Deploying MPLS Traffic Engineering Rodrigo Linhares rlinharecisco com





















- Slides: 96

Deploying MPLS Traffic Engineering Rodrigo Linhares rlinhare@cisco. com Consulting Systems Engineering Latin America Core Technologies Group © 2001, Cisco Systems, Inc. All rights reserved. 1

What It Is, How It Works, and How to Use It © 2001, Cisco Systems, Inc. All rights reserved. 2

Agenda • How MPLS-TE Works • Basic Configuration • Knobs! • Deploying and Designing © 2001, Cisco Systems, Inc. All rights reserved. 3

How MPLS-TE Works • How MPLS-TE works What good is MPLS-TE? Information distribution Path calculation Path setup Forwarding traffic down a tunnel © 2001, Cisco Systems, Inc. All rights reserved. 4

What Good Is MPLS-TE? • There are three kinds of networks 1. Those that have plenty of bandwidth everywhere 2. Those with congestion in some places, but not in others 3. Those with constant congestion everywhere • The first kind always evolves into the second kind! © 2001, Cisco Systems, Inc. All rights reserved. 5

What Good Is MPLS-TE? • MPLS-TE introduces a 4 th kind: 1. Those that have plenty of bandwidth everywhere 2. Those with congestion in some places, but not in others 3. Those with constant congestion everywhere 4. Those that use all of their bandwidth to its maximum efficiency, regardless of shortest-path routing! • MPLS-TE can help turn #2 into #4 If you have #1, you probably don’t need MPLS-TE—yet If you have #3, you’re stuck—you either need more bandwidth (or less traffic) © 2001, Cisco Systems, Inc. All rights reserved. 6

What Good Is MPLS-TE? What Is MPLS-TE? • Multi protocol label switching— traffic engineering What Is It Not? • Magic problem solving labor substitute which is totally effortless This Stuff Takes Work, but It’s Worth It!!! © 2001, Cisco Systems, Inc. All rights reserved. 7

Information Distribution • You need a link-state protocol as your IGP IS-IS or OSPF • Link-state requirement is only for MPLS-TE! Not a requirement for VPNs, etc! © 2001, Cisco Systems, Inc. All rights reserved. 8

Need for a Link-State Protocol • Why do I need a link-state protocol? To make sure info gets flooded To build a picture of the entire network © 2001, Cisco Systems, Inc. All rights reserved. 9

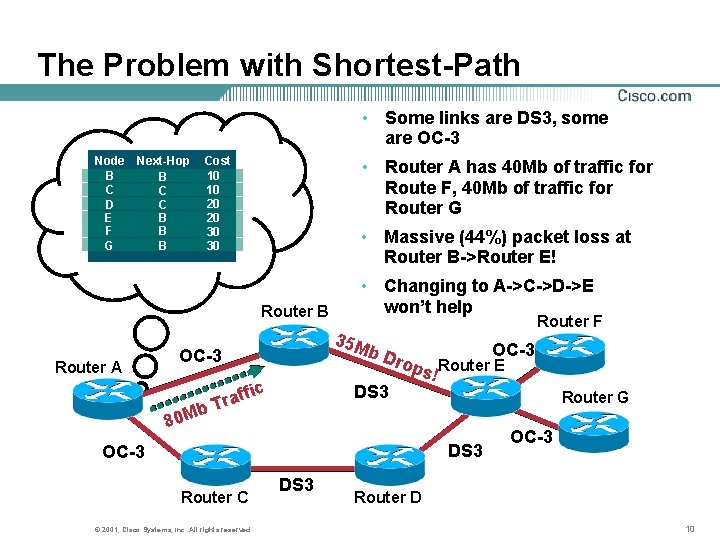
The Problem with Shortest-Path • Some links are DS 3, some are OC-3 Node B C D E F G Next-Hop B C C B B B Cost 10 10 20 20 30 30 • Router A has 40 Mb of traffic for Route F, 40 Mb of traffic for Router G • Massive (44%) packet loss at Router B->Router E! Router B Router A Router F 35 M OC-3 b. D rop Router E s! DS 3 OC-3 b 80 M • Changing to A->C->D->E won’t help ffic a r T DS 3 OC-3 Router C © 2001, Cisco Systems, Inc. All rights reserved. DS 3 Router G OC-3 Router D 10

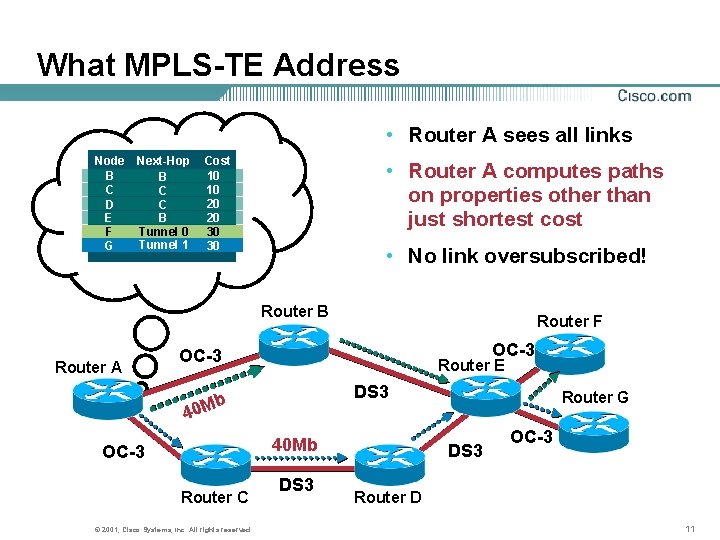
What MPLS-TE Address • Router A sees all links Node B C D E F G Next-Hop B C C B Tunnel 0 Tunnel 1 Cost 10 10 20 20 30 30 • Router A computes paths on properties other than just shortest cost • No link oversubscribed! Router B Router A Router F OC-3 Router E DS 3 b 40 Mb OC-3 Router C © 2001, Cisco Systems, Inc. All rights reserved. DS 3 Router G DS 3 OC-3 Router D 11

How MPLS-TE Works • How MPLS-TE works What good is MPLS-TE? Information distribution Path calculation Path setup Forwarding traffic down a tunnel © 2001, Cisco Systems, Inc. All rights reserved. 12

Information Distribution • IS-IS Uses Type 22 TLVs See draft-ietf-isis-traffic • OSPF Uses type 10 (opaque area—local) LSAs See draft-katz-yeung-ospf-traffic © 2001, Cisco Systems, Inc. All rights reserved. 13

Information Distribution • IS-IS and OSPF propagate the same information! Link identification TE metric Bandwidth information (physical, reserveable, available) Attribute flags © 2001, Cisco Systems, Inc. All rights reserved. 14

Information Distribution • TE flooding is local to a single {area|level} • Inter-{area|level} TE harder, but possible (think PNNI) © 2001, Cisco Systems, Inc. All rights reserved. 15

How MPLS-TE Works • How MPLS-TE works What good is MPLS-TE? Information distribution Path calculation Path setup Forwarding traffic down a tunnel © 2001, Cisco Systems, Inc. All rights reserved. 16

Path Calculation • Modified Dijkstra at tunnel head-end • Often referred to as CSPF Constrained SPF • …or PCALC (path calculation) © 2001, Cisco Systems, Inc. All rights reserved. 17

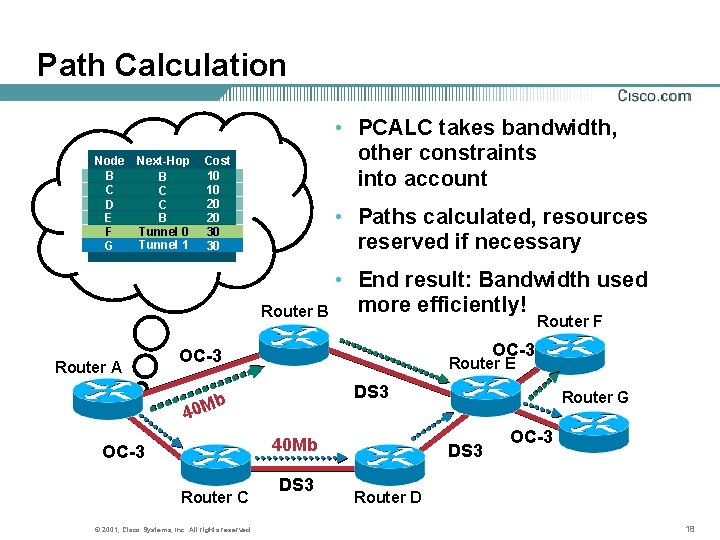
Path Calculation Node B C D E F G Next-Hop B C C B Tunnel 0 Tunnel 1 • PCALC takes bandwidth, other constraints into account Cost 10 10 20 20 30 30 • Paths calculated, resources reserved if necessary • End result: Bandwidth used more efficiently! Router B Router F Router A OC-3 Router E DS 3 b 40 Mb OC-3 Router C © 2001, Cisco Systems, Inc. All rights reserved. DS 3 Router G DS 3 OC-3 Router D 18

Path Calculation • What if there’s more than one path that meets the minimum requirements (bandwidth, etc. )? • PCALC algorithm: Find all paths with the lowest IGP cost Then pick the path with the highest minimum available bandwidth along the path Then pick the path with the lowest hop count (not IGP cost, but hop count) Then just pick one path at random © 2001, Cisco Systems, Inc. All rights reserved. 19

How MPLS-TE Works • How MPLS-TE works What good is MPLS-TE? Information distribution Path calculation Path setup Forwarding traffic down a tunnel © 2001, Cisco Systems, Inc. All rights reserved. 20

Path Setup • Cisco MPLS-TE uses RSVP • RFC 2205, plus draft-ietf-mpls-rsvp-lsp-tunnel (RSVP-TE) • Once the path is calculated, it is handed to RSVP • RSVP uses PATH and RESV messages to request an LSP along the calculated path © 2001, Cisco Systems, Inc. All rights reserved. 21

