Deep Security and VMware NSX Advanced Security Framework







- Slides: 31

Deep Security and VMware NSX Advanced Security Framework for the Software-Defined Data Center Anand Patil National Sales Manager, SDDC CONFIDENTIAL 1

Let’s begin with how things are, and how things should be… Your data center 2

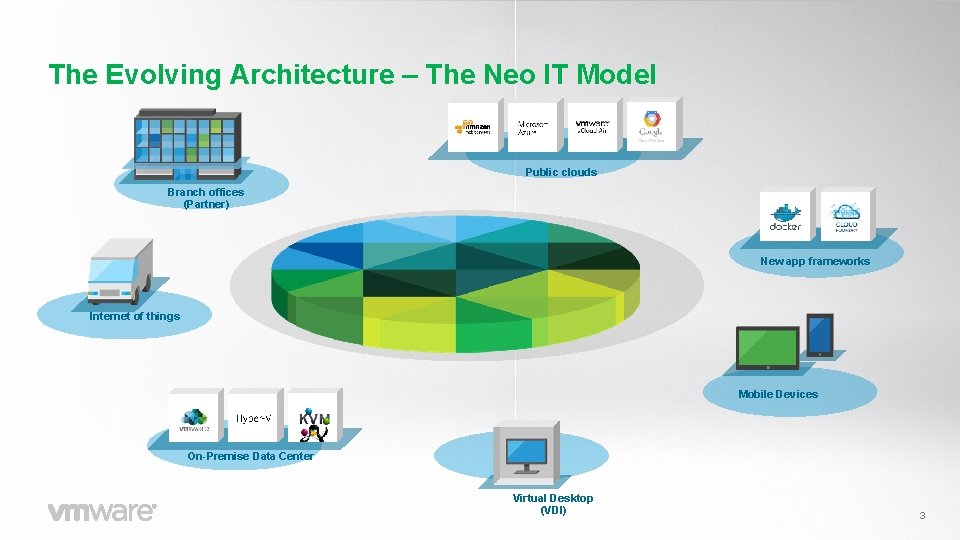
The Evolving Architecture – The Neo IT Model Public clouds Branch offices (Partner) New app frameworks Internet of things Mobile Devices On-Premise Data Center Virtual Desktop (VDI) 3

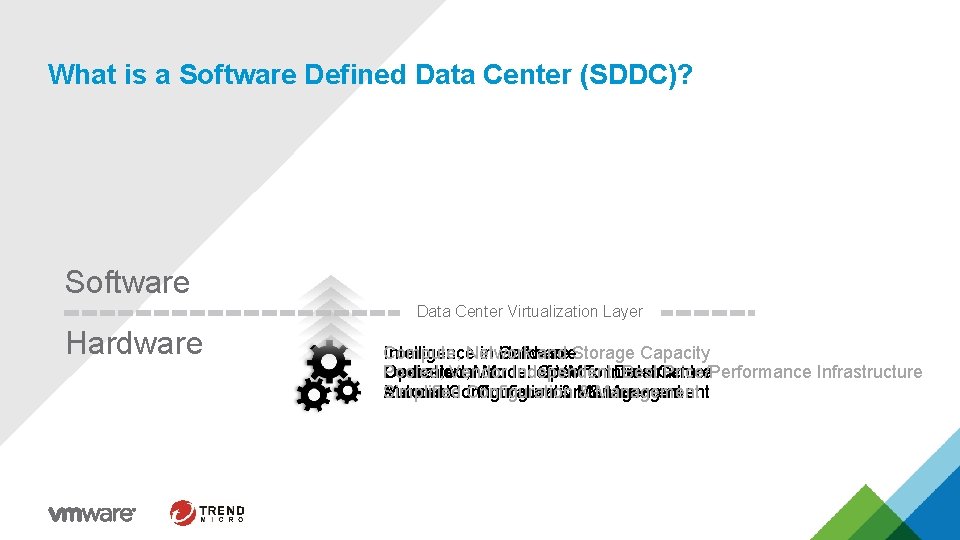
What is a Software Defined Data Center (SDDC)? Software Data Center Virtualization Layer Hardware Software Intelligence. Network in Hardware Compute, and Storage Capacity Operational Model of VM for. Infrastructure Data Dedicated, Vendor Specific Pooled, Vendor Independent, Best. Center Price/Performance Infrastructure Automated Configuration Management Manual Configuration & Management Simplified Configuration &&Management

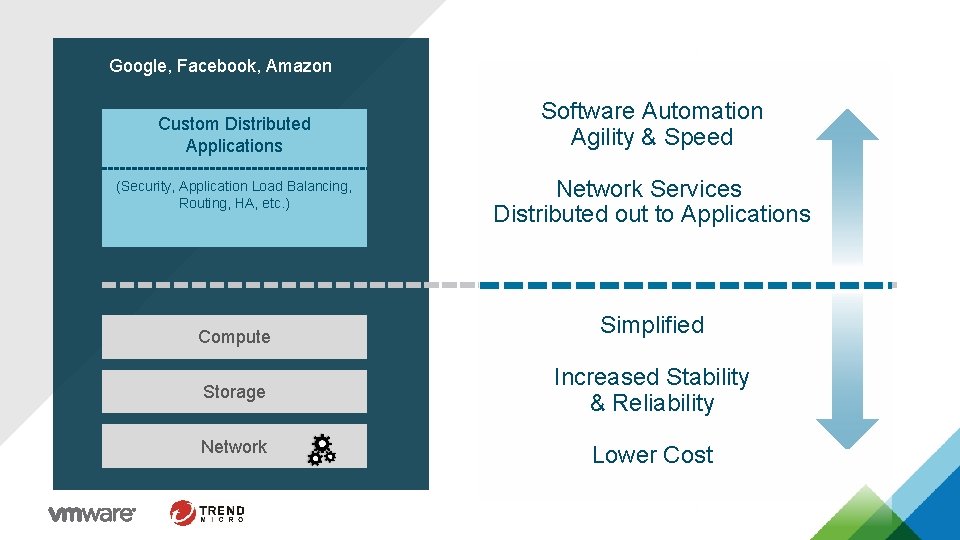
Google, Facebook, Amazon Custom Distributed Applications (Security, Application Load Balancing, Routing, HA, etc. ) Compute Software Automation Agility & Speed Network Services Distributed out to Applications Simplified Storage Increased Stability & Reliability Network Lower Cost

