Designing for Privacy and Personal Autonomy Privacy Live












- Slides: 31

Designing for Privacy and Personal Autonomy Privacy. Live Office of the Privacy Commissioner of New Zealand October 26, 2018 © 2018 Enterprivacy Consulting Group

R. Jason Cronk Principal Consultant Enterprivacy Consulting Group (US Based) Ø Ø Author of Strategic Privacy by Design 20 year background in Information Technology Ø Licensed lawyer in the U. S. Ø IAPP Fellow of Information Privacy CIPP/US, CIPM, CIPT 2

Why design for privacy? © 2018 Enterprivacy Consulting Group

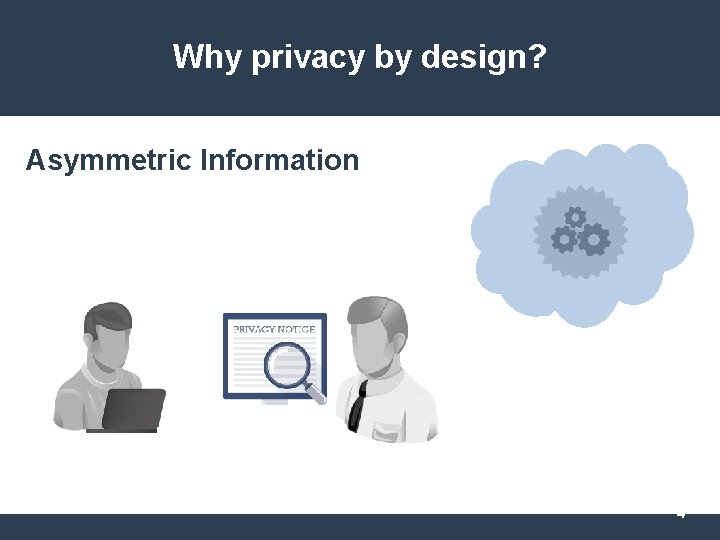
Why privacy by design? Asymmetric Information 4

Why privacy by design? Asymmetric Time Investment 5

Why privacy by design? Asymmetric Time Investment 6

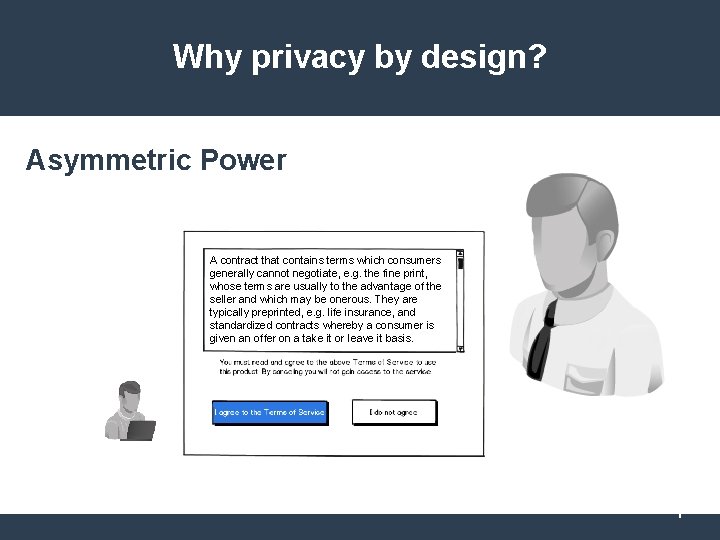
Why privacy by design? Asymmetric Power A contract that contains terms which consumers generally cannot negotiate, e. g. the fine print, whose terms are usually to the advantage of the seller and which may be onerous. They are typically preprinted, e. g. life insurance, and standardized contracts whereby a consumer is given an offer on a take it or leave it basis. 7

