Defender Message Strategies to Maximize Network Survivability for

Defender Message Strategies to Maximize Network Survivability for Multi-Stage Defense Resource Allocation under Incomplete Information 考量不完全資訊情況下多階段防禦資源分配 以最大化網路存活度之防禦者訊息策略 Advisor: Yeong-Sung Lin Presented by I-Ju Shih 1 2011/11/29

Agenda �Problem Description �Problem Formulation 2 2011/11/29

Problem Description 3 2011/11/29
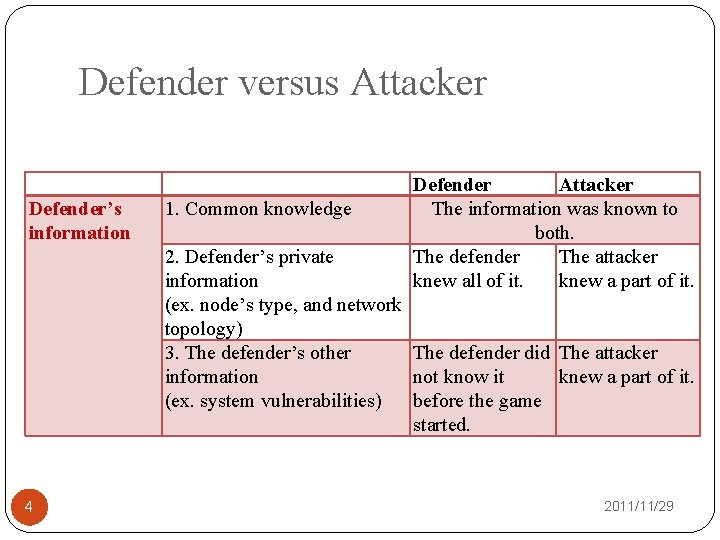
Defender versus Attacker Defender’s information 1. Common knowledge Defender Attacker The information was known to both. The defender The attacker knew all of it. knew a part of it. 2. Defender’s private information (ex. node’s type, and network topology) 3. The defender’s other The defender did The attacker information not know it knew a part of it. (ex. system vulnerabilities) before the game started. 4 2011/11/29
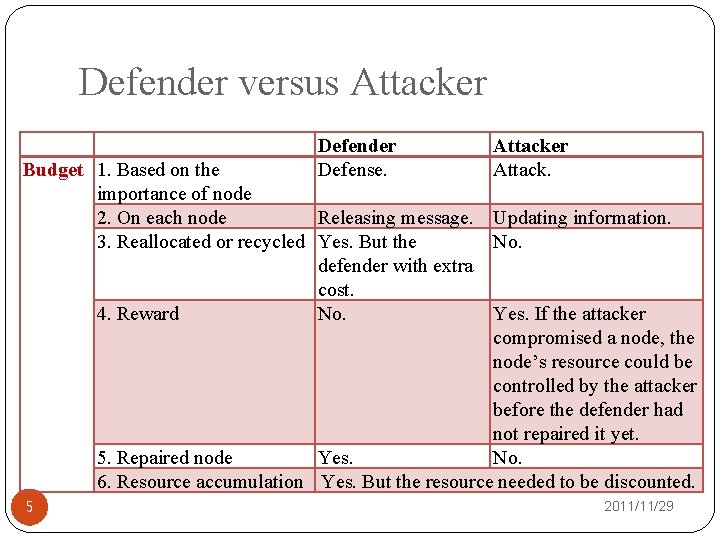
Defender versus Attacker Defender Defense. Attacker Attack. Budget 1. Based on the importance of node 2. On each node Releasing message. Updating information. 