Data Security and Cryptology XI Digital Signature its








































- Slides: 58

Data Security and Cryptology, XI Digital Signature, its’ Infrastructure and Usage in Estonia November 11 th, 2015 Valdo Praust mois@mois. ee Lecture Course in Estonian IT College Autumn 2015

Main Types of Cryptoalgorithms 1. Symmetric cryptoalgorithms or secret-key crypotoalgorithms are traditional (historical) cryptoalgorithms 2. Asymmetric cryptoalgorithms or public-key crypotoalgorithms are widely spread within last 30 years 3. Cryptographic message digests and similar constructions 4. Special-purpose algorithms for proofing, authentication etc

Cryptographic Hash or Cryptographic Message Digest Cryptgraphic hash (krüptoräsi) or cryptographic message digest (krüptograafiline sõnumilühend) or fingerprint or thumbprint is digest with a fixed lenght which is computed from an arbitrary-length message using an one-way function One-way function (ühesuunaline funktsioon) is such a function which is easy comutable but an inverse function is unfeasible (practically uncomputable)

Cryptographic Message Digest: Usage If we have a given message-hash pair and the hash corresponds to the message then we can always sure that the hash is certainly calculated from the given message Main usage of hashes are ensuring the integrity (usually helps public-key algorithm) Practically secure hash functions find a hash which lenght is at least 160 bit (in enhanced security cases 256 bits)

Cryptographic Hash: Usage Main usage of cryptographic hashes are authentication and ensuring of integrity (for example in digital signatures) One of the main reasons of cryptographis hashes’ usage is that public-key cryptoalgorithm is unsuitable for processing of long plaintexts

Cryptographic Message Digest: Principle

Most-Of-Used Hash Functions • SHA-1 – was constructed in 1996 in NSA using the same principles that were earlier used in MD 4 but increasing the security (using longer values). Lenght of hash is 160 bits (20 bytes) • RIPEMD-160 – was constructed in Belgium in early 1990 s. Finds 160 -bit (20 -byte) hash The practically used hash functions must compute at most 160 -bit hash (twice as long hash as was a minimal lenght of practically secure symmetric cryptoalgorithm, i. e. 2 x 80 bits)

Practically Unsecure Hash Functions • MD 2, MD 4 – preseccors of MD 5, made by Ron Rivesti, found 128 -bit hash • MD 5 – made by Ron Rivest in 1980 s. Founds 128 -bit hash (digest) For these hash functions there has been found both collisions and practical breaking expoits. Despite of this fact MD 5 is still unfotunately in use in numerous places

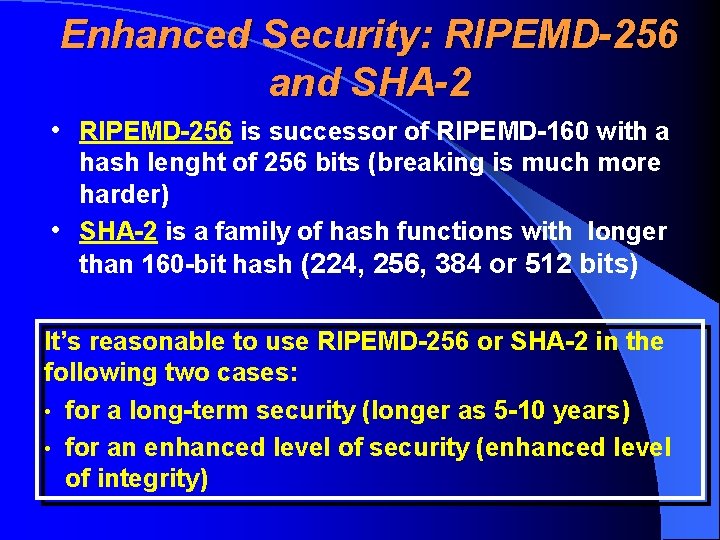
Enhanced Security: RIPEMD-256 and SHA-2 • RIPEMD-256 is successor of RIPEMD-160 with a hash lenght of 256 bits (breaking is much more harder) • SHA-2 is a family of hash functions with longer than 160 -bit hash (224, 256, 384 or 512 bits) It’s reasonable to use RIPEMD-256 or SHA-2 in the following two cases: • for a long-term security (longer as 5 -10 years) • for an enhanced level of security (enhanced level of integrity)

