Design and Modeling of Medium Access Control Protocols



![Wireless Ad Hoc Networks [IETF MANET] g Formed by wireless hosts (which may be Wireless Ad Hoc Networks [IETF MANET] g Formed by wireless hosts (which may be](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-4.jpg)




![Hidden Terminal Problem [Tobagi 75] g g Node B can communicate with A and Hidden Terminal Problem [Tobagi 75] g g Node B can communicate with A and](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-17.jpg)
![Busy Tone [Tobagi 75, Haas 98] g A receiver transmits busy tone when receiving Busy Tone [Tobagi 75, Haas 98] g A receiver transmits busy tone when receiving](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-18.jpg)
![MACA Solution for Hidden Terminal Problem [Karn 90] g When node A wants to MACA Solution for Hidden Terminal Problem [Karn 90] g When node A wants to](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-19.jpg)


![MILD Algorithm in MACAW [Bharghavan 94] g When a node successfully completes a transfer, MILD Algorithm in MACAW [Bharghavan 94] g When a node successfully completes a transfer,](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-37.jpg)
![Alternative Contention Resolution Mechanism [Hiperlan] g Elimination phase i. A node transmits a burst Alternative Contention Resolution Mechanism [Hiperlan] g Elimination phase i. A node transmits a burst](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-38.jpg)
![Receive-Initiated Mechanism [Talucci 97, Garcia 99] g In most protocols, sender initiates a transfer Receive-Initiated Mechanism [Talucci 97, Garcia 99] g In most protocols, sender initiates a transfer](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-39.jpg)

![Weighted Fair Queueing [Keshav 97 book] g Assign a weight to each node g Weighted Fair Queueing [Keshav 97 book] g Assign a weight to each node g](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-47.jpg)
![Distributed Fair Scheduling (DFS) [Vaidya 00 Mobicom] g A fully distributed algorithm for achieving Distributed Fair Scheduling (DFS) [Vaidya 00 Mobicom] g A fully distributed algorithm for achieving](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-48.jpg)


![Balanced MAC [Ozugur 98] g Variation on p-persistent protocol g A link access probability Balanced MAC [Ozugur 98] g Variation on p-persistent protocol g A link access probability](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-55.jpg)

![Estimation-Based Fair MAC [Bansou 00 Mobi. Hoc] g Attempts to equalize throughput/weight ratio for Estimation-Based Fair MAC [Bansou 00 Mobi. Hoc] g Attempts to equalize throughput/weight ratio for](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-59.jpg)

![Proportional Fair Contention Resolution (PFCR) [Nandagopal 00 Mobicom] g Proportional fairness: Allocate bandwidth Ri Proportional Fair Contention Resolution (PFCR) [Nandagopal 00 Mobicom] g Proportional fairness: Allocate bandwidth Ri](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-62.jpg)


![Variation in Backoff Interval [Aad 01] g For high priority packets g For low Variation in Backoff Interval [Aad 01] g For high priority packets g For low](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-68.jpg)
![Second Mechanism [Aad 01] g High priority packets always choose backoff in [0, CWh] Second Mechanism [Aad 01] g High priority packets always choose backoff in [0, CWh]](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-70.jpg)

![Priority Using Black Bursts [Hiperlan/1, Sobrinho 96, 99] g All nodes begin the priority Priority Using Black Bursts [Hiperlan/1, Sobrinho 96, 99] g All nodes begin the priority](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-73.jpg)

![Power Aware Multi-Access Protocol (PAMAS) [Singh 98] g A node powers off its radio Power Aware Multi-Access Protocol (PAMAS) [Singh 98] g A node powers off its radio](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-76.jpg)






![Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-96.jpg)
![Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-97.jpg)
![Small Addresses Save Energy [Schurgers 01 mobihoc] g In sensor networks, packet sizes are Small Addresses Save Energy [Schurgers 01 mobihoc] g In sensor networks, packet sizes are](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-99.jpg)


![Sender-Based “Autorate Fallback” [Kamerman 97] g Probing mechanisms g Sender decreases bit rate after Sender-Based “Autorate Fallback” [Kamerman 97] g Probing mechanisms g Sender decreases bit rate after](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-104.jpg)
![Receiver-Based Autorate MAC [Holland 01 mobicom] g Sender sends RTS containing its best rate Receiver-Based Autorate MAC [Holland 01 mobicom] g Sender sends RTS containing its best rate](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-106.jpg)

![Directional Carrier Sensing [Takai 02 mobihoc, Roychoudhury 02 tech] g Physical carrier sensing similar Directional Carrier Sensing [Takai 02 mobihoc, Roychoudhury 02 tech] g Physical carrier sensing similar](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-122.jpg)
![Exploiting Larger Range of Directional Antennas [Roychoudhury 02 tech] D C A g B Exploiting Larger Range of Directional Antennas [Roychoudhury 02 tech] D C A g B](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-123.jpg)

![Multi-Channel MAC with Soft Reservation [Nasipuri 00] g Similar to the simple scheme, channel Multi-Channel MAC with Soft Reservation [Nasipuri 00] g Similar to the simple scheme, channel](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-129.jpg)



- Slides: 134

Design and Modeling of Medium Access Control Protocols for Wireless Ad Hoc Networks Part 1: Nitin Vaidya Part 2: Rajive Bagrodia & Mineo Takai Mobi. Hoc 2002 Tutorial © 2002 1

Part 1 2 (c) 2002 Nitin Vaidya, UIUC

Design of Medium Access Control Protocols for Wireless Ad Hoc Networks Nitin H. Vaidya University of Illinois at Urbana-Champaign nhv@uiuc. edu http: //www. crhc. uiuc. edu/~nhv © 2002 Nitin Vaidya 3
![Wireless Ad Hoc Networks IETF MANET g Formed by wireless hosts which may be Wireless Ad Hoc Networks [IETF MANET] g Formed by wireless hosts (which may be](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-4.jpg)
Wireless Ad Hoc Networks [IETF MANET] g Formed by wireless hosts (which may be mobile) g Without (necessarily) using a pre-existing infrastructure g Routes between nodes may potentially contain multiple hops i. Ad hoc does not necessarily mean multi-hop, but research literature typically equates ad hoc with multi-hop 4 (c) 2002 Nitin Vaidya, UIUC

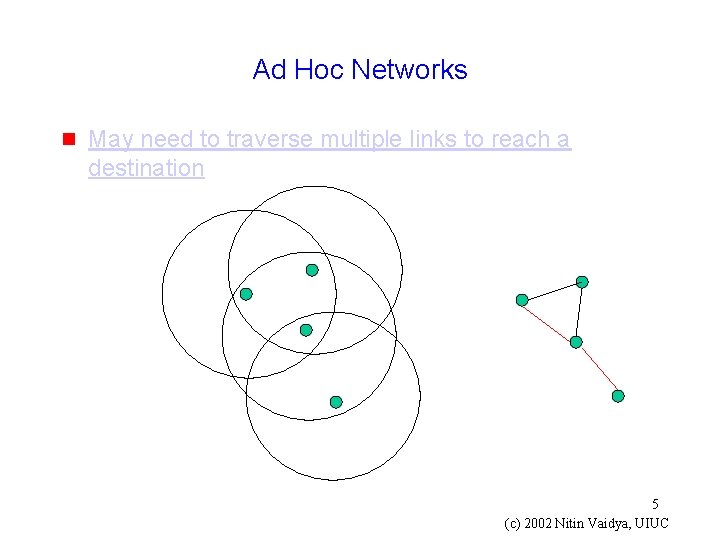
Ad Hoc Networks g May need to traverse multiple links to reach a destination 5 (c) 2002 Nitin Vaidya, UIUC

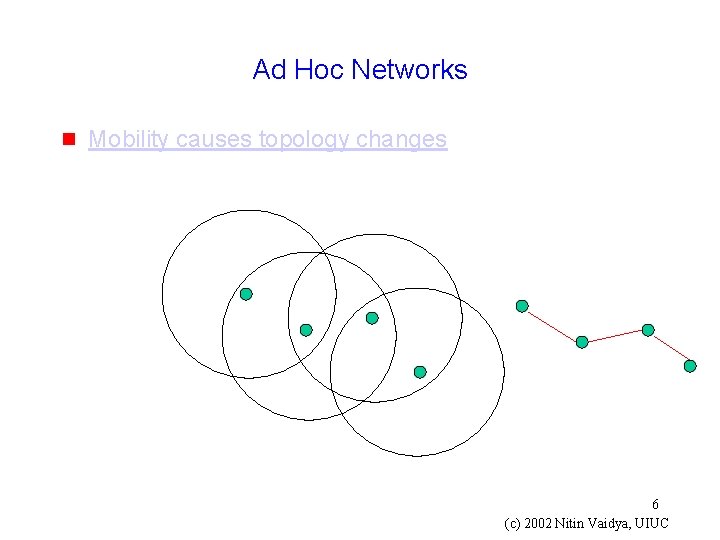
Ad Hoc Networks g Mobility causes topology changes 6 (c) 2002 Nitin Vaidya, UIUC

Why Ad Hoc Networks ? g Ease of deployment g Speed of deployment g Decreased dependence on infrastructure 7 (c) 2002 Nitin Vaidya, UIUC

Many Applications g Personal area networking g Military environments g Civilian environments g Emergency operations icell phone, laptop, ear phone, wrist watch isoldiers, tanks, planes itaxi cab network imeeting rooms isports stadiums iboats, small aircraft isearch-and-rescue ipolicing and fire fighting 8 (c) 2002 Nitin Vaidya, UIUC

Many Variations g Fully Symmetric Environment g Asymmetric Capabilities g Asymmetric Responsibilities iall nodes have identical capabilities and responsibilities itransmission ranges and radios may differ ibattery life at different nodes may differ iprocessing capacity may be different at different nodes ispeed of movement ionly some nodes may route packets isome nodes may act as leaders of nearby nodes (e. g. , cluster head) 9 (c) 2002 Nitin Vaidya, UIUC

Many Variations g Traffic characteristics may differ in different ad hoc networks ibit rate itimeliness constraints ireliability requirements iunicast / multicast / geocast ihost-based addressing / content-based addressing / capability-based addressing g May co-exist (and co-operate) with an infrastructurebased network 10 (c) 2002 Nitin Vaidya, UIUC

Many Variations g Mobility patterns may be different g Mobility characteristics ipeople sitting at an airport lounge i. New York taxi cabs ikids playing imilitary movements ipersonal area network ispeed ipredictability • direction of movement • pattern of movement iuniformity (or lack thereof) of mobility characteristics among different nodes 11 (c) 2002 Nitin Vaidya, UIUC

Some Challenges g g g Limited wireless transmission range Broadcast nature of the wireless medium Packet losses due to transmission errors Host mobility Battery constraints Ease of snooping on wireless transmissions (security hazard) 12 (c) 2002 Nitin Vaidya, UIUC

Research on Ad Hoc Networks Variations in capabilities & responsibilities X Variations in traffic characteristics, mobility models, etc. X Performance criteria (e. g. , optimize throughput, reduce energy consumption) + Research funding = Significant research activity 13 (c) 2002 Nitin Vaidya, UIUC

Medium Access Control g Wireless channel is a shared medium g Need access control mechanism to avoid interference g MAC protocol design has been an active area of research for many years [Chandra 00 survey] 14 (c) 2002 Nitin Vaidya, UIUC

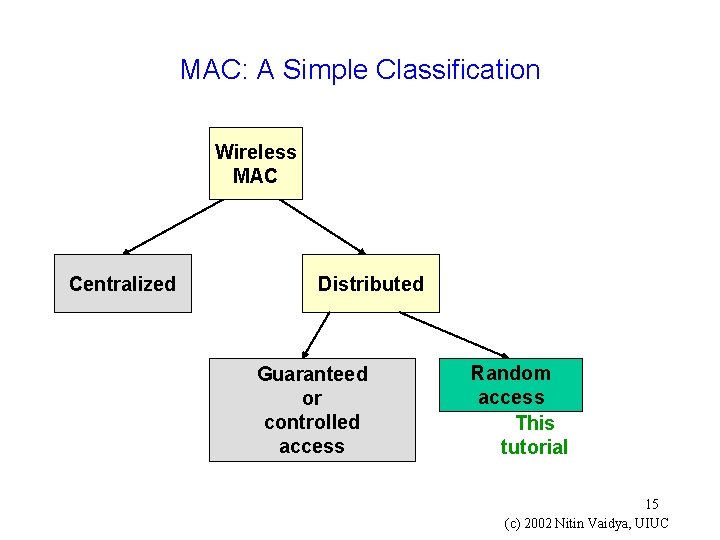
MAC: A Simple Classification Wireless MAC Centralized Distributed Guaranteed or controlled access Random access This tutorial 15 (c) 2002 Nitin Vaidya, UIUC

This tutorial g Mostly focus on random access protocols g Not a comprehensive overview of MAC protocols g Provides discussion of some example protocols (mostly from relatively recent literature) 16 (c) 2002 Nitin Vaidya, UIUC
![Hidden Terminal Problem Tobagi 75 g g Node B can communicate with A and Hidden Terminal Problem [Tobagi 75] g g Node B can communicate with A and](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-17.jpg)
Hidden Terminal Problem [Tobagi 75] g g Node B can communicate with A and C both A and C cannot hear each other When A transmits to B, C cannot detect the transmission using the carrier sense mechanism If C transmits, collision will occur at node B A B C 17 (c) 2002 Nitin Vaidya, UIUC
![Busy Tone Tobagi 75 Haas 98 g A receiver transmits busy tone when receiving Busy Tone [Tobagi 75, Haas 98] g A receiver transmits busy tone when receiving](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-18.jpg)
Busy Tone [Tobagi 75, Haas 98] g A receiver transmits busy tone when receiving data g All nodes hearing busy tone keep silent g Avoids interference from hidden terminals g Requires a separate channel for busy tone 18 (c) 2002 Nitin Vaidya, UIUC
![MACA Solution for Hidden Terminal Problem Karn 90 g When node A wants to MACA Solution for Hidden Terminal Problem [Karn 90] g When node A wants to](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-19.jpg)
MACA Solution for Hidden Terminal Problem [Karn 90] g When node A wants to send a packet to node B, node A first sends a Request-to-Send (RTS) to A g On receiving RTS, node A responds by sending Clear -to-Send (CTS), provided node A is able to receive the packet g When a node (such as C) overhears a CTS, it keeps quiet for the duration of the transfer i. Transfer duration is included in RTS and CTS both A B C 19 (c) 2002 Nitin Vaidya, UIUC

Reliability g Wireless links are prone to errors. High packet loss rate detrimental to transport-layer performance. g Mechanisms needed to reduce packet loss rate experienced by upper layers 20 (c) 2002 Nitin Vaidya, UIUC

