demystifying the facts around cyber security DEMYSTIFYING THE

demystifying the facts around cyber security DEMYSTIFYING THE FACTS AROUND CYBER SECURITY presented by ilicomm Technology Solutions

WELCOME demystifying the facts around cyber security Cyber Security has become big news, In 2004, the global cybersecurity market was worth $3. 5 billion — and in 2017 we expect it to be worth more than $120 billion (source. Cyber Security Ventures) Eighty four per cent of UK small business owners and 43% of senior executives of large companies are unaware of the forthcoming General Data Protection Regulation (GDPR) (source. Shred it) , allowing ty ri u c e s r e b y c d n u e facts aro h t fy ti s y m e d l il ish w u e g n W ti “ is d d n a n io in p nformed o i n a e k a m o t s te a g le t air. ” de o h f o t o l a s t’ a h w d rtant an between what’s impo

NHS HYSTERIA demystifying the facts around cyber security
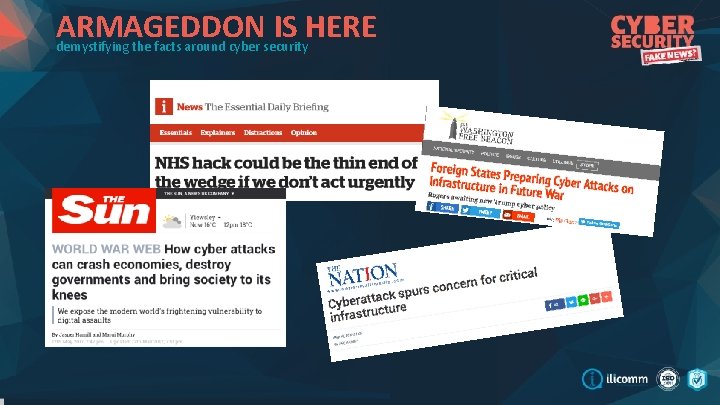
ARMAGEDDON IS HERE demystifying the facts around cyber security
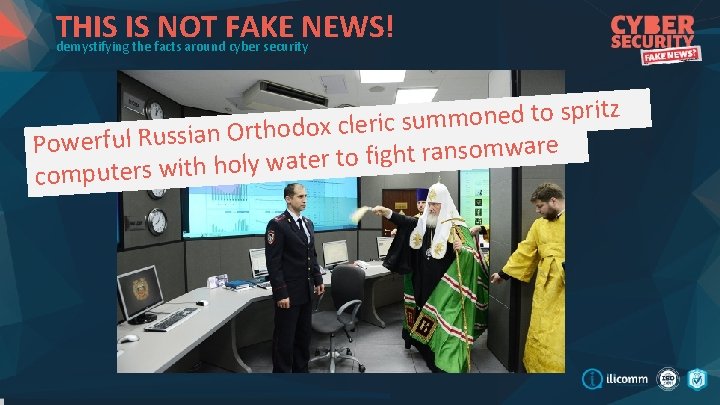
THIS IS NOT FAKE NEWS! demystifying the facts around cyber security z it r p s o t d e n o m m su ic r le c x o d o h t r O n ia s Powerful Rus are w m o s n a r t h ig f o t r e at w ly o h h it w s r e t u p m co

TRUSTED SOURCES? demystifying the facts around cyber security Social Media has fueled the rise of news articles and exposure. Facebook is by far the dominant social media news source with 44% of those surveyed using it to find, read, watch, share or comment on news each week. (source. Reuters) Unregulated news article’s, click bait and new technology vehicles has seen an unprecedented rise in content. Who can we trust?

The ever evolving world of Malware & Threat Landscape demystifying the facts around cyber security The rise in Security vendors is fueled by the rise in attacks and the sophistication used in the manipulation and exploitation of users and systems. ul a P n e b Reu d l o r a e y 11 dy d e t a w ho t c e n showed n o c can h c i h w r bea e b n a c d ou to the cl hacked.

THE BIRTH OF THE VIRUS demystifying the facts around cyber security BRAIN (1986) Launched in Pakistan and distributed around the world by floppy disk. Was designed to protect their medical software from piracy. AIDS TROJAN (1989) The first instance of Ransomware, distributed through floppy disks. The executable file encrypts the file name, though the decryption key was found within the code of the trojan. HAPPY 99 (1999) First known email virus greeted users with Happy new year 1999 then spread through a malicious attachment through the outlook contact book. Credited with being the first example of a modern worm.

THE BIRTH OF THE VIRUS demystifying the facts around cyber security LOVE LETTER(2000) Spread through email at the turn of the millennium via an attachment, transmitting its self to all email contacts. The email heading promised love but caused $5. 5 bn damage and overwrote many crucial files on the PC CODE RED (2001) First worm to spread without interaction. Targeted a Windows SQL vulnerability and spread within minutes. Followed a cycle of infecting between days 1 -19, performing DDOS attacks between 20 -27 and then going into remission for the rest of the month. FIZZER (2003) The first virus designed to make money. Infected a computer via email attachment and then forced it to send out spam emails. Due to the spread of the virus, many PC’s were compromised increasing the reach of the spam.

