Detecting Critical Nodes for MANET IDS A Karygiannis










- Slides: 12

Detecting Critical Nodes for MANET IDS A Karygiannis, E Antonakakis, and A Apostolopoulos Presented by: Sarah Casey 1

MANET Intrusion Detection Challenges No Central Authority or Administration Can only directly monitor neighbouring nodes (within radio range) Mobility allows malicious nodes to enter and leave the network at will 2

Additional Challenges Dynamic topology No trust relationships between nodes Little incentive for collaboration 3

Re-Routing Often possible Densely populated or highly mobile Easier than trying to monitor nodes and paths 4

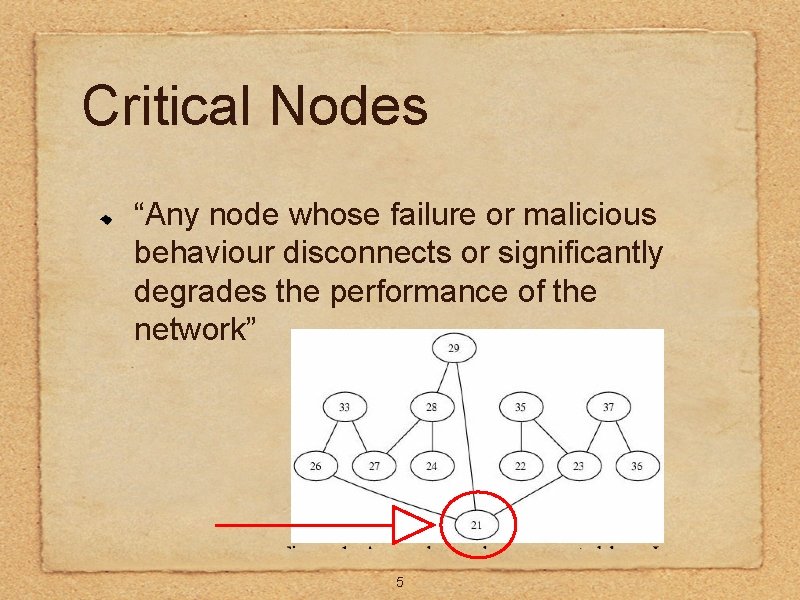
Critical Nodes “Any node whose failure or malicious behaviour disconnects or significantly degrades the performance of the network” 5

Critical Node Detection Step 1: Disable all links but one Step 2: Attempt to ping node under test Step 3: Restore original routing Iterate for all possible links except the link to the node under test. If another path exists, the node is not critical.

m. Lab Emulator, not a simulator Management software for real nodes Allows dynamic topology changes without physical node movement http: //csrc. nist. gov/manet/#m. Lab

Emulation Environment 12 nodes total 10 ARM, 2 x 86 topology changes every 5 -10 min “Detailed test conditions, . . . , and test results can be found on our project web site” - no URL provided

Critical Test vs Watchdog Monitoring CPU Usage: Watchdog - 60 -70% m. Critical - < 1%

Critical Test vs Watchdog Monitoring Initial Memory: Watchdog - 450 KB m. Critical - 125 KB m. Critical keeps tables of outgoing and incoming packet headers Track links and routes

Critical Test vs Watchdog Monitoring Additional Packet Loss: Watchdog - 0% m. Critical - 2 -4% Additional packet loss occurs when manipulating routing table during test

Conclusions Light weight alternative to full IDS monitoring on all nodes No cooperation from, or security association with, other nodes required If re-routing is possible, do it; If not, time to employ (limited) monitoring 12