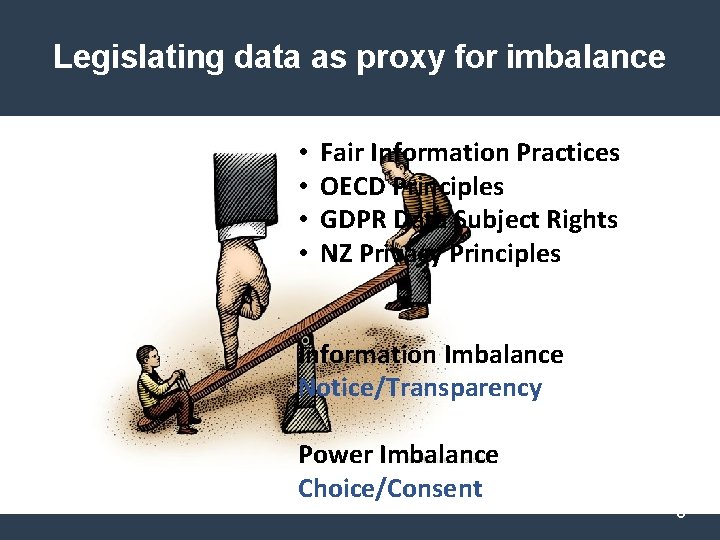
Legislating data as proxy for imbalance • • Fair Information Practices OECD Principles GDPR Data Subject Rights NZ Privacy Principles Information Imbalance Notice/Transparency Power Imbalance Choice/Consent 8

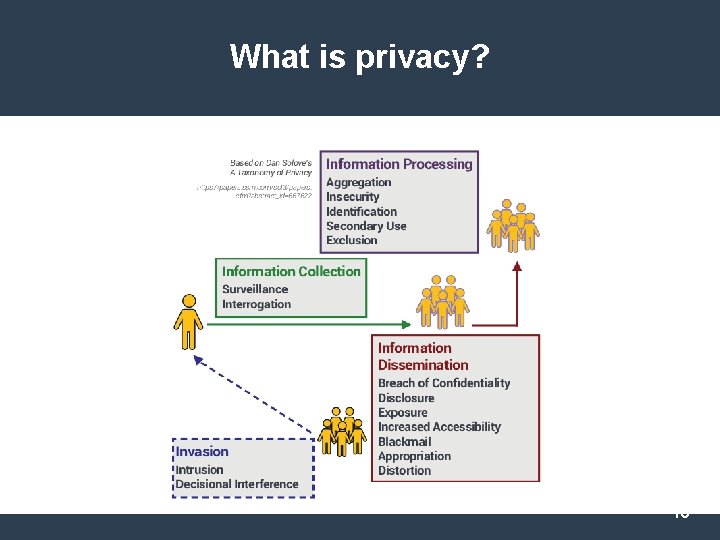
What is privacy? © 2018 Enterprivacy Consulting Group

What is privacy? 10

Information Collection Surveillance watching, listening to, or recording of an individual’s activities © 2018 Enterprivacy Consulting Group 11

Information Collection Interrogation questioning or probing for personal information 12

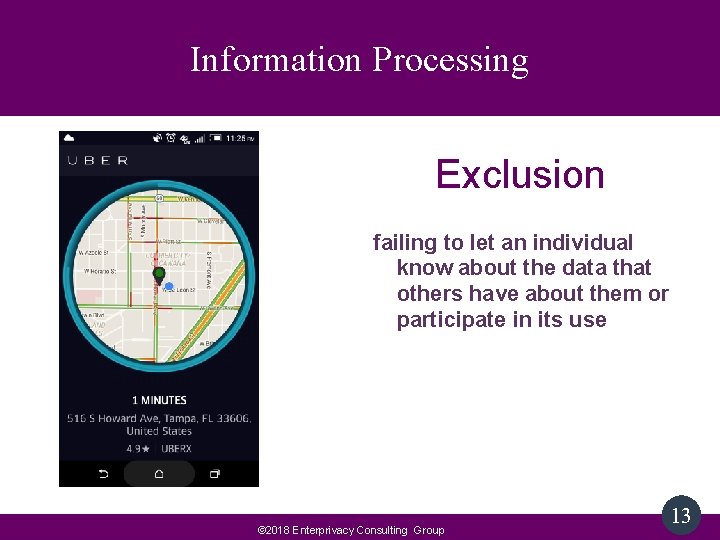
Information Processing Exclusion failing to let an individual know about the data that others have about them or participate in its use © 2018 Enterprivacy Consulting Group 13

