DesignTimeRunTime Mapping of SecurityCritical Applications in Heterogeneous MPSo



![Run-Time Mapping • Extended Constraint Graph Embedding: • Backtracking algorithm [1] with 100% bandwidth Run-Time Mapping • Extended Constraint Graph Embedding: • Backtracking algorithm [1] with 100% bandwidth](https://slidetodoc.com/presentation_image_h/11cb75ce9e857c424ee0fd1752377cac/image-19.jpg)
![Experimental Results • Integration of spatially isolated mapping into DAARM flow [1] • Java Experimental Results • Integration of spatially isolated mapping into DAARM flow [1] • Java](https://slidetodoc.com/presentation_image_h/11cb75ce9e857c424ee0fd1752377cac/image-20.jpg)




- Slides: 34

Design-Time/Run-Time Mapping of Security-Critical Applications in Heterogeneous MPSo. Cs Andreas Weichslgartner, Stefan Wildermann, Johannes Götzfried, Felix Freiling, Michael Glaß, Jürgen Teich Department of Computer Science Friedrich-Alexander-Universität Erlangen-Nürnberg (FAU), Germany andreas. weichslgartner@fau. de

• Number of cores in processors increases • Applications with various non-functional requirements (e. g. , timing, security) Slide 2

Side-Channel Attacks Task b does RSA: • Uses I-Cache • Uses BIGNUM lib • Code dependent on key b a Task a is malicious: • Dummy instructions • Uses I-Cache • Evicts BIGNUM instructions • Measures execution time Side-channel attack in shared resource Aciiçmez, Onur. "Yet another microarchitectural attack: exploiting I-cache. " Proceedings of the 2007 ACM workshop on Computer security architecture. ACM, 2007. Slide 3

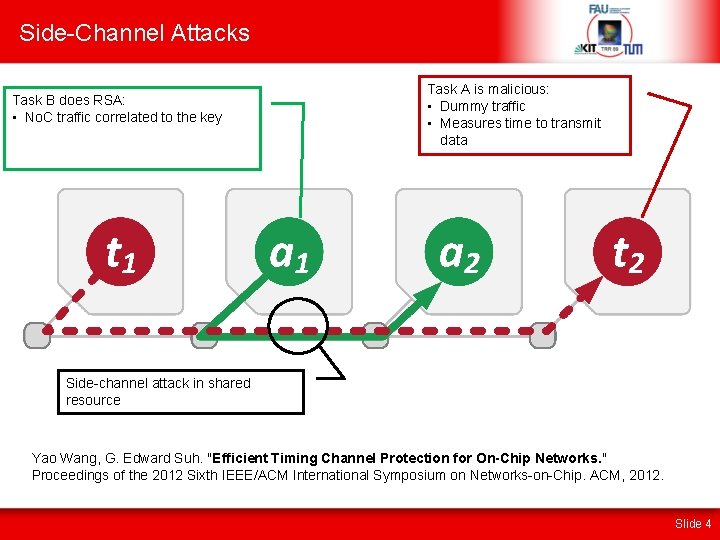
Side-Channel Attacks Task B does RSA: • No. C traffic correlated to the key Task A is malicious: • Dummy traffic • Measures time to transmit data Side-channel attack in shared resource Yao Wang, G. Edward Suh. "Efficient Timing Channel Protection for On-Chip Networks. " Proceedings of the 2012 Sixth IEEE/ACM International Symposium on Networks-on-Chip. ACM, 2012. Slide 4

Side-Channel Attacks How to prevent interference and side-channel attacks? Slide 5

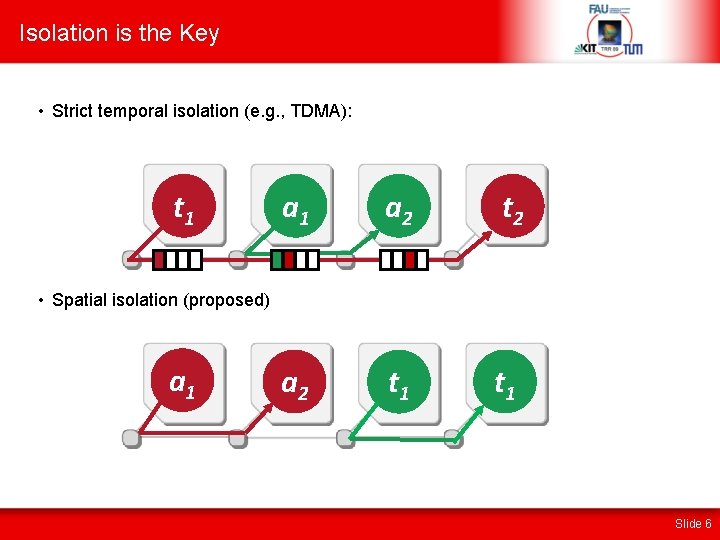
Isolation is the Key • Strict temporal isolation (e. g. , TDMA): t 1 a 2 t 2 a 2 t 1 • Spatial isolation (proposed) a 1 Slide 6

