Digging Deeper Into DPI Network Visibility Service Management

Digging Deeper Into DPI Network Visibility & Service Management Jay Klein May 2007

Outline l Origins of the Problem l Complexity l DPI for Security vs. DPI for Application Control l DPI - Glance through the basics 2
Market Trends and Drivers: Bandwidth l Broadband becoming ubiquitous l High penetration rates (over 50% in Korea, Taiwan, Holland Canada) l Over 50% of on-line households are BB l Telcos are upgrading infrastructure: l ADSL 2+ (20 -25 Mbps) l VDSL 2 (20 -30 Mbps) l FTTx l Bandwidth per user is ramping up: l BW expected to reach 20 M by 2010 (source: IDC, 2006) 3 More Bandwidth More Applications
Market Trends and Drivers: Applications P 2 P Vo. IP Ents. Online Gaming l Continue to be highly popular l Average of 40 -60% of overall BW l More applications use encryption l Bit. Torrent, e. Mule, Ares l Content providers seem to adopt P 2 P l Warner Bros to sell films via Bit. Torrent l Scalability 4 More Bandwidth More Applications
Market Trends and Drivers: Applications P 2 P Vo. IP Ents. Online Gaming l Numerous Internet Vo. IP providers: l Skype, Vonage, Google. Talk, Yahoo!Voice, Net 2 Phone l Vo. BB subscribers increased rapidly in 2005/6 l More SPs offer Voice & Data services bundled together 5 More Bandwidth More Applications
Market Trends and Drivers: Applications P 2 P Vo. IP Ents. Online Gaming l Usage of streaming applications increasing dramatically l You. Tube – 100 M videos/day l Numerous new Web-TV services launched l BBC, In 2 TV etc. l Skype to launch Venice Project – a Web TV service l Telcos launching IPTV services: Pay-TV and VOD l More than just a service differentiator 6 More Bandwidth More Applications
Market Trends and Drivers: Applications P 2 P Vo. IP Ents. Online Gaming l Consoles & PC offer “over the network” gaming experience l Stringent Bandwidth & Latency requirements 7 More Bandwidth More Applications

The Complexity l Numerous Applications - Many Protocols l Same Application – Different Implementations l Bittorrent has more than 30 different client implementations l IM or Vo. IP may deliver the same experience but don’t use similar protocols l Evolving Architectures l Skype evolved from Kazaa maintaining more or less the network topology l Joost (Venice Project) has just done the same 8

The Complexity l Mixture of Technologies, Diverse deployment scenarios l Various Clients: PC, Smartphone, Gaming Console l Client’s network surroundings: Firewall/NAT, Proxy l Monitor or Traffic Shape l Symmetric vs. Asymmetric l Frequent Updates l Can vary from twice a year to every month l Easy to enforce upgrade policy with quick reaction time l Typically will affect protocol format 9
The Complexity l Use of Encryption (Obfuscation) l Primarily designed for counter measuring operator’s throttling and monitoring efforts (e. Mule, Bittorrent) l In some cases protect proprietary implementation (Skype) l Cannot generalize - Need to differentiate use l “Good” (legit streaming, SW updates) vs. “Bad” (pirated file sharing) P 2 P l Need to recognize application subtleties for proper actions l Example: MSN IM – block Vo. IP & Streaming, allow Chat 10
DPI – Application Space vs. Security Space l Comparable in the sense of “Deep”, “Packet” & “Inspection” l Different Core Competence l Similar tools yet different know-how l Some “gray area” in the middle (e. g. , basic DDo. S) l When DPI aimed at applications l Applications = Services, typically “invited” by Operator, Enduser or both l When DPI is aimed at security risks l Risks = Weaknesses in Network & OS behavior l Need to deal with hostile “applications”, “services” 11
DPI – Application Space vs. Security Space l DPI for Security - Inspects L 3/4 and complements with L 7 info if required l DPI for Security often samples the data stream, indicates on a trend & recommends on action l When DPI is aimed at applications, starts at L 7 , track & learn the specific service l DPI for Applications must examine each connection and accurately identify & classify for any action beyond monitoring 12
Packet Inspection l Analyze encapsulated content in packet’s header and payload l Content may be spread over many packets l Different research and analysis tools are combined l The end result – a library of “signatures” l For each protocol/application a “Unique” Fingerprint set is found l Signatures may change over time 13

False Positives l The likelihood that application connections are caught by signatures of other applications l Some traffic is misidentified / misclassified l Signatures are too weak l Reason: Different protocols exhibit similar behavior or data patterns l Strengthen signature by combing several techniques leading to a complex & robust signature l Target 0% FP for controlling purposes 14

