Detecting Rogue 802 11 Access Points within the








- Slides: 25

Detecting Rogue 802. 11 Access Points within the Enterprise Kirby Kuehl Cisco Systems, Inc. 1

A Brief Introduction • • Access to a wired LAN is governed by access to an Ethernet port for that LAN. Therefore, access control for a wired LAN often is viewed in terms of physical access to LAN ports. Similarly, because data transmitted on a wired LAN is directed to a particular destination, privacy cannot be compromised unless someone uses specialized equipment to intercept transmissions on their way to their destination. In short, a security breach on a wired LAN is possible only if the LAN is physically compromised. With a wireless LAN, transmitted data is broadcast over the air using radio waves, so it can be received by any wireless LAN client in the area served by the data transmitter. Because radio waves travel through ceilings, floors, and walls, transmitted data may reach unintended recipients on different floors and even outside the building of the transmitter. Installing a wireless LAN may seem like putting Ethernet ports everywhere, including in your parking lot. Similarly, data privacy is a genuine concern with wireless LANs because there is no way to direct a wireless LAN transmission to only one recipient. 2

Rogue – Operating outside normal or desirable controls. • • SSID: (Service Set ID )The use of the SSID as a handle to permit/deny access is dangerous because the SSID typically is not well secured. An access point, the device that links wireless clients to the wired LAN, usually is set to broadcast its SSID in its beacons. WEP: (wired equivalent privacy) With open authentication, which is the default, the entire authentication process is done in clear-text, and a client can associate with an access point even without supplying the correct WEP key. With shared-key authentication, the access point sends the client a challenge text packet that the client must encrypt with the correct WEP key and return to the access point. If the client has the wrong key or no key, it will fail authentication and will not be allowed to associate with the access point. (Subject to attack with tools such as airsnort) 3

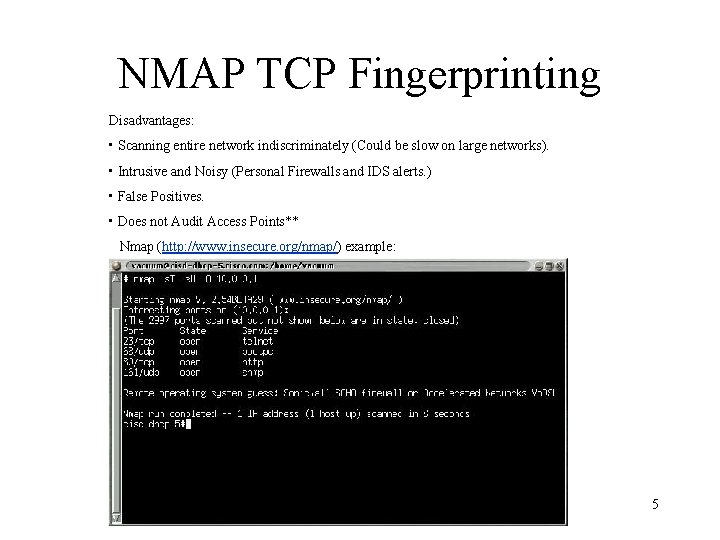
802. 11 b Detection Methods • TCP Fingerprinting (Nmap) 4

NMAP TCP Fingerprinting Disadvantages: • Scanning entire network indiscriminately (Could be slow on large networks). • Intrusive and Noisy (Personal Firewalls and IDS alerts. ) • False Positives. • Does not Audit Access Points** Nmap (http: //www. insecure. org/nmap/) example: 5

802. 11 b Detection Methods • TCP Fingerprinting (Nmap) • 802. 11 b Analyzer (War Driving) 6

