Database Security Chapter 24 20110613 cindy 2 Outline

+ Database Security 教育輪講 Chapter 24 2011/06/13 cindy

+ 2 Outline l Introduction to Database Security Issues l Discretionary Access Control Based on Granting and Revoking Privileges l Mandatory Access Control and Role-Based Access Control for Multilevel Security l SQL Injection l Introduction to Statistical Database Security and Flow control l Encryption and Public Key Infrastructures l Privacy Issues and Preservation

+ 3 Introduction to Database Security Issues l Types of Security Legal and ethical issues l Policy issues l System-related issues l The need in some organizations to identify multiple security levels l

+ 4 Introduction to Database Security Issues l Threats to Databases l Loss of integrity l l DB integrity refers to the requirement that information be protected from improper modification. Integrity is lost if unauthorized changes are made to the data by either intentional or accidental acts. l Loss of availability l DB availability refers to making objects available to a human user or a program to which they have a legitimate right. l Loss of confidentiality l DB confidentiality refers to the protection of data from unauthorized disclosure.

+ 5 Introduction to Database Security Issues l A DBMS typically includes a database security and authorization subsystem Discretionary security mechanisms l Mandatory security mechanisms l l To protect databases against various of threats, it is common to implement 4 kinds of control measures Access control l Inference control l Flow control l Data encryption l

+ 6 Introduction to Database Security Issues l Access control l The function: The security mechanism of a DBMS must include provisions for restricting access to the database system as a whole. l Is handled by creating users accounts and passwords to control the login process by the DBMS.

+ 7 Introduction to Database Security Issues l Flow control l prevents information from flowing in such a way that it reaches unauthorized users. (24. 6)

+ 8 Database security and the DBA l DBA Whose responsibilities include granting privileges to users and classifying users and data in accordance with the policy of the organization. l Has a DBA account in the DBMS l l Account creation Privilege granting Privilege revocation l Security level assignment l l
+ 9 Access control, User Accounts, and DB Audits l Whenever a person or a group of persons needs to access a DB system, the individual or group must first apply for a user account…. l The user must log in by entering the account number and password whenever the database access is needed. l Consists of reviewing the log to examine all accesses and operations applied to the database during a certain time period. DBA often set up auditing

+ 10 Sensitive Data l Sensitivity of data is a measure of the importance assigned to the data by its owner, for the purpose of denoting its need for protection l Not all the databases contain sensitive data l Several factors can cause data to be classified as sensitive

+ 11 Discretionary Access control Based on Granting and Revoking Privileges l The typical method of enforcing discretionary access control in a database system is based on the granting and revoking of privileges. l Types of Discretionary Privileges l The account level l DBA specifies the particular privileges that each account holds independently of the relations in the database l The relation (or table) level l DBA can control the privilege to access each individual relation or view in the database

+ 12 Types of Discretionary Privileges l The privileges at the account level apply to the capabilities to the account itself and can include the following parts: l l l CREATE CHEMA or CREATE TABLE privilege CREATE VIEW privilege ALTER privilege DROP privilege MODIFY privilege SELECT privilege l The second level of privileges applies to the relation level including l l Base relations and virtual (view) relations These privileges are defined for SQL 2

+ 13 Types of Discretionary Privileges l The granting and revoking of privileges generally follow an authorization model for discretionary privileges known as the access matrix model where The rows of a matrix M represents subjects (users, accounts, programs) l The columns represent objects (relations, records, columns, views, operations). l Each position M(i, j) in the matrix represents the types of privileges (read, write, update) that subject i holds on object j. l

+ 14 Types of Discretionary Privileges l In SQL the following types of privileges can be granted on each individual relation R: l SELECT privilege on R l l Gives the account retrieval privilege In SQL this gives the account the privilege to use the SELECT statement to retrieve tuples from R. l Modification privileges on R l l Gives the account the capability to modify the tuples of R In SQL this privilege is further divided into UPDATE, DELETE, and INSERT privileges to apply the corresponding SQL command to R. l Reference privilege on R l Give the account the capability to reference a relation R when specifying integrity constraints.