Side-Channel Attacks How to achieve spatial isolation in presence of dynamic application mixes? Slide 7

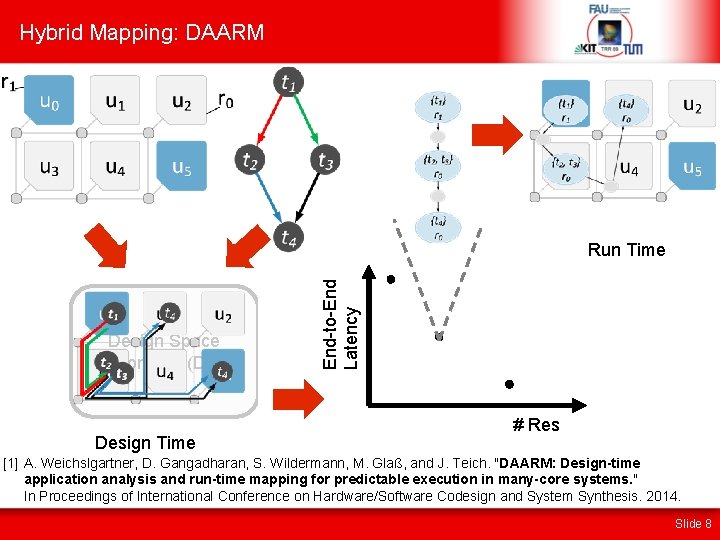
Hybrid Mapping: DAARM Design Space Exploration (DSE) Design Time End-to-End Latency Run Time # Res [1] A. Weichslgartner, D. Gangadharan, S. Wildermann, M. Glaß, and J. Teich. "DAARM: Design-time application analysis and run-time mapping for predictable execution in many-core systems. " In Proceedings of International Conference on Hardware/Software Codesign and System Synthesis. 2014. Slide 8

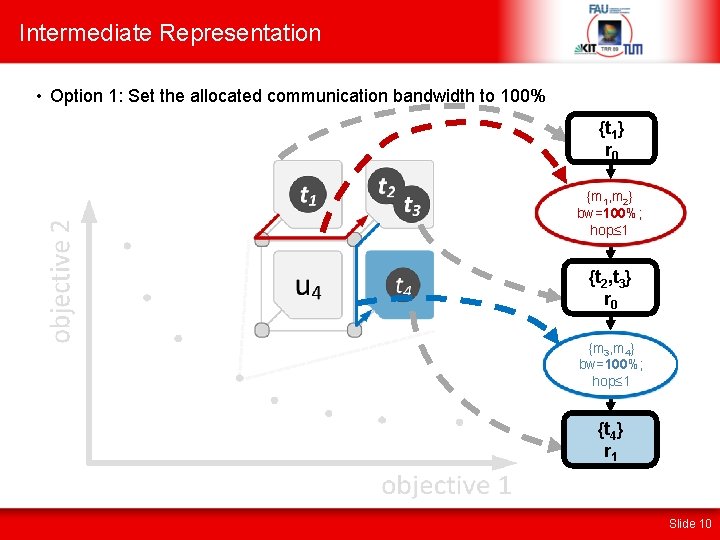
Intermediate Representation • Option 1: Set the allocated communication bandwidth to 100% {t 1} r 0 {m 1, m 2} bw=100%; bw=80%; hop≤ 1 {t 2, t 3} r 0 {m {m 33, m 44}} bw=100%; bw=70%; hop≤ 1 {t 4} r 1 Slide 10

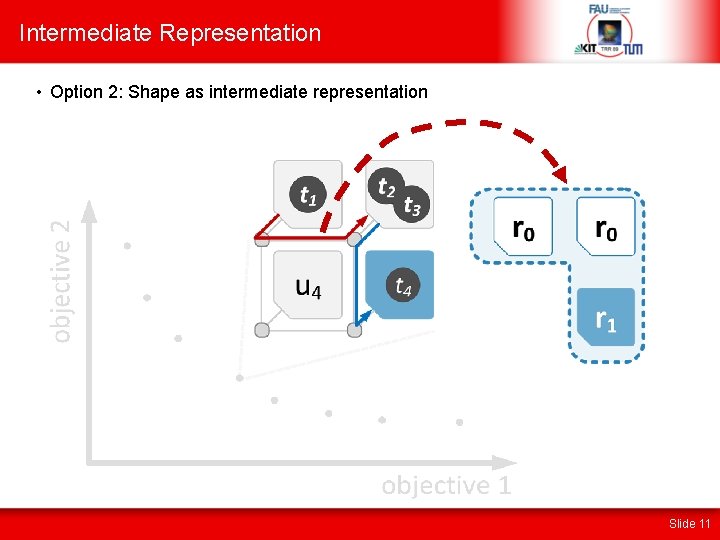
Intermediate Representation • Option 2: Shape as intermediate representation Slide 11

