Differentiated Services Diff Serv Definition of Diff Serv






















- Slides: 30

Differentiated Services (Diff. Serv) Definition of Diff. Serv Per Domain Behaviors and Rules for their Specification Papadimitriou Panagiotis 21/01/2004 1

Why Diff. Serv? n Internet currently provides “Best Effort” service (inadequate, Quality of Service not provided). n The IETF defined models, Int. Serv and Diff. Serv, are simply two ways of considering the fundamental problem of providing Qo. S for a given IP packet. n Diff. Serv mainly aims for seamless end-to-end Qo. S deployment with complete management, provisioning, and signaling support. 2

Diff. Serv at a glance n There is a clear need for relatively simple and coarse methods of providing differentiated classes of service for Internet traffic to support various types of applications and specific business requirements. n The differentiated services framework enables quality-of-service provisioning within a network domain by applying rules at the edges to create traffic aggregates and coupling each of these with a specific forwarding path treatment in the domain through use of a codepoint in the IP header. 3

Diff. Serv at a glance (2) Differentiated Services allows an approach to IP Qo. S which: n n is modular is increamentally deployable is scalable introduces minimal per-node complexity 4

Definitions n Differentiated Services Domain (DS Domain): a contiguous portion of the Internet over which a consistent set of differentiated services policies are administered in a coordinated fashion n Differential Services Boundary: the edge of a DS domain, where classifiers and traffic conditioners are likely to be deployed n Per Domain Behaviour (PDB): the expected treatment that an identifiable or target group of packets will receive from “edge to edge” of a DS domain n Per Hop Behaviour (PHB): defines the service at each hop; may be relative (compared to other PHBs) or absolute (in bandwidth or delay terms) 5

Definitions (2) n Traffic Aggregate: collection of packets with a codepoint (DSCP) that maps to the same PHB, usually in a DS domain or some subset of a DS domain n Behaviour Aggregate (BA): a collection of packets with the same codepoint (DSCP) crossing a link in a particular direction n Service Level Specification (SLS): a set of parameters and their values which together define the service offered to traffic stream by a DS domain n Autonomous System (AS): an independantly administered domain of the Internet 6

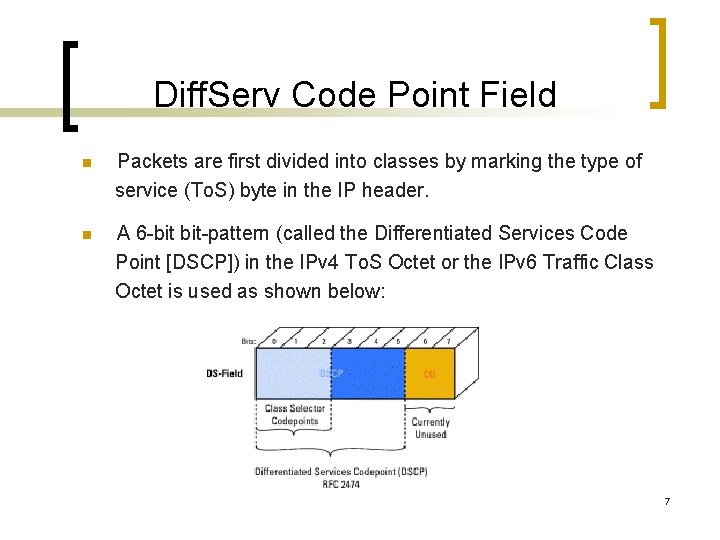
Diff. Serv Code Point Field n Packets are first divided into classes by marking the type of service (To. S) byte in the IP header. n A 6 -bit bit-pattern (called the Differentiated Services Code Point [DSCP]) in the IPv 4 To. S Octet or the IPv 6 Traffic Class Octet is used as shown below: 7