+ 15 Specifying Privileges through the User of Views l The mechanism of views is important… If account A of relation R wants another B to be able to retrieve only some fields of R, A can create a view V of R including only those attributes and then grant SELECT on V to B.

+ 16 Revoking of Privileges l In some cases it is desirable to grant a privilege to a user temporarily. For example: l The owner of a relation may want to grant the SELECT privilege to a user for a specific task and then revoke that privilege once the task is completed l Hence, a mechanism for revoking privileges is needed. In SQL, a REVOKE command is included for the purpose of canceling privileges

+ 17 GRANT OPTION l Owner A of R (relation) grants a privilege on R to another account B, it can be given to B with or without the GRANT OPTION l If the GRANT OPTION is given, it means B can also grant that privilege on R to other accounts l In this way, if owner account A revokes the privilege granted to B, all the privileges that B propagated based on that privilege should automatically be revoked

+ Granting and Revoking of Privileges examples l DBA creates 4 accounts –A 1, A 2, A 3, A 4 wants only A 1 to be able to create base relations. l GRANT CREATABLE TO A 1; l IN SQL 2, accomplish by having the DBA issue a CREATE SCHEMA command l CREATE SCHEMA EXAMPLE AUTHORIZATION A 1; l User account A 1 can now create tables under the schema called EXAMPLE. To continue, suppose that A 1 creates EMPLOYEE and DEPARTMENT, A 1 is the owner of the 2 relations and have has all the relation privileges on each of them. 18
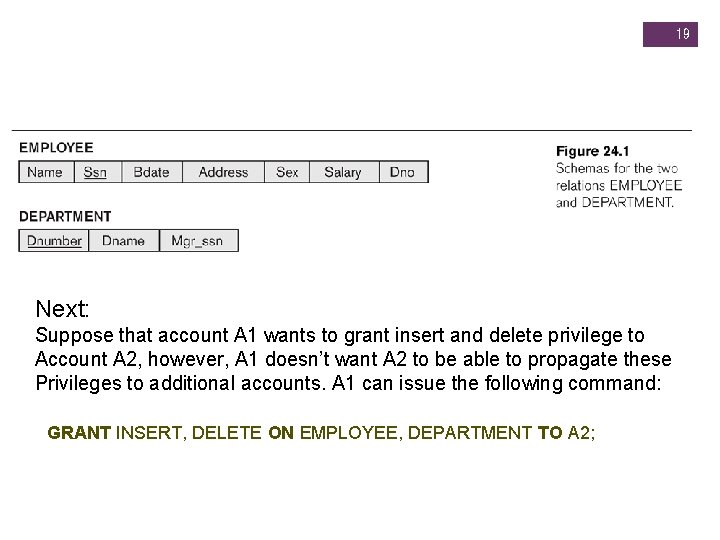
19 Next: Suppose that account A 1 wants to grant insert and delete privilege to Account A 2, however, A 1 doesn’t want A 2 to be able to propagate these Privileges to additional accounts. A 1 can issue the following command: GRANT INSERT, DELETE ON EMPLOYEE, DEPARTMENT TO A 2;
20 Next: Suppose that A 1 wants to allow account A 3 to retrieve information from Either of the two tables and also to be able to propagate the SELECT privilege to other accounts. A 1 can issue the command: GRANT SELECT ON EMPLOYEE, DEPARTMENT TO A 3 WITH GRANT OPTION; GRANT SELECT ON EMPLOYEE TO A 4; Now suppose that A 1 decides to revoke the SELECT privilege on the EMPLOYEE Relation from A 3. Automatically revoke A 1 can issue this command: the privilege from A 4 Revoke SELECT ON EMPLOYEE FROM A 3;
21 Next: suppose that A 1 wants to give back to A 3 a limited capability to SELECT from the EMPLOYEE relation and wants to allow A 3 to be able to propagate the privilege. The limitation is to retrieve only the Name, Bdate, and Address attributes and only for the tuples with Dno=5. A 1 can create the following view: CREATE VIEW A 3 EMPLOYEE AS SELECT Name, Bdate, Address FROM EMPLOYEE WHERE Dno=5; Now, A 1 can grant SELECT on the view A 3 EMPLOYEE to A 3 as GRANT SELECT ON A 3 EMPLOYEE TO A 3 WITH GRANT OPTION; Finally, suppose A 1 wants to allow A 4 to update only the Salary attribute of EMPLOYEE. A 1 can issue the following command: GRANT UPDATE ON EMPLOYEE (Salary) TO A 4;

