Defending Against DDo S Attacks Using Max min







- Slides: 47

Defending Against DDo. S Attacks Using Max -min Fair Server Centric Router Throttles David K. Y. Yau CS Dept, Purdue University Operating System Concepts 1. 1 John C. S. Lu CS&E Dept, CUHK

Motivations n Internet is an open and democratic environment F increasingly used for mission-critical work and commercial applications. n Many security threats are present or appearing F Easy to launch, even for naïve users. F need effective and flexible defenses to detect/trace/counter attacks F Goals: 4 protect innocent users; 4 prosecute criminals Operating System Concepts 1. 2 Ambitious goals

Network Denial-of-service Attacks n Some attacks quite subtle F securing protocols and intrusion detection (e. g. , BGP, TCP-syn attack) F at routing infrastructure, malicious dropping of packets, etc (low-rate TCP) n Others by brute force: - flooding (e. g. , UDP, valid Web Request) n Cripples victim: - precludes any sophisticated defense at victim site F Philosophical question: what is an “attacker”? F Viewed as resource management problem Operating System Concepts 1. 3

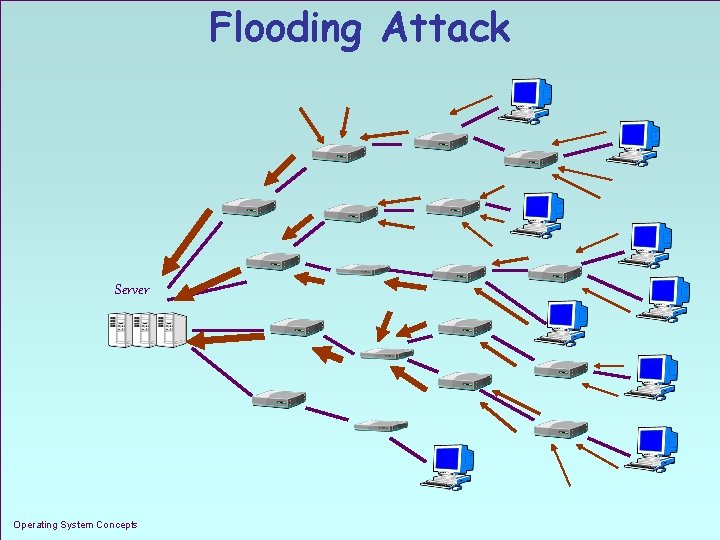
Flooding Attack Server Operating System Concepts 1. 4

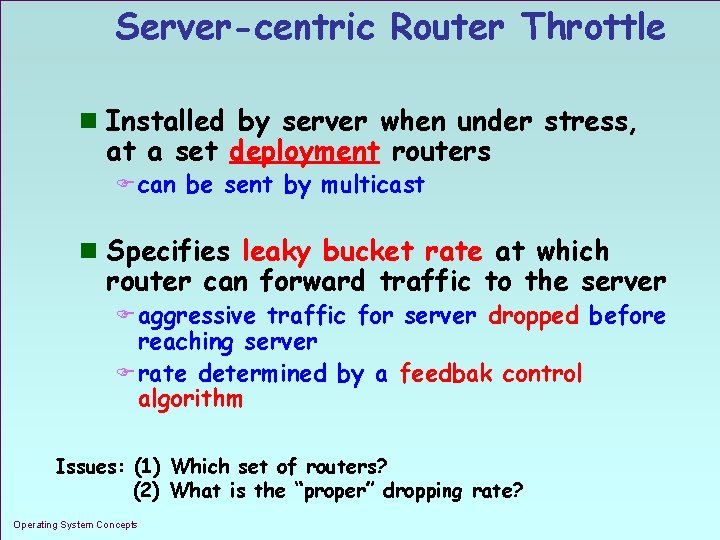
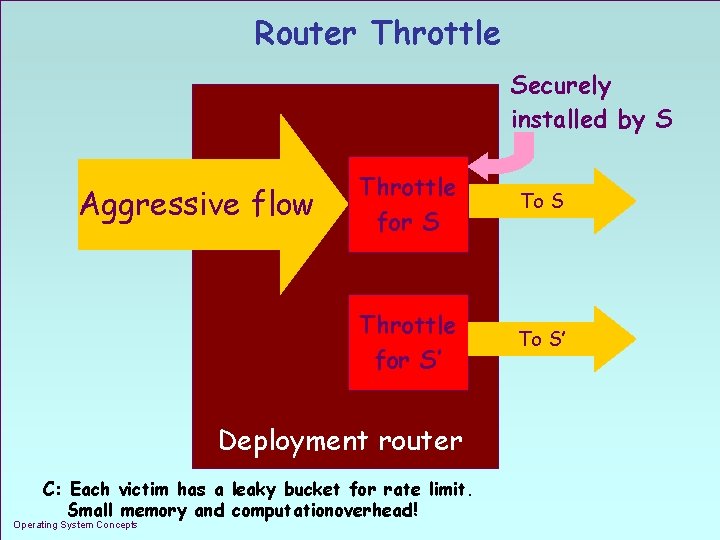
Server-centric Router Throttle n Installed by server when under stress, at a set deployment routers F can be sent by multicast n Specifies leaky bucket rate at which router can forward traffic to the server F aggressive traffic for server dropped before reaching server F rate determined by a feedbak control algorithm Issues: (1) Which set of routers? (2) What is the “proper” dropping rate? Operating System Concepts 1. 5

Router Throttle Securely installed by S Aggressive flow Throttle for S To S Throttle for S’ To S’ Deployment router C: Each victim has a leaky bucket for rate limit. Small memory and computationoverhead! Operating System Concepts 1. 6

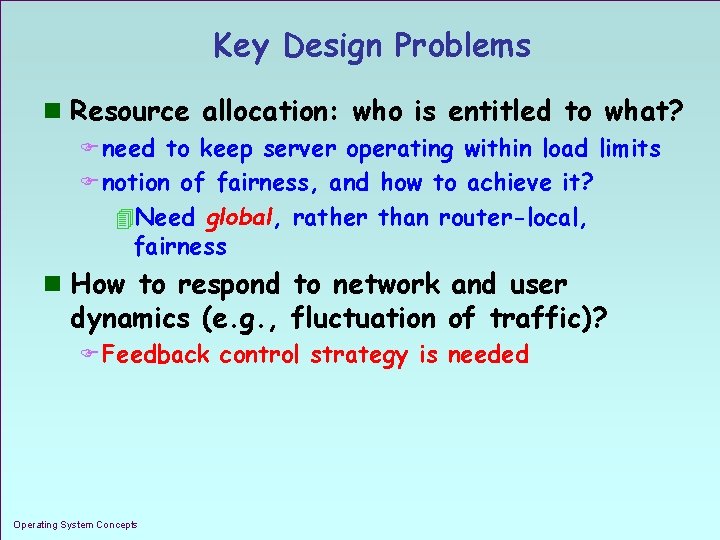
Key Design Problems n Resource allocation: who is entitled to what? F need to keep server operating within load limits F notion of fairness, and how to achieve it? 4 Need global, rather than router-local, fairness n How to respond to network and user dynamics (e. g. , fluctuation of traffic)? F Feedback control strategy is needed Operating System Concepts 1. 7

