Defending Tor from Network Adversaries A Case Study







- Slides: 19

Defending Tor from Network Adversaries: A Case Study of Network Path Prediction Joshua Juen, Aaron Johnson, Anupam Das, Nikita Borisov and Matthew Caesar

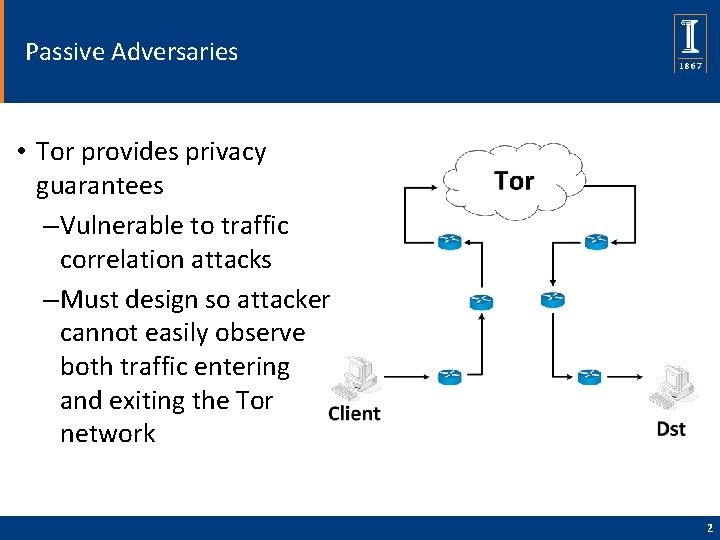
Passive Adversaries • Tor provides privacy guarantees – Vulnerable to traffic correlation attacks – Must design so attacker cannot easily observe both traffic entering and exiting the Tor network 2

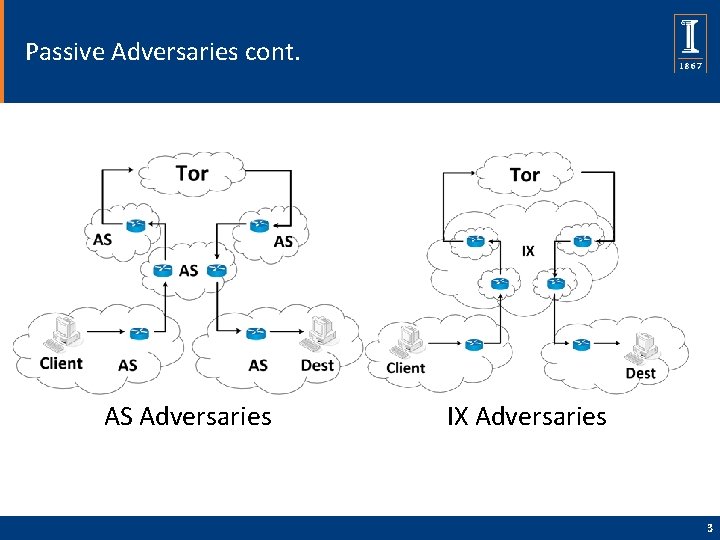
Passive Adversaries cont. AS Adversaries IX Adversaries 3

Mitigating Passive Adversaries • Proposed Solution: AS-level Mapping – Are AS-level routing predictions accurate enough to characterize threat? – Can AS-level predictions be used to construct safe paths in Tor? 4

Traceroute Measurement • Goal: Measure from Tor routers to the entire Internet – Dump every advertised prefix from Routeview’s RIBs – Approximately 500 k prefixes – Run Scamper using Paris Traceroute to each prefix • 28 Tor volunteers collected measurements – 23% AS guard and 26% AS exit probability – 4. 4 million unique IP paths 5

AS, IX Measurement • Measuring ASes – Measured IPs are mapped to ASes using Geo IP • Measuring IXes – Record known IX prefixes from Packet Clearing House and Peering. DB – Measured IXes are identified by IP address being contained in a known IX prefix 6

AS, IX Prediction • We predict AS paths using Qiu and Gao’s classic algorithm – Consider top 5 inferred ASes from Qui and Gao • We predict IX points using Augustine et al. ’s method – Discovered AS-AS hops at IXes by investigating 200 million CAIDA traceroutes – Produces a list of known AS-AS peerings at each IX 7

Realistic Vanilla Tor Simulation • Select paths using the Tor Path Simulator – Simulates the path selection of a single client over time • Recreate the state of the Tor network • 205 unique destination IP addresses • Choose 50 top client ASes – For each we choose 20 prefixes – 1000 total client Prefixes • 18 billion total streams considered 8

