Data Sniffing Over Airgaps AVNI SINGH GARIMA MAITHANI











- Slides: 29

Data Sniffing Over Airgaps AVNI SINGH GARIMA MAITHANI

AGENDA What is Airgap? Need for Airgap Attack Vectors Case Studies Mitigation 2


What is Airgap? 4

Remember this scene of the movie: - Mission Impossible 5

Major Applications ✘ Military computer systems and networks ✘ Government computer systems and networks ✘ Financial computer systems and networks ✘ Industrial control systems ✘ Life-critical systems 6

How secure is it? ? 7

8

Airgap Attack Vectors Magnetic Physical Media Acoustic Thermal Electromagnetic Light 9

EXFILTRATION THROUGH PHYSICAL MEDIA 1. 2. 3. Oldest form USB Flash drives Most common and well known example is Stuxnet 10

ACOUSTIC COVERT CHANNEL 1. ACOUSTIC: The term means hearing. 2. Noise emitted by computers (Printers, cooling fans, capacitors at keyboard, etc. )

ELECTROMAGNETIC COVERT CHANNEL • • • Few common examples are: - Airhoppers and GSMem It’s the most common channel known. Bell Labs originally noted this vulnerability back in WWII when Bell Telephone provided the military an encryption device called a 131 -B 2. They had one working in their laboratories when, by accident, someone noticed that each time the machine stepped, a spike would appear on an oscilloscope in a distant part of the lab. They studied these spikes more carefully and found out that they could read the plain text of the message being ciphered by the machine. 12

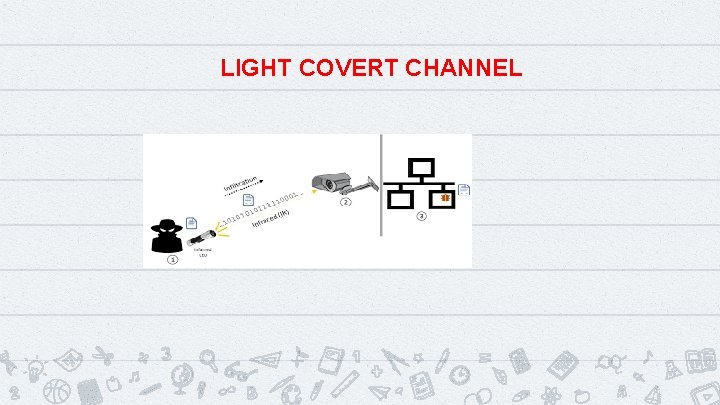
LIGHT COVERT CHANNEL

THERMAL COVERT CHANNEL 1. 2. 3. All electronic devices generate excess heat and require thermal management to improve reliability and prevent premature failure. Computers are no exception. This is usually done with fans and we’ve already seen how they can be abused to provide an exfiltration channel. Changes in temperature are shown to be an effective, albeit painfully slow, data channel. 14

CASE STUDY 1 Sniffing data of an HDMI cable through RF leaks 15

Tools required Software • SDR# • Tempest. SDR Hardware • Antenna: Hack. RF One/Yard Stick One/ RTL SDR 16

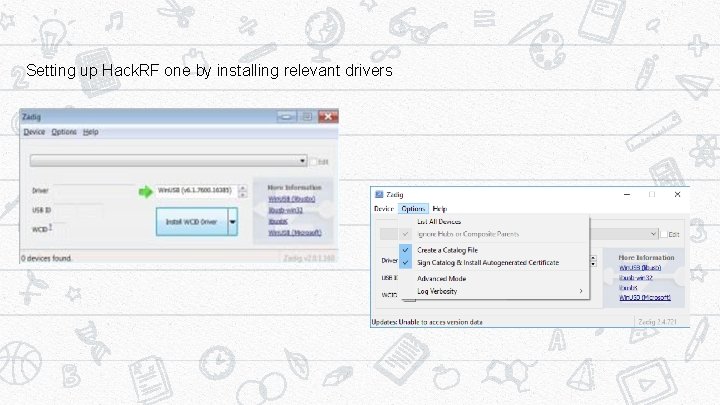
Setting up Hack. RF one by installing relevant drivers 17