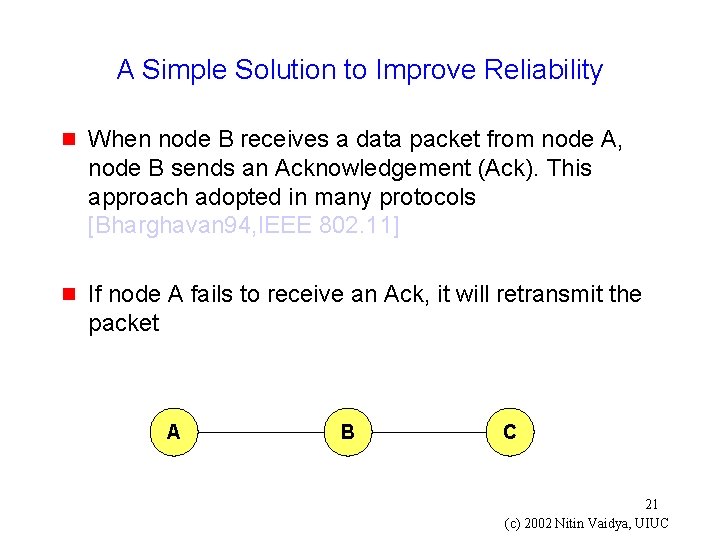
A Simple Solution to Improve Reliability g When node B receives a data packet from node A, node B sends an Acknowledgement (Ack). This approach adopted in many protocols [Bharghavan 94, IEEE 802. 11] g If node A fails to receive an Ack, it will retransmit the packet A B C 21 (c) 2002 Nitin Vaidya, UIUC

IEEE 802. 11 Wireless MAC g Distributed and centralized MAC components i. Distributed Coordination Function (DCF) i. Point Coordination Function (PCF) g DCF suitable for multi-hop ad hoc networking g DCF is a Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA) protocol 22 (c) 2002 Nitin Vaidya, UIUC

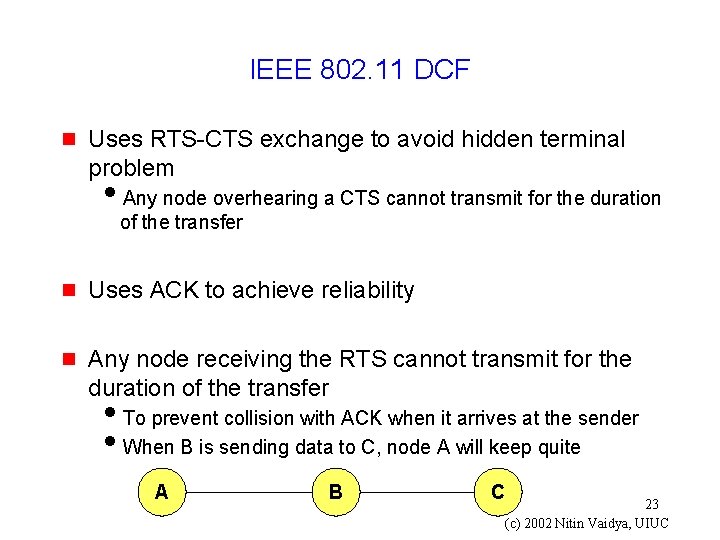
IEEE 802. 11 DCF g Uses RTS-CTS exchange to avoid hidden terminal problem i. Any node overhearing a CTS cannot transmit for the duration of the transfer g Uses ACK to achieve reliability g Any node receiving the RTS cannot transmit for the duration of the transfer i. To prevent collision with ACK when it arrives at the sender i. When B is sending data to C, node A will keep quite A B C 23 (c) 2002 Nitin Vaidya, UIUC

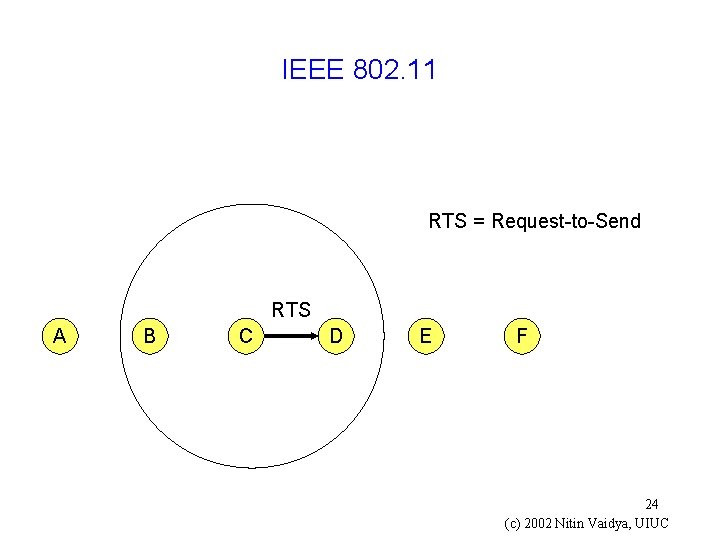
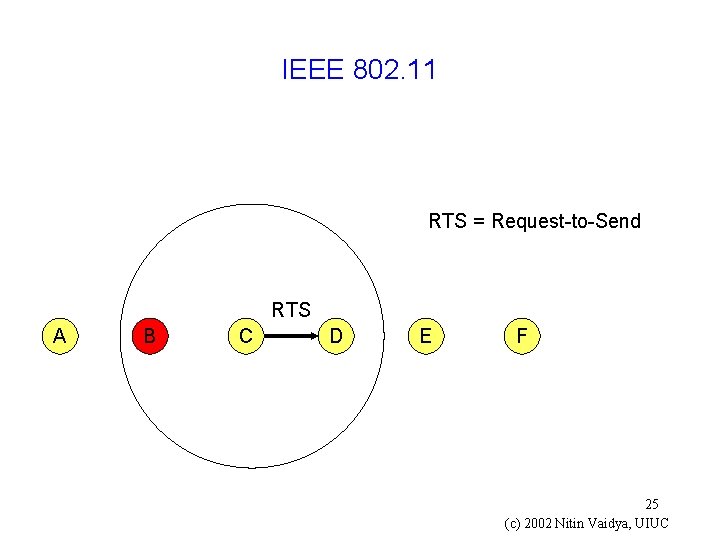
IEEE 802. 11 RTS = Request-to-Send RTS A B C D E F 24 (c) 2002 Nitin Vaidya, UIUC

IEEE 802. 11 RTS = Request-to-Send RTS A B C D E F 25 (c) 2002 Nitin Vaidya, UIUC

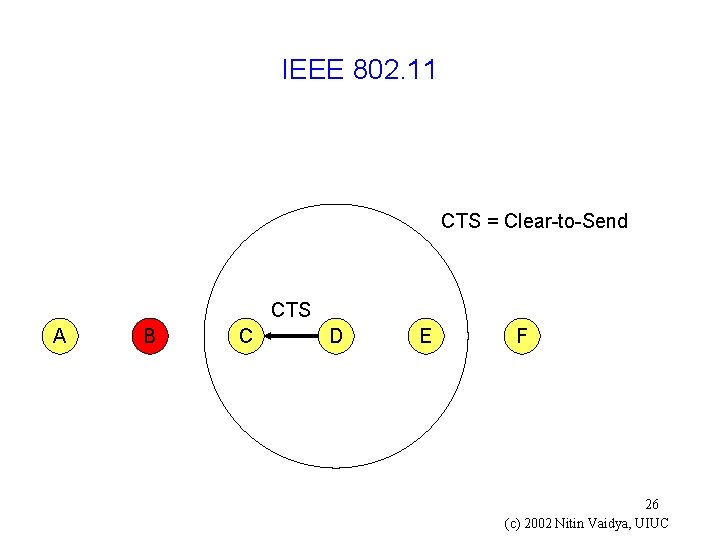
IEEE 802. 11 CTS = Clear-to-Send CTS A B C D E F 26 (c) 2002 Nitin Vaidya, UIUC

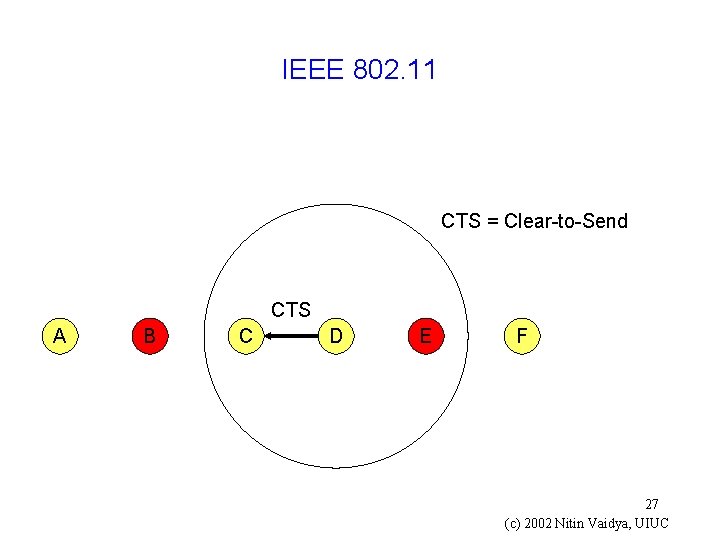
IEEE 802. 11 CTS = Clear-to-Send CTS A B C D E F 27 (c) 2002 Nitin Vaidya, UIUC

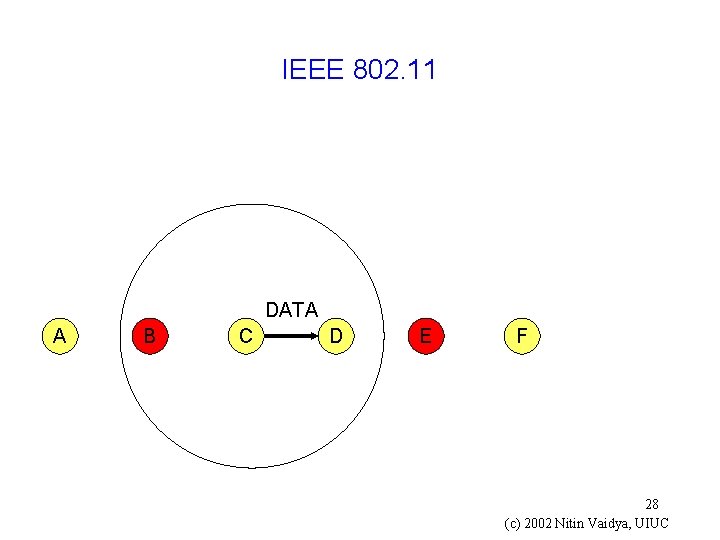
IEEE 802. 11 DATA A B C D E F 28 (c) 2002 Nitin Vaidya, UIUC

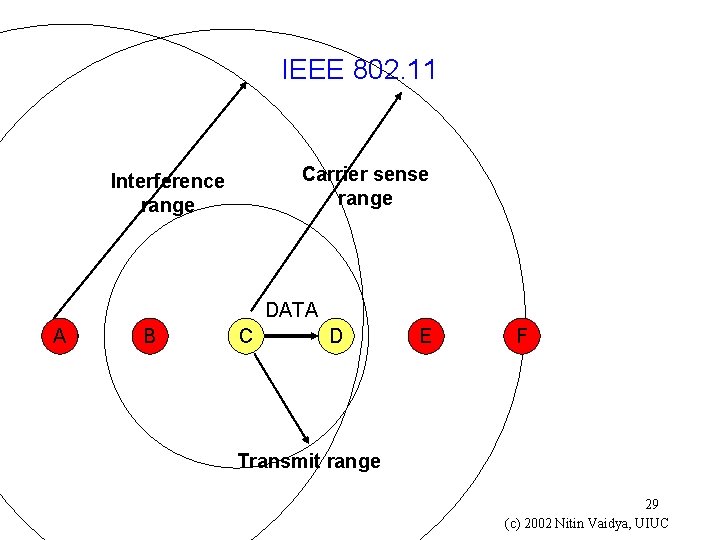
IEEE 802. 11 Carrier sense range Interference range DATA A B C D E F Transmit range 29 (c) 2002 Nitin Vaidya, UIUC

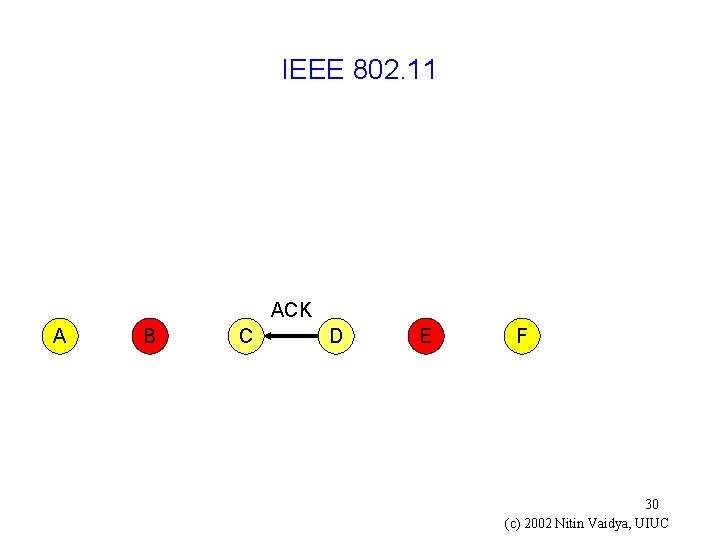
IEEE 802. 11 ACK A B C D E F 30 (c) 2002 Nitin Vaidya, UIUC

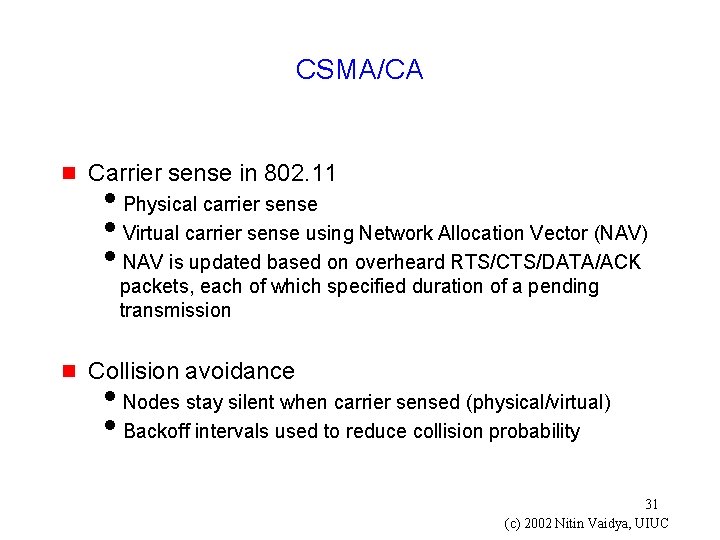
CSMA/CA g Carrier sense in 802. 11 i. Physical carrier sense i. Virtual carrier sense using Network Allocation Vector (NAV) i. NAV is updated based on overheard RTS/CTS/DATA/ACK packets, each of which specified duration of a pending transmission g Collision avoidance i. Nodes stay silent when carrier sensed (physical/virtual) i. Backoff intervals used to reduce collision probability 31 (c) 2002 Nitin Vaidya, UIUC