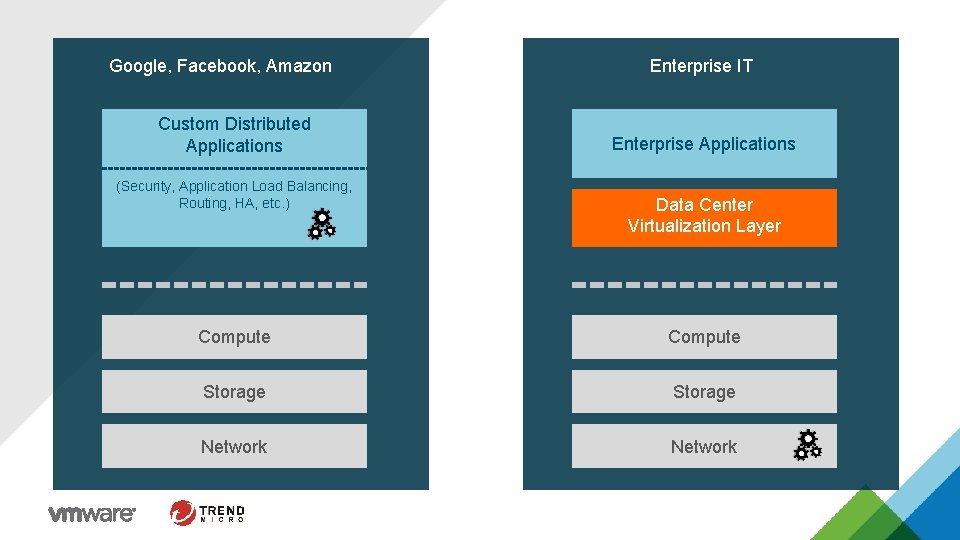
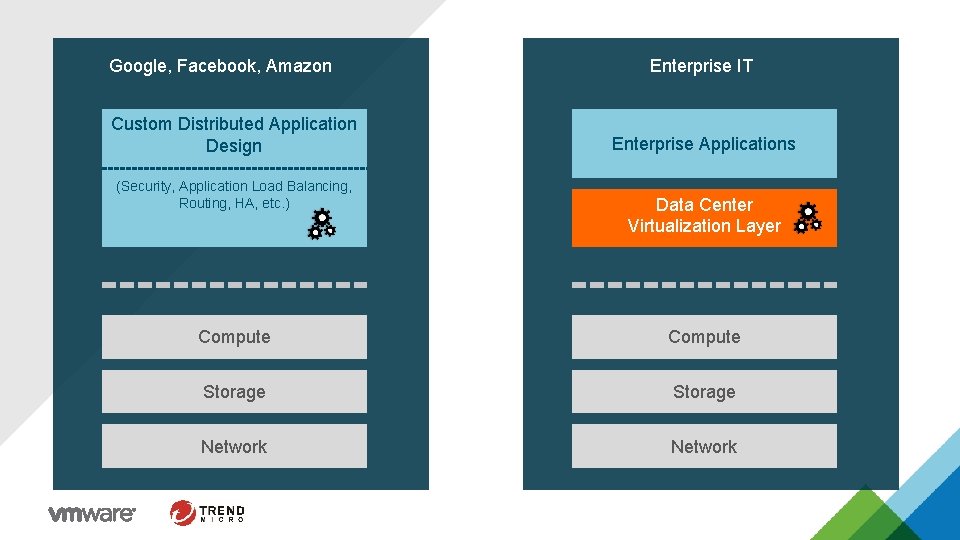
Google, Facebook, Amazon Custom Distributed Applications (Security, Application Load Balancing, Routing, HA, etc. ) Enterprise IT Enterprise Applications Data Center Virtualization Layer Compute Storage Network

Google, Facebook, Amazon Custom Distributed Application Design (Security, Application Load Balancing, Routing, HA, etc. ) Enterprise IT Enterprise Applications Data Center Virtualization Layer Compute Storage Network