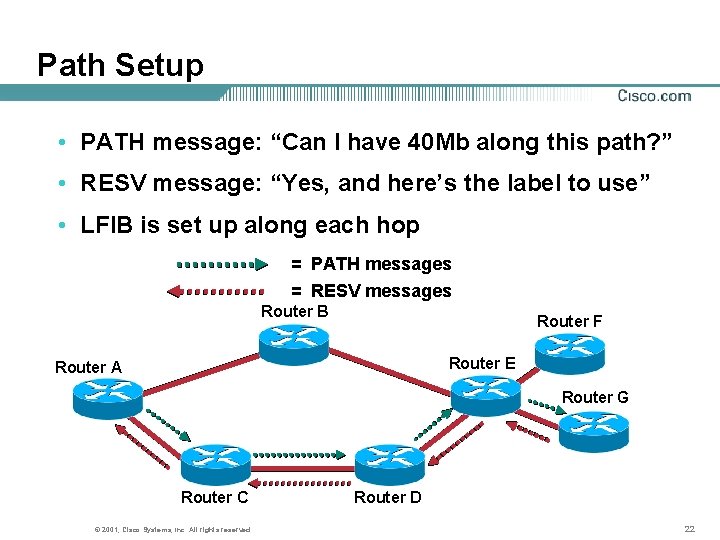
Path Setup • PATH message: “Can I have 40 Mb along this path? ” • RESV message: “Yes, and here’s the label to use” • LFIB is set up along each hop = PATH messages = RESV messages Router B Router F Router E Router A Router G Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D 22

How MPLS-TE Works • How MPLS-TE works What good is MPLS-TE? Information distribution Path calculation Path setup Forwarding traffic down a tunnel © 2001, Cisco Systems, Inc. All rights reserved. 23

Forwarding Traffic Down a Tunnel • There are three ways traffic can be forwarded down a TE tunnel Auto-route Static routes Policy routing • With the first two, MPLS-TE gets you unequal cost load balancing © 2001, Cisco Systems, Inc. All rights reserved. 24

Auto-Route • Auto-route = “Use the tunnel as a directly connected link for SPF purposes” • This is not the CSPF (for path determination), but the regular IGP SPF (route determination) © 2001, Cisco Systems, Inc. All rights reserved. 25

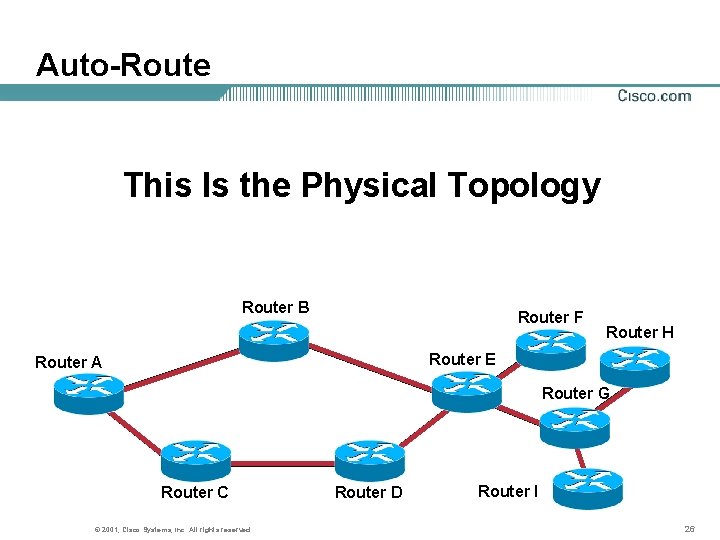
Auto-Route This Is the Physical Topology Router B Router F Router H Router E Router A Router G Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 26

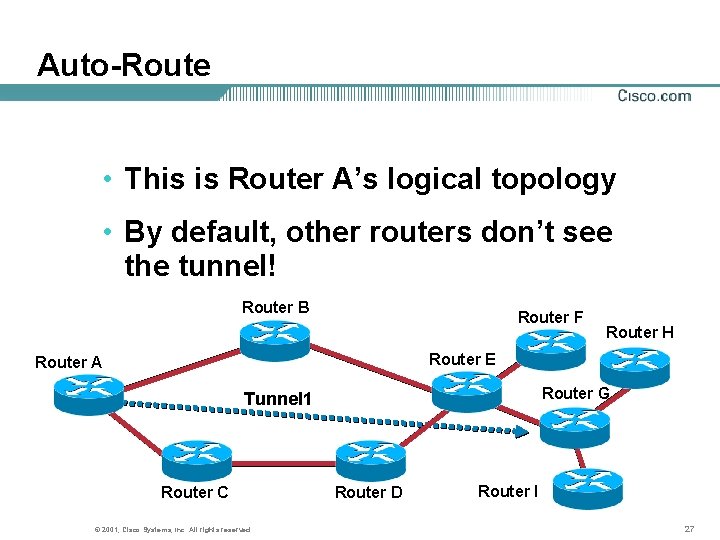
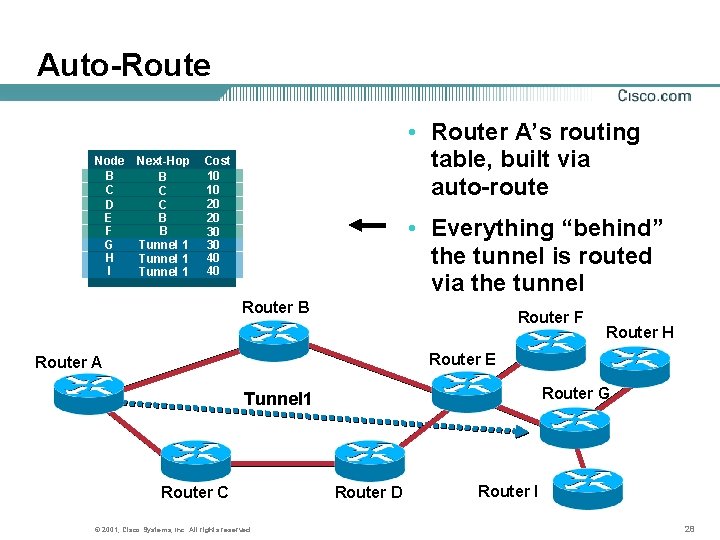
Auto-Route • This is Router A’s logical topology • By default, other routers don’t see the tunnel! Router B Router F Router H Router E Router A Router G Tunnel 1 Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 27

Auto-Route Node B C D E F G H I Next-Hop B C C B B Tunnel 1 • Router A’s routing table, built via auto-route Cost 10 10 20 20 30 30 40 40 • Everything “behind” the tunnel is routed via the tunnel Router B Router F Router H Router E Router A Router G Tunnel 1 Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 28

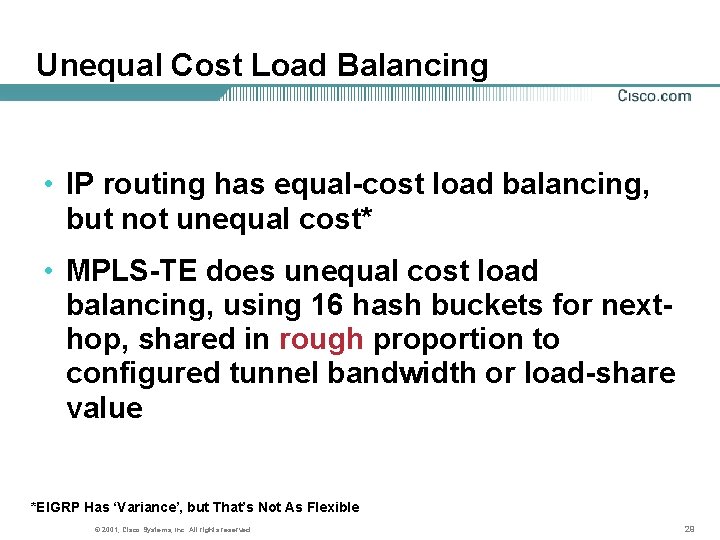
Unequal Cost Load Balancing • IP routing has equal-cost load balancing, but not unequal cost* • MPLS-TE does unequal cost load balancing, using 16 hash buckets for nexthop, shared in rough proportion to configured tunnel bandwidth or load-share value *EIGRP Has ‘Variance’, but That’s Not As Flexible © 2001, Cisco Systems, Inc. All rights reserved. 29

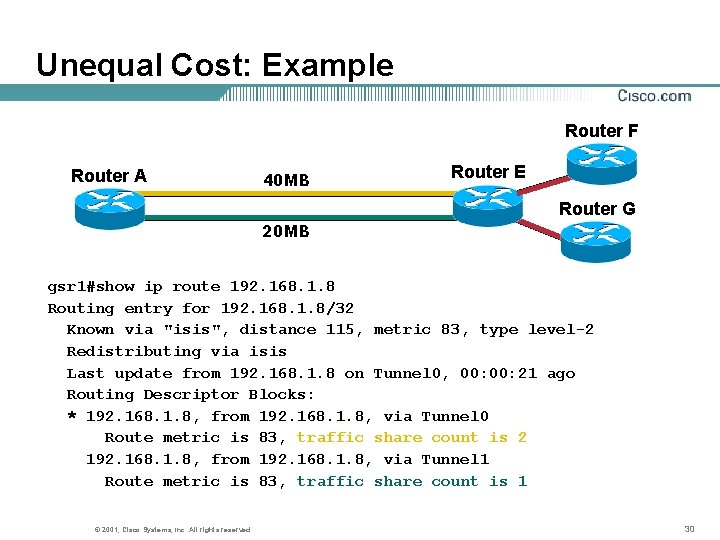
Unequal Cost: Example Router F Router A 40 MB Router E Router G 20 MB gsr 1#show ip route 192. 168. 1. 8 Routing entry for 192. 168. 1. 8/32 Known via "isis", distance 115, metric 83, type level-2 Redistributing via isis Last update from 192. 168. 1. 8 on Tunnel 0, 00: 21 ago Routing Descriptor Blocks: * 192. 168. 1. 8, from 192. 168. 1. 8, via Tunnel 0 Route metric is 83, traffic share count is 2 192. 168. 1. 8, from 192. 168. 1. 8, via Tunnel 1 Route metric is 83, traffic share count is 1 © 2001, Cisco Systems, Inc. All rights reserved. 30

