Datorntverk A lektion 8 Kapitel 16 Connecting LAN









- Slides: 64

Datornätverk A – lektion 8 Kapitel 16: Connecting LAN: s, Backbone Networks and Virtual Lans. (Kapitel 18: Frame Relay and ATM översiktligt)

Chapter 16 Connecting LANs, Backbone Networks, and Virtual LANs

Limitations of Ethernet Technologies • Distance (the length of the cable) ○ 200 m in Thin Ethernet (10 Base 2) ○ 100 m in twisted pair Ethernet (10 Base. T or 100 Base. T or Fast Ethernet) • Number of collisions when too many stations are connected to the same segment • The situation is similar in other LAN technologies

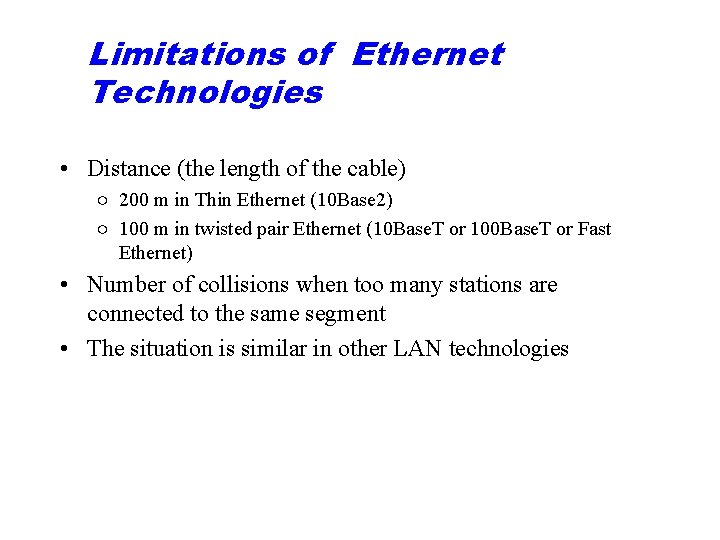
Figure 16. 2 Repeater

Note: A repeater connects segments of a LAN.

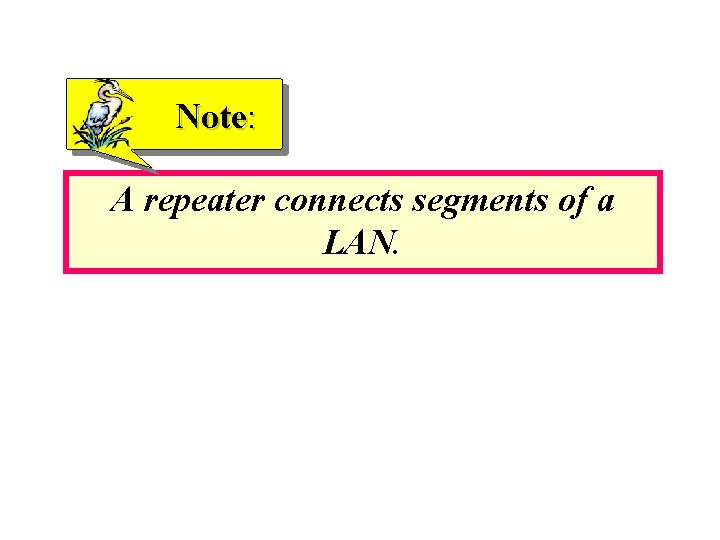
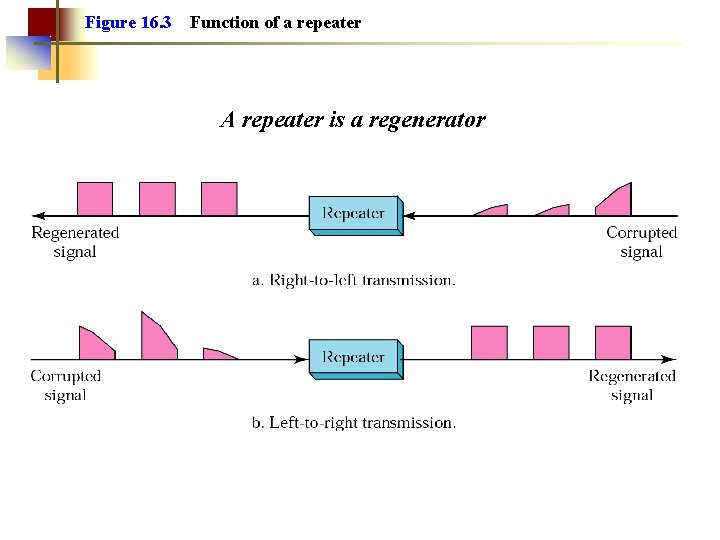
Note: A repeater forwards every frame bit-by -bit; it has no packet queues, no filtering capability and no collision detection.

Figure 16. 3 Function of a repeater A repeater is a regenerator

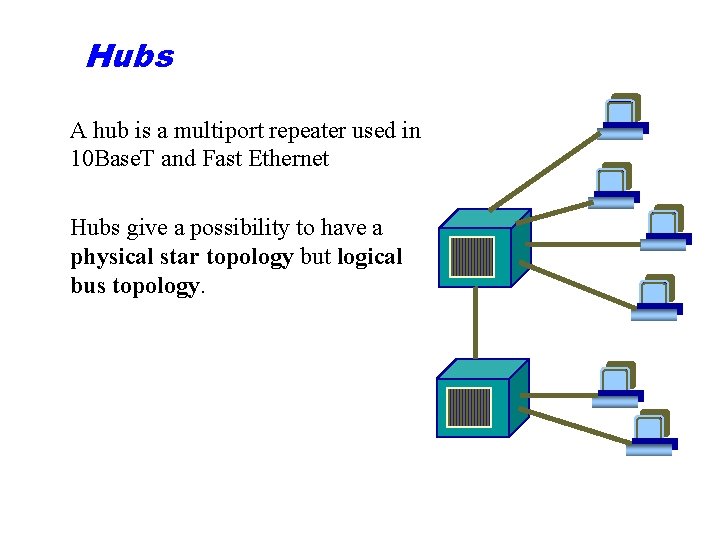
Hubs A hub is a multiport repeater used in 10 Base. T and Fast Ethernet Hubs give a possibility to have a physical star topology but logical bus topology.

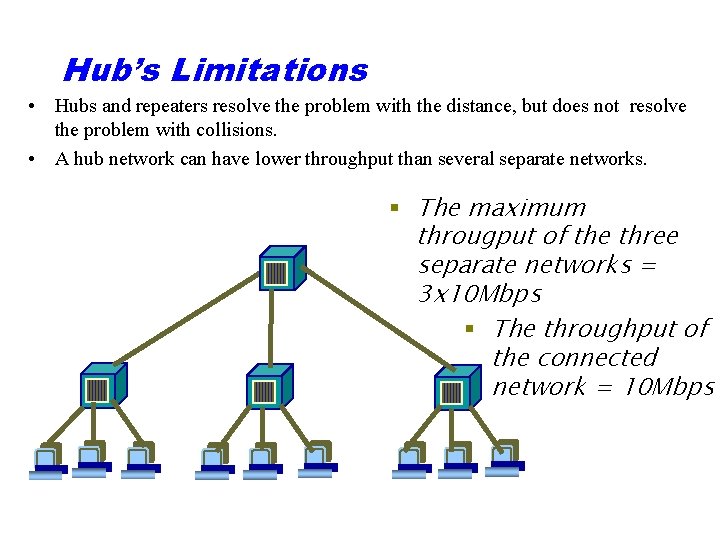
Hub’s Limitations • Hubs and repeaters resolve the problem with the distance, but does not resolve the problem with collisions. • A hub network can have lower throughput than several separate networks. § The maximum througput of the three separate networks = 3 x 10 Mbps § The throughput of the connected network = 10 Mbps

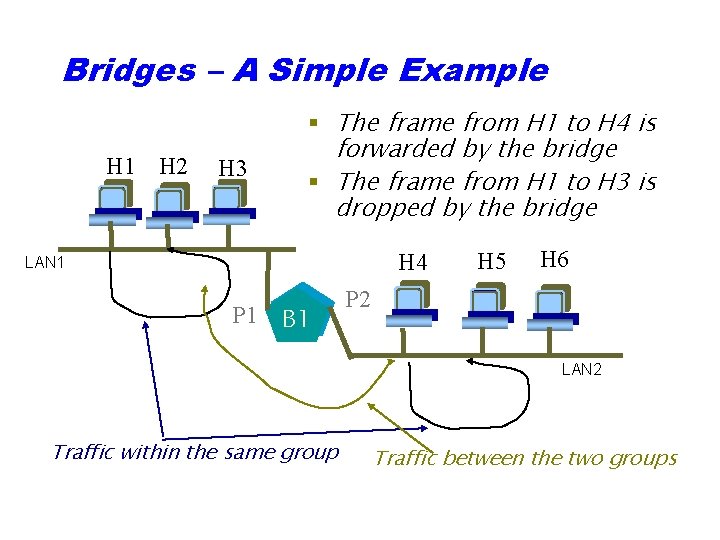
Bridges – A Simple Example H 1 H 2 H 3 § The frame from H 1 to H 4 is forwarded by the bridge § The frame from H 1 to H 3 is dropped by the bridge H 4 LAN 1 P 1 B 1 H 5 H 6 P 2 LAN 2 Traffic within the same group Traffic between the two groups