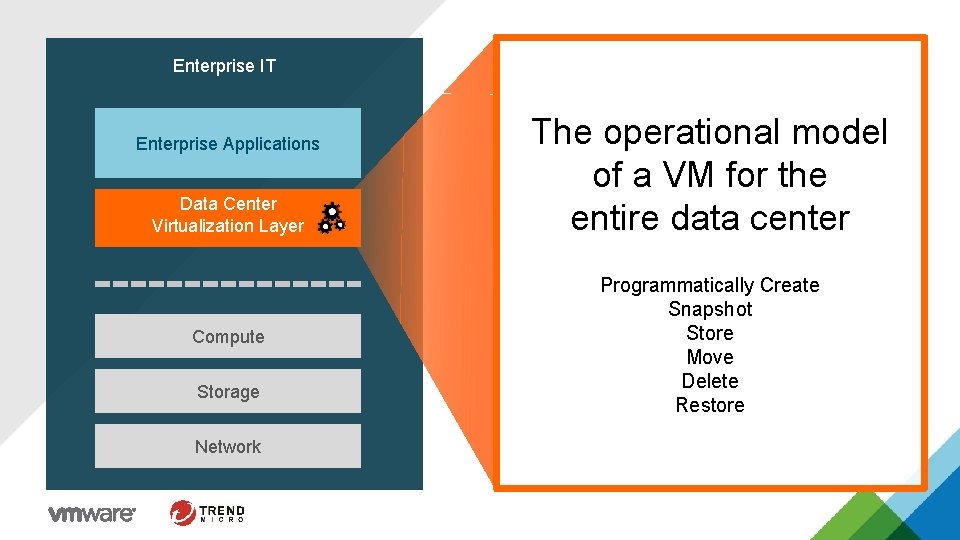
Enterprise IT Enterprise Applications Data Center Virtualization Layer Compute Storage Network The operational model of a VM for the entire data center Programmatically Create Snapshot Store Move Delete Restore

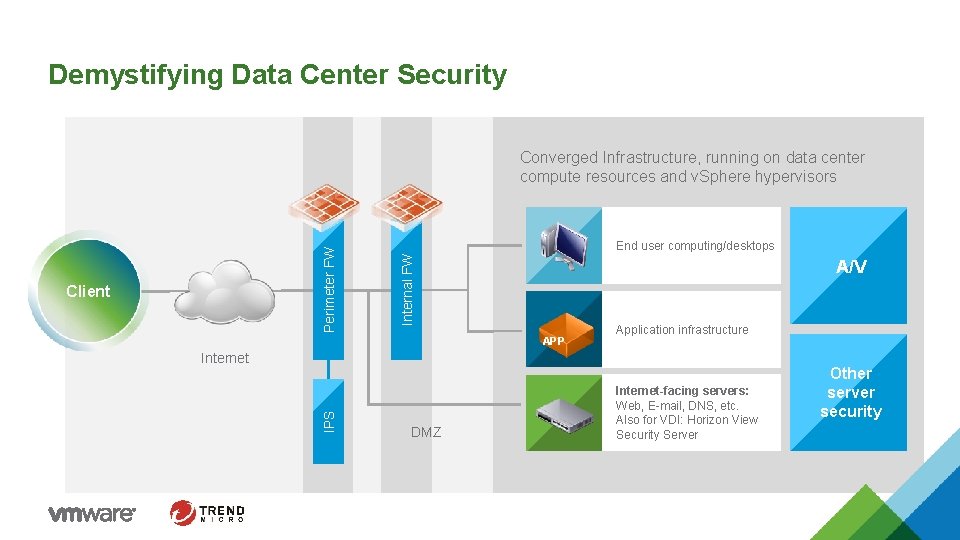
Demystifying Data Center Security Client End user computing/desktops Internal FW Perimeter FW Converged Infrastructure, running on data center compute resources and v. Sphere hypervisors A/V APP Application infrastructure IPS Internet DMZ Internet-facing servers: Web, E-mail, DNS, etc. Also for VDI: Horizon View Security Server Other server security 9

Why do breaches still occur? Data Center Perimeter Today’s data centers are protected by strong perimeter defense… But threats and exploits still infect servers. Lowpriority systems are often the target. Threats can lie dormant, waiting for the right moment to strike. 10110100110 1010000010 1001110010100 Attacks spread inside the data center, where internal controls are often weak. Critical systems are targeted. Server-server traffic growth has outpaced client-server traffic. The attack spreads and goes unnoticed. Possibly after months of reconnaissance, the infiltration relays secret data to the attacker.

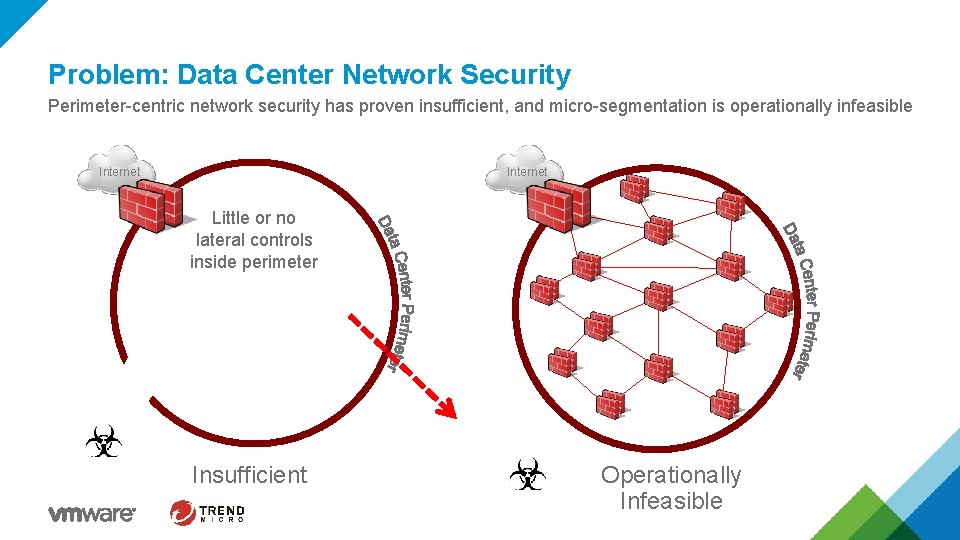
Problem: Data Center Network Security Perimeter-centric network security has proven insufficient, and micro-segmentation is operationally infeasible Internet Little or no lateral controls inside perimeter Insufficient Operationally Infeasible