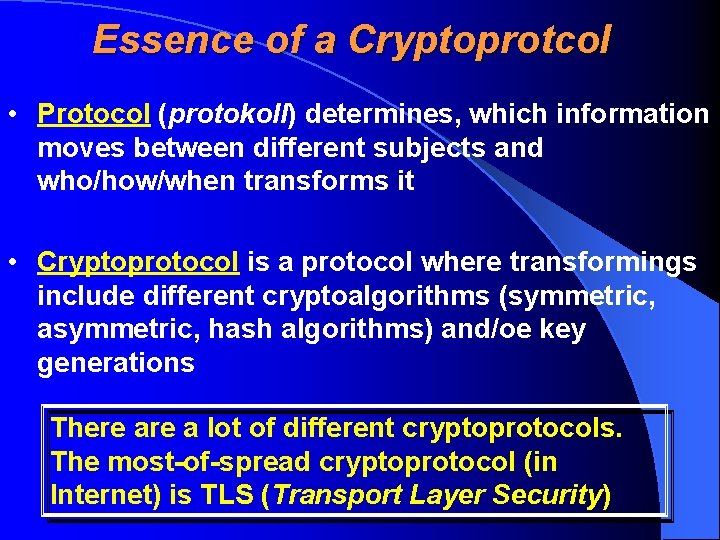
Essence of a Cryptoprotcol • Protocol (protokoll) determines, which information moves between different subjects and who/how/when transforms it • Cryptoprotocol is a protocol where transformings include different cryptoalgorithms (symmetric, asymmetric, hash algorithms) and/oe key generations There a lot of different cryptoprotocols. The most-of-spread cryptoprotocol (in Internet) is TLS (Transport Layer Security)

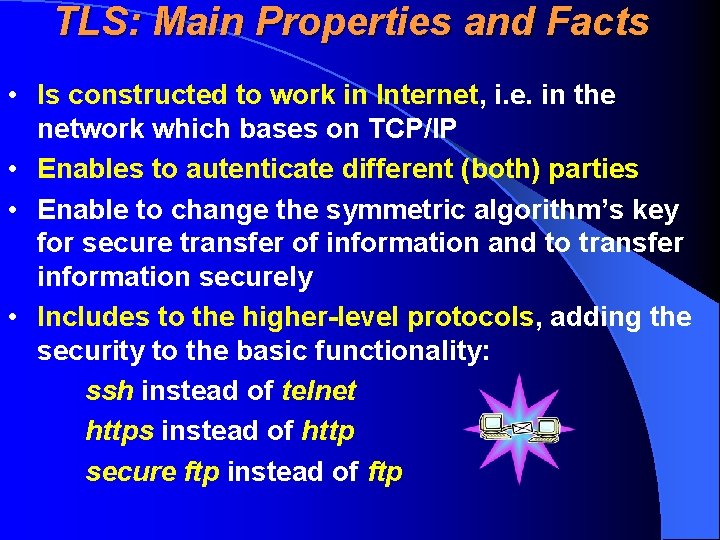
TLS: Main Properties and Facts • Is constructed to work in Internet, i. e. in the network which bases on TCP/IP • Enables to autenticate different (both) parties • Enable to change the symmetric algorithm’s key for secure transfer of information and to transfer information securely • Includes to the higher-level protocols, adding the security to the basic functionality: ssh instead of telnet https instead of http secure ftp instead of ftp

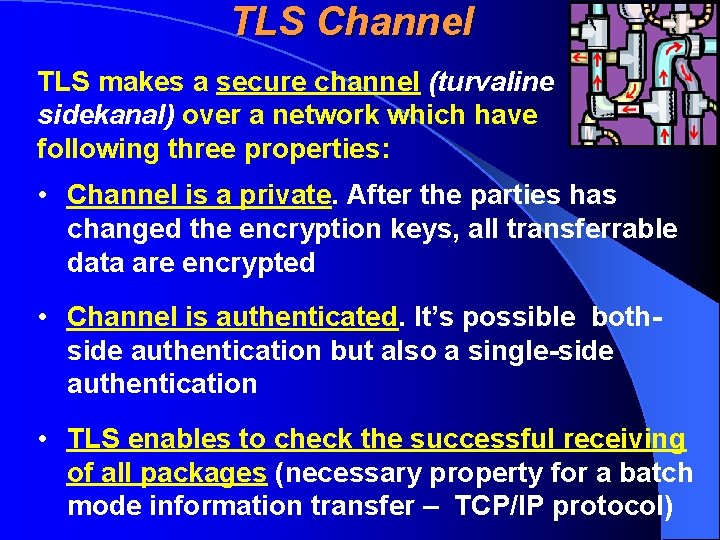
TLS Channel TLS makes a secure channel (turvaline sidekanal) over a network which have following three properties: • Channel is a private. After the parties has changed the encryption keys, all transferrable data are encrypted • Channel is authenticated. It’s possible bothside authentication but also a single-side authentication • TLS enables to check the successful receiving of all packages (necessary property for a batch mode information transfer – TCP/IP protocol)

