Deep Packet Inspection as a Service Yaron Koral




- Slides: 29

Deep Packet Inspection as a Service Yaron Koral† Joint work with Anat Bremler-Barr‡, Yotam Harchol† and David Hay† †The Hebrew University, Israel ‡IDC Herzliya, Israel This work was supported by European Research Council (ERC) Starting Grant no. 259085

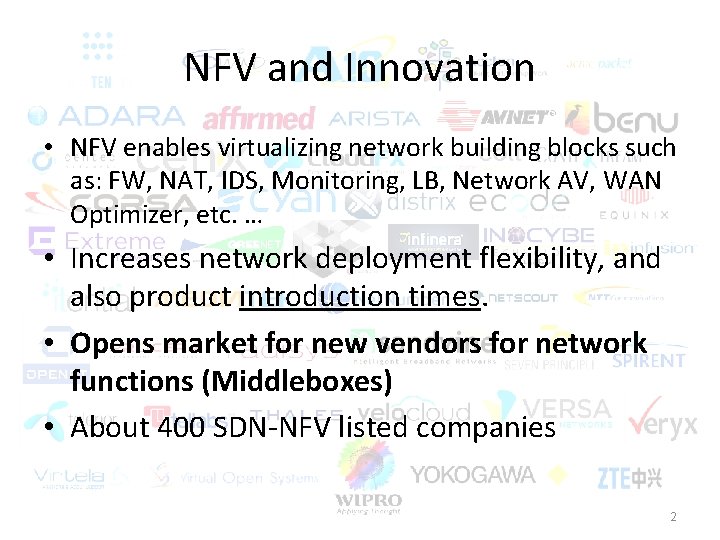
NFV and Innovation • NFV enables virtualizing network building blocks such as: FW, NAT, IDS, Monitoring, LB, Network AV, WAN Optimizer, etc. … • Increases network deployment flexibility, and also product introduction times. • Opens market for new vendors for network functions (Middleboxes) • About 400 SDN-NFV listed companies 2

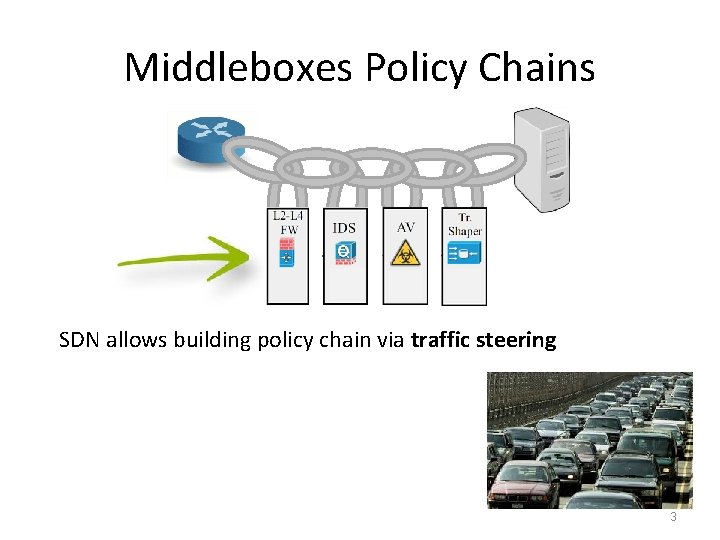
Middleboxes Policy Chains SDN allows building policy chain via traffic steering 3

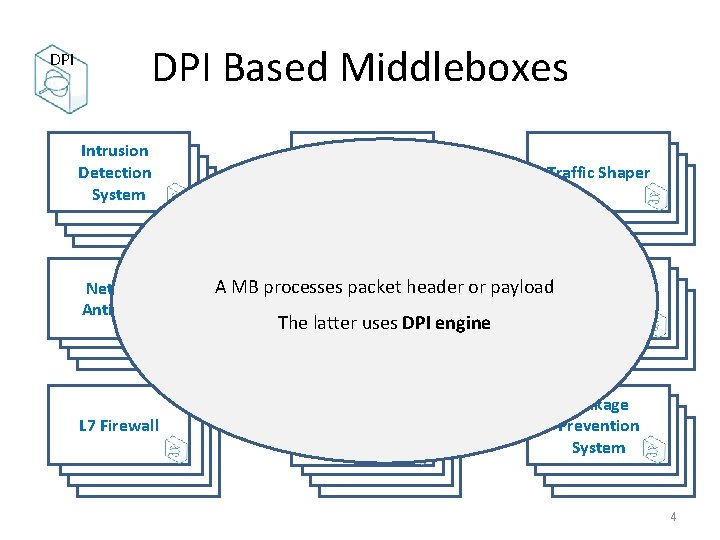
DPI Based Middleboxes Intrusion Detection System Network Anti-Virus L 7 Firewall Network Analytic Traffic Shaper A MB processes packet header or payload Lawful Copyright Enforcement Interception L 7 Load Balancer Leakage Prevention System The latter uses DPI engine 4

