Decrypting Tokenization What is it and why is






- Slides: 14

Decrypting Tokenization What is it and why is it important? Anne Fields, Crutchfield, Director Financial Compliance Nate Morgan, Cyber. Source, Product Manager Ian Poole, Cardinal. Commerce, Technical Product Manager

Tokenization 1. What is it & Types of Tokens 2. Merchant Perspective 3. Merchant Considerations 4. Q & A 2

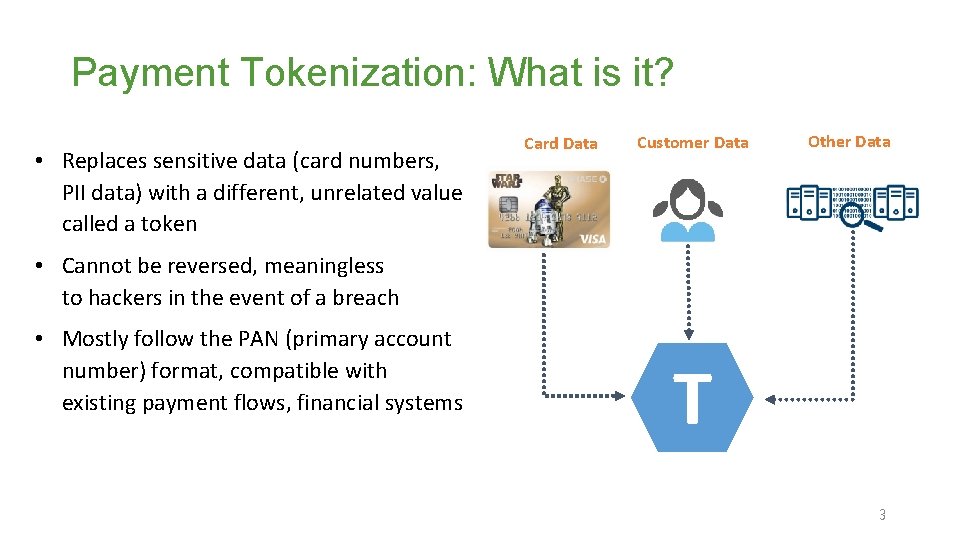
Payment Tokenization: What is it? • Replaces sensitive data (card numbers, PII data) with a different, unrelated value called a token Card Data Customer Data Other Data • Cannot be reversed, meaningless to hackers in the event of a breach • Mostly follow the PAN (primary account number) format, compatible with existing payment flows, financial systems T 3

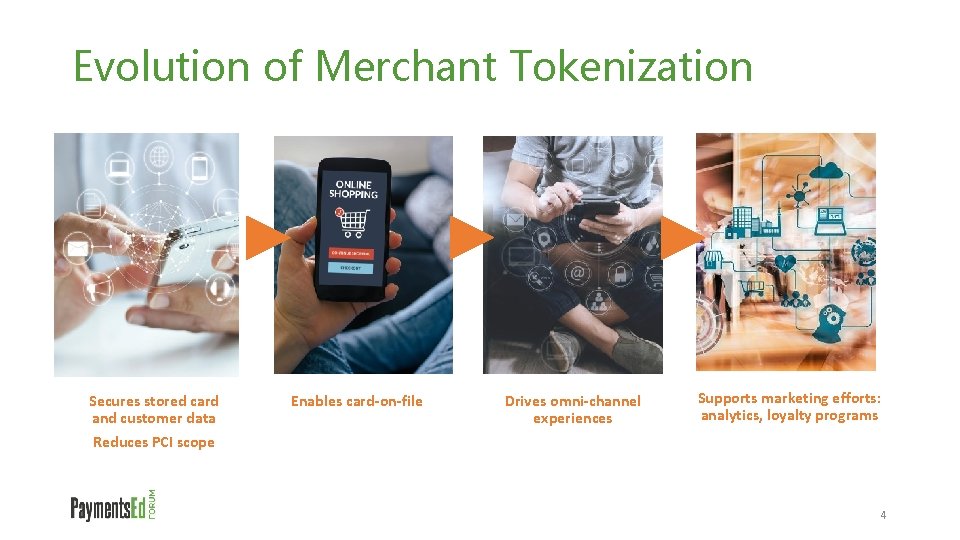
Evolution of Merchant Tokenization Secures stored card and customer data Enables card-on-file Drives omni-channel experiences Supports marketing efforts: analytics, loyalty programs Reduces PCI scope 4

Merchant Payment Tokens Your customer data is better protected in the event of a breach Seamless, friction-less payment experience • Renders sensitive card (and other) data worthless • Essential for bill payers / returning customers • Card data securely stored in your vault • Enables new, “Uber-like” experiences • PCI scope is reduced; no payment data in your network when using a PSP • Card updater service highly recommended • Tokens, not card numbers used for payment activities 5