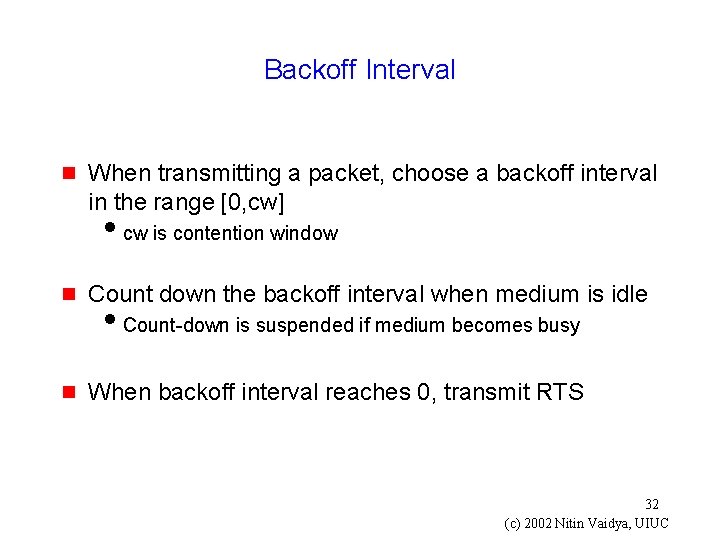
Backoff Interval g When transmitting a packet, choose a backoff interval in the range [0, cw] icw is contention window g Count down the backoff interval when medium is idle g When backoff interval reaches 0, transmit RTS i. Count-down is suspended if medium becomes busy 32 (c) 2002 Nitin Vaidya, UIUC

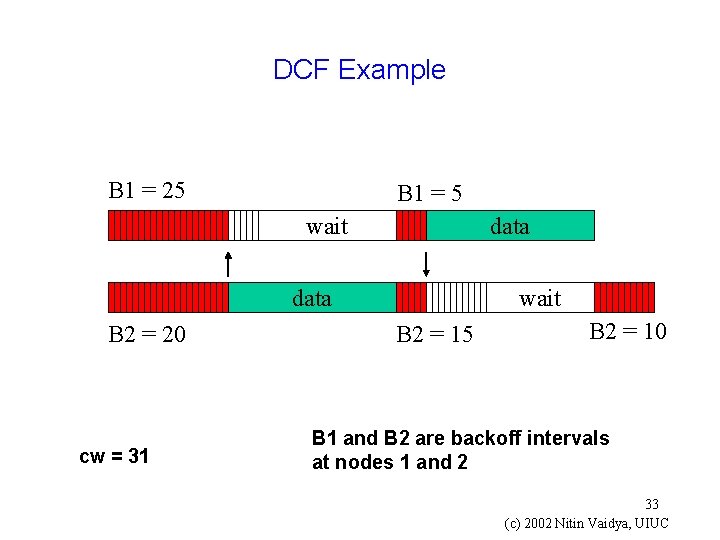
DCF Example B 1 = 25 B 1 = 5 wait data B 2 = 20 cw = 31 wait B 2 = 15 B 2 = 10 B 1 and B 2 are backoff intervals at nodes 1 and 2 33 (c) 2002 Nitin Vaidya, UIUC

Backoff Interval g The time spent counting down backoff intervals is a part of MAC overhead g Choosing a large cw leads to large backoff intervals and can result in larger overhead g Choosing a small cw leads to a larger number of collisions (when two nodes count down to 0 simultaneously) 34 (c) 2002 Nitin Vaidya, UIUC

g Since the number of nodes attempting to transmit simultaneously may change with time, some mechanism to manage contention is needed g IEEE 802. 11 DCF: contention window cw is chosen dynamically depending on collision occurrence 35 (c) 2002 Nitin Vaidya, UIUC

Binary Exponential Backoff in DCF g When a node fails to receive CTS in response to its RTS, it increases the contention window icw is doubled (up to an upper bound) g When a node successfully completes a data transfer, it restores cw to Cwmin g cw follows a sawtooth curve 36 (c) 2002 Nitin Vaidya, UIUC
![MILD Algorithm in MACAW Bharghavan 94 g When a node successfully completes a transfer MILD Algorithm in MACAW [Bharghavan 94] g When a node successfully completes a transfer,](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-37.jpg)
MILD Algorithm in MACAW [Bharghavan 94] g When a node successfully completes a transfer, reduces cw by 1 i. In 802. 11 cw is restored to cwmin i. In 802. 11, cw reduces much faster than it increases i. MACAW: cw reduces slower than it increases Exponential Increase Linear Decrease g MACAW can avoid wild oscillations of cw when large number of nodes contend for the channel 37 (c) 2002 Nitin Vaidya, UIUC
![Alternative Contention Resolution Mechanism Hiperlan g Elimination phase i A node transmits a burst Alternative Contention Resolution Mechanism [Hiperlan] g Elimination phase i. A node transmits a burst](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-38.jpg)
Alternative Contention Resolution Mechanism [Hiperlan] g Elimination phase i. A node transmits a burst for a random number (geometrically distributed) of slots i. If medium idle at the end of the burst, go to yield phase, else give up until next round g Yield phase i. Stay silent for a random number (geometrical distributed) of slots i. If medium still silent, transmit 38 (c) 2002 Nitin Vaidya, UIUC
![ReceiveInitiated Mechanism Talucci 97 Garcia 99 g In most protocols sender initiates a transfer Receive-Initiated Mechanism [Talucci 97, Garcia 99] g In most protocols, sender initiates a transfer](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-39.jpg)
Receive-Initiated Mechanism [Talucci 97, Garcia 99] g In most protocols, sender initiates a transfer g Alternatively, a receiver may send a Ready-To-Receive (RTR) message to a sender requesting it to being a packet transfer g Sender node on receiving the RTR transmits data g How does a receiver determine when to poll a sender with RTR? i. Based on history, and prediction of traffic from the sender 39 (c) 2002 Nitin Vaidya, UIUC

Fairness 40 (c) 2002 Nitin Vaidya, UIUC

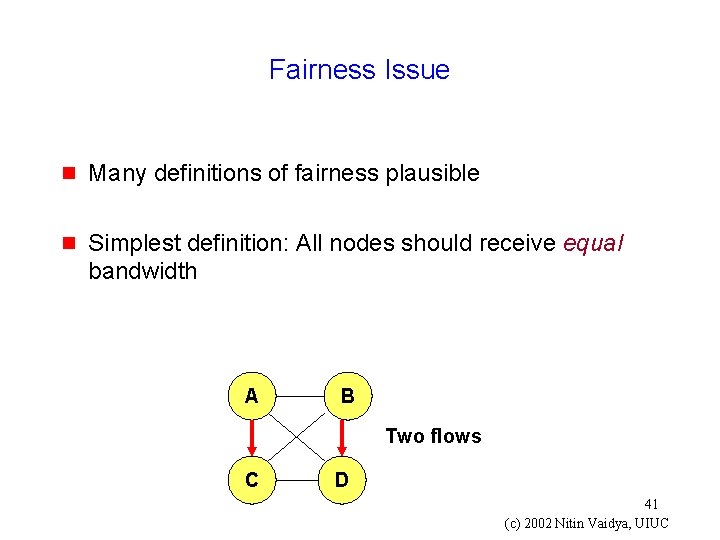
Fairness Issue g Many definitions of fairness plausible g Simplest definition: All nodes should receive equal bandwidth A B Two flows C D 41 (c) 2002 Nitin Vaidya, UIUC

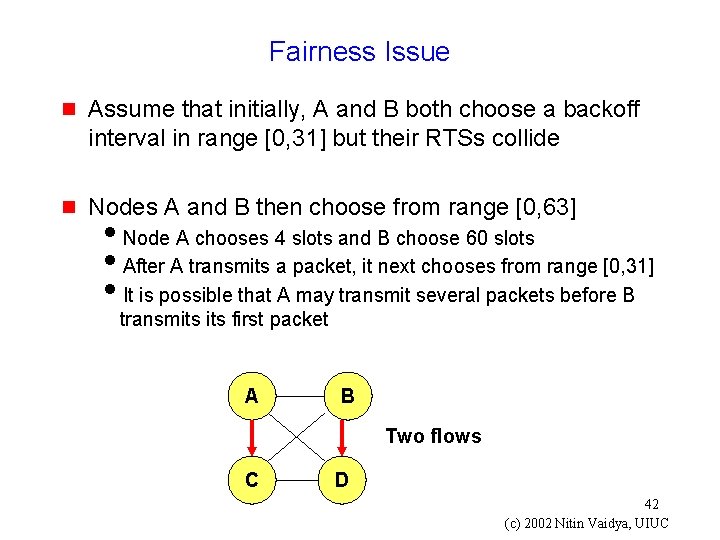
Fairness Issue g Assume that initially, A and B both choose a backoff interval in range [0, 31] but their RTSs collide g Nodes A and B then choose from range [0, 63] i. Node A chooses 4 slots and B choose 60 slots i. After A transmits a packet, it next chooses from range [0, 31] i. It is possible that A may transmit several packets before B transmits first packet A B Two flows C D 42 (c) 2002 Nitin Vaidya, UIUC

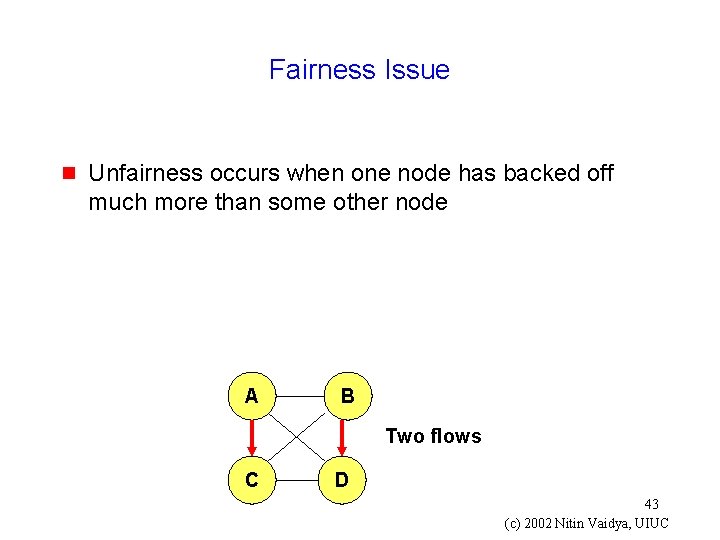
Fairness Issue g Unfairness occurs when one node has backed off much more than some other node A B Two flows C D 43 (c) 2002 Nitin Vaidya, UIUC

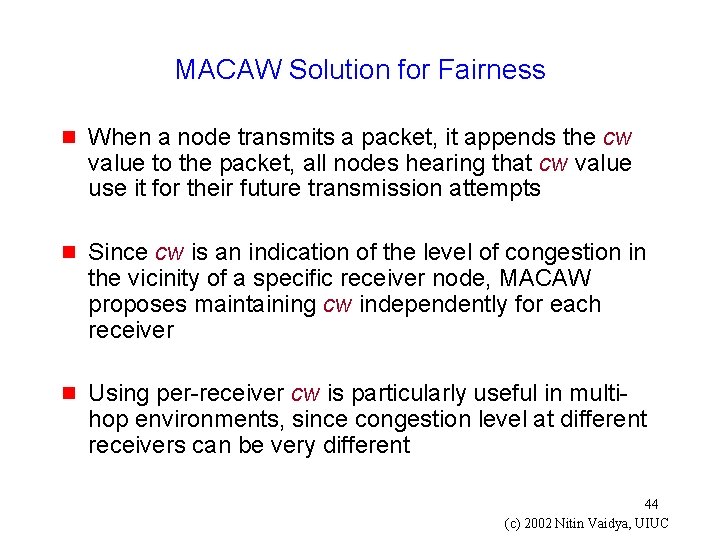
MACAW Solution for Fairness g When a node transmits a packet, it appends the cw value to the packet, all nodes hearing that cw value use it for their future transmission attempts g Since cw is an indication of the level of congestion in the vicinity of a specific receiver node, MACAW proposes maintaining cw independently for each receiver g Using per-receiver cw is particularly useful in multihop environments, since congestion level at different receivers can be very different 44 (c) 2002 Nitin Vaidya, UIUC

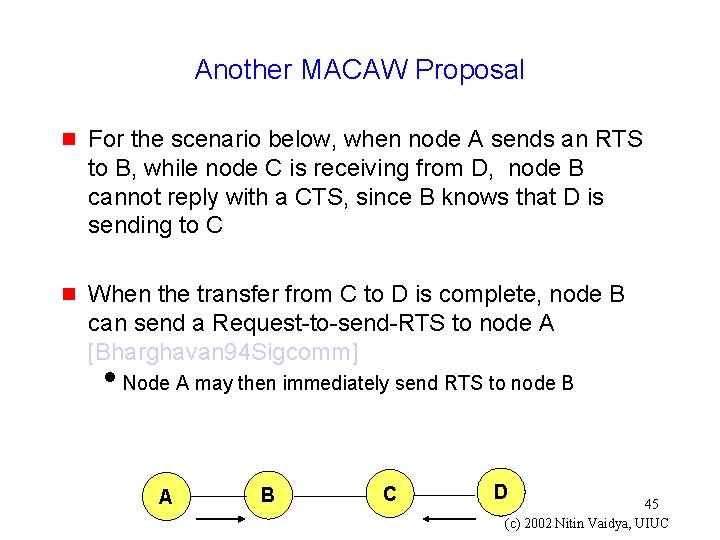
Another MACAW Proposal g For the scenario below, when node A sends an RTS to B, while node C is receiving from D, node B cannot reply with a CTS, since B knows that D is sending to C g When the transfer from C to D is complete, node B can send a Request-to-send-RTS to node A [Bharghavan 94 Sigcomm] i. Node A may then immediately send RTS to node B A B C D 45 (c) 2002 Nitin Vaidya, UIUC

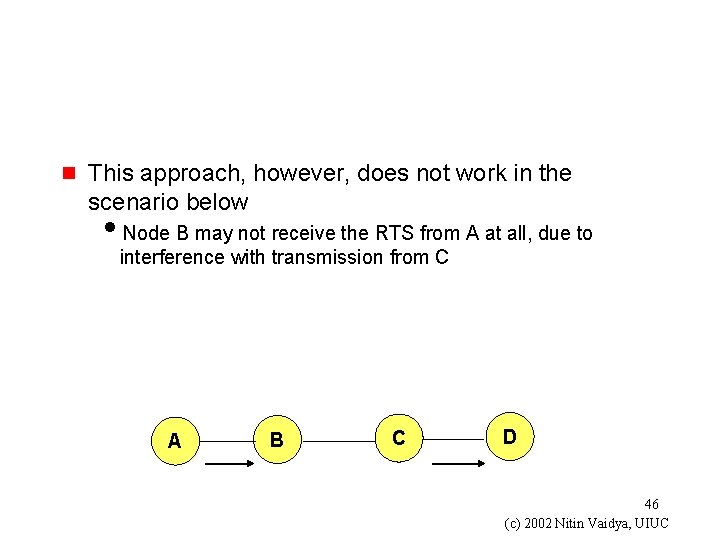
g This approach, however, does not work in the scenario below i. Node B may not receive the RTS from A at all, due to interference with transmission from C A B C D 46 (c) 2002 Nitin Vaidya, UIUC
![Weighted Fair Queueing Keshav 97 book g Assign a weight to each node g Weighted Fair Queueing [Keshav 97 book] g Assign a weight to each node g](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-47.jpg)
Weighted Fair Queueing [Keshav 97 book] g Assign a weight to each node g Bandwidth used by each node should be proportional to the weight assigned to the node 47 (c) 2002 Nitin Vaidya, UIUC
![Distributed Fair Scheduling DFS Vaidya 00 Mobicom g A fully distributed algorithm for achieving Distributed Fair Scheduling (DFS) [Vaidya 00 Mobicom] g A fully distributed algorithm for achieving](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-48.jpg)
Distributed Fair Scheduling (DFS) [Vaidya 00 Mobicom] g A fully distributed algorithm for achieving weighted fair queueing g Chooses backoff intervals proportional to (packet size / weight) g DFS attempts to mimic the centralized Self-Clocked Fair Queueing algorithm [Golestani] g Works well on a LAN 48 (c) 2002 Nitin Vaidya, UIUC