Information Processing Secondary Use using personal information for a purpose other than for what is was collected © 2018 Enterprivacy Consulting Group 14

Information Dissemination Distortion disseminating false or misleading information about an individual 15

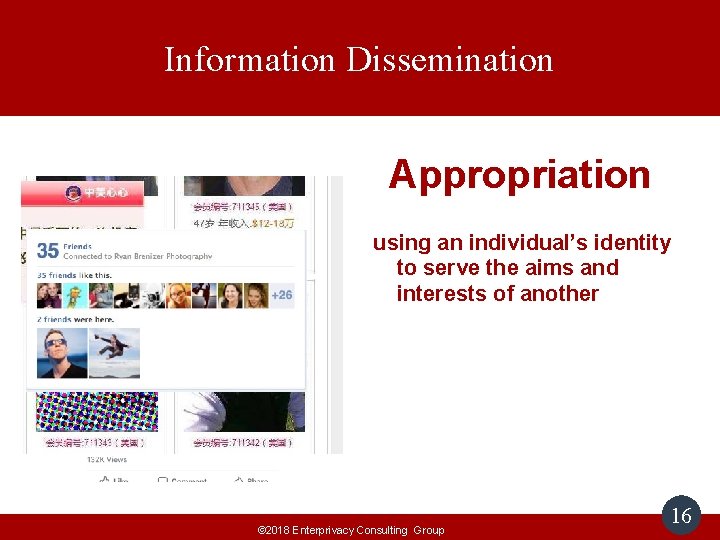
Information Dissemination Appropriation using an individual’s identity to serve the aims and interests of another © 2018 Enterprivacy Consulting Group 16

Invasion Intrusion disturbing an individual’s tranquility or solitude © 2018 Enterprivacy Consulting Group 17

Invasion Decisional Interference intruding into an individual’s decision making regarding their private affairs guilt, complaining, comparing, lying, denying (including excuses and rationalizations), feigning ignorance, or innocence (the “Who me? ” defense), blame, bribery, undermining, mind games, assumptions, “foot-in-the-door, ” reversals, emotional blackmail, evasiveness, forgetting, fake concern, sympathy, apologies, flattery, and gifts and favors. <Coercion-----Manipulation-------Persuasion> 18

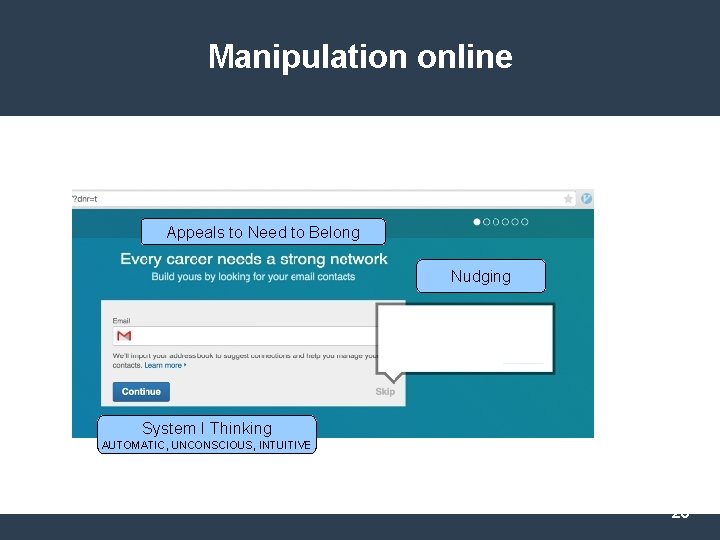
Manipulation online Exploit human psychology ● System I Thinking ● Need to belong to a social group ● Nudging (automatic, unconscious, intuitive) 19

Manipulation online Appeals to Need to Belong Nudging System I Thinking AUTOMATIC, UNCONSCIOUS, INTUITIVE 20

Privacy violations Researcher sharing of data with Cambridge Analytica (Breach of Confidentiality) Cambridge Analytica creating of psychographic profiles (Aggregation/Secondary Use/Exclusion) Manipulation of potential voters (Decisional Interference) 21 © 2018 Enterprivacy Consulting Group