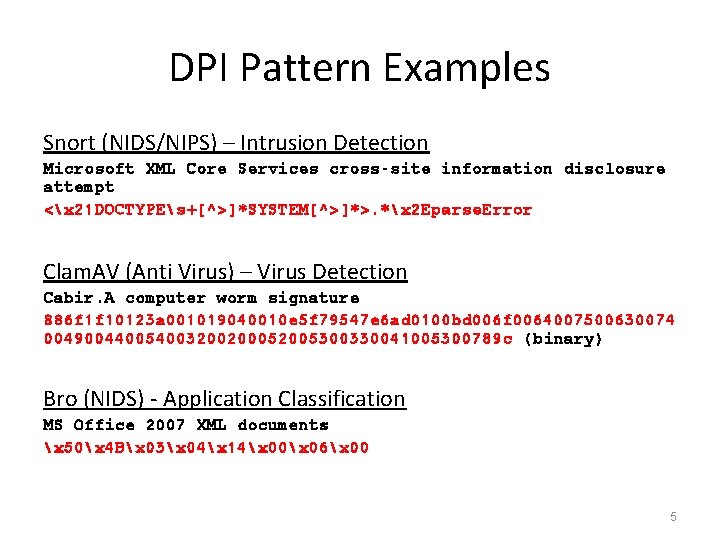
DPI Pattern Examples Snort (NIDS/NIPS) – Intrusion Detection Microsoft XML Core Services cross-site information disclosure attempt <x 21 DOCTYPEs+[^>]*SYSTEM[^>]*>. *x 2 Eparse. Error Clam. AV (Anti Virus) – Virus Detection Cabir. A computer worm signature 886 f 1 f 10123 a 001019040010 e 5 f 79547 e 6 ad 0100 bd 006 f 0064007500630074 004900440054003200200052005300330041005300789 c (binary) Bro (NIDS) - Application Classification MS Office 2007 XML documents x 50x 4 Bx 03x 04x 14x 00x 06x 00 5

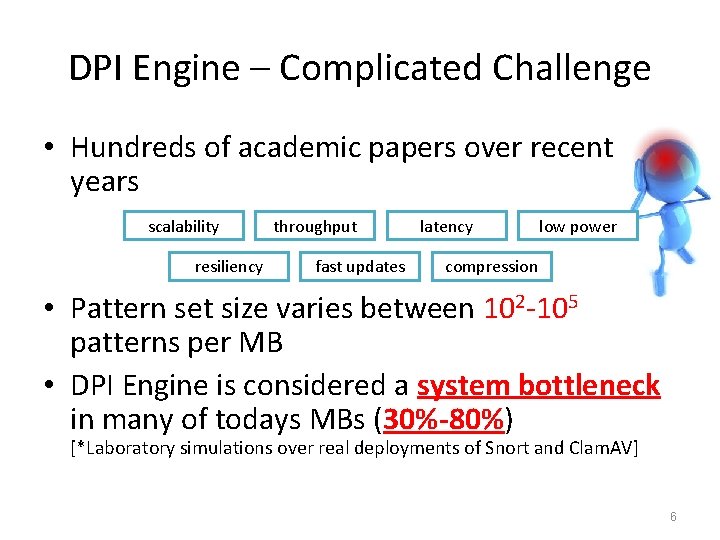
DPI Engine – Complicated Challenge • Hundreds of academic papers over recent years scalability resiliency throughput fast updates latency low power compression • Pattern set size varies between 102 -105 patterns per MB • DPI Engine is considered a system bottleneck in many of todays MBs (30%-80%) [*Laboratory simulations over real deployments of Snort and Clam. AV] 6