3. Reallocated or recycled Yes. But the No. defender with extra cost. 4. Reward No. Yes. If the attacker compromised a node, the node’s resource could be controlled by the attacker before the defender had not repaired it yet. 5. Repaired node Yes. No. 6. Resource accumulation Yes. But the resource needed to be discounted. 5 2011/11/29
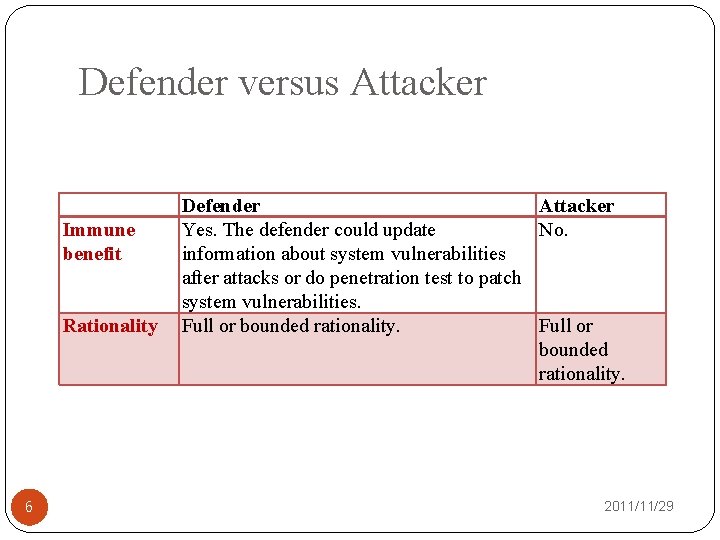
Defender versus Attacker Immune benefit Rationality 6 Defender Attacker Yes. The defender could update No. information about system vulnerabilities after attacks or do penetration test to patch system vulnerabilities. Full or bounded rationality. 2011/11/29

Objective � The network survivability is measured by ADOD. � The game has two players: an attacker (he, A) and a defender (she, 7 D). � Defender �Objective - minimize the damage of the network (ADOD). �Budget Constraint deploying the defense budget in nodes repairing the compromised node releasing message in nodes patching system vulnerabilities � Attacker �Objective - maximize the damage of the network (ADOD). �Budget Constraint – deploying the attack budget in nodes updating information 2011/11/29