What is being fair? n Baseline approach of dropping a fraction “f”, say ½, of traffic for each flow won’t work well F a flow can cause more damage to other flows simply by being more aggressive! n Rather, no flow should get a higher rate than another flow that has unmet demands F this way, we penalize “aggressive” flows only, but protect the well-behaving ones Operating System Concepts 1. 8

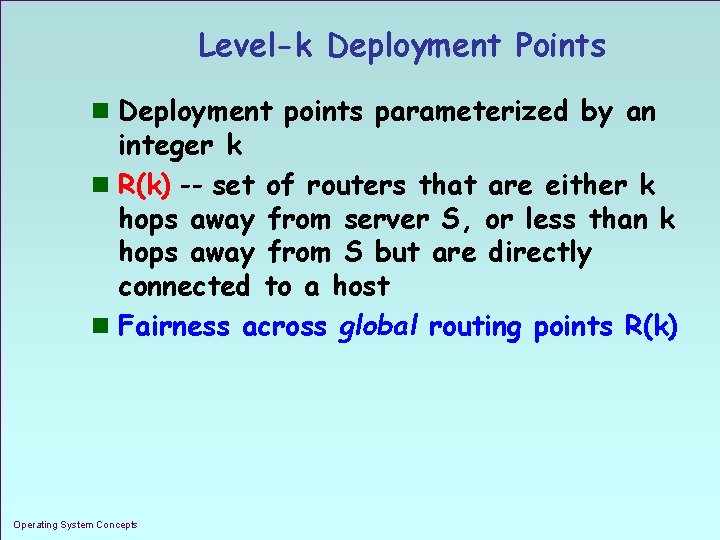
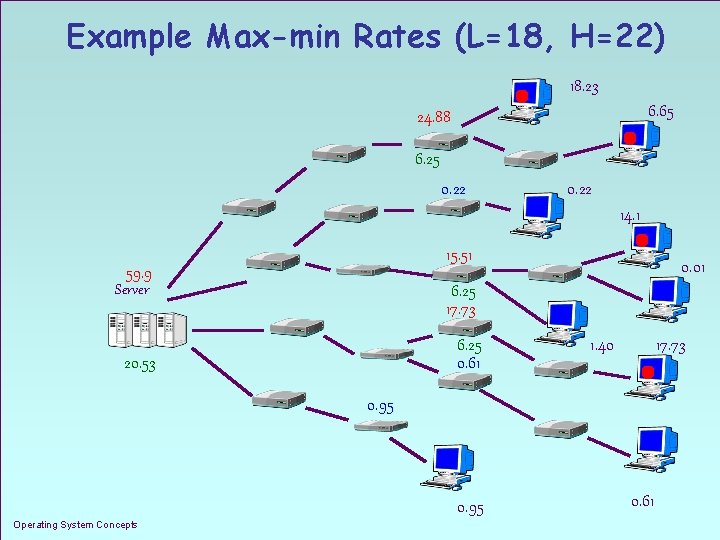
Level-k Deployment Points n Deployment points parameterized by an integer k n R(k) -- set of routers that are either k hops away from server S, or less than k hops away from S but are directly connected to a host n Fairness across global routing points R(k) Operating System Concepts 1. 10

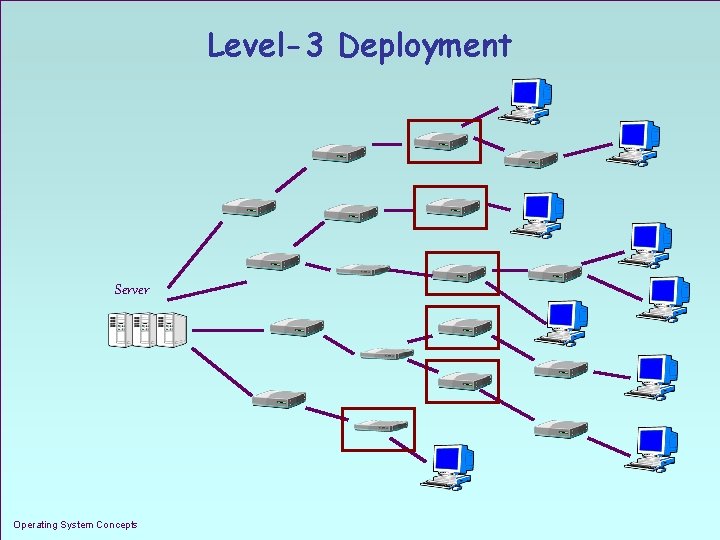
Level-3 Deployment Server Operating System Concepts 1. 11

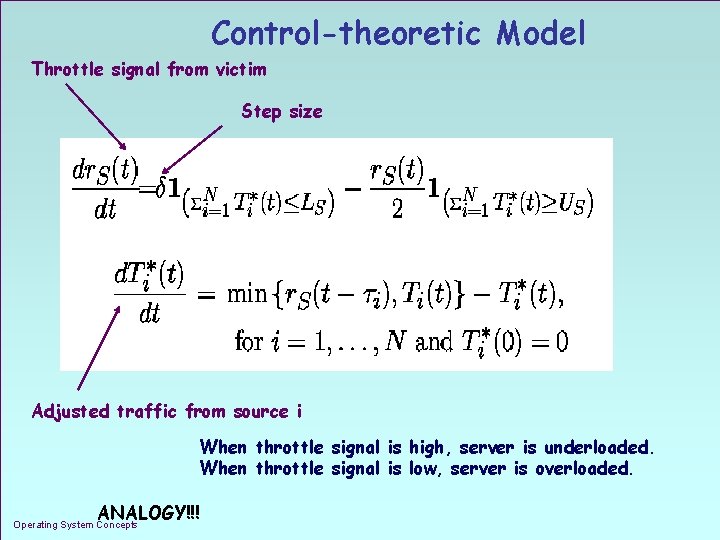
Feedback Control Strategy n Hysteresis control F high and low water marks for server load, to strengthen or relax router throttle n Additive increase/multiplicative decrease rate adjustment F increases when server load exceeds US, and decreases when server load falls below LS F throttle removed when a relaxed rate does not result in significant server load increase Operating System Concepts 1. 12