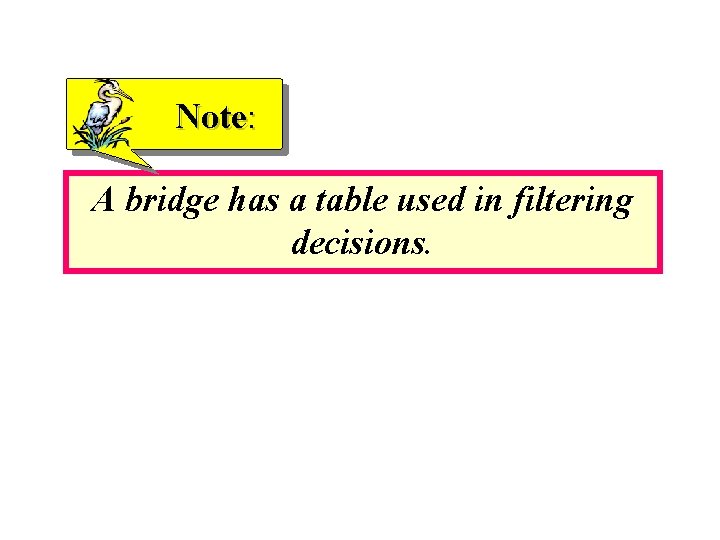
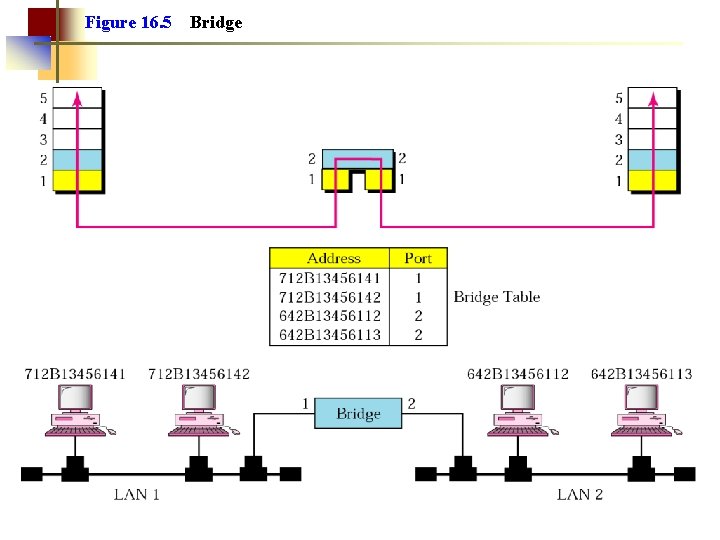
Note: A bridge has a table used in filtering decisions.

Figure 16. 5 Bridge

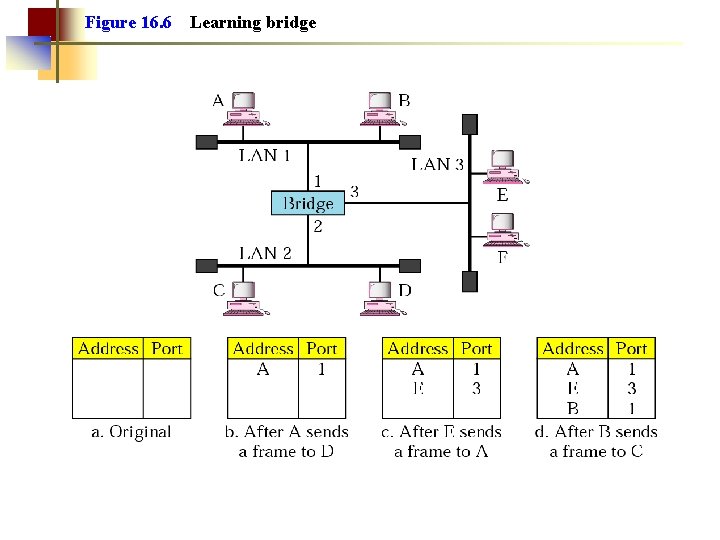
Figure 16. 6 Learning bridge

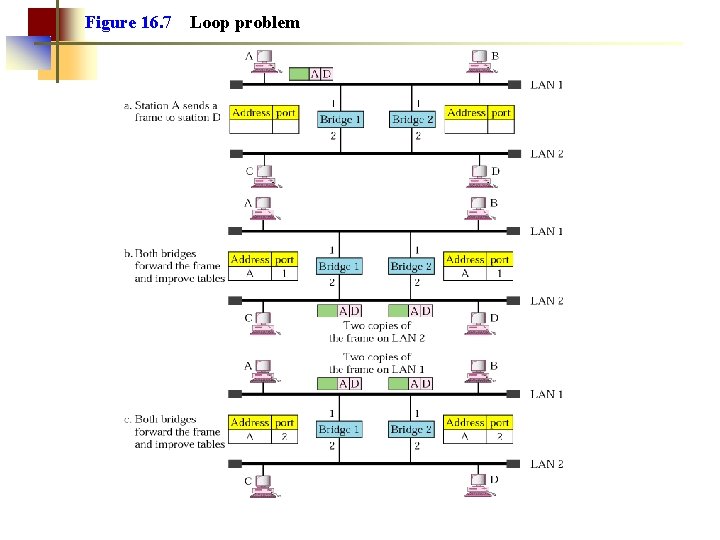
Figure 16. 7 Loop problem

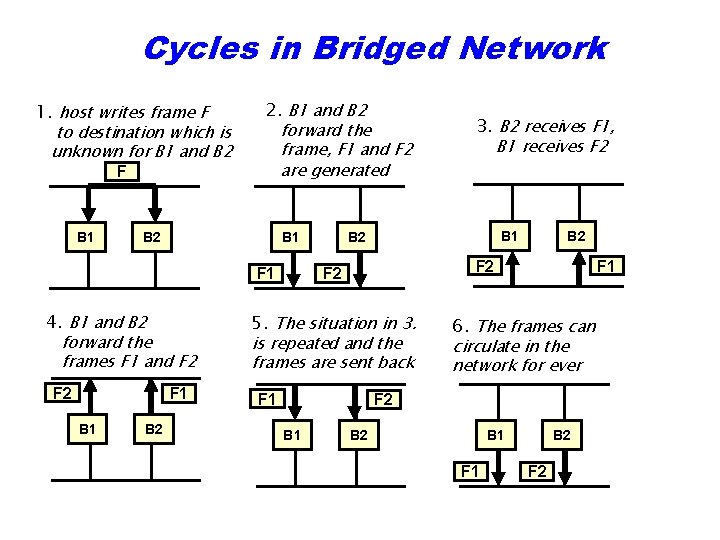
Cycles in Bridged Network 1. host writes frame F to destination which is unknown for B 1 and B 2 2. B 1 and B 2 forward the frame, F 1 and F 2 are generated F B 1 B 2 B 1 F 1 4. B 1 and B 2 forward the frames F 1 and F 2 F 1 B 2 3. B 2 receives F 1, B 1 receives F 2 B 1 B 2 F 2 5. The situation in 3. is repeated and the frames are sent back F 1 6. The frames can circulate in the network for ever F 2 B 1 B 2 B 1 F 1 B 2 F 2

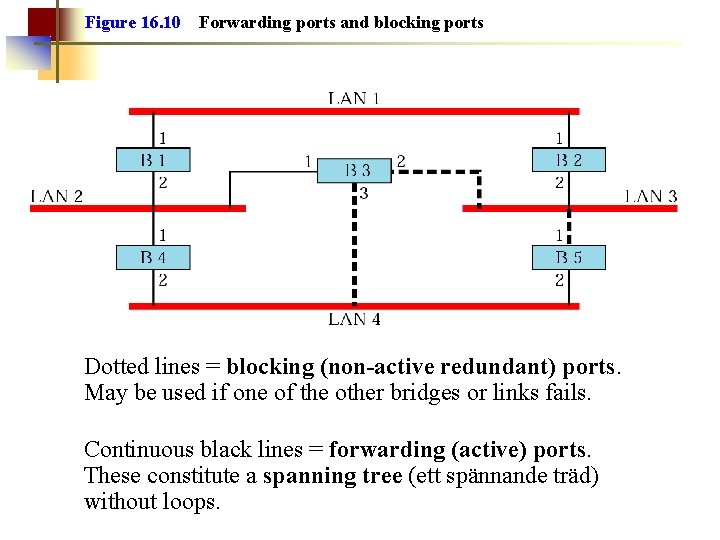
Figure 16. 10 Forwarding ports and blocking ports Dotted lines = blocking (non-active redundant) ports. May be used if one of the other bridges or links fails. Continuous black lines = forwarding (active) ports. These constitute a spanning tree (ett spännande träd) without loops.