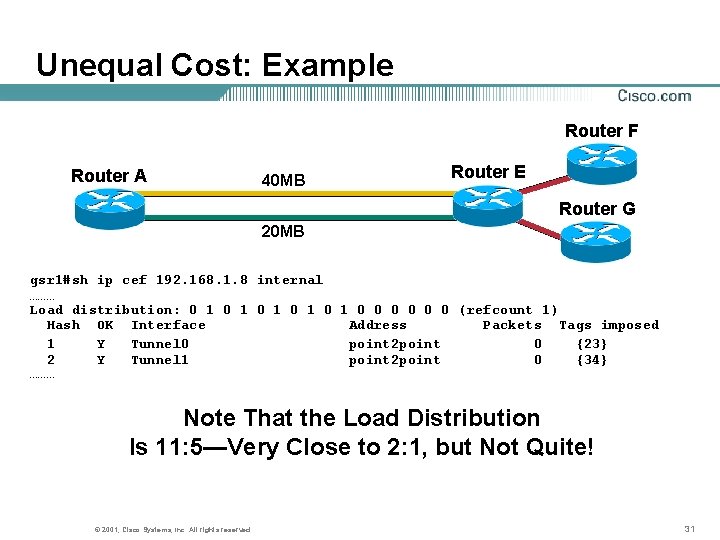
Unequal Cost: Example Router F Router A 40 MB Router E Router G 20 MB gsr 1#sh ip cef 192. 168. 1. 8 internal ……… Load distribution: 0 1 0 1 0 1 0 0 0 (refcount 1) Hash OK Interface Address Packets Tags imposed 1 Y Tunnel 0 point 2 point 0 {23} 2 Y Tunnel 1 point 2 point 0 {34} ……… Note That the Load Distribution Is 11: 5—Very Close to 2: 1, but Not Quite! © 2001, Cisco Systems, Inc. All rights reserved. 31

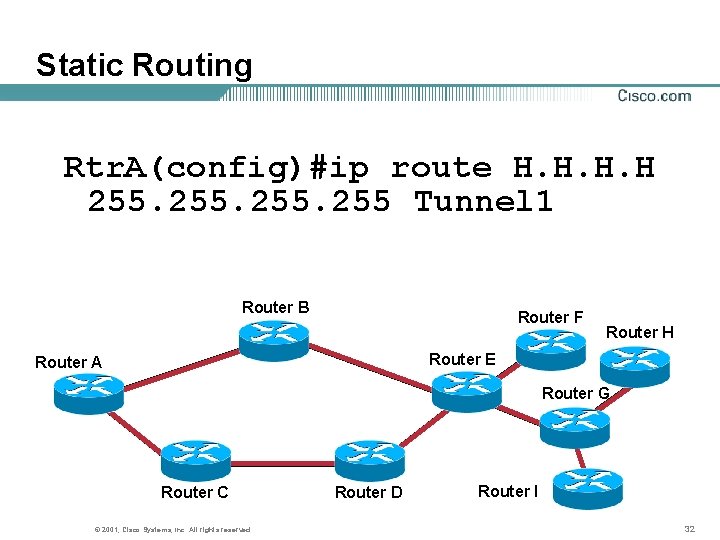
Static Routing Rtr. A(config)#ip route H. H 255 Tunnel 1 Router B Router F Router H Router E Router A Router G Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 32

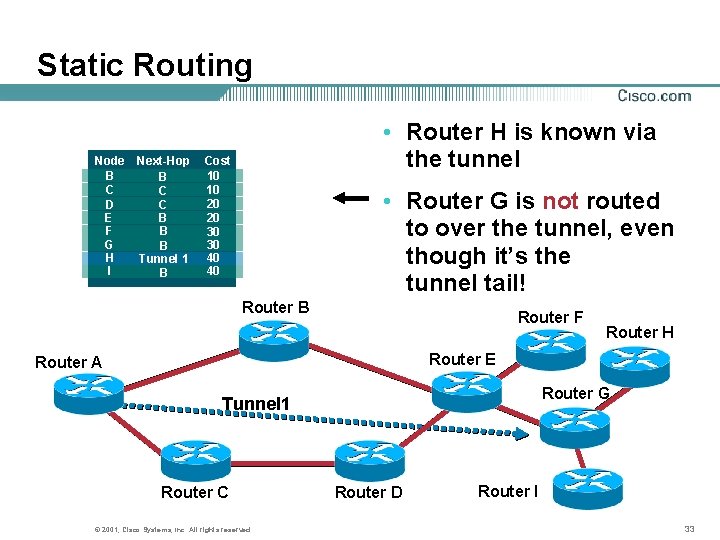
Static Routing Node B C D E F G H I Next-Hop B C C B B B Tunnel 1 B • Router H is known via the tunnel Cost 10 10 20 20 30 30 40 40 • Router G is not routed to over the tunnel, even though it’s the tunnel tail! Router B Router F Router H Router E Router A Router G Tunnel 1 Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 33

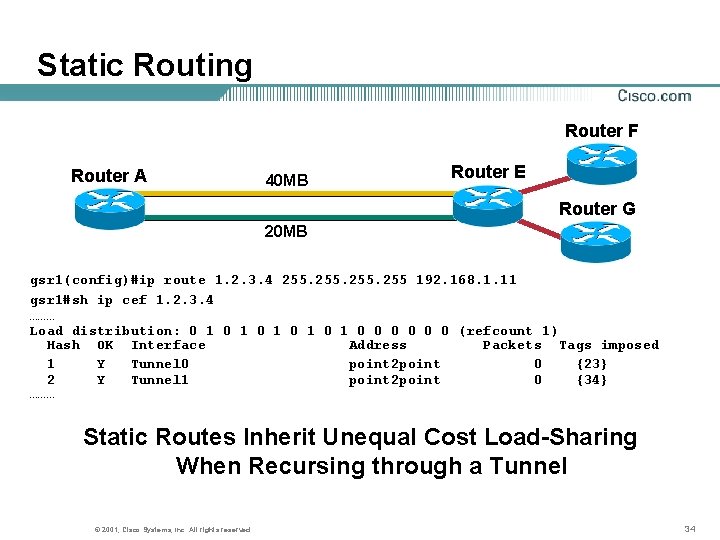
Static Routing Router F Router A 40 MB Router E Router G 20 MB gsr 1(config)#ip route 1. 2. 3. 4 255 192. 168. 1. 11 gsr 1#sh ip cef 1. 2. 3. 4 ……… Load distribution: 0 1 0 1 0 1 0 0 0 (refcount 1) Hash OK Interface Address Packets Tags imposed 1 Y Tunnel 0 point 2 point 0 {23} 2 Y Tunnel 1 point 2 point 0 {34} ……… Static Routes Inherit Unequal Cost Load-Sharing When Recursing through a Tunnel © 2001, Cisco Systems, Inc. All rights reserved. 34

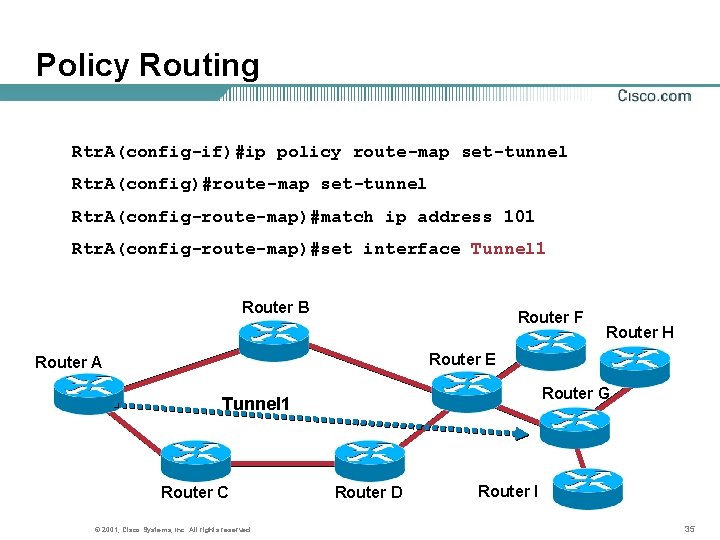
Policy Routing Rtr. A(config-if)#ip policy route-map set-tunnel Rtr. A(config)#route-map set-tunnel Rtr. A(config-route-map)#match ip address 101 Rtr. A(config-route-map)#set interface Tunnel 1 Router B Router F Router H Router E Router A Router G Tunnel 1 Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 35

Policy Routing Node B C D E F G H I Next-Hop B C C B B B • Routing table isn’t affected by policy routing Cost 10 10 20 20 30 30 40 40 • Need (12. 0(16)ST or 12. 2 T) or higher for ‘set interface tunnel’ to work Router B Router F Router H Router E Router A Router G Tunnel 1 Router C © 2001, Cisco Systems, Inc. All rights reserved. Router D Router I 36

Forwarding Traffic down a Tunnel • You can use any combination of autoroute, static routes, or PBR • …But simple is better unless you have a good reason • Recommendation: Either auto-route or statics to BGP next-hops, depending on your needs © 2001, Cisco Systems, Inc. All rights reserved. 37

Agenda • Prerequisites • How MPLS-TE Works • Basic Configuration • Knobs! • Deploying and Designing © 2001, Cisco Systems, Inc. All rights reserved. 38

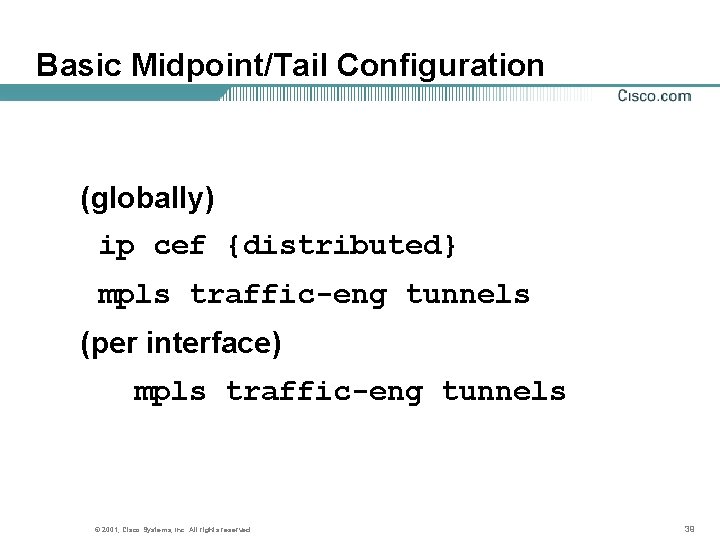
Basic Midpoint/Tail Configuration (globally) ip cef {distributed} mpls traffic-eng tunnels (per interface) mpls traffic-eng tunnels © 2001, Cisco Systems, Inc. All rights reserved. 39