How to design for privacy? ` © 2018 Enterprivacy Consulting Group

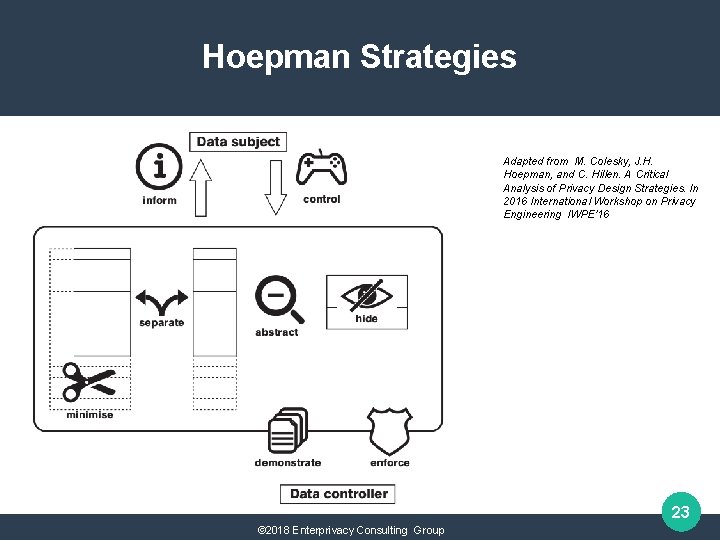
Hoepman Strategies Adapted from M. Colesky, J. H. Hoepman, and C. Hillen. A Critical Analysis of Privacy Design Strategies. In 2016 International Workshop on Privacy Engineering IWPE'16 23 © 2018 Enterprivacy Consulting Group

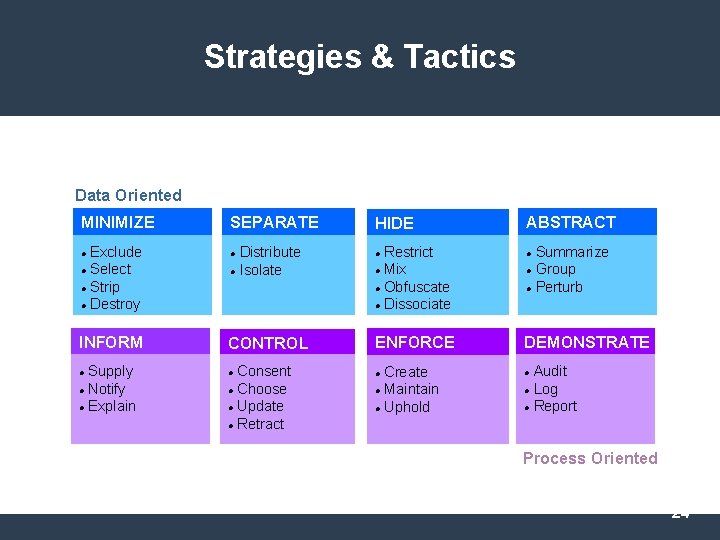
Strategies & Tactics Data Oriented MINIMIZE Exclude Select Strip Destroy INFORM Supply Notify Explain SEPARATE Distribute Isolate CONTROL Consent Choose Update Retract HIDE Restrict Mix Obfuscate Dissociate ABSTRACT Summarize Group Perturb ENFORCE DEMONSTRATE Create Maintain Uphold Audit Log Report Process Oriented 24