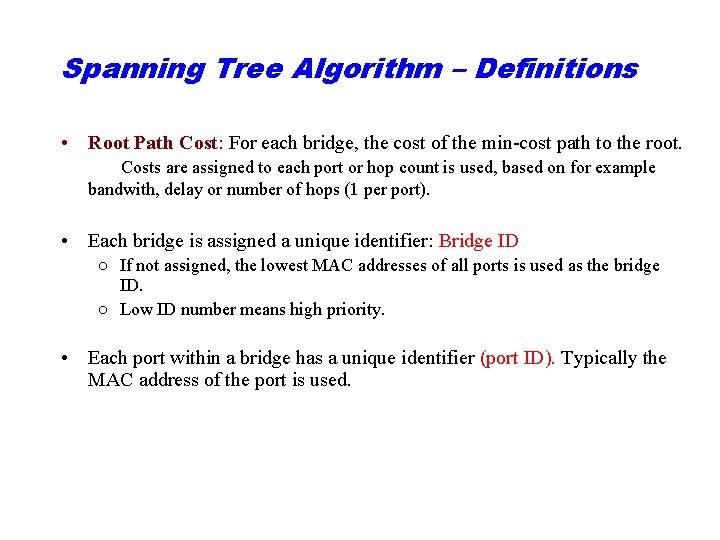
Spanning Tree Algorithm – Definitions • Root Path Cost: For each bridge, the cost of the min-cost path to the root. Costs are assigned to each port or hop count is used, based on for example bandwith, delay or number of hops (1 per port). • Each bridge is assigned a unique identifier: Bridge ID ○ If not assigned, the lowest MAC addresses of all ports is used as the bridge ID. ○ Low ID number means high priority. • Each port within a bridge has a unique identifier (port ID). Typically the MAC address of the port is used.

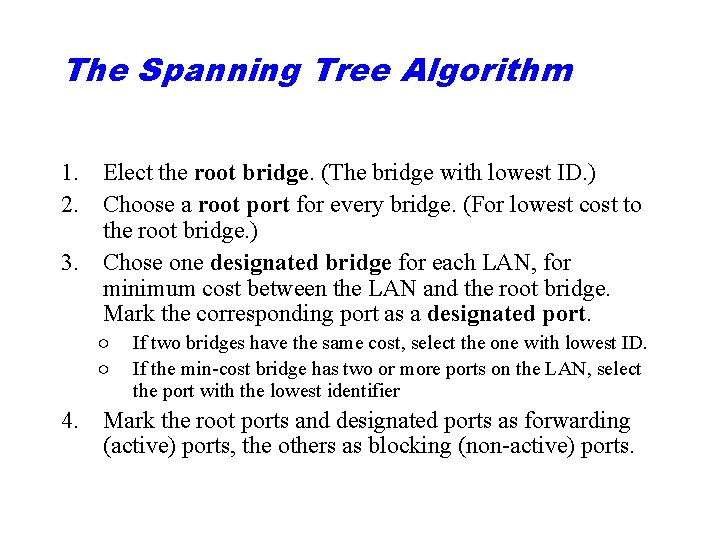
The Spanning Tree Algorithm 1. Elect the root bridge. (The bridge with lowest ID. ) 2. Choose a root port for every bridge. (For lowest cost to the root bridge. ) 3. Chose one designated bridge for each LAN, for minimum cost between the LAN and the root bridge. Mark the corresponding port as a designated port. ○ ○ If two bridges have the same cost, select the one with lowest ID. If the min-cost bridge has two or more ports on the LAN, select the port with the lowest identifier 4. Mark the root ports and designated ports as forwarding (active) ports, the others as blocking (non-active) ports.

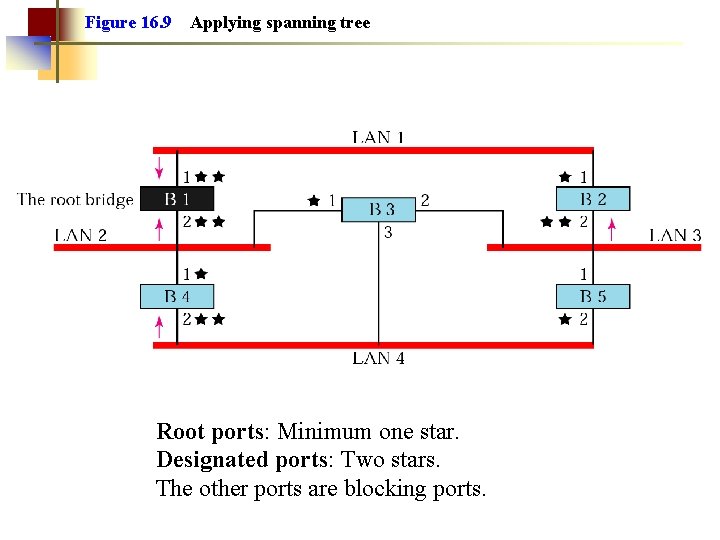
Figure 16. 9 Applying spanning tree Root ports: Minimum one star. Designated ports: Two stars. The other ports are blocking ports.

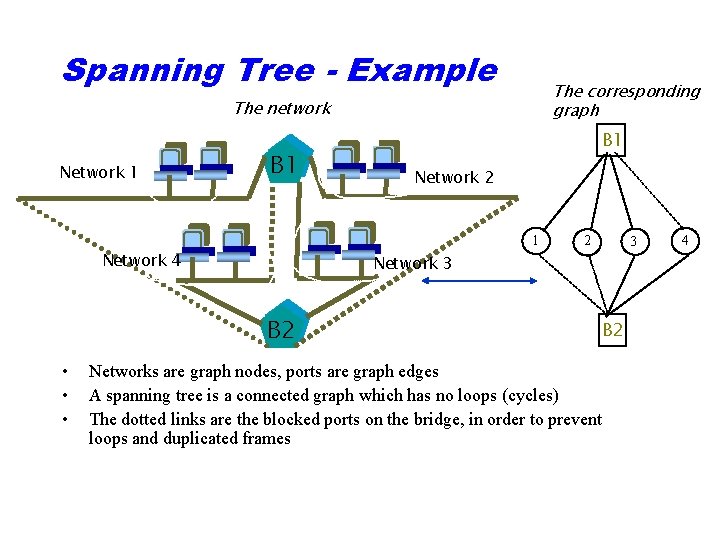
Spanning Tree - Example 1 Network 1 The corresponding graph The network B 1 Network 2 1 Network 4 3 Network 3 B 2 • • • 2 B 2 Networks are graph nodes, ports are graph edges A spanning tree is a connected graph which has no loops (cycles) The dotted links are the blocked ports on the bridge, in order to prevent loops and duplicated frames 4

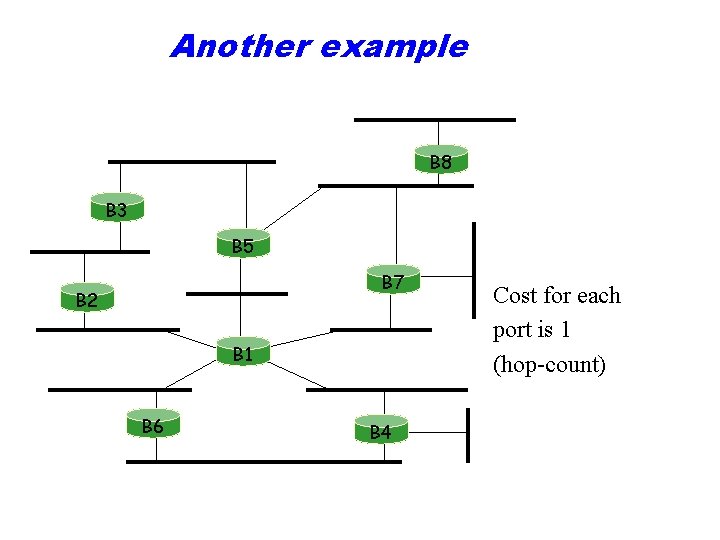
Another example B 8 B 3 B 5 B 7 B 2 B 1 B 6 B 4 Cost for each port is 1 (hop-count)

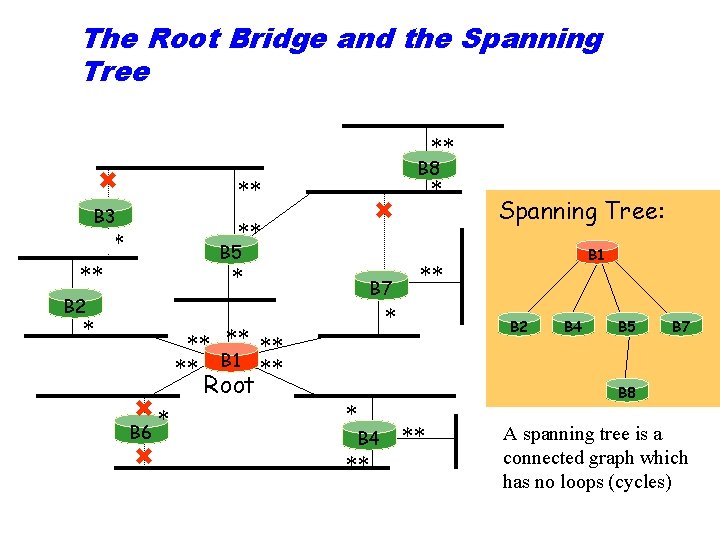
The Root Bridge and the Spanning Tree ** B 8 * ** B 3 ** * B 5 ** * B 7 B 2 * * B 6 * B 1 ** ** B 1 ** Root Spanning Tree: B 2 B 4 B 5 B 7 B 8 B 4 ** ** A spanning tree is a connected graph which has no loops (cycles)

