Deadlocks Example 1 Example 2 Example 2 Example
























































- Slides: 181

Deadlocks

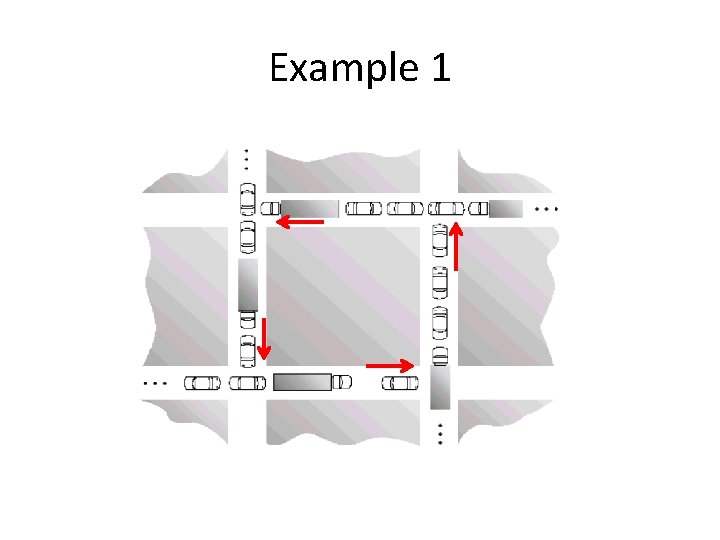
Example 1

Example 2

Example 2

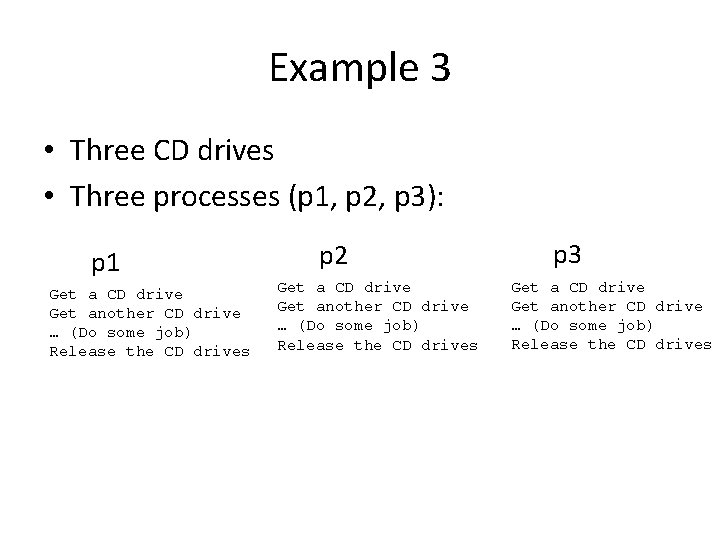
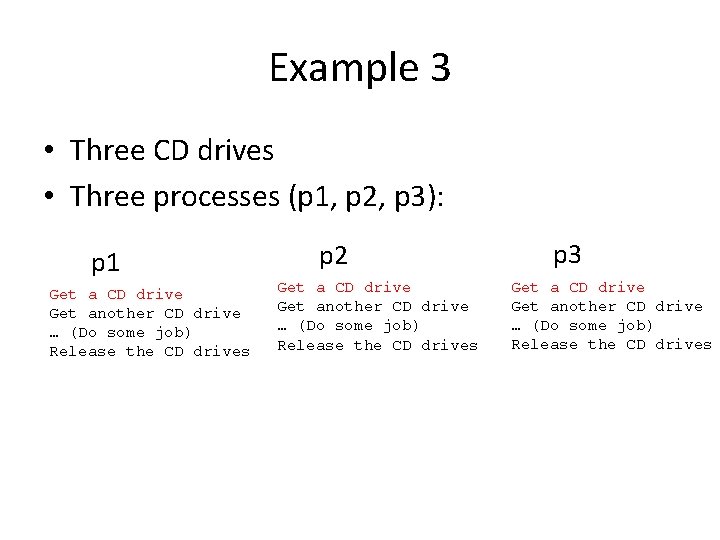
Example 3 • Three CD drives • Three processes (p 1, p 2, p 3): Get a CD drive Get another CD drive … (Do some job) Release the CD drives

Example 3 • Three CD drives • Three processes (p 1, p 2, p 3): p 1 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 2 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 3 Get a CD drive Get another CD drive … (Do some job) Release the CD drives

Example 3 • Three CD drives • Three processes (p 1, p 2, p 3): p 1 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 2 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 3 Get a CD drive Get another CD drive … (Do some job) Release the CD drives

Example 3 • Three CD drives • Three processes (p 1, p 2, p 3): p 1 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 2 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 3 Get a CD drive Get another CD drive … (Do some job) Release the CD drives

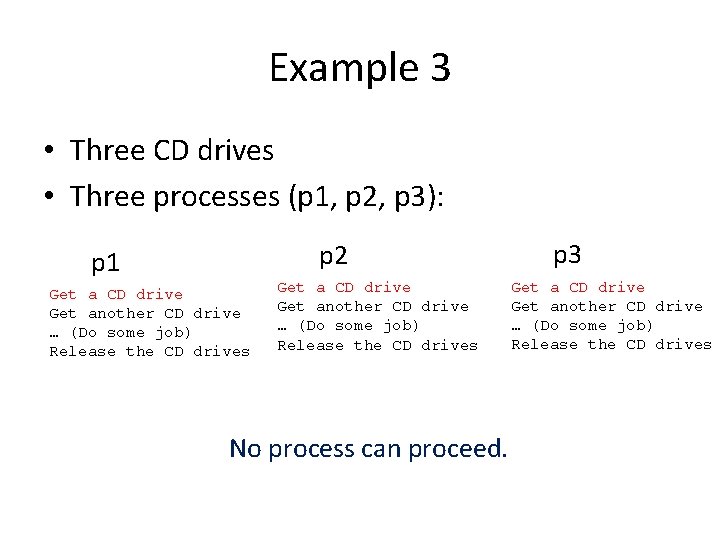
Example 3 • Three CD drives • Three processes (p 1, p 2, p 3): p 1 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 2 Get a CD drive Get another CD drive … (Do some job) Release the CD drives p 3 Get a CD drive Get another CD drive … (Do some job) Release the CD drives

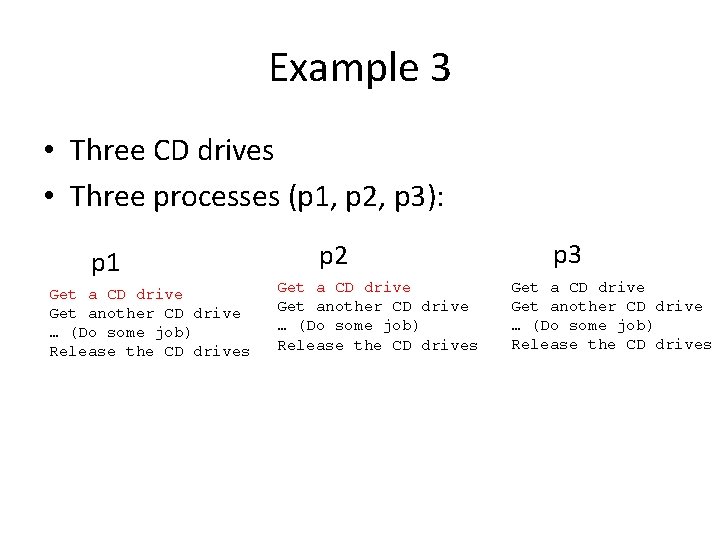
Example 3 • Three CD drives • Three processes (p 1, p 2, p 3): p 2 p 1 Get a CD drive Get another CD drive … (Do some job) Release the CD drives No process can proceed. p 3 Get a CD drive Get another CD drive … (Do some job) Release the CD drives

Conditions • • Mutual Exclusion Hold & Wait No Preemption Circular Wait

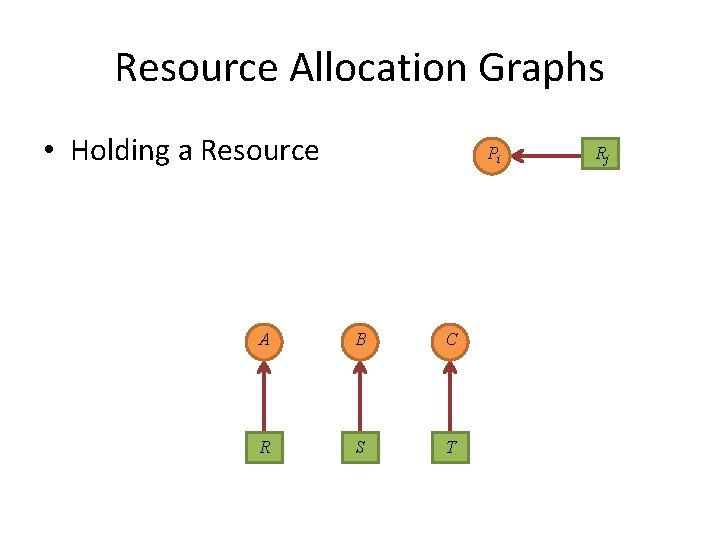
Resource Allocation Graphs • Processes • Resources Pi Rj A B C R S T

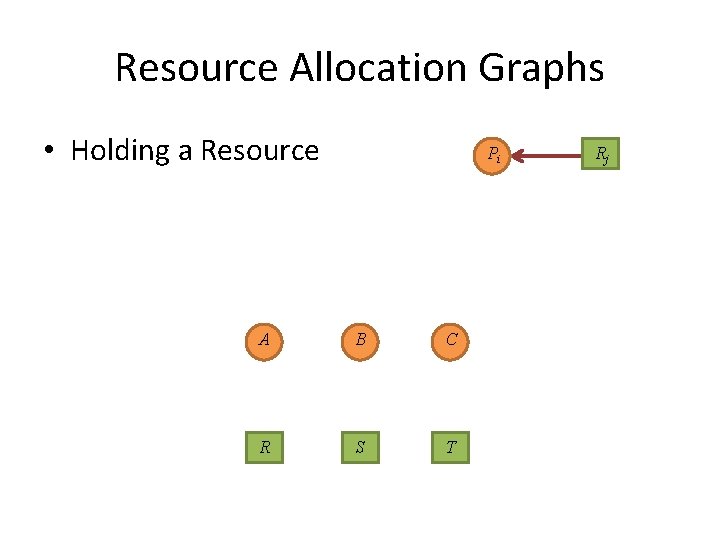
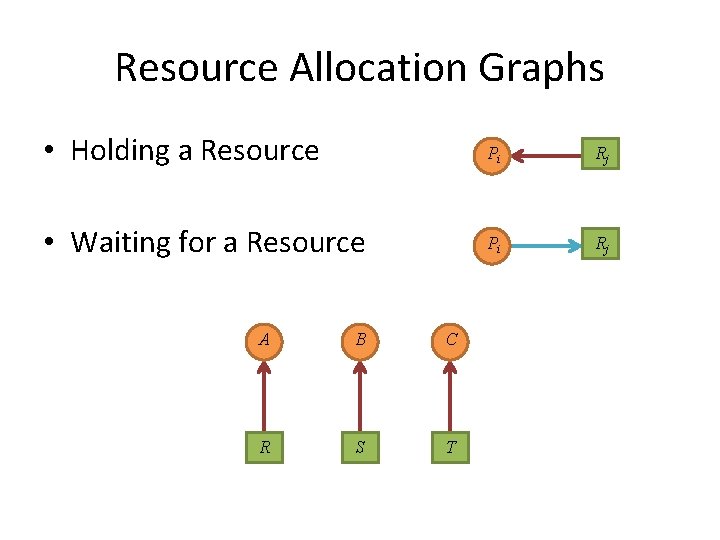
Resource Allocation Graphs • Holding a Resource Pi A B C R S T Rj

Resource Allocation Graphs • Holding a Resource Pi A B C R S T Rj

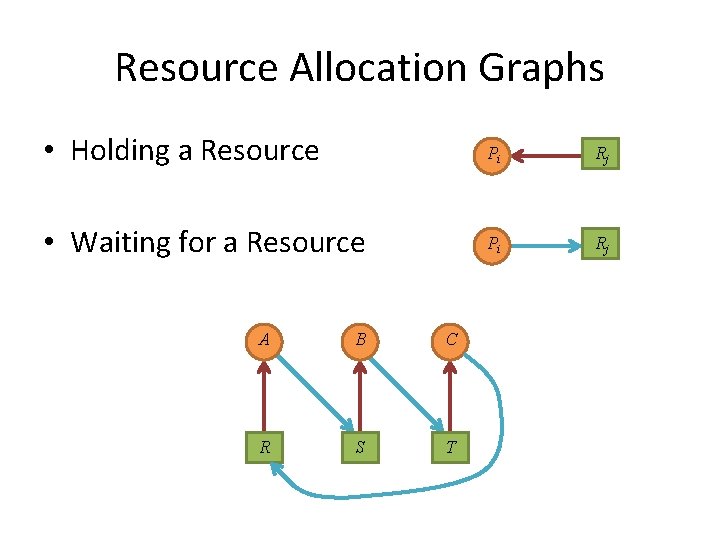
Resource Allocation Graphs • Holding a Resource Pi Rj • Waiting for a Resource Pi Rj A B C R S T

Resource Allocation Graphs • Holding a Resource Pi Rj • Waiting for a Resource Pi Rj A B C R S T