TLS Security and Problems • If B has his private key and the signed message already sent to A, it’s impossible to masquerade B to A – it is protected by cryptographic algorithms • It’s impossible to eavesdrop the communication between A and B without knowing the secret keys • But there remains a problem: if instead of real B the communication with A was started by a “false B” it can’t be discovered by A This problem cannot be solved only by TLS – it needs some additional resources

Dokcument as a Data Source An organized human activity has based on mediated information called data already in centuries. But in most of cases we need that data can be considered also as documents Documents are such a data, where there are • some (legal) meaning of data • a certain an unchangable relationsahip with data, creator of data and creation time of data Until the late 1990 s a document was synonym of a paper document

Evidentiary Value of a Document is a data where two following conditions are satisfied: • there’s possible to identify the creator of a document (and sometimes also a creation time) • there’s possible to verify that the document has remained unchanged after its’ creation (both occasionally and by the deliberate act) These properties together are called evidentiary value of a document (dokumendi tõestusväärtus) For a creation and preservetion of documents we can’t use any such a method where one or both evidetiary value properties are not satisfied

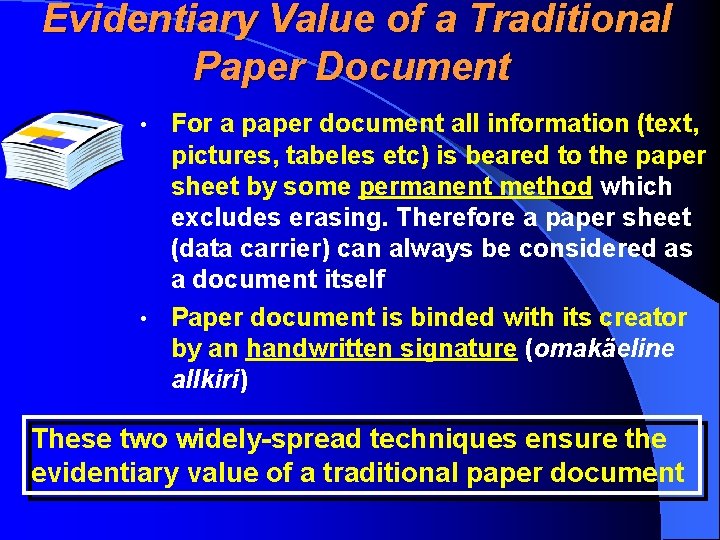
Evidentiary Value of a Traditional Paper Document For a paper document all information (text, pictures, tabeles etc) is beared to the paper sheet by some permanent method which excludes erasing. Therefore a paper sheet (data carrier) can always be considered as a document itself • Paper document is binded with its creator by an handwritten signature (omakäeline allkiri) • These two widely-spread techniques ensure the evidentiary value of a traditional paper document