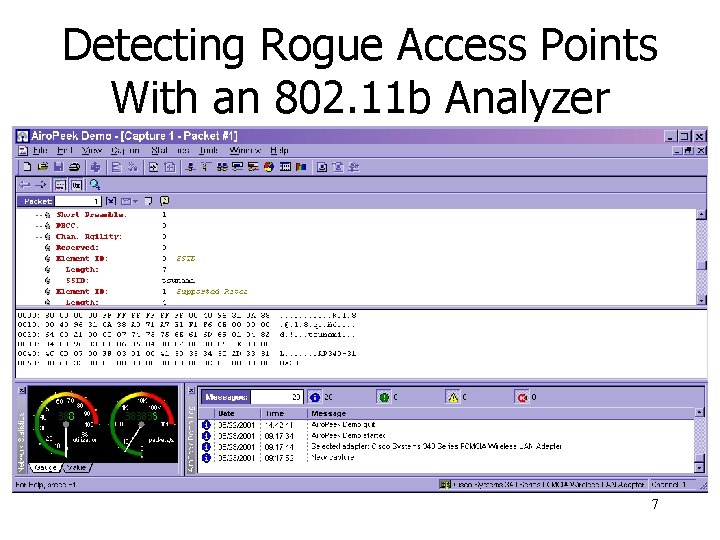
Detecting Rogue Access Points With an 802. 11 b Analyzer 7

“War Driving” is only a partial solution. Disadvantage: Using a Wireless Protocol Analyzer is limited by signal range. Cisco AP 340 Range @ 1 Mbps: 1500 ft. (460 m) open environment; 300 ft. (90 m) office Cisco AP 340 Range @ 11 Mbps: 400 ft. (120 m) open environment; 100 ft. (30 m) office Cisco AP 350 Range @ 11 Mbps: 800 ft (244 m) open environment; 130 ft (39. 6 m) office Cisco AP 350 Range @ 1 Mbps: 2000 ft (610 m) open environment; 350 ft (107 m) office War driving is typically accomplished using a modified access point with a high gain antenna (Yagi) which significantly increases the range (up to 6. 5 miles at 2 Mbps). Cisco Antennas: http: //www. cisco. com/warp/public/cc/pd/witc/ao 340 ap/prodlit/airoa_ds. htm 8

802. 11 b Detection Methods • TCP Fingerprinting (Nmap) • 802. 11 b Analyzer (War Driving) • SNMP 9

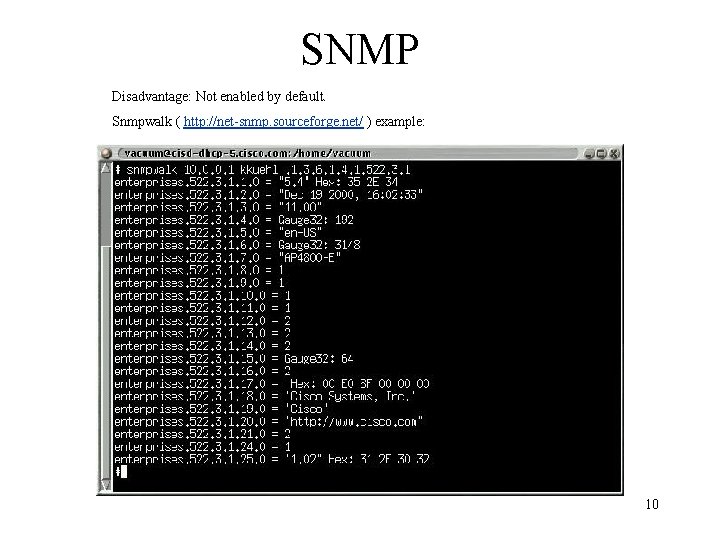
SNMP Disadvantage: Not enabled by default. Snmpwalk ( http: //net-snmp. sourceforge. net/ ) example: 10

802. 11 b Detection Methods • • TCP Fingerprinting (Nmap) 802. 11 b Analyzer (War Driving) SNMP The Origin of APTools. IPSU Ethereal 11