What about routing and shapes? Slide 12

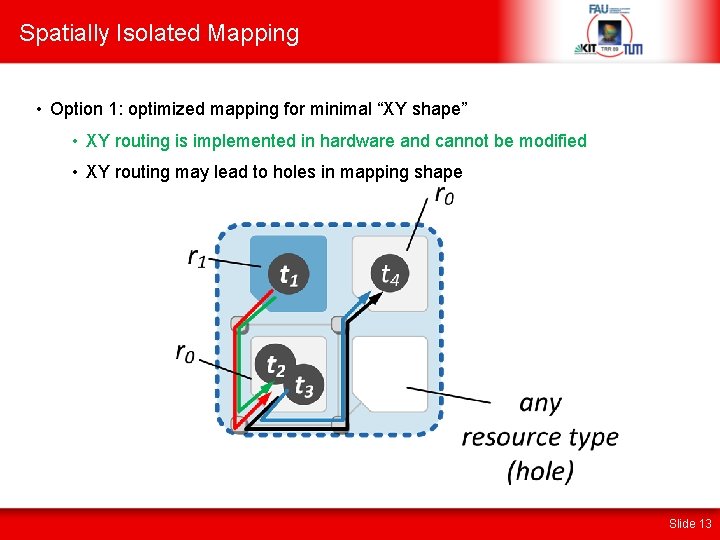
Spatially Isolated Mapping • Option 1: optimized mapping for minimal “XY shape” • XY routing is implemented in hardware and cannot be modified • XY routing may lead to holes in mapping shape Slide 13

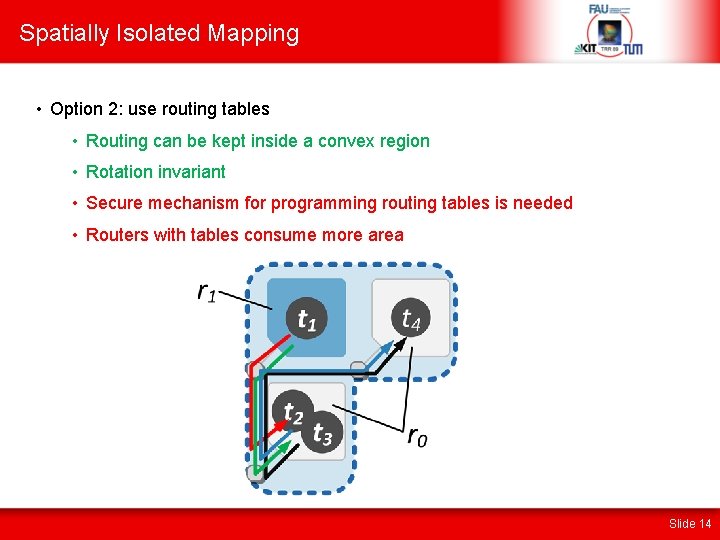
Spatially Isolated Mapping • Option 2: use routing tables • Routing can be kept inside a convex region • Rotation invariant • Secure mechanism for programming routing tables is needed • Routers with tables consume more area Slide 14

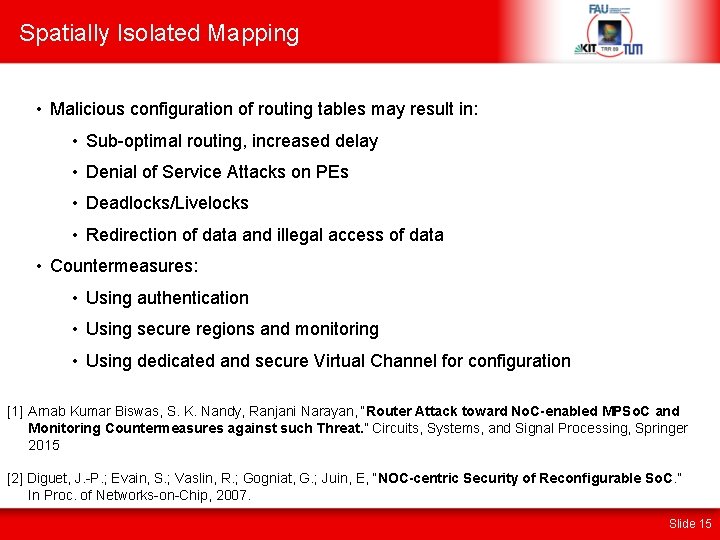
Spatially Isolated Mapping • Malicious configuration of routing tables may result in: • Sub-optimal routing, increased delay • Denial of Service Attacks on PEs • Deadlocks/Livelocks • Redirection of data and illegal access of data • Countermeasures: • Using authentication • Using secure regions and monitoring • Using dedicated and secure Virtual Channel for configuration [1] Arnab Kumar Biswas, S. K. Nandy, Ranjani Narayan, “Router Attack toward No. C-enabled MPSo. C and Monitoring Countermeasures against such Threat. ” Circuits, Systems, and Signal Processing, Springer 2015 [2] Diguet, J. -P. ; Evain, S. ; Vaslin, R. ; Gogniat, G. ; Juin, E, “NOC-centric Security of Reconfigurable So. C. ” In Proc. of Networks-on-Chip, 2007. Slide 15