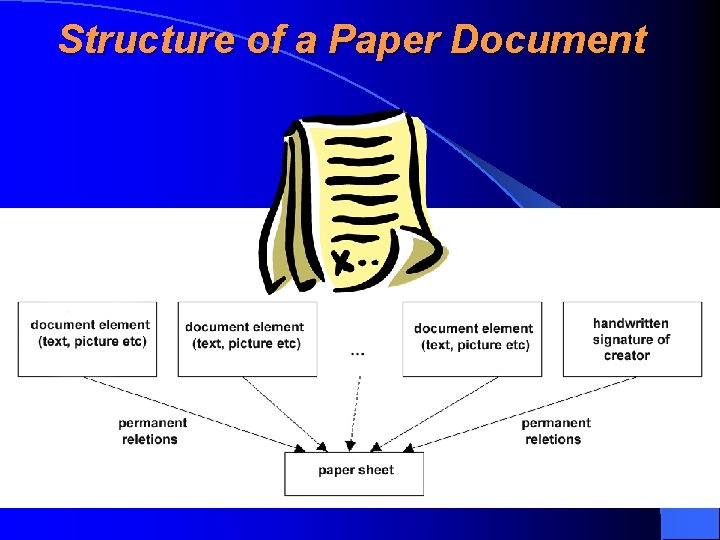
Structure of a Paper Document

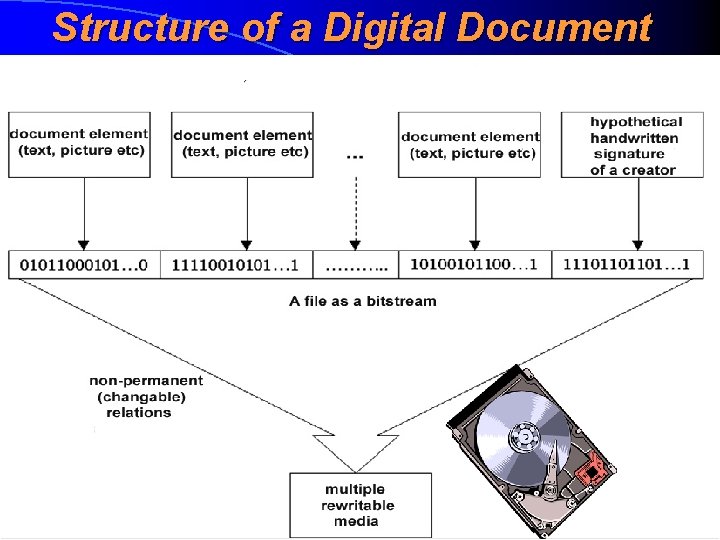
Evidentiary Value of a Digital Document: a Big Problem A fact: a digital information is usually kept and stored in a way which can’t permanently bind data to the data carrier. Multple writable media (hard disks, flash memory etc) are mass-used Conclusion: for a digital documents we can’t use the same methods as we use in paper documents – handwritten signature doesn’t help us because there isn’t any media by which the signature is related. Therefore, we must achieve evidentiary value in a different way

Structure of a Digital Document

Acheiving the Integrity Data integrity (andmete terviklus) is a ensuring that data are originated (information was stored into the data) by a certain subject and haven’t been altered (both occidentially and by a deliberate act) Differently from paper documents the integrity of digital data isn’t a default property: it must be achieved by some special activities (safeguards) Actually only possibility is a using of digital signature (digitaalsignatuur, digisignatuur) which is based on public-key cryptography Bureaucrats speak about evidentiary value, which is higly similar to integrity (used by IT security specialists)

Solution of Integrity for Digital Documents – a Digital Signature When it’s impossible to achieve the integrity (evidentiary value) on the level of data carrier, the only possibility is to use a technique which bind the data itself to the creator using mathematical relationships Actually this technique is called digital signature (digitaalallkiri, digiallkiri) which is up to present the only way, how we can ensure the provable integrity under the multiple rewritable media paradigm

Technical and Legal Views to Digital Signature A legal digital signature (digitaalallkiri, digiallkiri) is a legal concept which gives the document an evidentary value as handwritten signature gives such a value to paper-based document A technical digital signature (digitaalsignatuur, sigisignatuur) is a technical or cryptotechnical construction which uses public-key cryptoalgorithm for achieving the integrity • Up to present the only known way for giving a legal digital signature is a using of technical digital signature • Each legal digital signature is (up to present) a technical digital signature. But each technical digital signature isn’t of course a legal digital signature – it needs some authorities called public key infrastructure