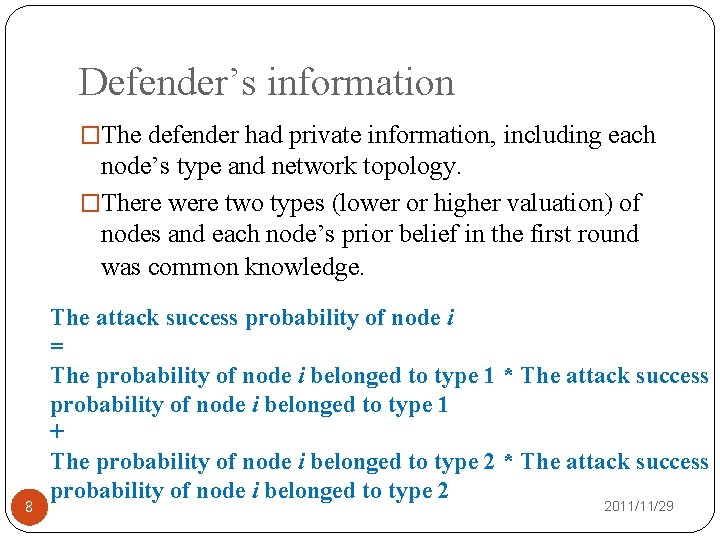
Defender’s information �The defender had private information, including each node’s type and network topology. �There were two types (lower or higher valuation) of nodes and each node’s prior belief in the first round was common knowledge. 8 The attack success probability of node i = The probability of node i belonged to type 1 * The attack success probability of node i belonged to type 1 + The probability of node i belonged to type 2 * The attack success probability of node i belonged to type 2 2011/11/29
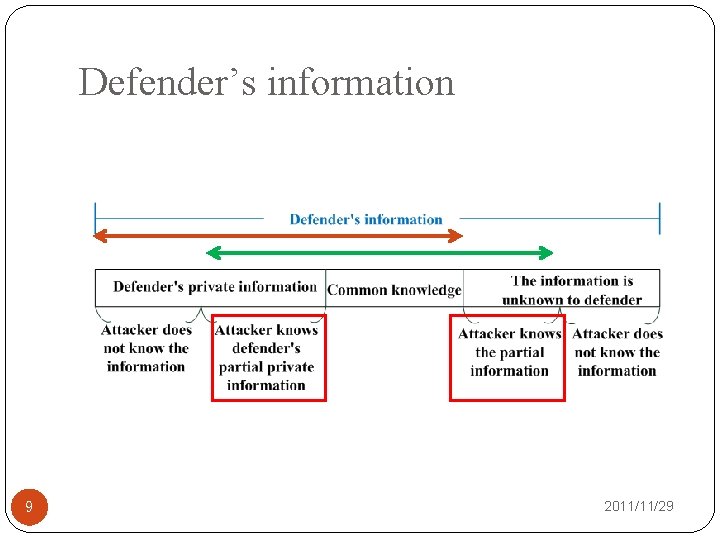
Defender’s information 9 2011/11/29
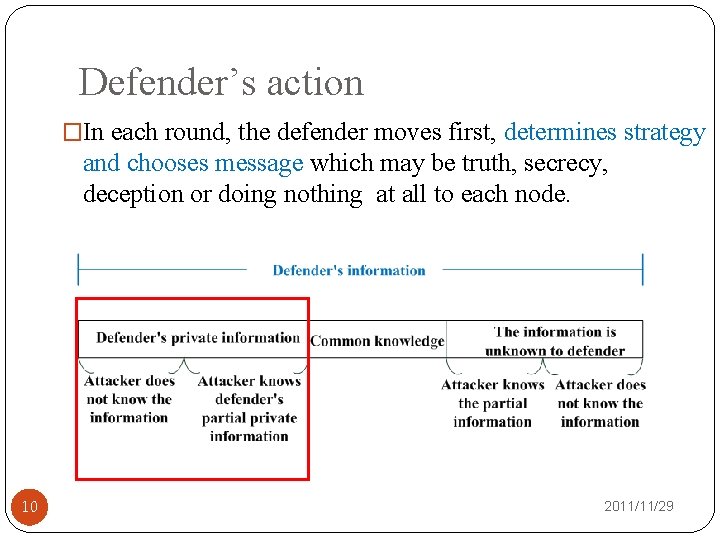
Defender’s action �In each round, the defender moves first, determines strategy and chooses message which may be truth, secrecy, deception or doing nothing at all to each node. 10 2011/11/29

Message releasing �Message releasing could be classified into two situations. A node’s information could be divided into different parts to release message by the defender. The defender could release a node’s defensive state as a message to the attacker. 11 2011/11/29