Fairness Definition n A resource control algorithm achieves level-k max-min fairness among the routers R(k) if the allowed forwarding rate of traffic for S at each router is the router’s max-min fair share of some rate r satisfying LS r US Operating System Concepts 1. 13

Fair Throttle Algorithm Operating System Concepts 1. 14

Example Max-min Rates (L=18, H=22) 18. 23 6. 65 24. 88 6. 25 0. 22 14. 1 15. 51 59. 9 Server 0. 01 6. 25 17. 73 6. 25 0. 61 20. 53 1. 40 17. 73 0. 95 Operating System Concepts 1. 15 0. 61

Interesting Questions n Can we preferentially drop attacker traffic over good user traffic? n Can we successfully keep server operating within design limits, so that good user traffic that makes it gets acceptable service? n How stable is such a control algorithm? How does it converge? Operating System Concepts 1. 16

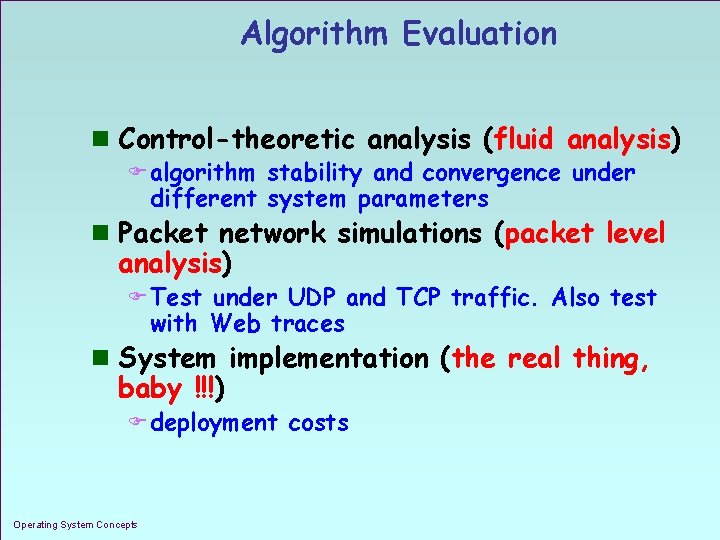
Algorithm Evaluation n Control-theoretic analysis (fluid analysis) F algorithm stability and convergence under different system parameters n Packet network simulations (packet level analysis) F Test under UDP and TCP traffic. Also test with Web traces n System implementation (the real thing, baby !!!) F deployment costs Operating System Concepts 1. 17

Control-theoretic Model Throttle signal from victim Step size Adjusted traffic from source i When throttle signal is high, server is underloaded. When throttle signal is low, server is overloaded. ANALOGY!!! Operating System Concepts 1. 18

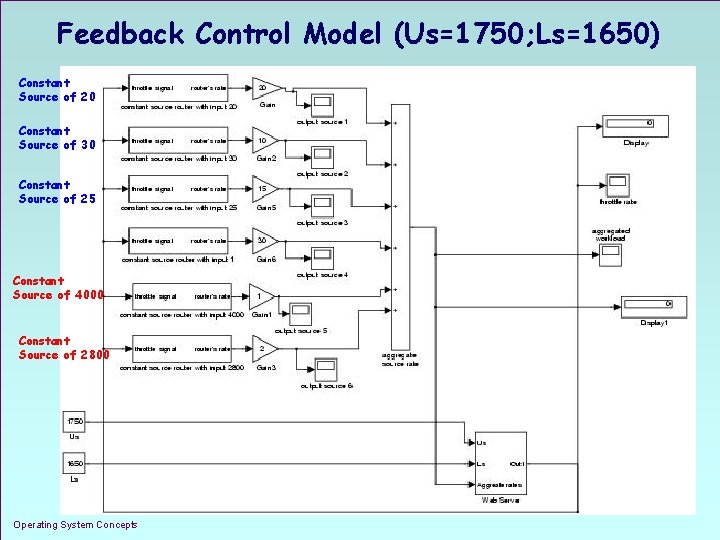
Feedback Control Model (Us=1750; Ls=1650) Constant Source of 20 Constant Source of 30 Constant Source of 25 Constant Source of 4000 Constant Source of 2800 Operating System Concepts 1. 19

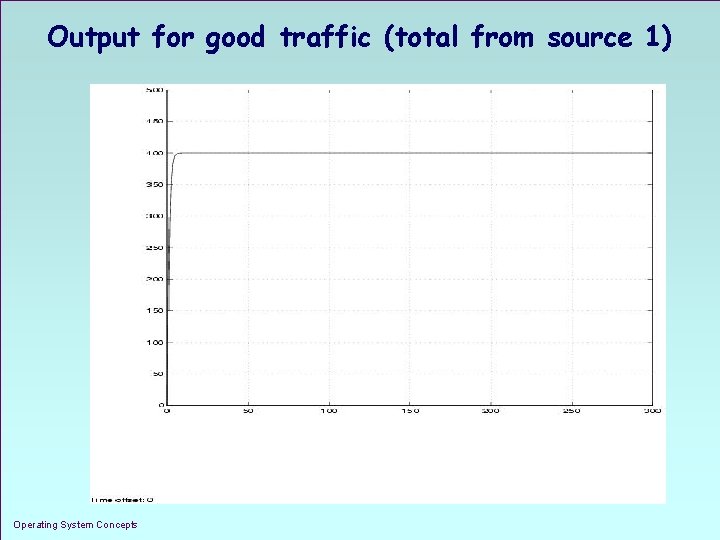
Output for good traffic (total from source 1) Operating System Concepts 1. 20

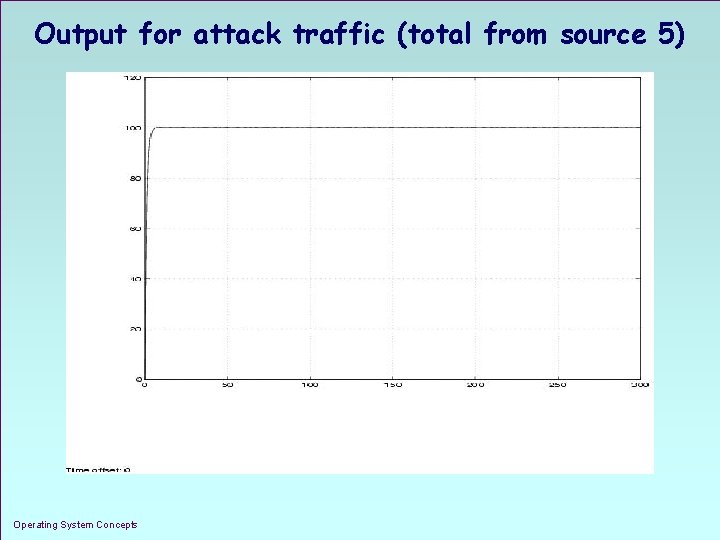
Output for attack traffic (total from source 5) Operating System Concepts 1. 21