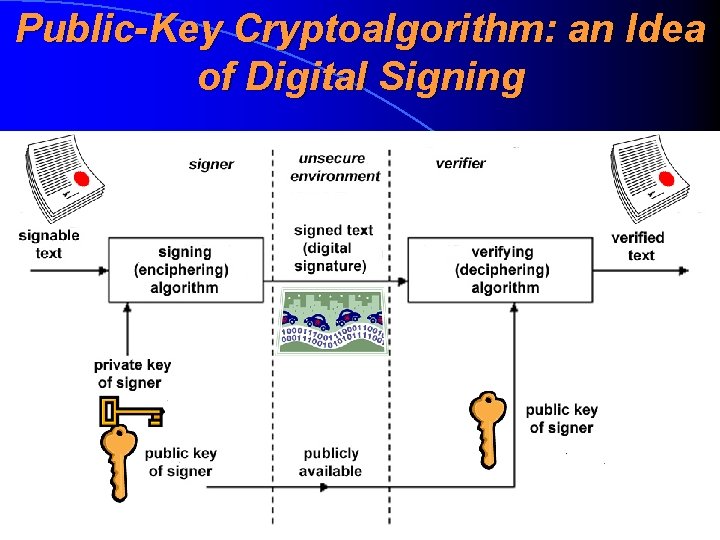
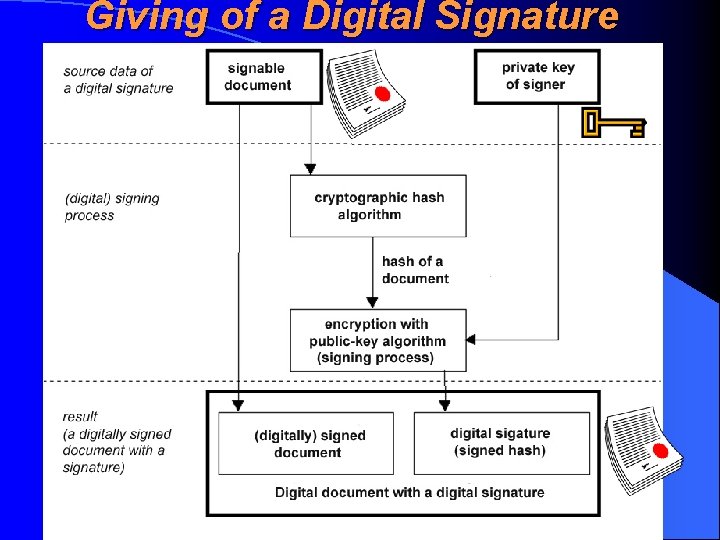
Essence of (Legal) Digital Signature (A legal) digital signature (digitaalallkiri, digiallkiri) is an additional data set which is added to signable document (signable data set) and which is created by a signer (allkirjastaja) using both the signable document and a private key of a signer and is performed by mathematical operations Digital signature uses the methods offered by a public-key cyrpotialgorihm (its use in digital signature or integrity acheiving mode)

Public-Key Cryptoalgorithm Public-key cryptoalgorithm (avaliku võtmega krüptoalgoritm) or asymmetric cryptoalgorithm (asümmeetriline krüptoalgoritm) uses two keys – if we encrypt by one key, we can decrypt it later by another key These keys are generated by a mathematical algrothm and are mathematically related to each other but there’s impossible in practice (infeasible) to found from public key to private key

Public-Key Cryptoalgorithm: Keys of public-key cryptoalgorithm are called usually public key and private key (avalik võti ja privaatvõti) • Public key is usually known for all parties (is public) • Private key is usually known or can be used only by a keypair owner (for a legal digital signature case by a signer)

Public-Key Cryptoalgorithm: an Idea of Digital Signing

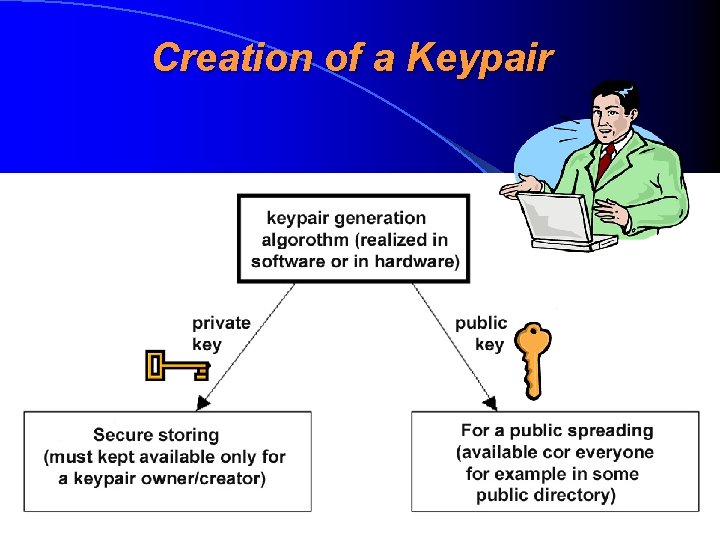
Giving of a Digital Signature In order to give a digital signature, the signer must have earlier-generated public-key cryptoalgorithm keypair (avaliku võtmega krüptoalgoritmi võtmepaar), which consists of: private key (privaatvõti, isiklik võti) • public key (avalik võti) • Both keys are digital data sets (bitstreams) Digital signature, which is given by a private key, is verifiable by the corresponding public key