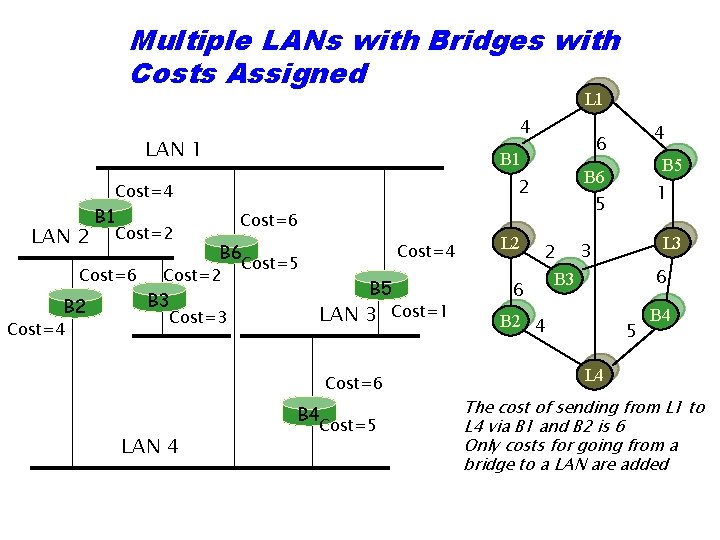
Multiple LANs with Bridges with Costs Assigned L 1 4 LAN 1 LAN 2 B 1 Cost=2 Cost=6 B 2 Cost=4 B 1 Cost=6 B 6 Cost=2 B 3 Cost=4 Cost=5 B 5 LAN 3 Cost=6 B 4 LAN 4 Cost=5 Cost=1 L 2 B 5 B 6 5 2 Cost=4 4 6 2 6 1 L 3 3 6 B 3 B 2 4 5 B 4 L 4 The cost of sending from L 1 to L 4 via B 1 and B 2 is 6 Only costs for going from a bridge to a LAN are added

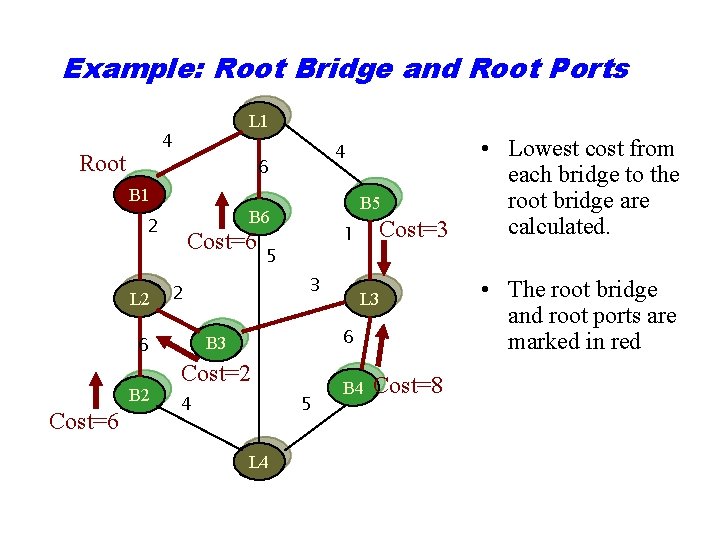
Example: Root Bridge and Root Ports L 1 4 Root 4 6 B 1 2 L 2 Cost=6 Cost=3 1 5 3 2 6 B 2 B 5 B 6 L 3 6 B 3 Cost=2 4 5 L 4 B 4 Cost=8 • Lowest cost from each bridge to the root bridge are calculated. • The root bridge and root ports are marked in red

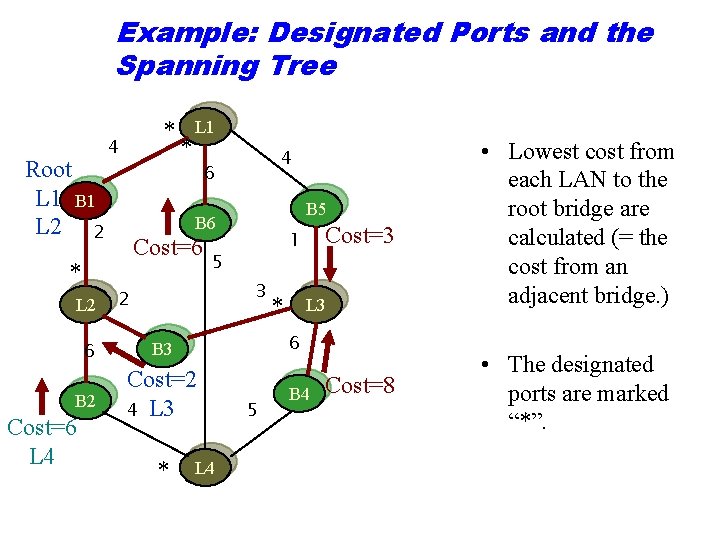
Example: Designated Ports and the Spanning Tree Root L 1 B 1 L 2 2 * 4 4 6 B 5 B 6 Cost=6 * L 2 * L 1 5 3 2 Cost=3 1 * L 3 6 B 2 Cost=2 4 L 3 B 4 Cost=6 L 4 * L 4 5 Cost=8 • Lowest cost from each LAN to the root bridge are calculated (= the cost from an adjacent bridge. ) • The designated ports are marked “*”.

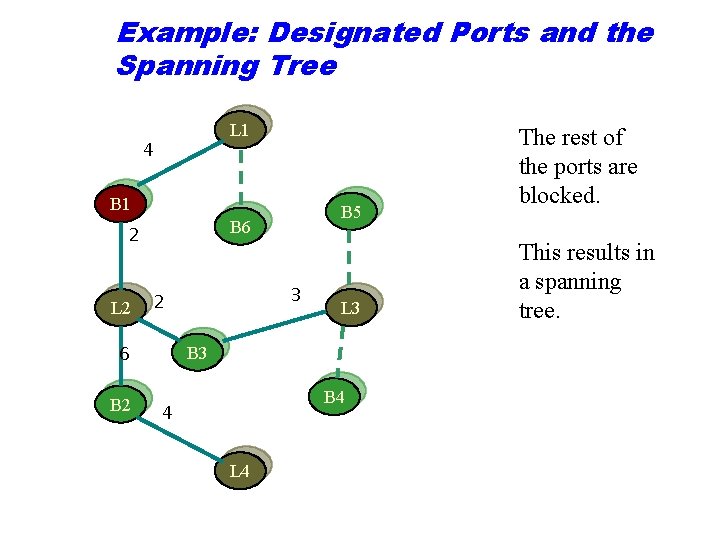
Example: Designated Ports and the Spanning Tree L 1 4 B 1 B 6 2 L 2 3 2 6 B 2 B 5 L 3 B 4 4 L 4 The rest of the ports are blocked. This results in a spanning tree.

Figure 16. 13 Connecting remote LANs

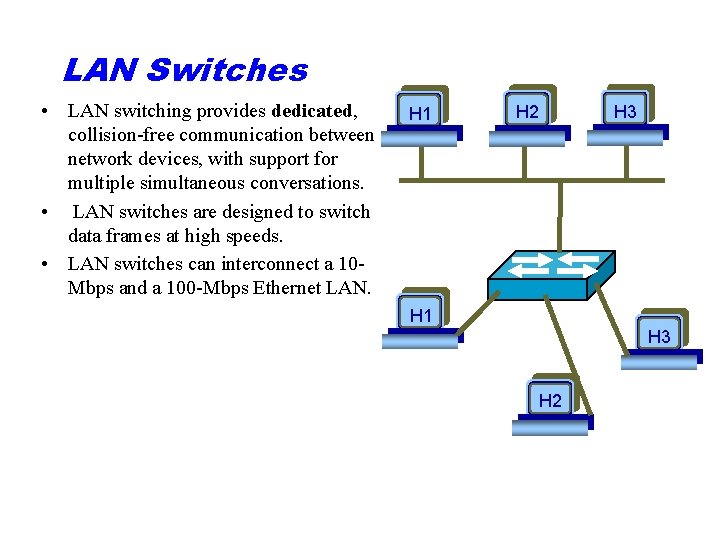
LAN Switches • LAN switching provides dedicated, collision-free communication between network devices, with support for multiple simultaneous conversations. • LAN switches are designed to switch data frames at high speeds. • LAN switches can interconnect a 10 Mbps and a 100 -Mbps Ethernet LAN. H 1 H 2 H 3 H 1 H 3 H 2