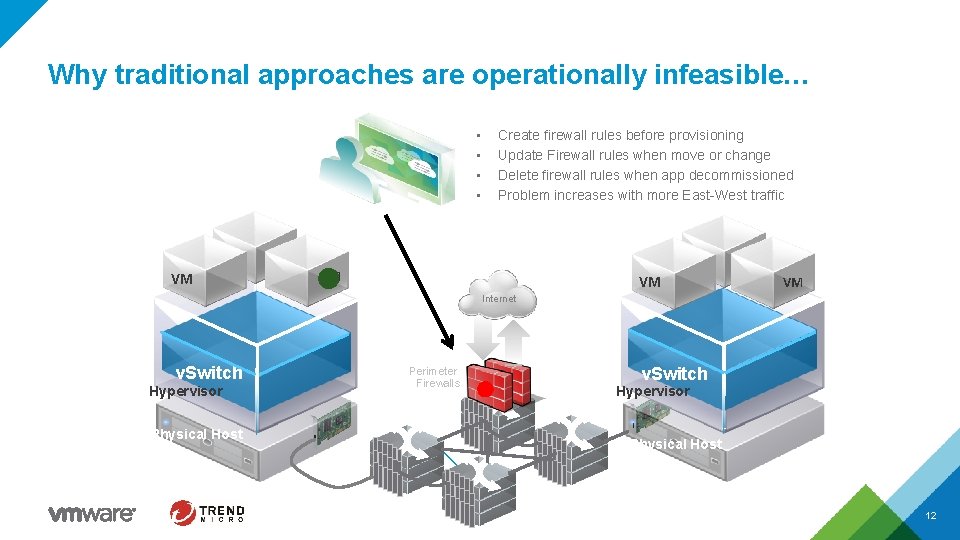
Why traditional approaches are operationally infeasible… • • VM Create firewall rules before provisioning Update Firewall rules when move or change Delete firewall rules when app decommissioned Problem increases with more East-West traffic VM VM VM Internet v. Switch Hypervisor Physical Host Perimeter Firewalls v. Switch Hypervisor Physical Host 12

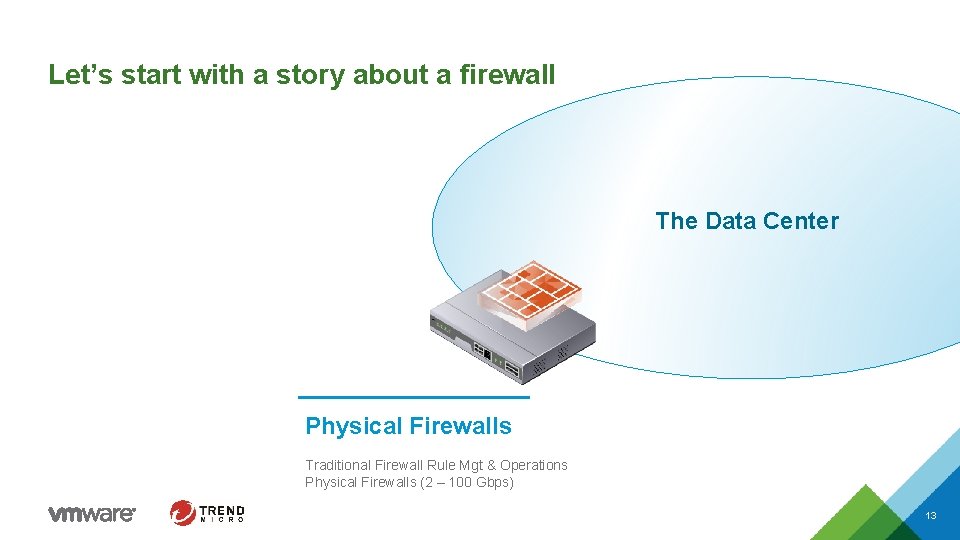
Let’s start with a story about a firewall The Data Center Physical Firewalls Traditional Firewall Rule Mgt & Operations Physical Firewalls (2 – 100 Gbps) 13

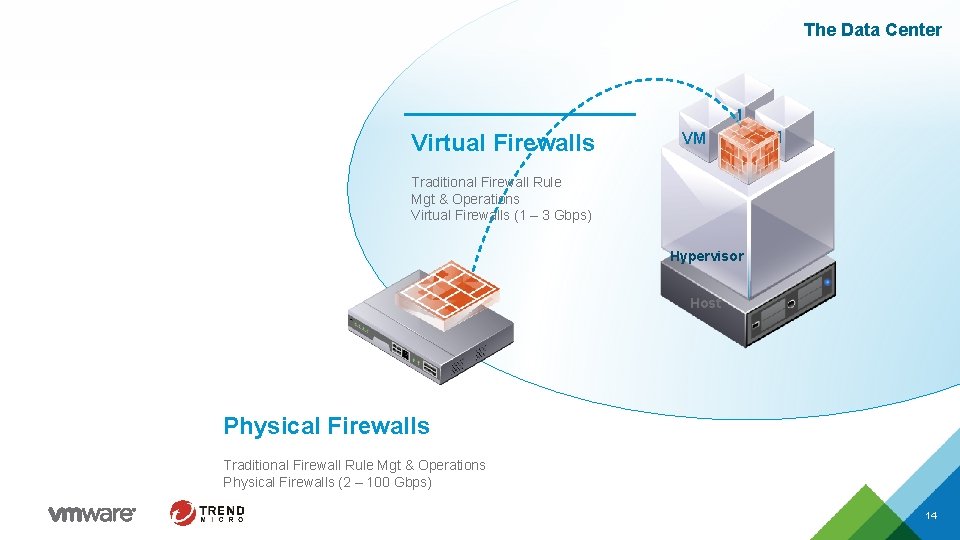
The Data Center VM Virtual Firewalls VM VM VM Traditional Firewall Rule Mgt & Operations Virtual Firewalls (1 – 3 Gbps) Hypervisor Host Physical Firewalls Traditional Firewall Rule Mgt & Operations Physical Firewalls (2 – 100 Gbps) 14

