Denial of Service A Brief Overview Denial of

Denial of Service A Brief Overview
Denial of Service • Significance of Do. S in Internet Security • Low-Rate Do. S Attacks – Timing and detection – Defense • High-Rate, Distributed Attacks – Botnets – Detection and Defense Strategies

Significance of Do. S • Accessibility to services is a key part of Internet Security. • The number of web sites and companies effected by Do. S attacks is high, and rising. • Banking companies attacked for revenge. • Businesses forced to pay criminals to prevent monetary losses caused by shutdown of their web sites.
![ITU-T Recommendation X. 805 Security Architecture [1] ITU-T Recommendation X. 805 Security Architecture [1]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-4.jpg)
ITU-T Recommendation X. 805 Security Architecture [1]
Low-Rate TCP Do. S Attack • Periodic short burst exploiting the minimum retransmission timeout of TCP flows. • Kuzmanovic and Knightly showed these attacks are feasible while difficult to detect. • Sun et al. proposed a distributed detection mechanism employing pattern matching using Dynamic Time Warping.
![TCP Retransmission Timer [6] TCP Retransmission Timer [6]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-6.jpg)
TCP Retransmission Timer [6]
![Low-Rate Attack Timing [8] Low-Rate Attack Timing [8]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-7.jpg)
Low-Rate Attack Timing [8]
![Dynamic Time Warping Histogram [8] Dynamic Time Warping Histogram [8]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-8.jpg)
Dynamic Time Warping Histogram [8]

Proposed Defense • Router detects matching traffic on output port, looks for it on each input port. If found on input port, push back detection to upstream routers. • If not detected at input ports, assume distributed attack method is being used. • Use Deficit Round Robin (DRR) scheduling to ensure fairness for flow from each input.

Distributed Denial of Service DDo. S

Distributed Denial of Service DDo. S • • Role of Botnets Botnet Creation Botnet Control Mechanism DDo. S Defense Strategies
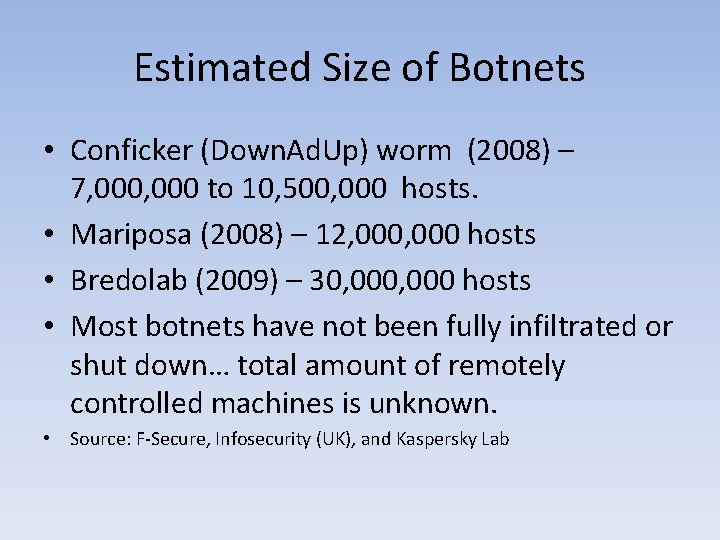
Estimated Size of Botnets • Conficker (Down. Ad. Up) worm (2008) – 7, 000 to 10, 500, 000 hosts. • Mariposa (2008) – 12, 000 hosts • Bredolab (2009) – 30, 000 hosts • Most botnets have not been fully infiltrated or shut down… total amount of remotely controlled machines is unknown. • Source: F-Secure, Infosecurity (UK), and Kaspersky Lab
Botnet Creation • Host computers are infected by worms, viruses, or by execution of trojan-horse software. • Worm propagation between web servers causes normally safe and legitimate web sites to serve malicious content to users, infecting the user’s computer.
![Worm-Based Botnet Creation [2] Worm-Based Botnet Creation [2]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-15.jpg)
Worm-Based Botnet Creation [2]
Botnet Command Control • Most common method of control is through use of Internet Relay Chat (IRC) protocols and servers. • Infected machines may also connect to controlling servers using HTTP protocol.
![IRC Controlled Botnet [4] IRC Controlled Botnet [4]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-17.jpg)
IRC Controlled Botnet [4]

DDo. S Defense Strategies • Monitoring and early detection. • Adaptive detection and defense employing Hop-Count Filtering. • Collaborative detection over multiple domains. • Traffic Visualization
Monitoring and Detection • Detect malware propagation during early, exponential growth phase. (trend detection) • Look for similar statistical characteristics. • Growth rate converges around a constant, positive exponential rate. • Non-uniform scan worm (Blaster) detection benefits from a widely distributed detection network.
![Worm Propagation Model [10] Worm Propagation Model [10]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-20.jpg)
Worm Propagation Model [10]
![Code Red and Blaster Propagation [9] Code Red and Blaster Propagation [9]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-21.jpg)
Code Red and Blaster Propagation [9]
![Worm Monitoring System [10] Worm Monitoring System [10]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-22.jpg)
Worm Monitoring System [10]