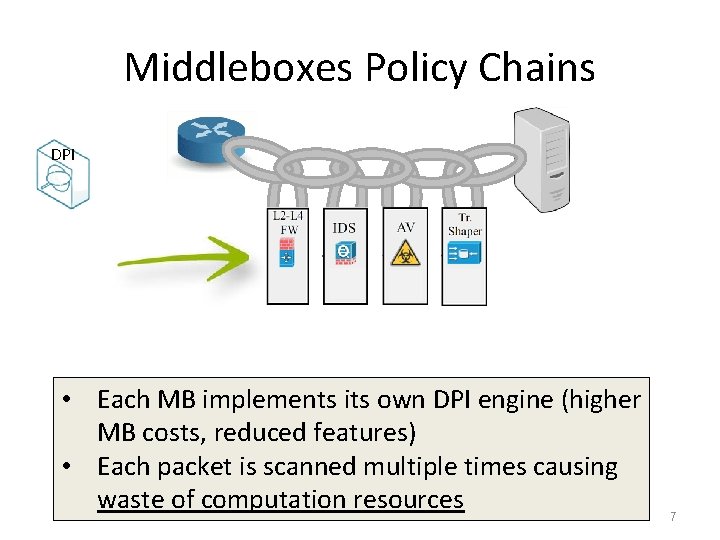
Middleboxes Policy Chains DPI • Each MB implements its own DPI engine (higher MB costs, reduced features) • Each packet is scanned multiple times causing waste of computation resources 7

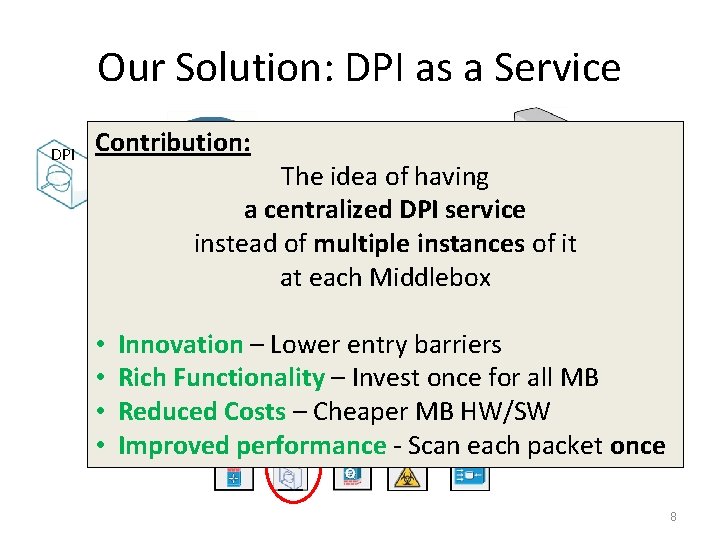
Our Solution: DPI as a Service DPI Contribution: The idea of having a centralized DPI service instead of multiple instances of it at each Middlebox • • Innovation – Lower entry barriers Rich Functionality – Invest once for all MB Reduced Costs – Cheaper MB HW/SW Improved performance - Scan each packet once 8

ARCHITECTURE 9

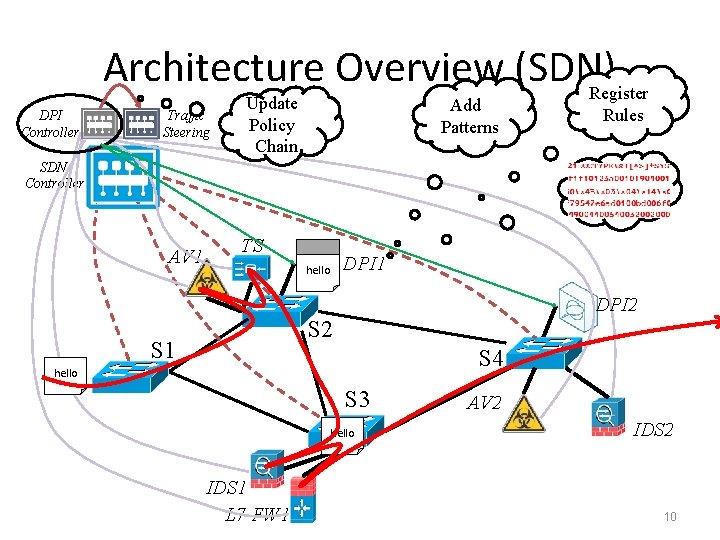
Architecture Overview (SDN) Register DPI Controller Traffic Steering Update Policy Chain Add Patterns Rules SDN Controller AV 1 TS DPI 1 hello DPI 2 S 1 S 4 hello S 3 hello IDS 1 L 7 FW 1 AV 2 IDS 2 10