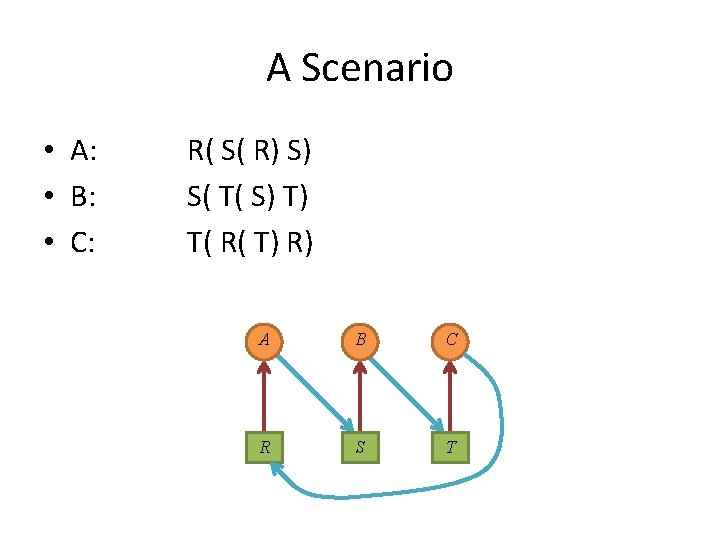
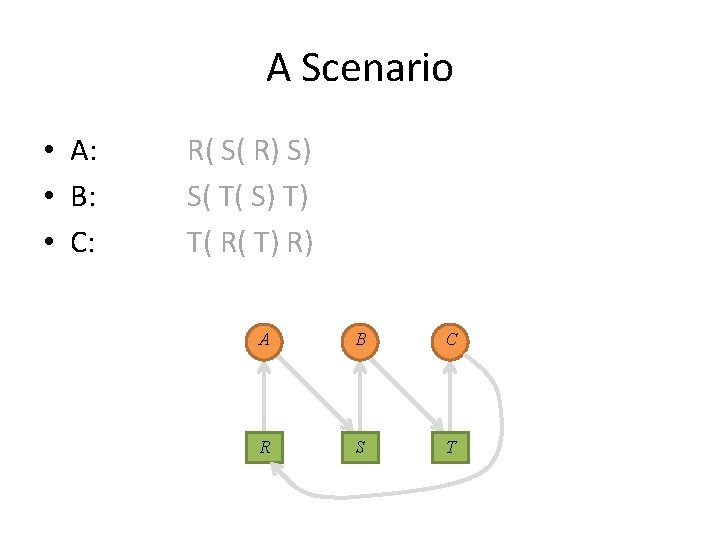
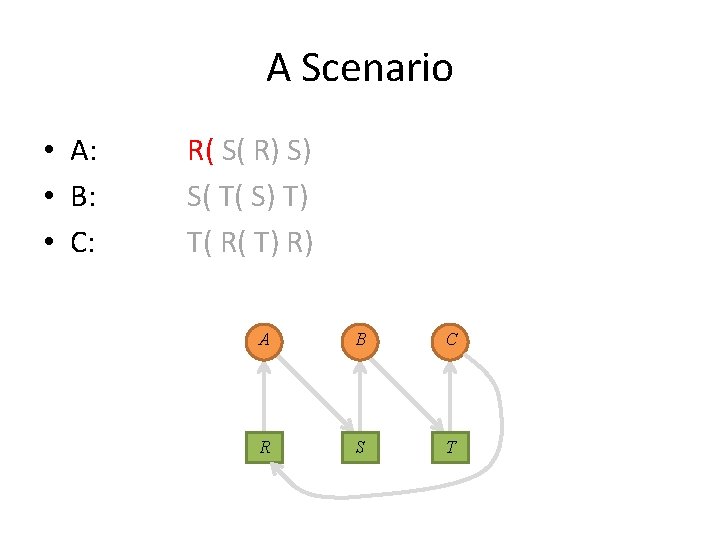
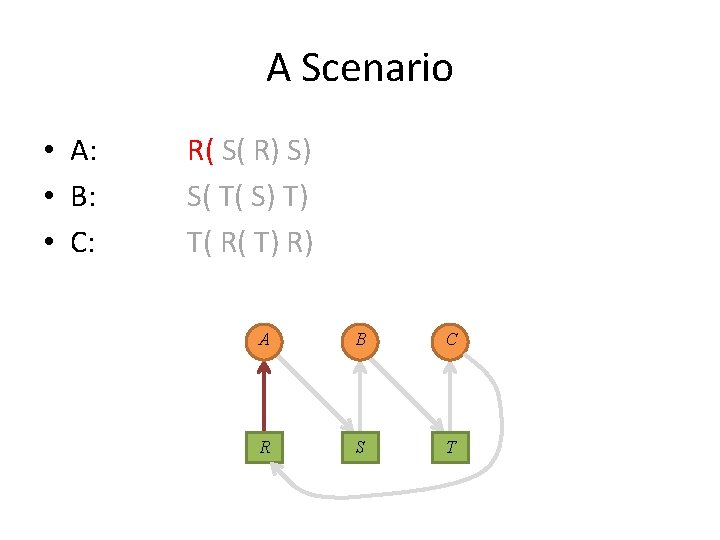
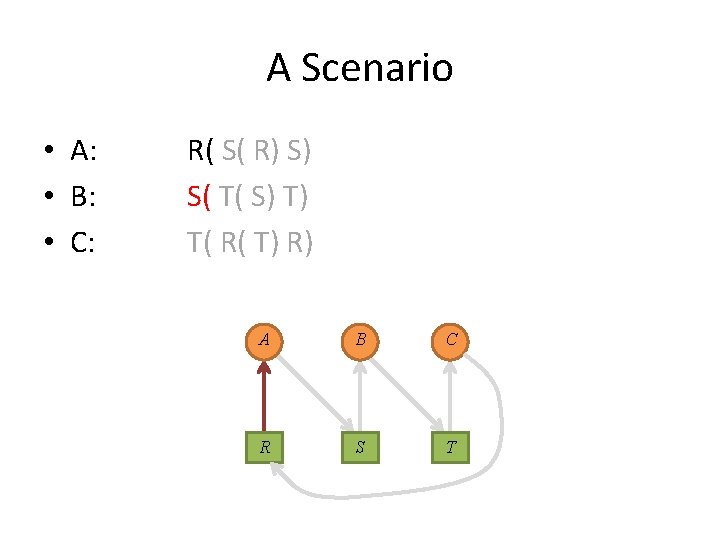
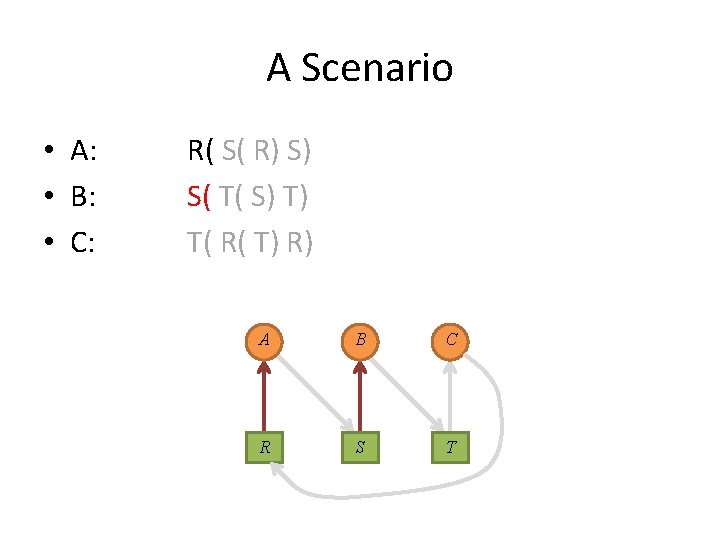
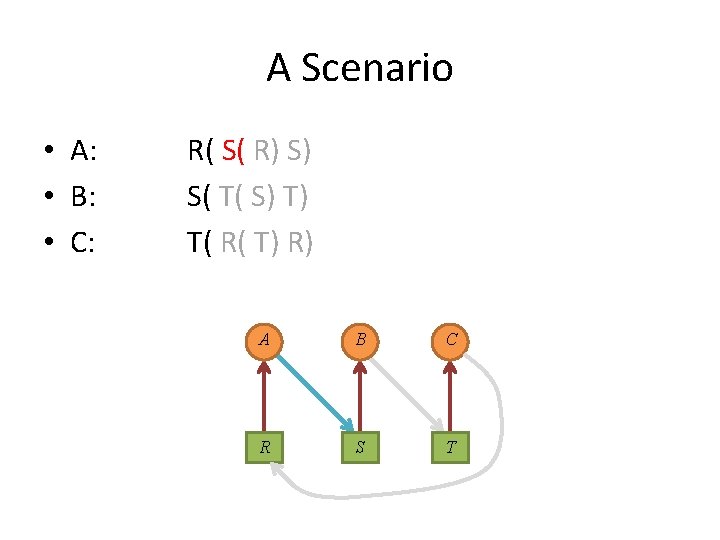
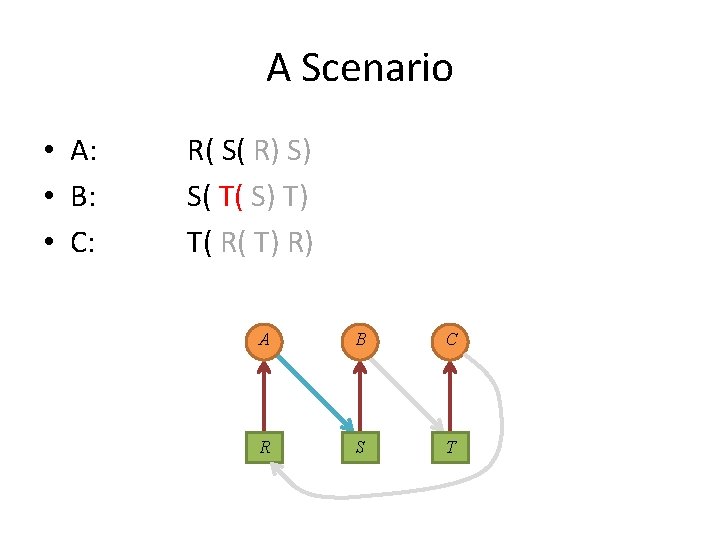
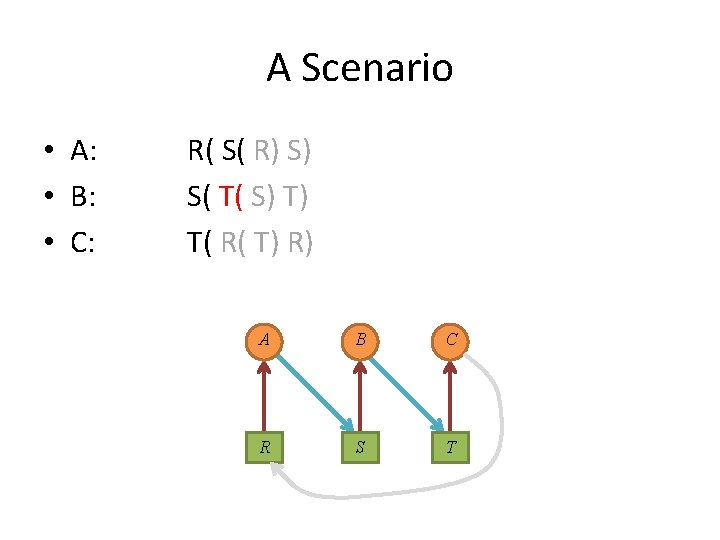
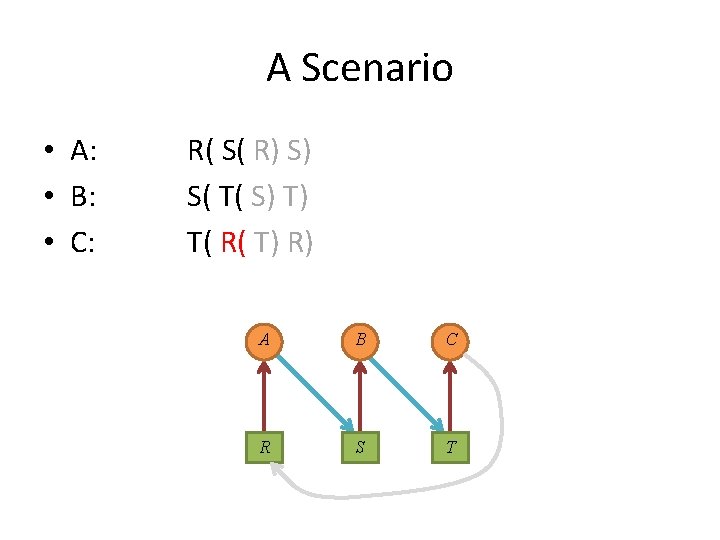
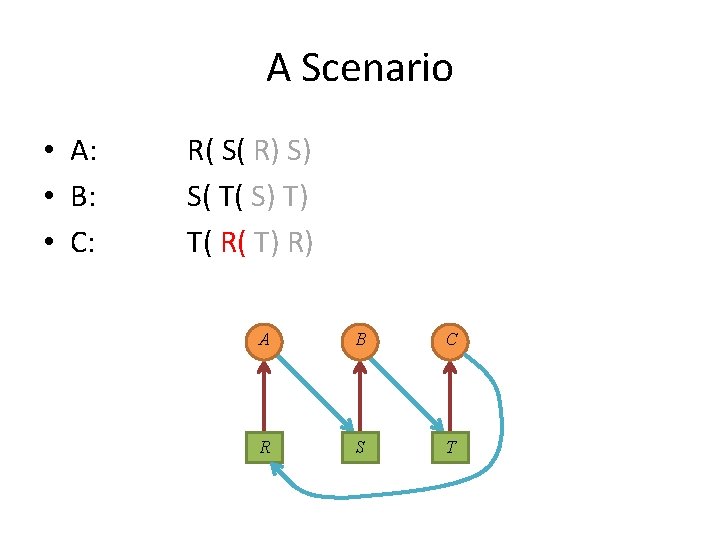
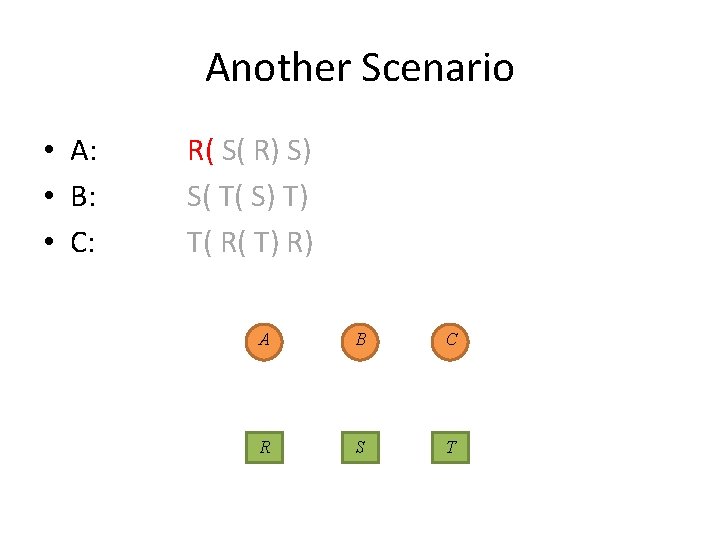
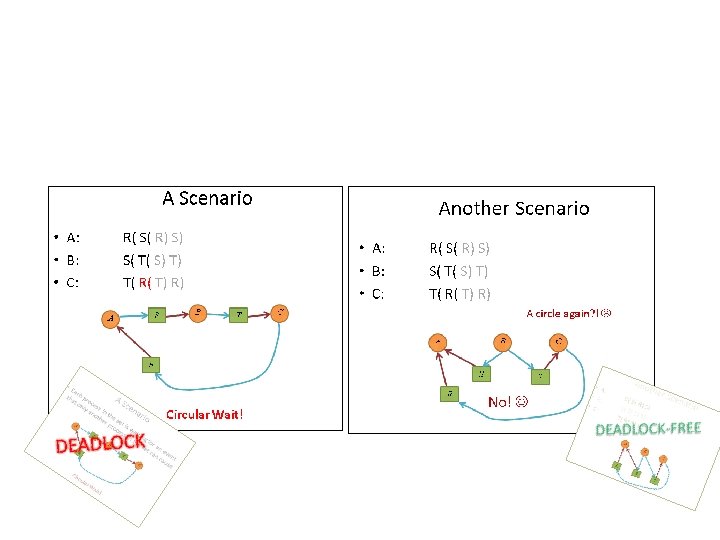
A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

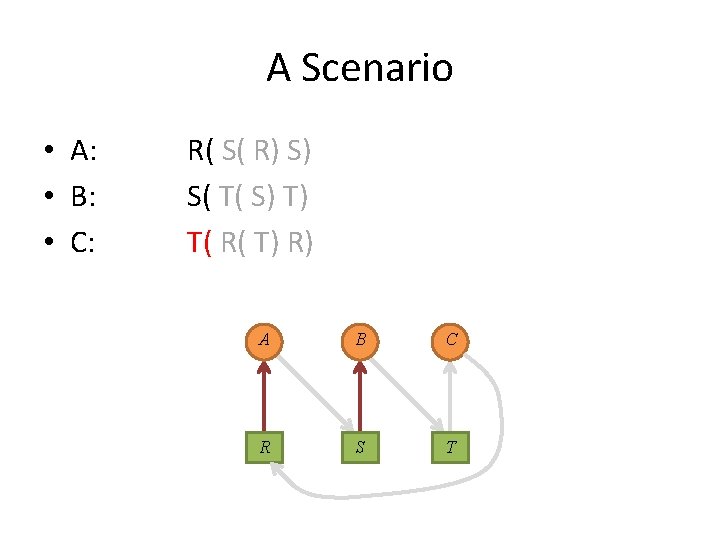
A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

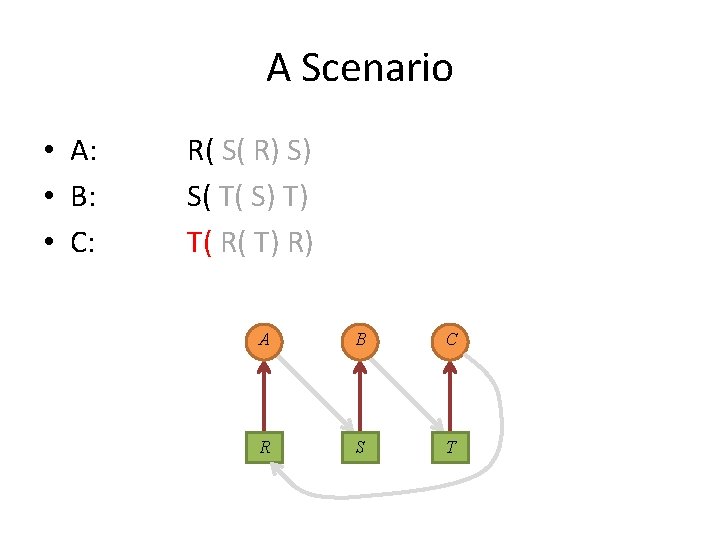
A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

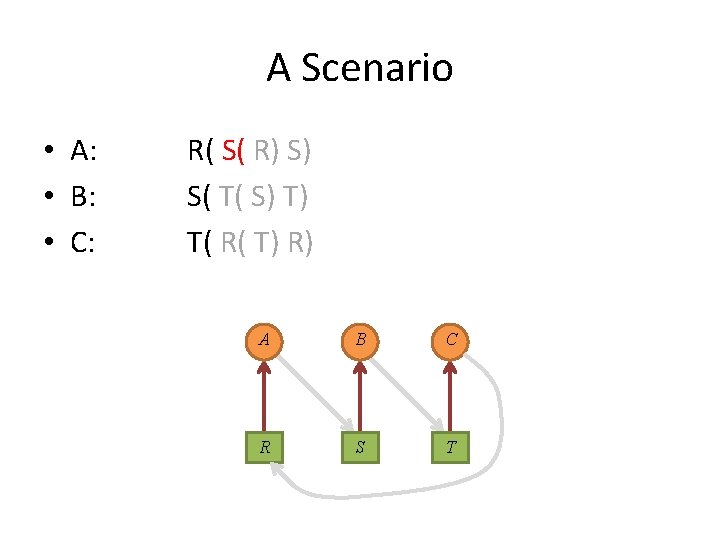
A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

A Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

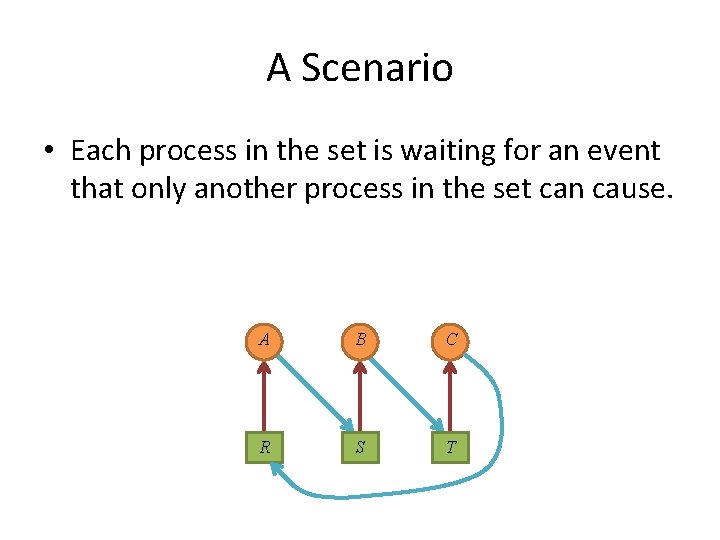
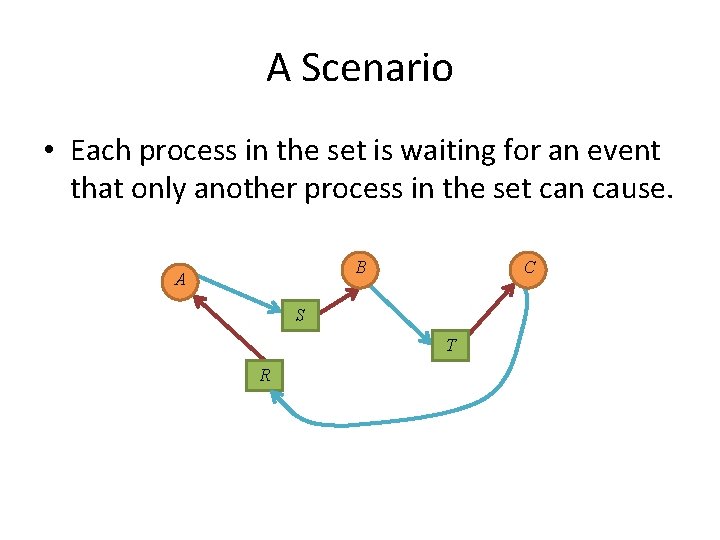
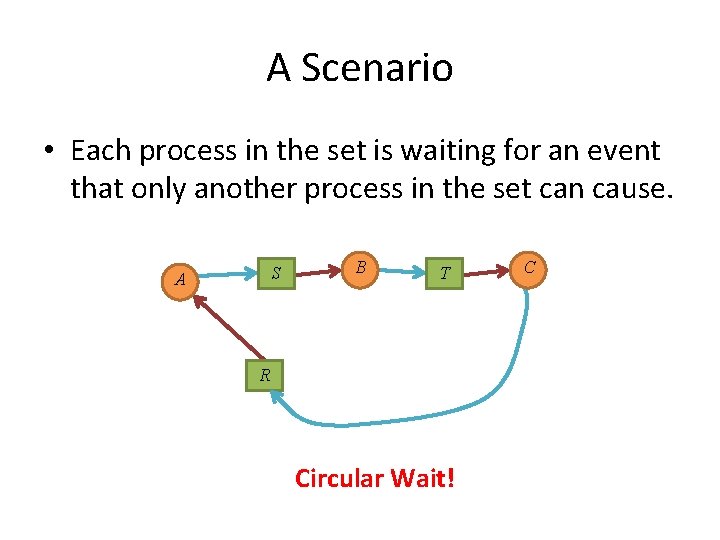
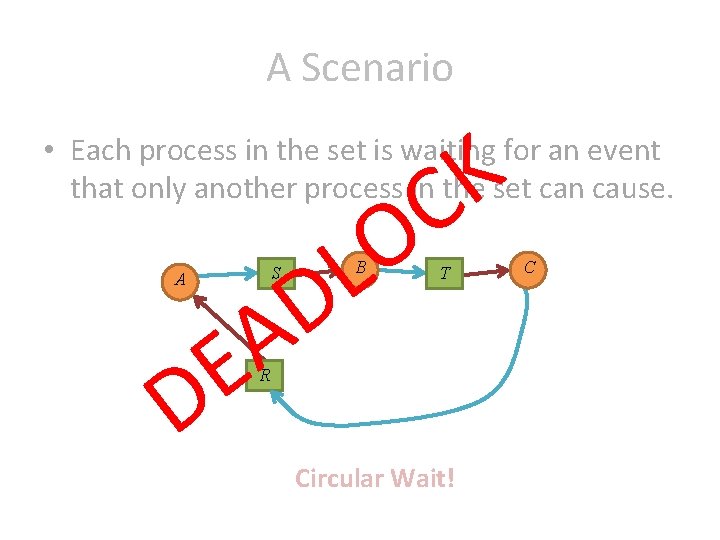
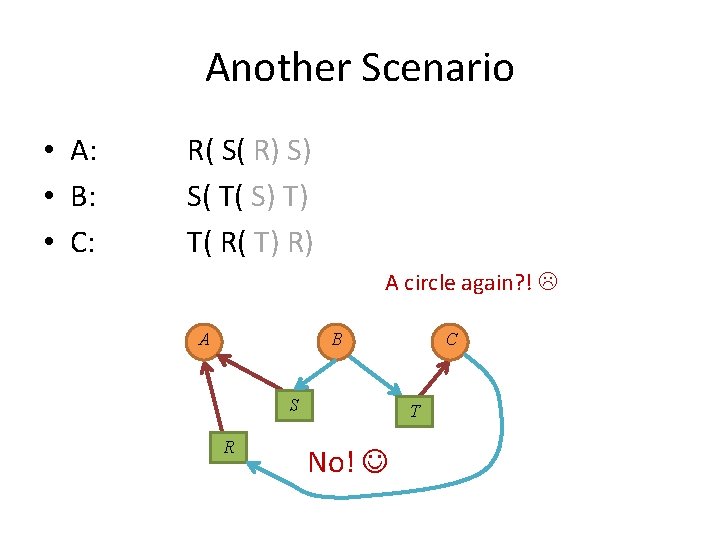
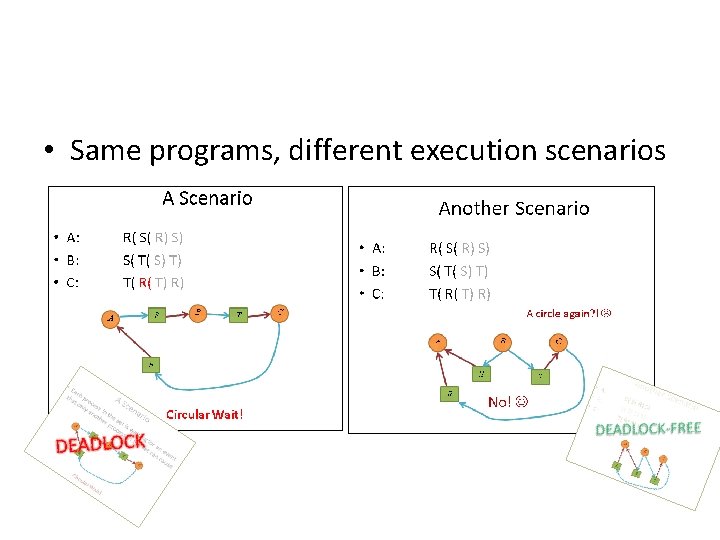
A Scenario • Each process in the set is waiting for an event that only another process in the set can cause. A B C R S T