+ 22 Specifying Limits on Propagation of Privileges l Horizontal propagation l To an integer number i means an account B given the GRANT OPPTION can grant the privilege to at most i other accounts l Vertical propagation Is more complicated l Limits the depth of the granting of privileges l

+ 23 Mandatory Access Control and Role-Based Access Control for Multilevel Security l What is MAC? l An approach l In many applications, an additional security policy is needed that classifies data and users based on security classes l Typically be combined with the discretionary access control mechanisms
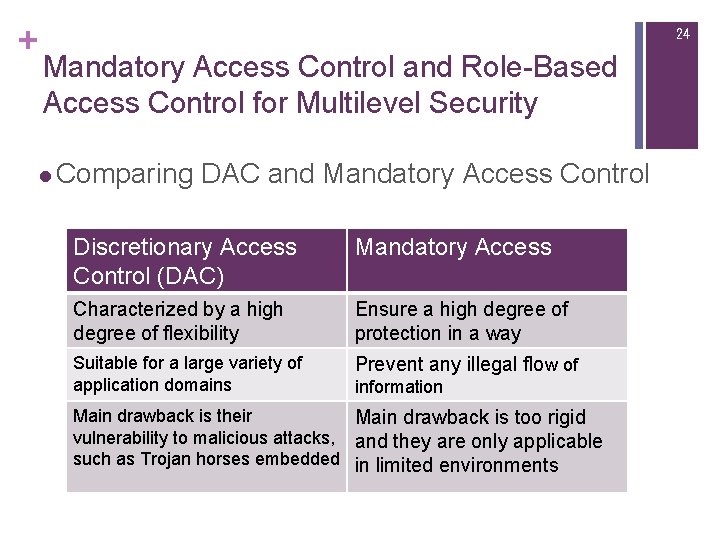
+ 24 Mandatory Access Control and Role-Based Access Control for Multilevel Security l Comparing DAC and Mandatory Access Control Discretionary Access Control (DAC) Mandatory Access Characterized by a high degree of flexibility Ensure a high degree of protection in a way Suitable for a large variety of application domains Prevent any illegal flow of information Main drawback is their Main drawback is too rigid vulnerability to malicious attacks, and they are only applicable such as Trojan horses embedded in limited environments

+ 25 Mandatory Access Control and Role-Based Access Control for Multilevel Security l Role-based Access control (RBAC) l Emerged for managing and enforcing security in large-scale enterprise-wide systems l Basic notion is that privileges and other permissions are associated with organizational roles, rather than individual users l Roles can be created using the CREATE ROLE and DESTROY ROLE command, GRNAT and REVOKE command be used to assign and revoke privileges from roles

+ 26 Mandatory Access Control and Role-Based Access Control for Multilevel Security l RBAC appears to be a viable alternative to traditional discretionary and mandatory access controls l It ensures that only authorized users are given access to certain data or resources l Role hierarchy in RBAC is a natural way to organize roles to reflect the organization’s lines of authority and responsibility l Role implement: Grant the roles to two types of employees GRANT ROLE full_time TO employee_type 1 GRANT ROLE intern TO employee_type 2

+ 27 Access Control Policies for E-Commerce and the Web l E-Commerce environments require elaborate access control policies that go beyond DBMSs. Conventional database environment E-commerce environment Resources to be protected are only traditional data, Usually performed Resources to be protected are not using a set of authorizations stated only traditional data but also by security officers or users knowledge and experience. according to some security policies. Such a simple paradigm is not well Calls for more flexibility in suited for a dynamic environment. specifying access control policies.