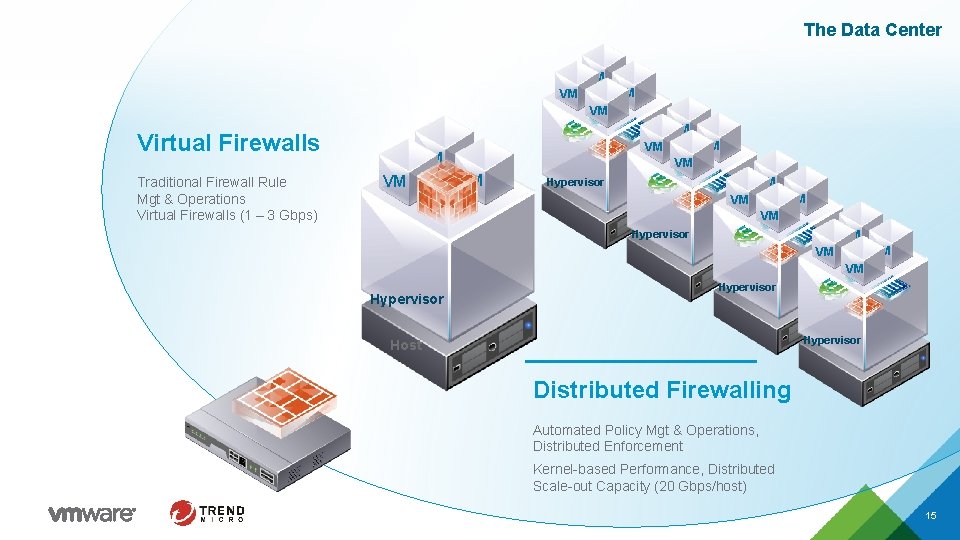
The Data Center VM VM VM Virtual Firewalls Traditional Firewall Rule Mgt & Operations Virtual Firewalls (1 – 3 Gbps) VM VM Hypervisor VM VM VM Hypervisor Host Distributed Firewalling Automated Policy Mgt & Operations, Distributed Enforcement Kernel-based Performance, Distributed Scale-out Capacity (20 Gbps/host) 15

The Data Center VM VM VM NSX v. Switch Hypervisor VM VM NSX v. Switch Hypervisor VM VM VM VM VM NSX v. Switch Hypervisor NSX v. Switch Hypervisor 16

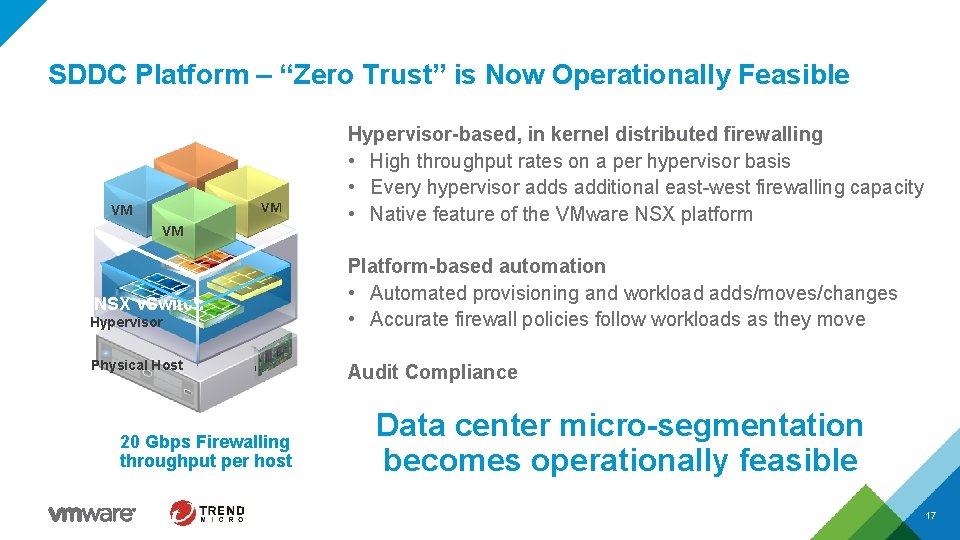
SDDC Platform – “Zero Trust” is Now Operationally Feasible VM VM VM NSX v. Switch Hypervisor Physical Host 20 Gbps Firewalling throughput per host Hypervisor-based, in kernel distributed firewalling • High throughput rates on a per hypervisor basis • Every hypervisor adds additional east-west firewalling capacity • Native feature of the VMware NSX platform Platform-based automation • Automated provisioning and workload adds/moves/changes • Accurate firewall policies follow workloads as they move Audit Compliance Data center micro-segmentation becomes operationally feasible 17