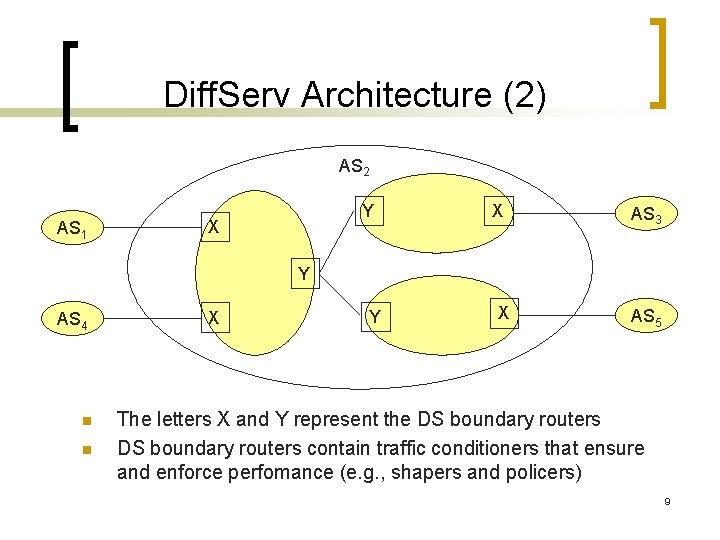
Diff. Serv Architecture n A DS-Domain is made up of DS Ingress nodes, DS Interior nodes (in the core), and DS Egress nodes. n Functionally all DS Ingress and Egress nodes can be categorized as a Boundary node, since they act as a demarcation point between the DS-Domain and the non-DSaware network. 8

Diff. Serv Architecture (2) AS 2 AS 1 Y X X AS 3 Y AS 4 n n X Y X AS 5 The letters X and Y represent the DS boundary routers contain traffic conditioners that ensure and enforce perfomance (e. g. , shapers and policers) 9

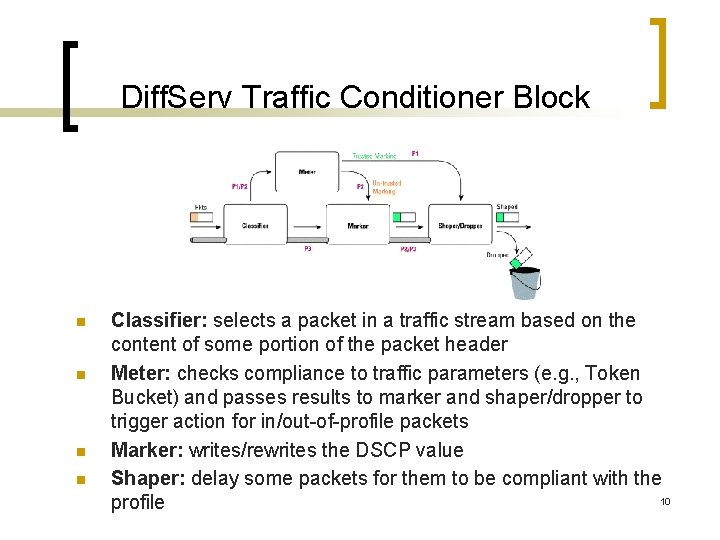
Diff. Serv Traffic Conditioner Block n n Classifier: selects a packet in a traffic stream based on the content of some portion of the packet header Meter: checks compliance to traffic parameters (e. g. , Token Bucket) and passes results to marker and shaper/dropper to trigger action for in/out-of-profile packets Marker: writes/rewrites the DSCP value Shaper: delay some packets for them to be compliant with the 10 profile

Diff. Serv Traffic Conditioner Block (2) A traffic conditioner typically: n n classifies the incoming packets into pre-defined aggregates meters them to determine compliance to traffic parameters (and determines if the packet is in profile, or out of profile), marks them appropriately by writing/re-writing the DSCP, and finally shapes (buffers to achieve a target flow rate) or drops the packet in case of congestion. 11

Defining PDBs n n Each PDB has measurable, quantifiable attributes that can be used to describe what happens to its packets as they enter and cross the DS domain. PDB attributes may be absolute or statistical and they may be parameterized by network properties. A PDB is applied to a target group of packets arriving at the edge of the DS domain. The target group is distinguished from all arriving packets by use of packet classifiers. 12