A Scenario • Each process in the set is waiting for an event that only another process in the set can cause. B A C S T R

A Scenario • Each process in the set is waiting for an event that only another process in the set can cause. S A B T R Circular Wait! C

A Scenario K C • Each process in the set is waiting for an event that only another process in the set can cause. S A O L D B A E D T R Circular Wait! C

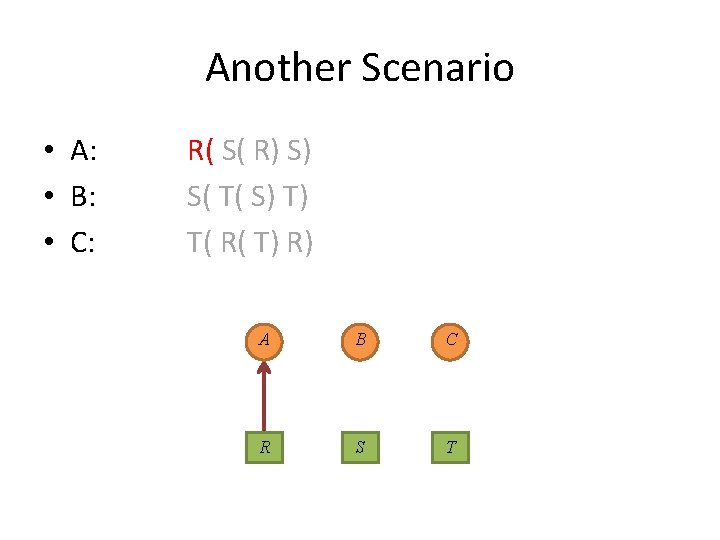
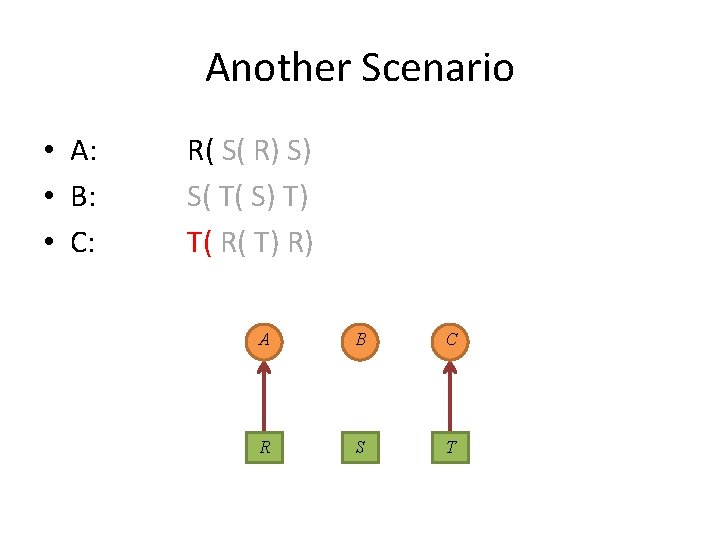
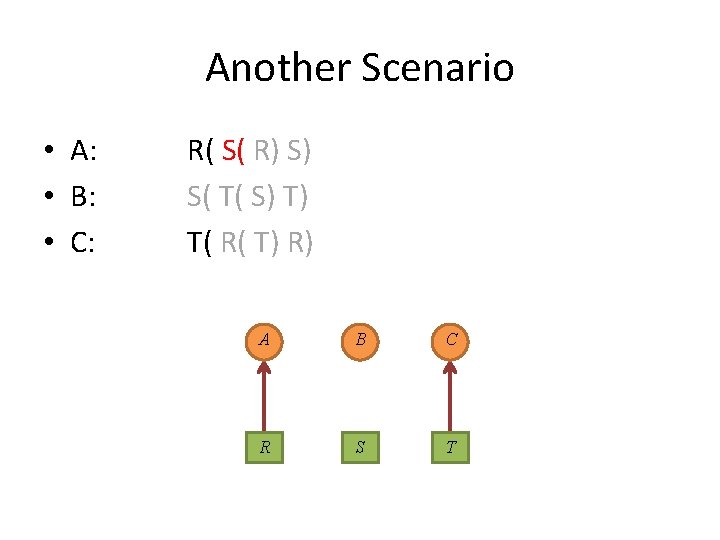
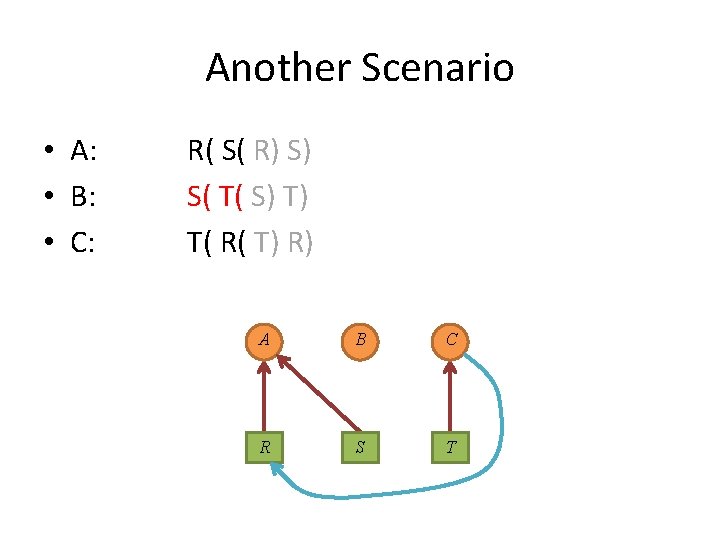
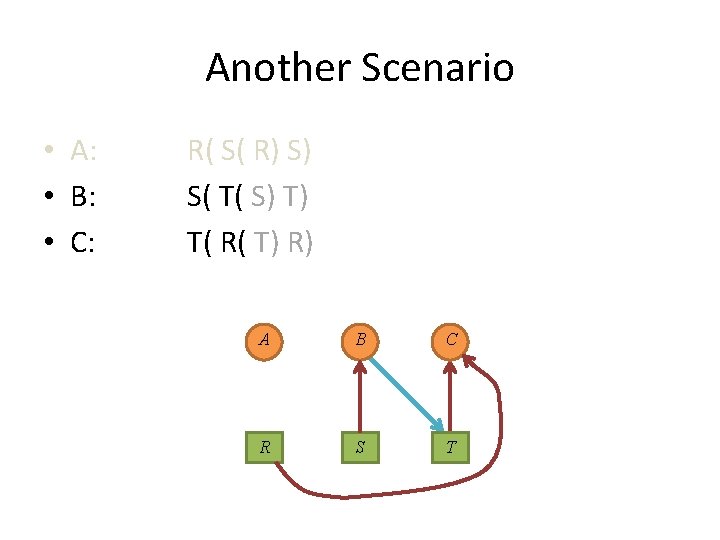
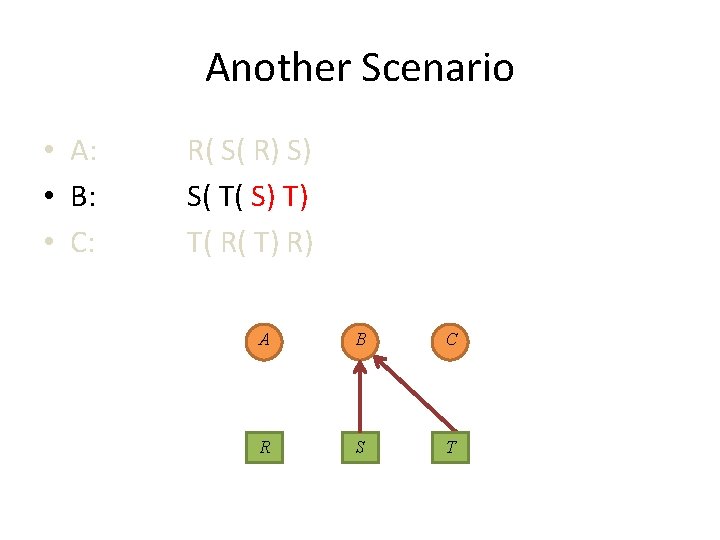
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

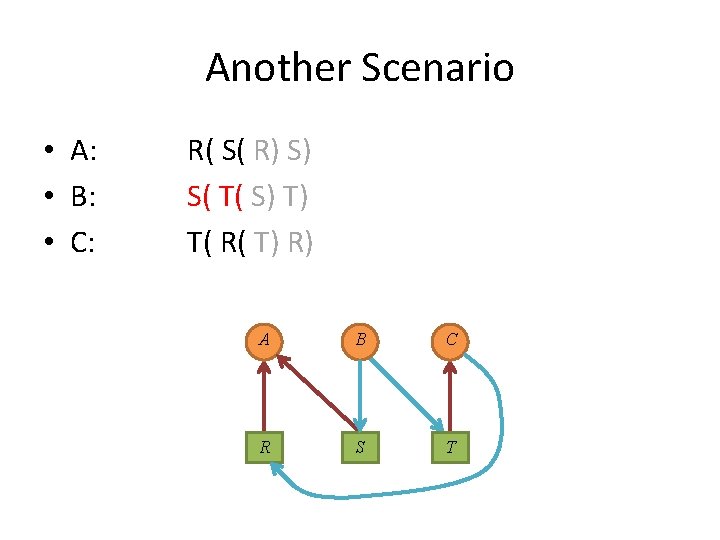
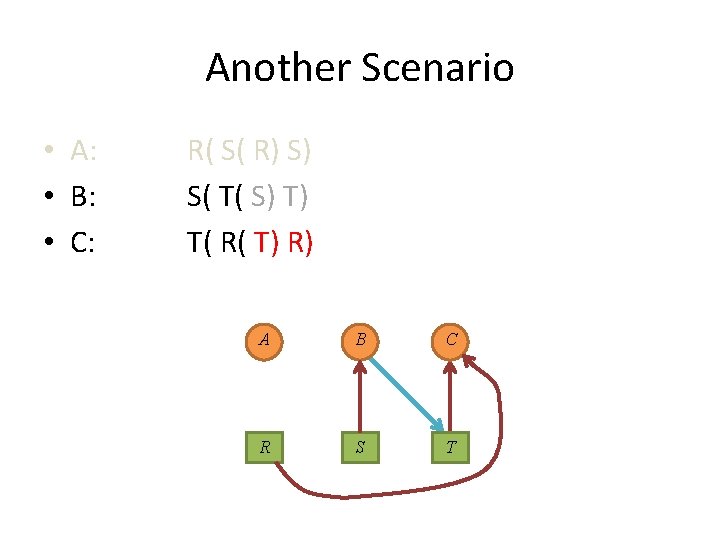
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

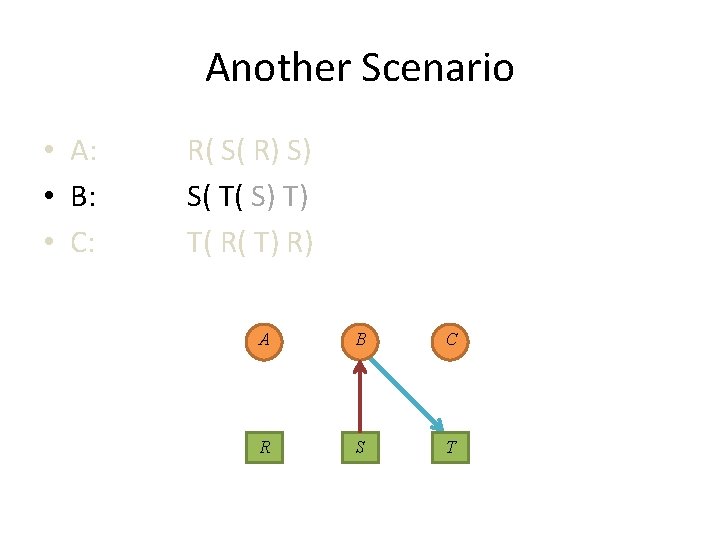
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

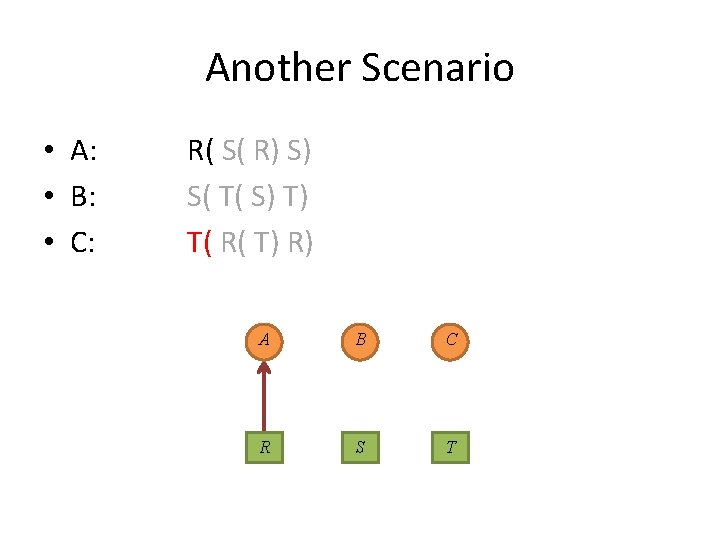
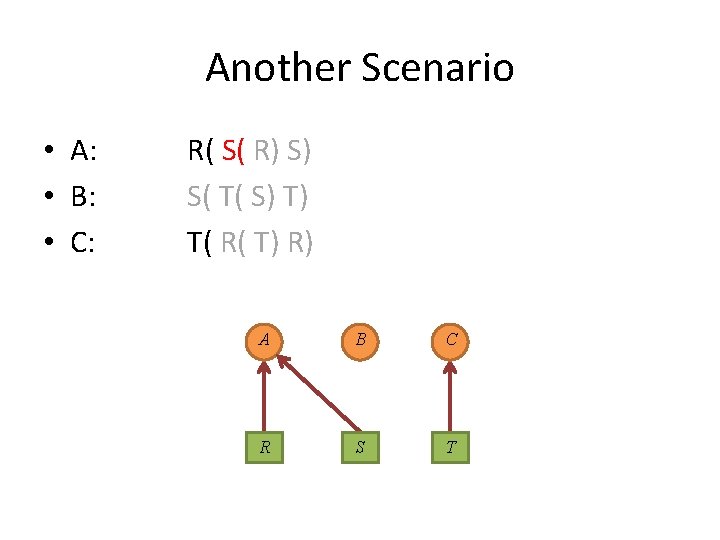
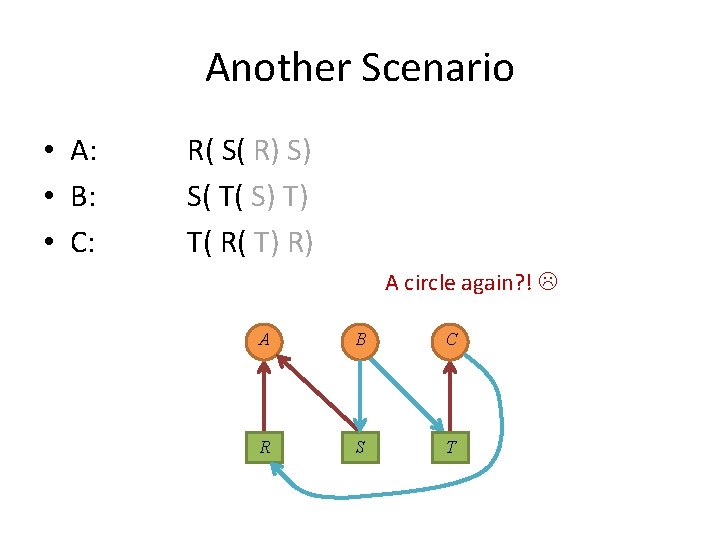
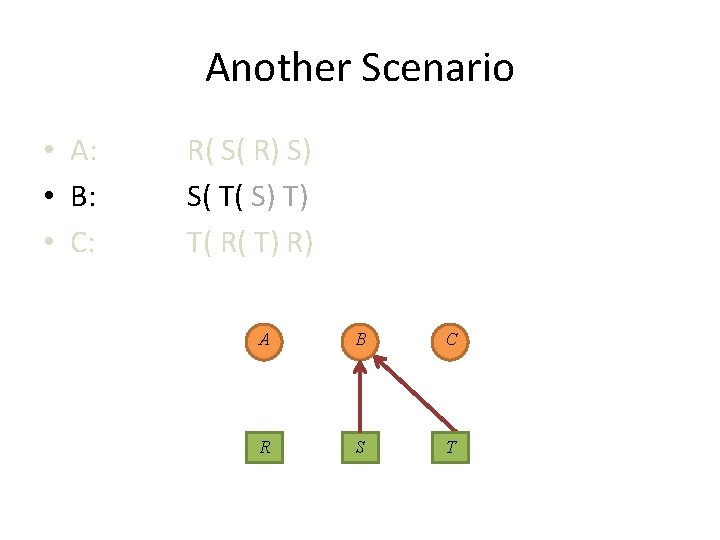
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A circle again? ! A B C R S T

