Data Security and Cryptology X Hash Functions Cryptoprotocols







































- Slides: 54

Data Security and Cryptology, X Hash Functions. Cryptoprotocols, TLS November 4 th, 2015 Valdo Praust mois@mois. ee Lecture Course in Estonian IT College Autumn 2015

Main Types of Cryptoalgorithms 1. Symmetric cryptoalgorithms or secret-key crypotoalgorithms are traditional (historical) cryptoalgorithms 2. Asymmetric cryptoalgorithms or public-key crypotoalgorithms are widely spread within last 25 -30 years 3. Cryptographic message digests and similar constructions 4. Special-purpose algorithms for proofing, authentication etc

Public-Key Cryptoalgorithm Public-key cryptoalgorithm (avaliku võtmega krüptoalgoritm) or asymmetric cryptoalgorithm (asümmeetriline krüptoalgoritm) uses two keys – if we encrypt by one key, we can decrypt it later by another key These keys are generated by a mathematical algrothm and are mathematically related to each other but there’s impossible in practice to found from one key another

Public-Key Cryptoalgorithm: Keys of public-key cryptoalgorithm are called usually public key and private key (avalik võti ja privaatvõti) • Public key is usually known for all parties (is public) • Private key is usually known only by a subject or a keypair owner (people, software, server, company, chipcard etc)

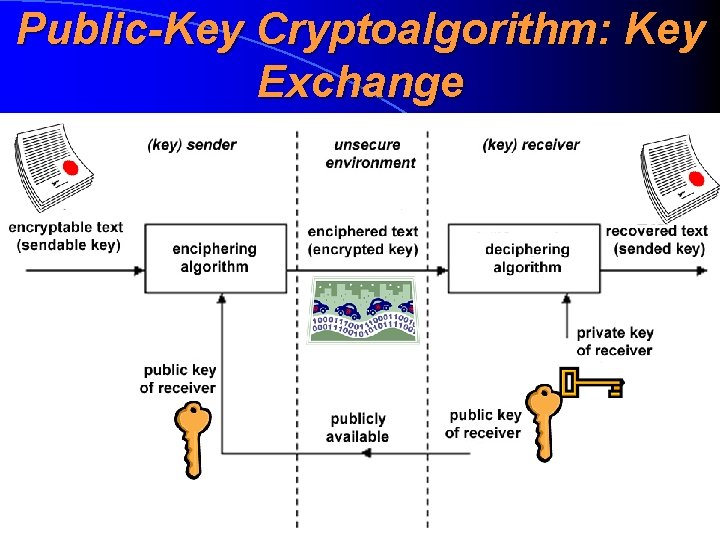
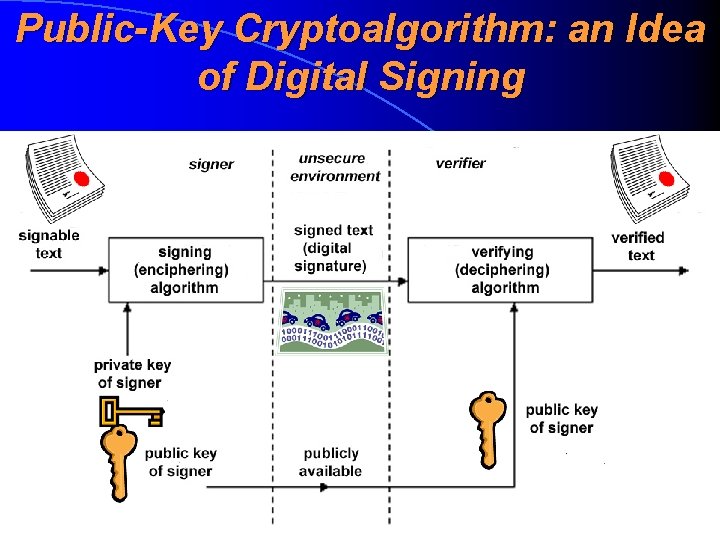
Public-Key Cryptoalgorithm: Usage • For a key exchanging purposes. We can transmit a symmetric cryptoalgorithm’s key in an encrypted manner without any tamperproof channel. We only need that a public key must be really public • For ensuring the integrity. This is the main usage of public-key cryptoalgorithm (and even the main field of contemporary cryptography) • Public-key crryptoalgorithm gives a basic idea of a digital signature (digisignatuur, digiallkiri)