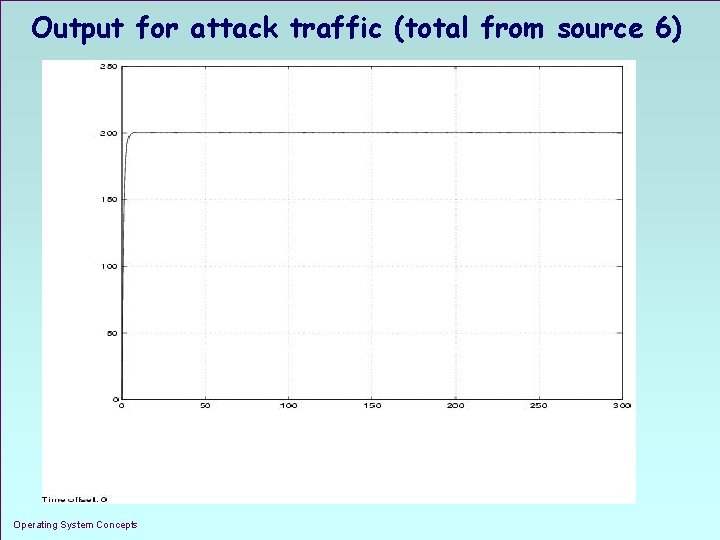
Output for attack traffic (total from source 6) Operating System Concepts 1. 22

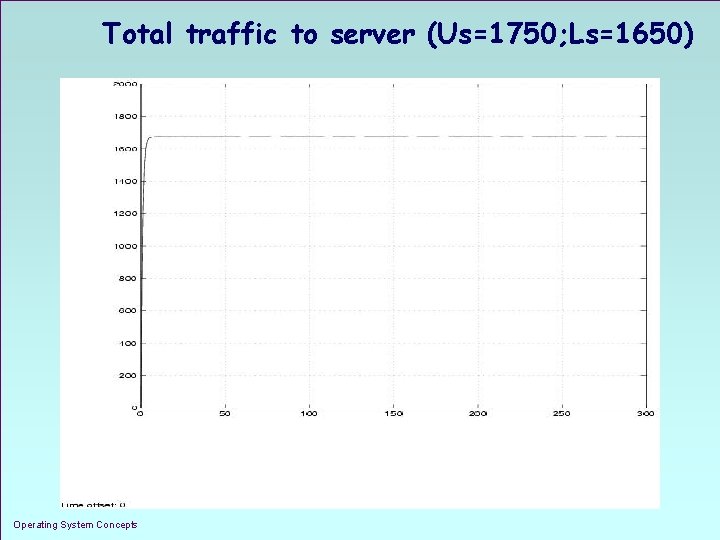
Total traffic to server (Us=1750; Ls=1650) Operating System Concepts 1. 23

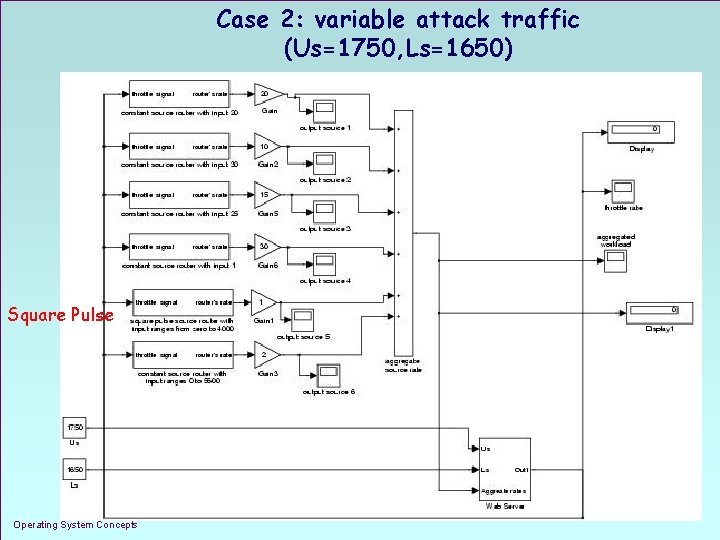
Case 2: variable attack traffic (Us=1750, Ls=1650) Square Pulse Operating System Concepts 1. 24

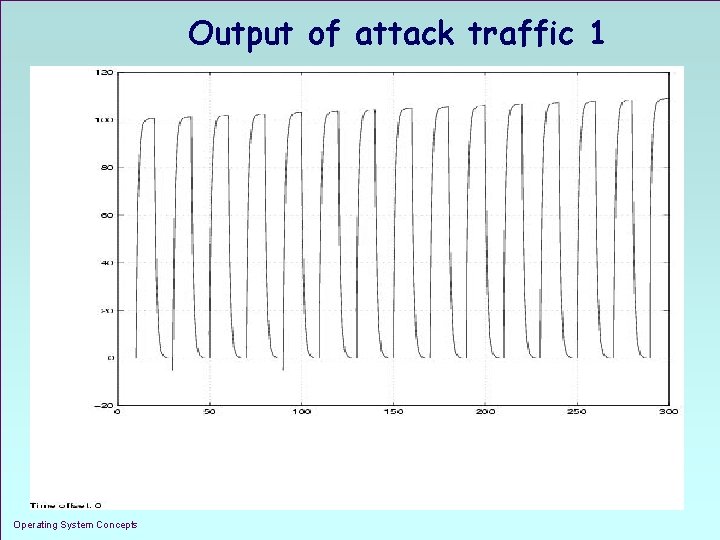
Output of attack traffic 1 Operating System Concepts 1. 25