+ 28 Access Control Policies for E-Commerce and the Web l Support for content-based access control l Content-based access control allows one to express access control policies that take the protection object content into account l Require access control policies based on user characteristics and qualifications rather than on specific and individual characteristics A possible solution, to better take into account user profiles in the formulation of access control policies, is to support the notion of credentials l A credential is a set of properties concerning a user that are relevant for security purposes l

+ 29 Access Control Policies for E-Commerce and the Web l XML is becoming the common representation language for document interchange over the web l XML is also becoming the language for e- commerce XML is expected to play a key role in access control for e-commerce applications

+ 30 SQL Injection l What is SQL Injection? l One of the most common threats to a database system, the attacker injects a string input through the application, which changes or manipulates the SQL statement to the attacker’s advantage
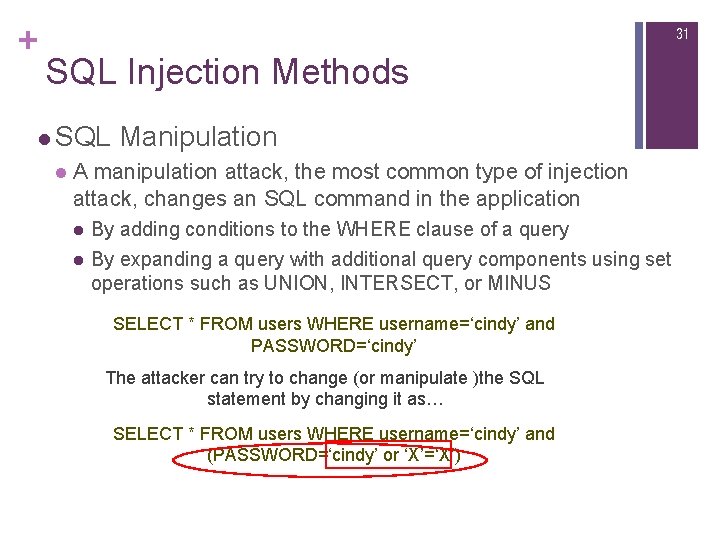
+ 31 SQL Injection Methods l SQL Manipulation l A manipulation attack, the most common type of injection attack, changes an SQL command in the application l l By adding conditions to the WHERE clause of a query By expanding a query with additional query components using set operations such as UNION, INTERSECT, or MINUS SELECT * FROM users WHERE username=‘cindy’ and PASSWORD=‘cindy’ The attacker can try to change (or manipulate )the SQL statement by changing it as… SELECT * FROM users WHERE username=‘cindy’ and (PASSWORD=‘cindy’ or ‘X’=‘X’)
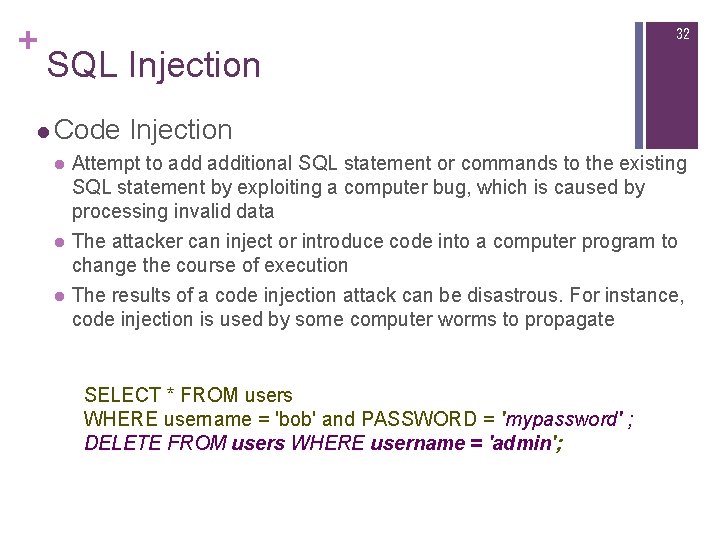
+ 32 SQL Injection l Code Injection l l l Attempt to additional SQL statement or commands to the existing SQL statement by exploiting a computer bug, which is caused by processing invalid data The attacker can inject or introduce code into a computer program to change the course of execution The results of a code injection attack can be disastrous. For instance, code injection is used by some computer worms to propagate SELECT * FROM users WHERE username = 'bob' and PASSWORD = 'mypassword' ; DELETE FROM users WHERE username = 'admin';
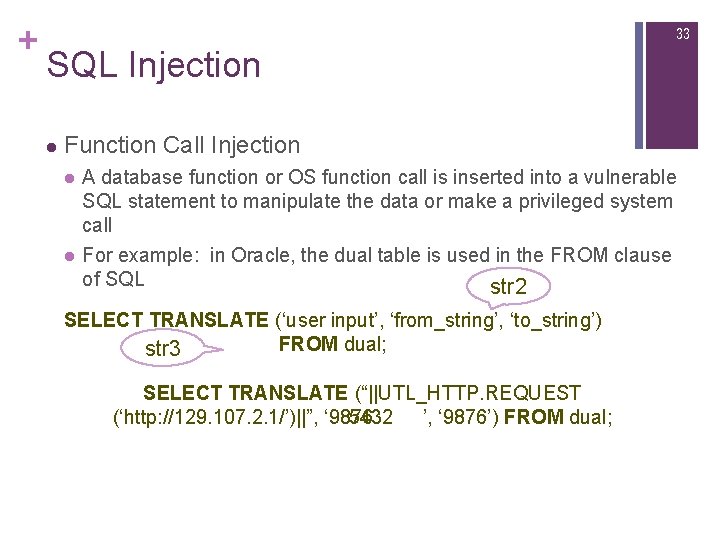
+ 33 SQL Injection l Function Call Injection l l A database function or OS function call is inserted into a vulnerable SQL statement to manipulate the data or make a privileged system call For example: in Oracle, the dual table is used in the FROM clause of SQL str 2 SELECT TRANSLATE (‘user input’, ‘from_string’, ‘to_string’) FROM dual; str 3 SELECT TRANSLATE (“||UTL_HTTP. REQUEST (‘http: //129. 107. 2. 1/’)||”, ‘ 9876 ’, ‘ 9876’) FROM dual; 5432