False Negatives l The likelihood that application connections are not caught by their designated signatures l End result – some portion of the suspected application traffic is not detected l Why? Signatures don’t cover all protocol occurrences l Examples: l IM = Chat, Streaming, Gaming, Vo. IP… l Environment – Proxy, NAT 15

Analysis by Port l Reasoning: l Many applications and protocols use a default port l Example: email l Incoming POP 3: 110 (995 if using SSL) l Outgoing SMTP: 25 l The Good - It’s easy, The Bad - It’s too easy l Many applications disguise themselves (e. g. , Port 80) l Port hopping large range, overlapping apps 18
Analysis by String Match l Reasoning: l Many applications have pure textual identifiers l Easy to search for l Very easy if in a specific location within a packet l Uniqueness not always guaranteed 19
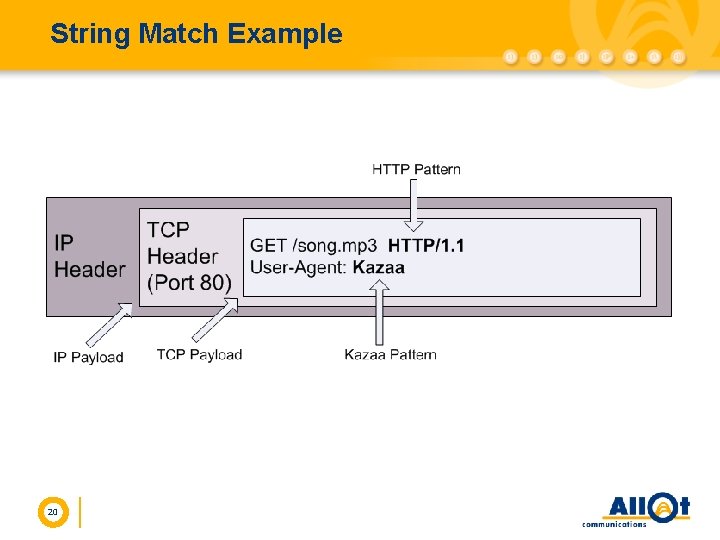
String Match Example 20
Analysis by Numerical Properties l Property is not only content: l Packet size l Payload/message length l Position within packet l In some cases sparse and spread over several packets 21
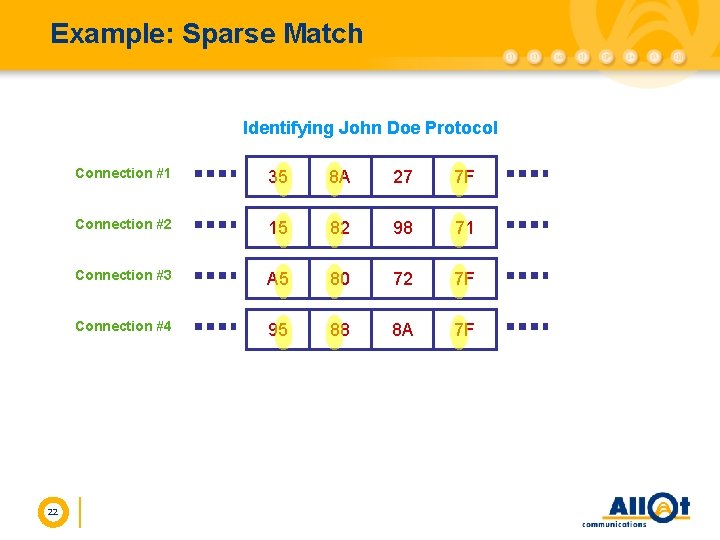
Example: Sparse Match Identifying John Doe Protocol 22 Connection #1 35 8 A 27 7 F Connection #2 15 82 98 71 Connection #3 A 5 80 72 7 F Connection #4 95 88 8 A 7 F
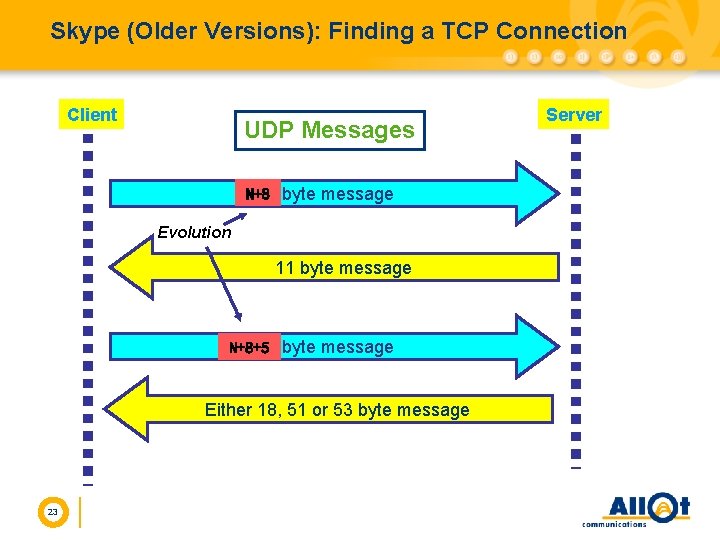
Skype (Older Versions): Finding a TCP Connection Client UDP Messages N+8 18 byte message Evolution 11 byte message N+8+5 23 byte message Either 18, 51 or 53 byte message 23 Server