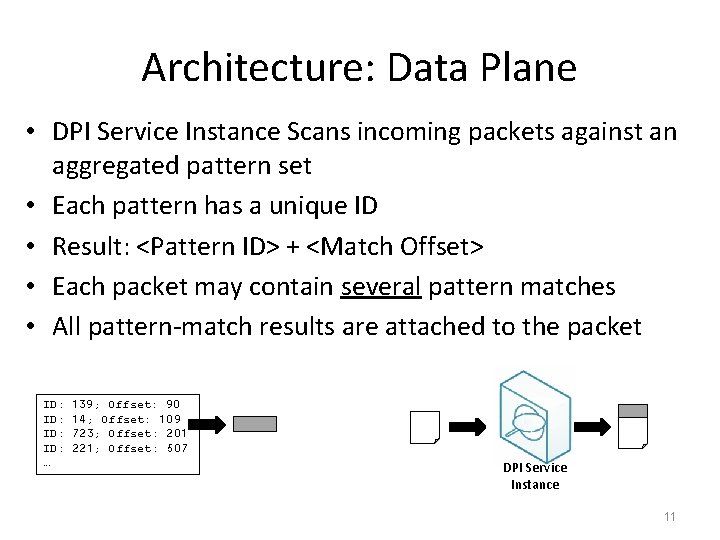
Architecture: Data Plane • DPI Service Instance Scans incoming packets against an aggregated pattern set • Each pattern has a unique ID • Result: <Pattern ID> + <Match Offset> • Each packet may contain several pattern matches • All pattern-match results are attached to the packet ID: ID: … 139; Offset: 90 14; Offset: 109 723; Offset: 201 221; Offset: 507 DPI Service Instance 11

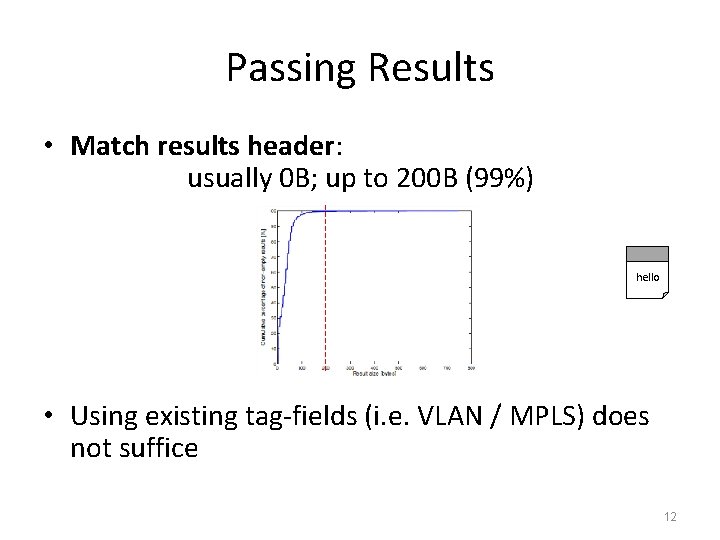
Passing Results • Match results header: usually 0 B; up to 200 B (99%) hello • Using existing tag-fields (i. e. VLAN / MPLS) does not suffice 12

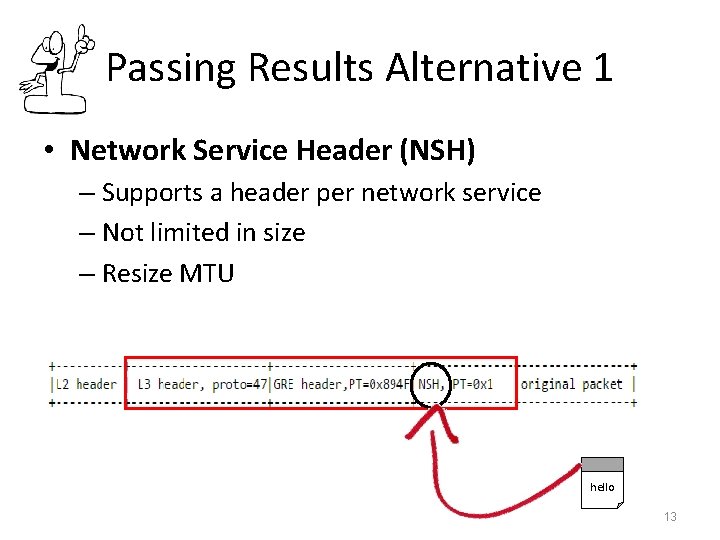
Passing Results Alternative 1 • Network Service Header (NSH) – Supports a header per network service – Not limited in size – Resize MTU hello 13