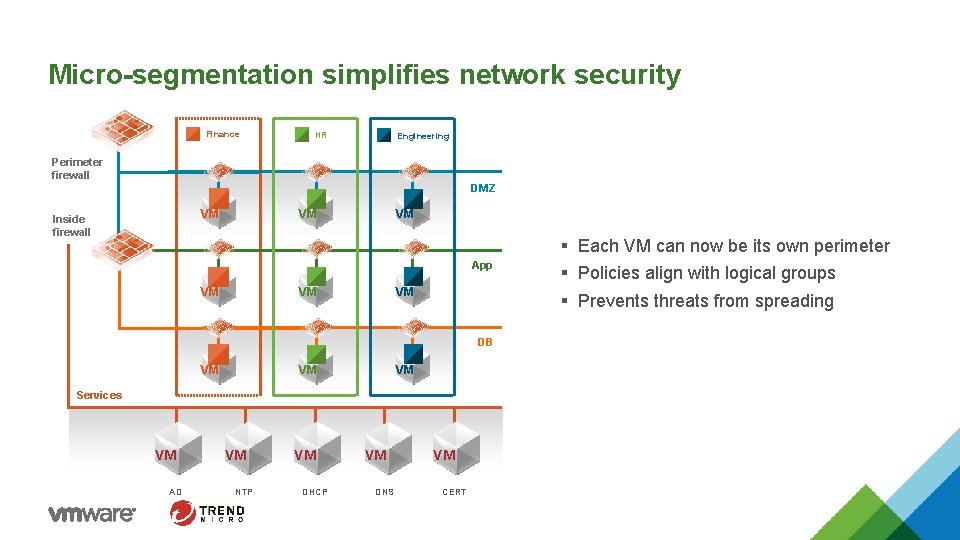
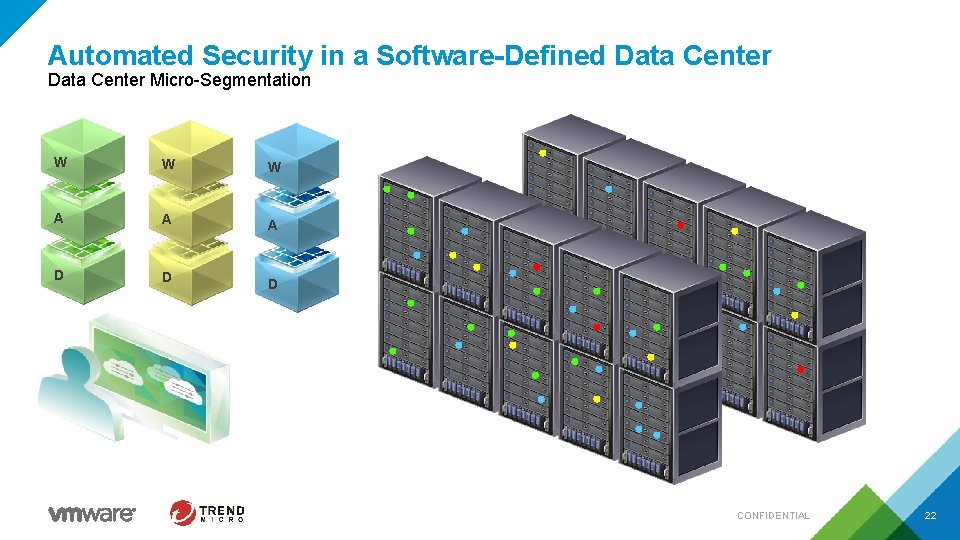
Micro-segmentation simplifies network security Finance HR Engineering Perimeter firewall DMZ VM Inside firewall VM VM App VM VM VM DB VM VM VM Services VM AD VM NTP VM DHCP VM DNS VM CERT § Each VM can now be its own perimeter § Policies align with logical groups § Prevents threats from spreading

Network Virtualization is at the core of an SDDC approach Non-Disrupting Deployment v. Switch Hypervisor Virtualization layer v. Switch Hypervisor v. Switch Network, storage, compute Hypervisor v. Switch Hypervisor

Network Virtualization is at the core of an SDDC approach Non-Disrupting Deployment v. Switch Hypervisor Virtual Data Centers v. Switch Hypervisor “Network hypervisor” v. Switch Hypervisor Virtualization layer v. Switch Hypervisor v. Switch Network, storage, compute Hypervisor v. Switch Hypervisor

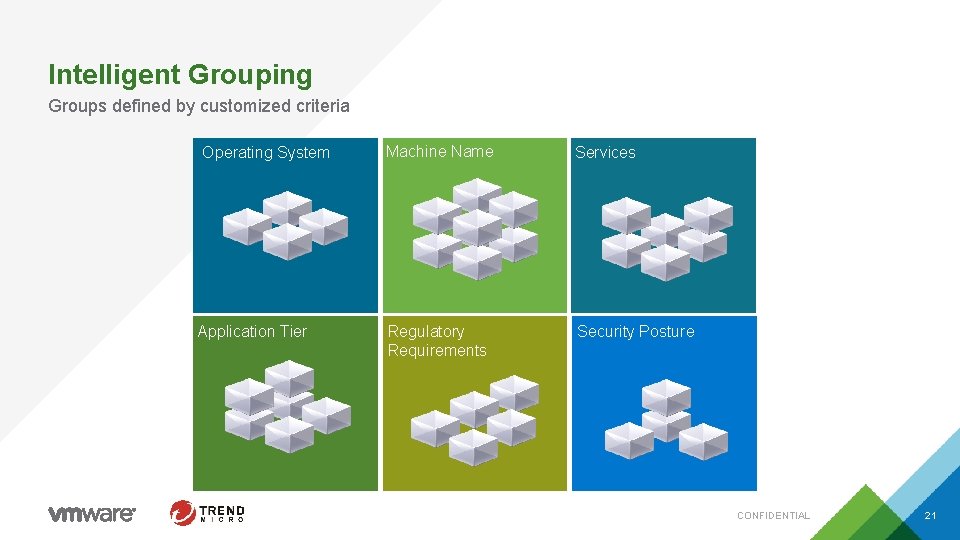
Intelligent Grouping Groups defined by customized criteria Operating System Application Tier Machine Name Services Regulatory Requirements Security Posture CONFIDENTIAL 21