Creation of a Keypair

Cryptographic Hash or Cryptographic Message Digest Cryptgraphic hash (krüptoräsi) or cryptographic message digest (krüptograafiline sõnumilühend) is digest with a fixed lenght which is computed from an arbitrary-length message using an one-way function This is a one-way relation (ühesuunaline seos) - for a given digest it’s impossible to restore the message Conclusion: if digest corresponds to message we can be always sure that the digest is computed just from the given message

The Role of Hash in Digital Signatures Digital signature is usually given to hash of a document, not to an original (long) document This is necessary, because the public-key algorithm is unsuitable for encryption of long messages (it works thousands times slower than a typical symmetric algorithm) Because it’s impossible to (re)construct a message using a hash, then the digital signature, which given to hash, is as good as a digital signature which is given to an original document (in the mean on integrity)

Giving of a Digital Signature

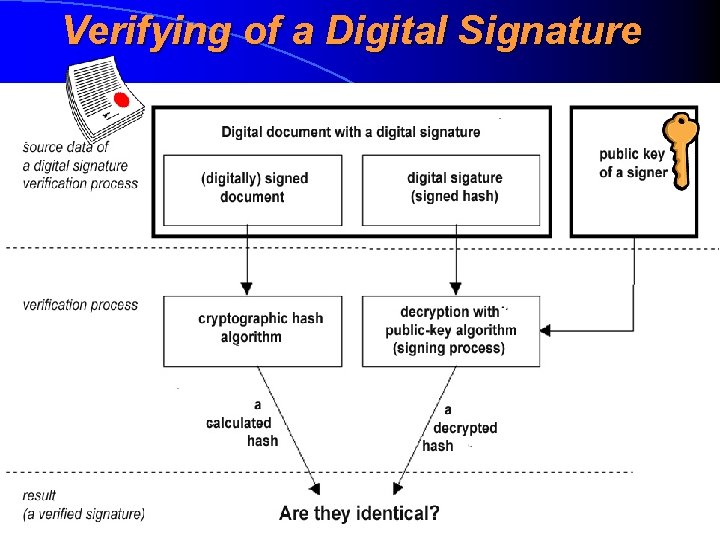
Verifying of a Digital Signature

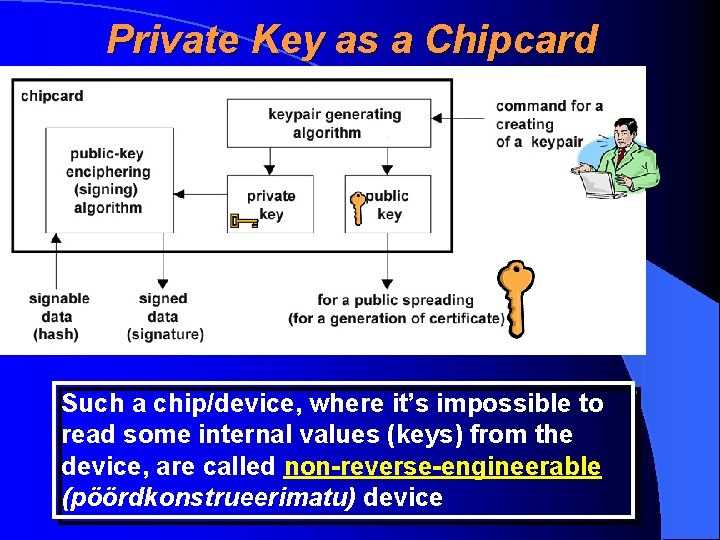
Private Key and its Usage Everyone, who has a private key of a signer can give unauthorizedly a digital signature of a signer Therefore we must keep private key extremly carefully preventing its unauthorized usage and spread The sufficiently secret way is to generate and use the public key in a special hardware device, for example in a chipcard (kiipkaart) consisting both a key generation and encryption algoritms and having possibilites of private key usage only inside the chip and unability to read private key outside the chip Estonian ID-Card and Mobile ID-Card are both such a cryptographic chipcards

Private Key as a Chipcard Such a chip/device, where it’s impossible to read some internal values (keys) from the device, are called non-reverse-engineerable (pöördkonstrueerimatu) device

A Necessity for a Certification Service Above-mentioned technique allows to bind a document to the public key (keypair) of a signer We are interested in binding a document with a signer as a physical person whith his/her name, personal or national idenfication number (isikukood) etc. Solution: we must additionally (previously) to bind the personal identification data of signer to the public key of a signer