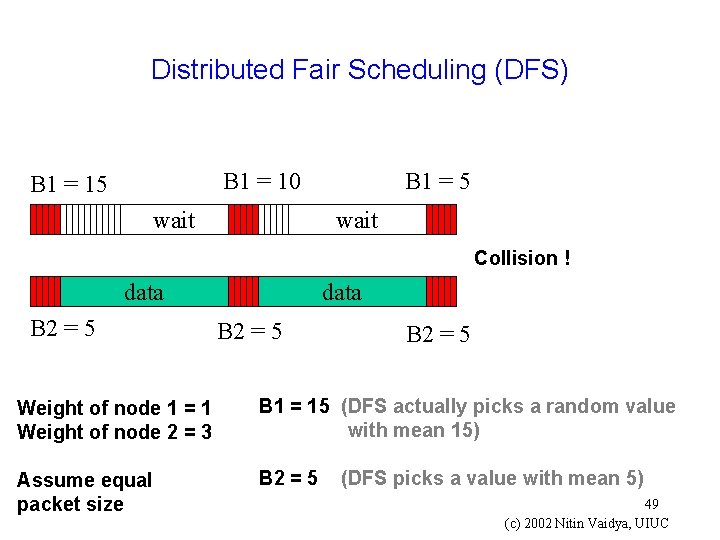
Distributed Fair Scheduling (DFS) B 1 = 5 B 1 = 10 B 1 = 15 wait Collision ! data B 2 = 5 Weight of node 1 = 1 Weight of node 2 = 3 B 1 = 15 (DFS actually picks a random value with mean 15) Assume equal packet size B 2 = 5 (DFS picks a value with mean 5) 49 (c) 2002 Nitin Vaidya, UIUC

Impact of Collisions g After collision resolution, either node 1 or node 2 may transmit a packet g The two alternatives may have different fairness properties (since collision resolution can result in priority inversion) 50 (c) 2002 Nitin Vaidya, UIUC

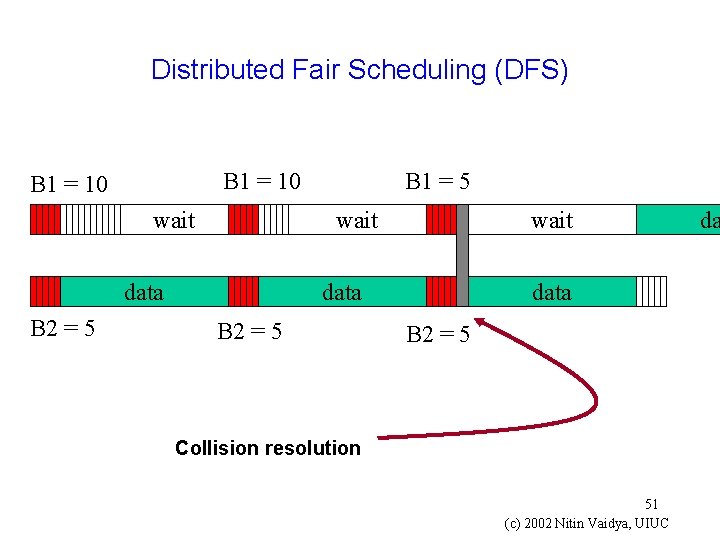
Distributed Fair Scheduling (DFS) wait data B 2 = 5 B 1 = 10 wait data B 2 = 5 Collision resolution 51 (c) 2002 Nitin Vaidya, UIUC da

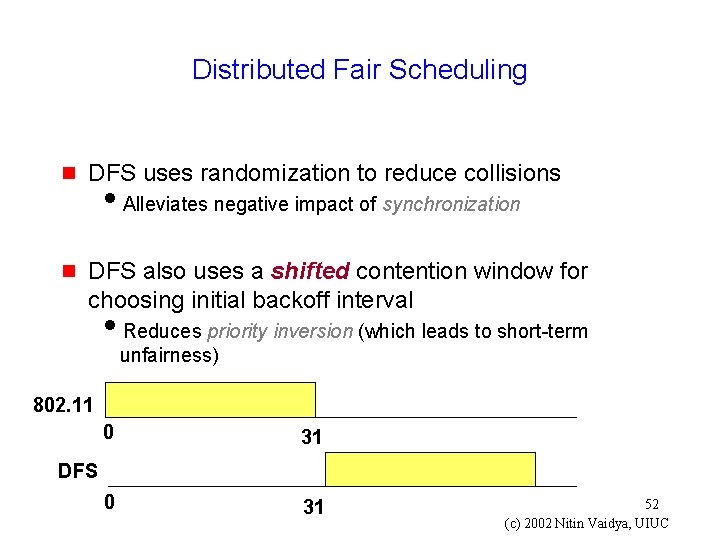
Distributed Fair Scheduling g DFS uses randomization to reduce collisions g DFS also uses a shifted contention window for choosing initial backoff interval i. Alleviates negative impact of synchronization i. Reduces priority inversion (which leads to short-term unfairness) 802. 11 0 31 DFS 52 (c) 2002 Nitin Vaidya, UIUC

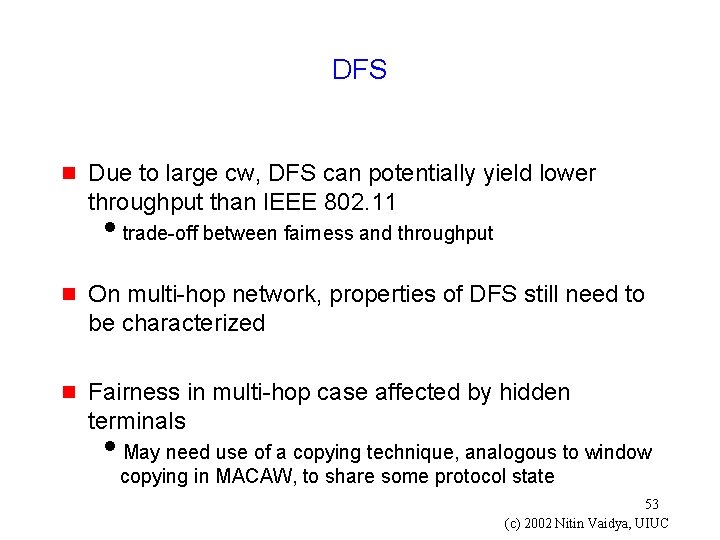
DFS g Due to large cw, DFS can potentially yield lower throughput than IEEE 802. 11 itrade-off between fairness and throughput g On multi-hop network, properties of DFS still need to be characterized g Fairness in multi-hop case affected by hidden terminals i. May need use of a copying technique, analogous to window copying in MACAW, to share some protocol state 53 (c) 2002 Nitin Vaidya, UIUC

Fairness in Multi-Hop Networks g Several definitions of fairness [Ozugur 98, Vaidya 99 MSR, Luo 00 Mobicom, Nandagopal 00 Mobicom] g Hidden terminals make it difficult to achieve a desired notion of fairness 54 (c) 2002 Nitin Vaidya, UIUC
![Balanced MAC Ozugur 98 g Variation on ppersistent protocol g A link access probability Balanced MAC [Ozugur 98] g Variation on p-persistent protocol g A link access probability](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-55.jpg)
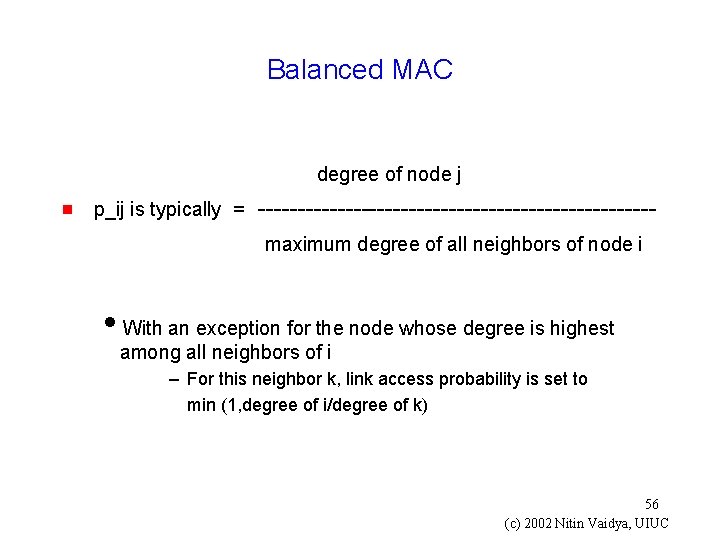
Balanced MAC [Ozugur 98] g Variation on p-persistent protocol g A link access probability p_ij is assigned to each link (i, j) from node i to node j g p_ij is a function of the 1 -hop neighbors of node i and 1 -hop neighbors of all neighbors of node i g Node i picks a back-off interval, and when it counts to 0, node i transmits with probability p_ij i. Otherwise, it picks another backoff interval, and repeats 55 (c) 2002 Nitin Vaidya, UIUC

Balanced MAC degree of node j g p_ij is typically = -------------------------maximum degree of all neighbors of node i i. With an exception for the node whose degree is highest among all neighbors of i – For this neighbor k, link access probability is set to min (1, degree of i/degree of k) 56 (c) 2002 Nitin Vaidya, UIUC

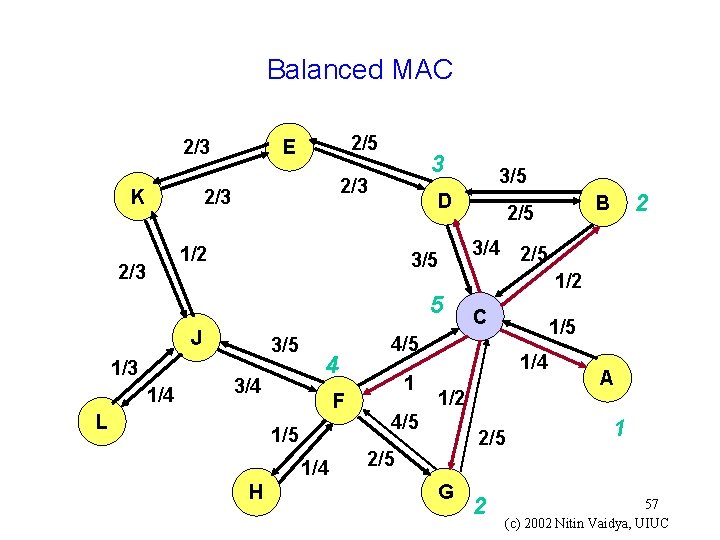
Balanced MAC 2/3 2/5 E 2/3 K 3 D 1/2 2/3 3/5 5 J 1/3 1/4 3/5 3/4 L 4 F 1/5 1/4 H 3/5 3/4 2/5 1/2 C 1/5 4/5 1 1/4 1/2 4/5 2/5 G 2 B 2/5 2 A 1 57 (c) 2002 Nitin Vaidya, UIUC

Balanced MAC g Results show that it can sometimes (not always) improve fairness g Fairness definition used here: max throughput / min throughout g Ad hoc solution i. Not seem to be based on a mathematical argument 58 (c) 2002 Nitin Vaidya, UIUC
![EstimationBased Fair MAC Bansou 00 Mobi Hoc g Attempts to equalize throughputweight ratio for Estimation-Based Fair MAC [Bansou 00 Mobi. Hoc] g Attempts to equalize throughput/weight ratio for](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-59.jpg)
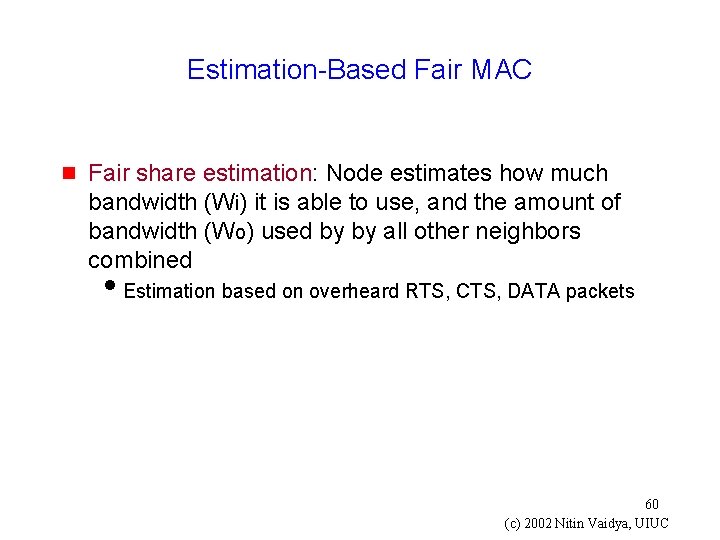
Estimation-Based Fair MAC [Bansou 00 Mobi. Hoc] g Attempts to equalize throughput/weight ratio for all nodes g Two parts of the algorithm i. Fair share estimation i. Window adjustment 59 (c) 2002 Nitin Vaidya, UIUC

Estimation-Based Fair MAC g Fair share estimation: Node estimates how much bandwidth (Wi) it is able to use, and the amount of bandwidth (Wo) used by by all other neighbors combined i. Estimation based on overheard RTS, CTS, DATA packets 60 (c) 2002 Nitin Vaidya, UIUC

Estimation-Based Fair MAC g Define: g Window adjustment: i. Ti = Wi / weight of i i. To = Wo / weight assigned to the group of neighbors of i i. Fairness index = Ti / To i. If fairness index is too large, cw = cw * 2 i. Else if fairness index is too small, cw = cw / 2 i. Else no change to cw (contention window) 61 (c) 2002 Nitin Vaidya, UIUC
![Proportional Fair Contention Resolution PFCR Nandagopal 00 Mobicom g Proportional fairness Allocate bandwidth Ri Proportional Fair Contention Resolution (PFCR) [Nandagopal 00 Mobicom] g Proportional fairness: Allocate bandwidth Ri](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-62.jpg)
Proportional Fair Contention Resolution (PFCR) [Nandagopal 00 Mobicom] g Proportional fairness: Allocate bandwidth Ri to node i such that any other allocation Si has the following property i. Si g (Si-Ri) / Ri < 0 Link access probability is dynamically changed depending on success/failure at transmitting a packet i. On success: Link access probability is increased by an additive factor a i. On failure: Link access probability is decreased by a multiplicative factor (1 -b) 62 (c) 2002 Nitin Vaidya, UIUC