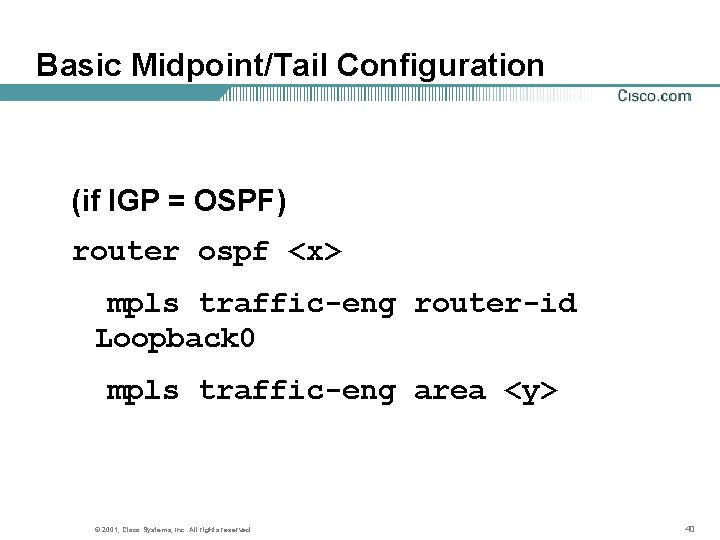
Basic Midpoint/Tail Configuration (if IGP = OSPF) router ospf <x> mpls traffic-eng router-id Loopback 0 mpls traffic-eng area <y> © 2001, Cisco Systems, Inc. All rights reserved. 40

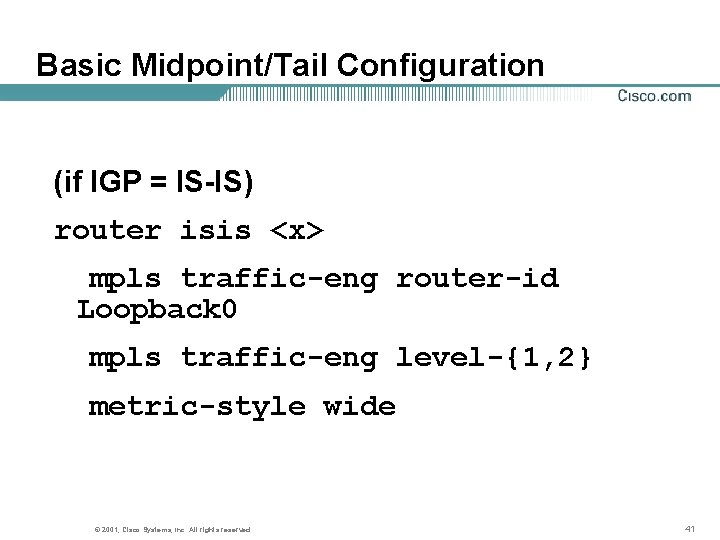
Basic Midpoint/Tail Configuration (if IGP = IS-IS) router isis <x> mpls traffic-eng router-id Loopback 0 mpls traffic-eng level-{1, 2} metric-style wide © 2001, Cisco Systems, Inc. All rights reserved. 41

Basic Head-End Configuration • Head-end needs the 4– 5 ‘mid/tail’ lines • But wait—there’s more! © 2001, Cisco Systems, Inc. All rights reserved. 42

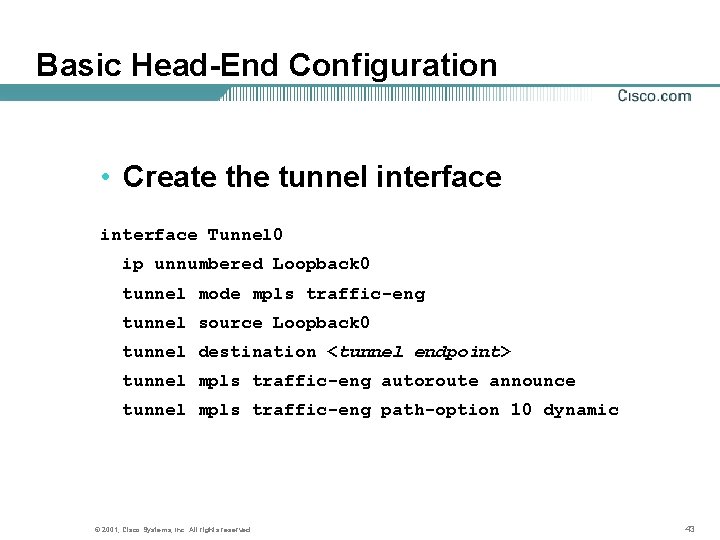
Basic Head-End Configuration • Create the tunnel interface Tunnel 0 ip unnumbered Loopback 0 tunnel mode mpls traffic-eng tunnel source Loopback 0 tunnel destination <tunnel endpoint> tunnel mpls traffic-eng autoroute announce tunnel mpls traffic-eng path-option 10 dynamic © 2001, Cisco Systems, Inc. All rights reserved. 43

Basic Head-End Configuration • Total configuration: 1 line globally 1 line per interface 2 lines if OSPF 3 lines if IS-IS + 7 lines per tunnel at head-end Not really much to the basic configuration © 2001, Cisco Systems, Inc. All rights reserved. 44

Agenda • Prerequisites • How MPLS-TE Works • Basic Configuration • Knobs! • Deploying and Designing © 2001, Cisco Systems, Inc. All rights reserved. 45

Knobs! • Influencing the path selection • Auto-bandwidth • Fast reroute • Diff. Serv-Aware Traffic Engineering © 2001, Cisco Systems, Inc. All rights reserved. 46

Knobs! • Influencing the path selection Bandwidth Priority Administrative weight Attributes and affinity © 2001, Cisco Systems, Inc. All rights reserved. 47

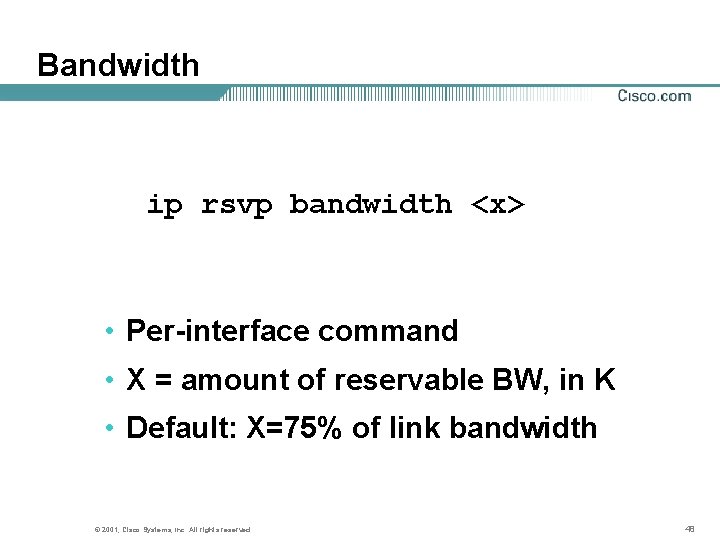
Bandwidth ip rsvp bandwidth <x> • Per-interface command • X = amount of reservable BW, in K • Default: X=75% of link bandwidth © 2001, Cisco Systems, Inc. All rights reserved. 48

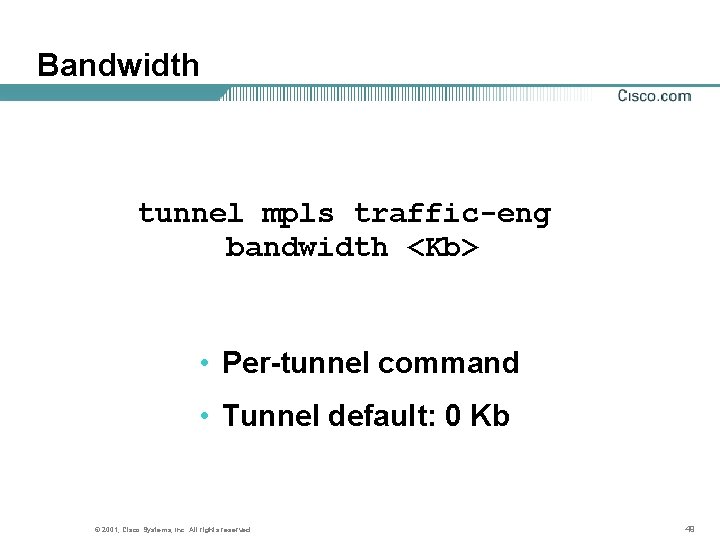
Bandwidth tunnel mpls traffic-eng bandwidth <Kb> • Per-tunnel command • Tunnel default: 0 Kb © 2001, Cisco Systems, Inc. All rights reserved. 49

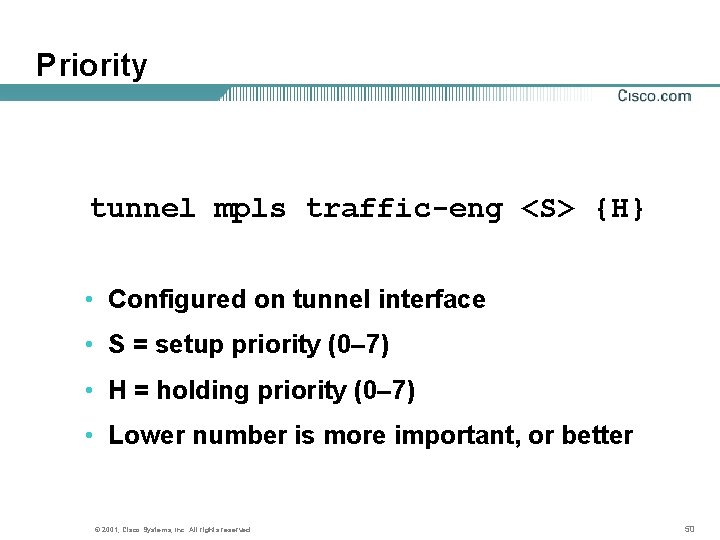
Priority tunnel mpls traffic-eng <S> {H} • Configured on tunnel interface • S = setup priority (0– 7) • H = holding priority (0– 7) • Lower number is more important, or better © 2001, Cisco Systems, Inc. All rights reserved. 50