Automated Security in a Software-Defined Data Center Micro-Segmentation W W W A A A D D D CONFIDENTIAL 22

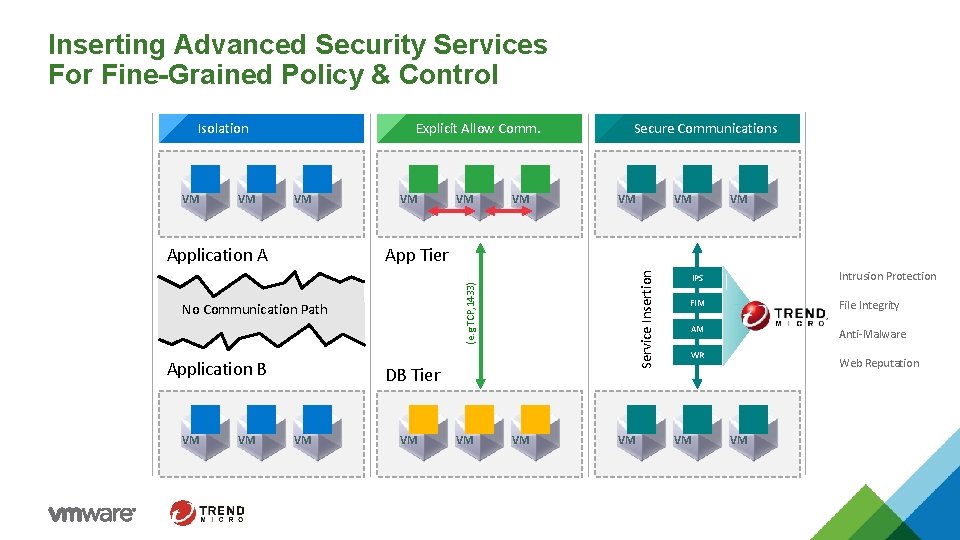
Inserting Advanced Security Services For Fine-Grained Policy & Control Isolation VM Application A VM Application B VM VM VM App Tier No Communication Path VM VM Service Insertion VM Secure Communications (e. g TCP, 1433) VM Explicit Allow Comm. DB Tier VM VM VM IPS Intrusion Protection FIM File Integrity AM Anti-Malware WR VM Web Reputation VM

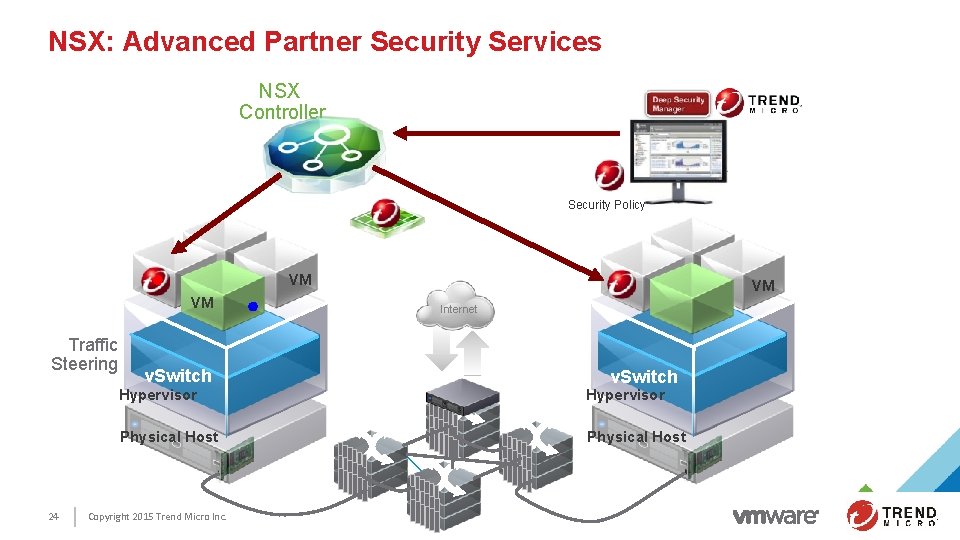
NSX: Advanced Partner Security Services NSX Controller Security Policy VM VM Traffic Steering 24 v. Switch VM Internet VM v. Switch Hypervisor Physical Host Copyright 2015 Trend Micro Inc.

NSX: Security Extensible Platform Add Trend Micro advanced services to your micro-segmentation deployment for greater security Apply the NSX operational model to your advanced security products Adapt to changing security conditions in the data center by enabling security solutions that share intelligence 1 2 3 VM Traditional Data Center NSX Data Center Static service chain Dynamic service chain In a traditional data center, security services must be configured when the network is architected, meaning the “chain” of services is locked in once deployed. This is an inefficient use of resources and cannot defend against changing threat conditions. In an NSX data center, 3 rd-party security solutions use NSX security tags to share intelligence, adapting to changing security conditions. NSX automatically applies the correct security function as needed.