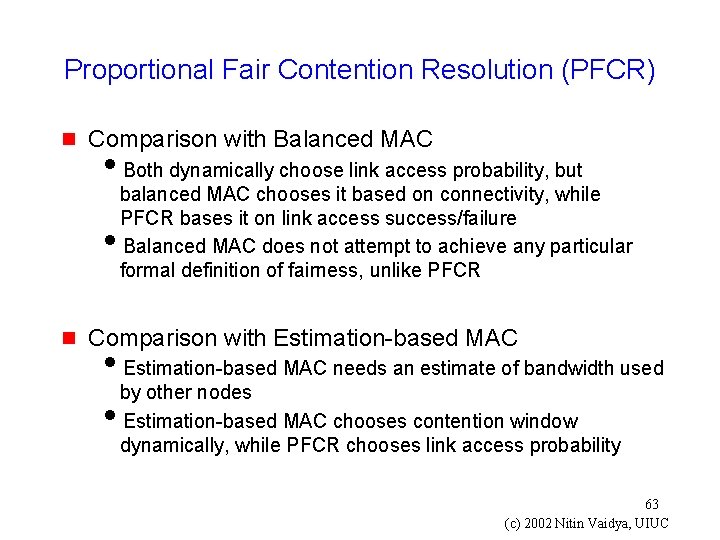
Proportional Fair Contention Resolution (PFCR) g Comparison with Balanced MAC i. Both dynamically choose link access probability, but balanced MAC chooses it based on connectivity, while PFCR bases it on link access success/failure i. Balanced MAC does not attempt to achieve any particular formal definition of fairness, unlike PFCR g Comparison with Estimation-based MAC i. Estimation-based MAC needs an estimate of bandwidth used by other nodes i. Estimation-based MAC chooses contention window dynamically, while PFCR chooses link access probability 63 (c) 2002 Nitin Vaidya, UIUC

Priority Scheduling 64 (c) 2002 Nitin Vaidya, UIUC

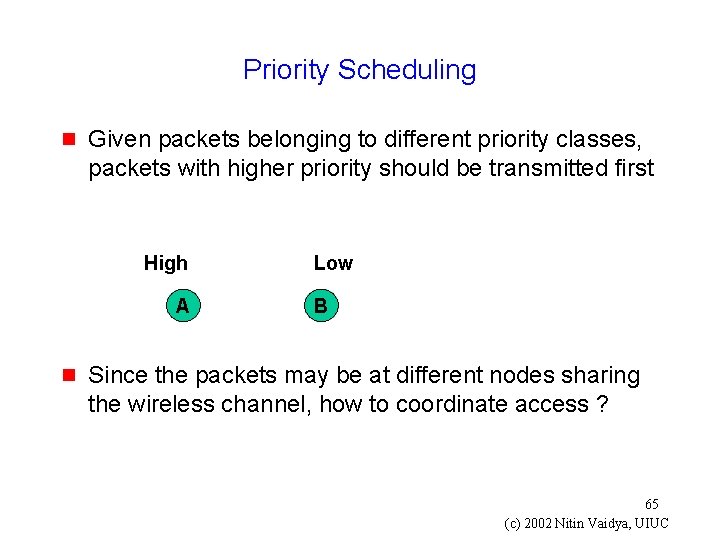
Priority Scheduling g Given packets belonging to different priority classes, packets with higher priority should be transmitted first High A g Low B Since the packets may be at different nodes sharing the wireless channel, how to coordinate access ? 65 (c) 2002 Nitin Vaidya, UIUC

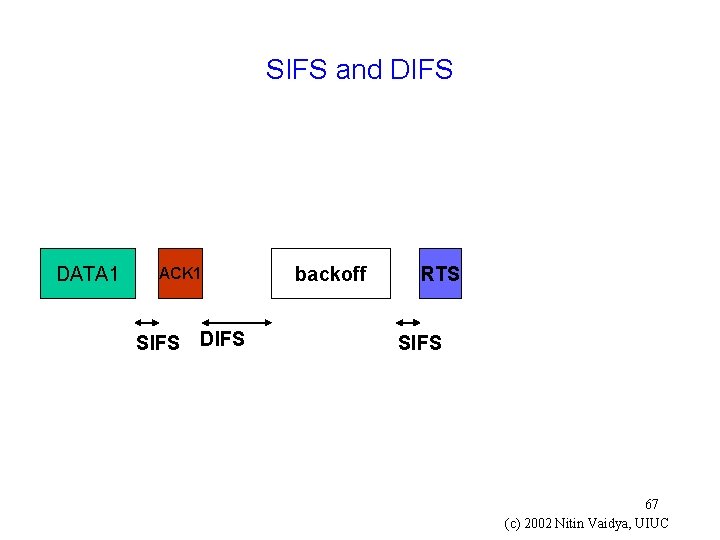
Priorities in 802. 11 g CTS and ACK have priority over RTS After channel becomes idle g If a node wants to send CTS/ACK, it transmits SIFS duration after channel goes idle g If a node wants to send RTS, it waits for DIFS > SIFS 66 (c) 2002 Nitin Vaidya, UIUC

SIFS and DIFS DATA 1 ACK 1 SIFS DIFS backoff RTS SIFS 67 (c) 2002 Nitin Vaidya, UIUC
![Variation in Backoff Interval Aad 01 g For high priority packets g For low Variation in Backoff Interval [Aad 01] g For high priority packets g For low](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-68.jpg)
Variation in Backoff Interval [Aad 01] g For high priority packets g For low priority packet g Higher priority packets use small backoff intervals i. Backoff interval in [0, CWh] i. Backoff interval in [CWh+1, CWl] i. Higher probability of transmitting a high priority packet before a pending low probability packet 68 (c) 2002 Nitin Vaidya, UIUC

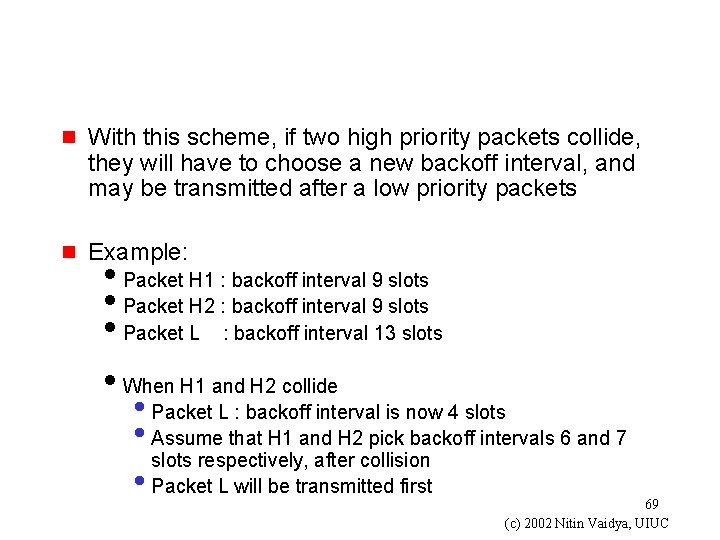
g With this scheme, if two high priority packets collide, they will have to choose a new backoff interval, and may be transmitted after a low priority packets g Example: i. Packet H 1 : backoff interval 9 slots i. Packet H 2 : backoff interval 9 slots i. Packet L : backoff interval 13 slots i. When H 1 and H 2 collide • Packet L : backoff interval is now 4 slots • Assume that H 1 and H 2 pick backoff intervals 6 and 7 slots respectively, after collision • Packet L will be transmitted first 69 (c) 2002 Nitin Vaidya, UIUC
![Second Mechanism Aad 01 g High priority packets always choose backoff in 0 CWh Second Mechanism [Aad 01] g High priority packets always choose backoff in [0, CWh]](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-70.jpg)
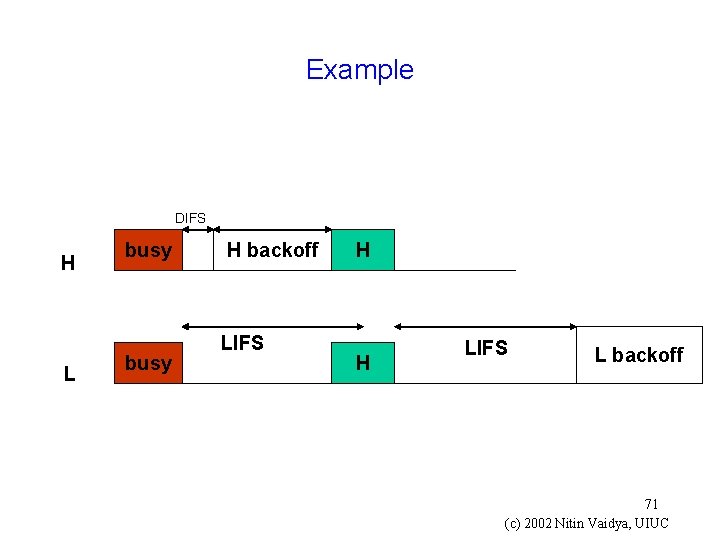
Second Mechanism [Aad 01] g High priority packets always choose backoff in [0, CWh] g Low priority packets wait for LIFS idle period before counting down where LIFS = DIFS + CWh g Ensures that high priority packets will always get a chance to transmit before a low priority packet can 70 (c) 2002 Nitin Vaidya, UIUC

Example DIFS H L busy H backoff LIFS H H LIFS L backoff 71 (c) 2002 Nitin Vaidya, UIUC

g Disadvantage: When no high priority packets, low priority packet unnecessarily wait for long periods of time g How to avoid priority reversal, and also minimize wait for low priority packets ? [Yang 02 Mobihoc] 72 (c) 2002 Nitin Vaidya, UIUC
![Priority Using Black Bursts Hiperlan1 Sobrinho 96 99 g All nodes begin the priority Priority Using Black Bursts [Hiperlan/1, Sobrinho 96, 99] g All nodes begin the priority](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-73.jpg)
Priority Using Black Bursts [Hiperlan/1, Sobrinho 96, 99] g All nodes begin the priority contention phase together g Higher priority node transmit a longer burst than low priority node g After transmitting its burst, a node listens to the channel g If channel still busy, the node has lost contention to a higher priority node 73 (c) 2002 Nitin Vaidya, UIUC

Energy Conservation 74 (c) 2002 Nitin Vaidya, UIUC

Energy Conservation g Since many mobile hosts are operated by batteries, MAC protocols which conserve energy are of interest g Two approaches to reduce energy consumption i. Power save: Turn off wireless interface when desirable i. Power control: Reduce transmit power 75 (c) 2002 Nitin Vaidya, UIUC
![Power Aware MultiAccess Protocol PAMAS Singh 98 g A node powers off its radio Power Aware Multi-Access Protocol (PAMAS) [Singh 98] g A node powers off its radio](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-76.jpg)
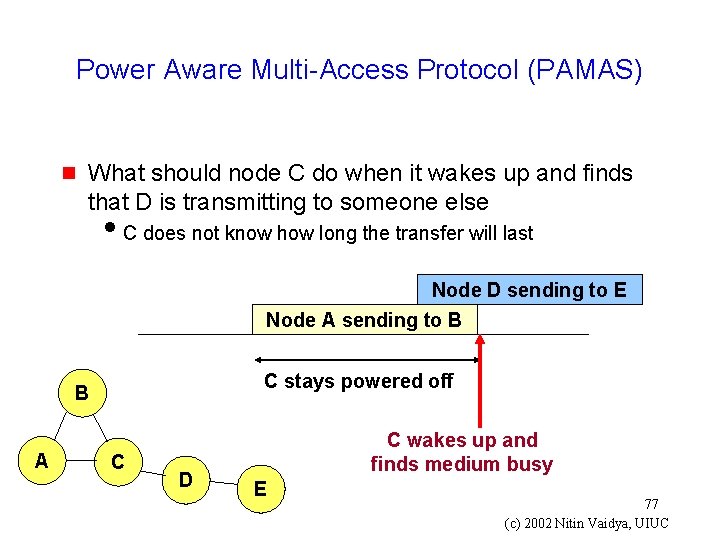
Power Aware Multi-Access Protocol (PAMAS) [Singh 98] g A node powers off its radio while a neighbor is transmitting to someone else Node A sending to B Node C stays powered off B A C 76 (c) 2002 Nitin Vaidya, UIUC

Power Aware Multi-Access Protocol (PAMAS) g What should node C do when it wakes up and finds that D is transmitting to someone else i. C does not know how long the transfer will last Node D sending to E Node A sending to B C stays powered off B A C D C wakes up and finds medium busy E 77 (c) 2002 Nitin Vaidya, UIUC

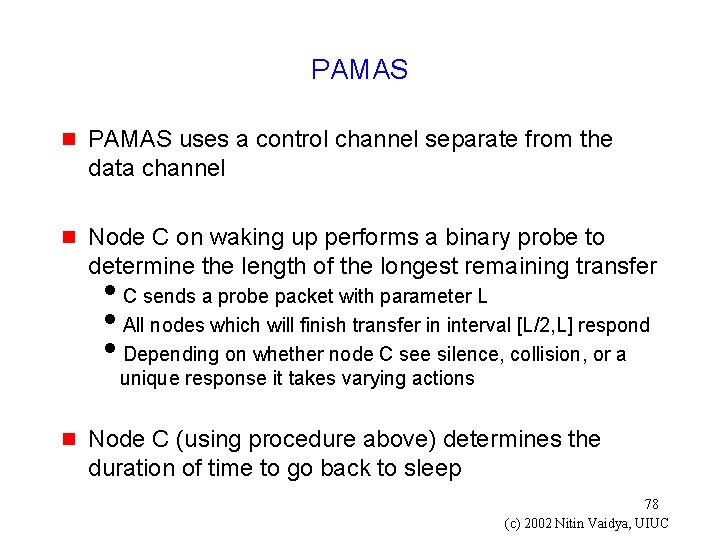
PAMAS g PAMAS uses a control channel separate from the data channel g Node C on waking up performs a binary probe to determine the length of the longest remaining transfer i. C sends a probe packet with parameter L i. All nodes which will finish transfer in interval [L/2, L] respond i. Depending on whether node C see silence, collision, or a unique response it takes varying actions g Node C (using procedure above) determines the duration of time to go back to sleep 78 (c) 2002 Nitin Vaidya, UIUC

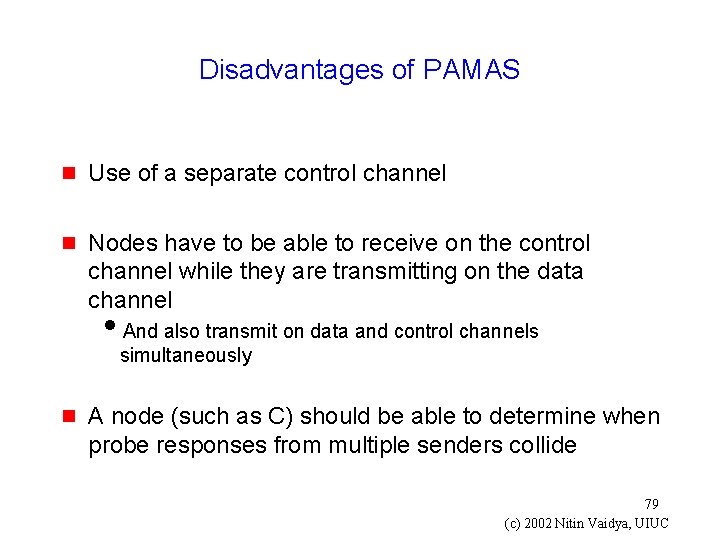
Disadvantages of PAMAS g Use of a separate control channel g Nodes have to be able to receive on the control channel while they are transmitting on the data channel i. And also transmit on data and control channels simultaneously g A node (such as C) should be able to determine when probe responses from multiple senders collide 79 (c) 2002 Nitin Vaidya, UIUC