Public-Key Cryptoalgorithm: Key Exchange

Public-Key Cryptoalgorithm: an Idea of Digital Signing

Most-of-Spread Public-Key Cryptoalgorithm: RSA The most-of-spread public-key cryptoalgorithm is RSA is considered to be practically secure with no less than 1024 -bit keylenght, for a long-time security there’s preferred 2048 -bit keylenght For RSA it is easy to calculate the public key from private key, but it’s practically impossible (infeasible) to calculate the private key from public key Public and private key are mathematically related to each other, but finding the private key from public key needs million years or more

Specificies of RSA • Was invented by Rivest, Shamir and Adleman in 1978 • Security of RSA is based on a fact that factorization of a number with big factors is an infeasible (practically unsolvable) task • Ensures practical security, doesn’t ensure theoretical security • Breaking usually needs millions of years (depending on keylenght) • Is very widely spread in all around the world • (most-of-spread public-key algoroithm)

RSA: Practical Details of Algorithm • For finding of an appropriate e there also some tests which ensure that it will relatively prime with (p 1)(q-1) • Greater common factor can be checked by an Euklidean algorithm • Other calculations (enciphering and deciphering) is a question of realising of modular arithmetics (can be done fast both in hardware and software)

RSA: Practical Properties • Enciphering and deciphering which use modular arithmtics are quite fast • Despite of these fact the RSA is slower from symmertrial algroithms (AES, IDEA, Blowfish etc) some thousand times • Keypair generation is much more slower from enciphering/deciphering. However, it can be realized even in software within a couple of seconds

Secure Usage of RSA • RSA supports any keylenght (lenght of pq) • RSA is considered to be practically secure from 1024 -bit keylenght, for a long-term security from 2048 -bit keylenght • Most-of-used values of keylenght are (512, 768), 1024, 2048 and 4096 bits (two first of them are already practically insecure) • 1024 -bit key: there’s a composite number of 310 decimal digits which has two 155 -digit prime factors

Practical Aspects of RSA • Has been for a long time patented in U. S. . Patent #4, 405, 829 was issued in September 20 th, 1983 • Patent has expired after 17 years, i. e. in 2000 • Description of algorithm is public, also a couple of different software realizations (some of them with a source code) • Hardware realizations are usually hundreds of times faster than software realizations

Collaboration of RSA with Symmetric Cryptoalgoriothms RSA is unsuitable for the encrytion of long plaintexts • If we use RSA for a key exchange purpose, we must only encrypt the symmetric algorithm key • If we use RSA for a digital signature (integrity) purposes then it was always used together with cryprographic hash algorithms. Therefore, only hash value is actually encrypted (signed) by RSA

Cryptographic Hash or Cryptographic Message Digest Cryptgraphic hash (krüptoräsi) or cryptographic message digest (krüptograafiline sõnumilühend) or fingerprint or thumbprint is digest with a fixed lenght which is computed from an arbitrary-length message using an one-way function One-way function (ühesuunaline funktsioon) is such a function which is easy comutable but an inverse function is unfeasible (practically uncomputable)

Cryptographic Message Digest: Usage If we have a given message-hash pair and the hash corresponds to the message then we can always sure that the hash is certainly calculated from the given message Main usage of hashes are ensuring the integrity (usually helps public-key algorithm) Practically secure hash functions find a hash which lenght is at least 160 bit (in enhanced security cases 256 bits)

Cryptographic Hash: Usage Main usage of cryptographic hashes are authentication and ensuring of integrity (for example in digital signatures) One of the main reasons of cryptographis hashes’ usage is that public-key cryptoalgorithm is unsuitable for processing of long plaintexts

Cryptographic Message Digest: Main Principle

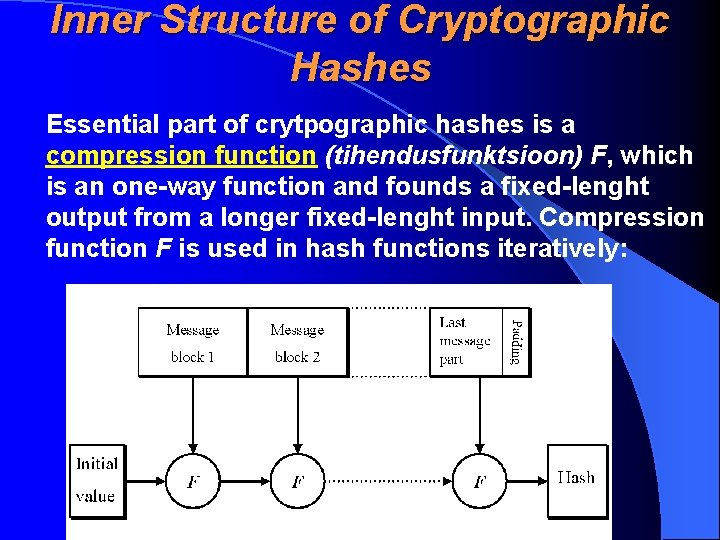
Inner Structure of Cryptographic Hashes Essential part of crytpographic hashes is a compression function (tihendusfunktsioon) F, which is an one-way function and founds a fixed-lenght output from a longer fixed-lenght input. Compression function F is used in hash functions iteratively:

Mandatory Properties of Message Digest (Hash Function) • Any (minor) change of message must cause a full changing of a digest • Digest must be easily computable (as a typical symmetric cryptoalgorithm) • Hash function must be a one-way function: for a given digest is must be infeasible to find any corresponding message which gives this digest • For a pair message-digest the computing of second preimage must be infeasible (hash function must be weakly collision-free) • There must be infeasible to find any such a message pairs which give the same digest (hash function must be collision -free) • Compression function F must be collision-free (hash function must be pseudo-collision-free)

Birthday Paradox: a probability that for N people the birthdays of two different people coincide, will grow proportionally with N 2 or will grow quite fast Reason: adding of a new people will add pairs of new people from previous people For N people there are N 2 – N different pairs For N=23 the probability is already greated than ½

Inbfluence of Birthday Paradox to Hash Functions Conclusion from Birthday Paradox: if the output of hash function is N-bit long, then the probability, that K trials will give two identical hashes is K = 1, 17 2 N/2 The simplest cryptanalytic attack (socalled exhaustive search for hash functions) of N-bit hash function needs a considering of 2 N/2 different variants

Most-Of-Used Hash Functions • SHA-1 – was constructed in 1996 in NSA using the same principles that were earlier used in MD 4 but increasing the security (using longer values). Lenght of hash is 160 bits (20 bytes) • RIPEMD-160 – was constructed in Belgium in early 1990 s. Finds 160 -bit (20 -byte) hash The practically used hash functions must compute at most 160 -bit hash (twice as long hash as was a minimal lenght of practically secure symmetric cryptoalgorithm, i. e. 2 x 80 bits)

Practically Unsecure Hash Functions • MD 2, MD 4 – preseccors of MD 5, made by Ron Rivesti, found 128 -bit hash • MD 5 – made by Ron Rivest in 1980 s. Founds 128 -bit hash (digest) For these hash functions there has been found both collisions and practical breaking expoits. Despite of this fact MD 5 is still unfotunately in use in numerous places