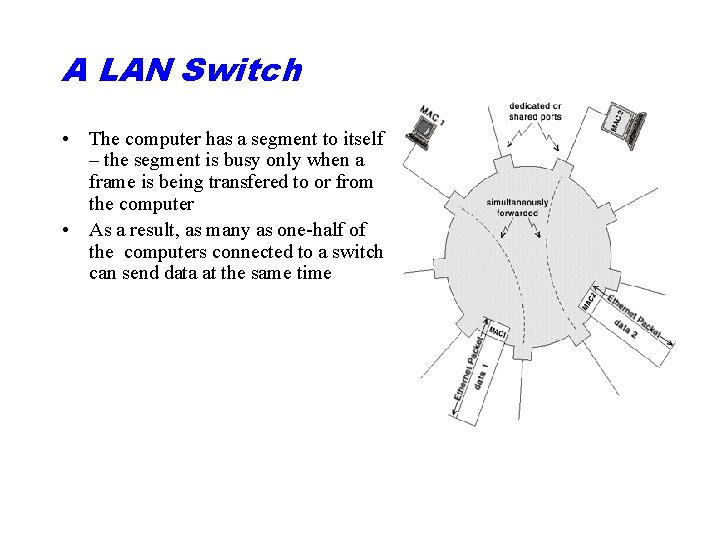
A LAN Switch • The computer has a segment to itself – the segment is busy only when a frame is being transfered to or from the computer • As a result, as many as one-half of the computers connected to a switch can send data at the same time

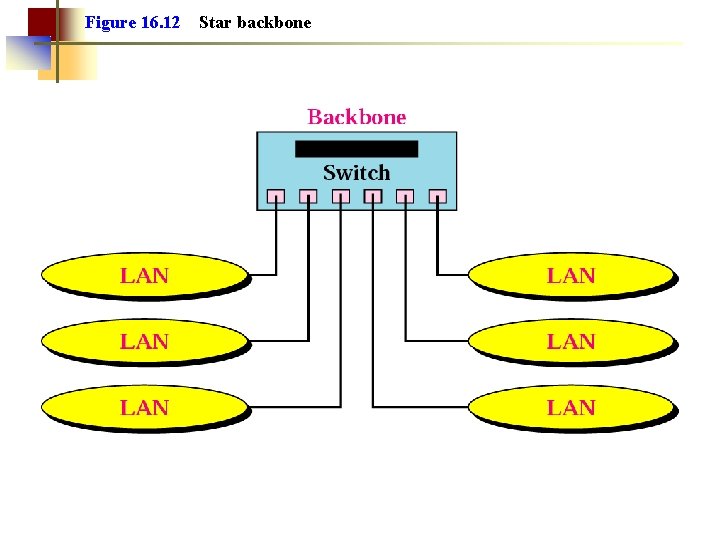
Figure 16. 12 Star backbone

16. 3 Virtual LANs Membership Configuration IEEE Standard Advantages

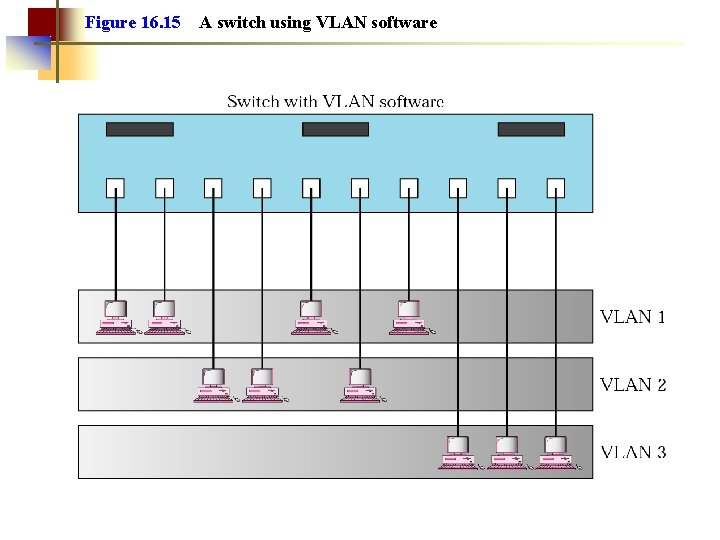
Figure 16. 15 A switch using VLAN software

Note: VLANs create broadcast domains.

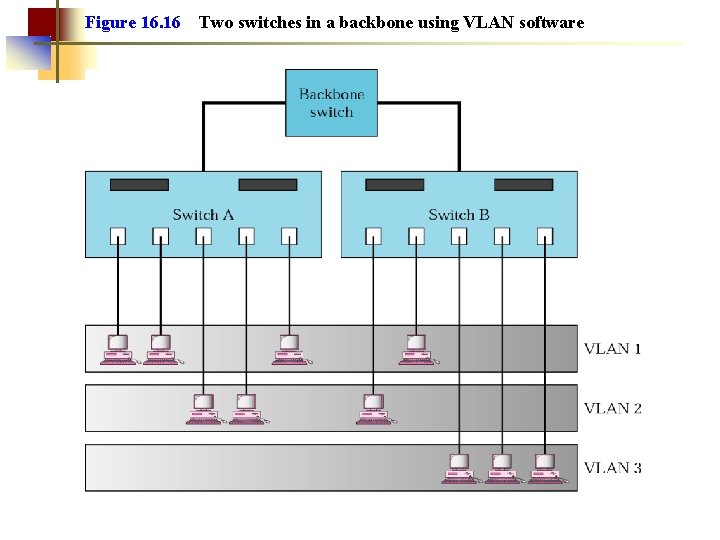
Figure 16. 16 Two switches in a backbone using VLAN software

Chapter 18 Virtual Circuit Switching: Frame Relay and ATM

Two Approaches to Packet Switching • Datagram networks (For example IP) ○ Analogous to the postal service ○ The inteligence is in the end devices (computers), the network should not be trusted ○ Each packet carries the destination address ○ Destination addresses are global internationally • Virtual circuit networks (For example X. 25, Frame Relay and ATM) ○ Analogous to the telephone service ○ The network should take all the responsibility, the end devices should be as simple as posible ○ The path that the packets follow is determined at the beginning of the transmission, but store and forward switching is used.

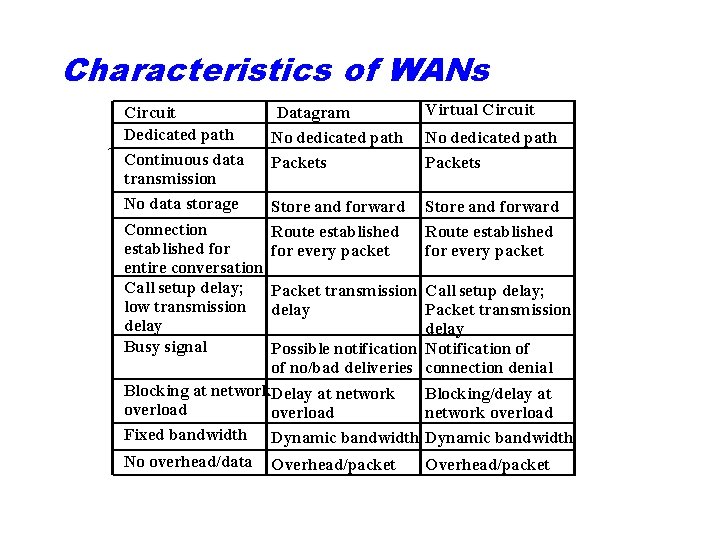
Characteristics of WANs Circuit Dedicated path Continuous data transmission No data storage Connection established for entire conversation Call setup delay; low transmission delay Busy signal Datagram No dedicated path Packets Virtual Circuit Store and forward Route established for every packet No dedicated path Packets Packet transmission Call setup delay; delay Packet transmission delay Possible notification Notification of of no/bad deliveries connection denial Blocking at network. Delay at network Blocking/delay at overload network overload Fixed bandwidth Dynamic bandwidth No overhead/data Overhead/packet

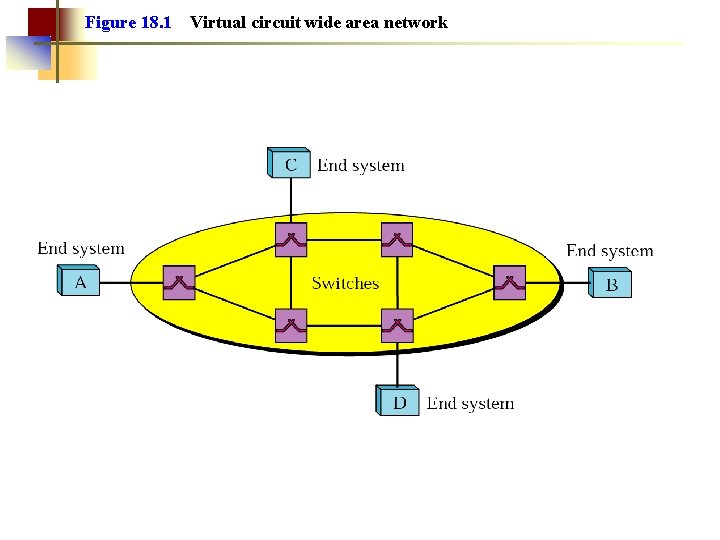
Figure 18. 1 Virtual circuit wide area network