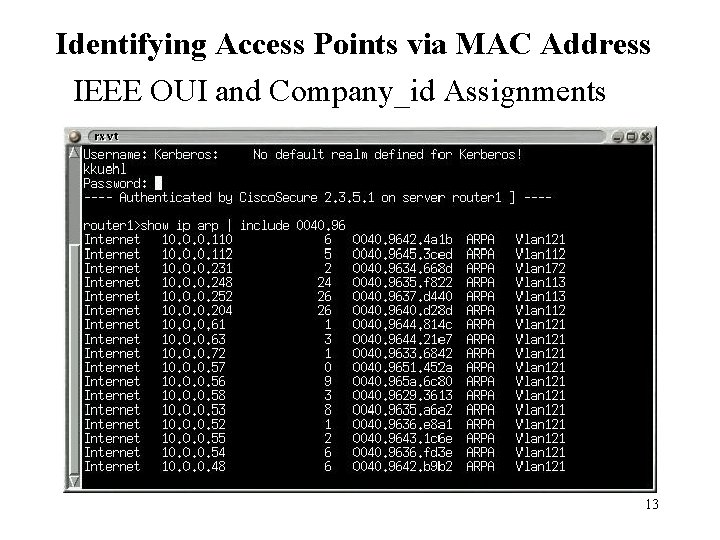
Detecting Access Points by Querying Routers and Switches Advantages: Not limited to the signal range of the access points like “war driving”. Positive Identification through MAC Address assignments and only queries Access Points and Access Point Clients. Audits Security Configuration. 12

Identifying Access Points via MAC Address IEEE OUI and Company_id Assignments 13

Determine if IP is an Access Point or Client via HTTPD Query Request: HEAD / HTTP/1. 0 Referer: http: //10. 0. 0. 10/ Connection: Keep-Alive User-Agent: Mozilla/4. 0 (compatible; MSIE 6. 0; Windows NT 5. 0) Host: 10. 0. 0. 9 Accept: */* Response: HTTP/1. 0 501 Not Implemented (Error Ignored) Server: thttpd/2. 03 11 jul 98 Content-type: text/html Date: THU, 01 JAN 1970 18: 40: 48 GMT Last-modified: THU, 01 JAN 1970 18: 40: 48 GMT Accept-Ranges: bytes Connection: close 14

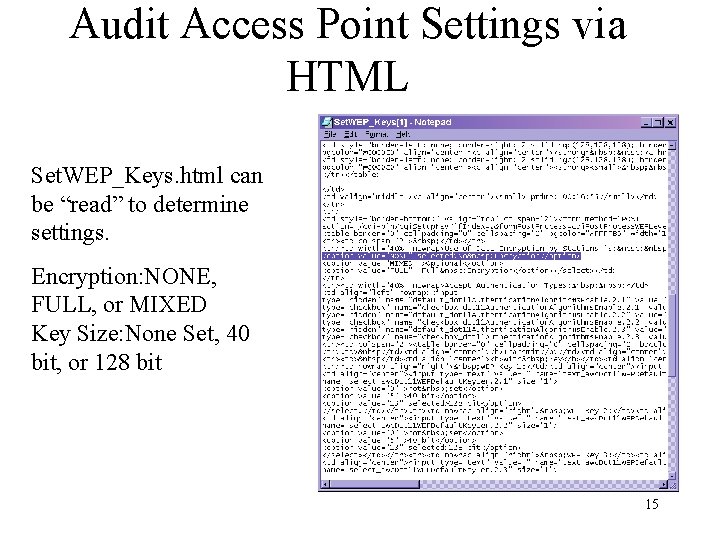
Audit Access Point Settings via HTML Set. WEP_Keys. html can be “read” to determine settings. Encryption: NONE, FULL, or MIXED Key Size: None Set, 40 bit, or 128 bit 15