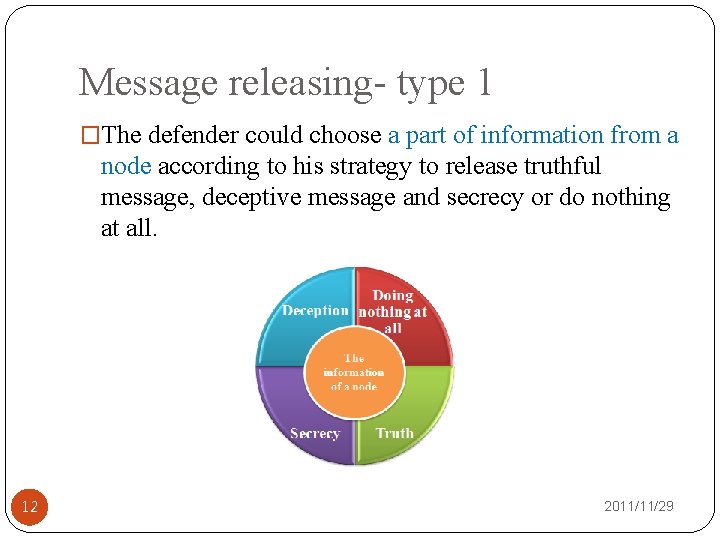
Message releasing- type 1 �The defender could choose a part of information from a node according to his strategy to release truthful message, deceptive message and secrecy or do nothing at all. 12 2011/11/29

Message releasing- type 2 �The defender released a node’s defensive state as a message, which was truth, deception, secrecy or doing nothing at all to each node as a mixed strategy. 13 2011/11/29

Message releasing �The defender chooses : 1. Doing nothing at all if and only if does not publicize information/defense. 2. Truthful message if and only if the public message = actual information/defense. 3. Secrecy if and only if the message is secret. 4. Deceptive message if and only if the message ≠ actual information/defense. Cost: Deceptive message > Secrecy > Truthful message > doing nothing at all 14 2011/11/29
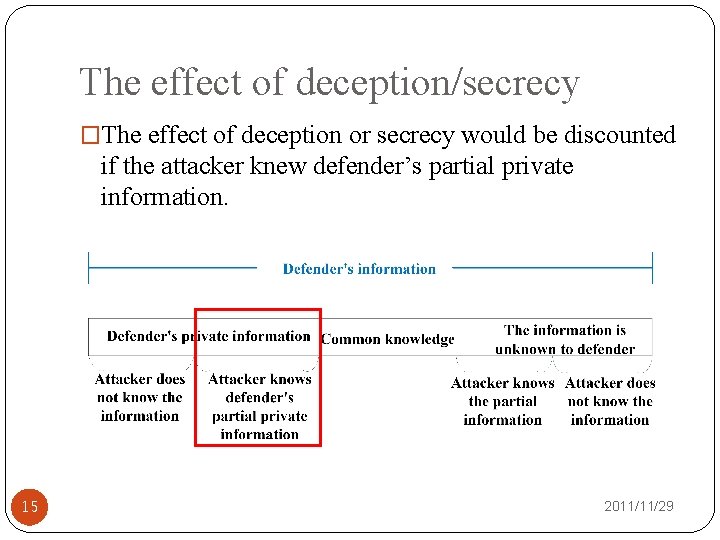
The effect of deception/secrecy �The effect of deception or secrecy would be discounted if the attacker knew defender’s partial private information. 15 2011/11/29
