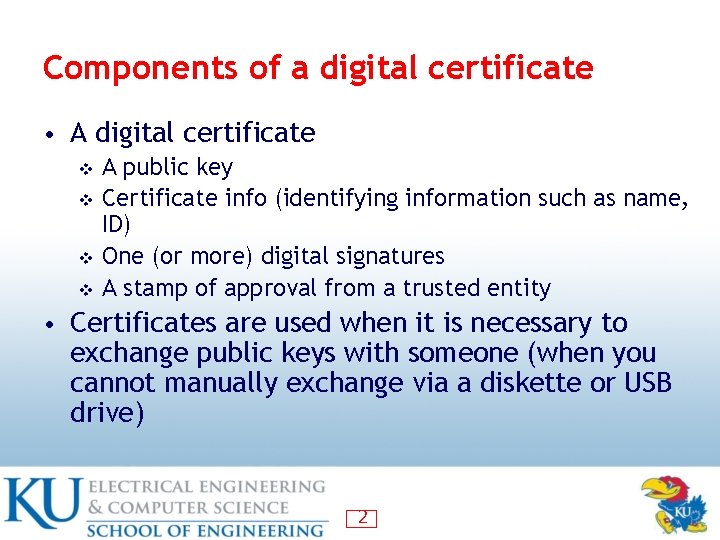
Components of a digital certificate • A digital certificate A public key v Certificate info (identifying information such as name, ID) v One (or more) digital signatures v A stamp of approval from a trusted entity v • Certificates are used when it is necessary to exchange public keys with someone (when you cannot manually exchange via a diskette or USB drive) 2
![Components of a digital certificate [2] 3 Components of a digital certificate [2] 3](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-3.jpg)
Components of a digital certificate [2] 3
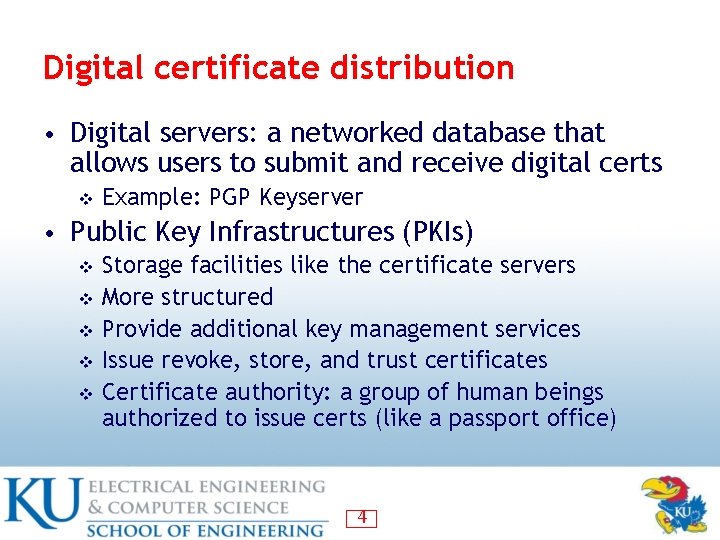
Digital certificate distribution • Digital servers: a networked database that allows users to submit and receive digital certs v Example: PGP Keyserver • Public Key Infrastructures (PKIs) Storage facilities like the certificate servers v More structured v Provide additional key management services v Issue revoke, store, and trust certificates v Certificate authority: a group of human beings authorized to issue certs (like a passport office) v 4

Common certificate format • The certificate holder’s public key: the public portion of key pair and key algorithm, e. g. , RSA • The certificate holder’s information: identity information about the user (e. g. , name, user ID, email address, photograph, and so on) • The digital signature of the certificate owner: the signature using the corresponding private key of the public key of the certificate • The certificate’s validity period: the certificate’s start date/time and expiration date/time; The preferred symmetric encryption algorithm for the key: e. g. , AES, Triple-DES, Twofish 5
![Common certificate format [2] 6 Common certificate format [2] 6](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-6.jpg)
Common certificate format [2] 6
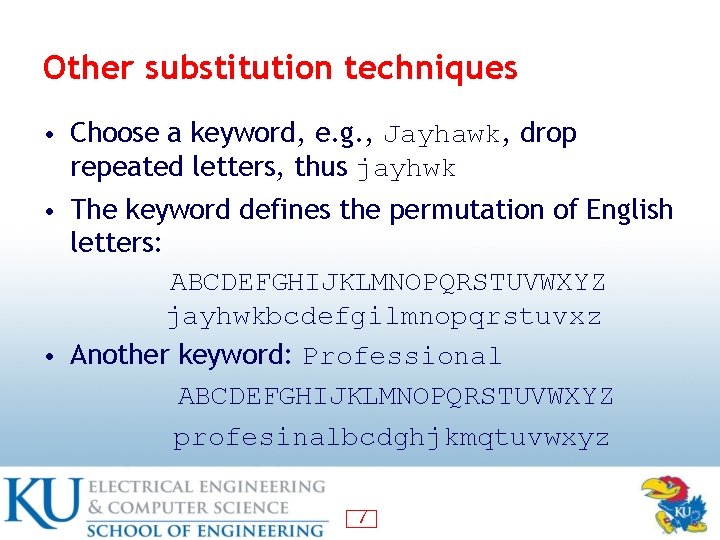
Other substitution techniques • Choose a keyword, e. g. , Jayhawk, drop repeated letters, thus jayhwk • The keyword defines the permutation of English letters: ABCDEFGHIJKLMNOPQRSTUVWXYZ jayhwkbcdefgilmnopqrstuvxz • Another keyword: Professional ABCDEFGHIJKLMNOPQRSTUVWXYZ profesinalbcdghjkmqtuvwxyz 7