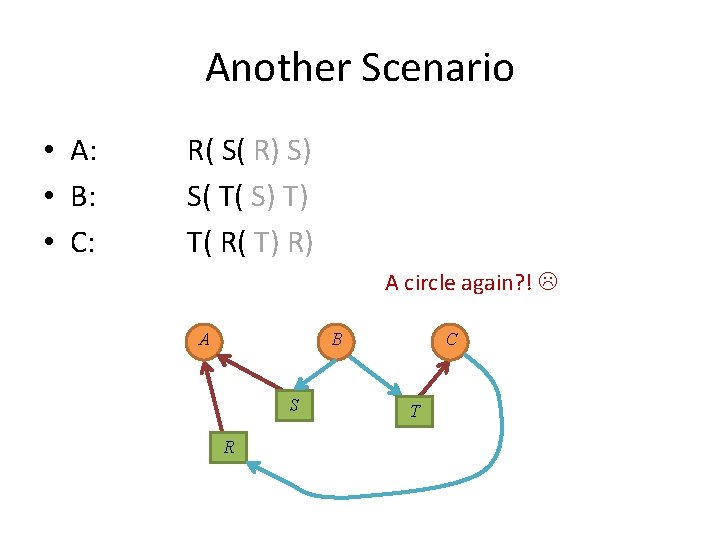
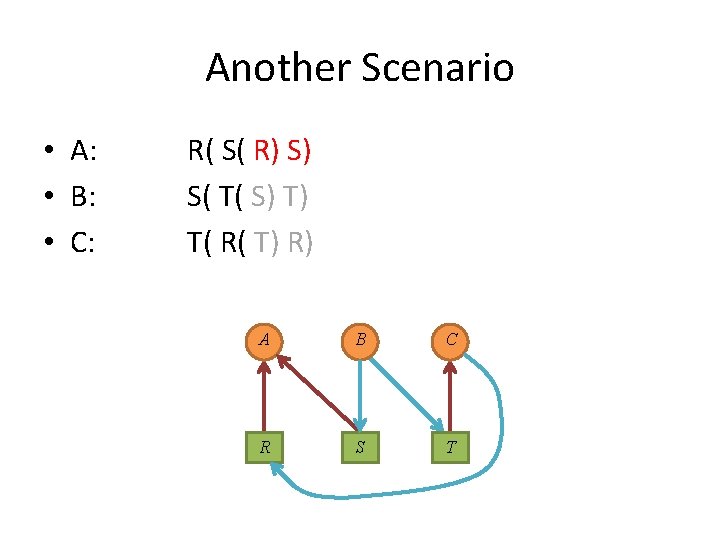
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A circle again? ! A B S R C T

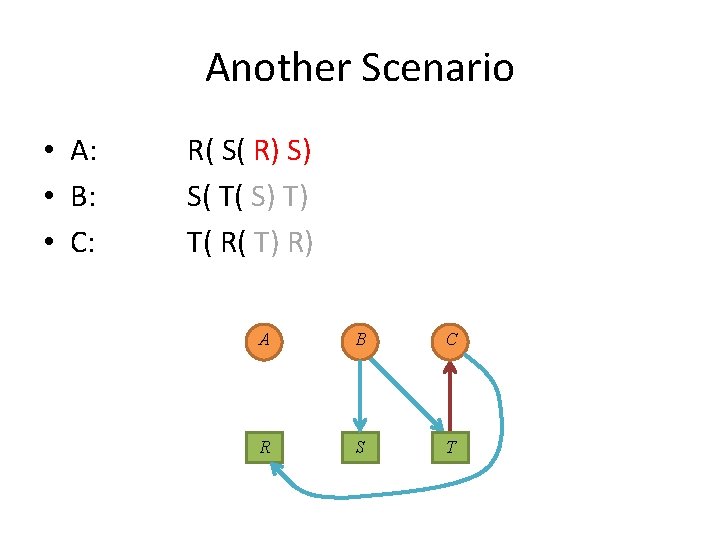
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A circle again? ! A B S R C T No!

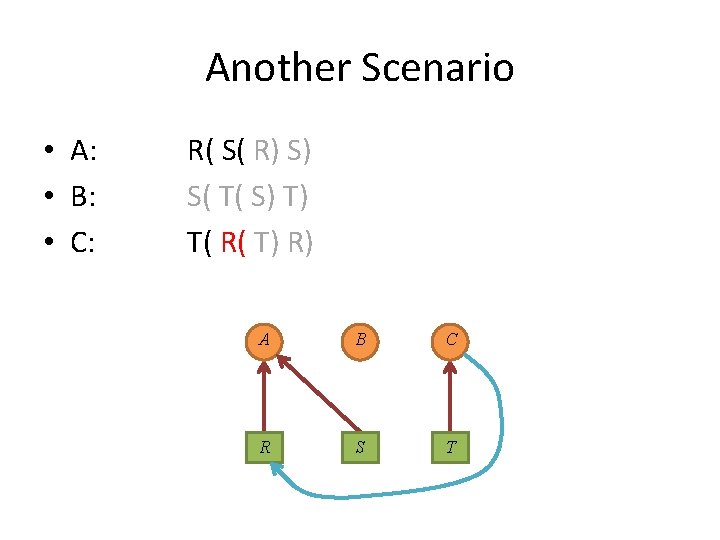
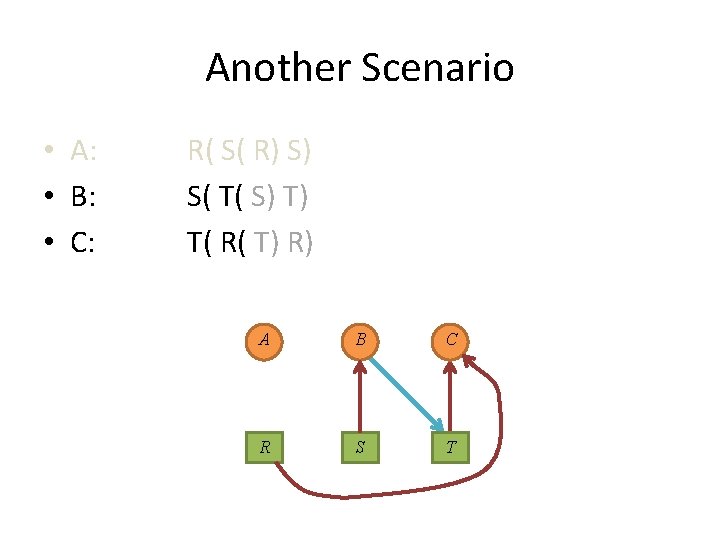
Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Another Scenario • A: • B: • C: R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

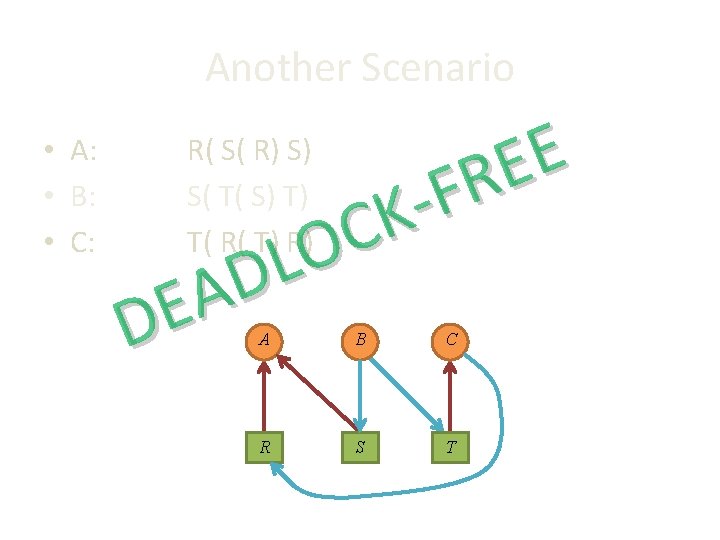
Another Scenario • A: • B: • C: E E R F K C O L D A E D R( S( R) S) S( T( S) T) T( R( T) R) A B C R S T

Now… What to do?

Now… What to do? – Ignore!

Ignore the problem: The Ostrich Algorithm • Reasons? – Rare – Not serious – Performance penalty – Some problems are really hard to detect

Ignore the problem: The Ostrich Algorithm • Reasons: – Rare – Not serious – Performance penalty – Some problems are really hard to detect

Ignore the problem: The Ostrich Algorithm • Reasons: – Rare – Not serious – Performance penalty – Some problems are really hard to detect

Ignore the problem: The Ostrich Algorithm • Reasons: – Rare – Not serious – Performance penalty – Some problems are really hard to detect

Ignore the problem: The Ostrich Algorithm • Reasons: – Rare – Not serious – Performance penalty – Some problems are really hard to detect

Now… What to do? • Possible Strategies – Ignore! – Detection and Recovery – Deadlock Avoidance (dynamically) – Deadlock Prevention (statically)

Now… What to do? • Possible Strategies – Ignore! – Detection and Recovery – Deadlock Avoidance (dynamically) – Deadlock Prevention (statically)
Recap • Deadlock?

Recap • Deadlock? • Conditions?

Recap • Deadlock? • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait

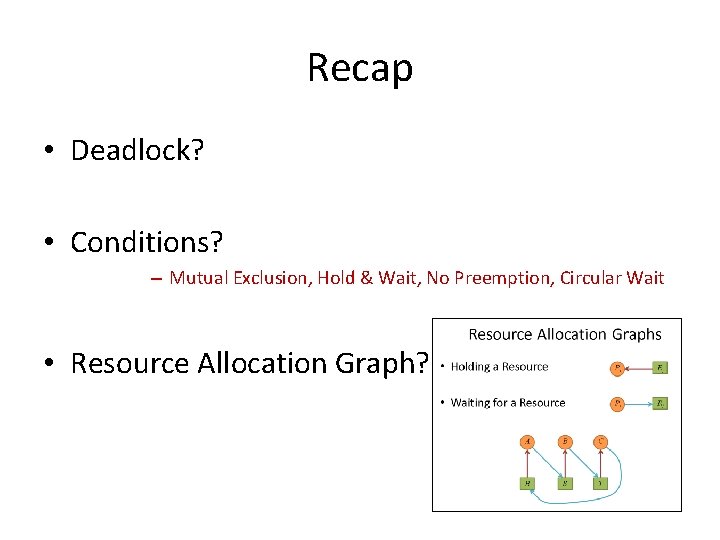
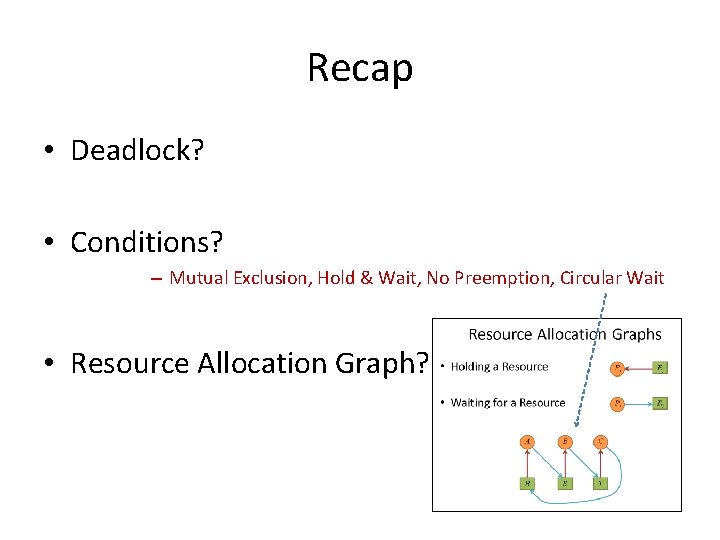
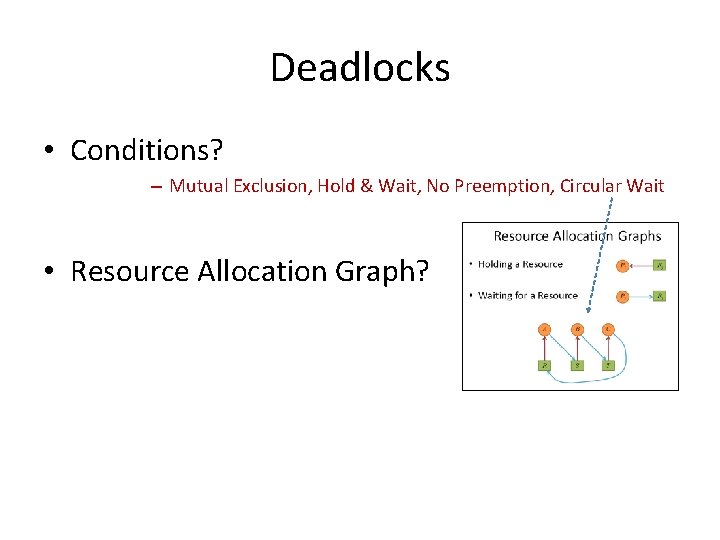
Recap • Deadlock? • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph?

Recap • Deadlock? • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph?

Recap • Deadlock? • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph?


• Same programs, different execution scenarios

Now… What to do? • Possible Strategies – Ignore! – Detection and Recovery – Deadlock Avoidance (dynamically) – Deadlock Prevention (statically)

Now… What to do? • Possible Strategies – Ignore! – Detection and Recovery – Deadlock Avoidance (dynamically) – Deadlock Prevention (statically)

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

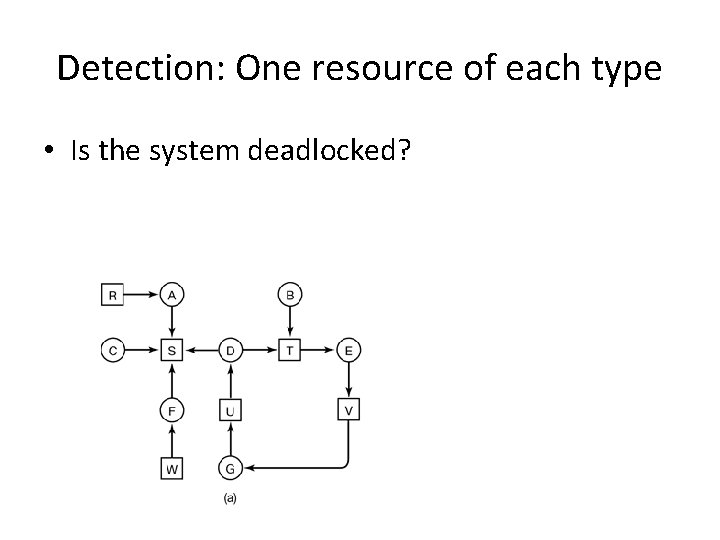
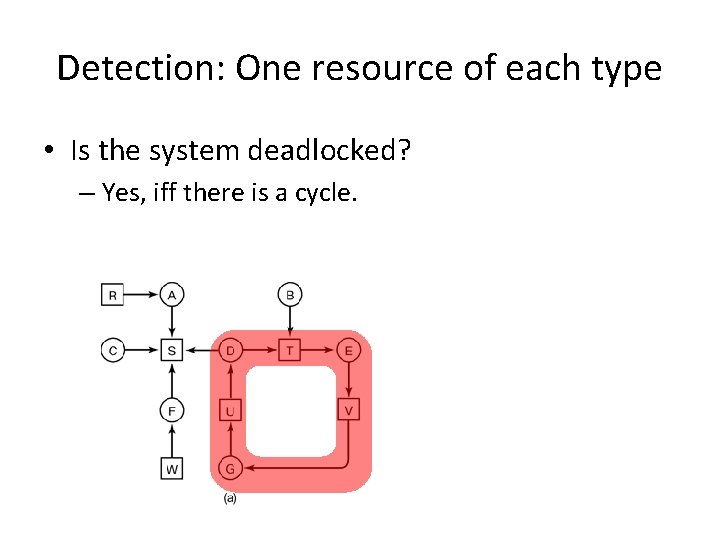
Detection: One resource of each type • Is the system deadlocked?

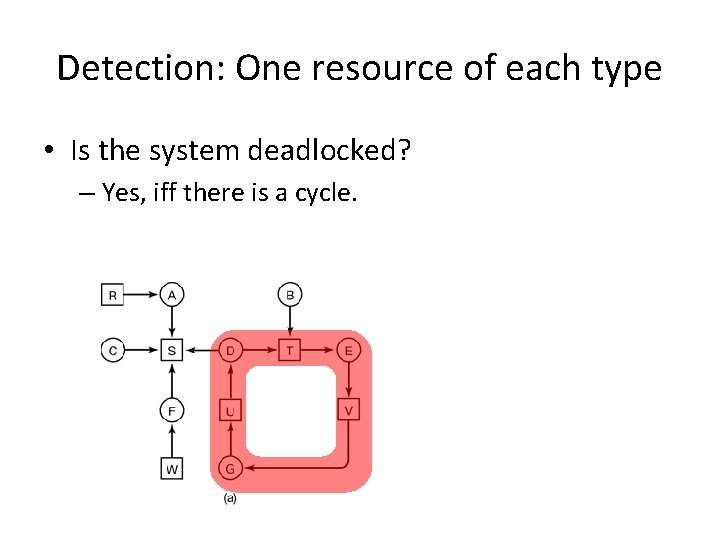
Detection: One resource of each type • Is the system deadlocked? – Yes, iff there is a cycle.

Detection: One resource of each type • Is the system deadlocked? – Yes, iff there is a cycle.