Attacker Model • Attacker controls one application • No physical access to hardware (e. g. , RAM dumping or chip probing) • Attacker has knowledge about victim‘s source code, mapping, scheduling • Trusted computing base (TCB): • Hardware • Operating System Slide 16

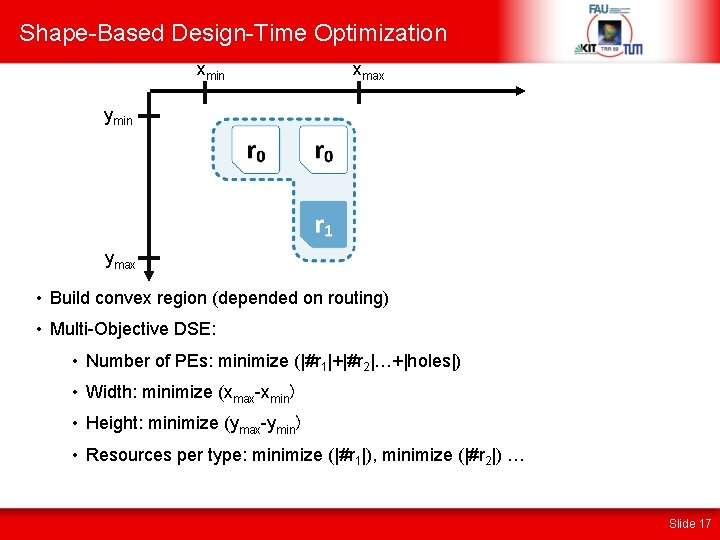
Shape-Based Design-Time Optimization xmin xmax ymin ymax • Build convex region (depended on routing) • Multi-Objective DSE: • Number of PEs: minimize (|#r 1|+|#r 2|…+|holes|) • Width: minimize (xmax-xmin) • Height: minimize (ymax-ymin) • Resources per type: minimize (|#r 1|), minimize (|#r 2|) … Slide 17

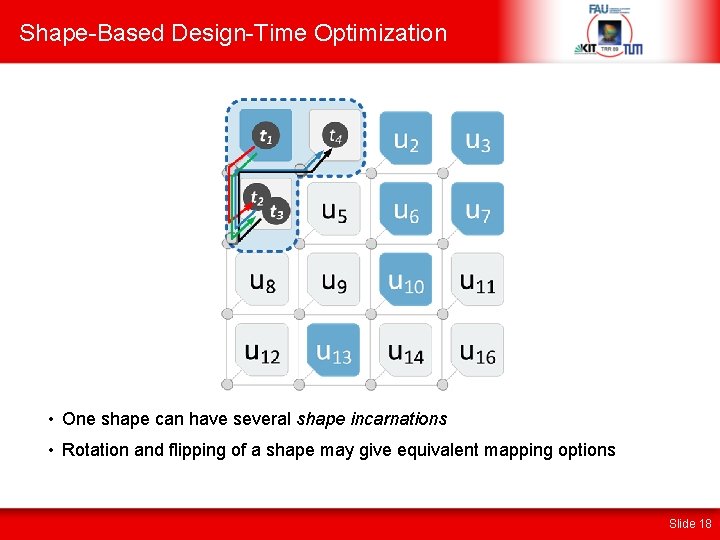
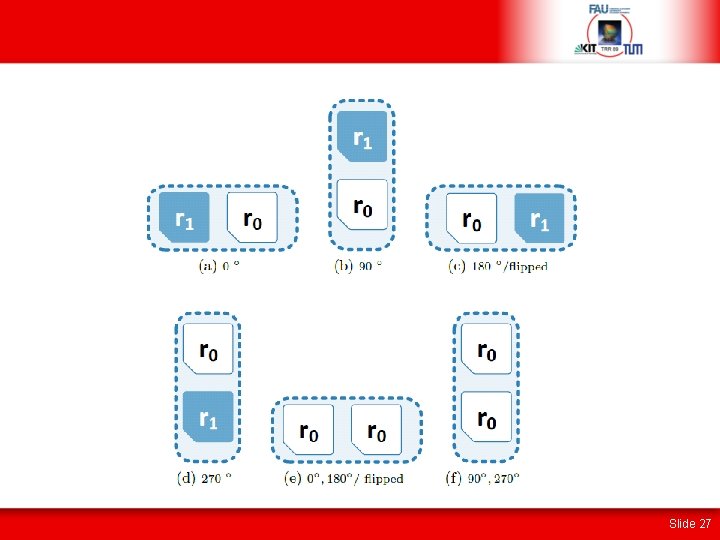
Shape-Based Design-Time Optimization • One shape can have several shape incarnations • Rotation and flipping of a shape may give equivalent mapping options Slide 18

