Detecting DDo S Attacks on ISP Networks Ashwin








- Slides: 12

Detecting DDo. S Attacks on ISP Networks Ashwin Bharambe Carnegie Mellon University Joint work with: Aditya Akella, Prof. Mike Reiter and Prof. Srinivasan Seshan

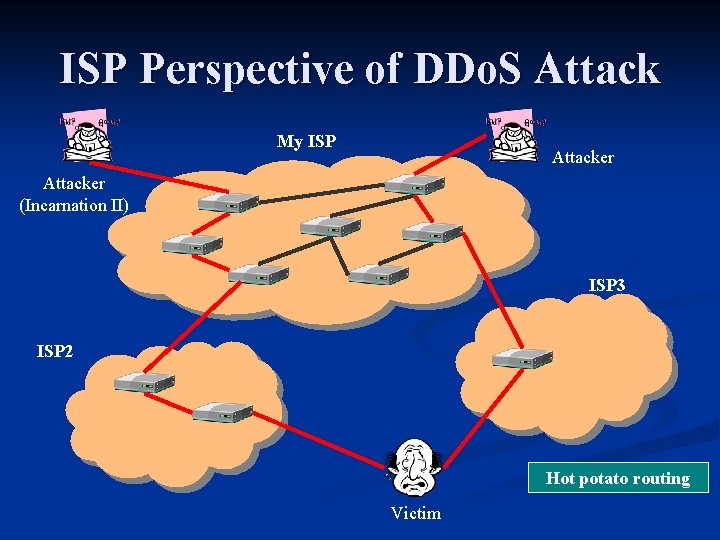
Problem Statement n How can an ISP find out if: Its Backbone is carrying “useless” attack traffic? n Its Backbone is itself under attack? n

ISP Perspective of DDo. S Attack My ISP Attacker (Incarnation II) ISP 3 ISP 2 Hot potato routing Victim

Problem Statement n How can an ISP find out if: Its Backbone is carrying “useless” attack traffic? n Its Backbone is itself under attack? n n Current solutions for DDo. S detection n Focus on end-node victims

Basic Approach 1. 2. Record “normal” traffic at routers Detect “abnormalities” in traffic Challenges a. b. c. d. e. What is normal and what is abnormal? Is it robust? How quickly can we identify deviations? Can it really be implemented on a backbone router? Response strategy?

Proposed Solution Maintain Traffic Profiles n Each router constructs profiles of traffic Longer time-windows normal traffic n Smaller time-windows current traffic n n Become suspicious if current profile violates normal profile

Important Challenges 1. Day-of-week and Time-of-day effects n 2. Maintain per-daytime statistics Flash crowds n Example of “harmless” but infrequent event n n Attack-volume alone is not a sufficient indicator “Fingerprint” the destination-bound traffic n Number of sources, source-subnets, flows, distribution of flow lengths, etc.

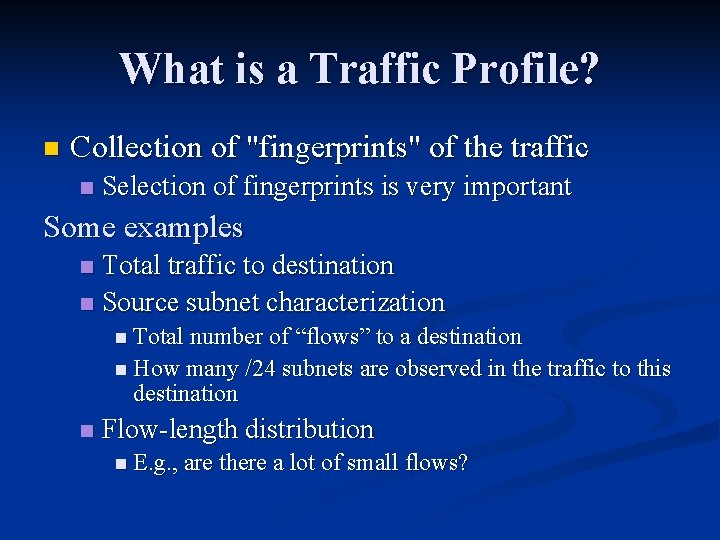
What is a Traffic Profile? n Collection of "fingerprints" of the traffic n Selection of fingerprints is very important Some examples Total traffic to destination n Source subnet characterization n n Total number of “flows” to a destination n How many /24 subnets are observed in the traffic to this destination n Flow-length distribution n E. g. , are there a lot of small flows?