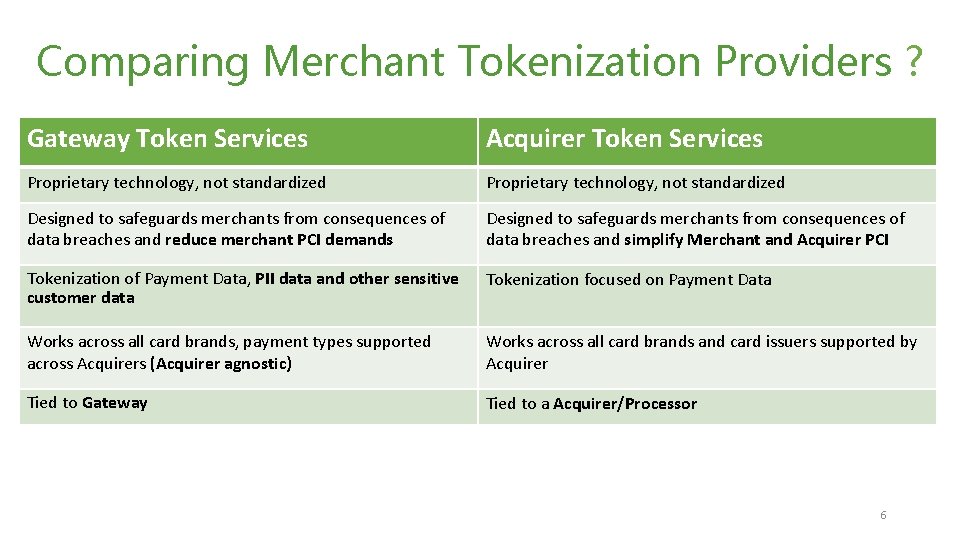
Comparing Merchant Tokenization Providers ? Gateway Token Services Acquirer Token Services Works across all card brands, payment types supported across Acquirers (Acquirer agnostic) Acquirer • Protection of stored card data Proprietary technology, not standardized • Reduced PCI scope • Processor Agnostic Designed to safeguards merchants from consequences of Support digital payment data • breaches andfor reduce merchant PCIsolutions demands like Apple Pay, Android Pay, etc. via network Tokenization of Payment Data, PII data and other sensitive tokens customer data • Tokenization of PII data (some providers cater to healthcare industries) Tied to Gateway • Proprietary, tied to the acquirer issuing the tokenmerchant switch acquirers, Proprietary technology, notcannot standardized integrate to/inter-operate with tokens from Designed to safeguards merchants from consequences of other acquirers data breaches and simplify Merchant and Acquirer PCI • Able to support POS and e. Commerce transactions (omni functionality) Tokenization focused on Payment Data • Other features similar to PSP tokens • Protection of stored payment data Works across all card brands and card issuers supported by • Reduced PCI scope Tied to a Acquirer/Processor 6

Evolution of Issuer Tokenization VTS MDES EMVCo standards; launch of VTS and MDES Enables digital payments such as Apple Pay, Android Pay Powers connected commerce, Io. T and other new payment experiences Future applications *EMVCo members include American Express, Discover, JCB, Master. Card, Union. Pay and Visa Note: All brand names and logos are the property of their respective owners, are used for identification purposes only, and do not imply product endorsement or affiliation with Visa

Issuer-Side (Network) Payment Tokens • Card brands * collaborated as EMVCo, developed standards for worldwide interoperability & security • Apple Pay was the first use case, now also Android Pay, Samsung Pay, etc. • Visa, Mastercard, Amex built solutions using token standards in the EMVCo framework and are the “TSP” of digital payment tokens • Issuers control activation, suspension, deactivation of tokens for cardholder • Tokens are unique to device, channel, and stored for future payments • May be single or multi-use, merchant specific or have time limitations 8