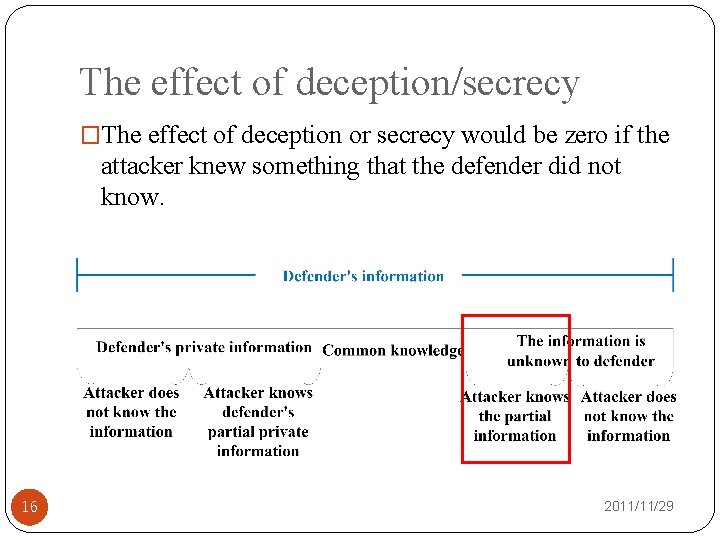
The effect of deception/secrecy �The effect of deception or secrecy would be zero if the attacker knew something that the defender did not know. 16 2011/11/29
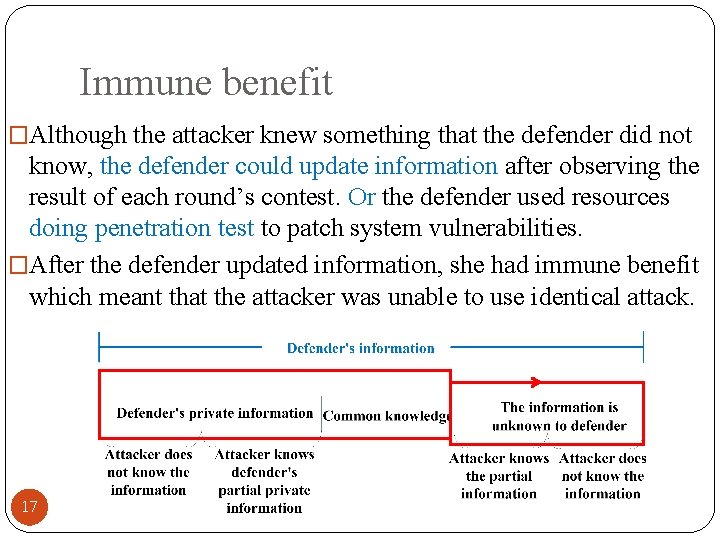
Immune benefit �Although the attacker knew something that the defender did not know, the defender could update information after observing the result of each round’s contest. Or the defender used resources doing penetration test to patch system vulnerabilities. �After the defender updated information, she had immune benefit which meant that the attacker was unable to use identical attack. 17
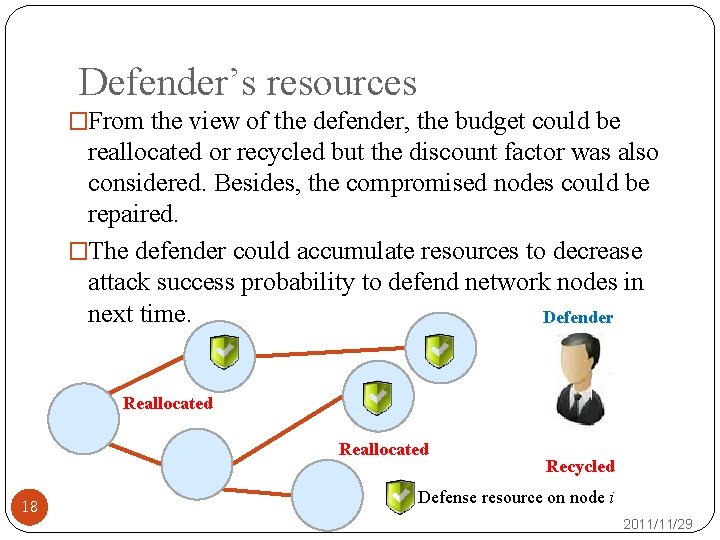
Defender’s resources �From the view of the defender, the budget could be reallocated or recycled but the discount factor was also considered. Besides, the compromised nodes could be repaired. �The defender could accumulate resources to decrease attack success probability to defend network nodes in next time. Defender Reallocated 18 Recycled Defense resource on node i 2011/11/29