SNMP Enabled or Disabled? 16

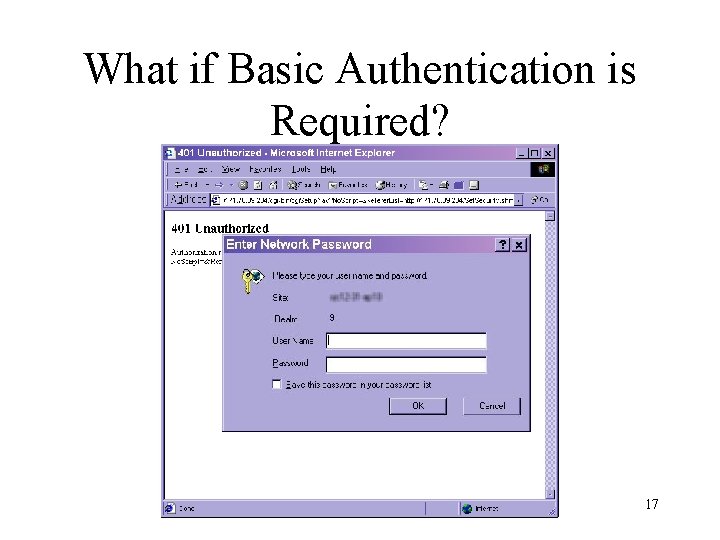
What if Basic Authentication is Required? 17

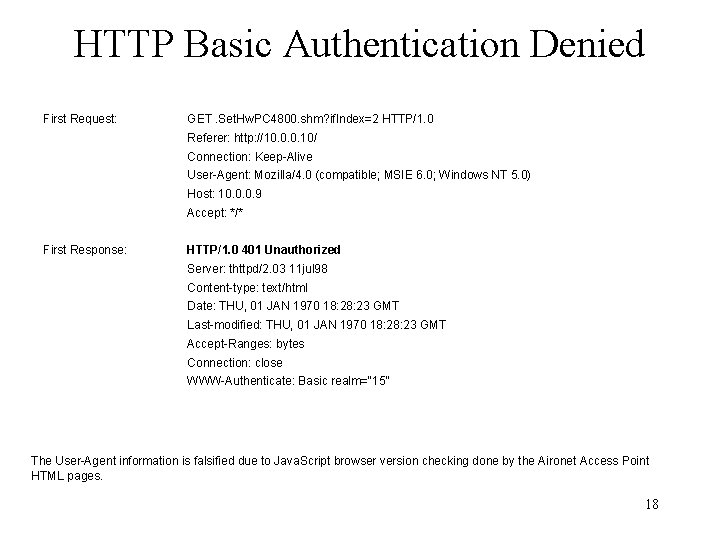
HTTP Basic Authentication Denied First Request: GET. Set. Hw. PC 4800. shm? if. Index=2 HTTP/1. 0 Referer: http: //10. 0. 0. 10/ Connection: Keep-Alive User-Agent: Mozilla/4. 0 (compatible; MSIE 6. 0; Windows NT 5. 0) Host: 10. 0. 0. 9 Accept: */* First Response: HTTP/1. 0 401 Unauthorized Server: thttpd/2. 03 11 jul 98 Content-type: text/html Date: THU, 01 JAN 1970 18: 23 GMT Last-modified: THU, 01 JAN 1970 18: 23 GMT Accept-Ranges: bytes Connection: close WWW-Authenticate: Basic realm="15“ The User-Agent information is falsified due to Java. Script browser version checking done by the Aironet Access Point HTML pages. 18

HTTP Basic Authentication Accepted The client then sends the user-ID and password, separated by a single colon (": ") character, within a base 64 encoded string in the http request. Second Request: GET /Set. Hw. PC 4800. shm? if. Index=2 HTTP/1. 0 Referer: http: //10. 0. 0. 10/ Connection: Keep-Alive User-Agent: Mozilla/4. 0 (compatible; MSIE 6. 0; Windows NT 5. 0) Host: 10. 0. 0. 9 Accept: */* Authorization: Basic YWRta. W 46 c. GFzcw== Second Response: HTTP/1. 0 200 OK Date: FRI, 02 JAN 1970 12: 00 GMT Expires: THU, 01 JAN 1970 12: 00 GMT Content-type: text/html The User-Agent information is falsified due to Java. Script browser version checking done by the Aironet Access Point HTML pages. 19

