Decode data privacy GDPR Program RIMS DELVAL Presentation
























- Slides: 44

Decode data privacy. GDPR Program RIMS DEL/VAL Presentation February 12, 2019 willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved.

GDPR Table of Contents § § § G D P GDPR Overview…………………. . Page 4 - 7 The Players……………………. . Page 9 -15 Compliance Adequacy Mechanisms……………. . Page 17 - 21 Sanctions Fines and Penalties…………. . Page 23 – 24 Cyber Insurance Considerations…………………. . . Page 26 GDPR, so far……………………Page 28 By: Gamelah Palagonia, FIP, CIPM, CIPT, CIPP/E, CIPP/US, CIPP/G, ARM, RPLU+ Senior Vice President

GDPR Overview willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 3

The General Data Protection Regulation (GDPR) GDPR is the most dramatic change in data privacy regulation in the past 20 years. GDPR went into force on May 25, 2018 replacing the Data Protection Directive 95/46/ EC. GDPR was designed to harmonize data privacy laws across Europe, protecting and empowering all individuals in the EU. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 4

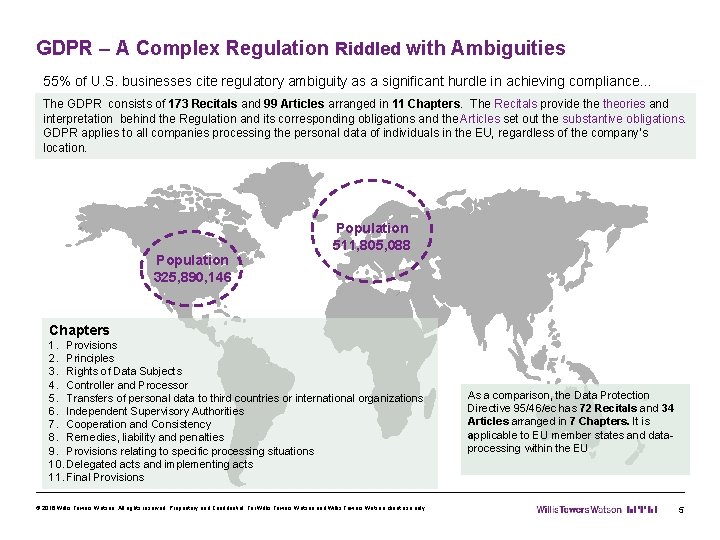
GDPR – A Complex Regulation Riddled with Ambiguities 55% of U. S. businesses cite regulatory ambiguity as a significant hurdle in achieving compliance… The GDPR consists of 173 Recitals and 99 Articles arranged in 11 Chapters. The Recitals provide theories and interpretation behind the Regulation and its corresponding obligations and the Articles set out the substantive obligations. GDPR applies to all companies processing the personal data of individuals in the EU, regardless of the company’s location. Population 325, 890, 146 Population 511, 805, 088 Chapters 1. Provisions 2. Principles 3. Rights of Data Subjects 4. Controller and Processor 5. Transfers of personal data to third countries or international organizations 6. Independent Supervisory Authorities 7. Cooperation and Consistency 8. Remedies, liability and penalties 9. Provisions relating to specific processing situations 10. Delegated acts and implementing acts 11. Final Provisions © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. As a comparison, the Data Protection Directive 95/46/ec has 72 Recitals and 34 Articles arranged in 7 Chapters. It is applicable to EU member states and dataprocessing within the EU 5

What firms are subject to GDPR? “GDPR applies to all businesses that processes personal data relating to either the offering of goods/services to individuals or “data subjects” in the EU or to the monitoring of their behavior in the EU. ” © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 6

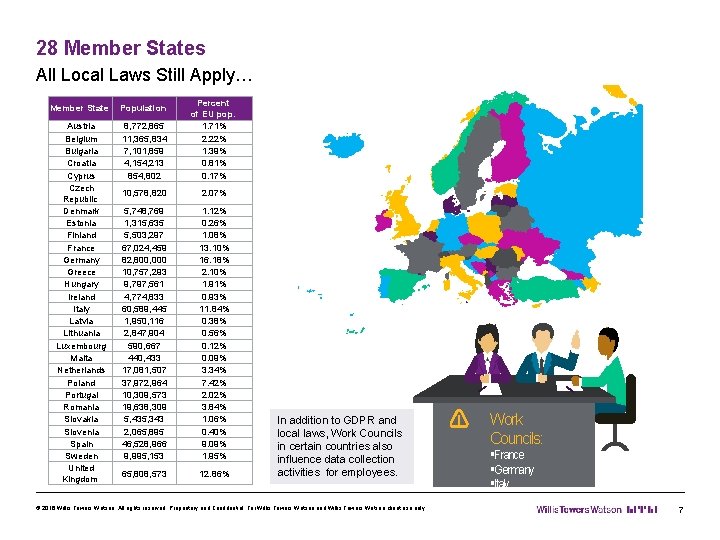
28 Member States All Local Laws Still Apply… Member State Population Austria Belgium Bulgaria Croatia Cyprus Czech Republic Denmark Estonia Finland France Germany Greece Hungary Ireland Italy Latvia Lithuania Luxembourg Malta Netherlands Poland Portugal Romania Slovakia Slovenia Spain Sweden United Kingdom 8, 772, 865 11, 365, 834 7, 101, 859 4, 154, 213 854, 802 Percent of EU pop. 1. 71% 2. 22% 1. 39% 0. 81% 0. 17% 10, 578, 820 2. 07% 5, 748, 769 1, 315, 635 5, 503, 297 67, 024, 459 82, 800, 000 10, 757, 293 9, 797, 561 4, 774, 833 60, 589, 445 1, 950, 116 2, 847, 904 590, 667 440, 433 17, 081, 507 37, 972, 964 10, 309, 573 19, 638, 309 5, 435, 343 2, 065, 895 46, 528, 966 9, 995, 153 1. 12% 0. 26% 1. 08% 13. 10% 16. 18% 2. 10% 1. 91% 0. 93% 11. 84% 0. 38% 0. 56% 0. 12% 0. 09% 3. 34% 7. 42% 2. 02% 3. 84% 1. 06% 0. 40% 9. 09% 1. 95% 65, 808, 573 12. 86% In addition to GDPR and local laws, Work Councils in certain countries also influence data collection activities for employees. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. Work Councils: §France §Germany §Italy 7