![Other substitution techniques [2] • Use every third letter (apply mod 26) adgjmpsvybehknqtwzcfilorux • Other substitution techniques [2] • Use every third letter (apply mod 26) adgjmpsvybehknqtwzcfilorux •](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-8.jpg)
Other substitution techniques [2] • Use every third letter (apply mod 26) adgjmpsvybehknqtwzcfilorux • Consider any possible permutation of the English letters How many? 26! v Even applying decryption at 1 microsecond, still takes over 1, 000 years v The primary issue: the knowledge of letter patterns in a text v Solution: Avoid using the same substitution for a letter v 8
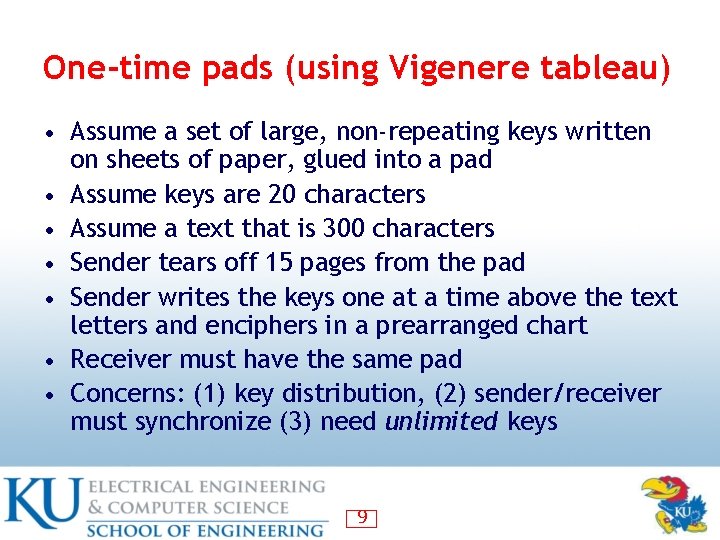
One-time pads (using Vigenere tableau) • Assume a set of large, non-repeating keys written • • • on sheets of paper, glued into a pad Assume keys are 20 characters Assume a text that is 300 characters Sender tears off 15 pages from the pad Sender writes the keys one at a time above the text letters and enciphers in a prearranged chart Receiver must have the same pad Concerns: (1) key distribution, (2) sender/receiver must synchronize (3) need unlimited keys 9
![One-time pads [2] • A toy example • Assume keys are 5 letters each; One-time pads [2] • A toy example • Assume keys are 5 letters each;](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-10.jpg)
One-time pads [2] • A toy example • Assume keys are 5 letters each; assume these two keys XYSWD and DHJTU • Assume you have a text that is eight characters, e. g. , “fly today” • Need two keys XYSWDDHJTU flytoday • Ciphertext: XYSWDDHJ 10
![One-time pads [3] • Using computers, random numbers can be generated for the keys One-time pads [3] • Using computers, random numbers can be generated for the keys](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-11.jpg)