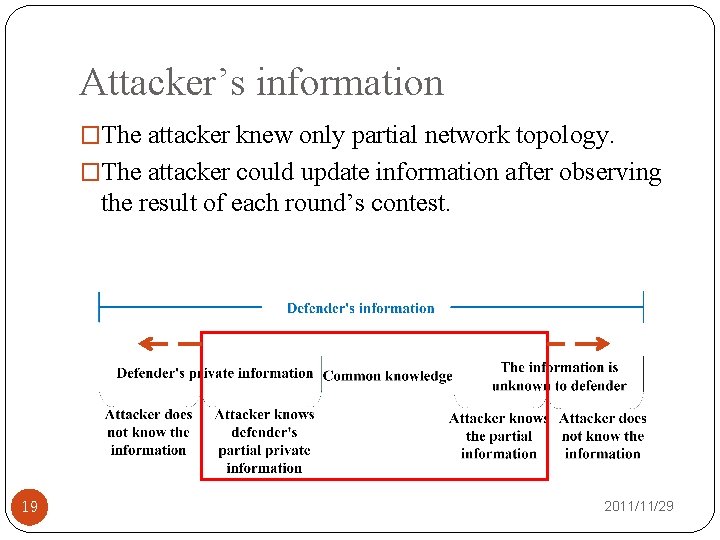
Attacker’s information �The attacker knew only partial network topology. �The attacker could update information after observing the result of each round’s contest. 19 2011/11/29

Attacker’s resources �The attacker could accumulate experience to increase attack success probability to compromise network nodes in next time. �The attacker could increase resources when the attacker compromised network nodes, before the defender had not repaired the nodes yet. 20 2011/11/29
Network topology �We considered a complex system with n nodes in series-parallel. �A node consisted of M components which might be different component or the same. (M ≥ 1) 21 2011/11/29
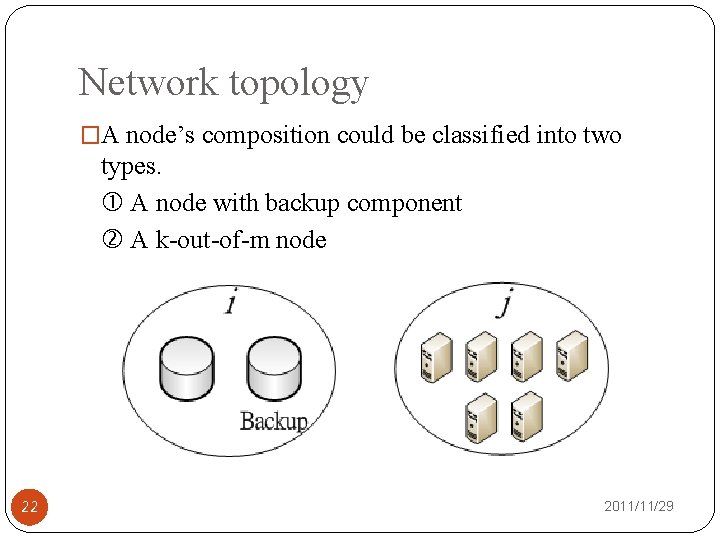
Network topology �A node’s composition could be classified into two types. A node with backup component A k-out-of-m node 22 2011/11/29
Network topology �The relationship between nodes could be classified into three types. Independence A node could function solely. Dependence When a node was destroyed, the nodes dependent on the