The Players Data Subjects/Personal Data, Controllers, Processors, DPA’s and DPO’s willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 8

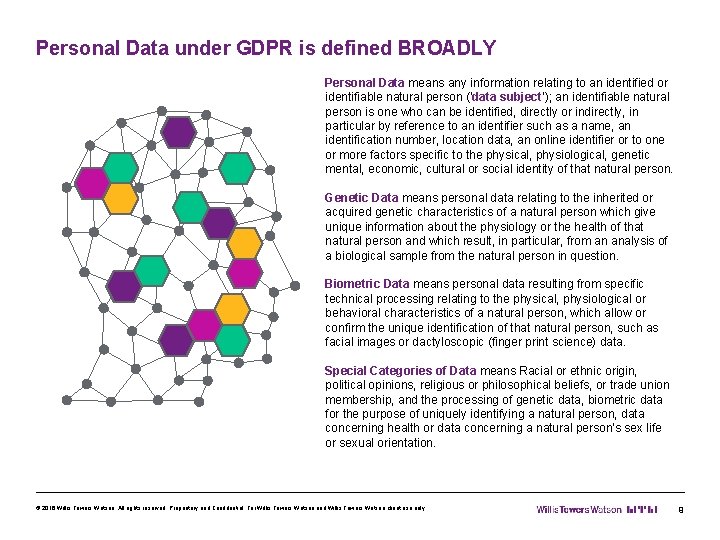
Personal Data under GDPR is defined BROADLY Personal Data means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic mental, economic, cultural or social identity of that natural person. Genetic Data means personal data relating to the inherited or acquired genetic characteristics of a natural person which give unique information about the physiology or the health of that natural person and which result, in particular, from an analysis of a biological sample from the natural person in question. Biometric Data means personal data resulting from specific technical processing relating to the physical, physiological or behavioral characteristics of a natural person, which allow or confirm the unique identification of that natural person, such as facial images or dactyloscopic (finger print science) data. Special Categories of Data means Racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 9

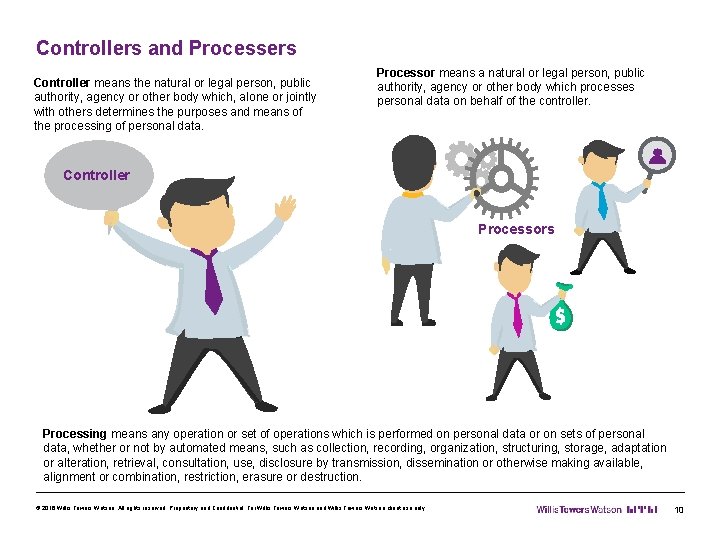
Controllers and Processers Controller means the natural or legal person, public authority, agency or other body which, alone or jointly with others determines the purposes and means of the processing of personal data. Processor means a natural or legal person, public authority, agency or other body which processes personal data on behalf of the controller. Controller Processors Processing means any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 10

Controllers and Processors Accountability = Demonstrable Compliance § Implementation of data protection policies and measures to ensure data processing activities are in compliance § Data Protection by design and by default § Record-keeping obligations by controllers and processors § Cooperation with supervisory authorities by controllers and processors § Carrying out DPIA’s for operations that present specific risks to individuals due to the nature or scope of the operation § Prior consultation with DPA’s on high-risk cases § Mandatory Data Protection Officers for the public sector and big data processing activities 1. 2. 3. 4. 5. 6. GDPR Principles Lawfulness, Fairness and Transparency Purpose Limitation Data Minimization Accuracy Storage Limitation Integrity, Confidentiality Must demonstrate compliance with these principles https: //gdpr-info. eu/art-5 -gdpr/ © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 11

Data Protection Authorities (DPA’s) DPAs are independent public authorities that supervise, through investigative and corrective powers, the application of the data protection law. They provide expert advice on data protection issues and handle complaints lodged against violations of the GDPR and the relevant national laws. There are 28 DPA’s – one for each EU Member State. DPA’s “Got the Power” § Investigatory Powers: These powers are quite comprehensive and leave controllers and processors nowhere to hide bad practices § Corrective Powers: Warn controllers and processors about dubious data processing activities, levy fines and/ or stop business activities § Authorization and Advisory Powers: The advisory powers map to the DPA duties in the areas of codes of conduct, certifications, marks, seals and international transfers of personal data Note: The FTC is the U. S. “DPA” equivalent http: //ec. europa. eu/newsroom/article 29/document. cfm? action=display&doc_id=50061 https: //ec. europa. eu/info/law-topic/data-protection/reform/what-are-data-protection-authorities-dpas_en https: //ec. europa. eu/commission/priorities/justice-and-fundamental-rights/data-protection/2018 -reform-eu-data-protection-rules_en © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 12

Accountability Mandatory DPO The DPO appointment is mandatory only: § The processing is carried out by a public authority or body, except for courts acting in their judicial capacity. § For those controllers and processors whose core activities consist of processing operations which require regular and systematic monitoring of data subjects on a large scale. DPO § The core activities of the controller or the processor consists of processing on a large scale of special categories of data pursuant to Article 9 and personal data relating to criminal convictions and offences pursuant to Article 10. DPO’s must be able to operate independently and should not be penalized for performing their tasks properly. DPO Requirements - Must be appointed on the basis of professional qualities and must have expert knowledge on data protection law and practices - May be a staff member or an external service provider - Contact details must be provided to the relevant Data Protection Authorities - Must be provided with appropriate resources to carry out their tasks and maintain their expert knowledge - Must report directly to the highest level of management - Must not carry out any other tasks that could result in a conflict of interest 72 Hour Breach Notification Processor Awareness = Controller Awareness Risk Managers need to be made aware of the DPO’s role in reporting data breaches! © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 13