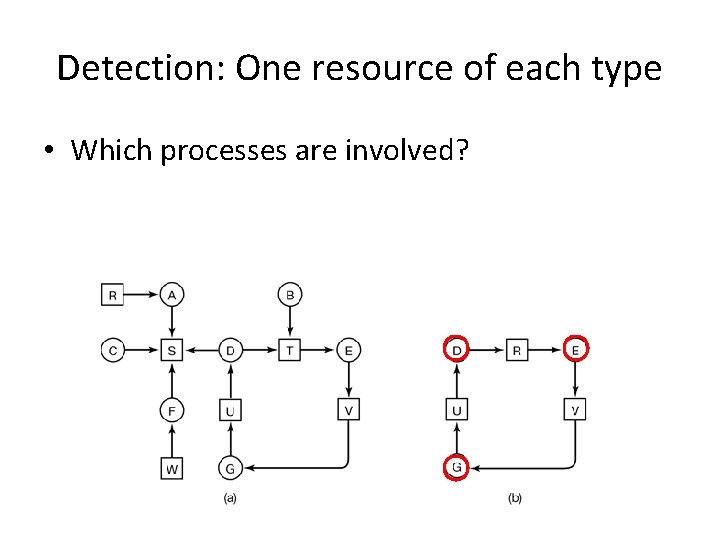
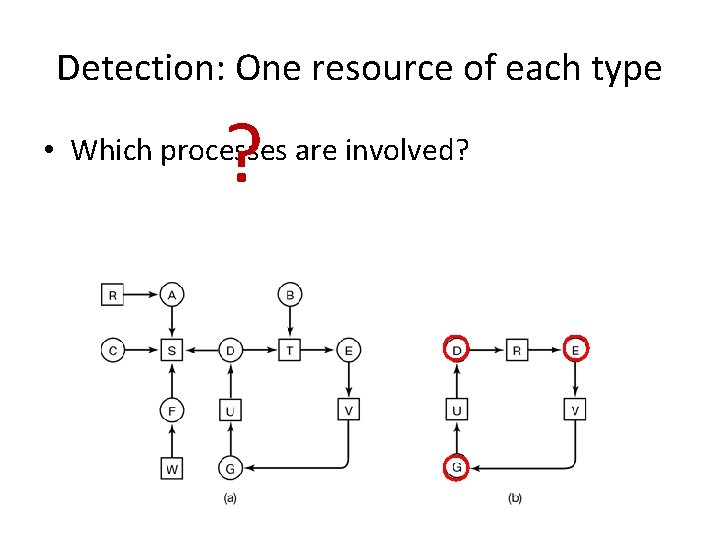
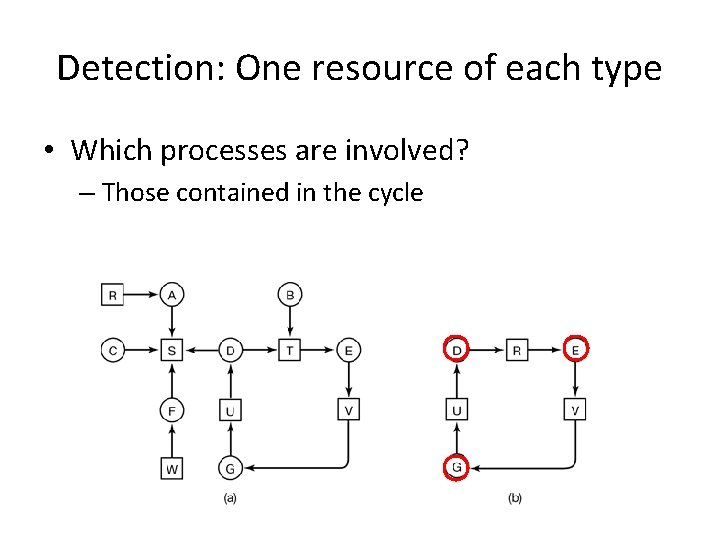
Detection: One resource of each type • Which processes are involved?

Detection: One resource of each type ? • Which processes are involved?

Detection: One resource of each type • Which processes are involved? – Those contained in the cycle

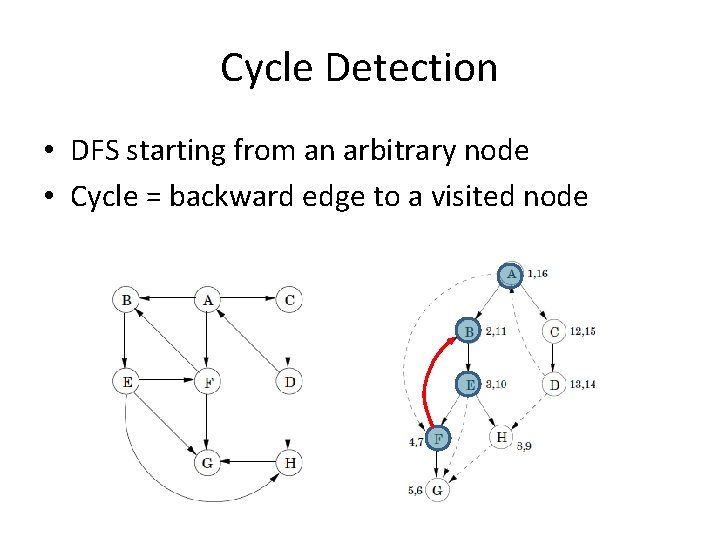
Cycle Detection

Cycle Detection ?

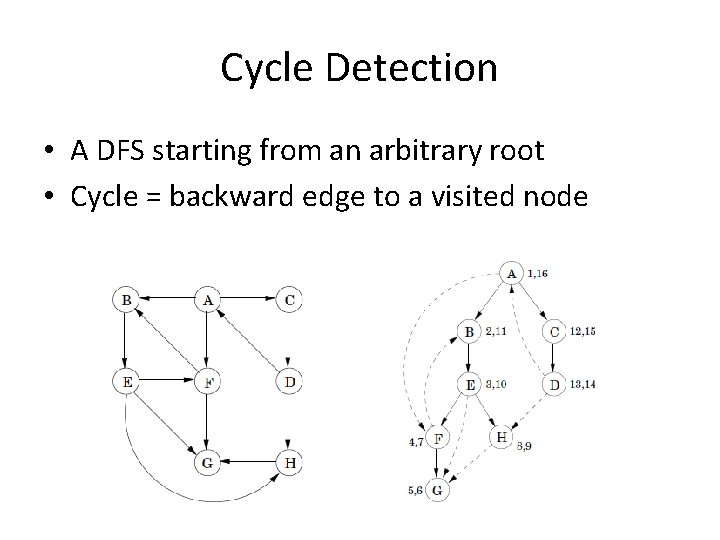
Cycle Detection • A DFS starting from an arbitrary root • Cycle = backward edge to a visited node

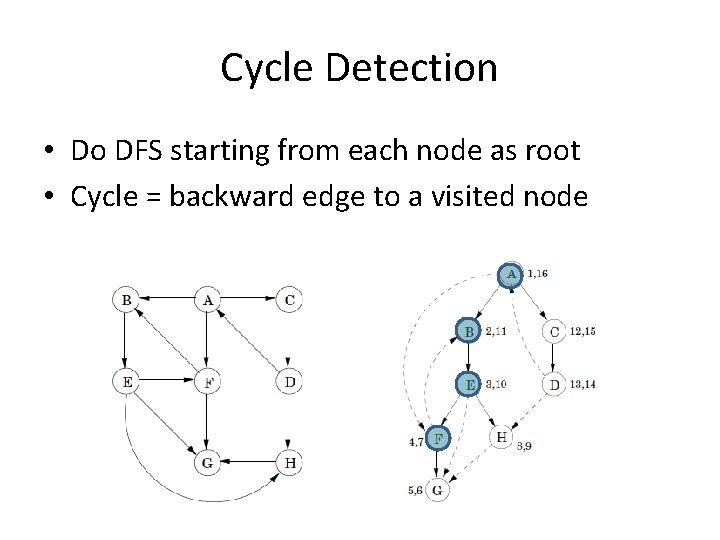
Cycle Detection • Do DFS starting from each node as root • Cycle = backward edge to a visited node

Cycle Detection • DFS starting from an arbitrary node • Cycle = backward edge to a visited node

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

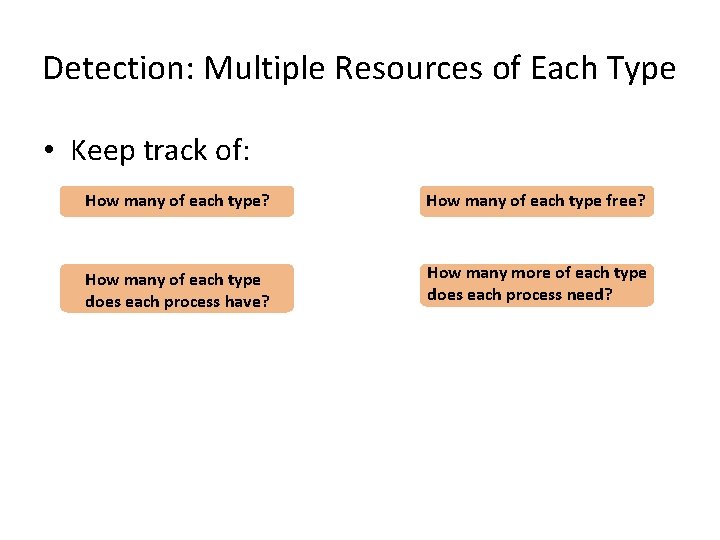
Detection: Multiple Resources of Each Type • Keep track of: How many of each type? How many of each type free? How many of each type does each process have? How many more of each type does each process need?

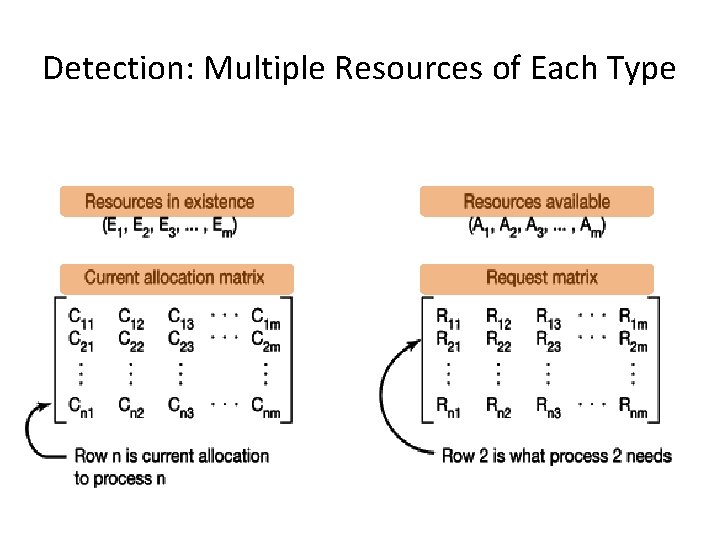
Detection: Multiple Resources of Each Type

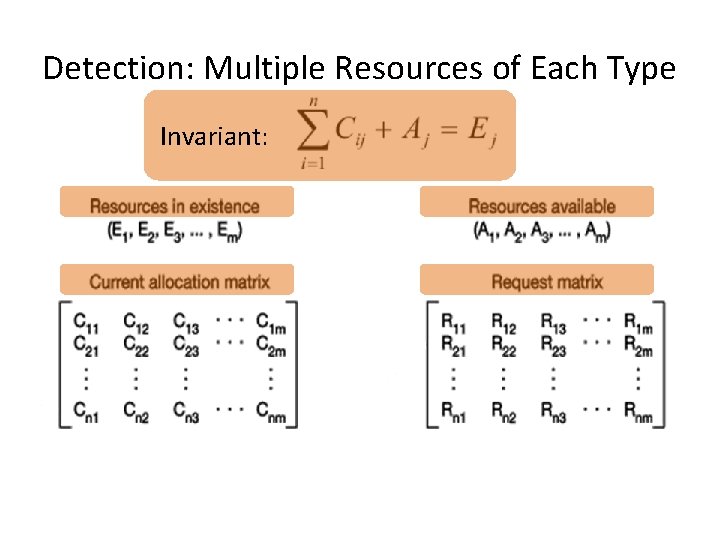
Detection: Multiple Resources of Each Type Invariant:

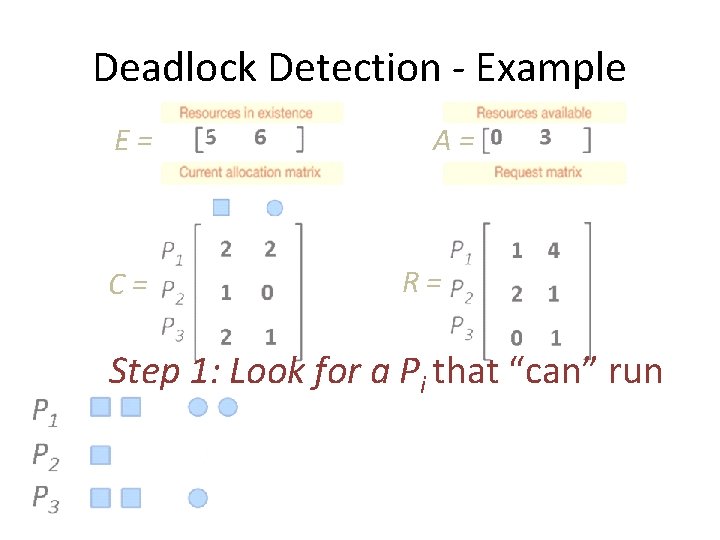
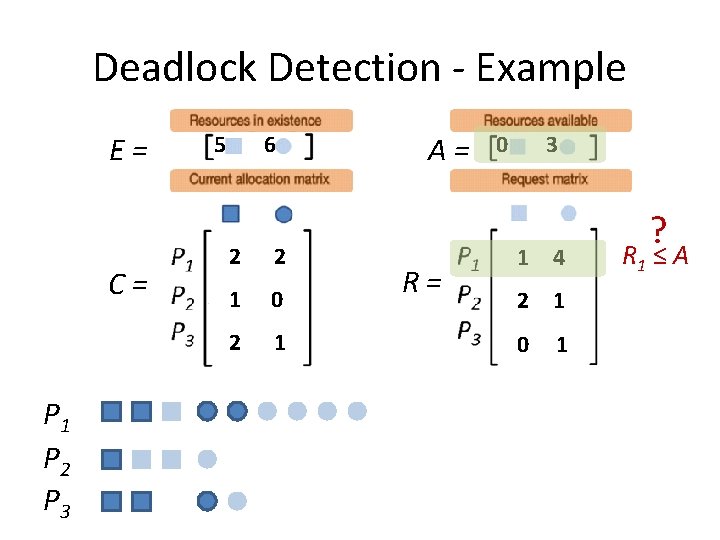
Detection: Multiple Resources of Each Type • Look for a Pi s. t. Ri ≤ A. – Pi can run. • If such a process is found, add Ci to A – It’s like Pi runs and terminates. • Repeat until no such process exists.

Detection: Multiple Resources of Each Type • Look for a Pi s. t. Ri ≤ A. – Pi can run. • If such a process is found, add Ci to A – It’s like Pi runs and terminates. • Repeat until no such process exists.

Detection: Multiple Resources of Each Type • Look for a Pi s. t. Ri ≤ A. – Pi can run. • If such a process is found, add Ci to A – It’s like Pi runs and terminates. • Repeat until no such process exists.

Detection: Multiple Resources of Each Type • Look for a Pi s. t. Ri ≤ A. – Pi can run. • If such a process is found, add Ci to A – It’s like Pi runs and terminates. • Repeat until no such process exists.

Detection: Multiple Resources of Each Type • Look for a Pi s. t. Ri ≤ A. – Pi can run. • If such a process is found, add Ci to A – It’s like Pi runs and terminates. • Repeat until no such process exists.

Detection: Multiple Resources of Each Type • Look for a Pi s. t. Ri ≤ A. – Pi can run. • If such a process is found, add Ci to A – It’s like Pi runs and terminates. • Repeat until no such process exists. • Are all the processes chosen? Iff no, deadlock.