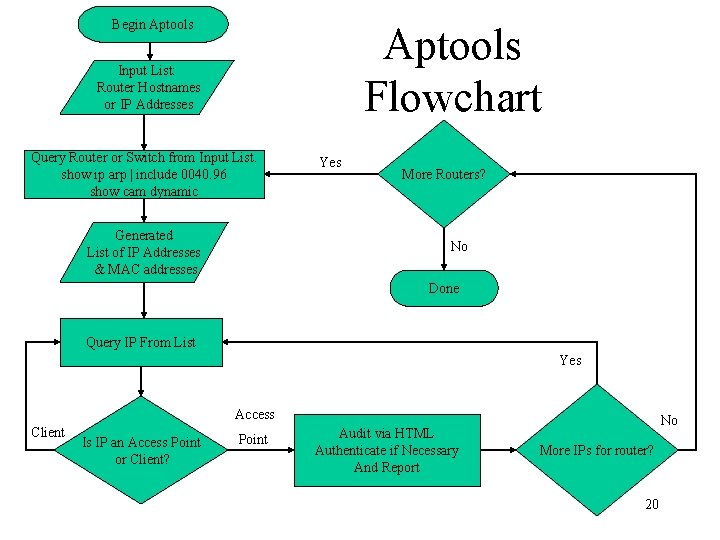
Begin Aptools Flowchart Input List: Router Hostnames or IP Addresses Query Router or Switch from Input List. show ip arp | include 0040. 96 show cam dynamic Generated List of IP Addresses & MAC addresses Yes More Routers? No Done Query IP From List Yes Access Client Is IP an Access Point or Client? Point Audit via HTML Authenticate if Necessary And Report No More IPs for router? 20

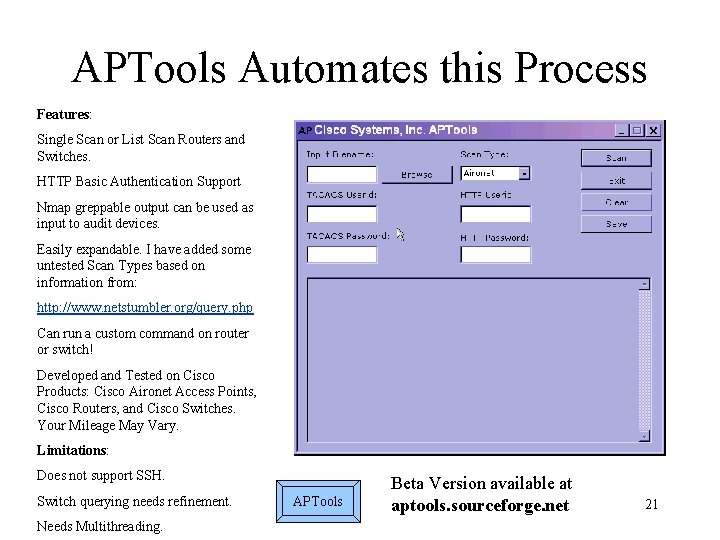
APTools Automates this Process Features: Single Scan or List Scan Routers and Switches. HTTP Basic Authentication Support Nmap greppable output can be used as input to audit devices. Easily expandable. I have added some untested Scan Types based on information from: http: //www. netstumbler. org/query. php Can run a custom command on router or switch! Developed and Tested on Cisco Products: Cisco Aironet Access Points, Cisco Routers, and Cisco Switches. Your Mileage May Vary. Limitations: Does not support SSH. Switch querying needs refinement. Needs Multithreading. APTools Beta Version available at aptools. sourceforge. net 21