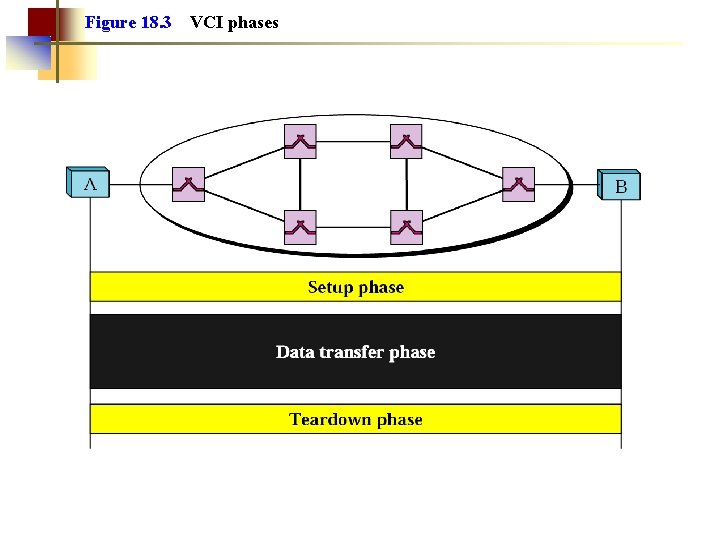
Figure 18. 3 VCI phases

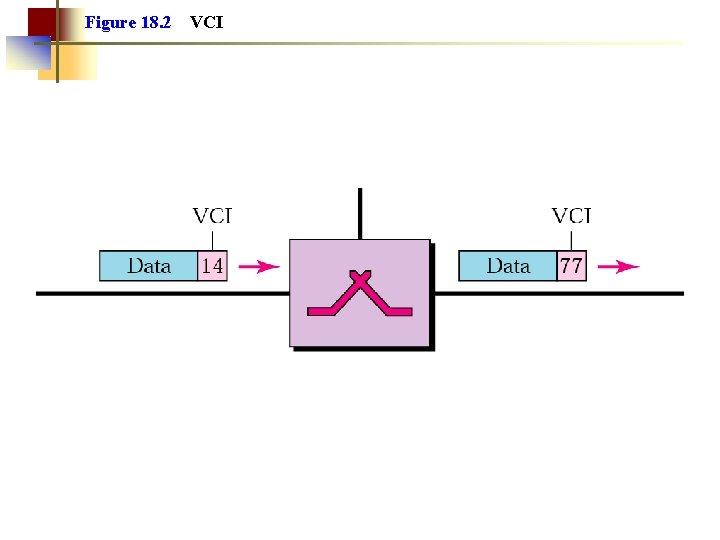
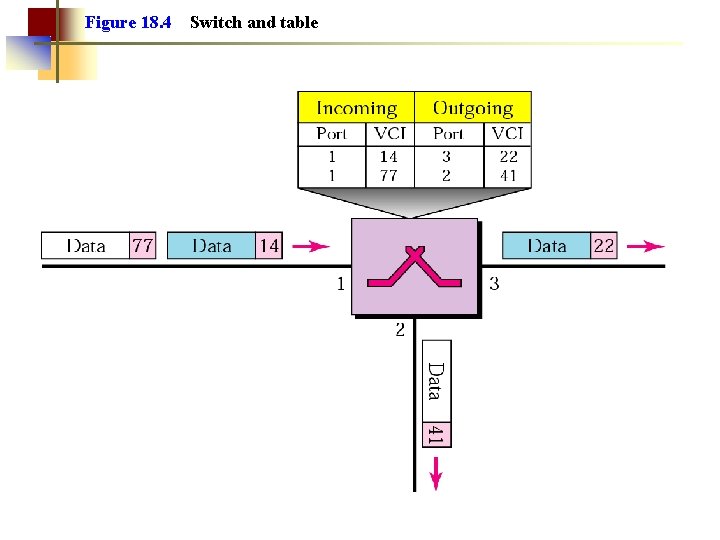
Virtual Circuit Network • Three Phases ○ Setup phase • Network protocol establishes a logical path called virtual circuit (VC). The path remains the same during transmission (all packets use it) ○ Data transfer phase • Each packet carries “tag” or “label” (virtual circuit id, VCI), which determines next hop (the link to which the packet should be forwarded). • At each node, the forwarding is done by inspecting the input line, the VCI and consulting the forwarding table at the switches. ○ Teardown phase • All switches remove the entries about the VCI from their tables

Figure 18. 2 VCI

Figure 18. 4 Switch and table

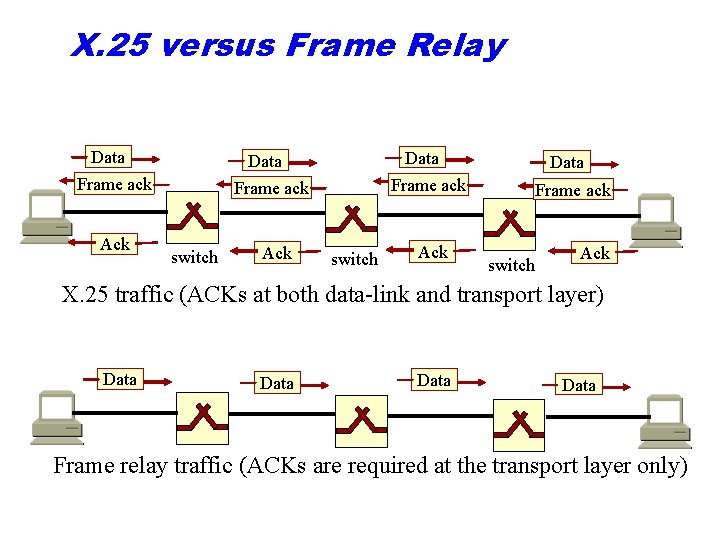
X. 25 Networks • Developed in 1970 s in European countries under the auspices of ITU ○ Public packet-switched networks ○ Uses virtual circuit connections • Switched virtual circuits – analog to dial-up in circuit switching • Permanent virtual circuits – analog to leased lines in circuit switching. ○ ○ Operates on the three lowest layers (physical, data-link and network layer) Performs error-contol and flow-control on the node-to-node basis Work at speed up to 64 Kbps Nowadays it is obsolete

Frame Relay • X. 25 data rates were not stisfactory for users looking for higher data rates and lower costs ○ Checking frames for error at every node is inefficient ○ Only one fourth of traffic is message traffic, the rest is overhead (necessary for transmission media that are more error prone) • Frame relay – public data network that have improved performance ○ Developed having in mind new transmission media that have much lower probability of error ○ Does not provide error checking and acknowledgement at both, the datalink layer and the network layer

X. 25 versus Frame Relay Data Frame ack Ack Data Frame ack switch Ack Data switch Ack Frame ack switch Ack X. 25 traffic (ACKs at both data-link and transport layer) Data Frame relay traffic (ACKs are required at the transport layer only)

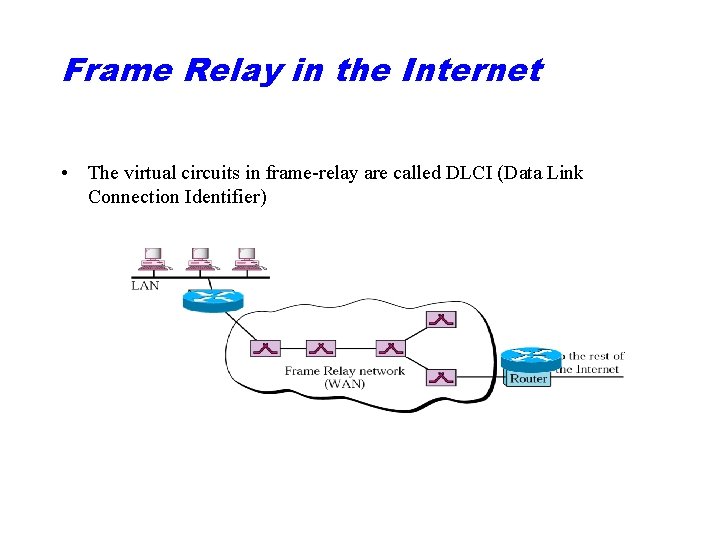
Frame Relay in the Internet • The virtual circuits in frame-relay are called DLCI (Data Link Connection Identifier)

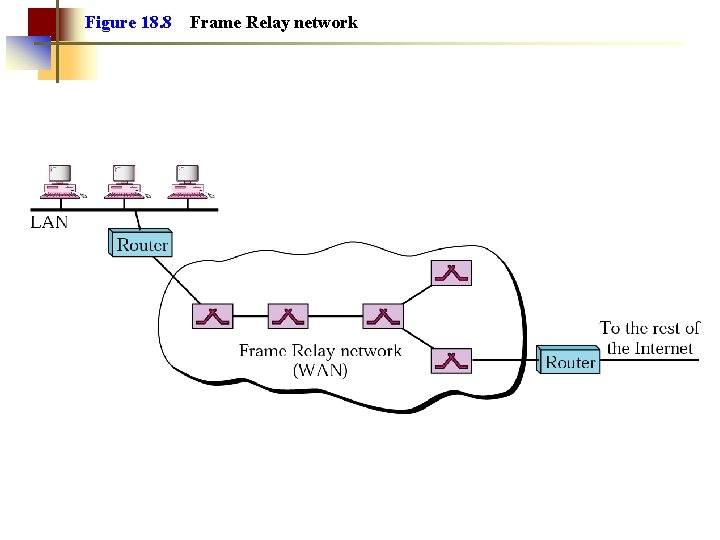
Figure 18. 8 Frame Relay network

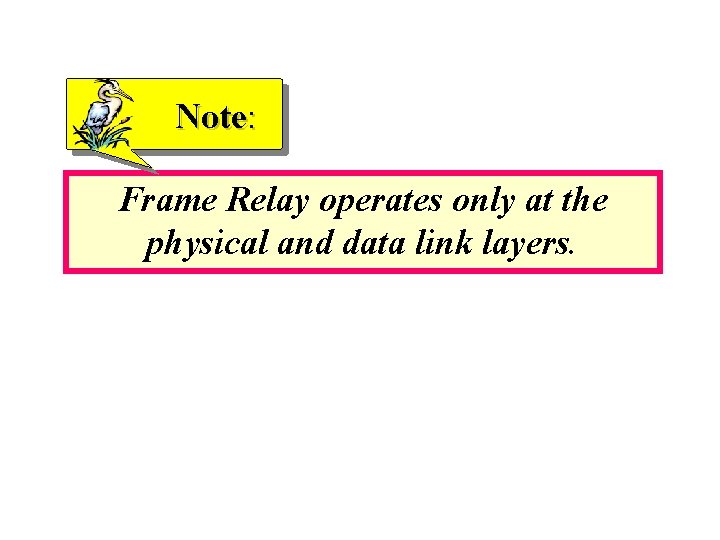
Note: Frame Relay operates only at the physical and data link layers.