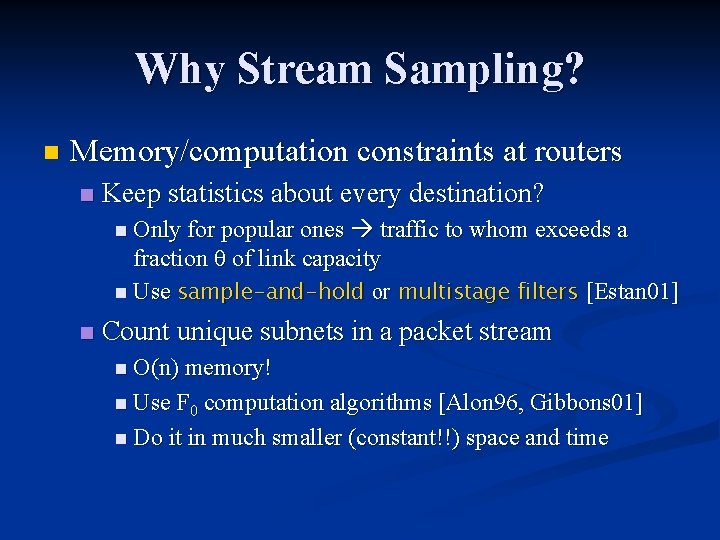
Why Stream Sampling? n Memory/computation constraints at routers n Keep statistics about every destination? n Only for popular ones traffic to whom exceeds a fraction of link capacity n Use sample-and-hold or multistage filters [Estan 01] n Count unique subnets in a packet stream n O(n) memory! n Use F 0 computation algorithms [Alon 96, Gibbons 01] n Do it in much smaller (constant!!) space and time

Proposed Solution Increasing Robustness n Single router has only local view can make mistakes n Traffic perturbations due to traffic engineering n False alarms! n Attacker can “mimic” normal traffic at a router n Attack goes undetected! Mimicking at more than a few routers within an ISP would be hard! n Use router consensus for reinforcing suspicions across routers n

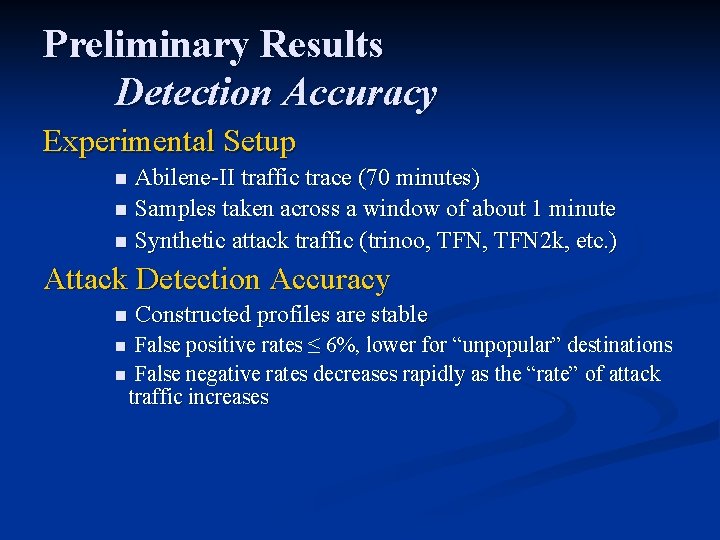
Preliminary Results Detection Accuracy Experimental Setup Abilene-II traffic trace (70 minutes) n Samples taken across a window of about 1 minute n Synthetic attack traffic (trinoo, TFN 2 k, etc. ) n Attack Detection Accuracy n Constructed profiles are stable False positive rates ≤ 6%, lower for “unpopular” destinations n False negative rates decreases rapidly as the “rate” of attack traffic increases n

Conclusions and Future Work n Conclusions Fingerprinting traffic allows for detection of subtle attack patterns not apparent from volume alone n Distributed detection makes it harder for an attacker to mimic traffic at multiple routers n n Directions for future work Identify various attack scenarios n Optimize computation/space requirements n Consensus algorithm; convergence and effectiveness n