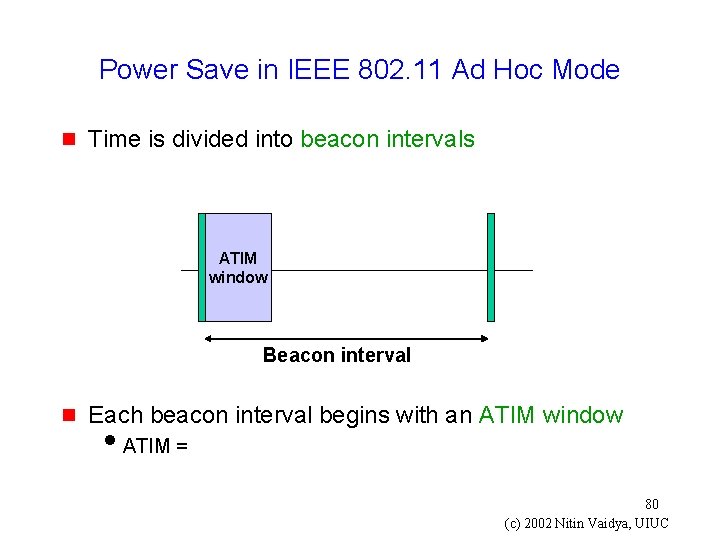
Power Save in IEEE 802. 11 Ad Hoc Mode g Time is divided into beacon intervals ATIM window Beacon interval g Each beacon interval begins with an ATIM window i. ATIM = 80 (c) 2002 Nitin Vaidya, UIUC

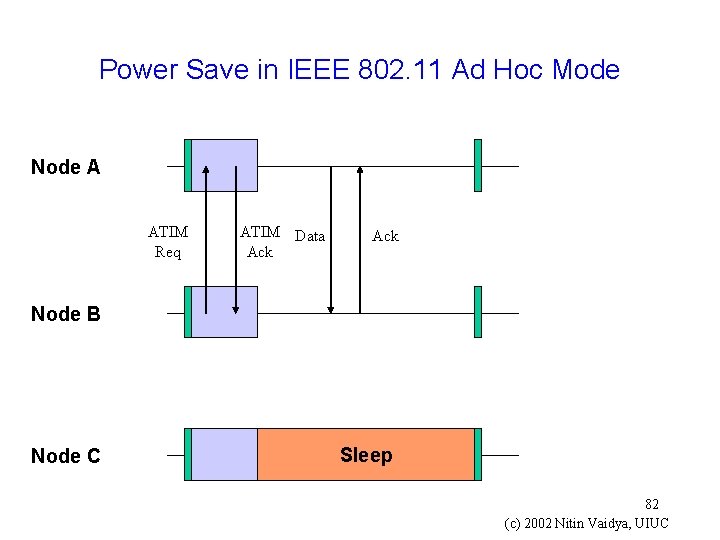
Power Save in IEEE 802. 11 Ad Hoc Mode g If host A has a packet to transmit to B, A must send an ATIM Request to B during an ATIM Window g On receipt of ATIM Request from A, B will reply by sending an ATIM Ack, and stay up during the rest of the beacon interval g If a host does not receive an ATIM Request during an ATIM window, and has no pending packets to transmit, it may sleep during rest of the beacon interval 81 (c) 2002 Nitin Vaidya, UIUC

Power Save in IEEE 802. 11 Ad Hoc Mode Node A ATIM Req ATIM Data Ack Node B Node C Sleep 82 (c) 2002 Nitin Vaidya, UIUC

Power Save in IEEE 802. 11 Ad Hoc Mode g Size of ATIM window and beacon interval affects performance [Woesner 98] g If ATIM window is too large, reduction in energy consumption reduced i. Energy consumed during ATIM window g If ATIM window is too small, not enough time to send ATIM request 83 (c) 2002 Nitin Vaidya, UIUC

Power Save in IEEE 802. 11 Ad Hoc Mode g How to choose ATIM window dynamically? g How to synchronize hosts? i. Based on observed load [Jung 02 infocom] i. If two hosts’ ATIM windows do not overlap in time, they cannot exchange ATIM requests i. Coordination requires that each host stay awake long enough (at least periodically) to discover out-of-sync neighbors [Tseng 02 infocom] ATIM 84 (c) 2002 Nitin Vaidya, UIUC

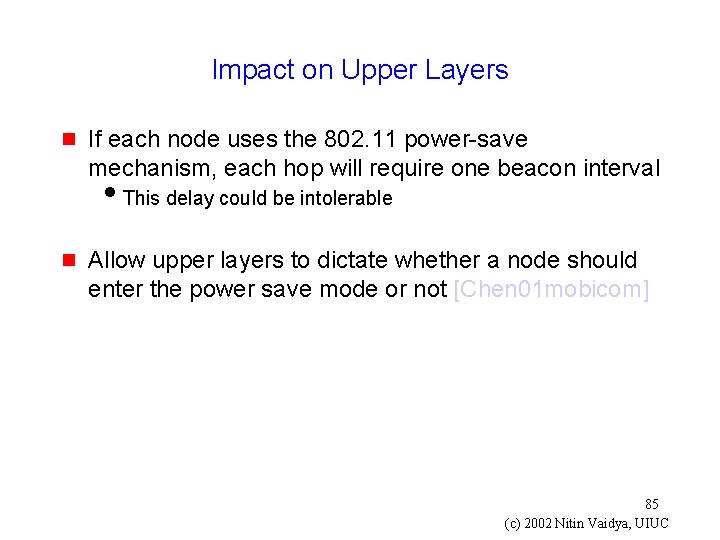
Impact on Upper Layers g If each node uses the 802. 11 power-save mechanism, each hop will require one beacon interval i. This delay could be intolerable g Allow upper layers to dictate whether a node should enter the power save mode or not [Chen 01 mobicom] 85 (c) 2002 Nitin Vaidya, UIUC

Energy Conservation g Power save g Power control 86 (c) 2002 Nitin Vaidya, UIUC

Power Control Power control has two potential benefit g Reduced interference & increased spatial reuse g Energy saving 87 (c) 2002 Nitin Vaidya, UIUC

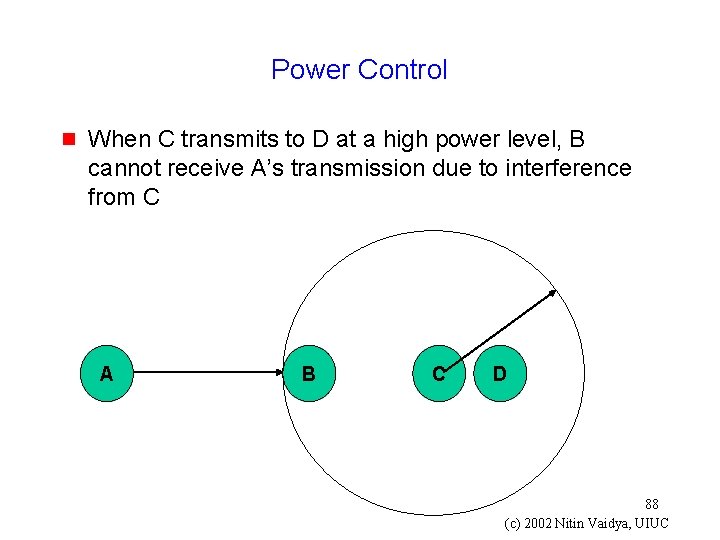
Power Control g When C transmits to D at a high power level, B cannot receive A’s transmission due to interference from C A B C D 88 (c) 2002 Nitin Vaidya, UIUC

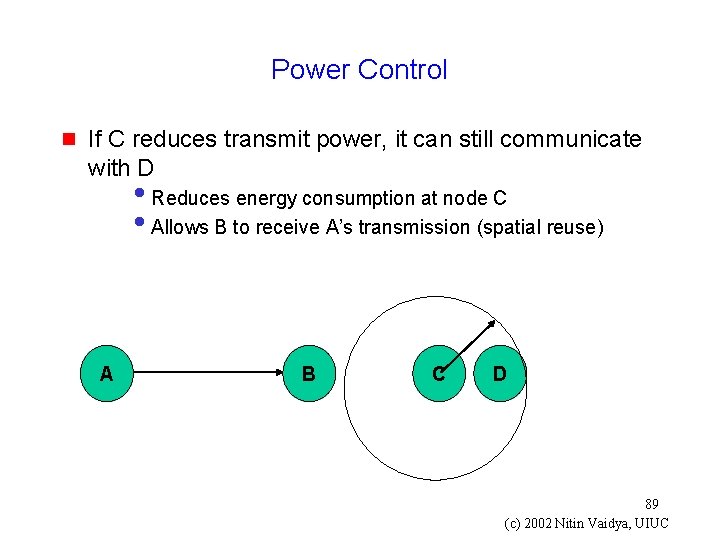
Power Control g If C reduces transmit power, it can still communicate with D • Reduces energy consumption at node C • Allows B to receive A’s transmission (spatial reuse) A B C D 89 (c) 2002 Nitin Vaidya, UIUC

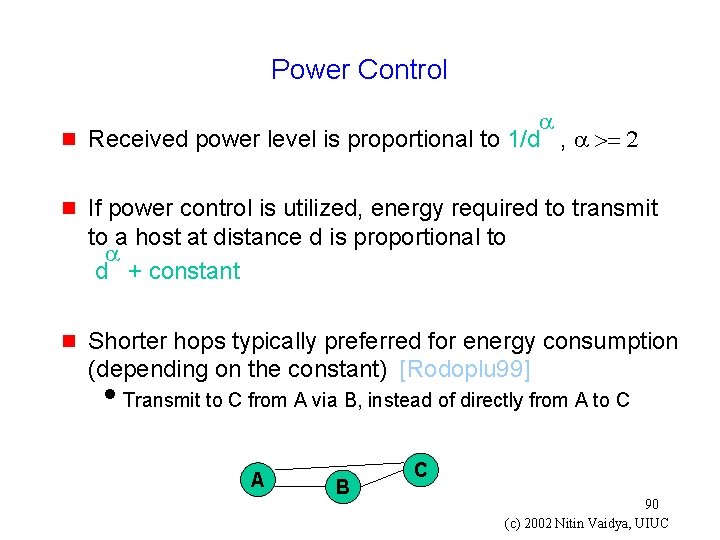
Power Control g a Received power level is proportional to 1/d , a >= 2 g If power control is utilized, energy required to transmit to a host at distance d is proportional to a d + constant g Shorter hops typically preferred for energy consumption (depending on the constant) [Rodoplu 99] i. Transmit to C from A via B, instead of directly from A to C A B C 90 (c) 2002 Nitin Vaidya, UIUC

Power Control with 802. 11 g A Transmit RTS/CTS/DATA/ACK at least power level needed to communicate with the received B C D g A/B do not receive RTS/CTS from C/D. Also do not sense D’s data transmission g B’s transmission to A at high power interferes with reception of ACK at C 91 (c) 2002 Nitin Vaidya, UIUC

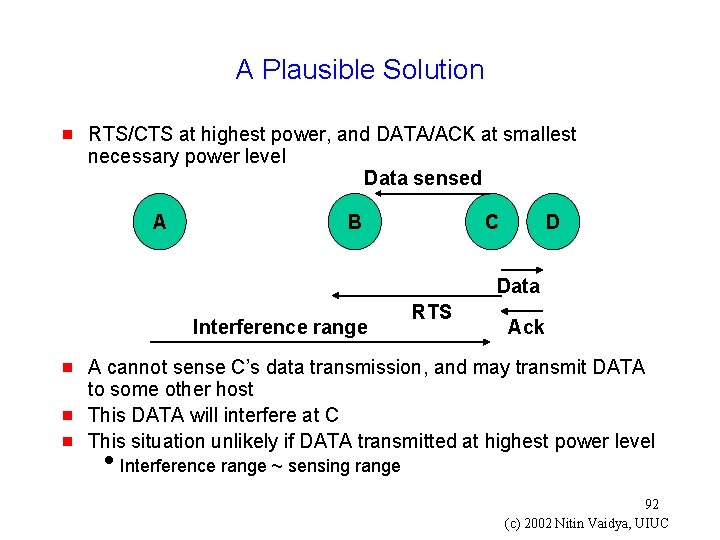
A Plausible Solution g RTS/CTS at highest power, and DATA/ACK at smallest necessary power level Data sensed A B C D Data Interference range g g g RTS Ack A cannot sense C’s data transmission, and may transmit DATA to some other host This DATA will interfere at C This situation unlikely if DATA transmitted at highest power level i. Interference range ~ sensing range 92 (c) 2002 Nitin Vaidya, UIUC

g Transmitting RTS at the highest power level also reduces spatial reuse g Nodes receiving RTS/CTS have to defer transmissions 93 (c) 2002 Nitin Vaidya, UIUC

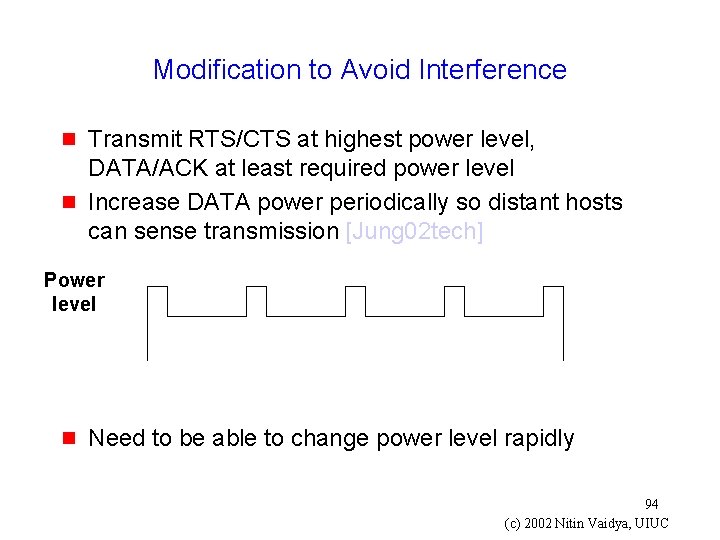
Modification to Avoid Interference g g Transmit RTS/CTS at highest power level, DATA/ACK at least required power level Increase DATA power periodically so distant hosts can sense transmission [Jung 02 tech] Power level g Need to be able to change power level rapidly 94 (c) 2002 Nitin Vaidya, UIUC