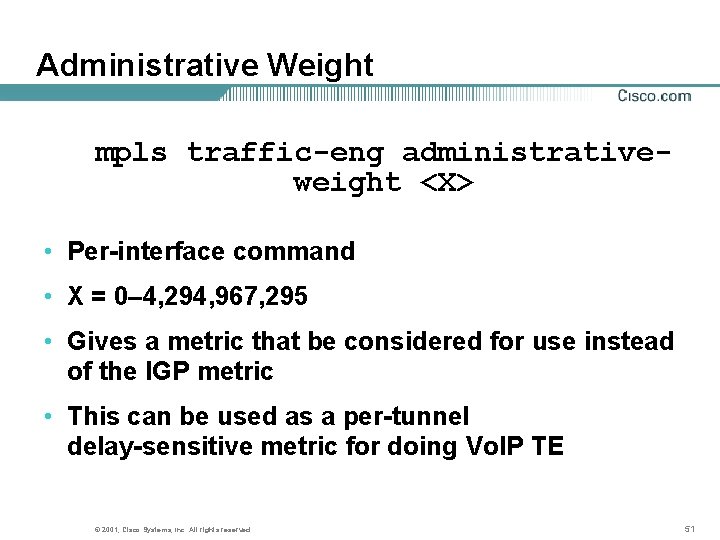
Administrative Weight mpls traffic-eng administrativeweight <X> • Per-interface command • X = 0– 4, 294, 967, 295 • Gives a metric that be considered for use instead of the IGP metric • This can be used as a per-tunnel delay-sensitive metric for doing Vo. IP TE © 2001, Cisco Systems, Inc. All rights reserved. 51

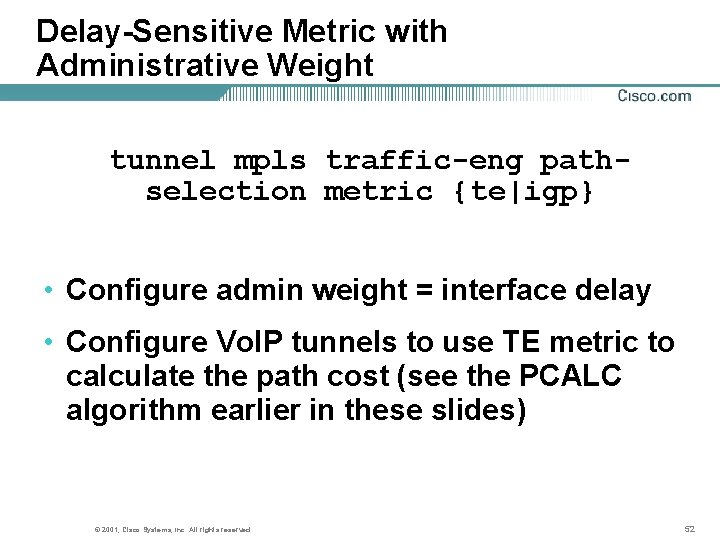
Delay-Sensitive Metric with Administrative Weight tunnel mpls traffic-eng pathselection metric {te|igp} • Configure admin weight = interface delay • Configure Vo. IP tunnels to use TE metric to calculate the path cost (see the PCALC algorithm earlier in these slides) © 2001, Cisco Systems, Inc. All rights reserved. 52

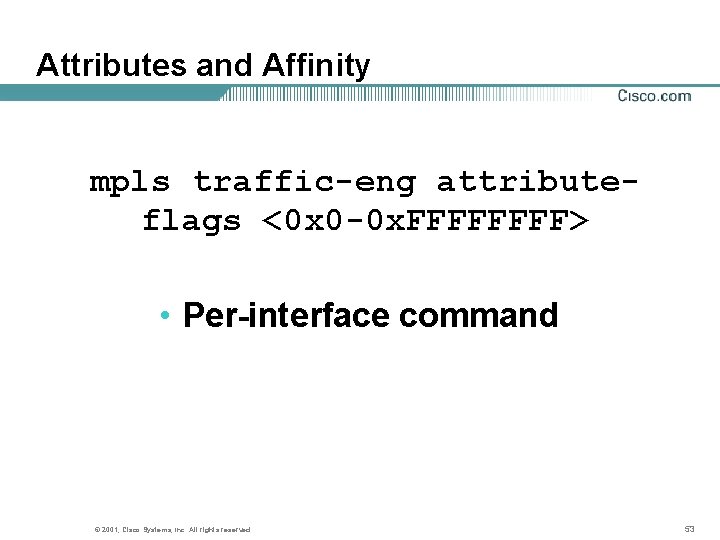
Attributes and Affinity mpls traffic-eng attributeflags <0 x 0 -0 x. FFFF> • Per-interface command © 2001, Cisco Systems, Inc. All rights reserved. 53

Attributes and Affinity tunnel mpls traffic-eng affinity <0 x 0 -0 x. FFFF> {mask <0 x 00 x. FFFF>} • Per-tunnel command • Mask is a collection of do-care bits • ‘affinity 0 x 2 mask 0 x. A’means ‘I care about bits 1 and 3 (with the values 2 and 8); bit 1 must be set, bit 3 must be 0’ © 2001, Cisco Systems, Inc. All rights reserved. 54

Attributes and Affinity • Q: How should I use link attributes? • A: To exclude some links from consideration by some tunnels • …So give a satellite link an attribute of 0 x 2, and any Vo. IP tunnels can be configured with ‘affinity 0 x 0 mask 0 x 2’ © 2001, Cisco Systems, Inc. All rights reserved. 55

Knobs! • Influencing the path selection • Auto-bandwidth • Fast reroute • Diff. Serv-Aware Traffic Engineering © 2001, Cisco Systems, Inc. All rights reserved. 56

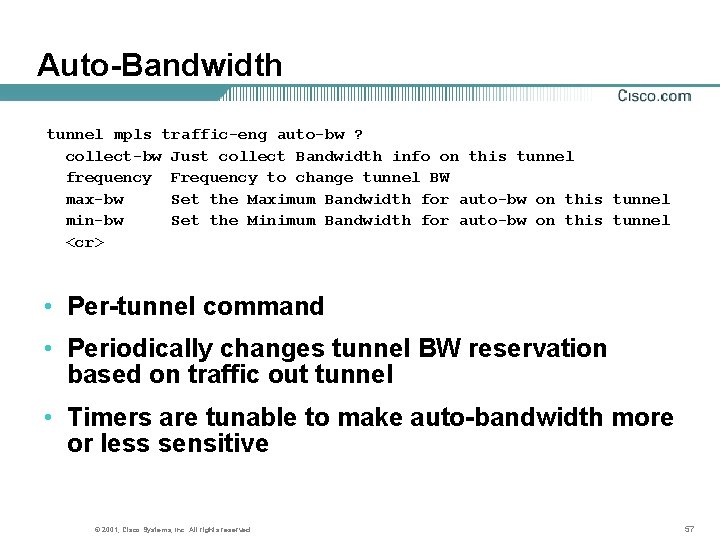
Auto-Bandwidth tunnel mpls traffic-eng auto-bw ? collect-bw Just collect Bandwidth info on this tunnel frequency Frequency to change tunnel BW max-bw Set the Maximum Bandwidth for auto-bw on this tunnel min-bw Set the Minimum Bandwidth for auto-bw on this tunnel <cr> • Per-tunnel command • Periodically changes tunnel BW reservation based on traffic out tunnel • Timers are tunable to make auto-bandwidth more or less sensitive © 2001, Cisco Systems, Inc. All rights reserved. 57

Knobs! • Influencing the path selection • Auto-bandwidth • Fast reroute • Diff. Serv-Aware Traffic Engineering © 2001, Cisco Systems, Inc. All rights reserved. 58

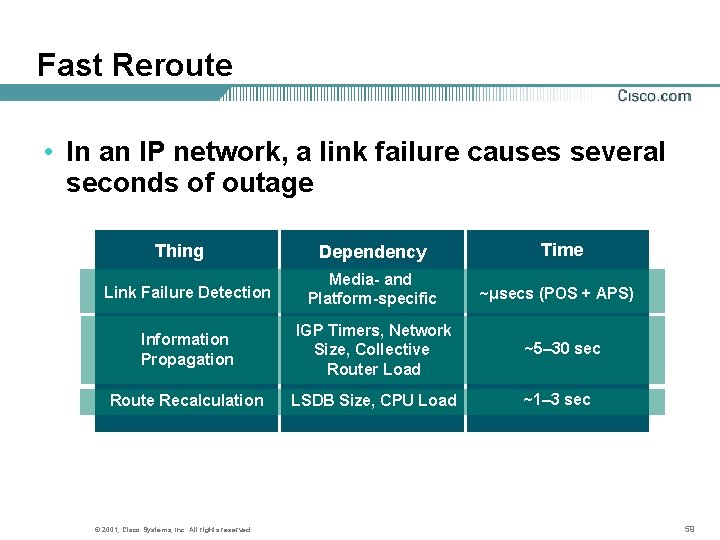
Fast Reroute • In an IP network, a link failure causes several seconds of outage Thing Dependency Time Link Failure Detection Media- and Platform-specific Information Propagation IGP Timers, Network Size, Collective Router Load ~5– 30 sec Route Recalculation LSDB Size, CPU Load ~1– 3 sec © 2001, Cisco Systems, Inc. All rights reserved. ~μsecs (POS + APS) 59