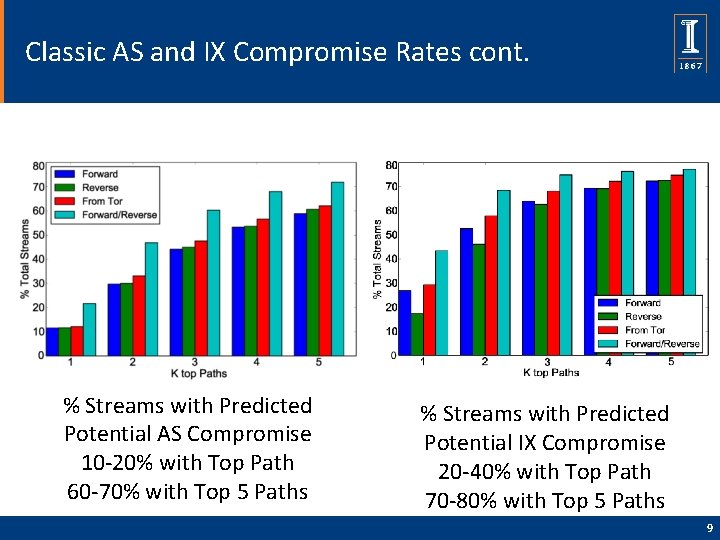
Classic AS and IX Compromise Rates cont. % Streams with Predicted Potential AS Compromise 10 -20% with Top Path 60 -70% with Top 5 Paths % Streams with Predicted Potential IX Compromise 20 -40% with Top Path 70 -80% with Top 5 Paths 9

Effect of More Top Paths • AS threats are identified by looking at the intersection of – All potential ASes on the guard path – All potential ASes on the exit path • When we consider the top K paths – We consider the total set of all ASes seen in the top K paths • Many top paths have completely different sets of ASes – The size of the set of paths scales roughly linearly with K – This causes a lot of over prediction with higher values of K 10

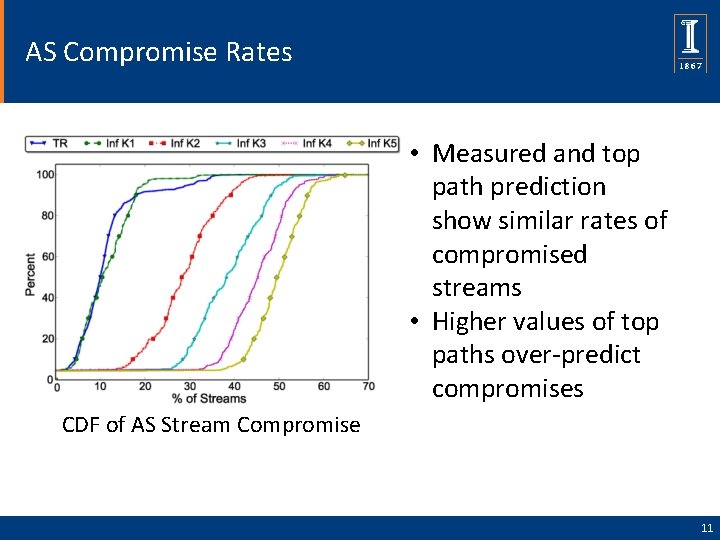
AS Compromise Rates • Measured and top path prediction show similar rates of compromised streams • Higher values of top paths over-predict compromises CDF of AS Stream Compromise 11

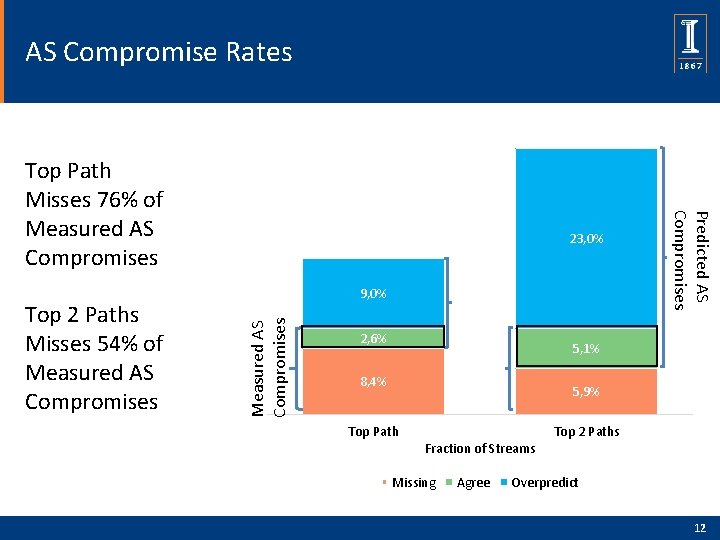
AS Compromise Rates 9, 0% Measured AS Compromises Top 2 Paths Misses 54% of Measured AS Compromises 23, 0% 2, 6% Predicted AS Compromises Top Path Misses 76% of Measured AS Compromises 5, 1% 8, 4% 5, 9% Top Path Fraction of Streams Missing Agree Top 2 Paths Overpredict 12