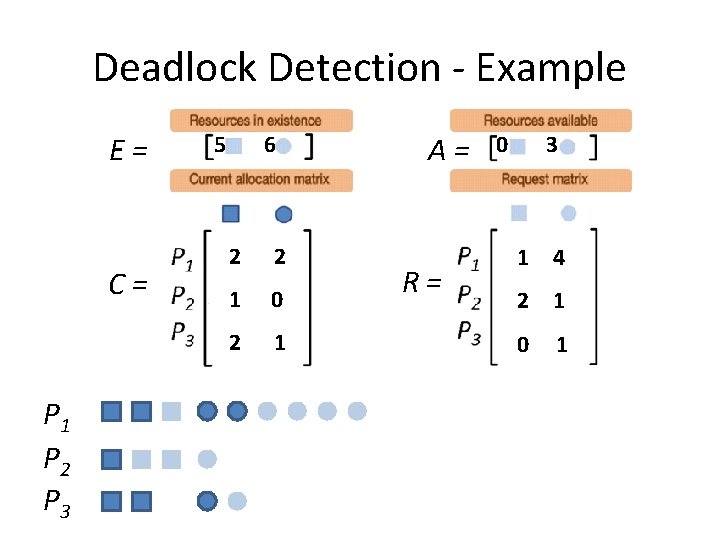
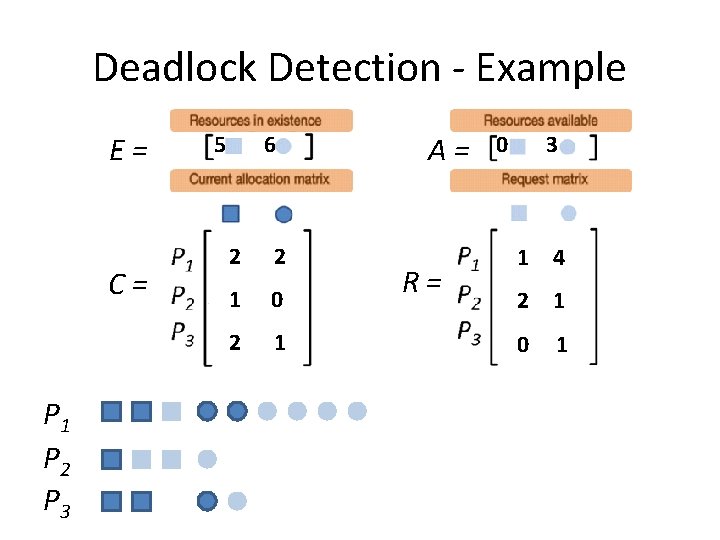
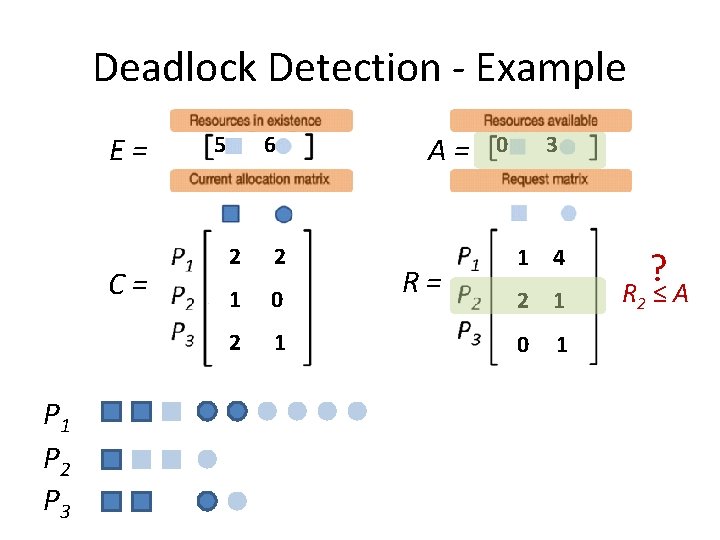
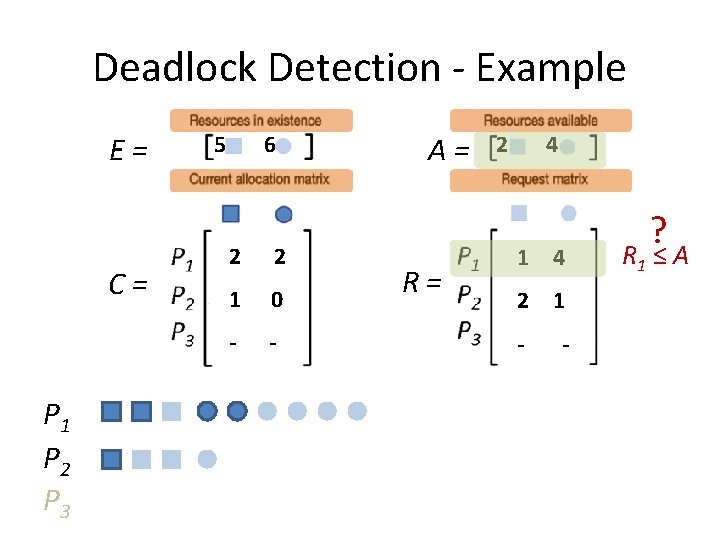
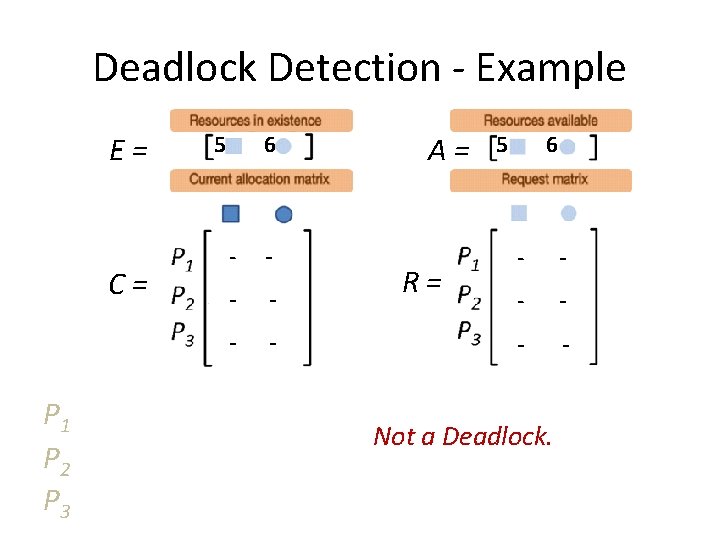
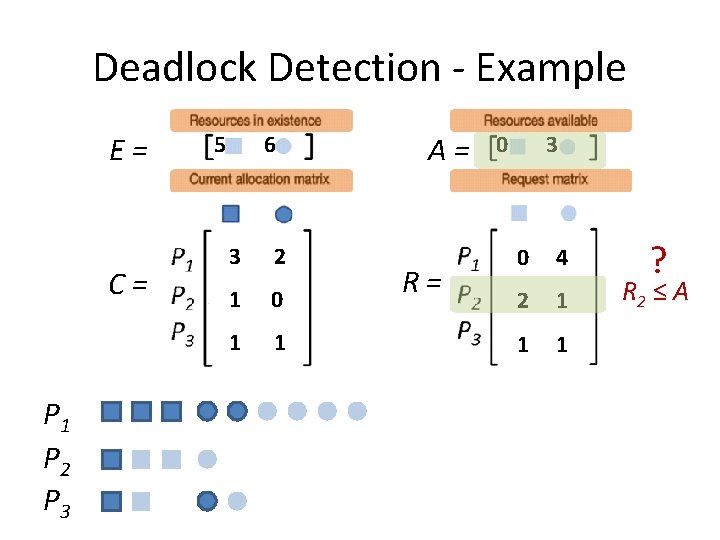
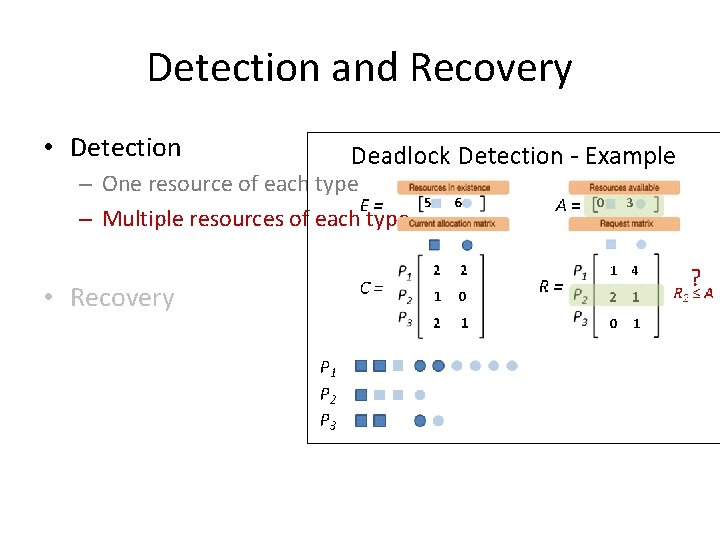
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1

Deadlock Detection - Example E= C= A= R= Step 1: Look for a Pi that “can” run

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1

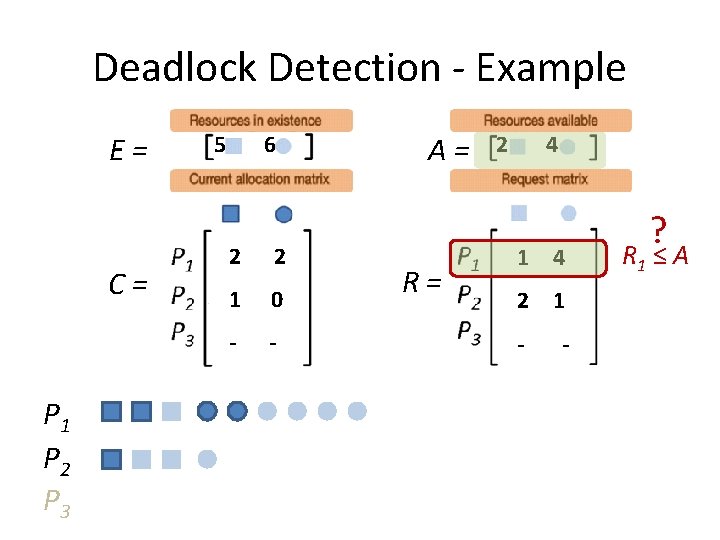
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1 ? R 1 ≤ A

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1 ? R 2 ≤ A

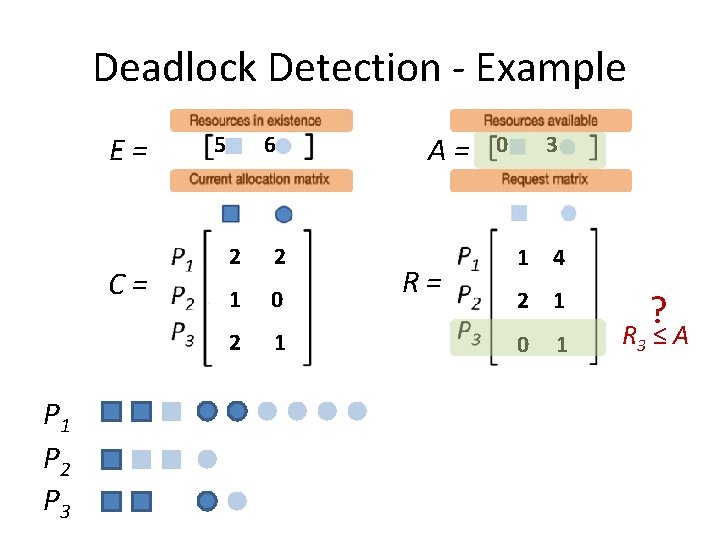
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1 ? R 3 ≤ A

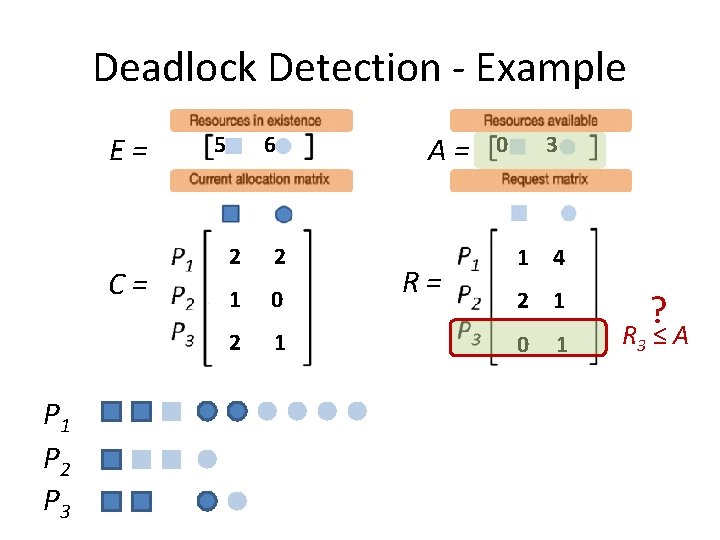
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1 ? R 3 ≤ A

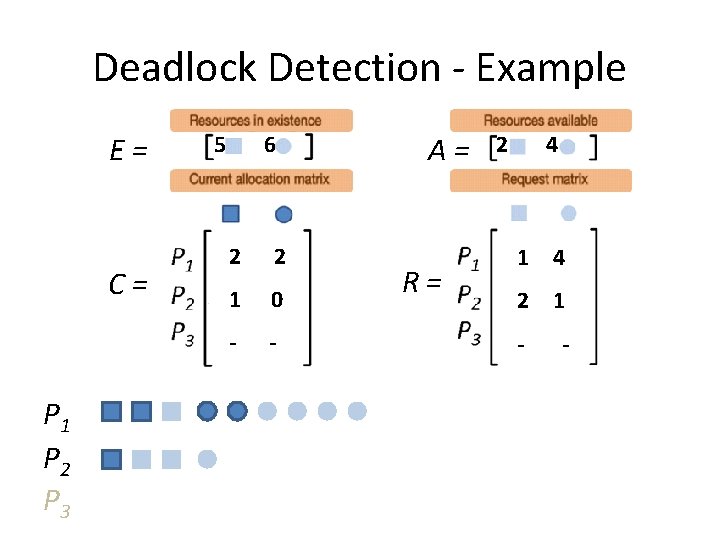
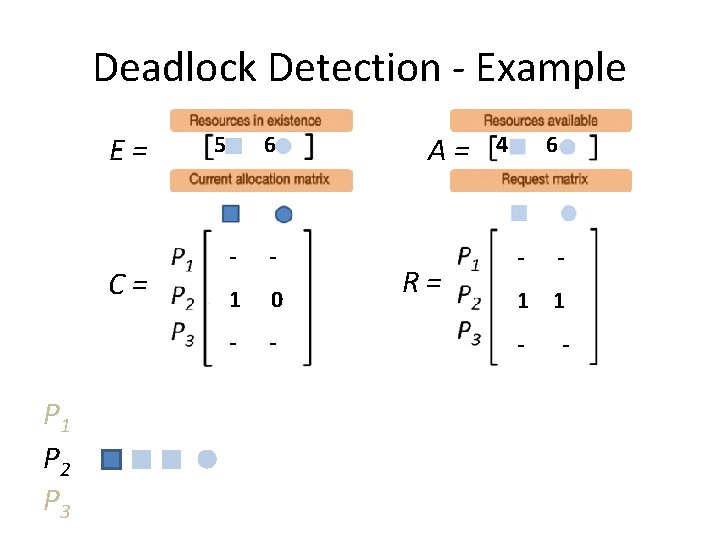
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 - - A= R= 2 4 1 4 2 1 - -

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 - - A= R= 2 4 1 4 2 1 - - ? R 1 ≤ A

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 - - A= R= 2 4 1 4 2 1 - - ? R 1 ≤ A

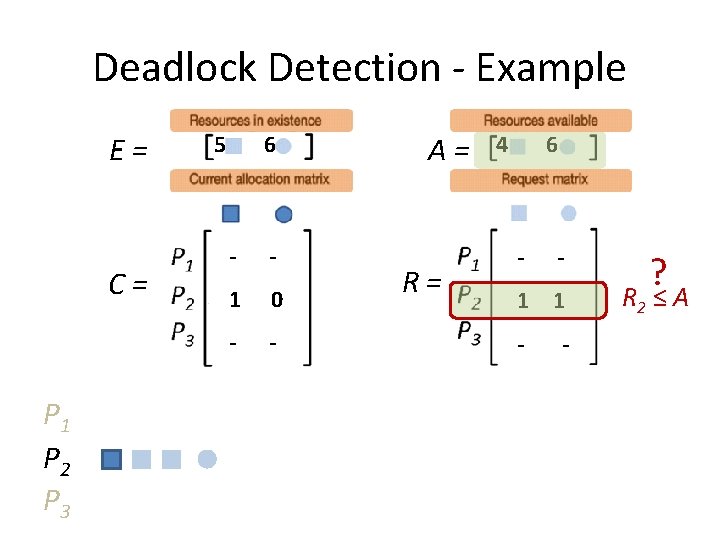
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 - - 1 0 - - A= R= 4 6 - - 1 1 - -

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 - - 1 0 - - A= R= 4 6 - - 1 1 - - ? R 2 ≤ A

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 - - - A= R= 5 6 - - - Not a Deadlock.

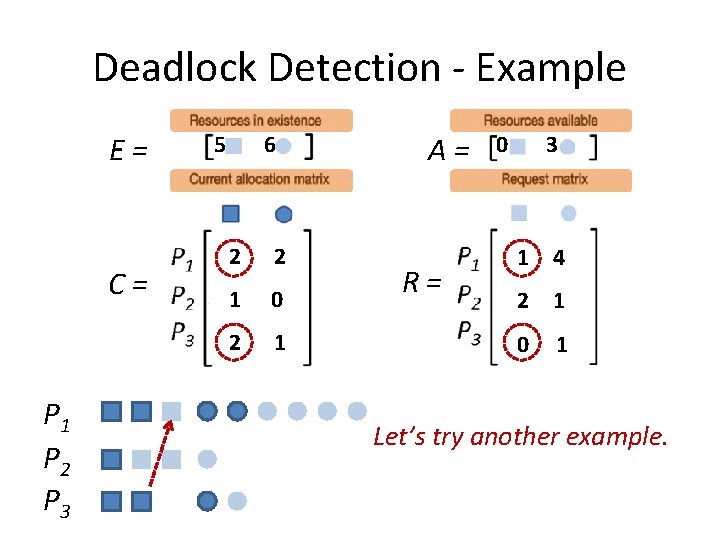
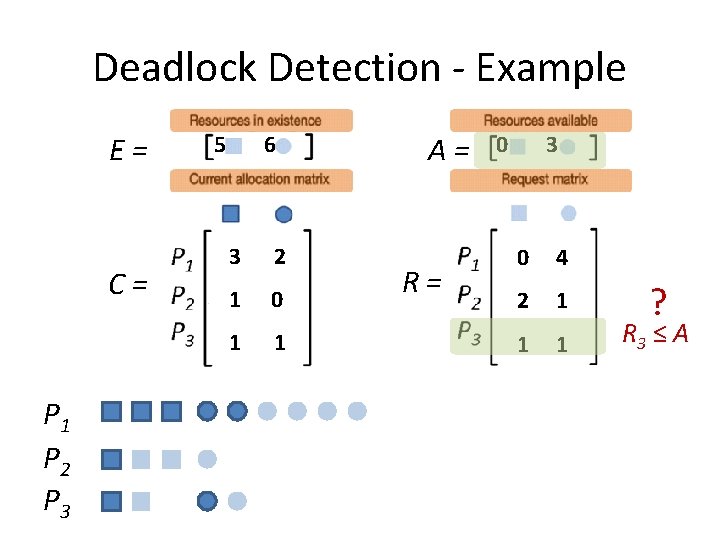
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 2 2 1 0 2 1 A= R= 0 3 1 4 2 1 0 1 Let’s try another example.