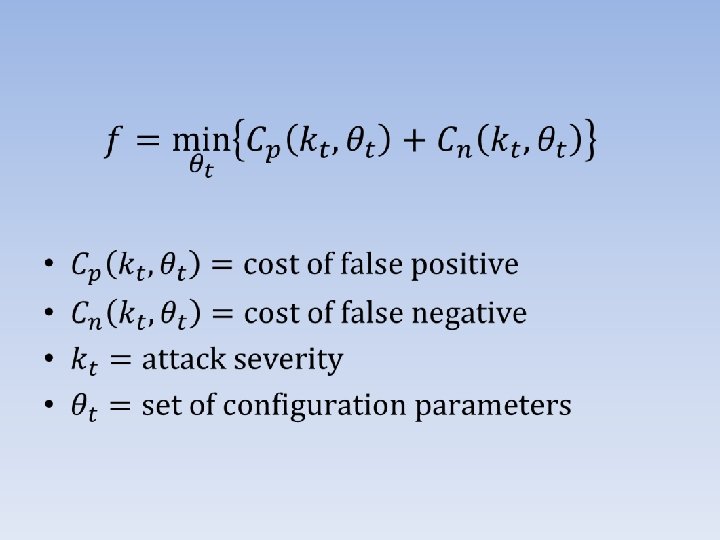
Adaptive Defense • Suitable for large traffic flows, such as worm propagation and DDo. S. • Relies a good estimation of attack severity. • Works to minimize sum of the costs of false positives and false negatives, by choosing the optimal configuration. • Easy to detect SYN flooding, but hard to filter. • Hop count filtering.

Hop Count Filtering • Spoofed packets may have a modified TTL in the IP header, but attackers cannot know the true hop count from the machines whose IP address it is faking to the target. • Memory constraints prevent storage of hopcount for every address, so address aggregation is used. • Filter selectivity adjusted adaptively.
![Adaptive Defense Architecture [9] Adaptive Defense Architecture [9]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-26.jpg)
Adaptive Defense Architecture [9]
![Adaptive HCF Cost [9] Adaptive HCF Cost [9]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-27.jpg)
Adaptive HCF Cost [9]
![Adaptive Defense Performance [9] Adaptive Defense Performance [9]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-28.jpg)
Adaptive Defense Performance [9]
Collaborative Detection Method • Use a distributed system to leverage network topology. • Implement in core ISP network domains covering edge networks where protected systems are physically connected. • Detection at traffic superflow level • Distributed Change-Point Detection (DCD) • Change Aggregation Trees (CAT)
![Superflow Traffic Model [3] Superflow Traffic Model [3]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-30.jpg)
Superflow Traffic Model [3]
Distributed Change-Point Detection Hierarchical detection architecture Deployed over multiple domains Central CAT server in each domain Merges CAT sub-trees from collaborative servers into a global CAT, with the root at the victim’s location. • Three layer organization. • •
DCD Three Layer Organization • At lowest layer, a single router detects local traffic fluctuations using a change-point detection program. • At each network domain, a CAT server constructs CAT sub-tree according to alerts collected from routers. • At highest layer, CAT servers form an overlay network, communicating over VPN channels.
Visualization Research Example • Using Hierarchical Network Maps • Treemap approach, with each node in the hierarchy drawn as a box placed inside its parent. • Using dimensions of IP address and time, the application of Internet monitoring can be realized.

Botnet Growth Example • Rapid spread of botnet computers in China in August 2006 over an eight day period, as observed by a large service provider. • Prefix labels anonymized here because of privacy concerns.
![Botnet Infections: Day 1 [7] Botnet Infections: Day 1 [7]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-35.jpg)
Botnet Infections: Day 1 [7]
![Botnet Infections: Day 5 [7] Botnet Infections: Day 5 [7]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-36.jpg)
Botnet Infections: Day 5 [7]
![Botnet Infections: Day 9 [7] Botnet Infections: Day 9 [7]](http://slidetodoc.com/presentation_image_h2/ecb188d5df47a9822fab7023e465578d/image-37.jpg)
Botnet Infections: Day 9 [7]

Conclusion • Denial of Service attacks are a continuing problem. • Active research is underway to study vulnerabilities to attacks and methods of mitigation. • Much work remains to be done before the problem will be solved.

Questions ?

- Slides: 40