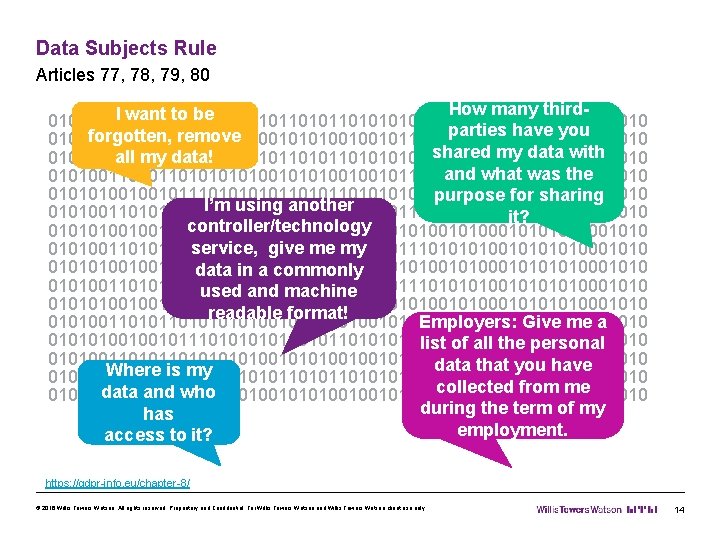
Data Subjects Rule Articles 77, 78, 79, 80 How many third. I want to be 010101001001011101011010101010001010001010 parties have you forgotten, remove 010100110101010100100101110101010001010 shared my data with all my data! 010101001001011101011010101010001010001010 and what was the 0101001101010101001001011101010100010101001001011101011010101010001010001010 purpose for sharing I’m using another 010100110101010100100101110101010001010 it? controller/technology 010101001001011101011010101010001010001010 service, give me my 0101001101010101001001011101010100010101001001011101011010101010001010001010 data in a commonly 010100110101010100100101110101010001010 used and machine 010101001001011101011010101010001010001010 readable format! Employers: Give me a 0101001101010101001001011101010100010101001001011101011010101010001010001010 list of all the personal 010100110101010100100101110101010001010 data that you have Where is my 010101001001011101011010101010001010001010 collected from me data and who 010100110101010100100101110101010001010 during the term of my has employment. access to it? https: //gdpr-info. eu/chapter-8/ © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 14

Data Subject Access Request Without undue delay, and in any event within one month of receipt of the request or provision by the requestor of additional information, or within one month of receipt of payment, if payment is required. If addressing the request is complex, or if many requests have been made at the same time, the period of time to respond may be extended by up to two additional months or 60 days. However, the Data Subject must be informed of such extension and the reasons for the delay in writing within one month of receipt of the request. https: //gdpr-info. eu/art-15 -gdpr/ © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 15

Compliance Adequacy Mechanisms How do businesses comply? What are the challenges? willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 16

Compliance Adequacy Mechanisms Standard Contractual Clauses or Model Clauses EU Controller to non-EU or EEA Controller EU Controller to non-EU or EEA Processor https: //ec. europa. eu/info/law-topic/data-protection/data-transfersoutside-eu/model-contracts-transfer-personal-data-third-countries_en Binding Corporate Rules (BCR’s) – U. S. Multinationals The most significant development in the area of international data transfers under GDPR is the inclusion of BCR’s as a mechanism available to Controllers and Processors to legitimize transfers within corporate groups. Contractual Liability Standard Contractual Liability Exclusion Any obligation an Insured has under written contract; provided, however, this exclusion shall not apply to liability an Insured would have in the absence of a contract. EU-U. S. Privacy Shield (replaces Safe Harbor) On October 6, 2015, the CJEU (Court of Justice of the European Union) issued its judgment declaring U. S. Safe Harbor invalid. On February 29, 2016, the new EU-U. S. Privacy Shield was born. The Privacy Shield Framework documentation is significantly more detailed than its predecessor, imposing more specific and exacting measures on organizations wishing to join the framework. Importantly, the Privacy Shield Framework also includes additional checks and balances designed to ensure that the privacy rights of EU individuals can be exercised when their data is being processed in the U. S. The Privacy Shield became effective August 1, 2016. U. S. businesses subject to the jurisdiction of the FTC or Department of Commerce (DOC) can join the Privacy Shield by filing an online registration at www. privacyshield. gov. Codes of Conduct and Certification Mechanisms One of the novelties of GDPR is the express addition of codes of conduct and certification mechanisms as adequacy mechanisms. Both these mechanisms are yet to be tested so it remains to be seen whether they provide a practical and effective solution to legitimize international data transfers. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. Preliminary 17

Major Challenges Forrester conducted a study revealing more than 80 percent of companies affected by GDPR would not be compliant by May 25, 2018. Of those companies, 50 percent will fail in their efforts to comply, while others will do so willingly, as the result of a cost-risk analysis. The major challenge for organizations is assessing its data collection processes against GDPR and ensuring continued compliance. Any organization subject to GDPR must carry out and regularly update gap analyses, data protection impact assessments, privacy audits and data breach roadmaps in order to stay on the right side of GDPR. Compliance Non-Compliance Industries at Higher Risk § Ad-Tech § Digital Marketing § Hospitality § Technology § Data Analytics § Social Media § Healthcare & Wellness Administrators § Criminal Background Service Providers § Processors of Special Categories of Data (DNA: Ancestory. com) © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 18

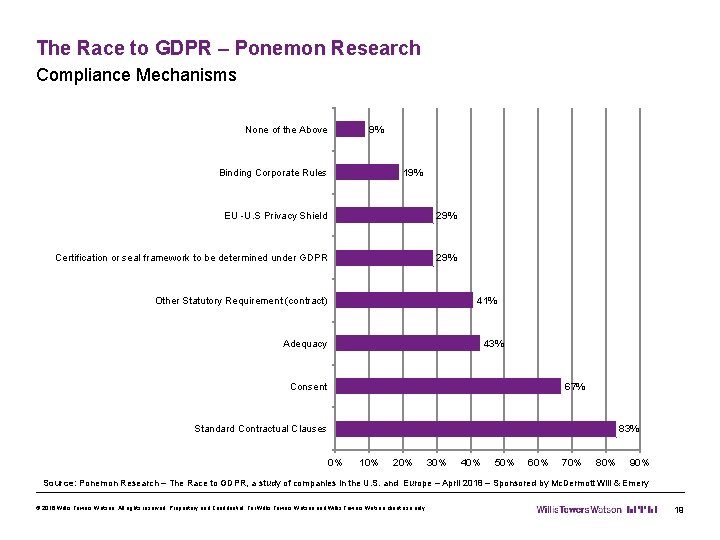
The Race to GDPR – Ponemon Research Compliance Mechanisms None of the Above 9% 19% Binding Corporate Rules EU -U. S Privacy Shield 29% Certification or seal framework to be determined under GDPR 29% Other Statutory Requirement (contract) 41% Adequacy 43% Consent 67% Standard Contractual Clauses 83% 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% Source: Ponemon Research – The Race to GDPR, a study of companies in the U. S. and Europe – April 2018 – Sponsored by Mc. Dermott Will & Emery © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 19