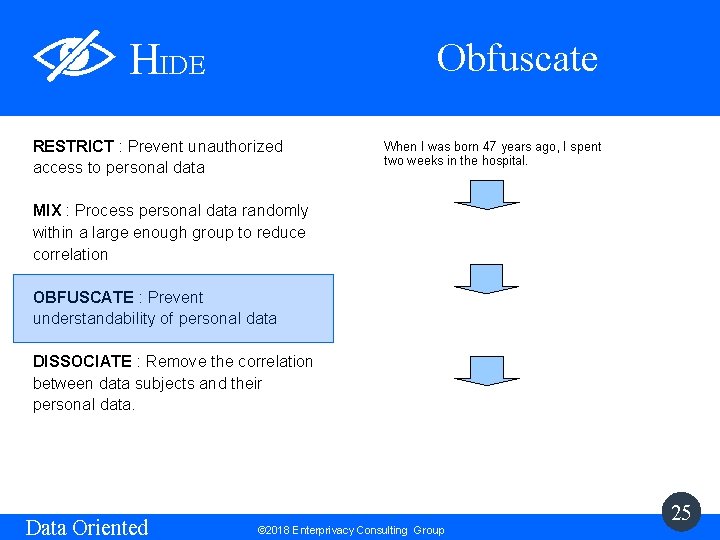
Obfuscate HIDE RESTRICT : Prevent unauthorized access to personal data When I was born 47 years ago, I spent two weeks in the hospital. MIX : Process personal data randomly within a large enough group to reduce correlation Two score and seven years heretofore, upon my nascency I remained in the sanitarium a fortnight. OBFUSCATE : Prevent understandability of personal data DISSOCIATE : Remove the correlation between data subjects and their personal data. Data Oriented ﻋﻠﻰ ، ﺍﺛﻨﻴﻦ ﻣﻦ ﺩﺭﺟﺔ ﻭﺳﺒﻊ ﺳﻨﻮﺍﺕ ﺣﺘﻰ ﺍﻵﻦ ﺑﻠﺪﻱ ﻧﻌﻤﺔ ﻇﻠﺖ ﻓﻲ ﺳﺎﻧﺘﺮﻳﻮﻡ ﺃﺴﺒﻮﻋﻴﻦ. 6 a 19700288 c 4 a 483 a 0 a 80 e 8812 d 4 bc 8086 d 45668 cbbc ef 4959133 b 421 efd 99306 aac 3 ba 3 f 4 a 6 f 6 cb 08 dfc 287 e 2 7 b 239312 ef 94411 e 755 d 6 c 22 a 3 d 369985 c 51 f 789 f 61 fa 4 af 79 f 3248 e 0535 b 494 f 5 dad 550 f 7 aa 03221 c 789 cf 7 c 0 f 2 3 e 34 c 5 f 94411 e 75 e © 2018 Enterprivacy Consulting Group 25

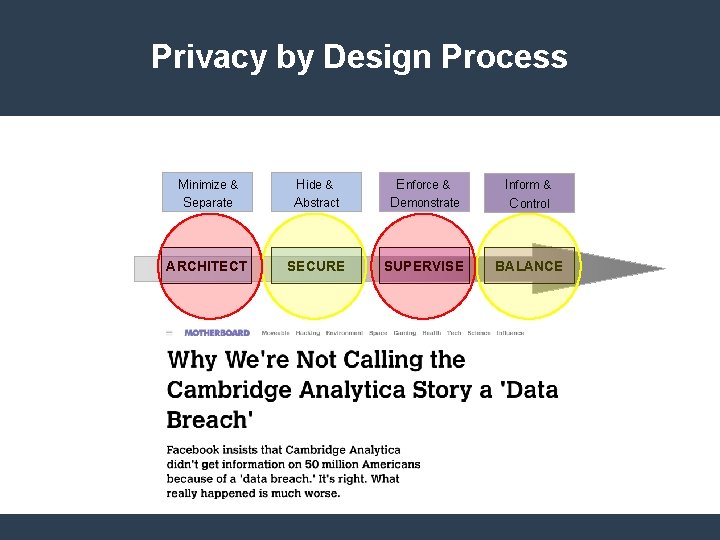
Privacy by Design Process Minimize & Separate Hide & Abstract Enforce & Demonstrate Inform & Control ARCHITECT SECURE SUPERVISE BALANCE “But, for the most part, technologists and firm lawyers thought about privacy in narrow ways, either as synonymous with encryption or limited to notice-and-choice. ” Prof. Ari Waldman

Privacy by Design Process ARCHITECT Persons Revenge, money, spite, curiosity, & control. SECURE SUPERVISE Governments BALANCE Organizations Law enforcement, Money, espionage, competitive control & advantage repression.

Trust “Brought to you by the most trusted personal info broker to ever testify before Congress” “Just say no to Facebook’s spy device. ” “Please don’t video monitor me Facebook”

Trust

Going to the gym

Thank You Thanks to 31 © 2018 Enterprivacy Consulting Group