Caveat g Energy saving by power control is limited to savings in transmit energy g Other energy costs may not change g For some 802. 11 devices, the energy consumption of the wireless interface reduces only by a factor of 2 when transmit power reduced from max to min possible for the device 95 (c) 2002 Nitin Vaidya, UIUC
![Power Controlled Multiple Access PCMA Monks 01 infocom g If receiver node R can Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-96.jpg)
Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can tolerate noise E, it sends a busy tone at power level C/E, where C is an appropriate constant g When some node X receives a busy-tone a power level Pr, it may transmit at power level Pt <= C/Pr busy tone data S R C/E X Pt Y 96 (c) 2002 Nitin Vaidya, UIUC
![Power Controlled Multiple Access PCMA Monks 01 infocom g If receiver node R can Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-97.jpg)
Power Controlled Multiple Access (PCMA) [Monks 01 infocom] g If receiver node R can tolerate noise E, it sends a busy tone at power level C/E, where C is an appropriate constant g When some node X receives a busy-tone a power level Pr, it may transmit at power level Pt <= C/Pr g Explanation: i. Gain of channel RX = gain of channel XR = g i. Busy tone signal level at X = Pr = g * C / E i. Node X may transmit at level = Pt = C/Pr = E/g i. Interference received by R = Pt * g = E 97 (c) 2002 Nitin Vaidya, UIUC

PCMA g Advantage i. Allows higher spatial reuse, as well as power saving using power control g Disadvantages: i. Need a separate channel for the busy tone i. Since multiple nodes may transmit the busy tones simultaneously, spatial reuse is less than optimal 98 (c) 2002 Nitin Vaidya, UIUC
![Small Addresses Save Energy Schurgers 01 mobihoc g In sensor networks packet sizes are Small Addresses Save Energy [Schurgers 01 mobihoc] g In sensor networks, packet sizes are](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-99.jpg)
Small Addresses Save Energy [Schurgers 01 mobihoc] g In sensor networks, packet sizes are small, and MAC addresses may be a substantial fraction of the packet g Observation: MAC addresses need only be unique within two hops E 1 G 0 D 3 A 2 C 0 F 2 B 1 g Fewer addresses are sufficient: Address size can be smaller. [Schurgers 00 mobihoc] uses Huffman coding to assign variable size encoding to the addresses Energy consumption reduced due to smaller addresses g 99 (c) 2002 Nitin Vaidya, UIUC

Adaptive Modulation 100 (c) 2002 Nitin Vaidya, UIUC

Adaptive Modulation g Channel conditions are time-varying g Received signal-to-noise ratio changes with time A B 101 (c) 2002 Nitin Vaidya, UIUC

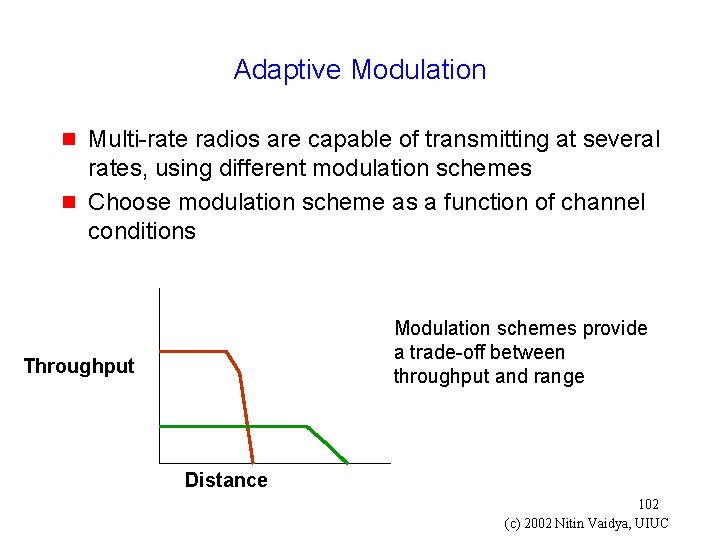
Adaptive Modulation g g Multi-rate radios are capable of transmitting at several rates, using different modulation schemes Choose modulation scheme as a function of channel conditions Modulation schemes provide a trade-off between throughput and range Throughput Distance 102 (c) 2002 Nitin Vaidya, UIUC

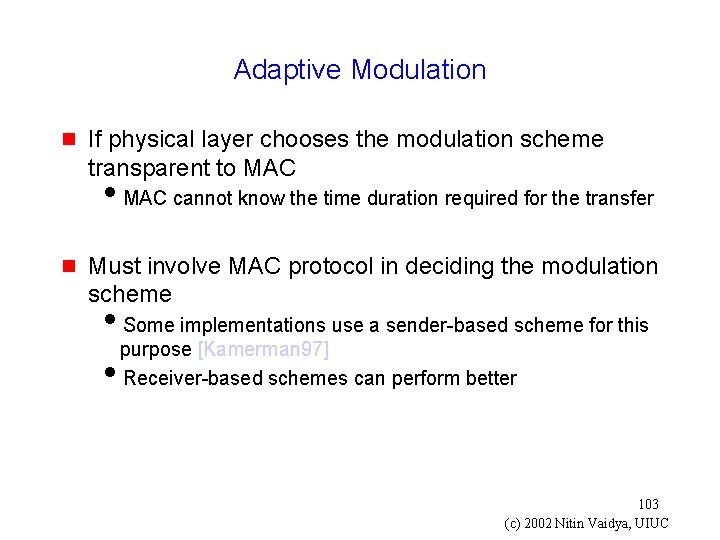
Adaptive Modulation g If physical layer chooses the modulation scheme transparent to MAC i. MAC cannot know the time duration required for the transfer g Must involve MAC protocol in deciding the modulation scheme i. Some implementations use a sender-based scheme for this purpose [Kamerman 97] i. Receiver-based schemes can perform better 103 (c) 2002 Nitin Vaidya, UIUC
![SenderBased Autorate Fallback Kamerman 97 g Probing mechanisms g Sender decreases bit rate after Sender-Based “Autorate Fallback” [Kamerman 97] g Probing mechanisms g Sender decreases bit rate after](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-104.jpg)
Sender-Based “Autorate Fallback” [Kamerman 97] g Probing mechanisms g Sender decreases bit rate after X consecutive transmission attempts fail g Sender increases bit rate after Y consecutive transmission attempt succeed 104 (c) 2002 Nitin Vaidya, UIUC

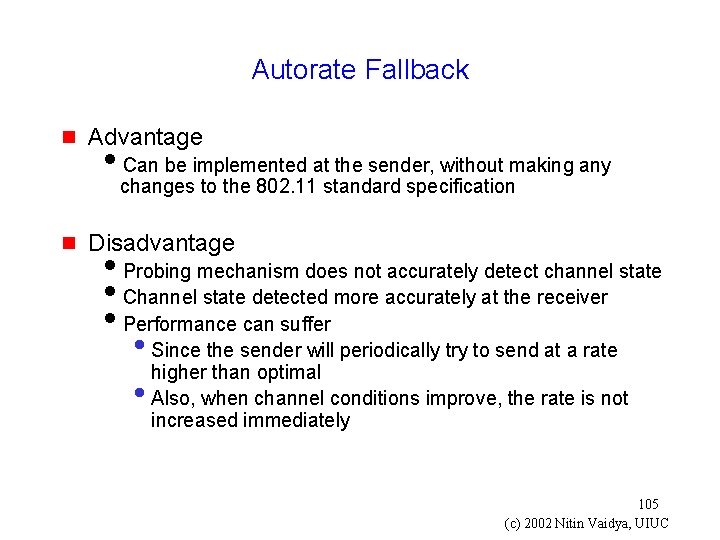
Autorate Fallback g Advantage i. Can be implemented at the sender, without making any changes to the 802. 11 standard specification g Disadvantage i. Probing mechanism does not accurately detect channel state i. Channel state detected more accurately at the receiver i. Performance can suffer • Since the sender will periodically try to send at a rate higher than optimal • Also, when channel conditions improve, the rate is not increased immediately 105 (c) 2002 Nitin Vaidya, UIUC
![ReceiverBased Autorate MAC Holland 01 mobicom g Sender sends RTS containing its best rate Receiver-Based Autorate MAC [Holland 01 mobicom] g Sender sends RTS containing its best rate](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-106.jpg)
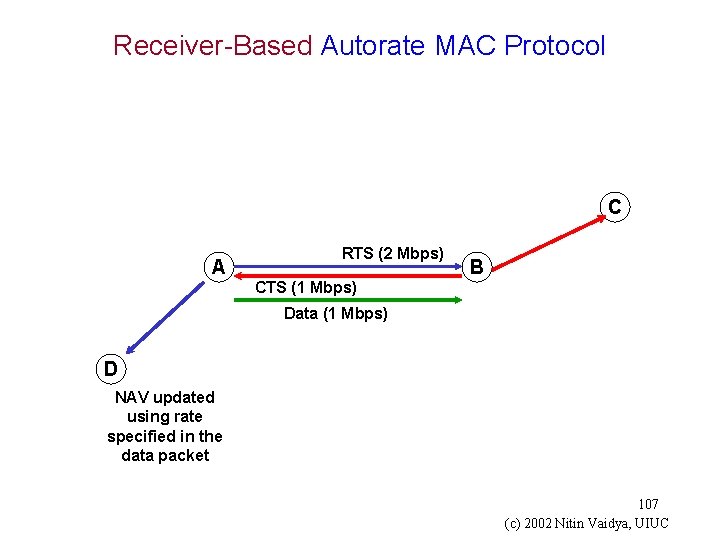
Receiver-Based Autorate MAC [Holland 01 mobicom] g Sender sends RTS containing its best rate estimate g Receiver chooses best rate for the conditions and sends it in the CTS g Sender transmits DATA packet at new rate g Information in data packet header implicitly updates nodes that heard old rate 106 (c) 2002 Nitin Vaidya, UIUC

Receiver-Based Autorate MAC Protocol C A RTS (2 Mbps) CTS (1 Mbps) B Data (1 Mbps) D NAV updated using rate specified in the data packet 107 (c) 2002 Nitin Vaidya, UIUC

Directional Antennas 108 (c) 2002 Nitin Vaidya, UIUC

Traditional MAC Protocols g Typically assume omni-directional antennas g With omni-directional antennas, packet transmission intended for one neighbor may cause interference at all neighbors. 109 (c) 2002 Nitin Vaidya, UIUC

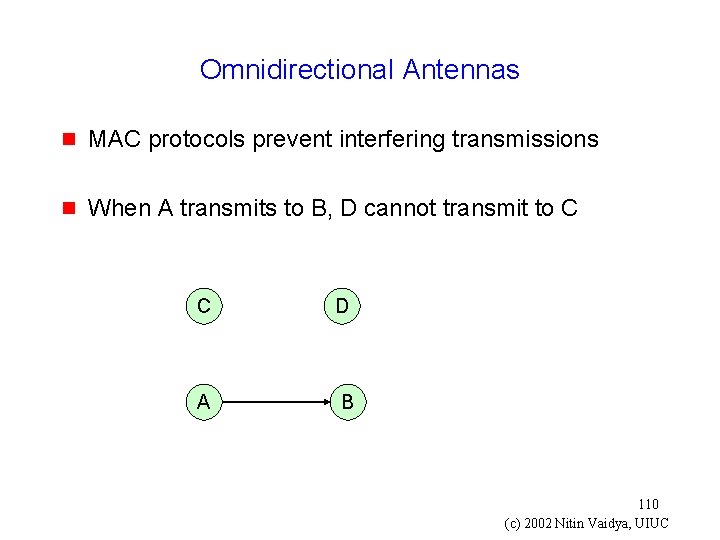
Omnidirectional Antennas g MAC protocols prevent interfering transmissions g When A transmits to B, D cannot transmit to C C D A B 110 (c) 2002 Nitin Vaidya, UIUC

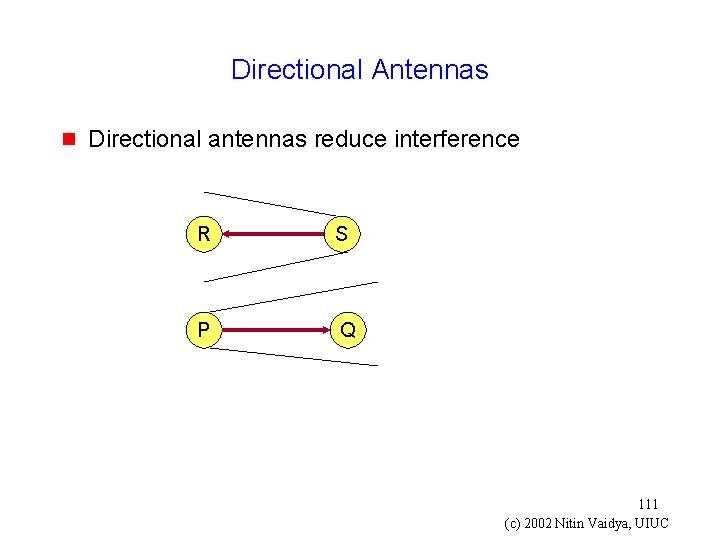
Directional Antennas g Directional antennas reduce interference R S P Q 111 (c) 2002 Nitin Vaidya, UIUC

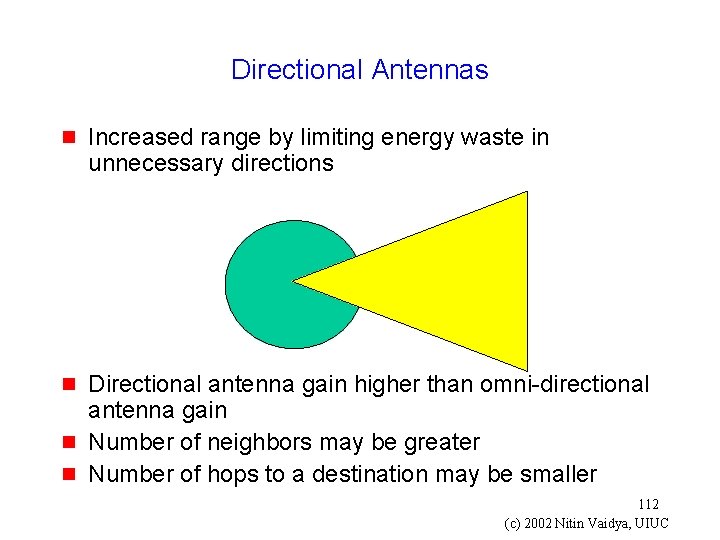
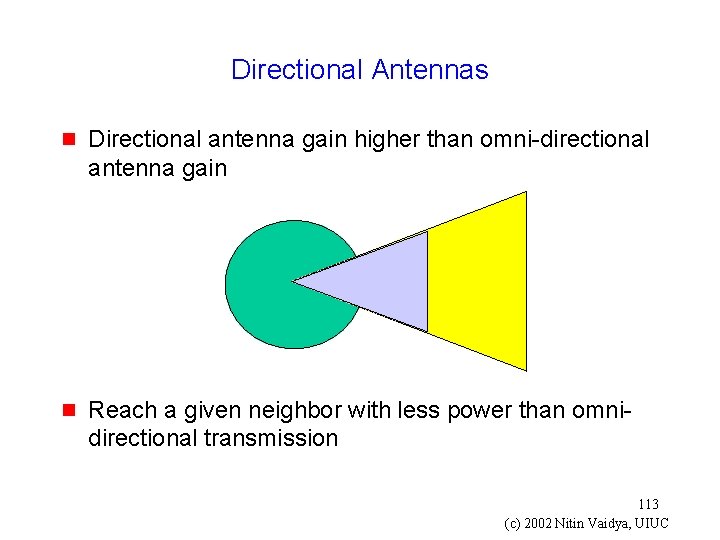
Directional Antennas g Increased range by limiting energy waste in unnecessary directions g Directional antenna gain higher than omni-directional antenna gain Number of neighbors may be greater Number of hops to a destination may be smaller g g 112 (c) 2002 Nitin Vaidya, UIUC