THE BIRTH OF THE VIRUS demystifying the facts around cyber security MEBROOT (2007) A trojan designed to sit on a system and observe, applying a key logger to help steal banking credentials and account passwords HUMMER (2016 mobile) Acquires root privileges allowing the malware to embed its self forever on an android platform. Pushes content onto the mobile phone like pornography or gaming apps. WANNACRY(2017) Infected 230 k computers in 150 countries within 24 hours.

GDPR & DATA PROTECTION LAWS demystifying the facts around cyber security Current data protection regulation

GDPR & DATA PROTECTION LAWS demystifying the facts around cyber security • Most businesses will have a GDPR requirement • Data is viewed as a business critical asset, yet because of it’s intangible nature many businesses do not place adequate protections around it • Data is not just an IT process and responsibility

INFORMATION SECURITY demystifying the facts around cyber security • Information security is concerned with how we identify that data, secure it and ethically use it. • Technology can be a great enabler, but there needs to be a greater thought process applied when deciding on it’s suitability for your organisation. • Cyber Security cannot be fixed by throwing technology at it. A security approach must be consistent across technology, policy and education.

INTRODUCTION demystifying the facts around cyber security KEITH HAYES 25 years experience in risk “opportunities” Held Global or EMEA security and infrastructure responsibility for : • • IBM Boots the Chemist Merrill Lynch Pfizer • • Siemens Dixons Carphone IMI Engineering Bound by a code of ethics

LET’S GET REAL – NOT “FAKE NEWS” demystifying the facts around cyber security GCHQ cyber-chief has recently slammed security outfits peddling: ’MEDIEVAL WITCHCRAFT ' Massively incentivised companies are being allowed to define the public perception of the problem – Fake news isn’t limited to Trump! THE REALITY? A UK telco was recently taken offline using a flaw that was older than the hacker alleged to have used it!

COMPLIANCE vs. RISK demystifying the facts around cyber security Who gets to say “That’s an acceptable risk? ” – You do! Collecting badges can be commercially valuable… It’s possible to be compliant to all of these standards, but still carry an undesired risk to the business……

DO THE BASICS WELL demystifying the facts around cyber security Cyberessentials - One of your “Five a Day”? ? ? Anyone guess the main driver for Cyberessentials certification? (based on our engagements? ) Forget the badge Any other “badges” in the room? and start thinking ISO 27001? about RISK and PCI-DSS? BUSINESS! GDPR?

WHAT CAN I DO TODAY? demystifying the facts around cyber security PROTECT THE CASH! Ensure there are non-tech processes that handle remittance advice. PROTECT THE INFORMATION ASSET Direct resources at income streams or differentiating services PROTECT THE BRAND “ I read an article that said” Ensure that third parties are compliant to the same standards and risk mitigation AWARENESS Why do you hear announcements at airports asking if you’ve seen an unattended bag? Targeted, job-function specific awareness campaigns deliver huge benefits in terms of security. Involve the staff positively in the decisions and measure the improvements.

GDPR? demystifying the facts around cyber security Heard of GDPR?

GDPR demystifying the facts around cyber security • GDPR is a regulation that's been in the making for years. • It gives back control to EU citizens and residents over their personal data, and applies to all companies that collect and process personal data of EU citizens and residents • It is complex, and like the Data Protection Act, is subject to interpretation

GDPR - Data Privacy & Data Protection demystifying the facts around cyber security "any information relating to an identified or identifiable natural person, "

GDPR demystifying the facts around cyber security Consent to collect and use personal data
GDPR – The right to be forgotten demystifying the facts around cyber security “without undue delay”

GDPR demystifying the facts around cyber security Pseudonymisation

GDPR demystifying the facts around cyber security Data Mapping

GDPR demystifying the facts around cyber security The appointment of Data Privacy Officers (DPO) for certain organisations

GDPR demystifying the facts around cyber security Mandatory privacy impact assessments (PIAs) and privacy by design

GDPR demystifying the facts around cyber security Liability for data processors as well as data controllers

GDPR demystifying the facts around cyber security Data breach reporting

GDPR demystifying the facts around cyber security Fines and Sanctions

GDPR demystifying the facts around cyber security “ DON’T QUOTE ME ON THIS, BUT REMEMBER MEDIEVAL WITCHCRAFT”? • “any information relating to an individual, whether it relates to his or her private, professional or public life. It can be anything from a name, a photo, an email address, bank details, posts on social networking websites, medical information, or a computer’s IP address. ” • • Fines of up to 4% of global turnover* You need a Data Protection officer – don’t you? Privacy-breach Impact assessments for every system* A record of positive consent to process* Right of erasure (Third parties) – Get the contracts right! Breach notification within 72 hours* Subject access requests within a month – no fee* How does that relate to Natwest?

SUMMARY demystifying the facts around cyber security Things to start today DATA CLASSIFICATION: RESILIENCE • Not a regulatory risk, but a straight • What do we have? Where is it business decision. How much now? What is it worth? Where downtime can each system or should it live? Who owns it? process take? How much in pounds and pence does the loss of a system • We can apply rules to data at rest cost? Per hour? Per day? or in flight but the business needs to identify the value of that data ASSURANCE • Don’t trust third parties Check and check again that controls are not only implemented, but working.

YOUR EVENT PACKS demystifying the facts around cyber security

QUESTIONS demystifying the facts around cyber security QUESTIONS
- Slides: 34