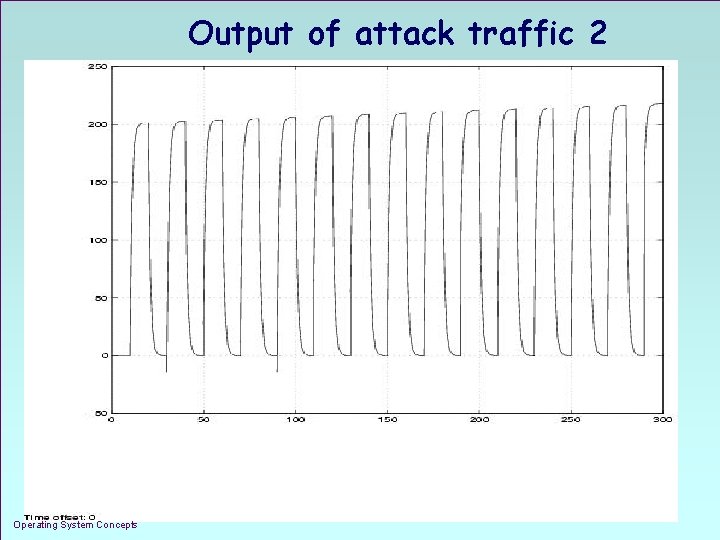
Output of attack traffic 2 Operating System Concepts 1. 26

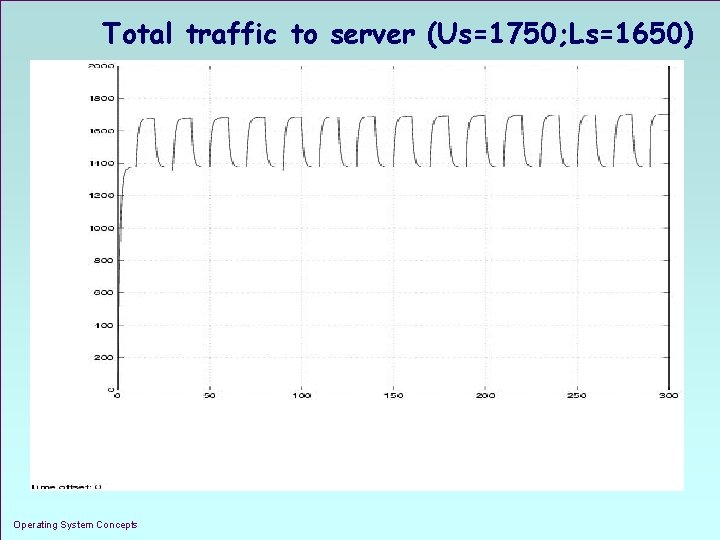
Total traffic to server (Us=1750; Ls=1650) Operating System Concepts 1. 27

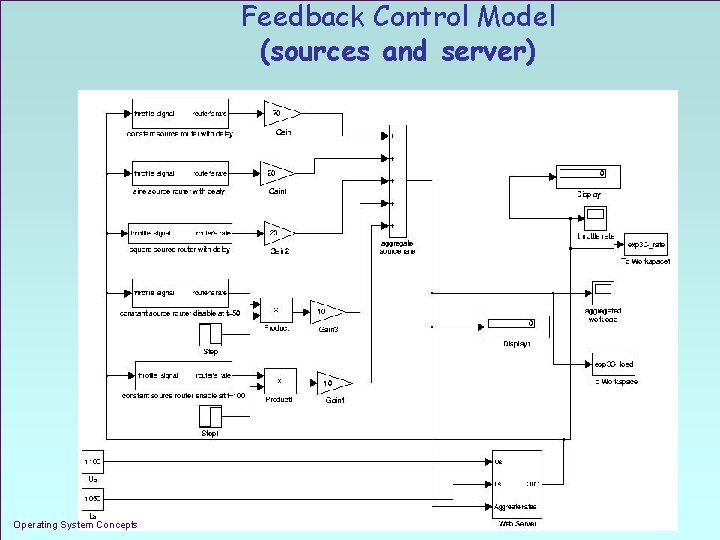
Feedback Control Model (sources and server) Operating System Concepts 1. 28

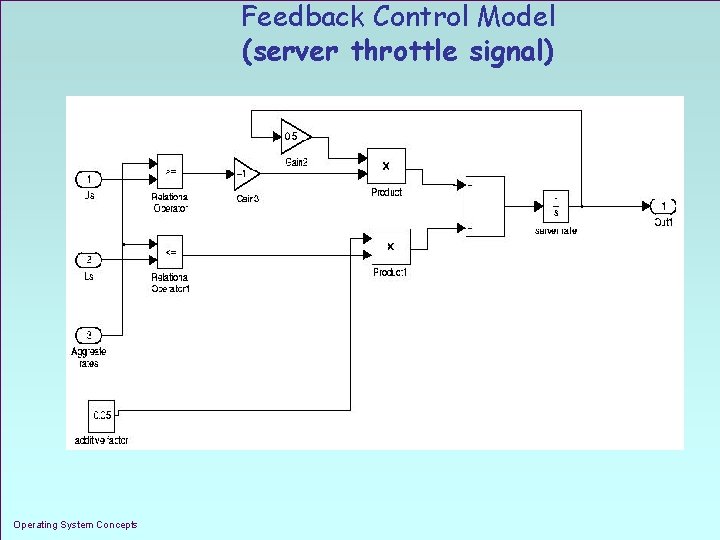
Feedback Control Model (server throttle signal) Operating System Concepts 1. 29

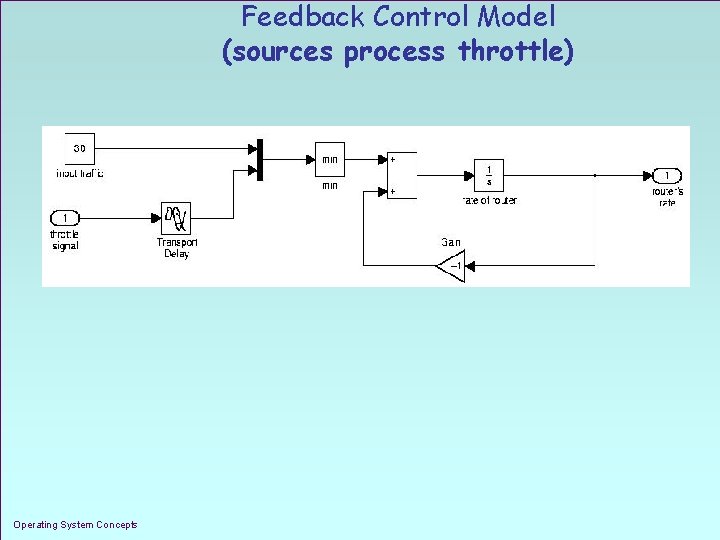
Feedback Control Model (sources process throttle) Operating System Concepts 1. 30