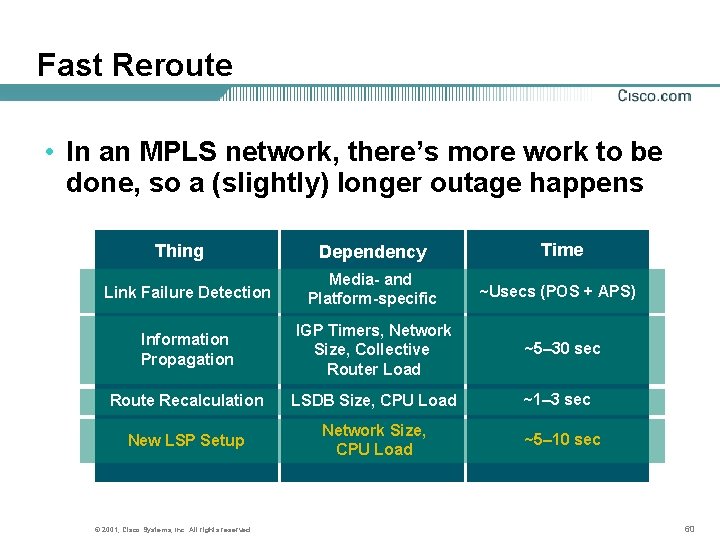
Fast Reroute • In an MPLS network, there’s more work to be done, so a (slightly) longer outage happens Dependency Time Link Failure Detection Media- and Platform-specific ~Usecs (POS + APS) Information Propagation IGP Timers, Network Size, Collective Router Load ~5– 30 sec Route Recalculation LSDB Size, CPU Load ~1– 3 sec New LSP Setup Network Size, CPU Load Thing © 2001, Cisco Systems, Inc. All rights reserved. ~5– 10 sec 60

Three Kinds of Fast Reroute • Link protection • Node protection • Path protection © 2001, Cisco Systems, Inc. All rights reserved. 61

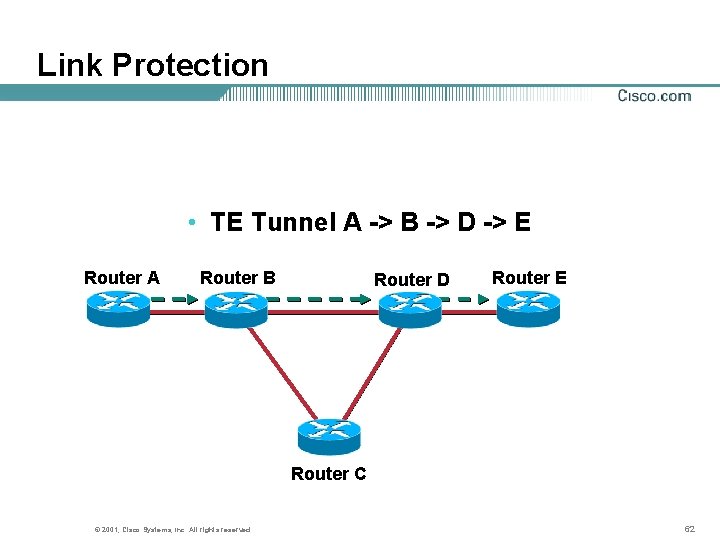
Link Protection • TE Tunnel A -> B -> D -> E Router A Router B Router D Router E Router C © 2001, Cisco Systems, Inc. All rights reserved. 62

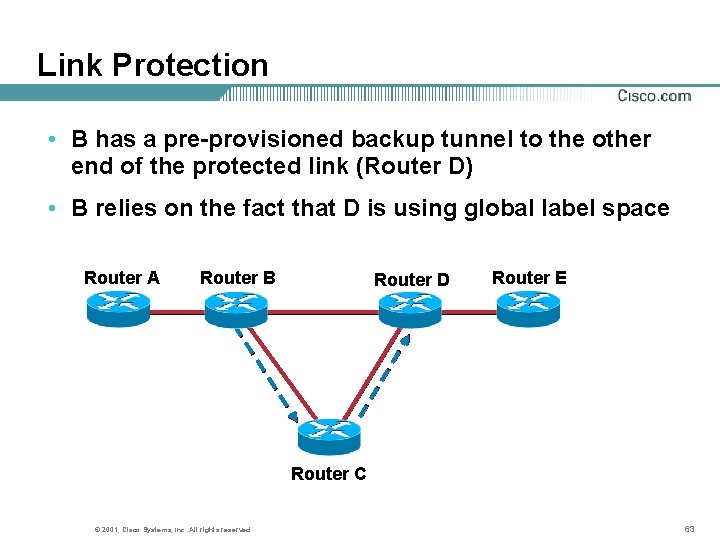
Link Protection • B has a pre-provisioned backup tunnel to the other end of the protected link (Router D) • B relies on the fact that D is using global label space Router A Router B Router D Router E Router C © 2001, Cisco Systems, Inc. All rights reserved. 63

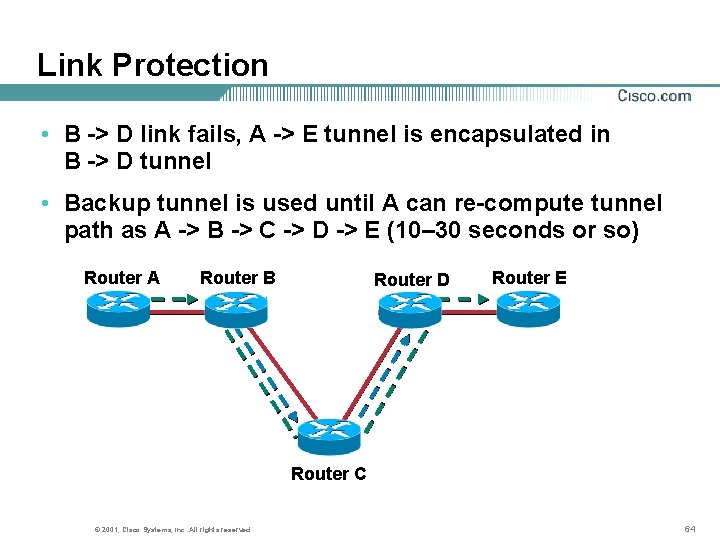
Link Protection • B -> D link fails, A -> E tunnel is encapsulated in B -> D tunnel • Backup tunnel is used until A can re-compute tunnel path as A -> B -> C -> D -> E (10– 30 seconds or so) Router A Router B Router D Router E Router C © 2001, Cisco Systems, Inc. All rights reserved. 64

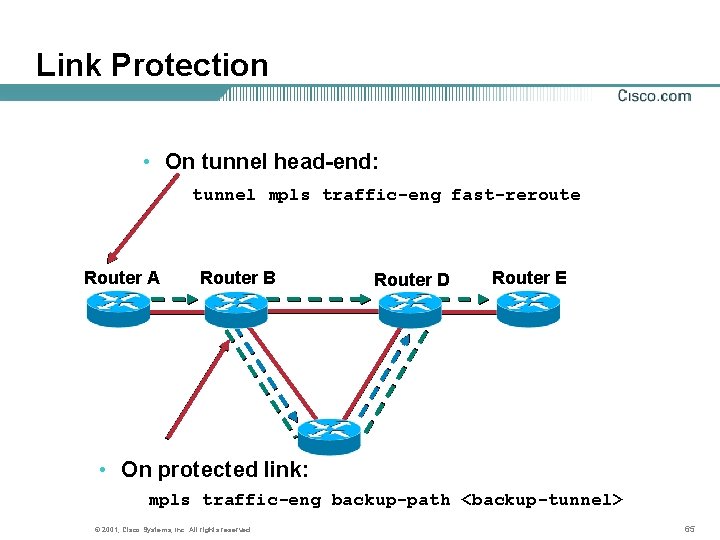
Link Protection • On tunnel head-end: tunnel mpls traffic-eng fast-reroute Router A Router B Router D Router E • On protected link: mpls traffic-eng backup-path <backup-tunnel> © 2001, Cisco Systems, Inc. All rights reserved. 65

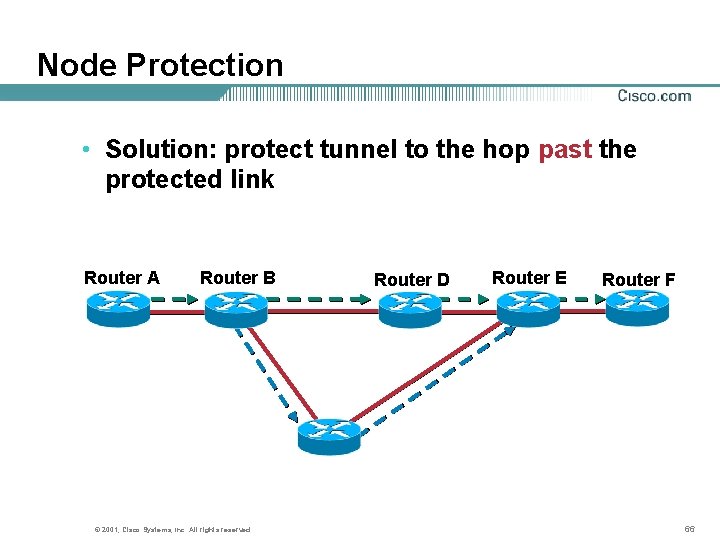
Node Protection • Solution: protect tunnel to the hop past the protected link Router A Router B © 2001, Cisco Systems, Inc. All rights reserved. Router D Router E Router F 66

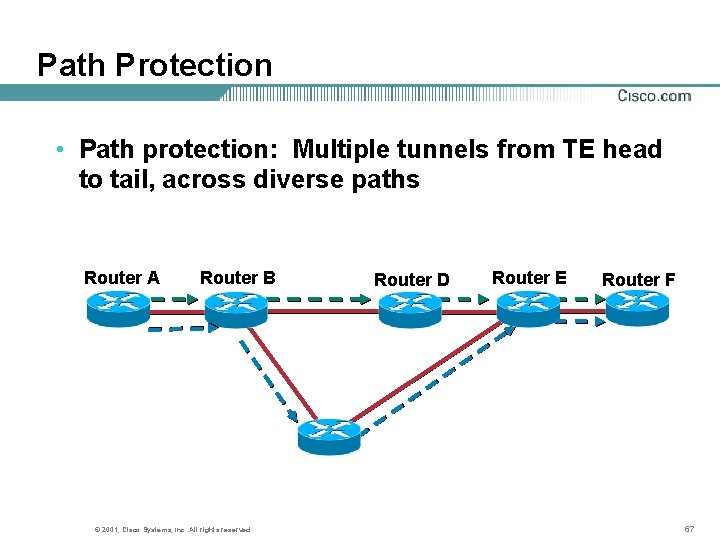
Path Protection • Path protection: Multiple tunnels from TE head to tail, across diverse paths Router A Router B © 2001, Cisco Systems, Inc. All rights reserved. Router D Router E Router F 67