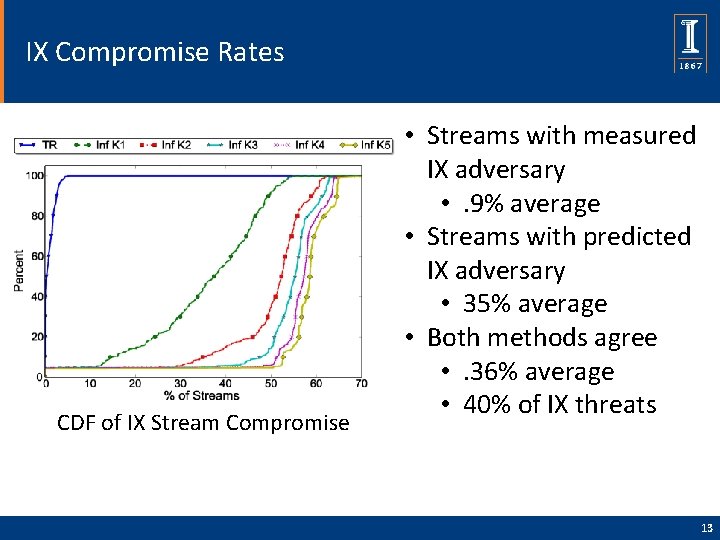
IX Compromise Rates CDF of IX Stream Compromise • Streams with measured IX adversary • . 9% average • Streams with predicted IX adversary • 35% average • Both methods agree • . 36% average • 40% of IX threats 13

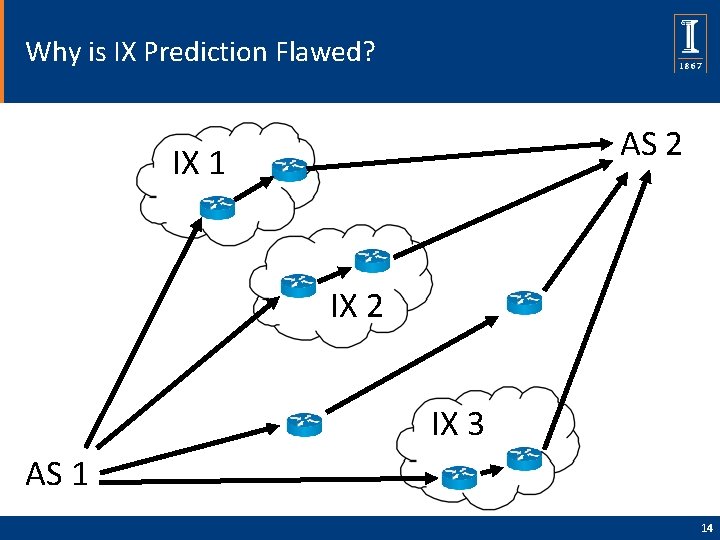
Why is IX Prediction Flawed? AS 2 IX 1 IX 2 IX 3 AS 1 14

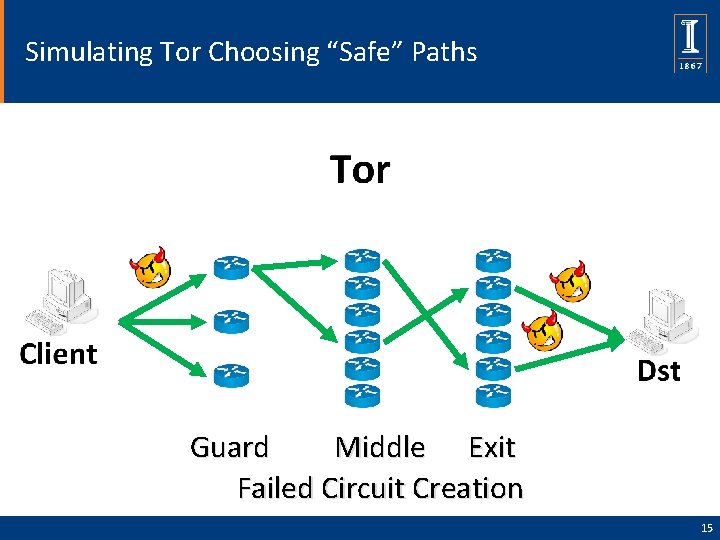
Simulating Tor Choosing “Safe” Paths Middle Exit Guard Failed Circuit Creation 15