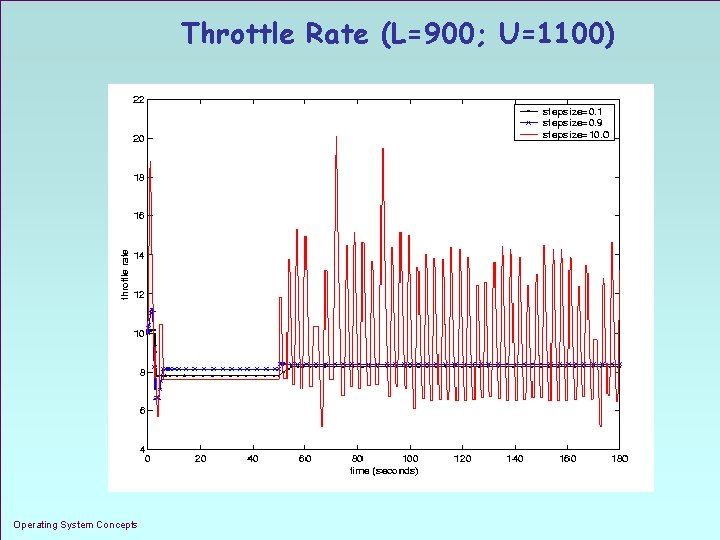
Throttle Rate (L=900; U=1100) Operating System Concepts 1. 31

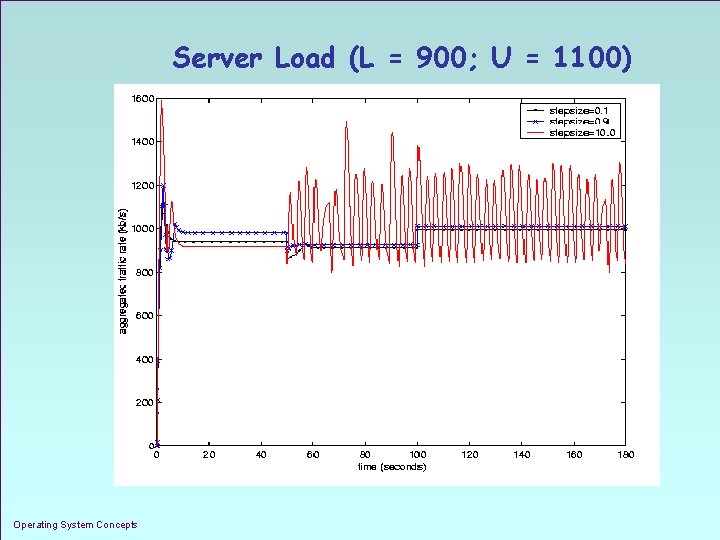
Server Load (L = 900; U = 1100) Operating System Concepts 1. 32

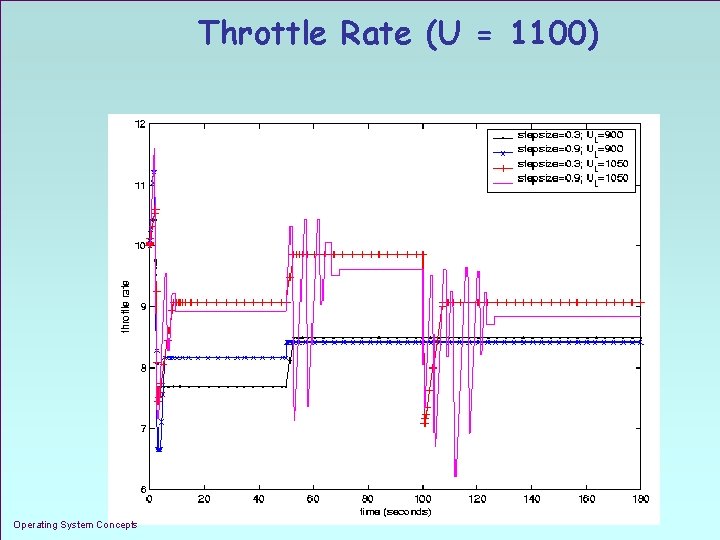
Throttle Rate (U = 1100) Operating System Concepts 1. 33

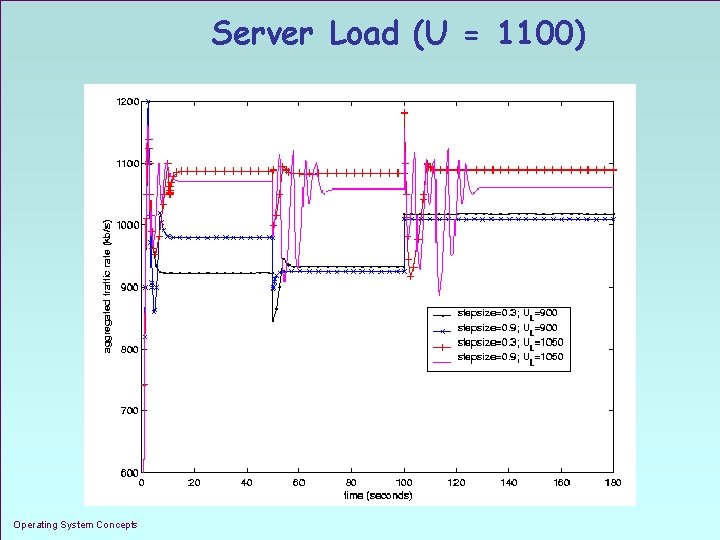
Server Load (U = 1100) Operating System Concepts 1. 34