+ 34 Risks Associated with SQL Injection l Database Fingerprinting l The attacker can determine the type of database being used in the backend so that he can use database-specific attacks that correspond to weaknesses in a particular DBMS l Denial of Service l The attacker can flood the server with requests, thus denying service to valid users, or they can delete some data l Bypassing Authentication l The attacker can gain access to the database as an authorized user and perform all the desired tasks
+ 35 Risks Associated with SQL Injection l Identifying Injectable Parameters l The attacker gathers important information about the type and structure of the back-end database of a Web application l Executing Remote Commands l Provides attackers with a tool to execute arbitrary commands on the database l Performing Privilege Escalation l Takes advantages of logical flaws within the database to upgrade the access level
+ 36 Protection Techniques against SQL Injection l Bind Variables (Using Parameterized Statements) Example: Consider the following example using Java and JDBC: Prepared. Statement stmt=conn. prepare. Statement (“SELECT * FROM EMPLOYEE WHERE EMPLOYEE_ID=? AND PASSWORD=? ”); stmt. set. String(1, employee_id); stmt. set. String(2, password); Embedding the user input into the statement ? Input is bound to a parameter
+ 37 Protection Techniques against SQL Injection l Filtering Input (Input Validation) Can be used to remove escape characters from input strings by using the SQL Replace function l Some SQL Manipulation attacks can be prevented by using this technique. However, if there could be a large number of escape characters, it is not reliable l l Function Security l Database functions, both standard and custom should be restricted

+ 38 Introduction to Statistical Database Security l Statistical databases l Used for statistical analysis purpose l An OLAP instead of OLTP system
+ 39 Introduction to Statistical Database Security l Statistical databases are used mainly to produce statistics about various populations l The database may contain confidential data about individuals l A population is a set of tuples of a relation that satisfy some selection condition Each selection condition on the PERSON relation will specify a particular population of PERSON tuples l For example, the condition Sex=‘M’ specifies the male population… l

+ 40 Introduction to Statistical Database Security l Statistical queries involve applying statistical functions to a population of tuples Retrieve the number of individuals or the average income ? However…statistical users are not allowed to retrieve individual data, such as the income of a specific person… Statistical database security techniques must prohibit the retrieval of individual data. This can be achieved by prohibiting queries that retrieve attribute values and by allowing only queries that involve statistical aggregate functions such as COUNT, SUM, MIN, MAX…