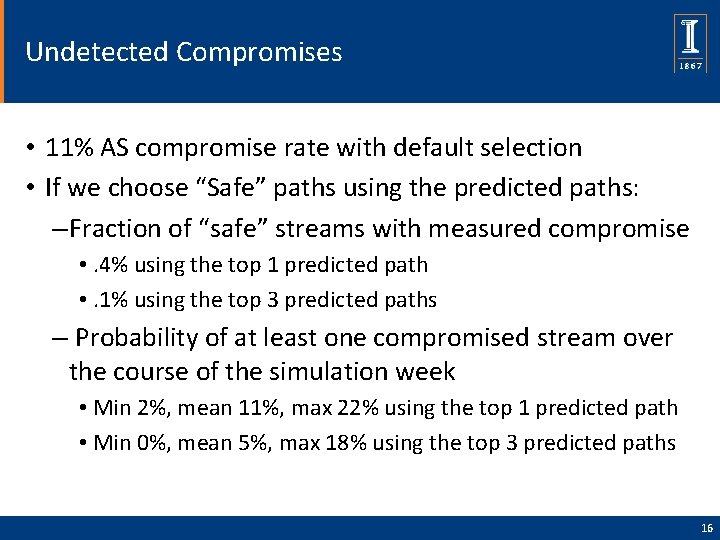
Undetected Compromises • 11% AS compromise rate with default selection • If we choose “Safe” paths using the predicted paths: – Fraction of “safe” streams with measured compromise • . 4% using the top 1 predicted path • . 1% using the top 3 predicted paths – Probability of at least one compromised stream over the course of the simulation week • Min 2%, mean 11%, max 22% using the top 1 predicted path • Min 0%, mean 5%, max 18% using the top 3 predicted paths 16

Unnecessary Failures • Consider when a stream fails due to no “safe” paths • Mean fraction of stream failures – 5. 1% using the top path – 6. 0% using the top 3 paths • 19% of these failures have measurements for validation • Mean fraction of failures that HAD a safe path from measurement – 96% using the top path – 95% using the top 3 paths • 100% chance that each client had at least one stream failure over the course of the week 17

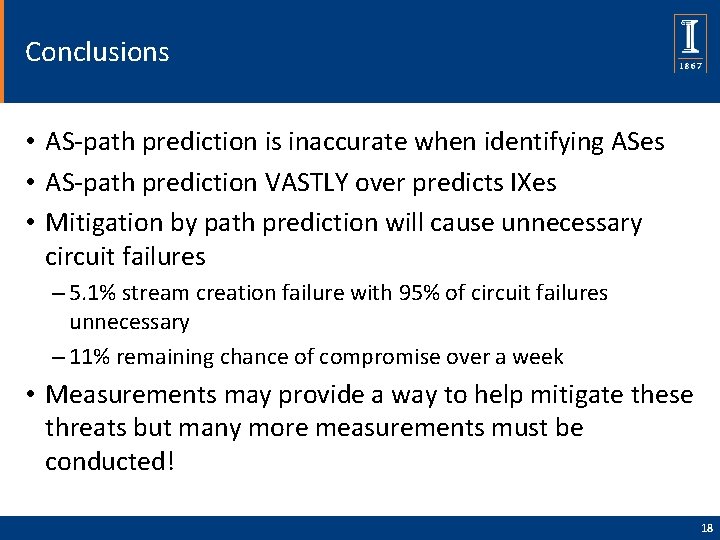
Conclusions • AS-path prediction is inaccurate when identifying ASes • AS-path prediction VASTLY over predicts IXes • Mitigation by path prediction will cause unnecessary circuit failures – 5. 1% stream creation failure with 95% of circuit failures unnecessary – 11% remaining chance of compromise over a week • Measurements may provide a way to help mitigate these threats but many more measurements must be conducted! 18