destroyed node would not operate normally. Interdependence When a node was destroyed, the node interdependent on the destroyed node would not operate normally and vice versa. 23 2011/11/29
24 2011/11/29

Problem Formulation 25 2011/11/29

Given �The total budget of network defender. �The total budget of cyber attacker. �Both the defender and the attacker have incomplete information about each other. 26 2011/11/29

Objective �Minimize the maximum damage degree of network (ADOD). 27 2011/11/29

Subject to �The total budget constraint of network defender. �The total budget constraint of cyber attacker. 28 2011/11/29
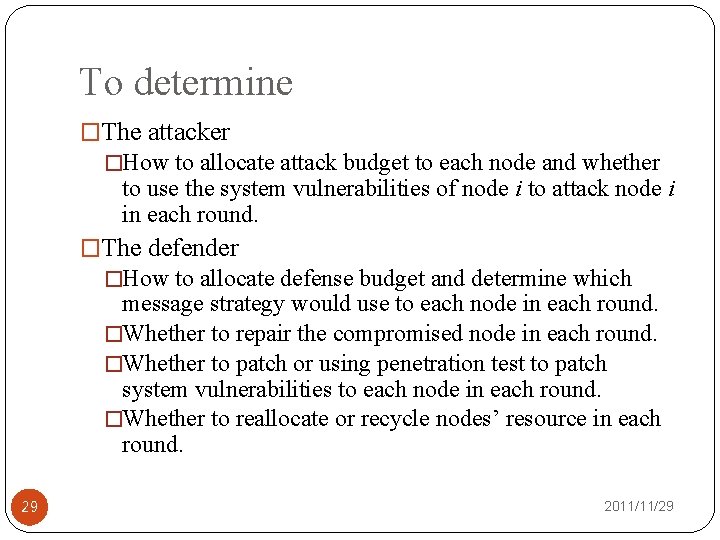
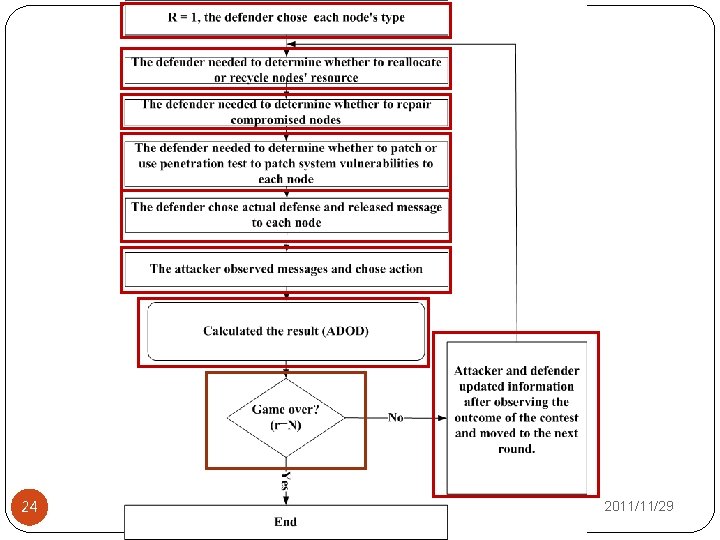
To determine �The attacker �How to allocate attack budget to each node and whether to use the system vulnerabilities of node i to attack node i in each round. �The defender �How to allocate defense budget and determine which message strategy would use to each node in each round. �Whether to repair the compromised node in each round. �Whether to patch or using penetration test to patch system vulnerabilities to each node in each round. �Whether to reallocate or recycle nodes’ resource in each round. 29 2011/11/29