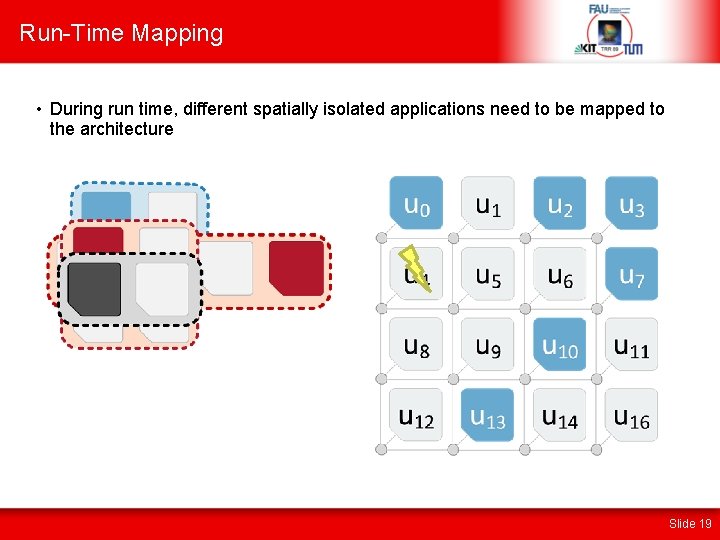
Run-Time Mapping • During run time, different spatially isolated applications need to be mapped to the architecture Slide 19
![RunTime Mapping Extended Constraint Graph Embedding Backtracking algorithm 1 with 100 bandwidth Run-Time Mapping • Extended Constraint Graph Embedding: • Backtracking algorithm [1] with 100% bandwidth](https://slidetodoc.com/presentation_image_h/11cb75ce9e857c424ee0fd1752377cac/image-19.jpg)
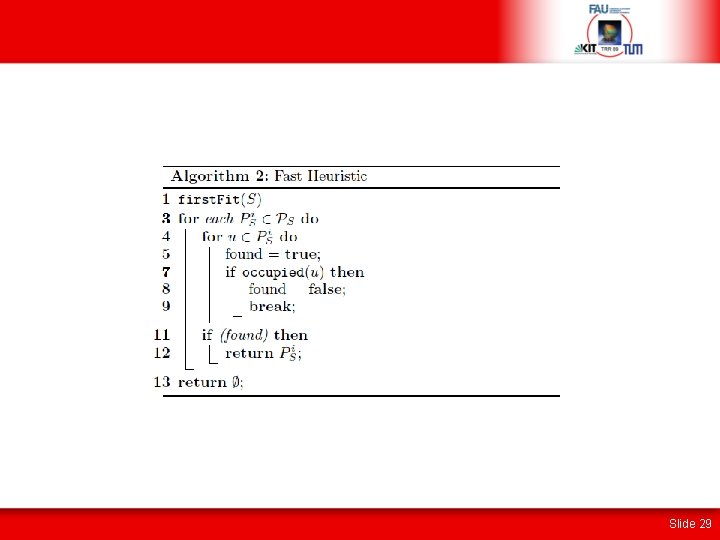
Run-Time Mapping • Extended Constraint Graph Embedding: • Backtracking algorithm [1] with 100% bandwidth constraint • First Fit Heuristic: • Map first shape incarnation which does not overlap with any other shape incarnation of another application • Shape incarnations can be computed at design-time or during run-time • Formulation as a Satisfiability Problem (SAT): • Concurrent shape selection and mapping of application • Can also be applied in an incremental way [1] A. Weichslgartner, D. Gangadharan, S. Wildermann, M. Glaß, and J. Teich. "DAARM: Design-time application analysis and run-time mapping for predictable execution in many-core systems. " In Proceedings of International Conference on Hardware/Software Codesign and System Synthesis. 2014. Slide 20
![Experimental Results Integration of spatially isolated mapping into DAARM flow 1 Java Experimental Results • Integration of spatially isolated mapping into DAARM flow [1] • Java](https://slidetodoc.com/presentation_image_h/11cb75ce9e857c424ee0fd1752377cac/image-20.jpg)
Experimental Results • Integration of spatially isolated mapping into DAARM flow [1] • Java implementation on Intel i 7 -2600 machine • Opt 4 J [2] for DSE, SAT 4 J [3] as SAT solver • 5 applications from the E 3 S Benchmark [4] • 3 different application mixes • 6 x 6 No. C architecture with 3 different processor types [1] A. Weichslgartner, D. Gangadharan, S. Wildermann, M. Glaß, and J. Teich. "DAARM: Design-time application analysis and run-time mapping for predictable execution in many-core systems. " In Proceedings of International Conference on Hardware/Software Codesign and System Synthesis. 2014. [2] M. Lukasiewycz, M. Glaß, F. Reimann, and J. Teich. “Opt 4 J - a modular framework for meta-heuristic optimization. ” In Proceedings of GECCO, 2011. [3] D. Le Berre and A. Parrain. “The SAT 4 J library, release 2. 2. ” Journal on Satisfiability, Boolean Modeling and Computation, 2010. [4] R. Dick. “Embedded system synthesis benchmarks suite (E 3 S)”, 2010. http: //ziyang. eecs. umich. edu/dickrp/e 3 s/ Slide 21