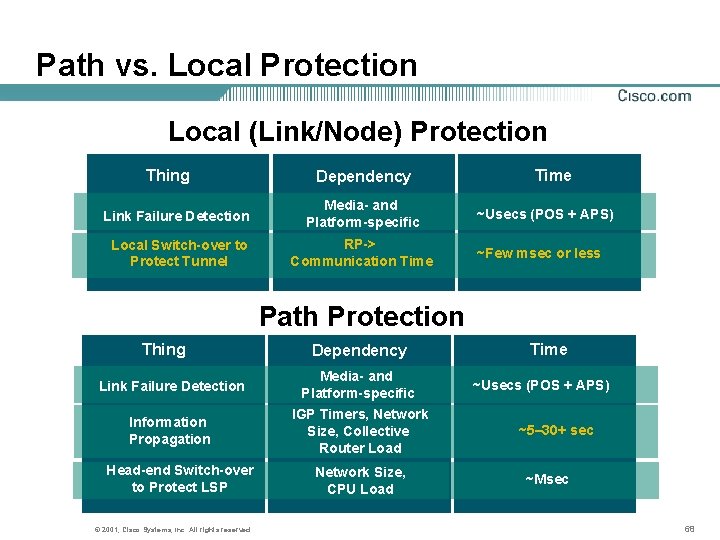
Path vs. Local Protection Local (Link/Node) Protection Thing Dependency Link Failure Detection Media- and Platform-specific Local Switch-over to Protect Tunnel RP-> Communication Time ~Usecs (POS + APS) ~Few msec or less Path Protection Thing Dependency Link Failure Detection Media- and Platform-specific Information Propagation IGP Timers, Network Size, Collective Router Load Head-end Switch-over to Protect LSP © 2001, Cisco Systems, Inc. All rights reserved. Network Size, CPU Load Time ~Usecs (POS + APS) ~5– 30+ sec ~Msec 68

Knobs! • Influencing the path selection • Auto-bandwidth • Fast reroute • Diff. Serv-Aware Traffic Engineering © 2001, Cisco Systems, Inc. All rights reserved. 69

Diff. Serv-Aware Traffic Engineering • MPLS can advertise and reserve bandwidth on a link • Works great, but what if you send a mix of LLQ (EF) and BE traffic down a TE tunnel? • Need some way to differentiate and reserve LLQ (EF) bandwidth on a link © 2001, Cisco Systems, Inc. All rights reserved. 70

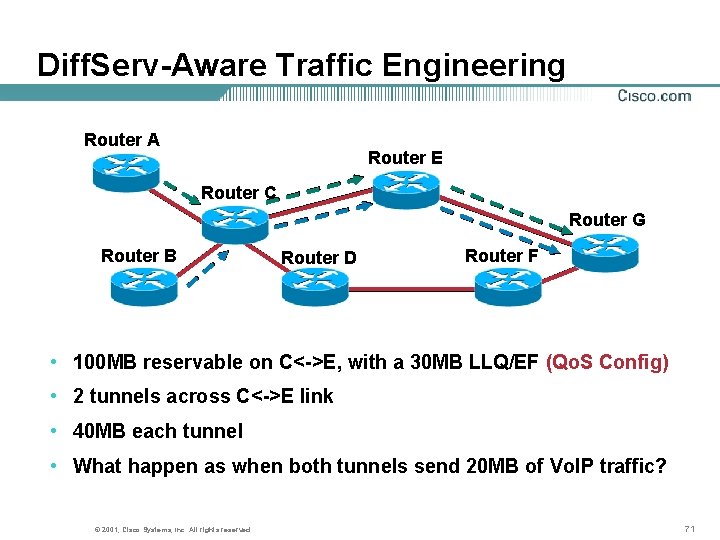
Diff. Serv-Aware Traffic Engineering Router A Router E Router C Router G Router B Router D Router F • 100 MB reservable on C<->E, with a 30 MB LLQ/EF (Qo. S Config) • 2 tunnels across C<->E link • 40 MB each tunnel • What happen as when both tunnels send 20 MB of Vo. IP traffic? © 2001, Cisco Systems, Inc. All rights reserved. 71

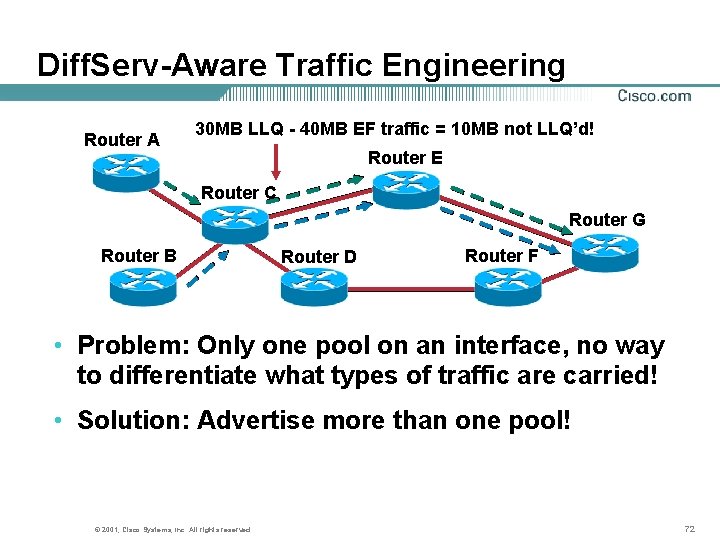
Diff. Serv-Aware Traffic Engineering Router A 30 MB LLQ - 40 MB EF traffic = 10 MB not LLQ’d! Router E Router C Router G Router B Router D Router F • Problem: Only one pool on an interface, no way to differentiate what types of traffic are carried! • Solution: Advertise more than one pool! © 2001, Cisco Systems, Inc. All rights reserved. 72

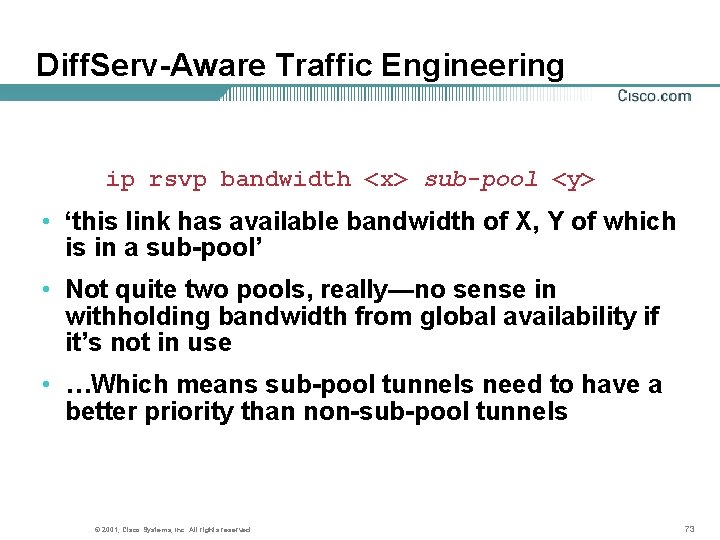
Diff. Serv-Aware Traffic Engineering ip rsvp bandwidth <x> sub-pool <y> • ‘this link has available bandwidth of X, Y of which is in a sub-pool’ • Not quite two pools, really—no sense in withholding bandwidth from global availability if it’s not in use • …Which means sub-pool tunnels need to have a better priority than non-sub-pool tunnels © 2001, Cisco Systems, Inc. All rights reserved. 73

Diff. Serv-Aware Traffic Engineering tunnel mpls traffic-eng bandwidth <x> sub-pool • ‘This tunnel wants to reserve X Kbps from a sub-pool’ • Sub-pool bandwidth is looked at instead of global pool bandwidth • If sub-pool bandwidth is not available, tunnel won’t come up © 2001, Cisco Systems, Inc. All rights reserved. 74

Agenda • Prerequisites • How MPLS-TE Works • Basic Configuration • Knobs! • Deploying and Designing © 2001, Cisco Systems, Inc. All rights reserved. 75

Deploying and Designing • Deployment methodologies • Scalability • Management • Security © 2001, Cisco Systems, Inc. All rights reserved. 76

Deployment Methodologies • Two ways to deploy MPLS-TE As needed to clear up congestion Full mesh between a set of routers • Both methods are valid, both have their pros and cons © 2001, Cisco Systems, Inc. All rights reserved. 77

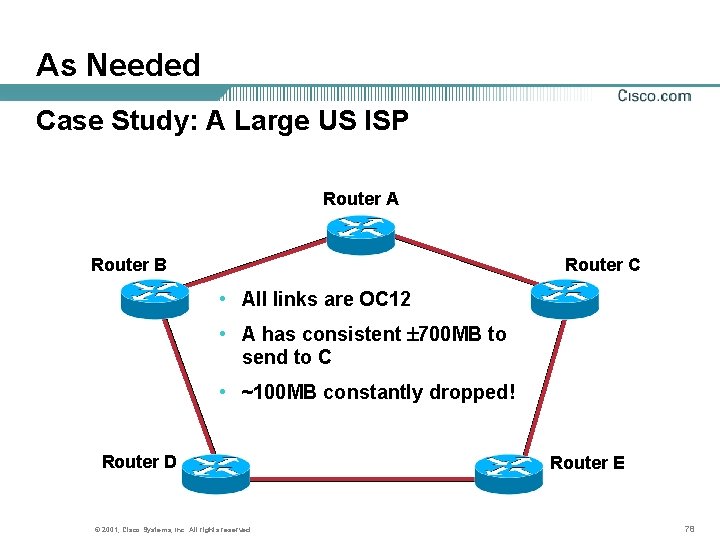
As Needed Case Study: A Large US ISP Router A Router B Router C • All links are OC 12 • A has consistent 700 MB to send to C • ~100 MB constantly dropped! Router D © 2001, Cisco Systems, Inc. All rights reserved. Router E 78

