Detection Scenarios Recon Weaponization Deliver File Behavior File
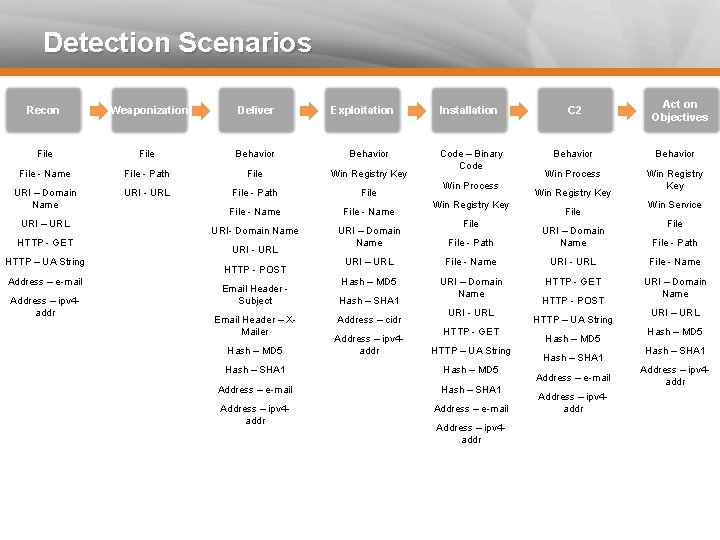
Detection Scenarios Recon Weaponization Deliver File Behavior File - Name File - Path File Win Registry Key URI – Domain Name URI – URL HTTP - GET HTTP – UA String Address – e-mail Address – ipv 4 addr URI - URL File - Path Exploitation File - Name URI- Domain Name URI – Domain Name URI - URL HTTP - POST Email Header Subject Email Header – XMailer Hash – MD 5 Act on Objectives Installation C 2 Code – Binary Code Behavior Win Process Win Registry Key File Win Service File - Path URI – Domain Name File - Path URI – URL File - Name URI - URL File - Name Hash – MD 5 URI – Domain Name HTTP - GET URI – Domain Name Hash – SHA 1 Address – cidr Address – ipv 4 addr URI - URL HTTP - GET HTTP – UA String Hash – SHA 1 Hash – MD 5 Address – e-mail Hash – SHA 1 Address – ipv 4 addr Address – e-mail Address – ipv 4 addr HTTP - POST HTTP – UA String Hash – MD 5 Hash – SHA 1 Address – e-mail Address – ipv 4 addr URI – URL Hash – MD 5 Hash – SHA 1 Address – ipv 4 addr
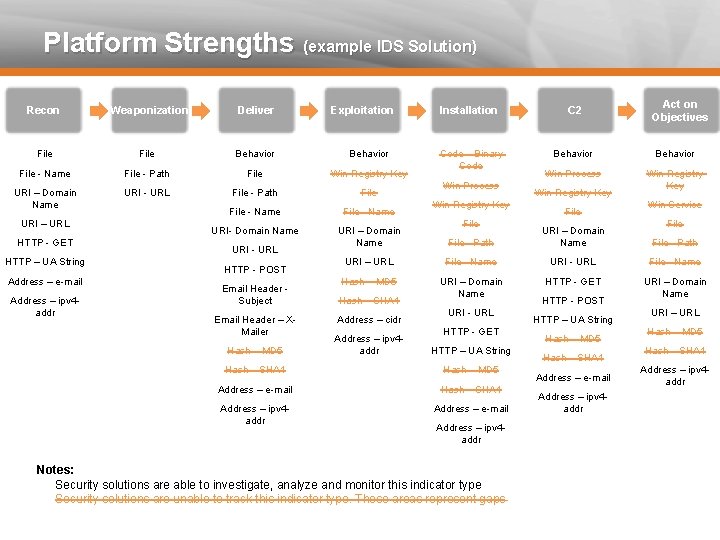
Platform Strengths (example IDS Solution) Recon Weaponization Deliver File Behavior File - Name File - Path File Win Registry Key URI – Domain Name URI – URL HTTP - GET HTTP – UA String Address – e-mail Address – ipv 4 addr URI - URL File - Path Exploitation File - Name URI- Domain Name URI – Domain Name URI - URL HTTP - POST Email Header Subject Email Header – XMailer Hash – MD 5 Act on Objectives Installation C 2 Code – Binary Code Behavior Win Process Win Registry Key File Win Service File - Path URI – Domain Name File - Path URI – URL File - Name URI - URL File - Name Hash – MD 5 URI – Domain Name HTTP - GET URI – Domain Name Hash – SHA 1 Address – cidr Address – ipv 4 addr URI - URL HTTP - GET HTTP – UA String Hash – SHA 1 Hash – MD 5 Address – e-mail Hash – SHA 1 Address – ipv 4 addr Address – e-mail Address – ipv 4 addr Notes: Security solutions are able to investigate, analyze and monitor this indicator type Security solutions are unable to track this indicator type. These areas represent gaps HTTP - POST HTTP – UA String Hash – MD 5 Hash – SHA 1 Address – e-mail Address – ipv 4 addr URI – URL Hash – MD 5 Hash – SHA 1 Address – ipv 4 addr
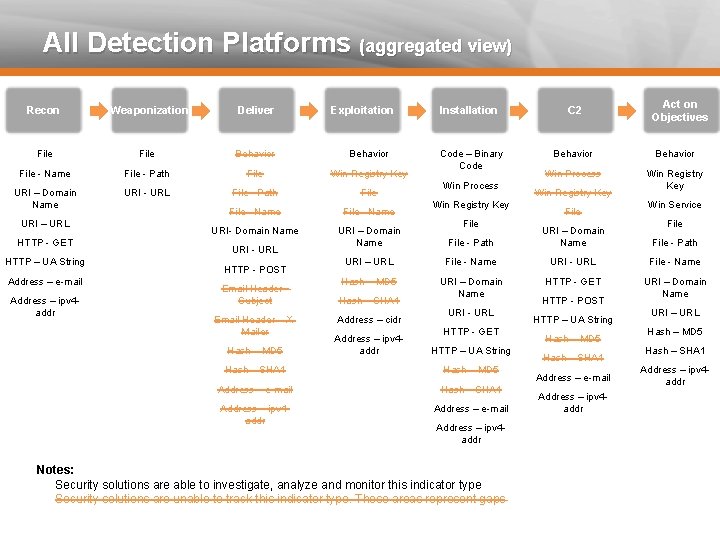