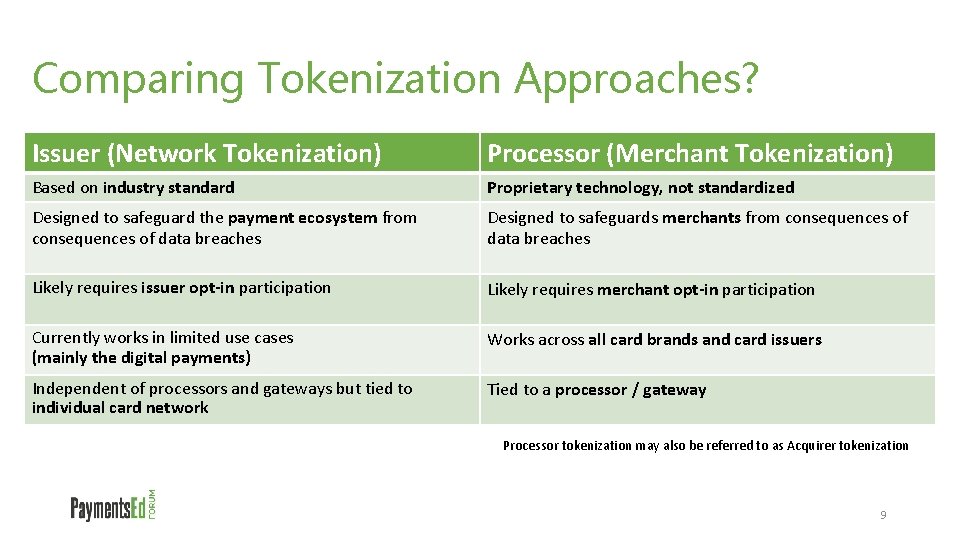
Comparing Tokenization Approaches? Issuer (Network Tokenization) Processor (Merchant Tokenization) Based on industry standard Proprietary technology, not standardized Designed to safeguard the payment ecosystem from consequences of data breaches Designed to safeguards merchants from consequences of data breaches Likely requires issuer opt-in participation Likely requires merchant opt-in participation Currently works in limited use cases (mainly the digital payments) Works across all card brands and card issuers Independent of processors and gateways but tied to individual card network Tied to a processor / gateway Processor tokenization may also be referred to as Acquirer tokenization 9

Tokenization & Connected Commerce • Allows commerce to be embedded in everything • Device manufacturers, large businesses are becoming token requestors • Gearing to enable secure, device-driven on-demand transactions on a massive scale • e. Comm wallet, Io. T wallet, Issuer wallet, Wearable wallets, POS – tap and pay 10

Merchant Perspective • Why did we consider Tokenization? • How do we Tokenize? • What did we want to accomplish with Tokenization? 11

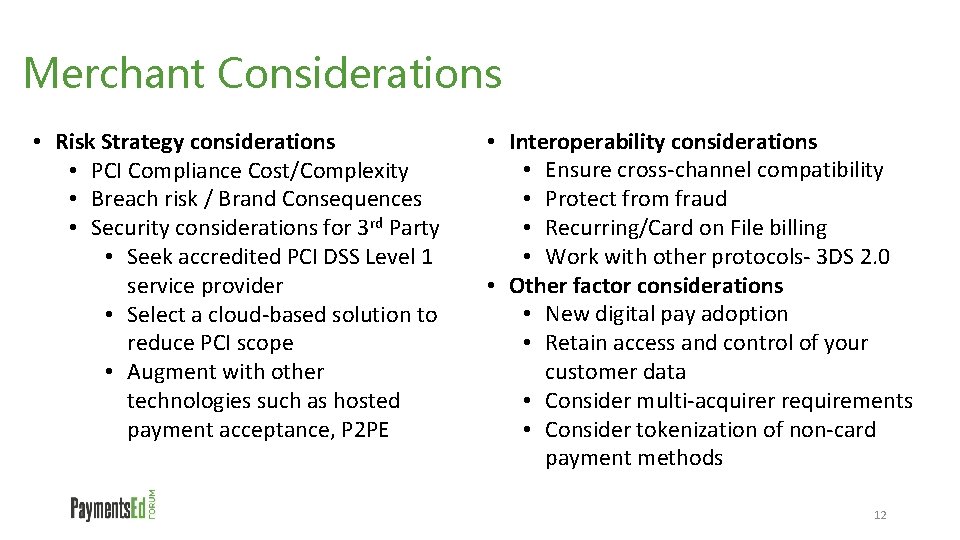
Merchant Considerations • Risk Strategy considerations • PCI Compliance Cost/Complexity • Breach risk / Brand Consequences • Security considerations for 3 rd Party • Seek accredited PCI DSS Level 1 service provider • Select a cloud-based solution to reduce PCI scope • Augment with other technologies such as hosted payment acceptance, P 2 PE • Interoperability considerations • Ensure cross-channel compatibility • Protect from fraud • Recurring/Card on File billing • Work with other protocols- 3 DS 2. 0 • Other factor considerations • New digital pay adoption • Retain access and control of your customer data • Consider multi-acquirer requirements • Consider tokenization of non-card payment methods 12

Questions from the audience 13

Tokenization Panel • Anne Fields, Crutchfield, Director Financial Compliance • afields@crutchfield. com • Nate Morgan, Cyber. Source, Product Manager • nmorgan@visa. com • Ian Poole, Cardinal. Commerce, Technical Product Manager • ipoole@cardinalcommerce. com If you have any questions about the presentation, go to our Linked. In Group (the Payments Education Forum) and request an invitation (this is a closed group specifically for the payments industry). 14