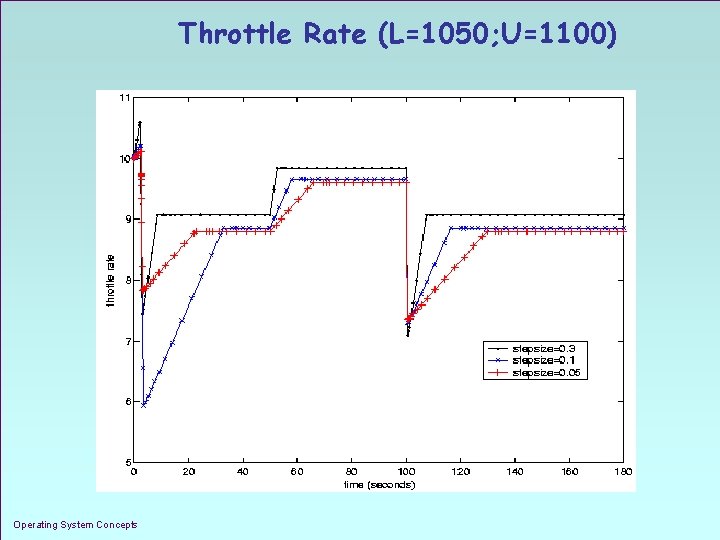
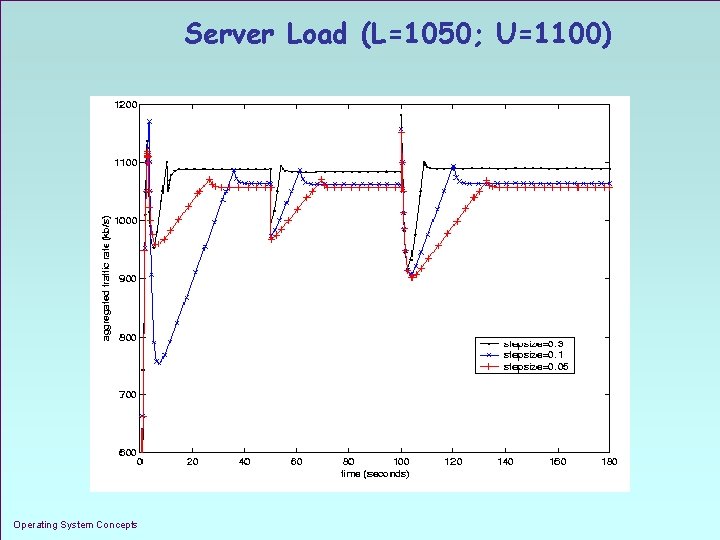
Throttle Rate (L=1050; U=1100) Operating System Concepts 1. 35

Server Load (L=1050; U=1100) Operating System Concepts 1. 36

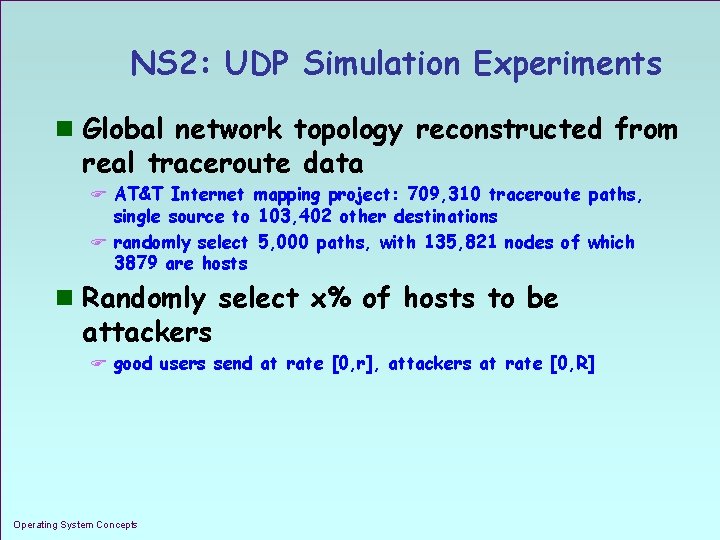
NS 2: UDP Simulation Experiments n Global network topology reconstructed from real traceroute data F AT&T Internet mapping project: 709, 310 traceroute paths, single source to 103, 402 other destinations F randomly select 5, 000 paths, with 135, 821 nodes of which 3879 are hosts n Randomly select x% of hosts to be attackers F good users send at rate [0, r], attackers at rate [0, R] Operating System Concepts 1. 37

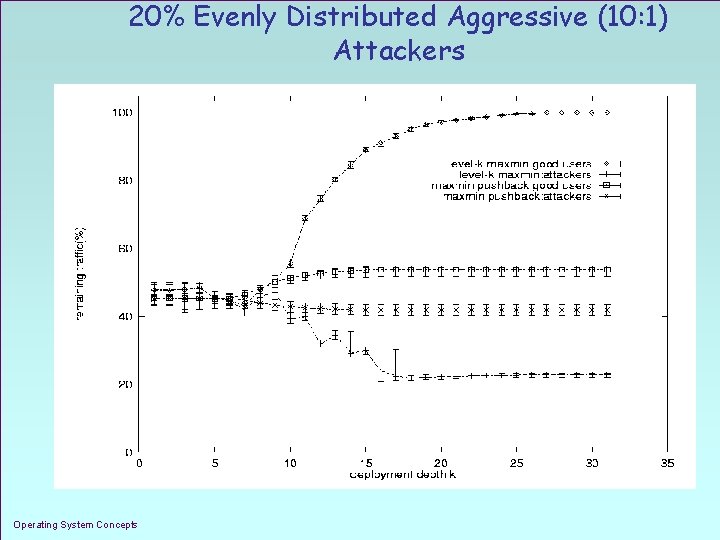
20% Evenly Distributed Aggressive (10: 1) Attackers Operating System Concepts 1. 38

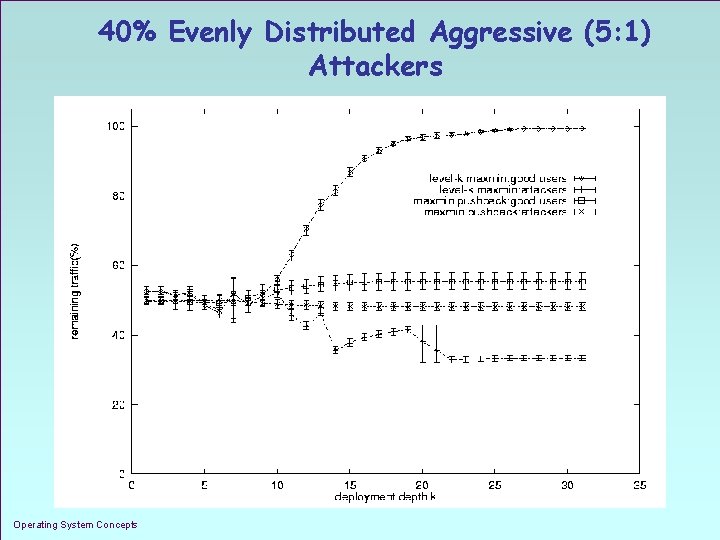
40% Evenly Distributed Aggressive (5: 1) Attackers Operating System Concepts 1. 39