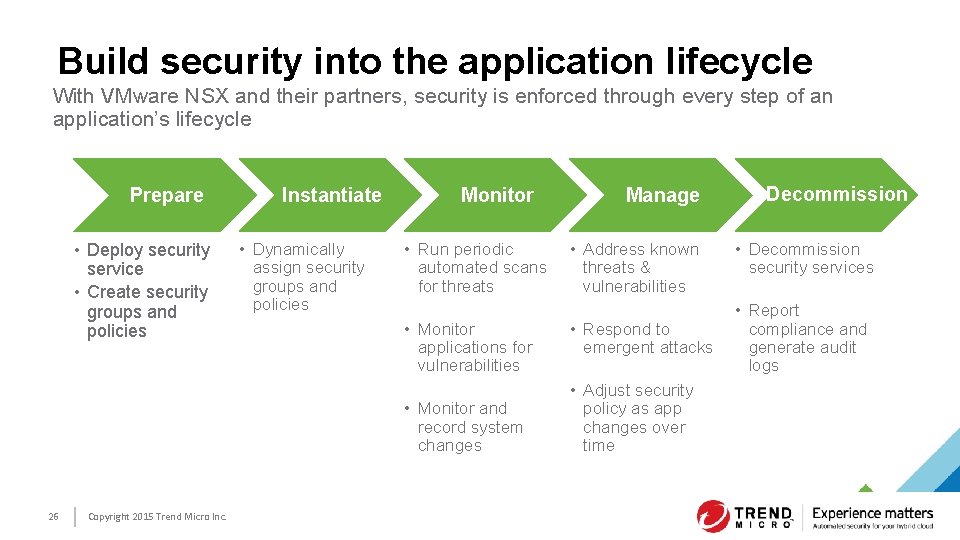
Build security into the application lifecycle With VMware NSX and their partners, security is enforced through every step of an application’s lifecycle Prepare • Deploy security service • Create security groups and policies Instantiate • Dynamically assign security groups and policies Monitor • Run periodic automated scans for threats • Monitor applications for vulnerabilities • Monitor and record system changes 26 Copyright 2015 Trend Micro Inc. Manage • Address known threats & vulnerabilities • Respond to emergent attacks • Adjust security policy as app changes over time Decommission • Decommission security services • Report compliance and generate audit logs

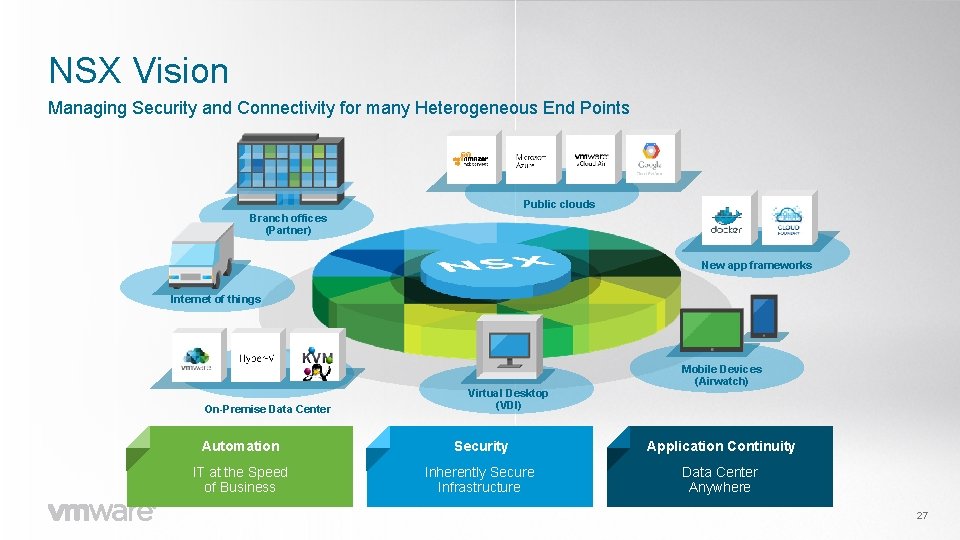
NSX Vision Managing Security and Connectivity for many Heterogeneous End Points Public clouds Branch offices (Partner) New app frameworks Internet of things On-Premise Data Center Virtual Desktop (VDI) Mobile Devices (Airwatch) Automation Security Application Continuity IT at the Speed of Business Inherently Secure Infrastructure Data Center Anywhere 27

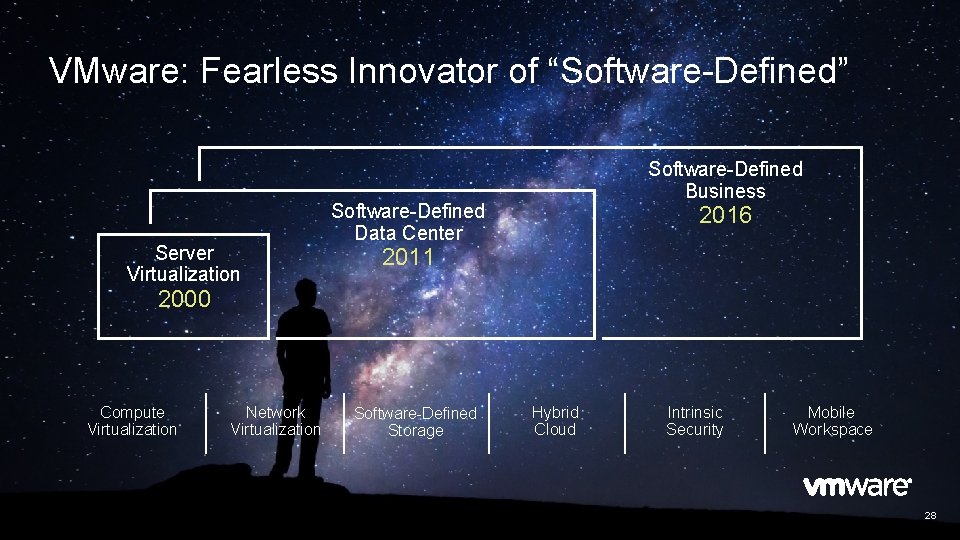
VMware: Fearless Innovator of “Software-Defined” Server Virtualization Software-Defined Business Software-Defined Data Center 2016 2011 2000 Compute Virtualization Network Virtualization Software-Defined Storage Hybrid Cloud Intrinsic Security Mobile Workspace 28

Thank You!

Thank you

CONFIDENTIAL 31