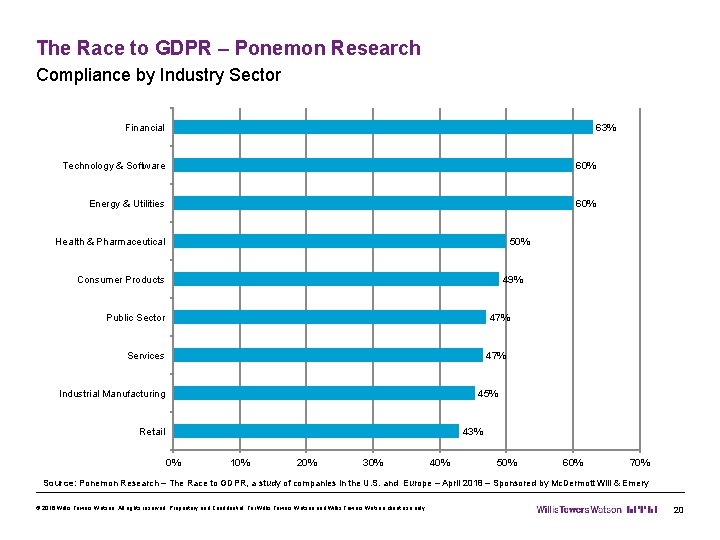
The Race to GDPR – Ponemon Research Compliance by Industry Sector Financial 63% Technology & Software 60% Energy & Utilities 60% Health & Pharmaceutical 50% Consumer Products 49% Public Sector 47% Services 47% Industrial Manufacturing 45% Retail 0% 43% 10% 20% 30% 40% 50% 60% 70% Source: Ponemon Research – The Race to GDPR, a study of companies in the U. S. and Europe – April 2018 – Sponsored by Mc. Dermott Will & Emery © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 20

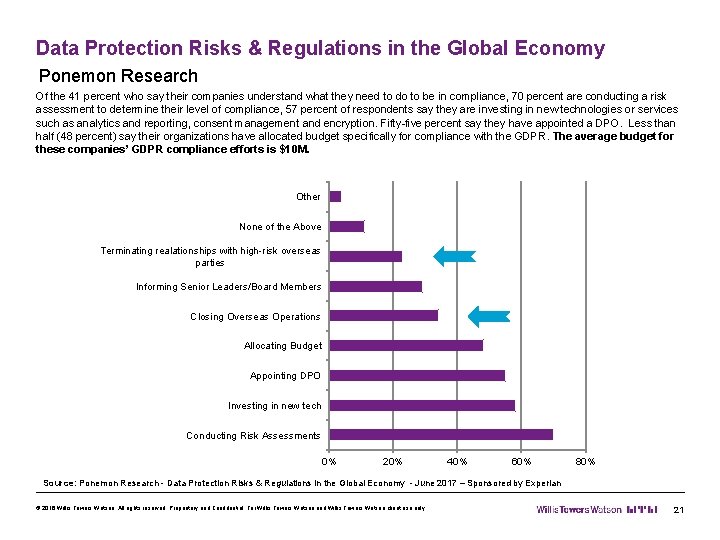
Data Protection Risks & Regulations in the Global Economy Ponemon Research Of the 41 percent who say their companies understand what they need to do to be in compliance, 70 percent are conducting a risk assessment to determine their level of compliance, 57 percent of respondents say they are investing in new technologies or services such as analytics and reporting, consent management and encryption. Fifty-five percent say they have appointed a DPO. Less than half (48 percent) say their organizations have allocated budget specifically for compliance with the GDPR. The average budget for these companies’ GDPR compliance efforts is $10 M. Other None of the Above Terminating realationships with high-risk overseas parties Informing Senior Leaders/Board Members Closing Overseas Operations Allocating Budget Appointing DPO Investing in new tech Conducting Risk Assessments 0% 20% 40% 60% 80% Source: Ponemon Research - Data Protection Risks & Regulations in the Global Economy - June 2017 – Sponsored by Experian © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 21

Sanctions, Fines and Penalties Articles 83 willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 22

Sanctions & Penalties “Effective, Proportionate, Dissuasive” Depending on the nature of contravention and the status of the entity being pursued, fines may be imposed up to a set financial cap (up to $10 M euros, in some cases, or $20 M in others), or up to a percentage of worldwide revenues (2% or 4%). Article 83 (4) Article 83 (5) Cover issues such as children consent, data protection by design and by default, engagement of processors by controllers, records of processing, cooperation with regulators, security breach notification, DPIAs, DPOs, codes of conduct and certification. Covers issues such as the data protection principles, lawfulness of processing, consent, processing of special category data, the data subjects rights, international transfer, failure to comply with the DPA’s investigatory and corrective powers. § Fines up to $10 M euro for non-undertakings (not engaged in economic activity, e. g. , public authorities) § Fines up to $20 M euros for non-undertakings § Fines up to the higher of $10 M euro or 2 percent of total worldwide revenues in preceding year for undertakings § Fines up to the higher of $20 M euros or 4 percent of total worldwide annual revenues in preceding year for undertakings Supervisory authority should have the power to impose administrative fines. Member States shall lay down the rules on other penalties applicable to infringements of this Regulation in particular for infringements which are not subject to administrative fines pursuant to Article 83, and shall take all measures necessary to ensure that they are implemented. Such penalties shall be effective, proportionate and dissuasive. https: //gdpr-info. eu/art-83 -gdpr/ © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 23

Avoiding Fines and Penalties Resistance is Futile – Assimilation is Inevitable Compliance is the key to avoiding liabilities and resulting fines and other penalties © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 24