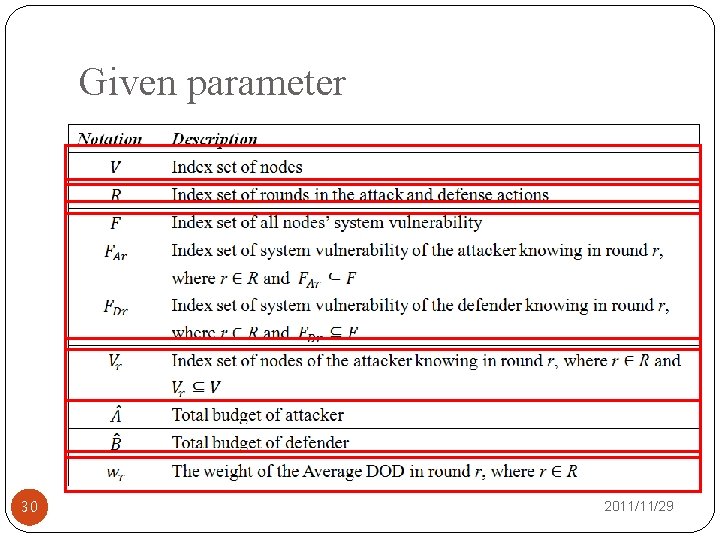
Given parameter 30 2011/11/29
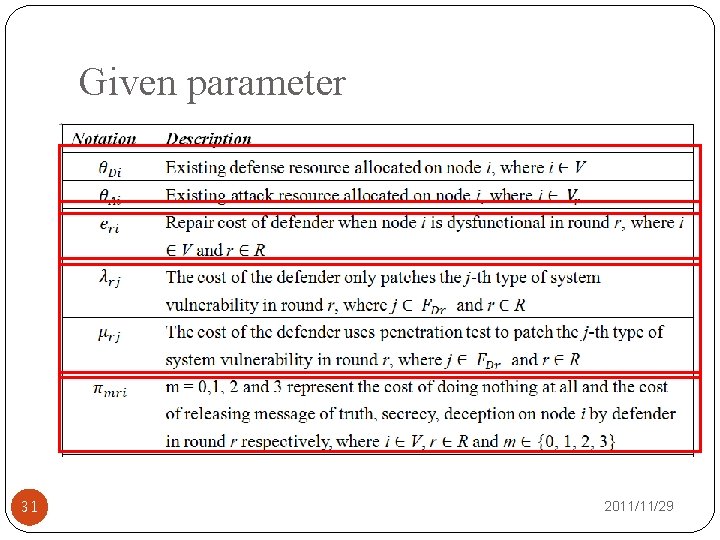
Given parameter 31 2011/11/29
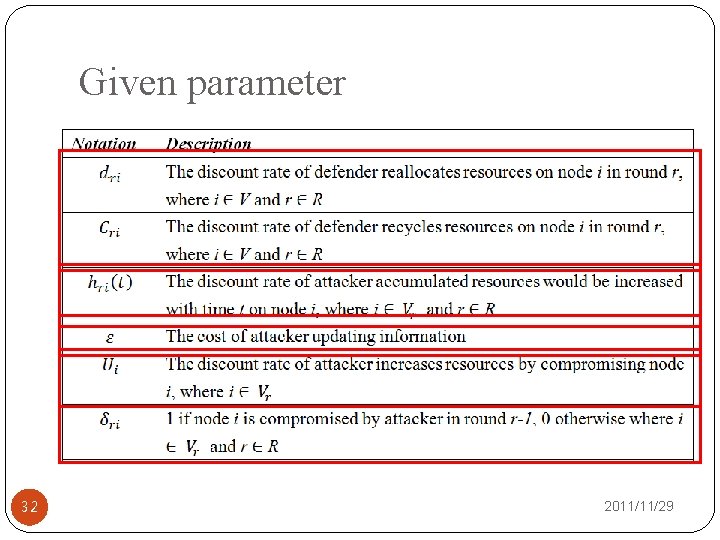
Given parameter 32 2011/11/29
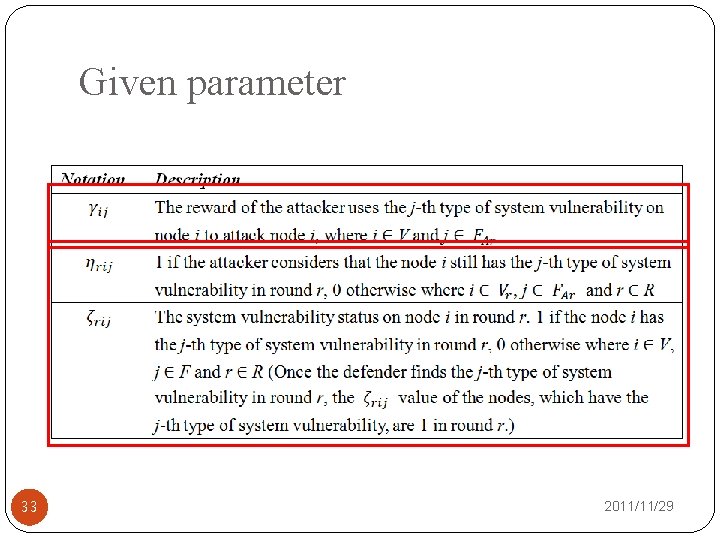
Given parameter 33 2011/11/29
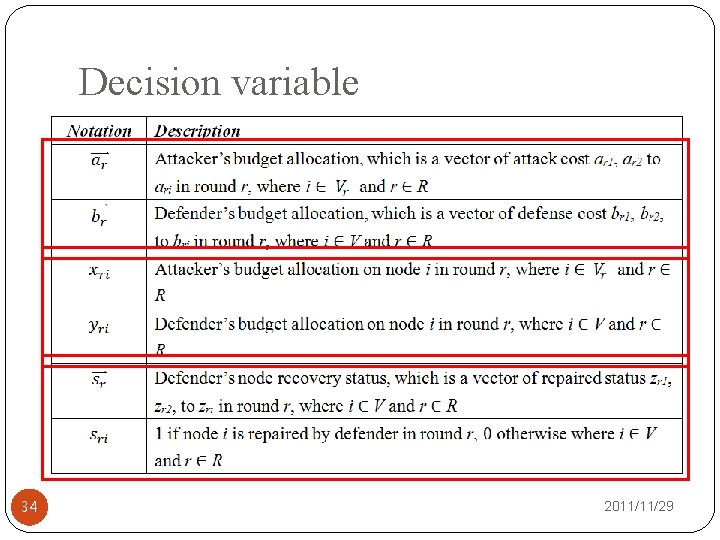
Decision variable 34 2011/11/29
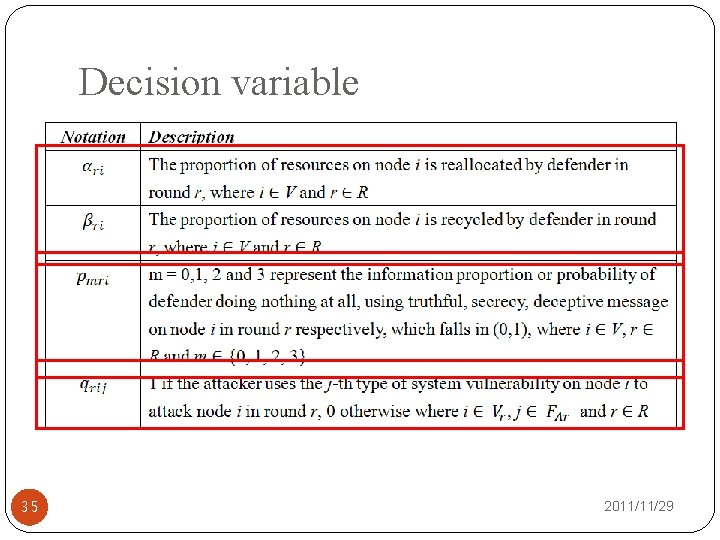
Decision variable 35 2011/11/29
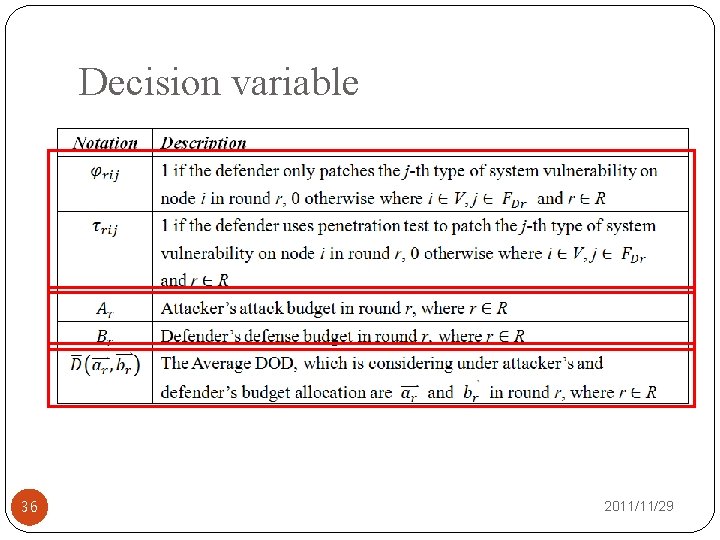
Decision variable 36 2011/11/29
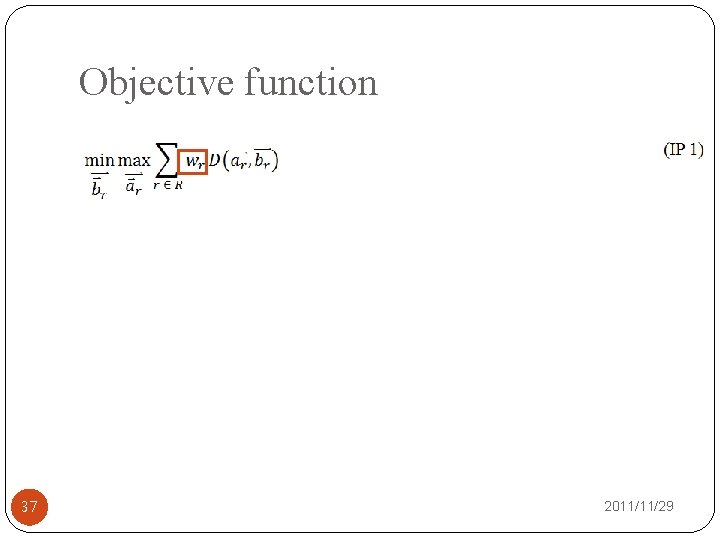
Objective function 37 2011/11/29
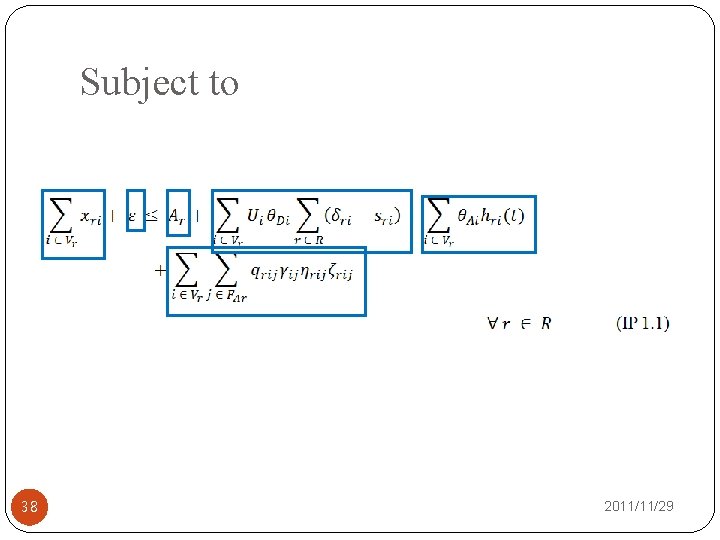
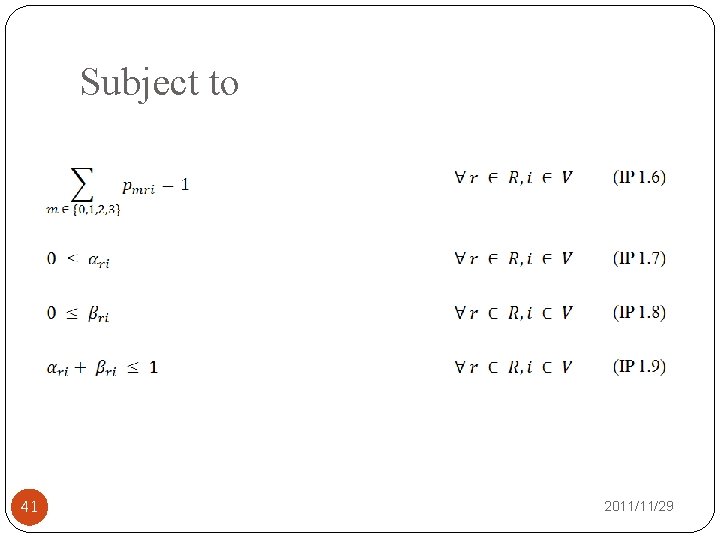
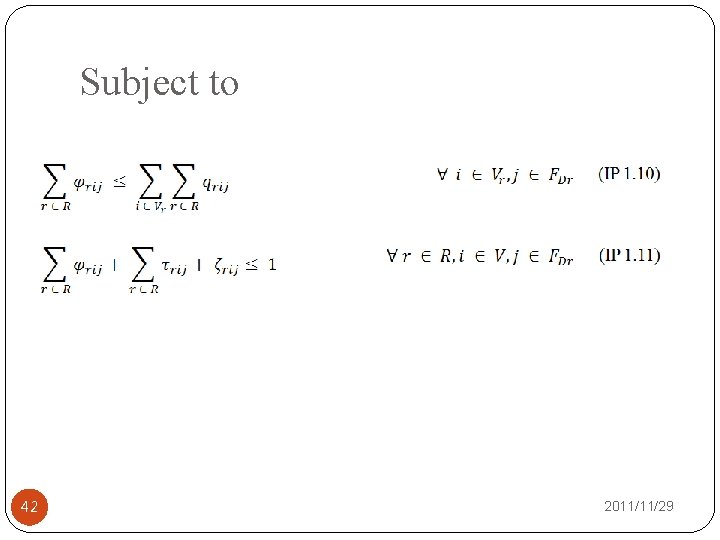
Subject to 38 2011/11/29
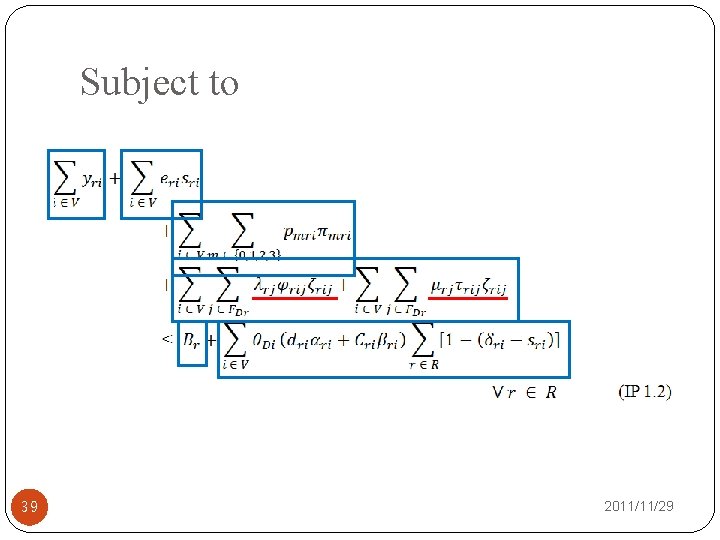
Subject to 39 2011/11/29
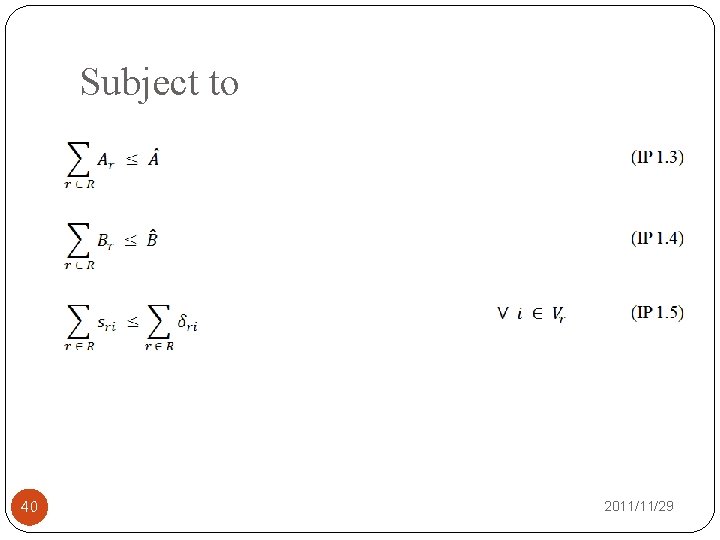
Subject to 40 2011/11/29
Subject to 41 2011/11/29
Subject to 42 2011/11/29
Thanks for your listening. 43 2011/11/29
- Slides: 43