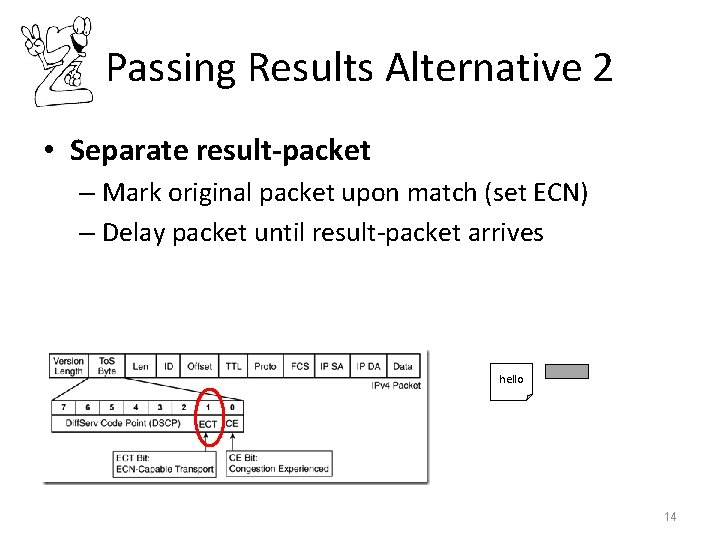
Passing Results Alternative 2 • Separate result-packet – Mark original packet upon match (set ECN) – Delay packet until result-packet arrives hello 14

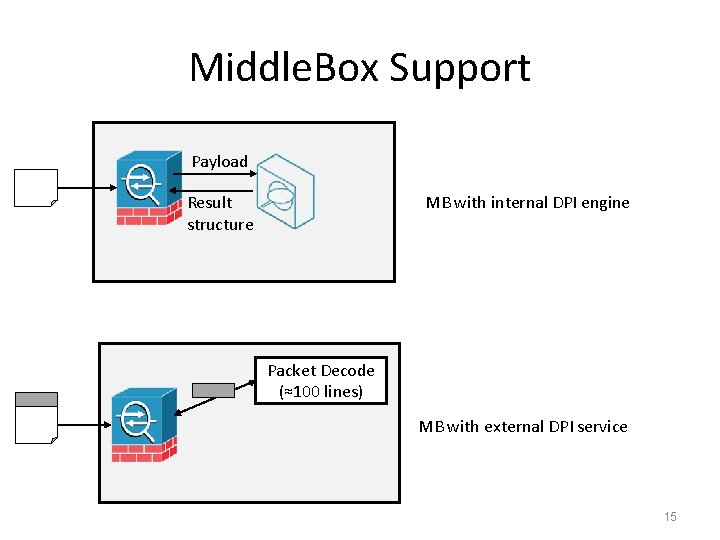
Middle. Box Support Payload MB with internal DPI engine Result structure Packet Decode (≈100 lines) MB with external DPI service 15

QUESTION: ARE THE DPI ALGORITHMS SCALABLE? 16

Are DPI Algorithms Scalable? • Short Answer: YES! • What are the DPI Algorithms? String Matching 886 f 1 f 10123 a 001019040010 e 5 f 79547 e 6 ad 0100 bd 006 f 00640075006300740049004400540032002000520053 00330041005300789 c Regex Matching <x 21 DOCTYPEs+[^>]*SYSTEM[^>]*>. *x 2 Eparse. Error 17