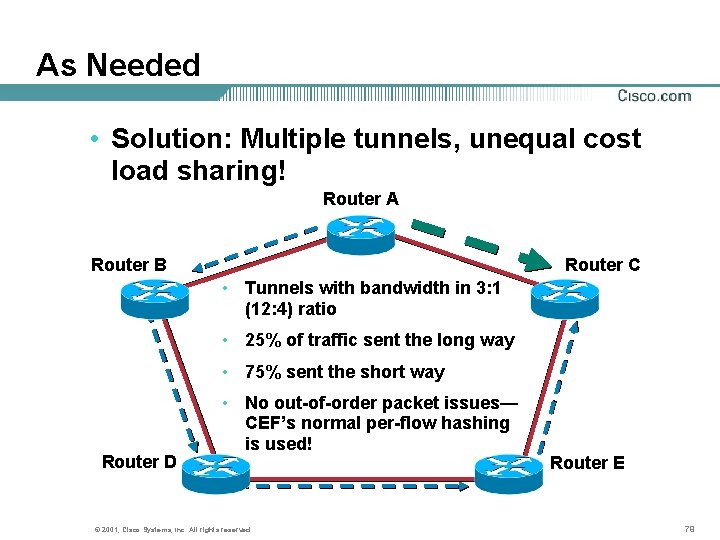
As Needed • Solution: Multiple tunnels, unequal cost load sharing! Router A Router B Router C • Tunnels with bandwidth in 3: 1 (12: 4) ratio • 25% of traffic sent the long way • 75% sent the short way Router D • No out-of-order packet issues— CEF’s normal per-flow hashing is used! © 2001, Cisco Systems, Inc. All rights reserved. Router E 79

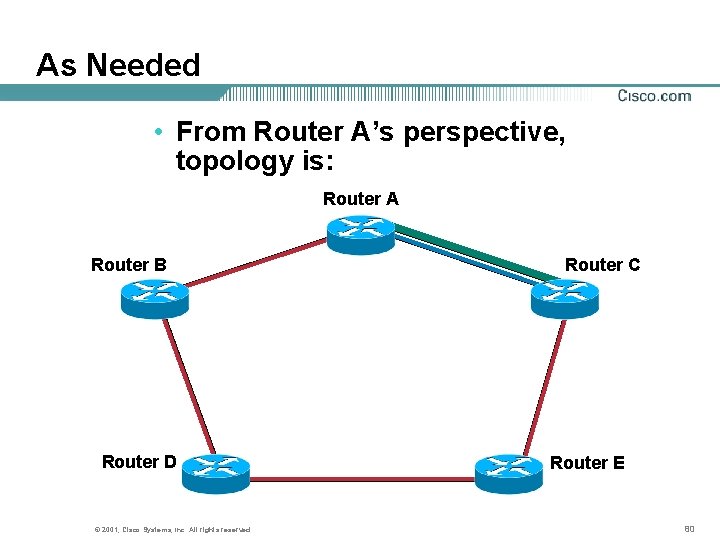
As Needed • From Router A’s perspective, topology is: Router A Router B Router D © 2001, Cisco Systems, Inc. All rights reserved. Router C Router E 80

As Needed • As needed—Easy, quick, but hard to track over time • Easy to forget why a tunnel is in place • Inter-node BW requirements may change, tunnels may be working around issues that no longer exist © 2001, Cisco Systems, Inc. All rights reserved. 81

Full Mesh • Put a full mesh of TE tunnels between routers • Initially deploy tunnels with 0 bandwidth (some folks deploy full mesh just to get router-to-router (pop-to-pop) traffic matrix) • Watch tunnel interface statistics, see how much bandwidth you are using between router pairs Tunnels are interfaces—use IF-MIB! Make sure that tunnel <= network BW © 2001, Cisco Systems, Inc. All rights reserved. 82

Full Mesh • Physical topology is: Router A Router B Router D © 2001, Cisco Systems, Inc. All rights reserved. Router C Router E 83

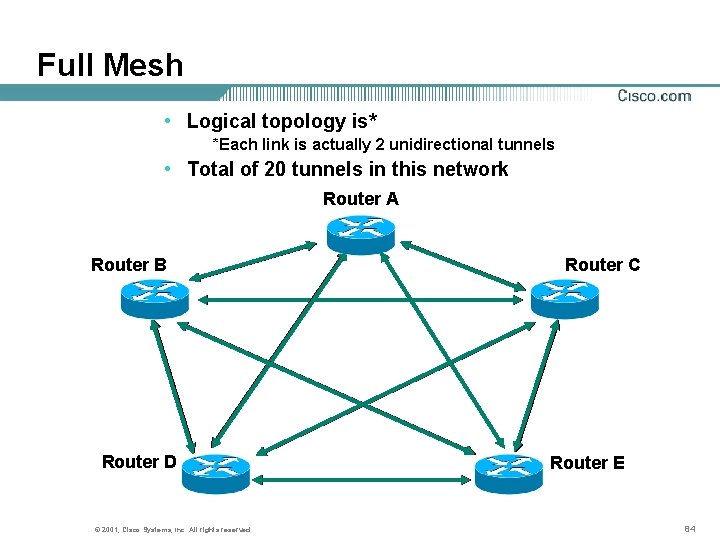
Full Mesh • Logical topology is* *Each link is actually 2 unidirectional tunnels • Total of 20 tunnels in this network Router A Router B Router D © 2001, Cisco Systems, Inc. All rights reserved. Router C Router E 84

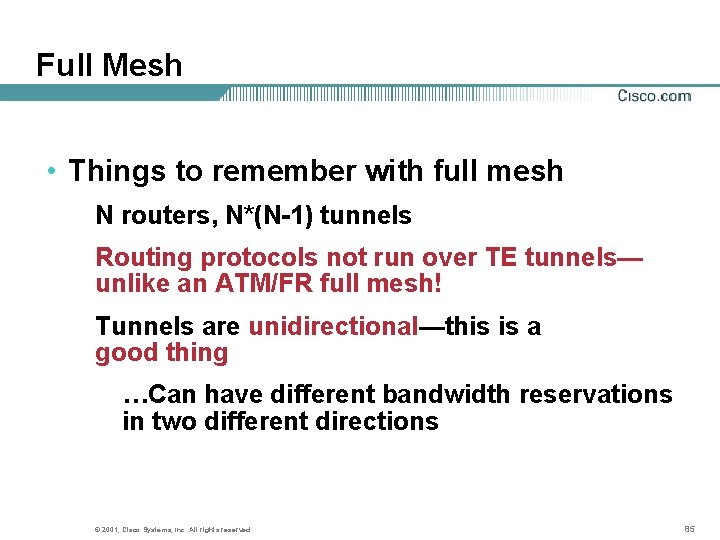
Full Mesh • Things to remember with full mesh N routers, N*(N-1) tunnels Routing protocols not run over TE tunnels— unlike an ATM/FR full mesh! Tunnels are unidirectional—this is a good thing …Can have different bandwidth reservations in two different directions © 2001, Cisco Systems, Inc. All rights reserved. 85

Deploying and Designing • Deployment methodologies • Scalability • Management • Security © 2001, Cisco Systems, Inc. All rights reserved. 86

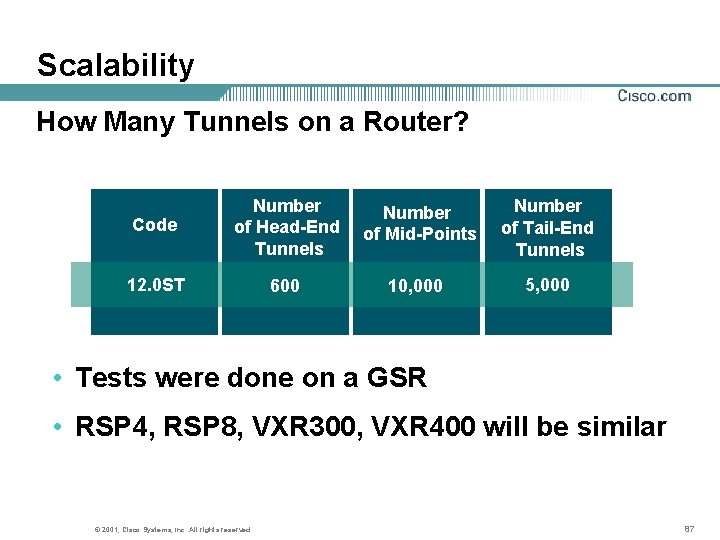
Scalability How Many Tunnels on a Router? Code Number of Head-End Tunnels Number of Mid-Points Number of Tail-End Tunnels 12. 0 ST 600 10, 000 5, 000 • Tests were done on a GSR • RSP 4, RSP 8, VXR 300, VXR 400 will be similar © 2001, Cisco Systems, Inc. All rights reserved. 87

Scalability http: //www. cisco. com/univercd/cc/td/doc/p roduct/software/ios 120/120 newft/120 limit/1 20 st/120 st 14/scalable. htm • Or just search CCO for “Scalability Enhancements for MPLS Traffic Engineering” © 2001, Cisco Systems, Inc. All rights reserved. 88

Deploying and Designing • Deployment methodologies • Scalability • Management • Security © 2001, Cisco Systems, Inc. All rights reserved. 89

Traffic Engineering MIBs • Interfaces MIB • MPLS-TE-MIB • CISCO-TE-MIB • MPLS-DS-TE-MIB © 2001, Cisco Systems, Inc. All rights reserved. 90

Tunnel. Vision • Need a tool to help manage TE LSPs? • Tunnel. Vision (server and client component, will run on Solaris and Windows 2000) • Not a network modeling tool! Use WANDL, Orchestream, Make. Sys, Opnet, and others © 2001, Cisco Systems, Inc. All rights reserved. 91

Tunnel. Vision • Cisco is also working with an external partner to add protection path calculation • The partner has world-class algorithm development experience • Tunnel. Vision will feed topology to this tool, tool will calculate backup paths © 2001, Cisco Systems, Inc. All rights reserved. 92

Deploying and Designing • Deployment methodologies • Scalability • Management • Security © 2001, Cisco Systems, Inc. All rights reserved. 93

Security • MPLS-TE is not enabled on externally facing interfaces • Biggest security risk is spoofed RSVP Hacker would have to know a lot about your topography to do anything RSVP authentication exists (rfc 2747), not yet implemented, on the radar • If you’re concerned about spoofed RSVP, then add RSVP to the ACLs you probably already use to stop spoofed BGP, OSPF, etc. • u. RPF also helps here © 2001, Cisco Systems, Inc. All rights reserved. 94

Conclusion Basically, TE helps you to optimize your network resources utilization, provide a better quality of service and enhance the network and services availability. © 2001, Cisco Systems, Inc. All rights reserved. 95

Obrigado!