Cyber Insurance Considerations willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 25

Cyber Insurance Considerations § § GDPR Endorsement Definition of Personal Data Important Coverage Triggers Insurability of Fines/Penalties https: //gdpr-info. eu/art-83 -gdpr/ © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 26

GDPR, so far willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 27

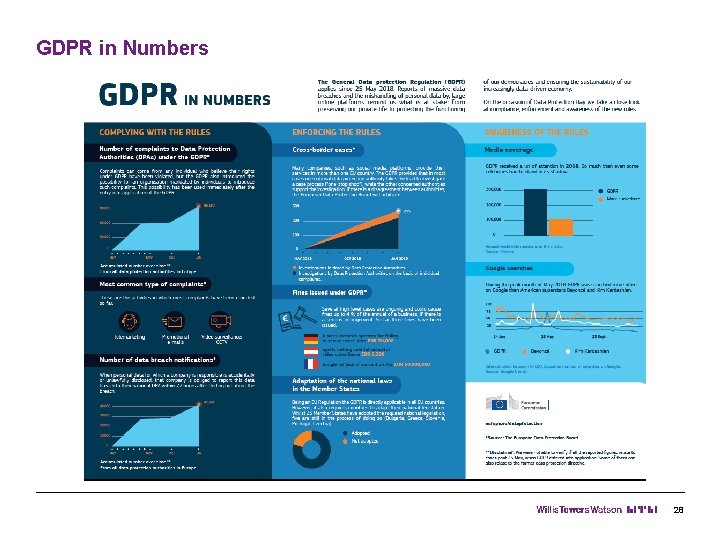
GDPR in Numbers 28

Resources Key Definitions, Key GDPR Articles, Additional Resources willistowerswatson. com © 2017 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 29

Key Definitions § Controller means the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data; where the purposes and means of such processing are determined by Union or Member State law, the controller or the specific criteria for its nomination may be provided for by Union or Member State law. § Processor means a natural or legal person, public authority, agency or other body which processes personal data on behalf of the controller. § Third party means a natural or legal person, public authority, agency or body other than the data subject, controller, processor and persons who, under the direct authority of the controller or processor, are authorized to process personal data. § Processing means any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction. § Restriction of Processing means the marking of stored personal data with the aim of limiting their processing in the future. § Consent of the data subject means any freely given, specific, informed and unambiguous indication of the data subject’s wishes by which he or she, by a statement or by a clear affirmative action, signifies agreement to the processing of personal data relating to him or her. § Personal Data Breach means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed. § Profiling means any form of automated processing of personal data consisting of the use of personal data to evaluate certain personal aspects relating to a natural person, in particular to analyze or predict aspects concerning that natural person’s performance at work, economic situation, health, personal preferences, interests, reliability, behavior, location or movements. § Pseudonymization means the processing of personal data in such a manner that the personal data can no longer be attributed to a specific data subject without the use of additional information, provided that such additional information is kept separately and is subject to technical and organizational measures to ensure that the personal data are not attributed to an identified or identifiable natural person. § Filing System means any structured set of personal data which are accessible according to specific criteria, whether centralized, decentralized or dispersed on a functional or geographical basis. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 30

Meaning of Undertaking Recital 150 of the GDPR states that where administrative fines are imposed on an undertaking, an ‘undertaking’ should be understood in accordance with Articles 101 and 102 - Treaty on the Functioning of the European Union (TFEU). http: //ec. europa. eu/competition/antitrust/legislation/articles. html The meaning of undertaking in the relation to Articles 101 and 102 of TFEU has frequently been examined in case law, which has concluded that where one company exercises “control” over another company, they form a single economic entity and, hence, are part of the same undertaking or company. Control has been defined in case law as “the ability to exercise decisive influence” over another entity, with the result that the latter does not enjoy real autonomy in determining its commercial policy on the market. This includes where a parent has a majority shareholding in a subsidiary – the parent is in the position to exercise control over that subsidiary and so there is a rebuttable presumption (with the burden of proof resting on the parent company) that the parent does exercise such control. Where the parent is a minority shareholder, there is no presumption of control, and a range of factors will be taken into account to assess whether they have control, including: the size of the parent’s shareholding; representation on the board of directors of the subsidiary; the ability to influence the commercial policy of the subsidiary; and evidence of efforts to do so. What does this mean for multinational companies that process personal data? The term ‘undertaking’ is construed very broadly. With the risk of ‘getting it wrong’ substantially higher under the GDPR, the wise approach would be to assume that group revenues could be used by supervisory authorities when calculating administrative fines. However, case law has demonstrated that what amounts to an ‘undertaking’ will turn on the facts of each case. Source: https: //www. dlapiperdataprotection. com/index. html © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 31

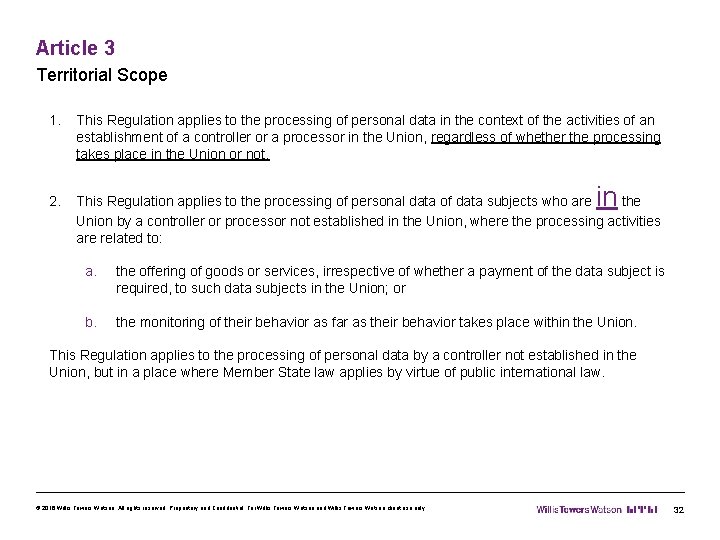
Article 3 Territorial Scope 1. This Regulation applies to the processing of personal data in the context of the activities of an establishment of a controller or a processor in the Union, regardless of whether the processing takes place in the Union or not. 2. This Regulation applies to the processing of personal data of data subjects who are the Union by a controller or processor not established in the Union, where the processing activities are related to: in a. the offering of goods or services, irrespective of whether a payment of the data subject is required, to such data subjects in the Union; or b. the monitoring of their behavior as far as their behavior takes place within the Union. This Regulation applies to the processing of personal data by a controller not established in the Union, but in a place where Member State law applies by virtue of public international law. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 32