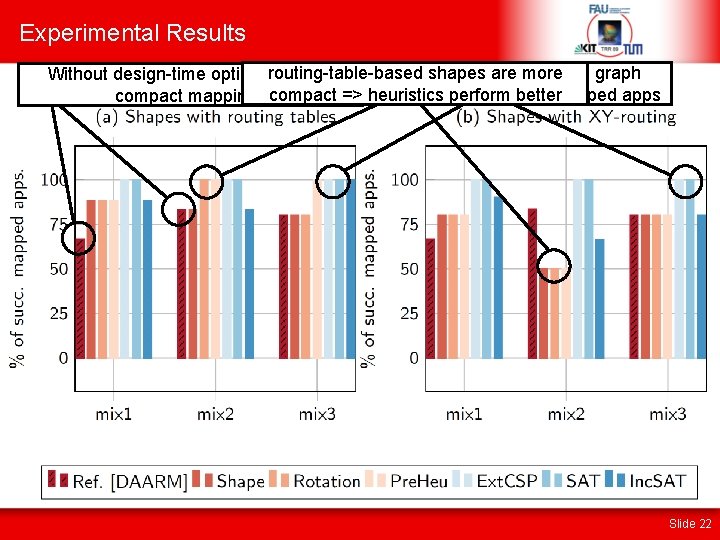
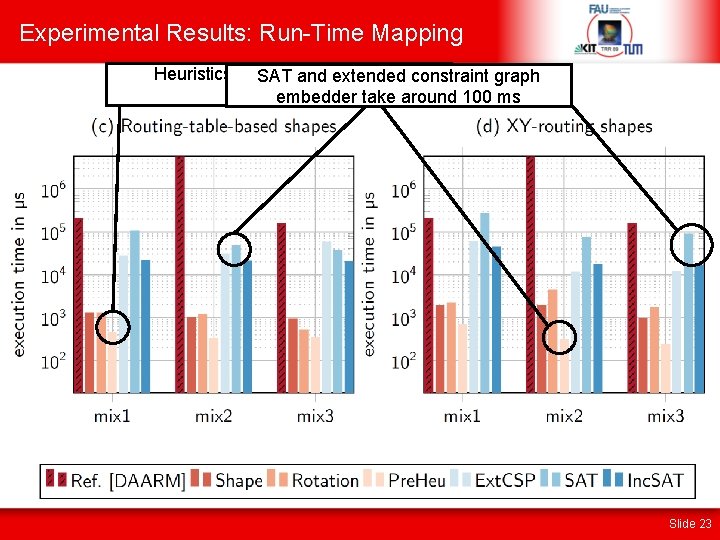
Experimental Results routing-table-based shapes are more SAT and extended constraint graph Without design-time optimization for mapping result both 100% mapped apps compact mappings compact => heuristics perform better Slide 22

Experimental Results: Run-Time Mapping Heuristics produce mappings in SAT and extended constraint graph microseconds embedder take around 100 ms Slide 23

Conclusion • Sharing of No. C resources opens possibilities for side-channel attacks • Spatial isolation of communication and computation closes side channels • We implemented spatially isolated mapping into the DAARM hybrid application flow: • At design time spatially isolated mapping shapes are optimized • During run-time, shapes are mapped by fast heuristics or a exact SAT-mapper • Mapping time between microseconds (heuristics) and hundred of milliseconds (SAT) Folie 24

This work was supported by the German Research Foundation (DFG) as part of the Transregional Collaborative Re-search Center ”Invasive Computing” (SFB/TR 89). www. invasic. de Slide 25