All Detection Platforms (aggregated view) Recon Weaponization Deliver File Behavior File - Name File - Path File Win Registry Key URI – Domain Name URI – URL HTTP - GET HTTP – UA String Address – e-mail Address – ipv 4 addr URI - URL File - Path Exploitation File - Name URI- Domain Name URI – Domain Name URI - URL HTTP - POST Email Header Subject Email Header – XMailer Hash – MD 5 Act on Objectives Installation C 2 Code – Binary Code Behavior Win Process Win Registry Key File Win Service File - Path URI – Domain Name File - Path URI – URL File - Name URI - URL File - Name Hash – MD 5 URI – Domain Name HTTP - GET URI – Domain Name Hash – SHA 1 Address – cidr Address – ipv 4 addr URI - URL HTTP - GET HTTP – UA String Hash – SHA 1 Hash – MD 5 Address – e-mail Hash – SHA 1 Address – ipv 4 addr Address – e-mail Address – ipv 4 addr Notes: Security solutions are able to investigate, analyze and monitor this indicator type Security solutions are unable to track this indicator type. These areas represent gaps HTTP - POST HTTP – UA String Hash – MD 5 Hash – SHA 1 Address – e-mail Address – ipv 4 addr URI – URL Hash – MD 5 Hash – SHA 1 Address – ipv 4 addr

Visibility Gaps by Threat Actor Recon HTTP – UA String Weaponization Deliver Exploitation Installation C 2 Act on Objectives File Email Header - Subject Hash – MD 5 File - Path Email Header – X-Mailer Hash – SHA 1 URI - URL
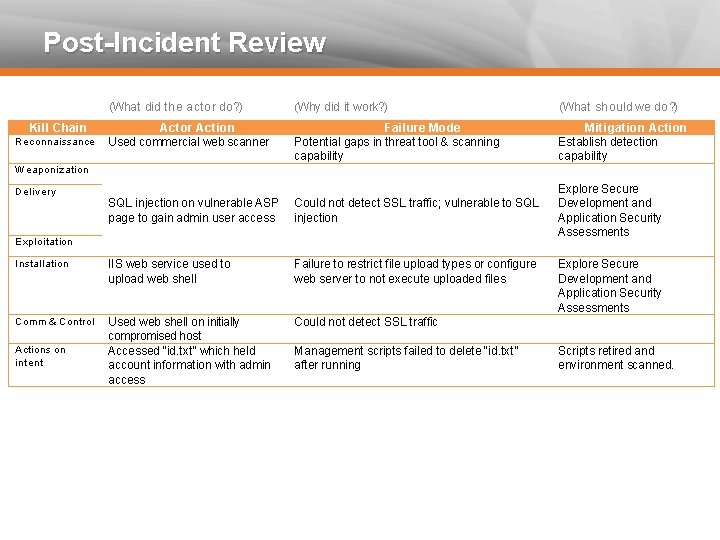
Post-Incident Review (What did the actor do? ) (Why did it work? ) (What should we do? ) Actor Action Used commercial web scanner Failure Mode Potential gaps in threat tool & scanning capability Mitigation Action Establish detection capability SQL injection on vulnerable ASP page to gain admin user access Could not detect SSL traffic; vulnerable to SQL injection Explore Secure Development and Application Security Assessments Installation IIS web service used to upload web shell Failure to restrict file upload types or configure web server to not execute uploaded files Comm & Control Used web shell on initially compromised host Accessed “id. txt” which held account information with admin access Could not detect SSL traffic Kill Chain Reconnaissance Weaponization Delivery Exploitation Actions on intent Management scripts failed to delete “id. txt” after running Explore Secure Development and Application Security Assessments Scripts retired and environment scanned.
- Slides: 5