Behavior and Heuristic Analysis l Behavior = the way in which something functions or operates l Heuristic = problem-solving by experimental and especially trial-and-error methods l OK, but what does this mean? Examples: l Statistics: on average payload size is between X to Y l Actions: Login using TCP connection followed by a UDP connection on subsequent port number l Extremely effective analysis when application uses encryption 24
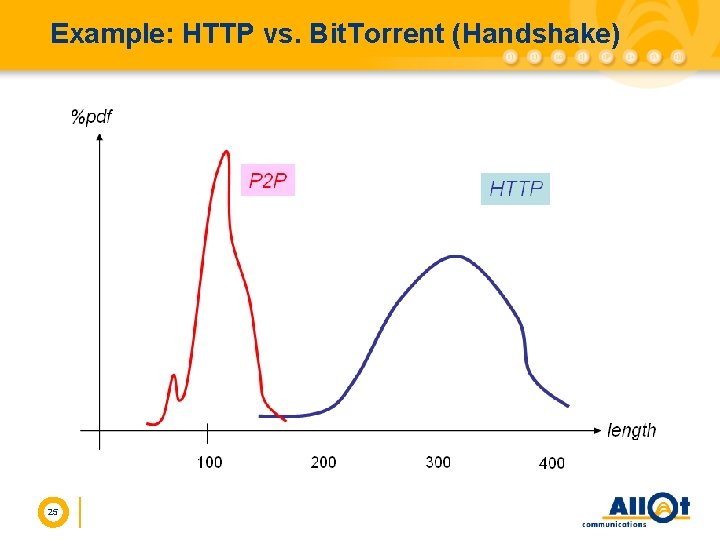
Example: HTTP vs. Bit. Torrent (Handshake) 25
DPI in Real Life l Network Visibility – The key for understanding how bandwidth is utilized l Which application? l Which user? l When? Where? l Traffic Management (Application Control) l Block l Shape (limit, Qo. S, Qo. E) l Service Management (Subscriber Control) l Associate connection (IP X. Y. Z. W) with a user and its service use policy 26
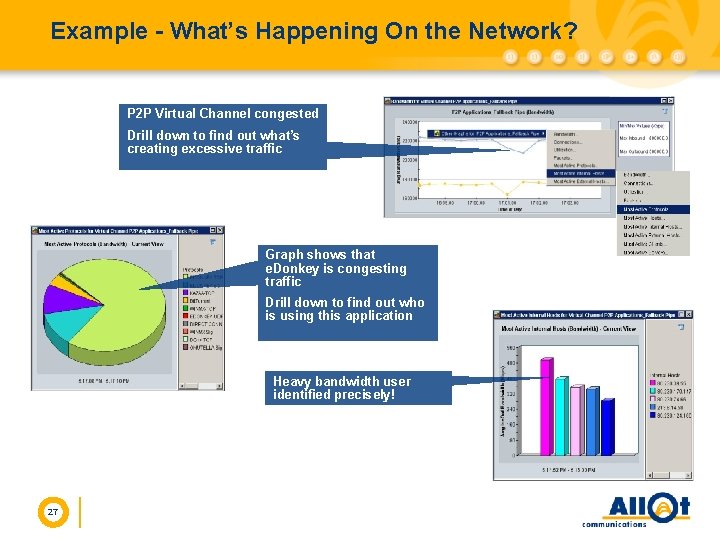
Example - What’s Happening On the Network? P 2 P Virtual Channel congested Drill down to find out what’s creating excessive traffic Graph shows that e. Donkey is congesting traffic Drill down to find out who is using this application Heavy bandwidth user identified precisely! 27

Thank You 28
- Slides: 26