Backup Slide 26

Slide 27

Slide 28

Slide 29

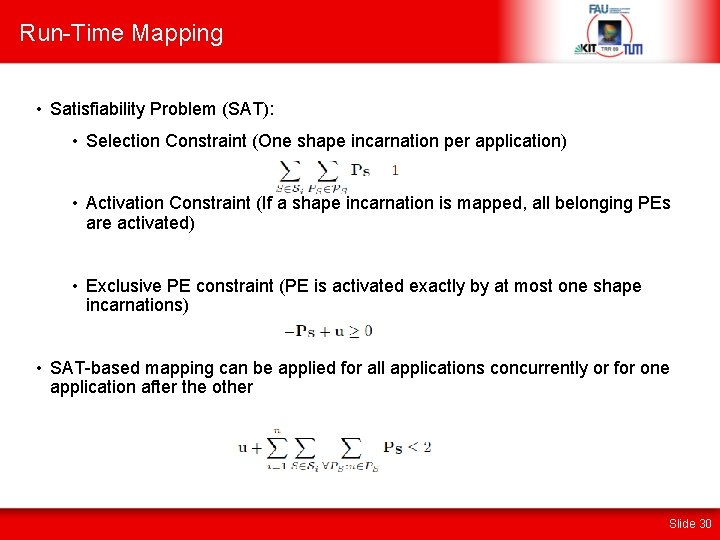
Run-Time Mapping • Satisfiability Problem (SAT): • Selection Constraint (One shape incarnation per application) • Activation Constraint (If a shape incarnation is mapped, all belonging PEs are activated) • Exclusive PE constraint (PE is activated exactly by at most one shape incarnations) • SAT-based mapping can be applied for all applications concurrently or for one application after the other Slide 30

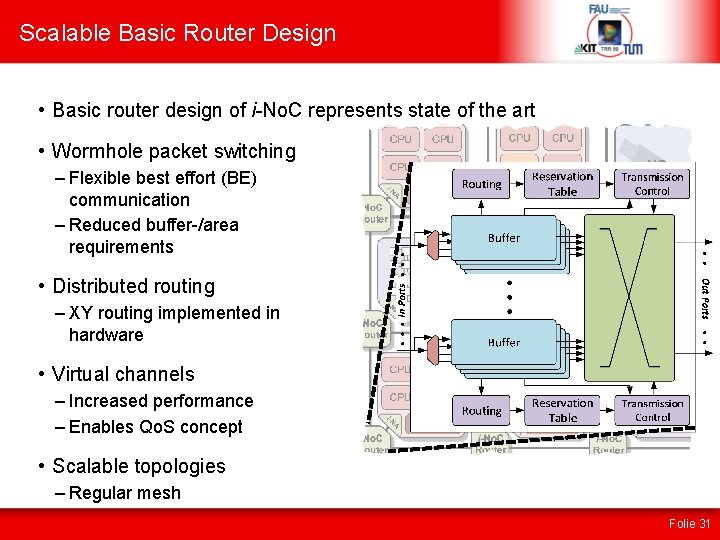
Scalable Basic Router Design • Basic router design of i-No. C represents state of the art • Wormhole packet switching – Flexible best effort (BE) communication – Reduced buffer-/area requirements • Distributed routing – XY routing implemented in hardware • Virtual channels – Increased performance – Enables Qo. S concept • Scalable topologies – Regular mesh Folie 31

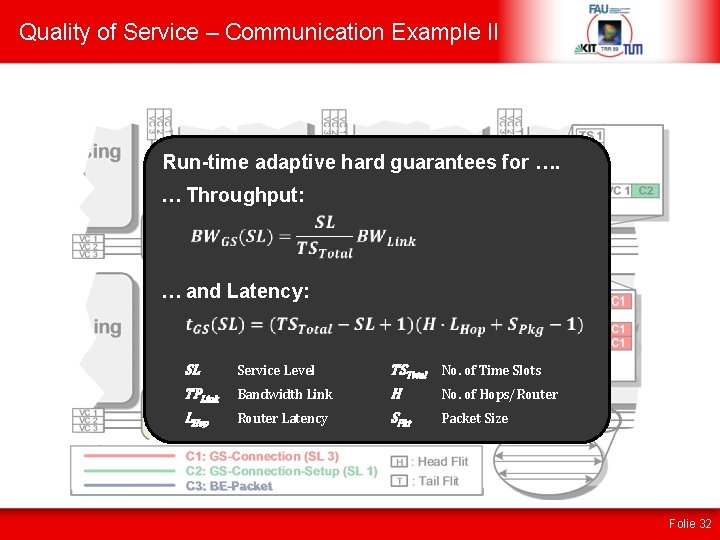
Quality of Service – Communication Example II Run-time adaptive hard guarantees for …. … Throughput: … and Latency: SL Service Level TSTotal No. of Time Slots TPLink Round-Robin Scheduling Bandwidth Link H No. of Hops/Router LHop Packet Size für Time Slots (TS) Router Latency SPkt Folie 32