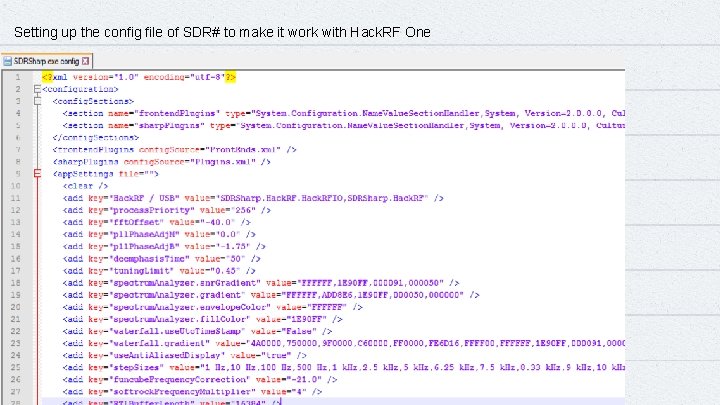
Setting up the config file of SDR# to make it work with Hack. RF One 18

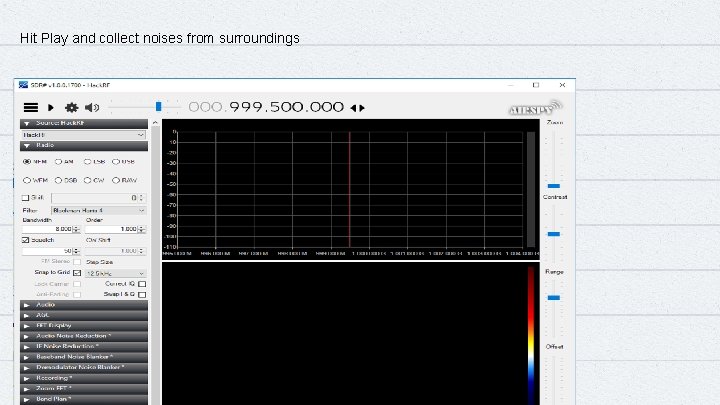
Hit Play and collect noises from surroundings 19

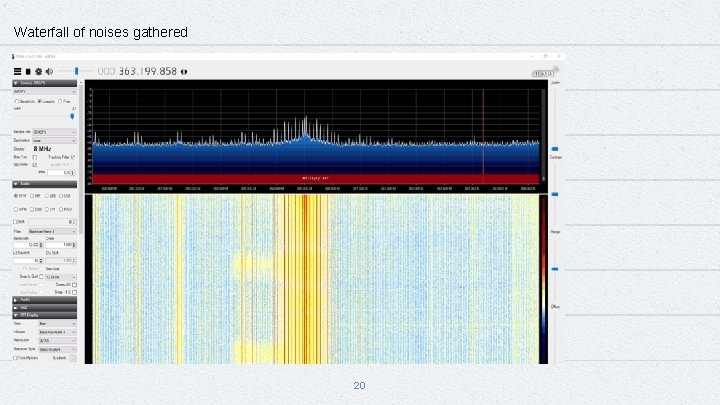
Waterfall of noises gathered 20

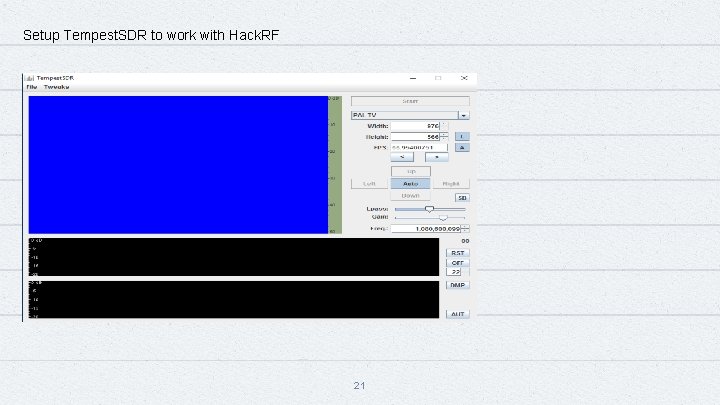
Setup Tempest. SDR to work with Hack. RF 21