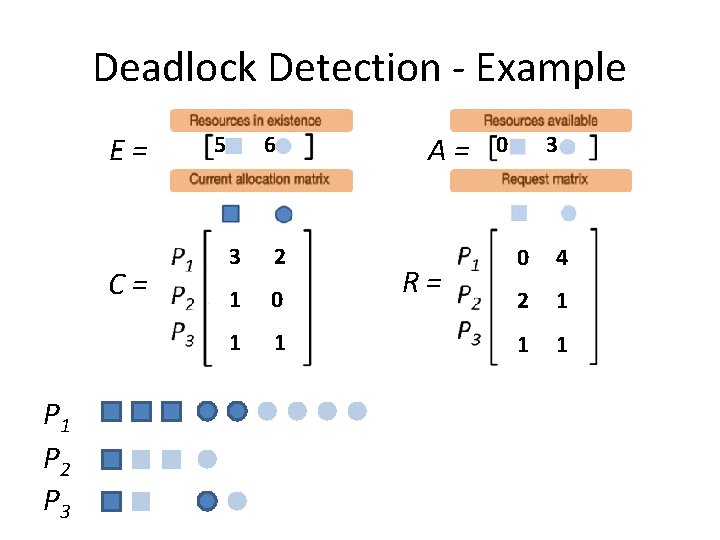
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 3 2 1 0 1 1 A= R= 0 3 0 4 2 1 1 1

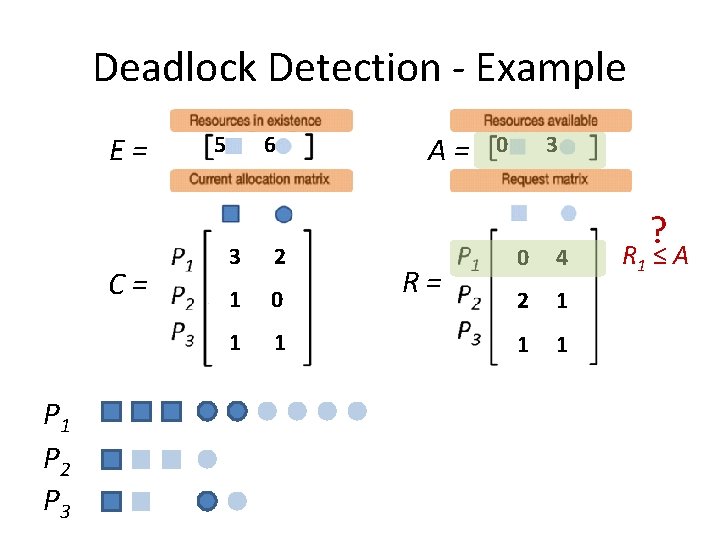
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 3 2 1 0 1 1 A= R= 0 3 0 4 2 1 1 1 ? R 1 ≤ A

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 3 2 1 0 1 1 A= R= 0 3 0 4 2 1 1 1 ? R 2 ≤ A

Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 3 2 1 0 1 1 A= R= 0 3 0 4 2 1 1 1 ? R 3 ≤ A

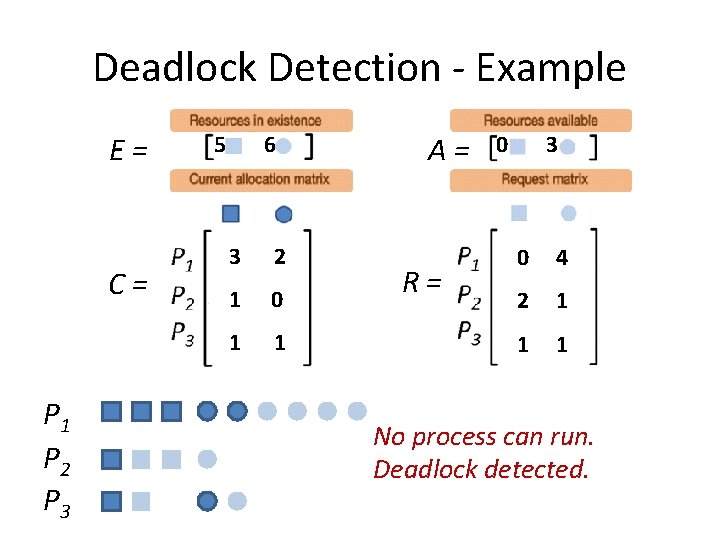
Deadlock Detection - Example E= C= P 1 P 2 P 3 5 6 3 2 1 0 1 1 A= R= 0 3 0 4 2 1 1 1 No process can run. Deadlock detected.

Deadlock Detection • We know how to check for a deadlock situation. • But when to check?

Deadlock Detection • We know how to detect a deadlock situation. • But when to check? – Upon each resource request – Every k minutes – When CPU utilization drops

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

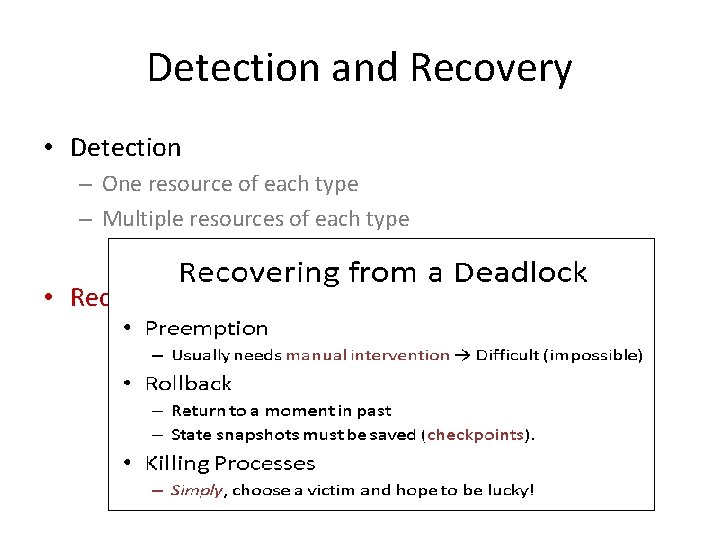
Recovering from a Deadlock • Preemption – Usually needs manual intervention → Difficult (impossible) • Rollback – Return to a moment in past – State snapshots must be saved (checkpoints). • Killing Processes – Simply, choose a victim and hope to be lucky!

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery • We assumed we have prior knowledge of all resource requirements.

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery • We assumed we have prior knowledge of all resource requirements. Not a realistic assumption!

Now… What to do? • Possible Strategies – Ignore! – Detection and Recovery – Deadlock Avoidance (dynamically) – Deadlock Prevention (statically)

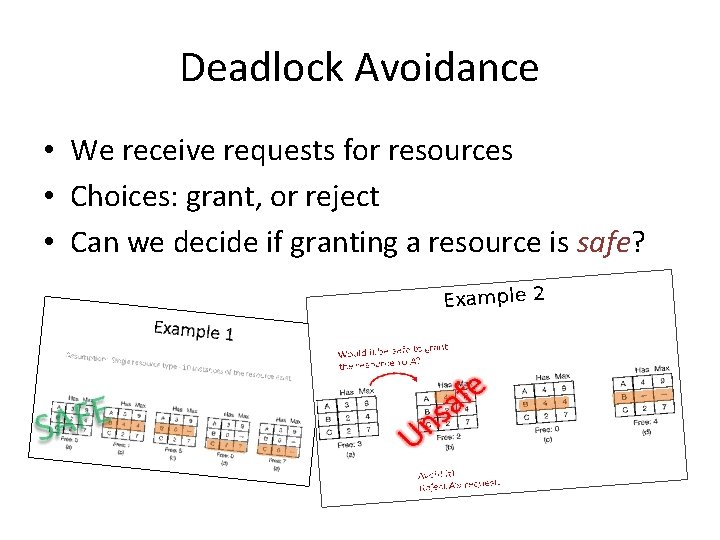
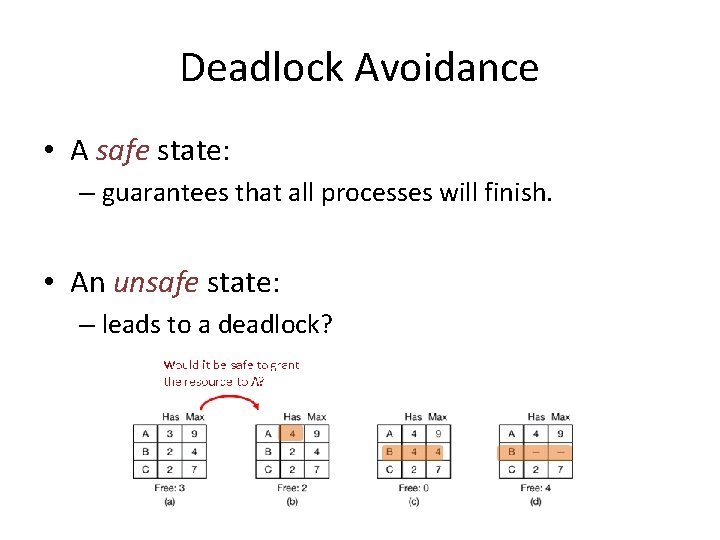
Deadlock Avoidance • We receive requests for resources • Choices: grant, or reject • Can we decide if granting a resource is safe?

Deadlock Avoidance • Examine E, A, C, and R. • A state is said to be safe if – It is not deadlocked – There is some scheduling order in which every process can run to completion even if all of them request their maximum number of resources immediately.

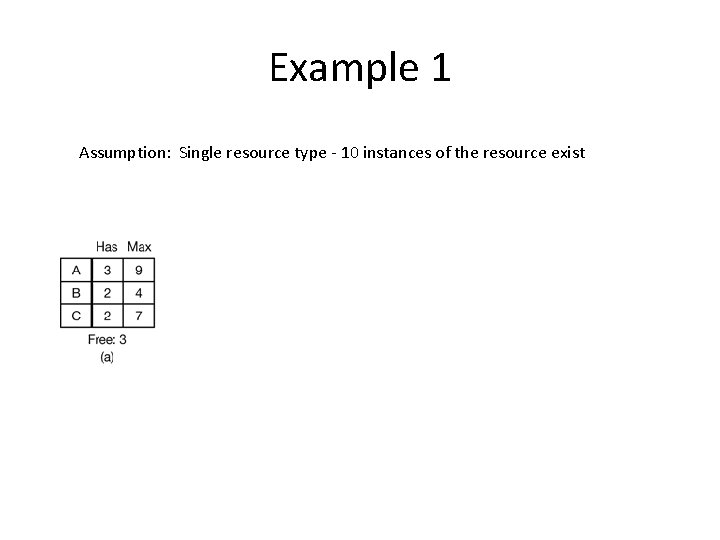
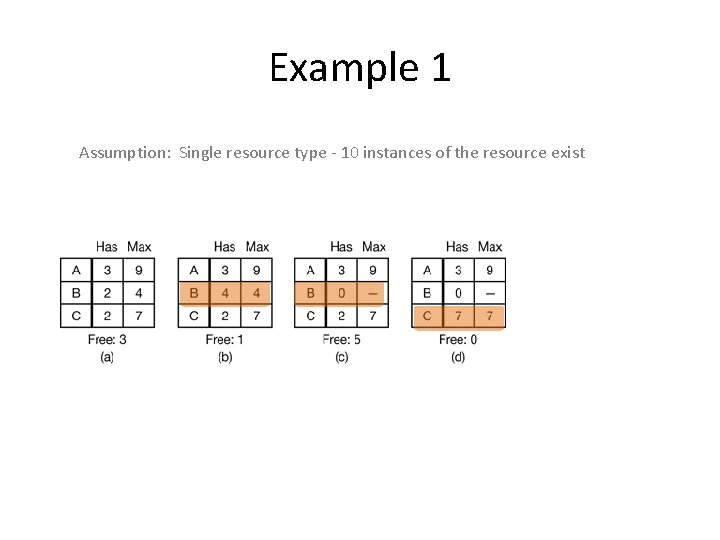
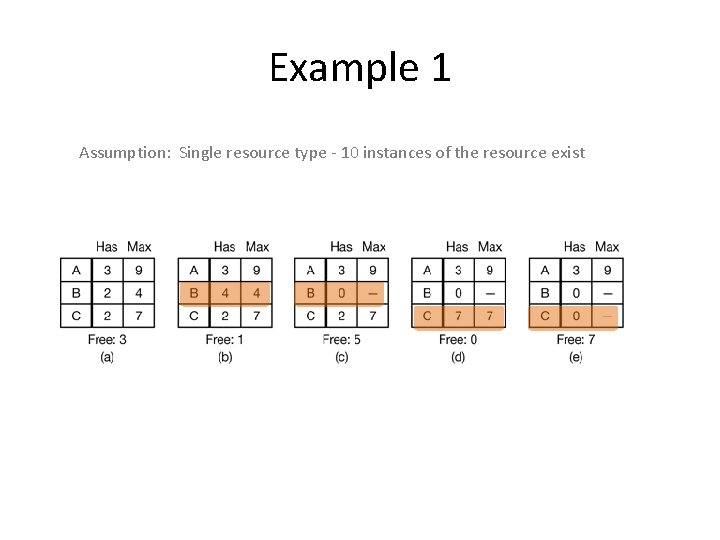
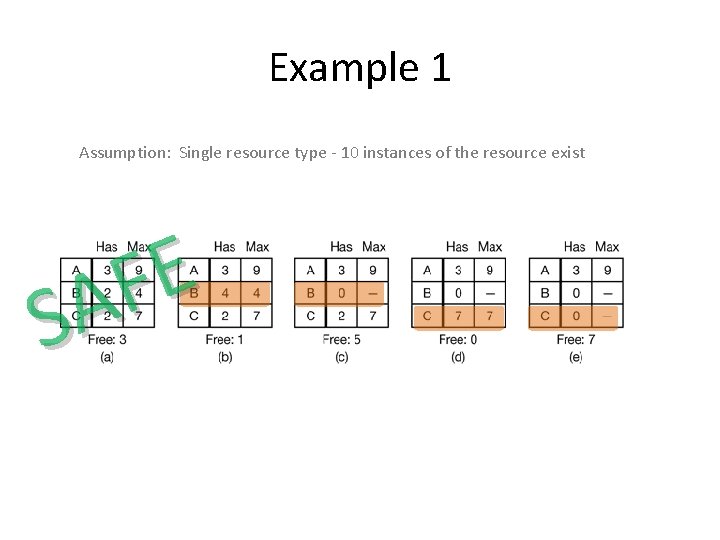
Example 1 Assumption: Single resource type - 10 instances of the resource exist

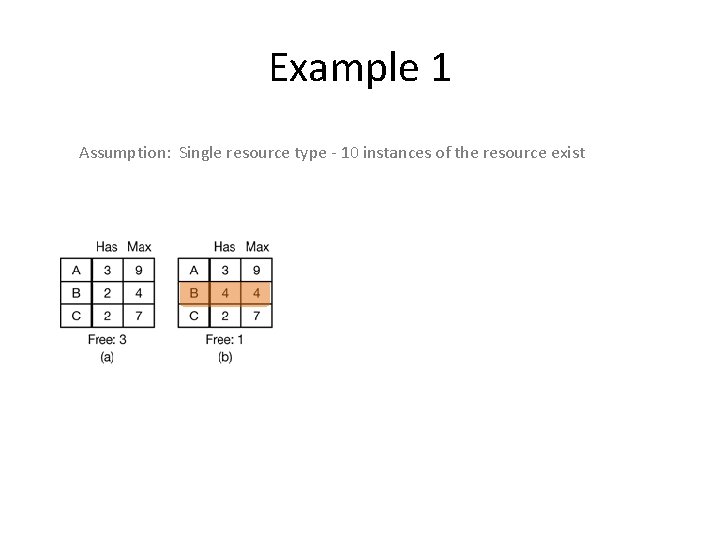
Example 1 Assumption: Single resource type - 10 instances of the resource exist

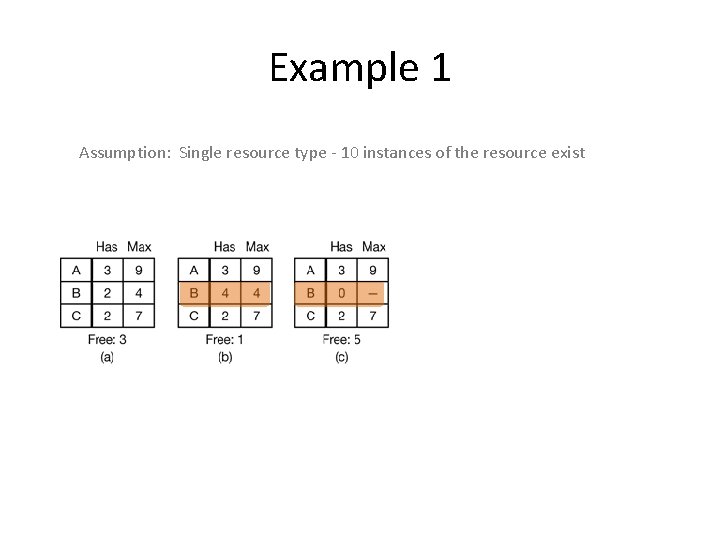
Example 1 Assumption: Single resource type - 10 instances of the resource exist

Example 1 Assumption: Single resource type - 10 instances of the resource exist

Example 1 Assumption: Single resource type - 10 instances of the resource exist

Example 1 Assumption: Single resource type - 10 instances of the resource exist E F A S

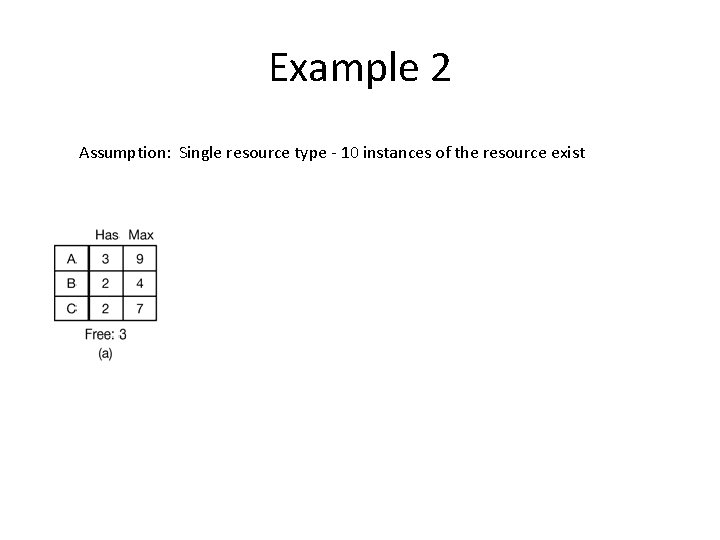
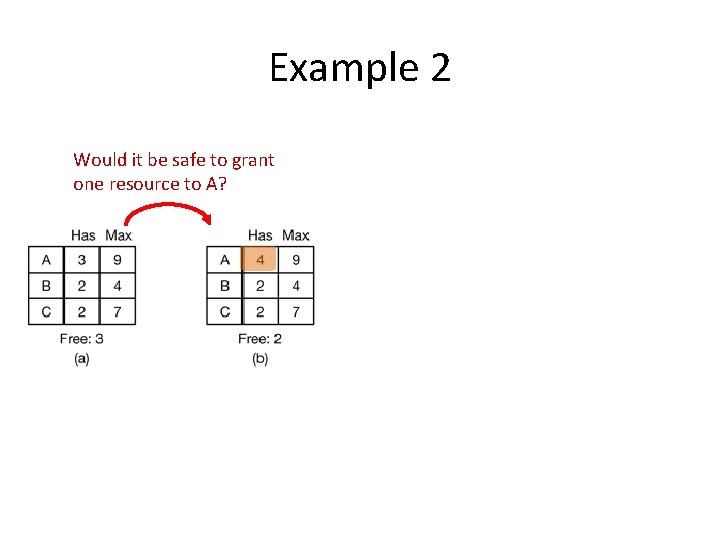
Example 2 Assumption: Single resource type - 10 instances of the resource exist

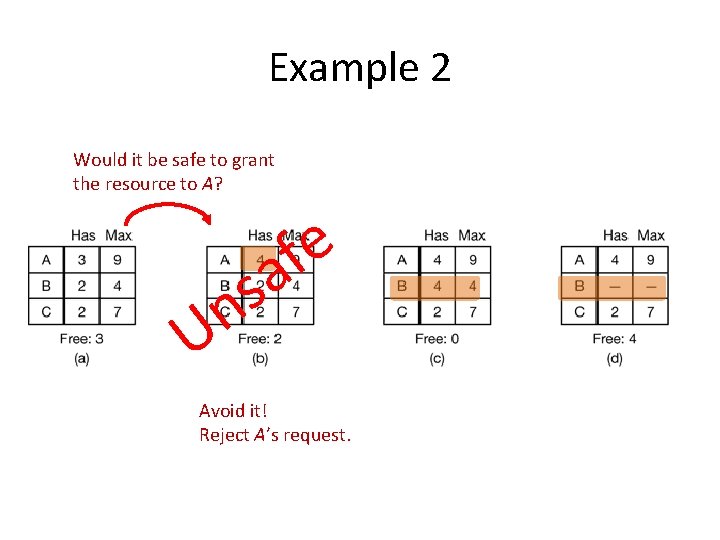
Example 2 Would it be safe to grant one resource to A?