Principles of Certification Binding of personal idenfication data (name, personal identification number) to public key is called certification (sertifitseerimine) A result of certification (by the means of digital signature) is a certificate (sertifikaat) which is always a digital document Certificates are usually issued by a special certificartion authorities (CAs, sertifitseerimiskeskus, sertifitseerimisteenuse osutaja)

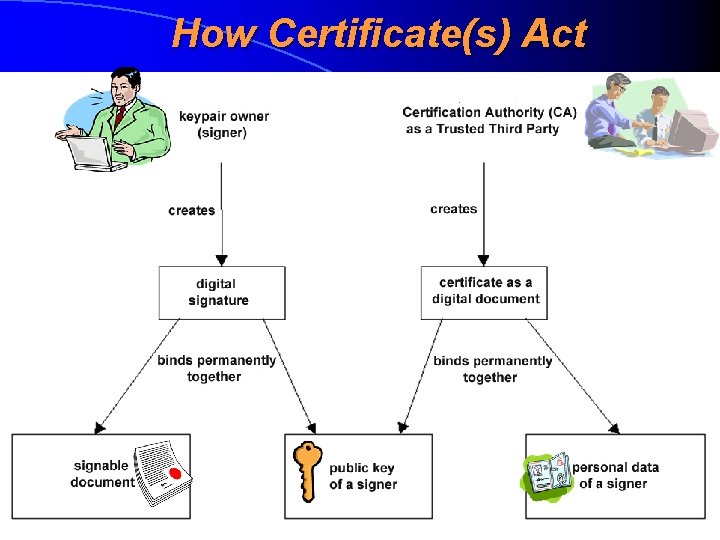
How Certificate(s) Act

Certificate A certificate (sertifikaat) is a digital document created and signed digitally by a certification authority. Certificate typically consists of personal data of signature owner, private key of signature owner and a specific certificate-related data (issuer, expiration date, issuing time etc) Instead of public keys there always spread and used certificates (consisting these keys). For a verification of digital signature it’s always mandatory to have a certificate of a signer

Problems (Necessity for Additional Subjects) We can’t excude the cases when a private key will still appear to the hands of unauthorized persons. In these cases the unauthorized owner of key can produce an unlimited amount of digital signatures Solution: we must allow the revocation of certificates (sertifikaatide tühistamine) Revocation is not so simple. We must ensure that these singatures, which are given before revocation must remain valid, but none of these signatures, which are tried to give after revocation, will became valid

Solution of Certificates’ Revocation Problem We need to acheive the long-time evidence value of signed documents: we must to able prove the evidence even a couple of years or even decades after the hypothetical revocation of corresponding certificates Conclusion: we must add two following techniques to the (legal) digital signature infrastructure: We must add a provable time-stamp to all activies/results (signatures, revocation acts, etc) • We must create a comparison possibility of different time stamps before signature verification (is there any revocation act which time is earlier than a time of a signature? ) •

Time-Stamp Principles Time-stamp (ajatempel) is an additional data set which is added to the original data set. There’s possibility to provably compare the creation time of different timestaps (data sets) Time-stapms are issued by a certain time-stamp authorities (ajatemplikeskused, ajatempliteenuse osutajad) Time-stamp authority calculates the next timestamp from the following sources using one-way funtsion (hash): • from the data (hash), which is sent to timestamp authority • from the previously issued time-stamp

Time-Stamp Principles One-way chaining of sequential time-stamps ensures that there is impossible to change already issued time-stamps and there is impossible to issue new time-stamp between already issued time-stamps • All time-stamps and their’ issuing times and calculating algoroithms are public • Time-stamp was taken from a time-stamp authority immediately after the calculating of the digital signature

Digitally Unsuitable Technique: a Revocation List Certificates’ revocation list (sertifikaatide tühistuslist) is a list kept by a certification authority(-ies), which consists of data of all possible revocations An initial idea was to check each signature against a revocation list online during the each verification of signature Why such a solution is unsuitable?