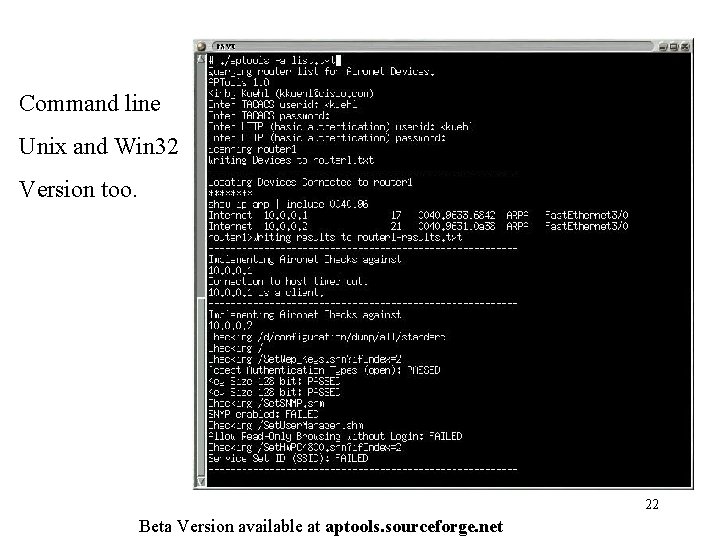
Command line Unix and Win 32 Version too. 22 Beta Version available at aptools. sourceforge. net

Works Cited Cisco Aironet http: //www. cisco. com/warp/public/cc/pd/witc/ao 340 ap/prodlit/airoa_ds. htm Assessing Wireless Security With Airo. Peek http: //www. wildpackets. com/elements/Airo. Peek_Security. pdf Wild. Packets Airo. Peek http: //www. wildpackets. com/products/airopeek IEEE OUI and Company_id Assignments http: //standards. ieee. org/regauth/oui/index. shtml http: //www. netstumbler. org Snmpwalk http: //net-snmp. sourceforge. net HTTP Basic Authentication http: //www. w 3. org/Protocols/HTTP/1. 0/spec. html - Basic. AA Nmap http: //www. insecure. org/nmap Remote OS Detection via TCP/IP fingerprinting http: //www. insecure. org/nmap-fingerprinting-article. html List of Default SSIDS 23

End of Presentation Please remember to fill out the Speaker evaluation forms. 24

Cisco Aironet Security Solution Provides Dynamic WEP to Address Researchers' Concerns Recently, researchers at the University of California, at Berkeley, published a document identifying "security flaws in the 802. 11 security protocol (WEP), " that "seriously undermine the security claims of the system" and use WEP insufficient for wireless LAN (WLAN) security. Articles about the researchers' findings have appeared in The Wall Street Journal and other publications. (Review the summary at http: //www. isaac. cs. berkeley. edu/isaac/wep-faq. html and detailed paper at http: //www. isaac. cs. berkeley. edu/isaac/wep-draft. pdf. ) Cisco was aware of these limitations before the company defined its Aironet® security architecture. With the recent Aironet Software Release 11. 0 and ACS 2. 6, Cisco offers centrally managed, dynamic per user, per session WEP that addresses several of the concerns that the researchers refer to in their paper. Cisco agrees with Berkeley researchers who cite inherent weaknesses in WEP as defined by IEEE 802. 11 b, the standard for WLANs, and that these weaknesses exist regardless of the length of the encryption key used. The weakness of most WLANs is their use of static WEP keys shared among users. "In practice, most installations use a single key that is shared between all mobile stations and access points, " the Berkeley report states. "More sophisticated key management techniques can be used to help defend from the attacks we describe; however, no commercial system we are aware of has mechanisms to support such techniques. " URL: http: //www. cisco. com/warp/public/cc/pd/witc/ao 350 ap/prodlit/1281_pp. htm Airsnort ( http: //airsnort. sourceforge. net) and WEPCrack (http: //wepcrack. sourceforge. net) are two utilities that can be used to recover WEP keys. 25