+ 41 Introduction to Flow Control l What is Flow Control? l Flow control regulates the distribution or information among accessible object l A flow between object X and object Y occurs when a program reads from X and writes values into Y l Flow controls check that information contained in some objects does not flow explicitly or implicitly into less protected objects l Thus, a user cannot get indirectly in Y what he cannot get directly in X

+ 42 Introduction to Flow Control l Flow policy l Specifies the channels along with information is allowed to move l The simplest flow policy specifies just two classes of information –confidential (C) and nonconfidential (N) l allow all flows except those from class C to class N l Can solve the confinement problem that arises when a service program handles data such as customer’s confidential information

+ 43 Introduction to Flow Control l Covert Channels l l Allows a transfer of information that violates the security or the policy Specially, allows information to pass from a higher classification level to a lower classification level through improper means l Covert Channels can be classified into two broad categories: l l Storage channels do not require any temporal synchronization, in that information is conveyed by accessing system information or what is otherwise inaccessible to the user. Timing channel allow the information to be conveyed by the timing of events or processes

+ 44 Encryption and Public Key Infrastructures l Encryption is a means of maintaining secure data in an insecure environment l Encryption consist of applying an encryption algorithm to data using some prespecified encryption key l The resulting data has to be decrypted using a decryption key to recover the original data

+ 45 The Data Encryption and Advanced Encryption Standards l Data Encryption Standard (DES) is a system developed by the U. S government for use by the general public. It has been widely accepted as a cryptographic standard both in the U. S and abroad l Can provide end-to-end encryption on the channel between sender A and receiver B l Based on a symmetric-key algorithm that uses a 56 -bite key l

+ 46 The Data Encryption and Advanced Encryption Standards l NIST introduced it after questioning the adequacy of DES. l This algorithm has a block size of 128 bits, can use keys of 128, 192, or 256 bits, compared with DES’s 56 -bit key
+ 47 Symmetric Key Encryption l Symmetric key encryption l Use one key for both encryption and decryption l Users exchanging data keep this key to themselves l The algorithm used for symmetric encryption is called secret-key algorithm l Drawback is that both sender and recipient must exchange the common key in a secure manner
+ 48 Public (Asymmetric) Key Encryption l Public key encryption l As a new kind of cryptosystem, Was proposed in 1976 l Public key algorithms are based on mathematical functions They also involve the use of two separate keys. l The use of two keys can have profound consequences in the areas of confidentiality, key distribution, and authentication l

+ 49 Public (Asymmetric) Key Encryption l The two Keys l Are referred to as the public key and the private key l The private key is kept secret, but it is referred to as private key rather than a secret key

+ 50 Challenges of Database Security l Data Quality l The DB community needs techniques and organizational solutions to assess and attest the quality of data l Intellectual Property Rights Watermarking techniques for relational data l Protect content from unauthorized duplication and distribution by enabling provable ownership of the content l l Database Survivability l Database system need to operate and continue their functions

+ 51 Database Survivability(cont. ) l A DBMS, in addition to making every effort to prevent an attack and detecting one in the event of occurrence, should be able to do the following: l Confinement l l Damage assessment l l Determine the extent of the problem, including failed functions and corrupted data Reconfiguration l l The immediate action to eliminate the attacker’s access to the system Reconfigure to allow operation to continue in a degraded mode while recovery proceeds Fault treatment l To the extent possible, identify the weakness exploited in the attack and take steps to prevent a recurrence

+ 52 Summary l Database Security and Authorization l Discretionary Access Control l Mandatory Access Control and Role-Based Access Control for Multilevel Security l Statistical Database Security l Flow Control l Encryption and Public Key Infrastructures l Challenges of Database Security

+ 53 Note l OLAP l online analytical processing, is an approach to swiftly answer multi-dimensional analytical queries l Typical applications of OLAP include business reporting for sales, marketing, financial reporting and similar areas l OLTP l Online transaction processing, refers to a class of systems that facilitate and manage transaction-oriented applications l Typically for data entry and retrieval transaction processing
- Slides: 53