Shortcomings of Revocation List Technique • Each signature verification needs onlinequery • Revocation list will became a real bottleneck • What will happen with signed documents when certification authority (revocation list) disappear (has been destroyed)? It’s reasonable that signature (document) verification ability always preserves with the document, not in different place or using some different (additional) authorities

A Suitable Technique: Validity of Approval Validity of approal (kehtivuskinnitus) is a query to certification authority which has made immediately after giving a digital signature Validity of approval is stored next to the signature and is (with a corresponding certificate and timestamp) a digital proof that during the signing process the certificate was valid (there’s no revocations in force) When digital signature in equipped with such a validity of approval then it’s possible to verify signature without any online connections. But a sigining process (taking of time-stamp and validity of approval) always needs online connection

Digital Document with Digital Signature with all Necessary Additional Requisites

Certification Infrastructure Certification infrastructure (sertifitseerimise taristu) or public-key infrastructure (PKI, avaliku võtme taristu) consists of five following mandatory components necessary for secure giving and verifying of digital signatures: • non-reverese-engineerably realized hardwarebased public-key container • certification authority (CA) • validity of approval service (at the CA) • time-stamping authority • organization and coordination of services (usually in national level)

Data Format Data format (andmevorming, vorming) — a desciption how different type of information – text, picture, voice, video etc – is coded into the queue of 0’s and 1’s A pre-agreed (standardised) data format gives to data (to data file) a concrete and unique meaning. If we have data but do not have the data format desciption, then we do not have the information, carried by the data

From Data Format to Meaning Different data formats are supported by a different application software, which usually allow to write the file in certain format, or to made the content of data (information) humanperceptable etc. A typical end-user usually don’t know anything about different data formats and interpretation. He/she usually associates the certain format only to the certain software which is able to interpretate these format(s). End user usually receives only an human-perceptable form, prepared by the software, so-calles WYSIWYG (What You See Is What You Get, in Estonian adekvaatkuva)

Demands to the Signable Document Format Digital signature is technically binded to the bitstream, but we sign a documnt with a certain meaning (text, pictures, hypertext etc). Relationship between meaning and bitstream is determined by a used data format (andmevorming) Conclusion: for signing there are suitable onlyu these formats which have a unique meaning and which description is publicly available Recommended formats: PDF, RTF, JPG, GIF. . . Unrecommended formats: DOC, DOCX, XLSX, . . .

Legal Regulation There’s necessary to regulate legally: • conditions of keypairs and their’ generating devices • requirements to certification authorities • requirements to time-stamp authorities • organization and coordination of services When these questions are solved (usually in the level of corresponding National Act) then we can state that digital documents with digital signatures have the same legal status as paber documents with handwritten signatures

Digital Signature in Estonia, I 1. Estonian National Digital Signature Act was adopted in 2000. It defines the conditions, which technical digital signatures (digisignatuurid) are acceptable as a legal digital signatures (digiallkirjad) 2. Time-stamp service is an essential integral part of Estonian legal digital signature

Digital Signature in Estonia, II 3. Both certification and time-stamping authorities are delegated to a private sector 4. State-based organization and coordination is concentrated into National Certification Register which is kept by an Estonian Ministry of Economic Affairs and Communication

Digital Signature and Estonia, III 5. In 2001 there was registrated the first certification authority Sertifitseerimiskeskuse AS. It received also time-stamping license and became a major subject in Estonia in the field of digital signatures. The validity of approvals (OCSPconfirmations) service is charged (for a physical persion up to 10 signatures in one month are free of charge)

Digital Signature and Estonia, IV 6. In 2002 there were issued first Estonian ID-cards. Today more than 95% of Estonian citizens are equipped with such a cards 7. In late 2002 there was introduced the practical digital document format Digi. DOC (file extension. ddoc) which is based on base 64 coding and stores the result in text format

Digital Signatures and Estonia, V 8. During the last ten years the practical usage of digital signatures are spread almost to all categories of documents both in private and public sector 9. In 2007 there were issued first Mobile-ID cards for Estonian biggest cellular phone service provider EMT clients. In 2009 the Mobile-ID project was expanded also for other GSM service providers

Digital Signature and Estonia, VI 10. In 2009 there was introduced a digital stamp (digitempel) – an analogue for a digital signature for a legal entities (companies) 11. In late 2010 there was introduced a digital ID-card (digitaalne isikutunnistus)- a backup ID-card for a physical persons having only a digital part and no visual part (therefore unsuitable to use as a national identity document)

Digital Signature and Estonia, VII 12. In 2010 there was introduced a Digi. DOC 3 standard which uses 2048 bit RSA instead of 1024 bit RSA 13. In 2014 -16 there took place a migration from DDOC format to international standard BDOC (more compact binary compressed files, more possibilites, possibility for new and more strong cryptoalgorithms etc)