Special Categories of Data (Article 9) Processing of personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation shall be prohibited unless: a. the data subject has given explicit consent to the processing of those personal data for one or more specified purposes, except where Union or Member State law provide that the prohibition referred to in paragraph 1 may not be lifted by the data subject; b. processing is necessary for the purposes of carrying out the obligations and exercising specific rights of the controller or of the data subject in the field of employment and social security and social protection law in so far as it is authorised by Union or Member State law or a collective agreement pursuant to Member State law providing for appropriate safeguards for the fundamental rights and the interests of the data subject; c. processing is necessary to protect the vital interests of the data subject or of another natural person where the data subject is physically or legally incapable of giving consent; d. processing is carried out in the course of its legitimate activities with appropriate safeguards by a foundation, association or any other not-forprofit body with a political, philosophical, religious or trade union aim and on condition that the processing relates solely to the members or to former members of the body or to persons who have regular contact with it in connection with its purposes and that the personal data are not disclosed outside that body without the consent of the data subjects; e. processing relates to personal data which are manifestly made public by the data subject; f. processing is necessary for the establishment, exercise or defence of legal claims or whenever courts are acting in their judicial capacity; g. processing is necessary for reasons of substantial public interest, on the basis of Union or Member State law which shall be proportionate to the aim pursued, respect the essence of the right to data protection and provide for suitable and specific measures to safeguard the fundamental rights and the interests of the data subject; h. processing is necessary for the purposes of preventive or occupational medicine, for the assessment of the working capacity of the employee, medical diagnosis, the provision of health or social care or treatment or the management of health or social care systems and services on the basis of Union or Member State law or pursuant to contract with a health professional and subject to the conditions and safeguards referred to in paragraph 3; i. processing is necessary for reasons of public interest in the area of public health, such as protecting against serious cross-border threats to health or ensuring high standards of quality and safety of health care and of medicinal products or medical devices, on the basis of Union or Member State law which provides for suitable and specific measures to safeguard the rights and freedoms of the data subject, in particular professional secrecy; j. processing is necessary for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes in accordance with Article 89(1) based on Union or Member State law which shall be proportionate to the aim pursued, respect the essence of the right to data protection and provide for suitable and specific measures to safeguard the fundamental rights and the interests of the data subject. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 33

Article 25 Data Protection by Design and by Default Taking into account the state of the art, the cost of implementation and the nature, scope, context and purposes of processing as well as the risks of varying likelihood and severity for rights and freedoms of natural persons posed by the processing, the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organizational measures, such as pseudonymisation, which are designed to implement data-protection principles, such as data minimization, in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects. The controller shall implement appropriate technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed. That obligation applies to the amount of personal data collected, the extent of their processing, the period of their storage and their accessibility. In particular, such measures shall ensure that by default personal data are not made accessible without the individual’s intervention to an indefinite number of natural persons. An approved certification mechanism pursuant to Article 42 may be used as an element to demonstrate compliance with the requirements set out in paragraphs 1 and 2 of this Article. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 34

Article 30 – Part 1 Records of Processing (1) Each controller and, where applicable, the controller’s representative, shall maintain a record of processing activities under its responsibility. That record shall contain all of the following information: a. the name and contact details of the controller and, where applicable, the joint controller, the controller’s representative and the data protection officer; b. the purposes of the processing; c. a description of the categories of data subjects and of the categories of personal data; d. the categories of recipients to whom the personal data have been or will be disclosed including recipients in third countries or international organizations; e. where applicable, transfers of personal data to a third country or an international organization, including the identification of that third country or f. g. international organization and, in the case of transfers referred to in the second subparagraph of Article 49(1), the documentation of suitable safeguards; where possible, the envisaged time limits for erasure of the different categories of data; where possible, a general description of the technical and organizational security measures referred to in Article 32(1). (2) Each processor and, where applicable, the processor’s representative shall maintain a record of all categories of processing activities carried out on behalf of a controller, containing: a. the name and contact details of the processor or processors and of each controller on behalf of which the processor is acting, and, where applicable, of the controller’s or the processor’s representative, and the data protection officer; b. the categories of processing carried out on behalf of each controller; c. where applicable, transfers of personal data to a third country or an international organization, including the identification of that third country or d. international organization and, in the case of transfers referred to in the second subparagraph of Article 49(1), the documentation of suitable safeguards; where possible, a general description of the technical and organizational security measures referred to in Article 32(1). (3) The records referred to in paragraphs 1 and 2 shall be in writing, including in electronic form. (4) The controller or the processor and, where applicable, the controller’s or the processor’s representative, shall make the record available to the supervisory authority on request. (5) The obligations referred to in paragraphs 1 and 2 shall not apply to an enterprise or an organization employing fewer than 250 persons unless the processing it carries out is likely to result in a risk to the rights and freedoms of data subjects, the processing is not occasional, or the processing includes special categories of data as referred to in Article 9(1) or personal data relating to criminal convictions and offences referred to in Article 10. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 35

Article 30 – Part 2 WRITTEN RECORDS OF PROCESSING Article 30 - Records of Processing Must be written or digital form and be made available to DPA’s upon request! Not applicable to businesses with fewer than 250 employees unless the processing it carries out is likely to result in a risk to the rights and freedoms of data subjects, the processing is not occasional, or the processing includes special categories of data or personal data relating to criminal convictions and offences. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 36