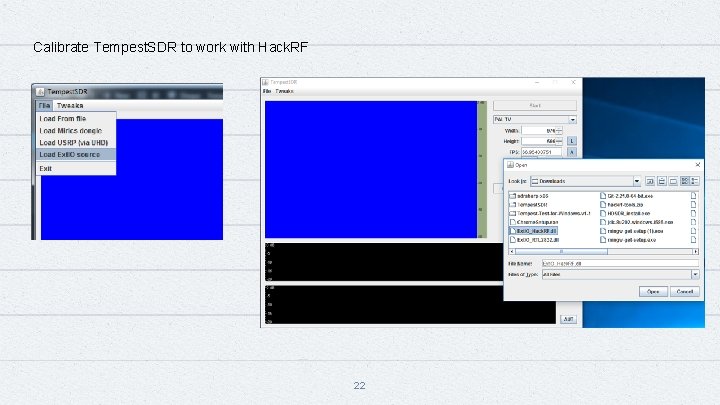
Calibrate Tempest. SDR to work with Hack. RF 22

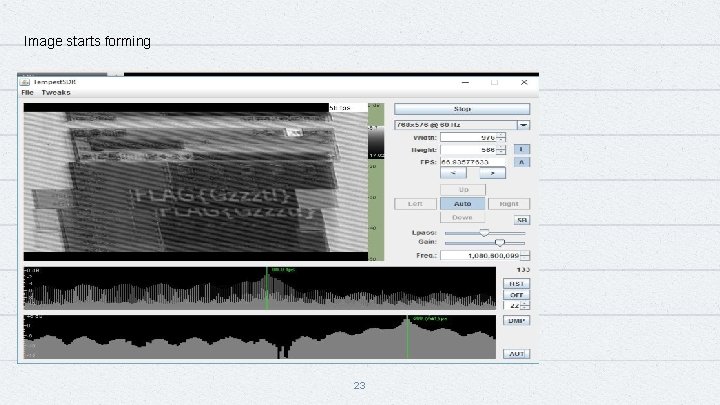
Image starts forming 23

CASE STUDY 2 Sniffing energy levels to guess cryptographic algorithms 24

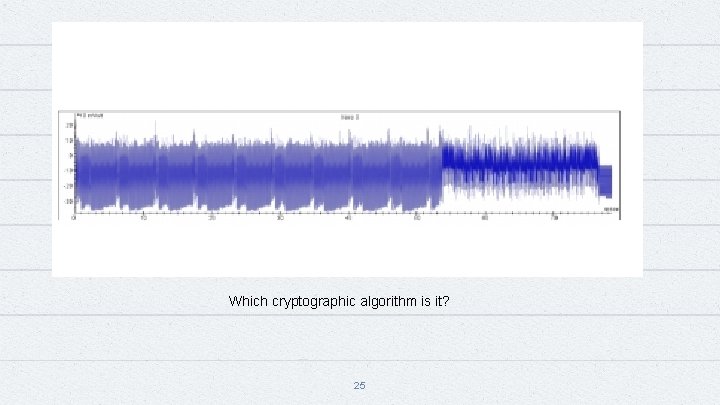
Which cryptographic algorithm is it? 25

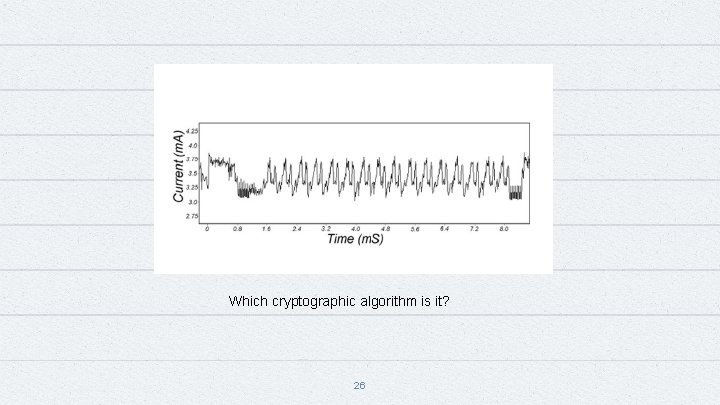
Which cryptographic algorithm is it? 26

Mitigation Techniques • Masking of signal • Faradays cage like setup • Shielding mechanisms 27

THANKS! Any questions? You can find us at Linkedin Profile: -Garima Maithani Twitter Handle: - @avnisingh_s 28

References and Credits https: //www. thesslstore. com/blog/air-gapped-computer/ https: //hackaday. com/2017/02/02/hacking-the-aether/ https: //i. blackhat. com/us-18/Wed-August-8/us-18 -Guri-Air. Gap. pdf Anush Swaminathan Stephan Picek : Case study 2 https: //images. app. goo. gl/Hok 2887 Mcs. ZSew 1 a 8 https: //images. app. goo. gl/85 u. Hypj 1 ne 6 za. Axy 6 29