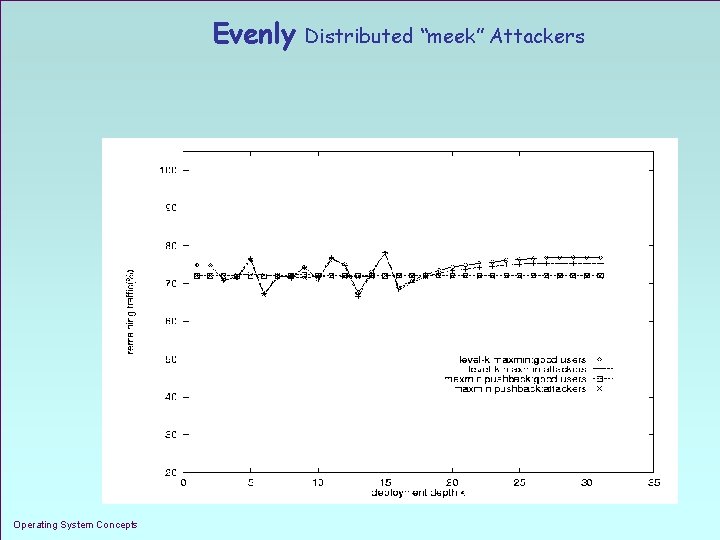
Evenly Operating System Concepts Distributed “meek” Attackers 1. 40

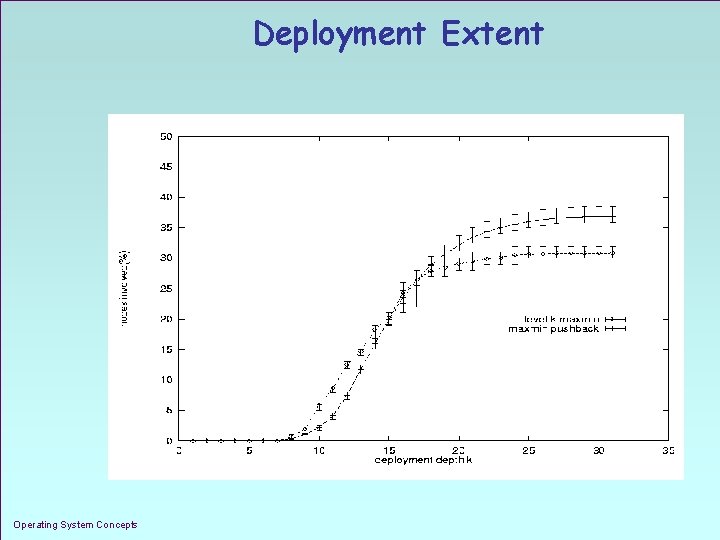
Deployment Extent Operating System Concepts 1. 41

NS 2: TCP Simulation Experiment n Clients access web server via HTTP 1. 0 over TCP Reno n Simulated network subset of AT&T traceroute topology F 85 hosts, 20% attackers n Web clients make request probabilistically with empirical document size and inter-request time distributions Operating System Concepts 1. 42

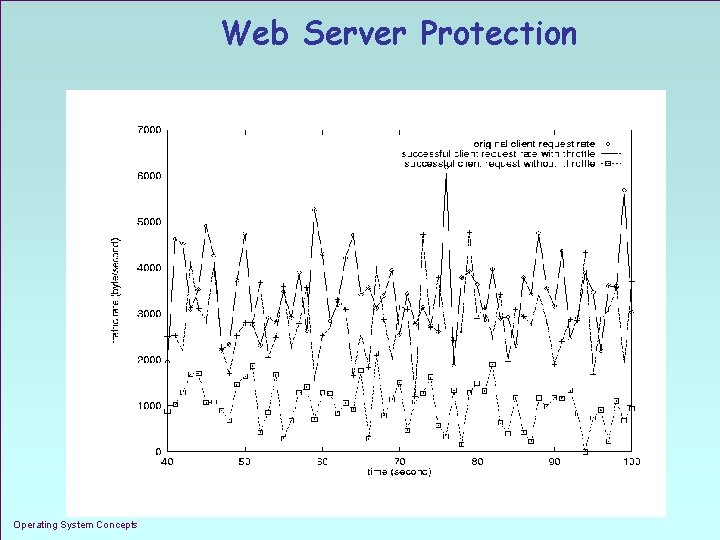
Web Server Protection Operating System Concepts 1. 43

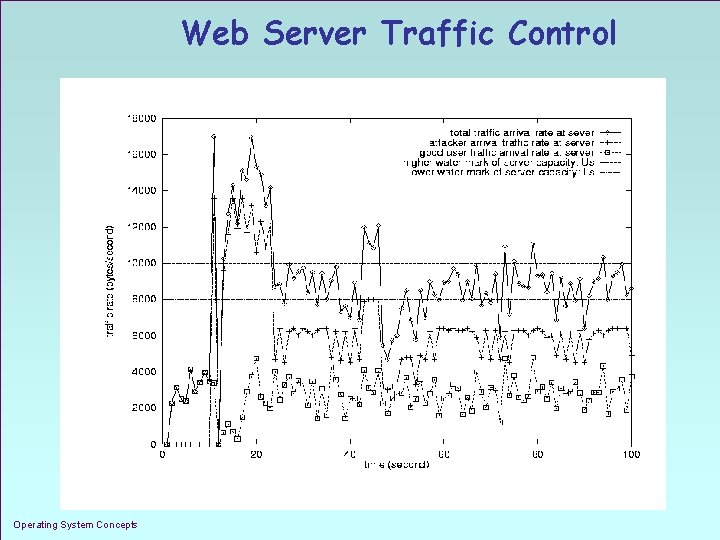
Web Server Traffic Control Operating System Concepts 1. 44

System Implementation n On Linux router Floadable kernel module FCPU resource reservation n Deployment platform FPentium 4/2 G Hz PC Fmultiple 10/100 Mb/s Ethernet interfaces Operating System Concepts 1. 45

System Implementation: cont n OPERA: An Open-Source Extensible Router Architecture http: //www. cse. cuhk. edu. hk/~cslui/ANSRlab/software/opera/ n A Linux-based package for implementing a software programmable router architecture with the aim to facilitate networking experiments for the research community. Using this architecture, one can dynamically load new extension and services into the programmable router. Some interesting extensions include Qo. S support and traceback of DDo. S attacks. ) n Dynamic module loading n Resource reservation n General extension framework n Secured Communication Operating System Concepts 1. 46

Future Work n Offered load-aware control algorithm for computing throttle rate F impact on convergence and stability n Policy-based notion of fairness F heterogeneous network regions, by size, susceptibility to attacks, tariff payment n Selective deployment issues n Impact on real user applications n Defense for other forms of DDo. S like the reflector attack, BGP cascading failure. . etc. Operating System Concepts 1. 48

Conclusions n Extensible routers can help improve network health n Presented a server-centric router throttle mechanism for DDo. S flooding attacks F can better protect good user traffic from aggressive attacker traffic F can keep server operational under an ongoing attack F has efficient implementation Operating System Concepts 1. 49