GDPR: Factors to Consider Prior to Imposing Fines (Article 83) All fines have to be “effective, proportionate and dissuasive” and they can be imposed in conjunction with the exercise of the DPA’s investigatory and corrective powers in Article 58, meaning that serious breaches of the regulation can be met with multiple responses. However, if the controller or processor breaches various requirements of GDPR, the total amount of the fine cannot exceed the amount that is specified for the most serious breach, which means each breach will need a particular quantum assigned to it. Before a fine can be imposed or the quantum decided upon, the DPAs need to consider these factors as follows: Administrative fines shall, depending on the circumstances for each individual case, be imposed in addition to or instead of measures referred to in points (a) to (h) and (j) of Article 58 (2). When deciding whether to impose an administrative fine and deciding on the amount of the administrative fine in each individual case due regard shall be given to the following: a. the nature, gravity and duration of the infringement taking into account the nature scope or purpose of the processing concerned, as well as the number of data subjects affected and the level of damage suffered by them; b. the intentional or negligent character of the infringement; c. any action taken by the controller or processor to mitigate the damage suffered by the data subjects; d. the degree of responsibility of the controller or processor taking into account technical and organizational measures implemented by them pursuant to Articles 25 and 32; e. any relevant previous infringements by the controller or processor; f. the degree of cooperation with the supervisory authority, in order to remedy the infringement and mitigate the possible adverse effects of the infringement; g. the categories of personal data affected by the infringement; h. The manner in which the infringement became known to the supervisory authority, in particular whether, and if so, to what extent, the controller or processor notified the infringement; i. where measures referred to in Article 58 (2) have previously been ordered against the controller or processor concerned with regard to the same subject matter, compliance with those measures; j. adherence to approved codes of conduct pursuant to Article 40 or approved certification mechanisms pursuant to Article 42; and k. any other aggravating or mitigating factor applicable to the circumstances of the case, such as financial benefits gained or losses avoided directly or indirectly from the infringement. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 37

Security of Processing Controllers and Processors Security of Processing (Article 32) - “Risk-based Approach” Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including inter alia as appropriate: a. the pseudonymisation and encryption of personal data; b. the ability to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services; c. the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident; d. a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing. In assessing the appropriate level of security account shall be taken in particular of the risks that are presented by processing, in particular from accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to personal data transmitted, stored or otherwise processed. Adherence to an approved code of conduct as referred to in Article 40 or an approved certification mechanism as referred to in Article 42 may be used as an element by which to demonstrate compliance with the requirements set out in paragraph 1 of this Article. The controller and processor shall take steps to ensure that any natural person acting under the authority of the controller or the processor who has access to personal data does not process them except on instructions from the controller, unless he or she is required to do so by Union or Member State law. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 38

Article 35 – Part 1 Data Protection Impact Assessment (DPIA) 1) 1) Where a type of processing in particular using new technologies, and taking into account the nature, scope, context and purposes of the processing, is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall, prior to the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data. A single assessment may address a set of similar processing operations that present similar high risks. 2) The controller shall seek the advice of the data protection officer, where designated, when carrying out a data protection impact assessment. 3) A data protection impact assessment referred to in paragraph 1 shall in particular be required in the case of: a. a systematic and extensive evaluation of personal aspects relating to natural persons which is based on automated processing, including profiling, and on which decisions are based that produce legal effects concerning the natural person or similarly significantly affect the natural person; b. processing on a large scale of special categories of data referred to in Article 9(1), or of personal data relating to criminal convictions and offences referred to in Article 10; or c. a systematic monitoring of a publicly accessible area on a large scale. 4) The supervisory authority shall establish and make public a list of the kind of processing operations which are subject to the requirement for a data protection impact assessment pursuant to paragraph 1. The supervisory authority shall communicate those lists to the Board referred to in Article 68. 5) The supervisory authority may also establish and make public a list of the kind of processing operations for which no data protection impact assessment is required. The supervisory authority shall communicate those lists to the Board. 6) Prior to the adoption of the lists referred to in paragraphs 4 and 5, the competent supervisory authority shall apply the consistency mechanism referred to in Article 63 where such lists involve processing activities which are related to the offering of goods or services to data subjects or to the monitoring of their behavior in several Member States, or may substantially affect the free movement of personal data within the Union. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 39

Article 35 – Part 1 Data Protection Impact Assessment (DPIA) 1) 1) Where a type of processing in particular using new technologies, and taking into account the nature, scope, context and purposes of the processing, is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall, prior to the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data. A single assessment may address a set of similar processing operations that present similar high risks. 2) The controller shall seek the advice of the data protection officer, where designated, when carrying out a data protection impact assessment. 3) A data protection impact assessment referred to in paragraph 1 shall in particular be required in the case of: a. a systematic and extensive evaluation of personal aspects relating to natural persons which is based on automated processing, including profiling, and on which decisions are based that produce legal effects concerning the natural person or similarly significantly affect the natural person; b. processing on a large scale of special categories of data referred to in Article 9(1), or of personal data relating to criminal convictions and offences referred to in Article 10; or c. a systematic monitoring of a publicly accessible area on a large scale. 4) The supervisory authority shall establish and make public a list of the kind of processing operations which are subject to the requirement for a data protection impact assessment pursuant to paragraph 1. The supervisory authority shall communicate those lists to the Board referred to in Article 68. 5) The supervisory authority may also establish and make public a list of the kind of processing operations for which no data protection impact assessment is required. The supervisory authority shall communicate those lists to the Board. 6) Prior to the adoption of the lists referred to in paragraphs 4 and 5, the competent supervisory authority shall apply the consistency mechanism referred to in Article 63 where such lists involve processing activities which are related to the offering of goods or services to data subjects or to the monitoring of their behavior in several Member States, or may substantially affect the free movement of personal data within the Union. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 40