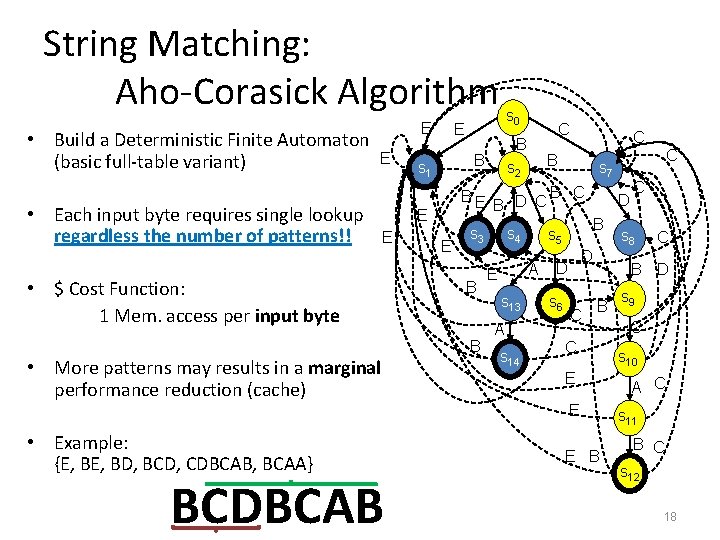
String Matching: Aho-Corasick Algorithm • Build a Deterministic Finite Automaton (basic full-table variant) E E • Each input byte requires single lookup regardless the number of patterns!! BE • $ Cost Function: 1 Mem. access per input byte E B • More patterns may results in a marginal performance reduction (cache) B D C s 4 s 13 A s 14 B C D B D D s 6 C BCDBCAB C s 8 C B D B C E E • Example: {E, BD, BCD, CDBCAB, BCAA} C s 7 s 5 A E C B s 2 s 3 B C B B s 1 E E s 0 E E B s 9 C s 10 A C s 11 B C s 12 18

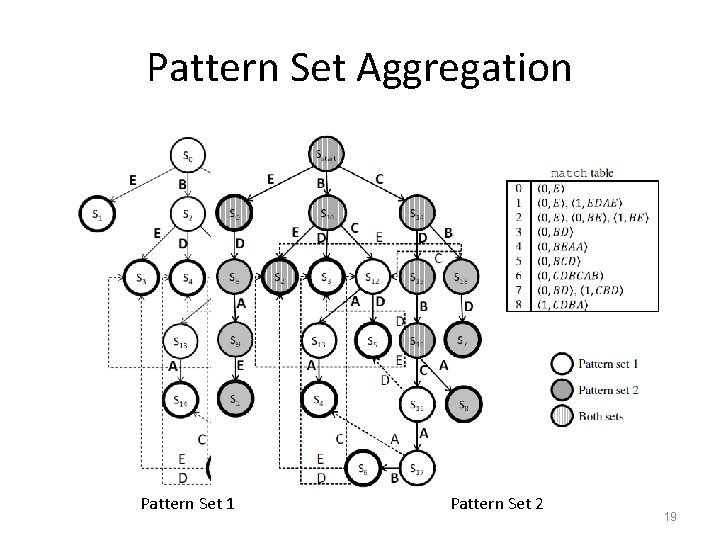
Pattern Set Aggregation Pattern set 1 Pattern set 2 Pattern Set 1 Pattern Set 2 Both sets 19

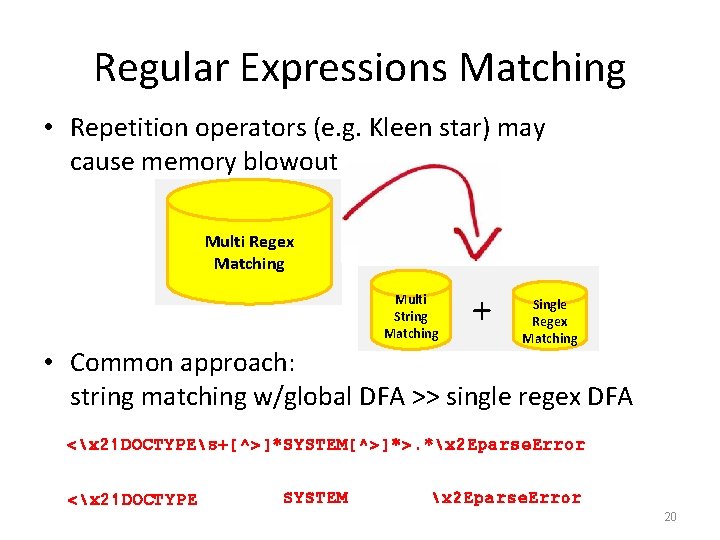
Regular Expressions Matching • Repetition operators (e. g. Kleen star) may cause memory blowout Multi Regex Matching Multi String Matching + Single Regex Matching • Common approach: string matching w/global DFA >> single regex DFA <x 21 DOCTYPEs+[^>]*SYSTEM[^>]*>. *x 2 Eparse. Error <x 21 DOCTYPE SYSTEM x 2 Eparse. Error 20