Note: Frame Relay does not provide flow or error control; they must be provided by the upper-layer protocols.

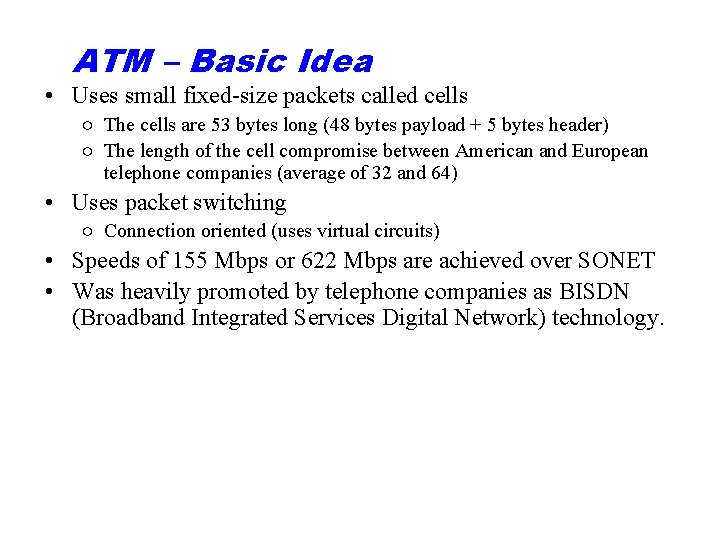
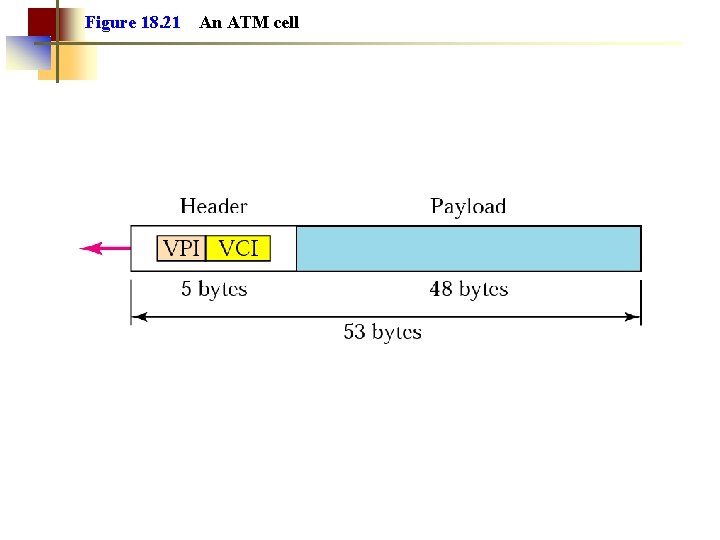
ATM – Basic Idea • Uses small fixed-size packets called cells ○ The cells are 53 bytes long (48 bytes payload + 5 bytes header) ○ The length of the cell compromise between American and European telephone companies (average of 32 and 64) • Uses packet switching ○ Connection oriented (uses virtual circuits) • Speeds of 155 Mbps or 622 Mbps are achieved over SONET • Was heavily promoted by telephone companies as BISDN (Broadband Integrated Services Digital Network) technology.

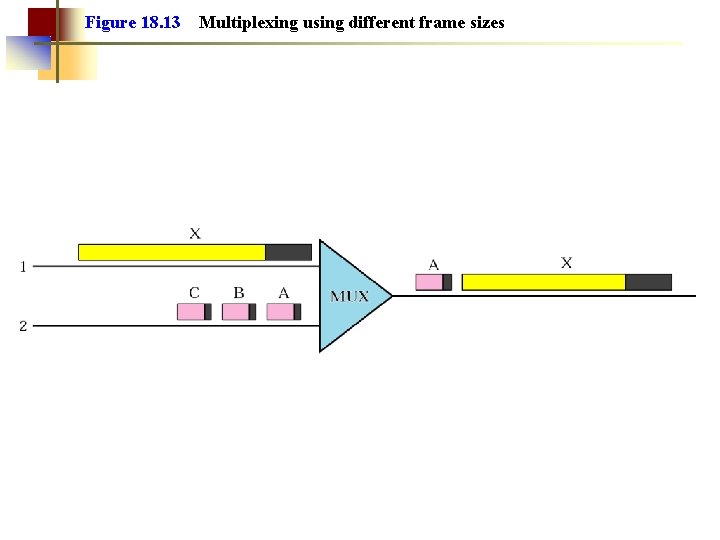
Figure 18. 13 Multiplexing using different frame sizes

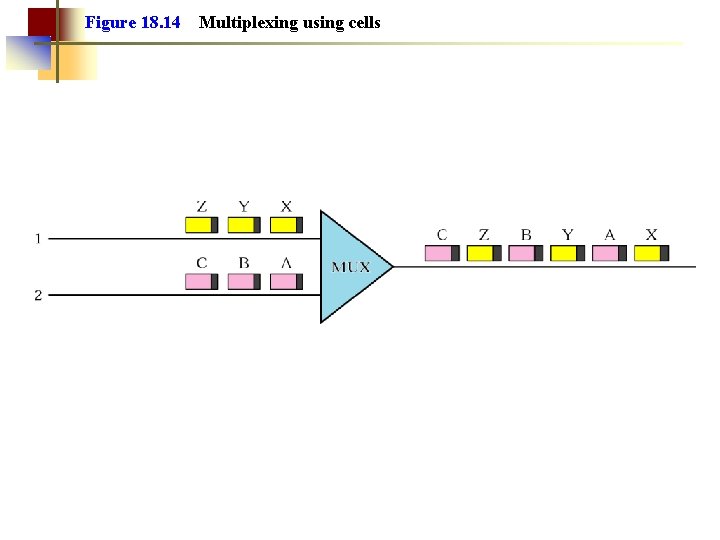
Figure 18. 14 Multiplexing using cells

Note: A cell network uses the cell as the basic unit of data exchange. A cell is defined as a small, fixed-sized block of information.

ATM Basic Concepts • Nagotiated Service Contract ○ Logical connections called Virtual circuits • The sender nagotiates a ”requested path” with the network for a connection to the destination ○ End-to-end Quality of Service • When setting up a connection the sender specifies the atributes of the call (type, sped, . . . ) which determine end-to-end quality of service • Virtual Circuit Network ○ Well defined connection procedures ○ Dedicated capacity per connection ○ Flexible access speeds • Cell based (short packets with fixed size) • All kinds of data look same to the network