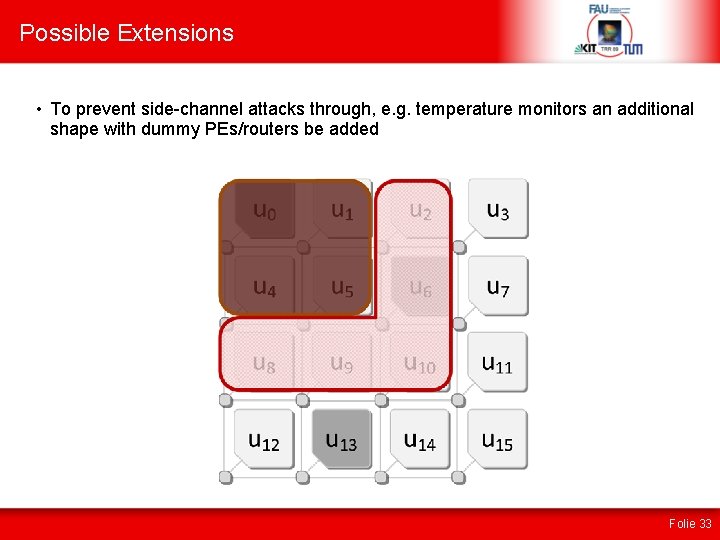
Possible Extensions • To prevent side-channel attacks through, e. g. temperature monitors an additional shape with dummy PEs/routers be added Folie 33

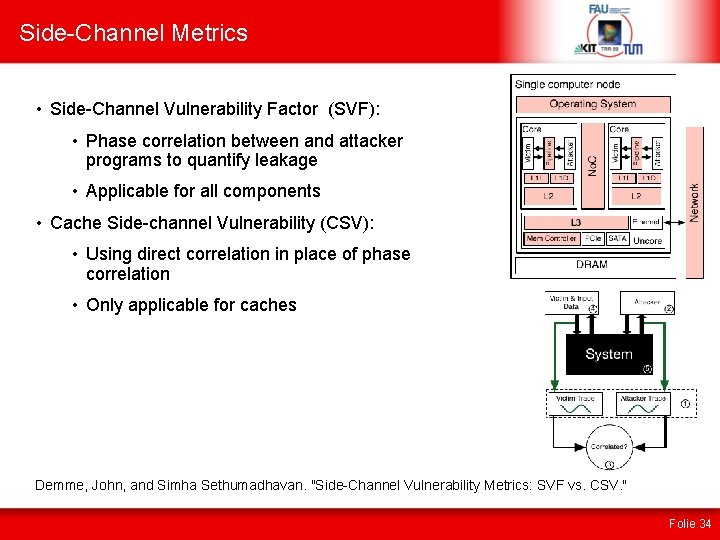
Side-Channel Metrics • Side-Channel Vulnerability Factor (SVF): • Phase correlation between and attacker programs to quantify leakage • Applicable for all components • Cache Side-channel Vulnerability (CSV): • Using direct correlation in place of phase correlation • Only applicable for caches Demme, John, and Simha Sethumadhavan. "Side-Channel Vulnerability Metrics: SVF vs. CSV. " Folie 34

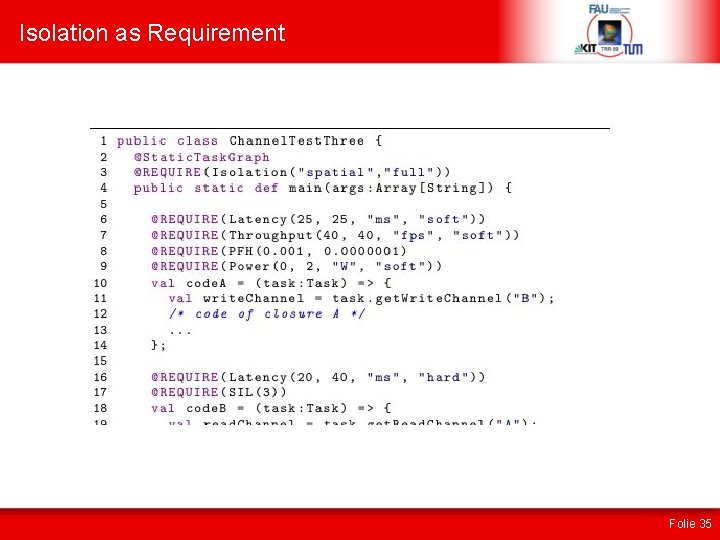
Isolation as Requirement Folie 35