DPI is Scalable, not Trivial… Encode DFA in TCAM Compact. DFA, To. N 2014 ACCH, To. N 2012 Resilient Multi-Core DPI over Compressed Traffic MCA 2, ANCS 2012 21

DPI AS A SERVICE & DIFFERENT MIDDLEBOXES LAYOUTS 22

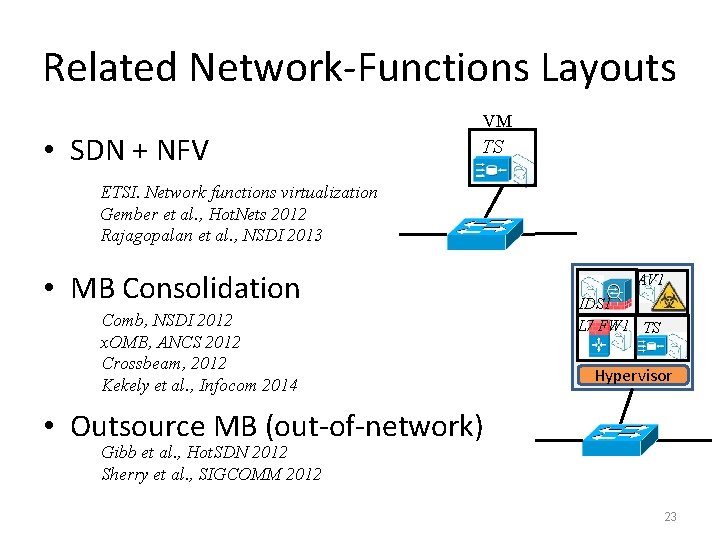
Related Network-Functions Layouts • SDN + NFV VM TS ETSI. Network functions virtualization Gember et al. , Hot. Nets 2012 Rajagopalan et al. , NSDI 2013 • MB Consolidation Comb, NSDI 2012 x. OMB, ANCS 2012 Crossbeam, 2012 Kekely et al. , Infocom 2014 AV 1 IDS 1 L 7 FW 1 TS Hypervisor • Outsource MB (out-of-network) Gibb et al. , Hot. SDN 2012 Sherry et al. , SIGCOMM 2012 23

EXPERIMENTAL RESULTS 24

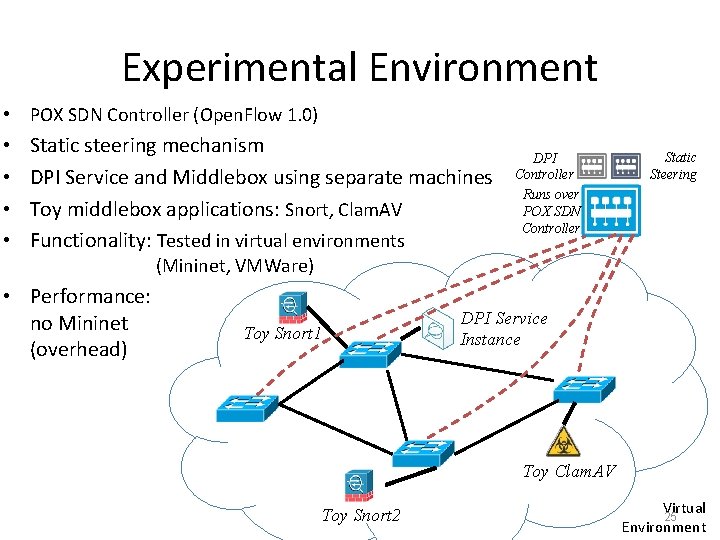
Experimental Environment • POX SDN Controller (Open. Flow 1. 0) • • Static steering mechanism DPI Service and Middlebox using separate machines Toy middlebox applications: Snort, Clam. AV Functionality: Tested in virtual environments DPI Controller Runs over POX SDN Controller Static Steering (Mininet, VMWare) • Performance: no Mininet (overhead) Toy Snort 1 DPI Service Instance Toy Clam. AV Toy Snort 2 Virtual 25 Environment