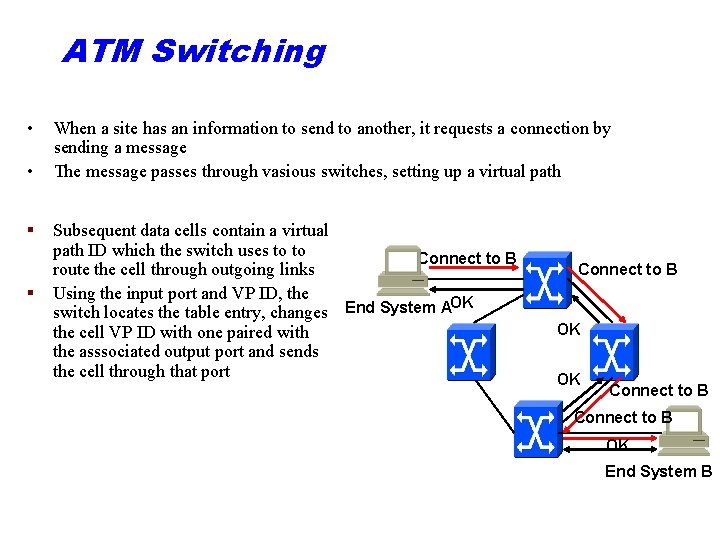
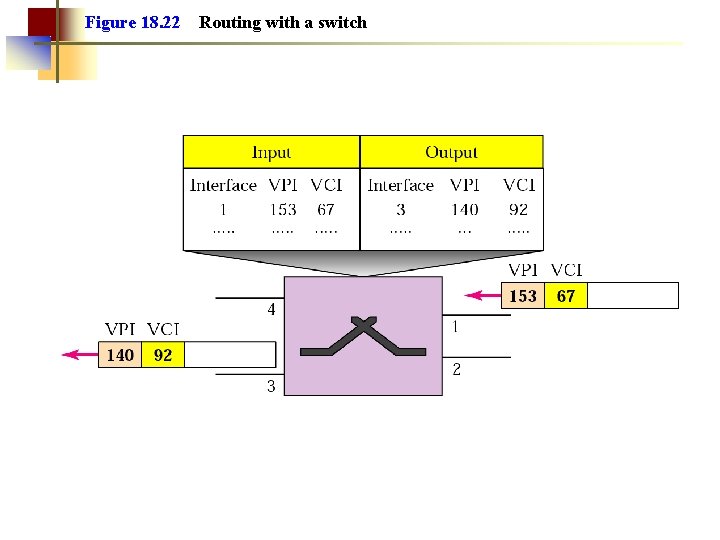
ATM Switching • • § § When a site has an information to send to another, it requests a connection by sending a message The message passes through vasious switches, setting up a virtual path Subsequent data cells contain a virtual path ID which the switch uses to to Connect to B route the cell through outgoing links Using the input port and VP ID, the OK switch locates the table entry, changes End System A the cell VP ID with one paired with the asssociated output port and sends the cell through that port Connect to B OK OK Connect to B OK End System B

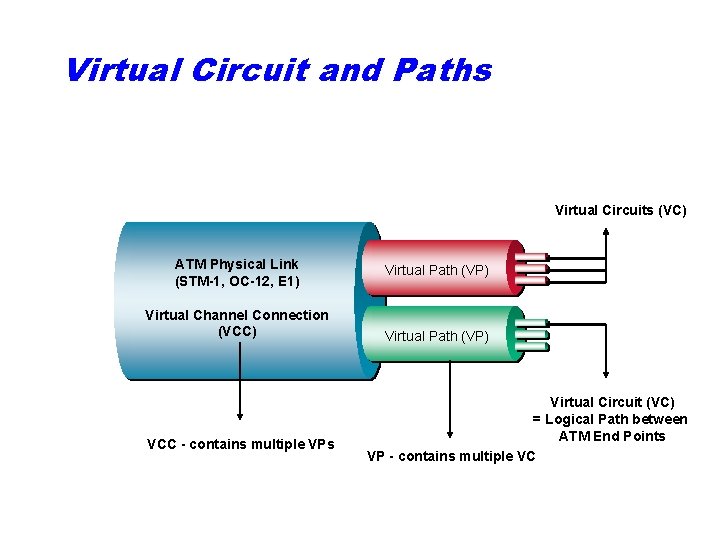
Virtual Circuit and Paths Virtual Circuits (VC) ATM Physical Link (STM-1, OC-12, E 1) Virtual Channel Connection (VCC) VCC - contains multiple VPs Virtual Path (VP) Virtual Circuit (VC) = Logical Path between ATM End Points VP - contains multiple VC

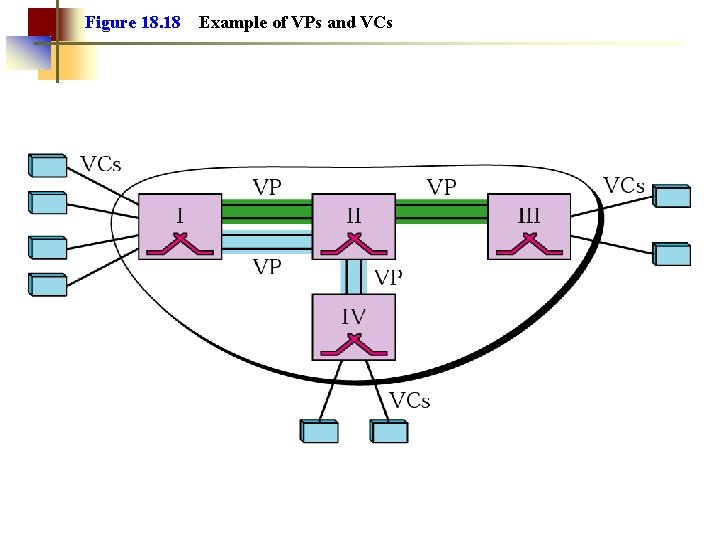
Figure 18. 18 Example of VPs and VCs

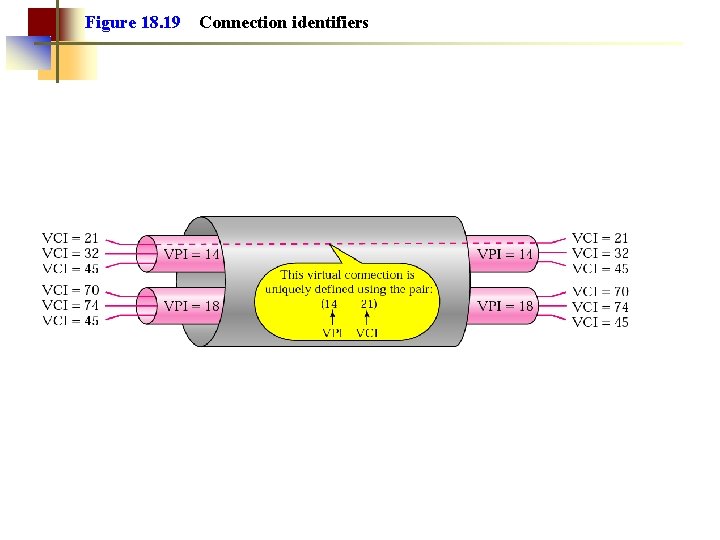
Note: Note that a virtual connection is defined by a pair of numbers: the VPI and the VCI.

Figure 18. 19 Connection identifiers

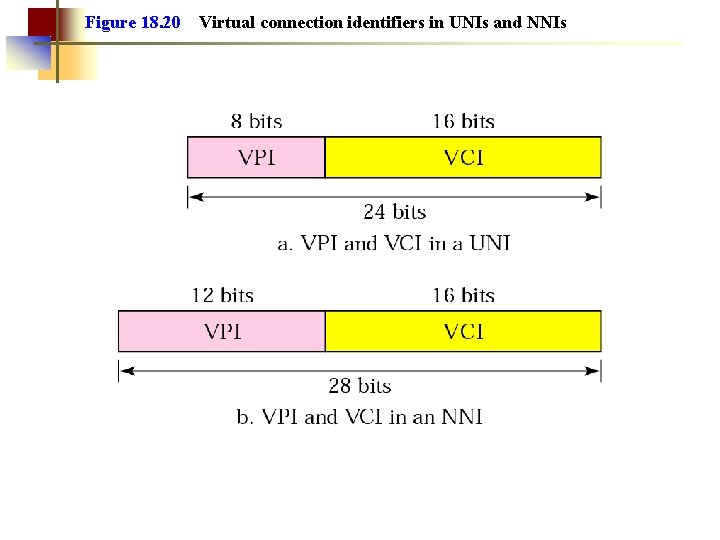
Figure 18. 20 Virtual connection identifiers in UNIs and NNIs

Figure 18. 21 An ATM cell

Figure 18. 22 Routing with a switch

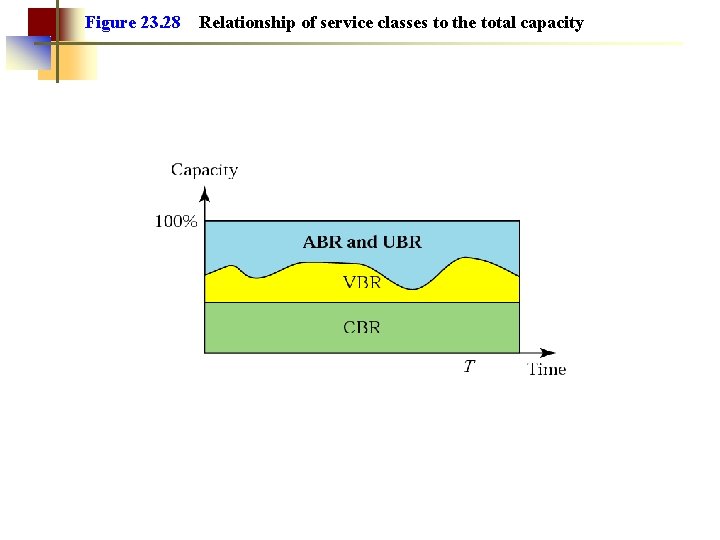
ATM Quality of Service Models • CBR (Constant Bit Rate) ○ Carries real time (constant bit rate) traffic ○ Guaranties rate, delay and loss of cells • UBR (Unspecified Bit Rate) ○ No other guarantee besides in-order delivery of cells • ABR (Available Bit Rate) ○ No guarantee on transmision rate, but if possible the user can use a higher rate than in UBR. ○ Congestion feedback from the network • VBR ○ The variable bit-rate is requested by the sender ○ Targeted toward real-time services like CBR

Figure 23. 28 Relationship of service classes to the total capacity