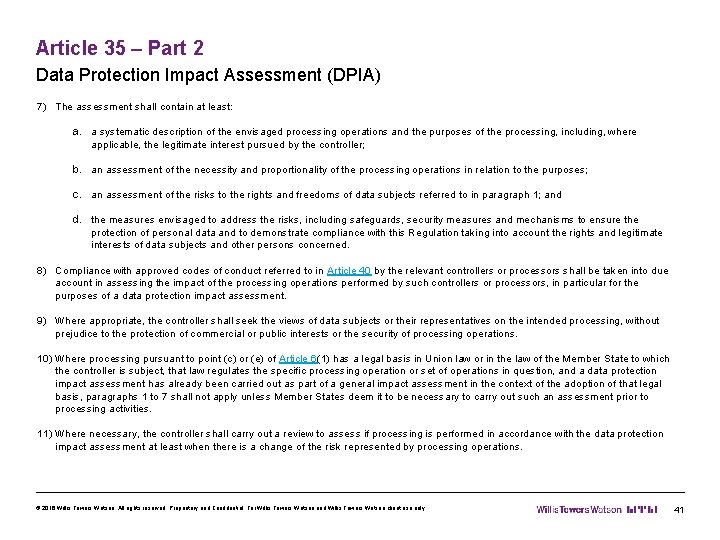
Article 35 – Part 2 Data Protection Impact Assessment (DPIA) 7) The assessment shall contain at least: a. a systematic description of the envisaged processing operations and the purposes of the processing, including, where applicable, the legitimate interest pursued by the controller; b. an assessment of the necessity and proportionality of the processing operations in relation to the purposes; c. an assessment of the risks to the rights and freedoms of data subjects referred to in paragraph 1; and d. the measures envisaged to address the risks, including safeguards, security measures and mechanisms to ensure the protection of personal data and to demonstrate compliance with this Regulation taking into account the rights and legitimate interests of data subjects and other persons concerned. 8) Compliance with approved codes of conduct referred to in Article 40 by the relevant controllers or processors shall be taken into due account in assessing the impact of the processing operations performed by such controllers or processors, in particular for the purposes of a data protection impact assessment. 9) Where appropriate, the controller shall seek the views of data subjects or their representatives on the intended processing, without prejudice to the protection of commercial or public interests or the security of processing operations. 10) Where processing pursuant to point (c) or (e) of Article 6(1) has a legal basis in Union law or in the law of the Member State to which the controller is subject, that law regulates the specific processing operation or set of operations in question, and a data protection impact assessment has already been carried out as part of a general impact assessment in the context of the adoption of that legal basis, paragraphs 1 to 7 shall not apply unless Member States deem it to be necessary to carry out such an assessment prior to processing activities. 11) Where necessary, the controller shall carry out a review to assess if processing is performed in accordance with the data protection impact assessment at least when there is a change of the risk represented by processing operations. © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 41

Article 82 Right to compensation and liability 1) Any person who has suffered material or non-material damage as a result of an infringement of this Regulation shall have the right to receive compensation from the controller or processor for the damage suffered. 2) Any controller involved in processing shall be liable for the damage caused by processing which infringes this Regulation. A processor shall be liable for the damage caused by processing only where it has not complied with obligations of this Regulation specifically directed to processors or where it has acted outside or contrary to lawful instructions of the controller. 3) A controller or processor shall be exempt from liability under paragraph 2 if it proves that it is not in any way responsible for the event giving rise to the damage. 4) Where more than one controller or processor, or both a controller and a processor, are involved in the same processing and where they are, under paragraphs 2 and 3, responsible for any damage caused by processing, each controller or processor shall be held liable for the entire damage in order to ensure effective compensation of the data subject. 5) Where a controller or processor has, in accordance with paragraph 4, paid full compensation for the damage suffered, that controller or processor shall be entitled to claim back from the other controllers or processors involved in the same processing that part of the compensation corresponding to their part of responsibility for the damage, in accordance with the conditions set out in paragraph 2. 6) Court proceedings for exercising the right to receive compensation shall be brought before the courts competent under the law of the Member State referred to in Article 79(2). © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 42

Pivotal Cases Leading to GDPR Europe v. Facebook (established class action against Facebook in Austria) June 2017 http: //www. europe-v-facebook. org/sk/PA_CJEU_en. pdf Maximillian Schrems v. Data Protection Commissioner, C-362/14, October 6, 2015 Mr. Schrems lodged a complaint with the Irish supervisory authority (the Data Protection Commissioner), taking the view that, in the light of the revelations made in 2013 by Edward Snowden concerning the activities of the United States intelligence services (in particular the National Security Agency (‘the NSA’), the law and practice of the United States do not offer sufficient protection against surveillance by the public authorities of the data transferred to that country. https: //curia. europa. eu/jcms/upload/docs/application/pdf/2015 -10/cp 150117 en. pdf Vidal Hall v. Google, Inc. EWCA Civ 311, March 27, 2015 https: //www. judiciary. gov. uk/wp-content/uploads/2015/03/google-v-vidal-hall-judgment. pdf Google Spain SL and Google Inc. v. Agencia Espanola de Protecion de Dataos (AEPD) and Mario Costieja Gonzalez, C-131/12, May 13, 2014 Decision by the Court of Justice of the European Union (CJEU) held that an Internet Search Engine operator is responsible for the processing that it carries out of personal information which appears on web pages published by third parties. The outcome of the ruling is that an Internet search engine must consider requests from individuals to remove links to freely accessible web pages resulting from a search on their name. Grounds for removal include cases where the search result(s) "appear to be inadequate, irrelevant or no longer relevant or excessive in the light of the time that had elapsed. "If the search engine rejects the request, the individual may ask relevant authorities to consider the case. Under certain conditions, the search engine may be ordered to remove the links from search results. https: //en. wikipedia. org/wiki/Google_Spain_v_AEPD_and_Mario_Costeja_Gonz%C 3%A 1 lez Digital Rights Ireland, Seitlinger and Others, C-293/12, April 8, 2014 http: //europeanlawblog. eu/2014/04/08/joined-cases-c-29312 -and-59412 -digital-rights-ireland-seitlinger-and-others-the-good-thebad-and-the-ugly/ © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 43

Additional Resources Book: European Data Protection–Law and Practice, Eduardo Ustaran, CIPP/E. , Partner, Hogan Lovells – An IAPP Publication, 2018 FTC: https: //www. ftc. gov/enforcement/statutes/federal-trade-commission-act https: //www. ftc. gov/news-events/press-releases/2017/11/ftc-gives-final-approval-settlements-companies-falsely-claimed ICO Enforcement Actions: https: //ico. org. uk/action-weve-taken/enforcement/ Displays all 173 Recitals and 99 Articles: https: //gdpr-info. eu/ Resource for SME’s: http: //ec. europa. eu/justice/smedataprotect/index_en. htm Global Law Firm Resources for GDPR Updates: https: //www. twobirds. com/en/hot-topics/general-data-protection-regulation http: //privacylawblog. fieldfisher. com/ (GDPR APP is available for download at i. Tunes for i. Phone and Androids) https: //www. huntonprivacyblog. com/publications/ https: //privacylaw. proskauer. com/ https: //www. hoganlovells. com/en/service/privacy-and-cybersecurity https: //www. dlapiper. com/en/us/ https: //www. bakerlaw. com/Privacy. Data. Protection https: //www. mofo. com/special-content/gdpr-readiness-center/ https: //www. venable. com/Privacy-and-Data-Security-Practices/ https: //www. pillsburylaw. com/en/services/gdpr. html © 2016 Willis Towers Watson. All rights reserved. Proprietary and Confidential. For Willis Towers Watson and Willis Towers Watson client use only. 44