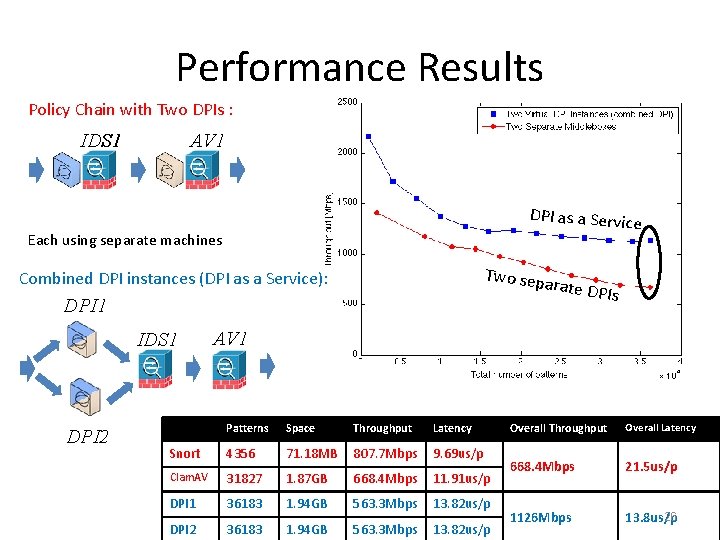
Performance Results Policy Chain with Two DPIs : IDS 1 AV 1 DPI as a Service Each using separate machines Two sep Combined DPI instances (DPI as a Service): arate DP Is DPI 1 IDS 1 DPI 2 AV 1 Patterns Space Throughput Latency Snort 4356 71. 18 MB 807. 7 Mbps 9. 69 us/p Clam. AV 31827 1. 87 GB 668. 4 Mbps 11. 91 us/p DPI 1 36183 1. 94 GB 563. 3 Mbps 13. 82 us/p DPI 2 36183 1. 94 GB 563. 3 Mbps 13. 82 us/p Overall Throughput Overall Latency 668. 4 Mbps 21. 5 us/p 1126 Mbps 26 13. 8 us/p

Future Work • Potential tasks to be “outsourced” as a service: – Payload Processing (Decryption/Decompression) • Retrieve raw data – Session reconstruction (Connection Tracking) • For session processing rather than packet processing – Header/protocol analysis • For protocol aware network functions • Use the DPI to extend Open. Flow based switches – Use the tags created by the DPI service to drive policies in conventional switches. 28

Conclusions • DPI is a common service used by today’s MB • Thanks to its scalability it may be easily exported as a stand-alone network service • DPI as a Service provides: – Innovation (Lower entry barriers) – Network scalability – Lower costs (Cheaper MB Hardware) 29

Thank You!!
 Applesauce with raspberry puree mre
Applesauce with raspberry puree mre Deep packet inspection definition
Deep packet inspection definition Deep packet inspection architecture
Deep packet inspection architecture Deep packet inspection encrypted traffic
Deep packet inspection encrypted traffic Deep packet inspection wireshark
Deep packet inspection wireshark Deep packet inspection architecture
Deep packet inspection architecture Graves hastalığı
Graves hastalığı Kanp koral
Kanp koral Yaron shohat
Yaron shohat Yaron ernst
Yaron ernst Stateless packet filtering definition
Stateless packet filtering definition Deep packet injection
Deep packet injection Deep pocket inspection
Deep pocket inspection Deep asleep deep asleep it lies
Deep asleep deep asleep it lies Deep forest towards an alternative to deep neural networks
Deep forest towards an alternative to deep neural networks 深哉深哉
深哉深哉 Food safety and inspection service definition
Food safety and inspection service definition In service inspection
In service inspection Itil service transition definition
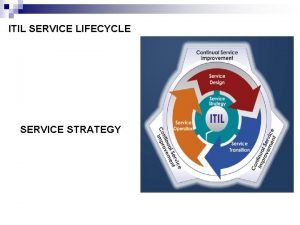
Itil service transition definition Itil lifecycle phases
Itil lifecycle phases Continual service improvement 7 steps
Continual service improvement 7 steps Factors that influence desired service
Factors that influence desired service Evolution of soa
Evolution of soa Mpls class of service
Mpls class of service New service development process cycle
New service development process cycle Service owner vs service manager
Service owner vs service manager Help desk improvement plan
Help desk improvement plan Adp self pay
Adp self pay The label side of the dental film packet
The label side of the dental film packet Reed yorke umd
Reed yorke umd