Defining PDBs (2) The action of the PDB on the target group has 2 parts: n n The first part is the use of traffic conditioning to create a traffic aggregate. During traffic conditioning, conformant packets are marked with a DSCP for the PHB associated with the PDB. The second part is the treatment experienced by packets from the same traffic aggregate transiting the interior of a DS domain, between and inside of DS domain boundaries. 13

The effects of traffic conditioning on the target group n n n This effect is quantified by the relationship of the emerging traffic aggregate to the entering target group. This relationship can depend on the arriving traffic pattern as well the configuration of the traffic conditioners. There may be a “loss rate” on the arriving target group that results from sending too much traffic or the traffic with the wrong temporal characteristics. 14

Crossing the DS Domain n DSCPs should not change in the interior of DS domain as there is no traffic conditioning being applied. n If it is necessary to reapply the kind of traffic conditioning that could result in remarking, there should be a DS domain boundary at that point, though such an “interior” boundary can have “lighter weight” rules in its TCA (Traffic Conditioning Aggrements). 15

Crossing the DS Domain (2) n n A PDB operates between N ingress points and M egress points at the DS domain boundary (N ≥ 1, M ≥ 1). Even in the degenerate case where N = M = 1, PDB attributes are more complex than the definition of PHB attributes since the concatenation of the behavior of intermediate nodes affects the former. A complex case with N > 1, M > 1 involves splits and merges in the traffic path. Analytic, simulation and experimental work will be necessary to understand even the simpler PDBs. 16

Constructing PDBs n A DS domain is configured to meet the network operator's traffic engineering goals for the domain independently of the performance goals for a particular flow of a traffic aggregate. n Multiple PDBs may use the same PHB. The specification of a PDB can contain a list of PHBs and their required configuration, all of which would result in the same PDB. In operation, it is expected that a single domain will use a single PHB to implement a particular PDB, though different domains may select different PHBs. n Multiple PDBs might use the same PHB in which case the transit performance of traffic aggregates of these PDBs will be the same. 17

PDBs using PHB Groups The use of PHB groups to construct PDBs can be done in several ways: n A single PHB member of a PHB group might be used to construct a single PDB. The traffic conditioning for that PDB and the required configuration of the particular PHB would be defined in such a way that there is no dependence or relationship with the manner in which other PHBs of the group are used. n A single PDB can be constructed using more than one PHB from the same PHB group. 18

PDBs using PHB Groups (2) n A set of related PDBs might be defined using a PHB group. This is appropriate when the traffic conditioners that create the traffic aggregates associated with each PDB have some relationships and interdependencies such that the traffic aggregates for these PDBs should be described and characterized together. The transit attributes will depend on the PHB associated with the PDB and will not be the same for all PHBs in the group, though there may be some parameterized interrelationship between the attributes of each of these PDBs. 19

Format for Specification of PDBs n 1. Applicability Statement All PDB specs must have an applicability statement that outlines the intended use of this PDB and the limits to its use. n 2. Technical Specification In general, rules or guidelines to create the PDB. The technical specification must list the classification and traffic conditioning required (if any) and the PHB (or PHBs) to be used with any additional requirements on their configuration. 20

Format for Specification of PDBs (2) n 3. Attributes PDB’s attributes tell how it behaves under ideal conditions if configured in a specified manner Drop rate, throughput, delay bouns, etc. Attributes must be explicit, quantifiable and defensible n 4. Parameters Maximum number of hops Minimum bandwidth Total number of entry / exit points of the PDB Minimum buffer size for the PDB at a network node 21

Format for Specification of PDBs (3) n 5. Assumptions PDBs will be usually specified assuming lossless links, no link failures and relatively stable routing n 6. Example uses A PDB specification must give example uses to motivate the understanding of ways in which a diffserv network could make use of the PDB n 7. Security Considerations for each PDB 22