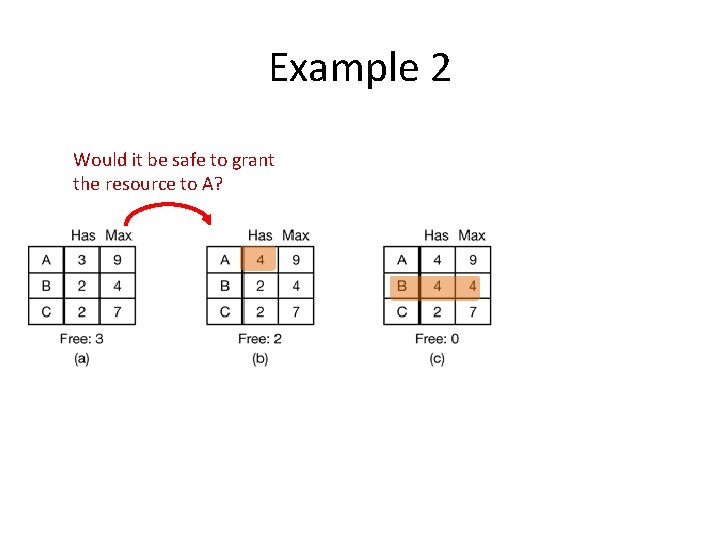
Example 2 Would it be safe to grant the resource to A?

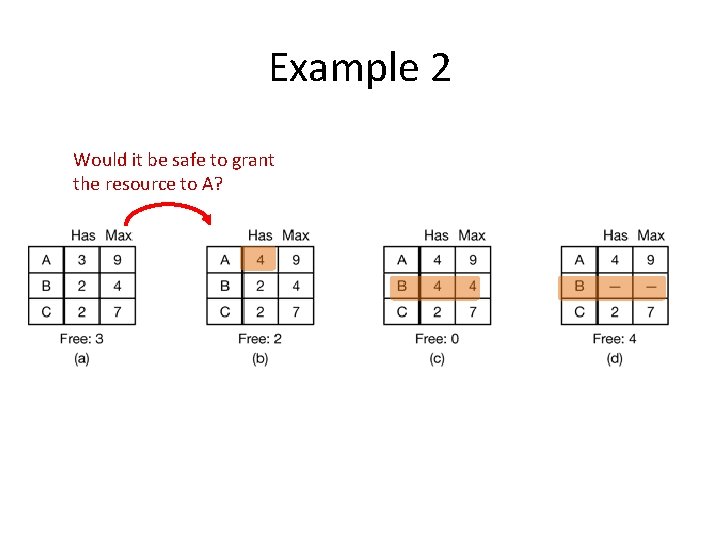
Example 2 Would it be safe to grant the resource to A?

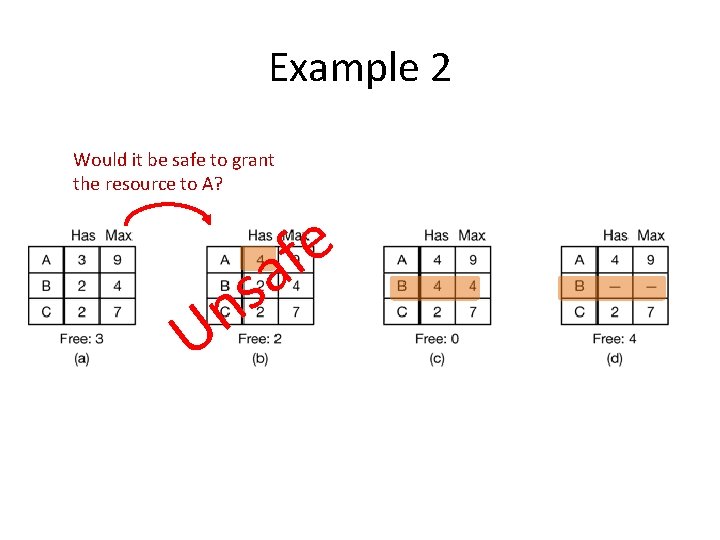
Example 2 Would it be safe to grant the resource to A? U s n e f a

Example 2 Would it be safe to grant the resource to A? e f a s n U Avoid it! Reject A’s request.

Deadlock Avoidance • A safe state: – guarantees that all processes will finish. • An unsafe state: – leads to a deadlock?

Deadlocks • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait

Deadlocks • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait

Deadlocks • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph?

Deadlocks • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph?

Deadlocks • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph? • Solutions? – – Ignore Detection and recovery Avoidance (Dynamic) Prevention (Static)

Deadlocks • Conditions? – Mutual Exclusion, Hold & Wait, No Preemption, Circular Wait • Resource Allocation Graph? • Solutions? – – Ignore Detection and recovery Avoidance (Dynamic) Prevention (Static)

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

Detection and Recovery • Detection – One resource of each type – Multiple resources of each type • Recovery

Deadlock Avoidance • We receive requests for resources • Choices: grant, or reject • Can we decide if granting a resource is safe?


Does an unsafe state always lead to a deadlock?

Deadlock Avoidance • A safe state: – guarantees that all processes will finish. • An unsafe state: – leads to a deadlock?

Banker’s Algorithm • Upon receiving a resource request: • Determine whether granting leads to a safe or unsafe state: – If safe , grant the resource. – If unsafe, reject the request. • Remark. We use the same algorithms described in the deadlock detection (single/multiple resource types).

Banker’s Algorithm • Upon receiving a resource request: • Determine whether granting leads to a safe or unsafe state: – If safe , grant the resource. – If unsafe, reject the request. • Remark. We use the same algorithms described in the deadlock detection (single/multiple resource types).

Now… What to do? • Possible Strategies – Ignore! – Detection and Recovery – Deadlock Avoidance (dynamically) – Deadlock Prevention (statically)

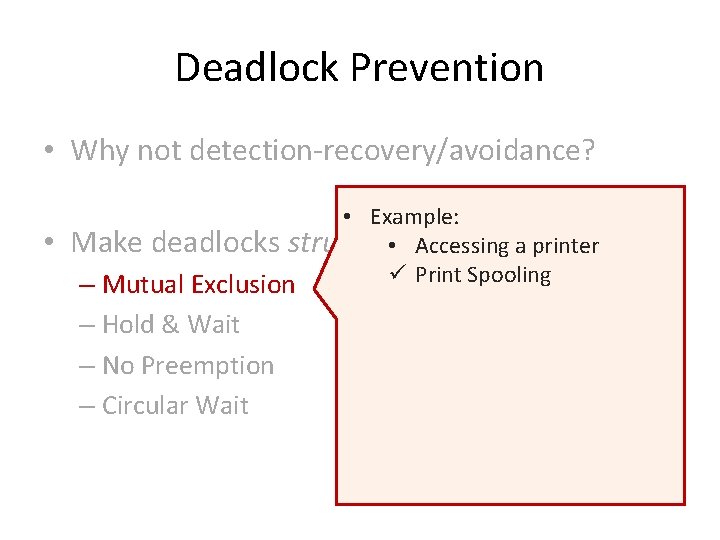
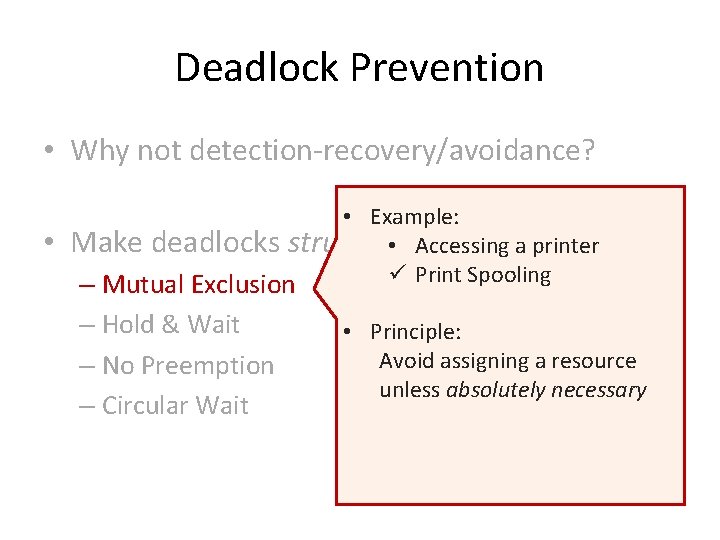
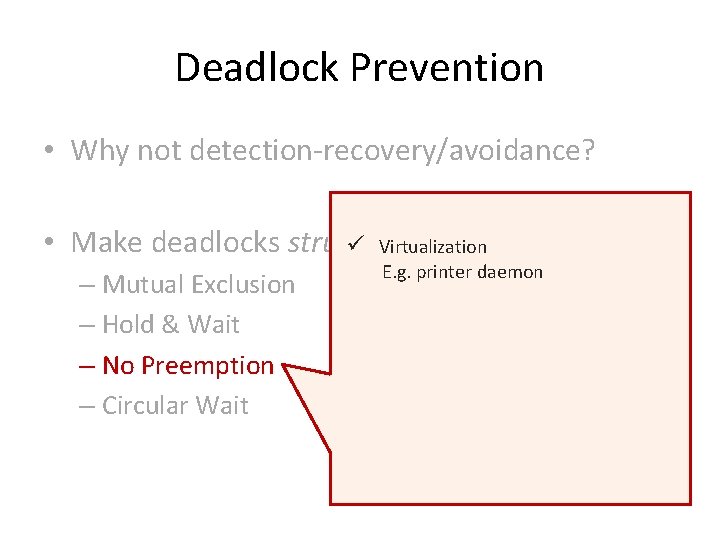
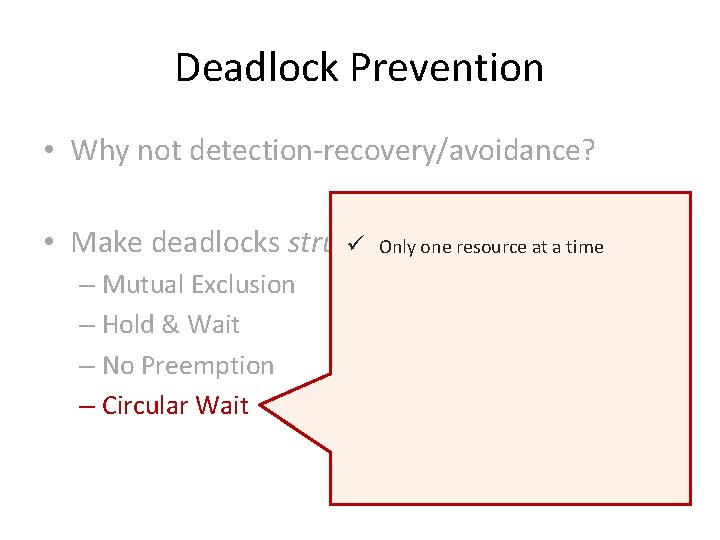
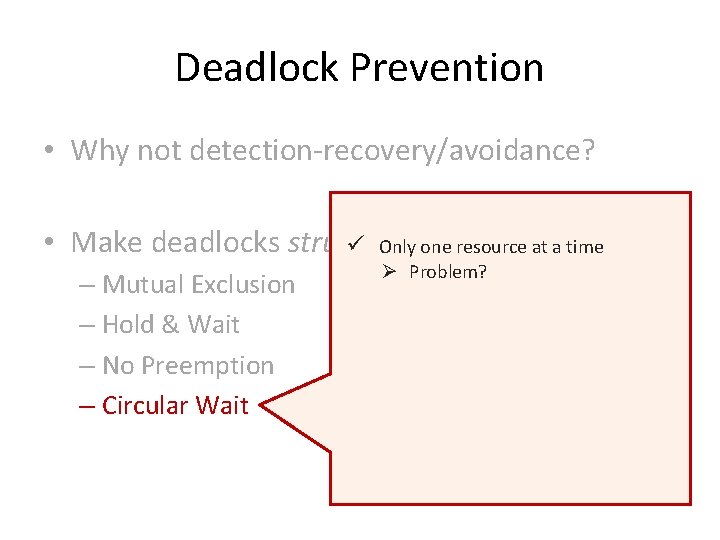
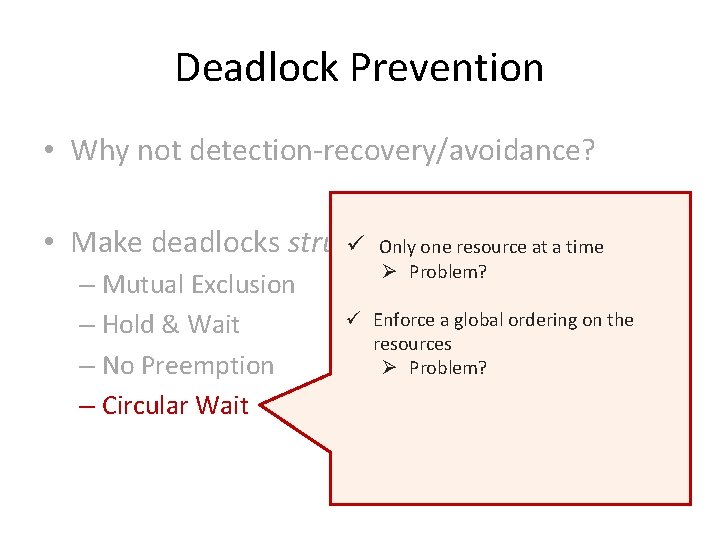
Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally impossible

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally impossible – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait

Deadlock Prevention • Why not detection-recovery/avoidance? • • Example: Make deadlocks structurally impossible • Accessing a printer ü Print Spooling – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait

Deadlock Prevention • Why not detection-recovery/avoidance? • • Example: Make deadlocks structurally impossible • Accessing a printer ü Print Spooling – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait • Principle: Avoid assigning a resource unless absolutely necessary

Deadlock Prevention • Why not detection-recovery/avoidance? Do not hold & wait! • Make deadlocks structurally impossible – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks Do not hold & wait! structurally ü Requestimpossible all the resources in the – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait beginning.

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks Do not hold & wait! structurally ü Requestimpossible all the resources in the – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait beginning. Ø Problems?

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks Do not hold & wait! structurally ü Requestimpossible all the resources in the – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait beginning. Ø Problems? ü When issuing a request, release the previously held resources temporarily

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally impossible ü Virtualization – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait E. g. printer daemon

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally impossible ü Virtualization – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait E. g. printer daemon Ø Problems?

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally ü Only oneimpossible resource at a time – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally ü Only oneimpossible resource at a time – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait Ø Problem?

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally ü Only oneimpossible resource at a time – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait Ø Problem? ü Enforce a global ordering on the resources

Deadlock Prevention • Why not detection-recovery/avoidance? • Make deadlocks structurally ü Only oneimpossible resource at a time – Mutual Exclusion – Hold & Wait – No Preemption – Circular Wait Ø Problem? ü Enforce a global ordering on the resources Ø Problem?

Two-phase locking • In databases – Phase 1: Try locking all the required records • Success: go to phase 2 • Failure: release the acquired locks and retry – Phase 2: Do the work

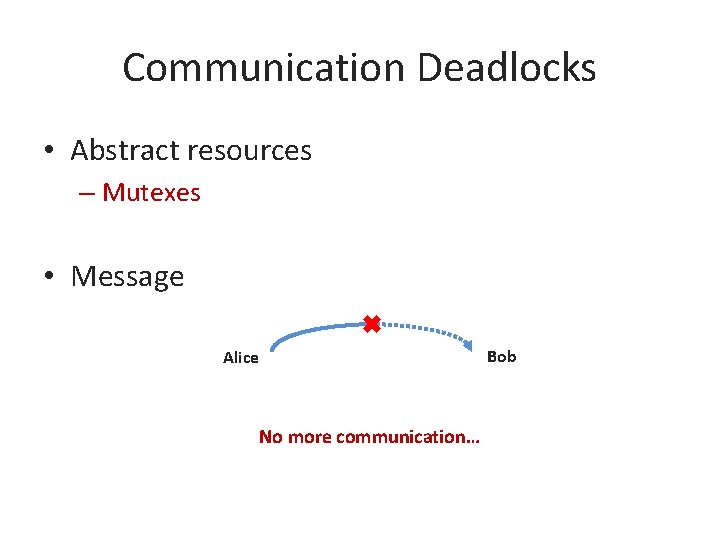
Communication Deadlocks • Abstract resources – Mutexes • Message Alice Bob

Communication Deadlocks • Abstract resources – Mutexes • Message Alice Bob

Communication Deadlocks • Abstract resources – Mutexes • Message Alice Bob

Communication Deadlocks • Abstract resources – Mutexes • Message Alice Bob

Communication Deadlocks • Abstract resources – Mutexes • Message Alice Bob

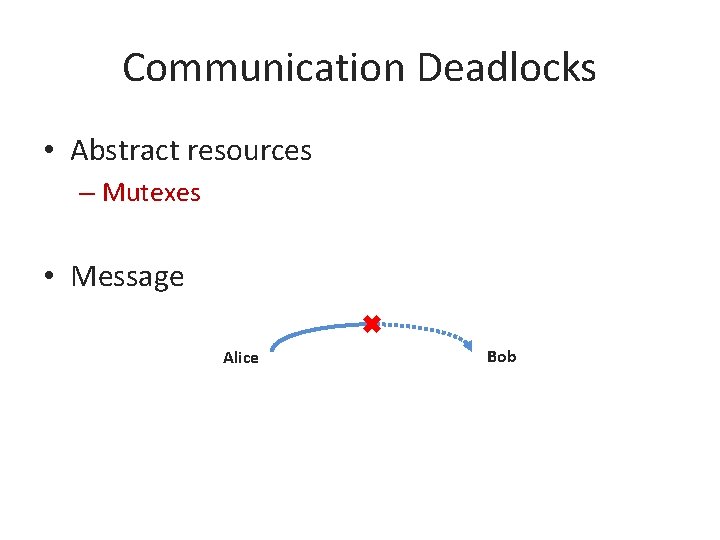
Communication Deadlocks • Abstract resources – Mutexes • Message Alice No more communication… Bob

Solution?

Livelocks • Processes are not blocked literally • Functionally equivalent to the deadlocks • Example: – Busy waiting for mutual exclusion

Starvation • Some processes never receive service due to the policy of offering the service • Example: –?

Starvation • Some processes never receive service due to the policy of offering the service • Example: – SJF: A long process and a steady stream of small processes