Directional Antennas g Directional antenna gain higher than omni-directional antenna gain g Reach a given neighbor with less power than omnidirectional transmission 113 (c) 2002 Nitin Vaidya, UIUC

Directional Antennas Potential benefits g Higher spatial reuse g Greater range (for given transmit power) g Reduction in energy consumption But need new MAC protocols to best utilize directional antennas 114 (c) 2002 Nitin Vaidya, UIUC

Directional MAC (D-MAC) g Many proposals using RTS/CTS exchange [Ko 00 infocom, Nasipuri 00, Roychoudhury 02 tech, Takai 02 mobihoc] g Proposals differ in how the RTS/CTS are transmitted i. In a particular direction i. In all directions (omni-directional) i. In a subset of directions 115 (c) 2002 Nitin Vaidya, UIUC

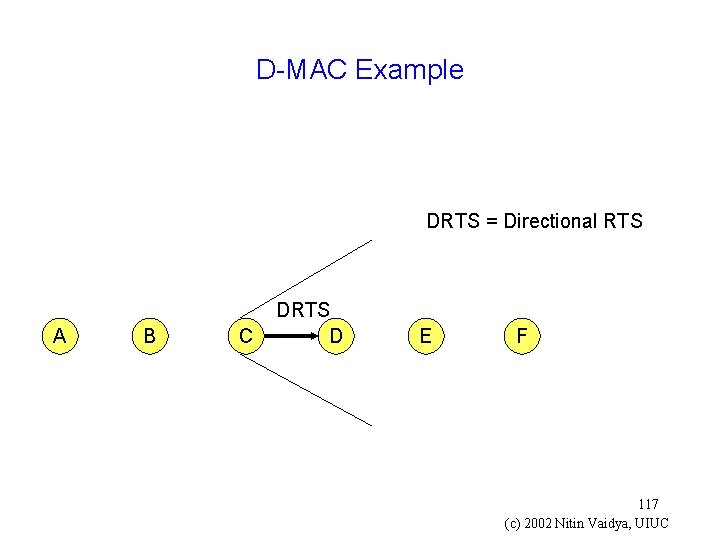
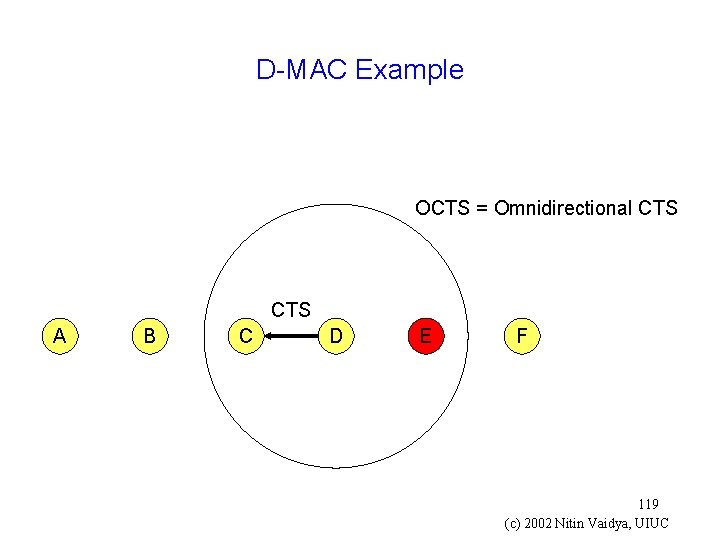
Directional MAC (D-MAC) Example g Directional RTS (DRTS) g Omnidirectional CTS (OCTS) 116 (c) 2002 Nitin Vaidya, UIUC

D-MAC Example DRTS = Directional RTS A B C DRTS D E F 117 (c) 2002 Nitin Vaidya, UIUC

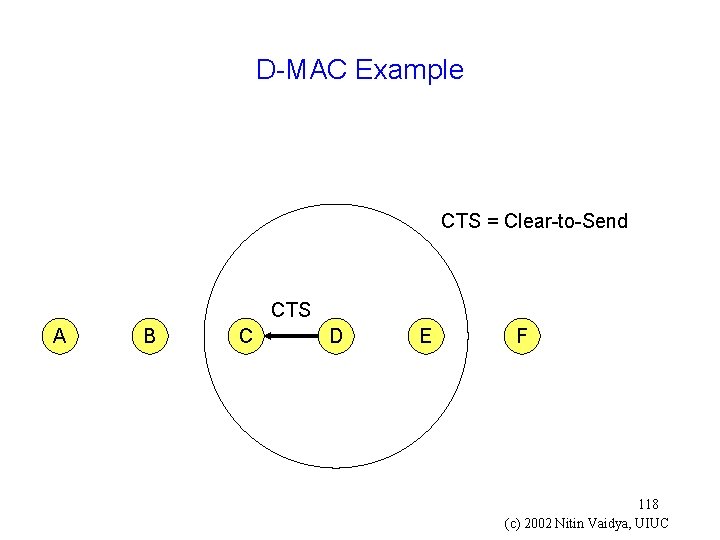
D-MAC Example CTS = Clear-to-Send CTS A B C D E F 118 (c) 2002 Nitin Vaidya, UIUC

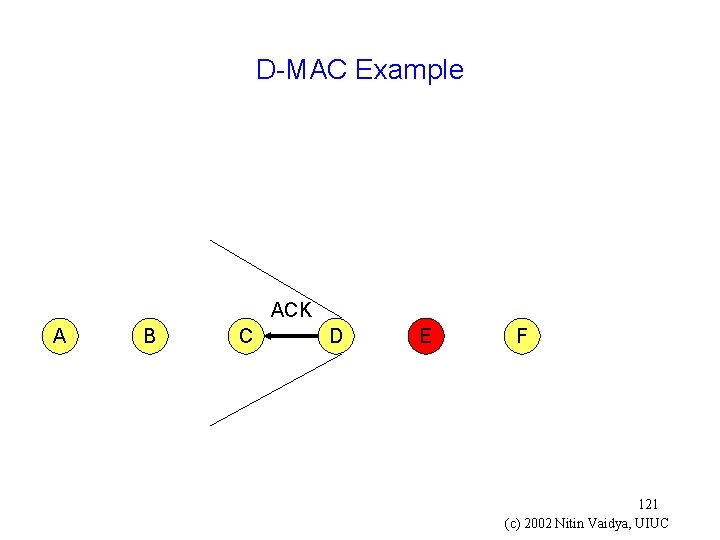
D-MAC Example OCTS = Omnidirectional CTS A B C D E F 119 (c) 2002 Nitin Vaidya, UIUC

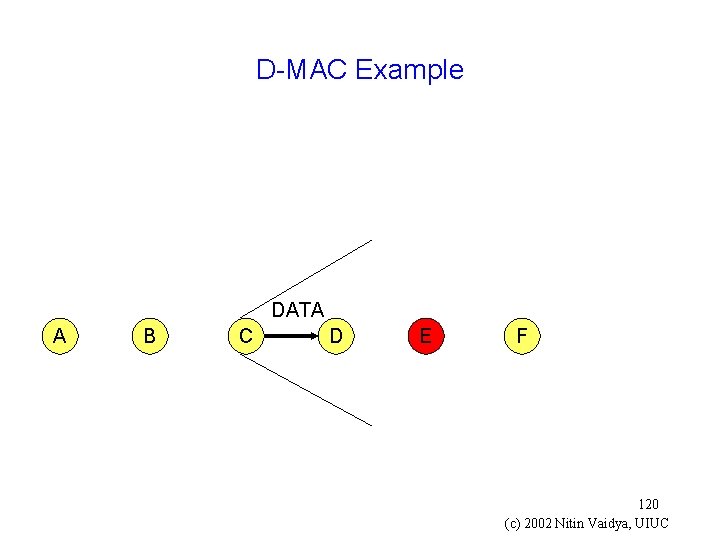
D-MAC Example DATA A B C D E F 120 (c) 2002 Nitin Vaidya, UIUC

D-MAC Example ACK A B C D E F 121 (c) 2002 Nitin Vaidya, UIUC
![Directional Carrier Sensing Takai 02 mobihoc Roychoudhury 02 tech g Physical carrier sensing similar Directional Carrier Sensing [Takai 02 mobihoc, Roychoudhury 02 tech] g Physical carrier sensing similar](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-122.jpg)
Directional Carrier Sensing [Takai 02 mobihoc, Roychoudhury 02 tech] g Physical carrier sensing similar to omni antennas g Virtual carrier sensing somewhat different i. When RTS/CTS received from a particular direction, record the direction of arrival and duration of proposed transfer i. Channel assumed to be busy in the direction from which RTS/CTS received 122 (c) 2002 Nitin Vaidya, UIUC
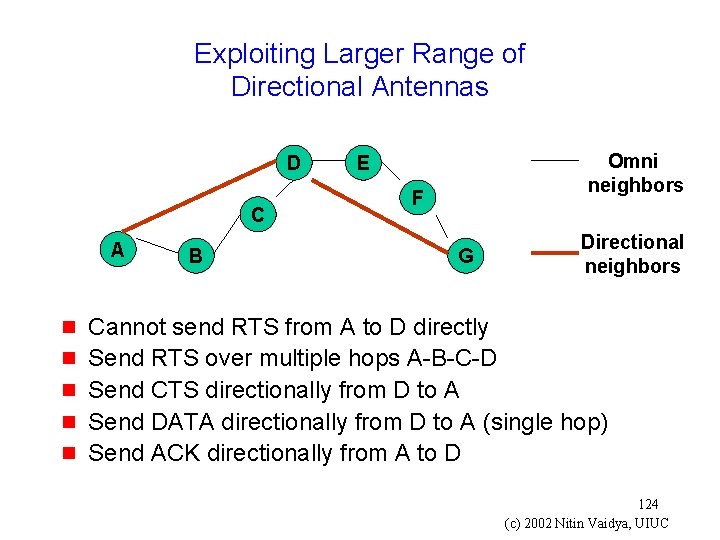
![Exploiting Larger Range of Directional Antennas Roychoudhury 02 tech D C A g B Exploiting Larger Range of Directional Antennas [Roychoudhury 02 tech] D C A g B](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-123.jpg)
Exploiting Larger Range of Directional Antennas [Roychoudhury 02 tech] D C A g B Omni neighbors E F G Directional neighbors When transmission needs to be schedules, receiving node is in omni-receive mode smaller gain 123 (c) 2002 Nitin Vaidya, UIUC

Exploiting Larger Range of Directional Antennas D C A g g g B Omni neighbors E F G Directional neighbors Cannot send RTS from A to D directly Send RTS over multiple hops A-B-C-D Send CTS directionally from D to A Send DATA directionally from D to A (single hop) Send ACK directionally from A to D 124 (c) 2002 Nitin Vaidya, UIUC

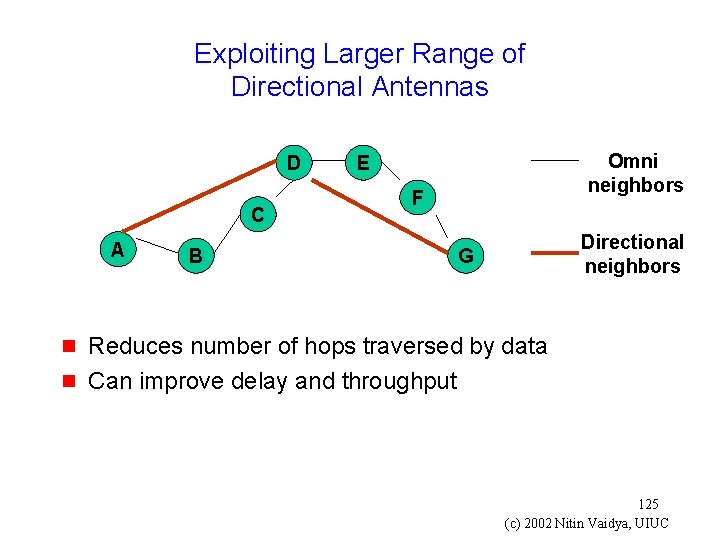
Exploiting Larger Range of Directional Antennas D C A g g B Omni neighbors E F Directional neighbors G Reduces number of hops traversed by data Can improve delay and throughput 125 (c) 2002 Nitin Vaidya, UIUC

Multiple Channels 126 (c) 2002 Nitin Vaidya, UIUC

Multiple Channels g Multiple channels in ad hoc networks: typically defined by a particular code (CDMA) or frequency band (FDMA) g TDMA requires time synchronization among hosts in ad hoc network i. Difficult g Many MAC protocols have been proposed 127 (c) 2002 Nitin Vaidya, UIUC

Multi-Channel MAC: A simple approach g Divide bandwidth into multiple channels g Choose any one of the idle channels g Use a single-channel protocol on the chosen channel i. ALOHA i. MACA 128 (c) 2002 Nitin Vaidya, UIUC
![MultiChannel MAC with Soft Reservation Nasipuri 00 g Similar to the simple scheme channel Multi-Channel MAC with Soft Reservation [Nasipuri 00] g Similar to the simple scheme, channel](https://slidetodoc.com/presentation_image_h/b6bea18769f76a486357ba88801753af/image-129.jpg)
Multi-Channel MAC with Soft Reservation [Nasipuri 00] g Similar to the simple scheme, channel used recently for a successful transmission preferred g Tends to “reserve” channels 129 (c) 2002 Nitin Vaidya, UIUC

Another Protocol g Use one (control) channel for RTS/CTS and remaining (data) channels for DATA/ACK g Each host maintains NAV table, with one entry for each data channel g Sender sends RTS to destination, specifying the channels that are free per sender’s table g Receiver replies with CTS specifying a channel that it also thinks is free i. A channel is used only if both sender and receiver conclude that it is free 130 (c) 2002 Nitin Vaidya, UIUC

Related Standards Activities 131 (c) 2002 Nitin Vaidya, UIUC

Related Standards Activities g IEEE 802. 11 g Hiperlan/2 g Blue. Tooth g IETF manet (Mobile Ad-hoc Networks) working group ihttp: //grouper. ieee. org/groups/802/11/ ihttp: //www. etsi. org/technicalactiv/hiperlan 2. htm ihttp: //www. bluetooth. com ihttp: //www. ietf. org/html. charters/manet-charter. html 132 (c) 2002 Nitin Vaidya, UIUC

Tutorial on Mobile Ad Hoc Networks g www. crhc. uiuc. edu/~nhv 133 (c) 2002 Nitin Vaidya, UIUC

Thank you !! For more information, send e-mail to Nitin Vaidya at nhv@uiuc. edu © 2002 Nitin Vaidya 134