On PDB Attributes n Topic for Discussion: Under what conditions can we join the output of a DS domain to another under the same traffic conditioning and expectations? n n Although there are many ways in which traffic might be distributed, creating quantifiable, realizable PDBs that can be concatenated into multi-domain services limits the realistic scenarios. A PDB's attributes with a clear statement of the conditions under which the attributes hold is critical to the composition of multi-domain services. 23

On PDB Attributes (2) There are two ways to characterize PDBs with respect to time: n Properties over "long" time periods, or average behaviors. A PDB specification should report these as the rates or throughput seen over some specified time period. n Properties of “short” time behavior, usually expressed as the allowable burstiness in a traffic aggregate. The short time behavior is important in understanding buffering requirements (and associated loss characteristics) and for metering and conditioning considerations at DS boundaries 24

Reference Best Effort PDB n n n We define as a reference a Best Effort PDB, a PDB that has little in the way of rules or expectations A Best Effort (BE) PDB is for sending “normal internet traffic” across a diffserv network The definition and use of this PDB is to preserve, to a reasonable extent, the pre-diffserv delivery expectation for packets in a diffserv network that do not require any special differentiation 25

A look at Int. Serv/RSVP n n The Intergated Services (Int. Serv) model relies on the Resource Reservation Protocol (RSVP) to signal and reserve the desired Qo. S for each flow in the network. Two types of service can be requested via RSVP (assuming all network devices support RSVP along the path from the source to the destination): The first type is a very strict guaranteed service that provides for firm bounds on end-to-end delay and assured bandwidth for traffic that conforms to the reserved specifications. The second type is a controlled load service that provides for a better than best effort and low delay service under light to moderate network loads. Thus, it is possible (at least theoretically) to provide the requisite Qo. S for every flow in the network, provided it is signaled using RSVP and the resources are available. 26

Multi-Protocol Label Switching (MPLS) n n A standards-based technique used to manage and optimize traffic flow for large-scale networks. In an MPLS network, incoming packets are assigned a label by a label edge router (LER). Label switch routers (LSRs) use these labels to forward the packets through the network along a label switch path (LSP). Each LSR removes the existing label and assigns a new one. MPLS combines the advantages of bridges (Layer 2 switching, which is used in ATM and frame relay) and routers (Layer 3 switching, which is used in IP). MPLS serves to create faster and more scalable networks to facilitate quality of service, class of service, and the use of VPNs. Discuss: Differences between Diff. Serv and MPLS? 27

Diff. Serv vs MPLS n n n Diffserv, as mentioned before, takes the IP TOS (type of service) field, renames it the DS byte, and uses it to carry information about IP packet service requirements. It operates at Layer 3 only and does not deal with lower layers. On the other hand, MPLS specifies ways that Layer 3 traffic can be mapped to connection-oriented Layer 2 transports like ATM and Frame Relay. MPLS adds a label containing specific routing information to each IP packet and allows routers to assign explicit paths to various classes of traffic. It also offers traffic engineering and techniques that can boost IP routing efficiency 28

Diff. Serv Issues/Problems n Topic for Discussion: Drawbacks of Diff. Serv? n Provisioning Unlike RSVP/Int. Serv, Diff. Serv needs to be provisioned. Setting up the various classes throughout the network requires knowledge of the applications and traffic statistics for aggregates of traffic on the network. This process of application discovery and profiling can be timeconsuming, although there are tools that can make life easier (e. g. NBAR application discovery, Protocol Analyzers) 29

Diff. Serv Issues/Problems (2) n Billing and Monitoring Management is still a big issue. Even though packets/sec, bytes/sec and many other counters are available via the class-based Management Information Base (MIB), billing and monitoring are still difficult issues. n Qo. S and Routing One of the biggest drawbacks of Diff. Serv comes from the fact that signaling/provisioning happens separate from the routing process. Thus, there may exist a path (e. g. OSPF, ISIS, EIGRP) in the network that has the required resources, even when Diff. Serv fails to find the resources. 30