One-time pads [3] • Using computers, random numbers can be generated for the keys • To send a 300 -letter message Generate the next 300 random numbers v Scale to be between 1 -26 v Use a number to decipher each letter v 11
![One-time pads [4] • Pictorially 12 One-time pads [4] • Pictorially 12](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-12.jpg)
One-time pads [4] • Pictorially 12
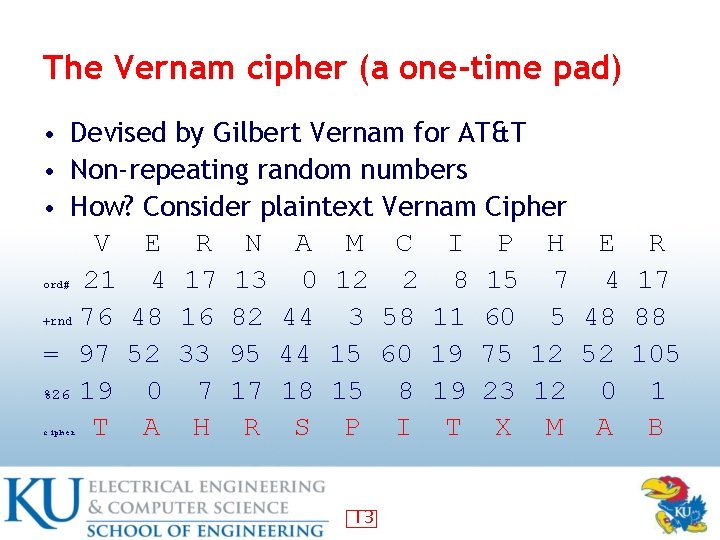
The Vernam cipher (a one-time pad) • Devised by Gilbert Vernam for AT&T • Non-repeating random numbers • How? Consider plaintext Vernam Cipher V 21 +rnd 76 = 97 %26 19 T ord# cipher E 4 48 52 0 A R 17 16 33 7 H N 13 82 95 17 R A 0 44 44 18 S M 12 3 15 15 P 13 C 2 58 60 8 I I 8 11 19 19 T P 15 60 75 23 X H 7 5 12 12 M E 4 48 52 0 A R 17 88 105 1 B
An example of combining substitution and transposition • The Soviet encryption during the WWII • Handout 14

How is a key used? • Suppose we have a key, computer • How is it used to encrypt a plaintext? • A toy approach • The key, computer, in ASCII is Dec: 097 111 109 112 117 116 101 114 v Binary: 01100011 01101101 … v • A plaintext, “secretly” in binary: v 01110011 01100101 01100011 … • XOR the two! 15
![How is a key used? [2] • Much more complex in real algorithms • How is a key used? [2] • Much more complex in real algorithms •](http://slidetodoc.com/presentation_image_h/372a4541c6baf9b182d4973b7855fa9e/image-16.jpg)
How is a key used? [2] • Much more complex in real algorithms • F is a round function • Ki, for i in 2. . 16, are new keys generated from the original key by a complex algorithm • �is the xor operation 16
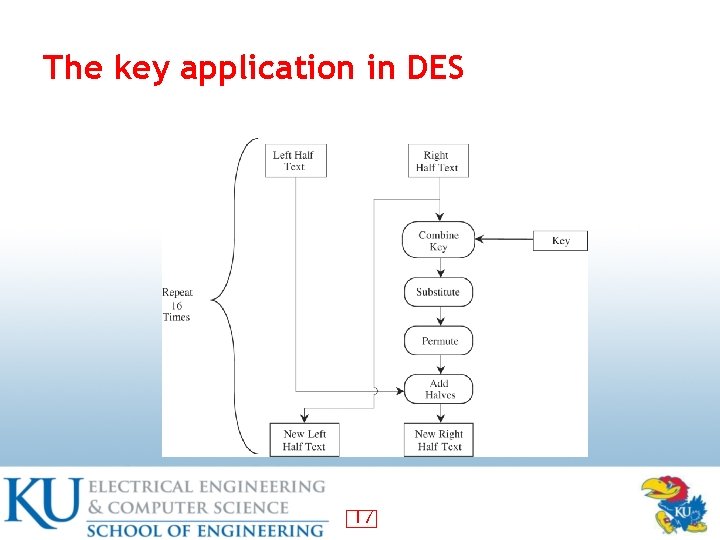
The key application in DES 17
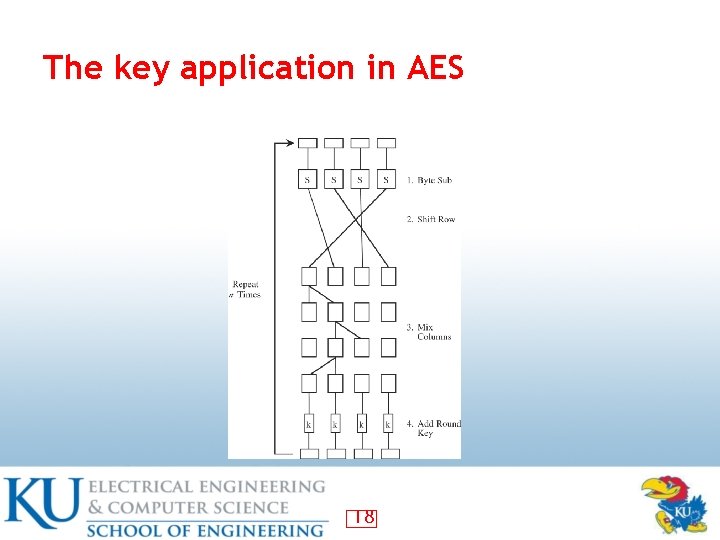
The key application in AES 18

Key distribution revisited • Five persons need to communicate securely • How many keys should the system maintain? • How many lines of communication? n * (n -1)/2 Two people: 1 line of communication v Three people: 3 lines of communication v Four people: 6 lines of communication v Five people: 10 lines of communication v • Concerns: Maintaining the distributed the keys 19
- Slides: 19