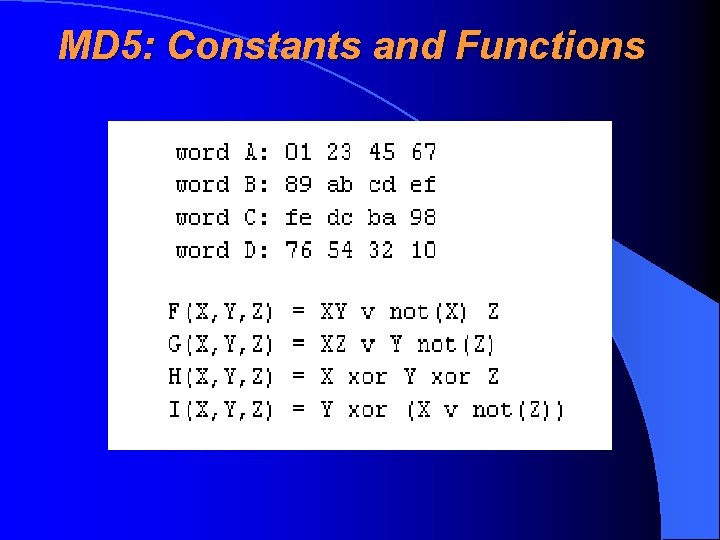
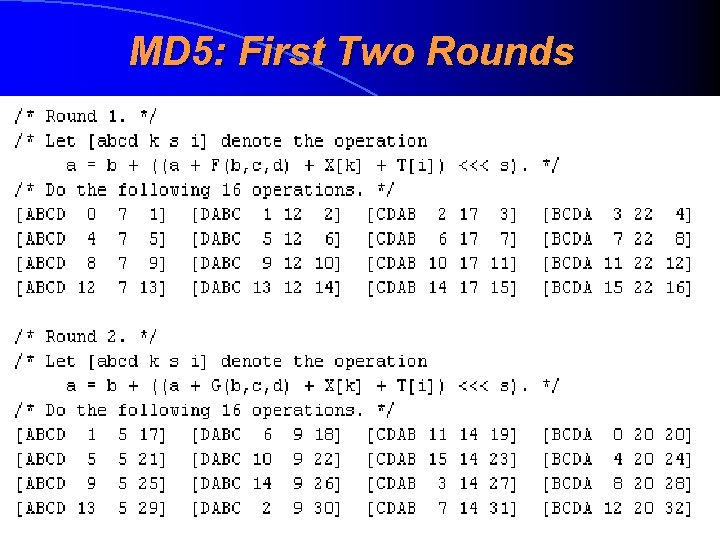
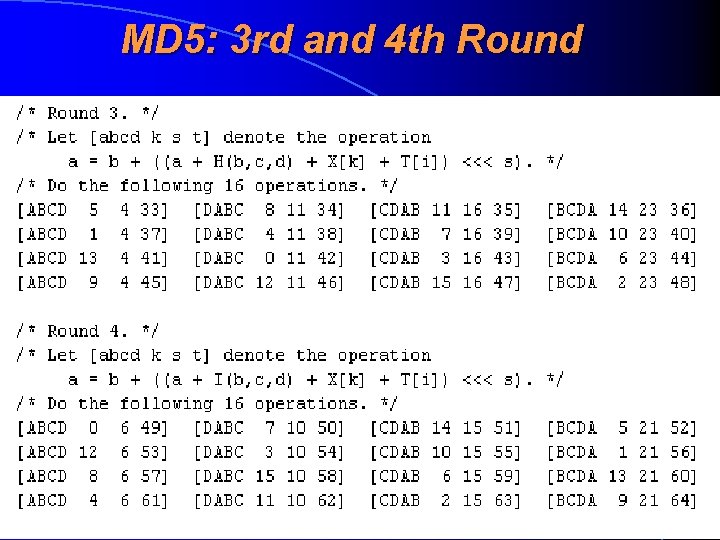
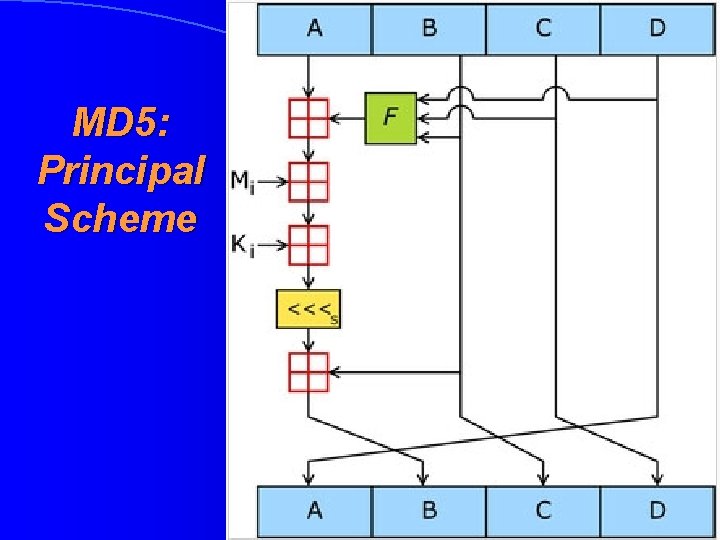
MD 5: Detailed Overview • Hash lenght is 128 bits (16 bytes) • Was constructed by Ron Rivest in 1991 • Consists of four different rounds (raund), which process the message by the 512 -bit portions • During each round there was taken the result of previous round and it is “mixed” to the next 512 bits of message

MD 5: Constants and Functions

MD 5: First Two Rounds

MD 5: 3 rd and 4 th Round

MD 5: Principal Scheme

MD 5: Security and Analysis • 128 -bit hash is too short regarding of Birthday Attack (must be at least 160 bits) • In 1993 there were found collisions for a compression function (Boer, Bosselaers) • In 2004 there were found collisions for a full algorithm (Wang, Feng, Lai, Yu, one hour for host computer) • In 2005 there was succeeded a practical breaking of signatures based on MD 5 (Lenstra, Wang, Weger) • In 2006 collisions were able to construct within one minute (Klima)

MD 5: Use in Emegrency Situations For an emergency situations, a temporary usage of MD 5 is allowed only in the following cases: • In a key strengthening mode (võtmetugevdus) – hash function is used twice in a row. In makes attacking time much more longer • Salting (soolamine) of passwords and keys – before using a hash function some random bitstream (socalled salt) is added. It makes dictionary attacks (sõnastikründed) must more difficult to realize However, even in these cases it is not guaranteed that hash functions will be not broken at the nearest future – it is recommended to use SHA-1 or RIPEMD-160

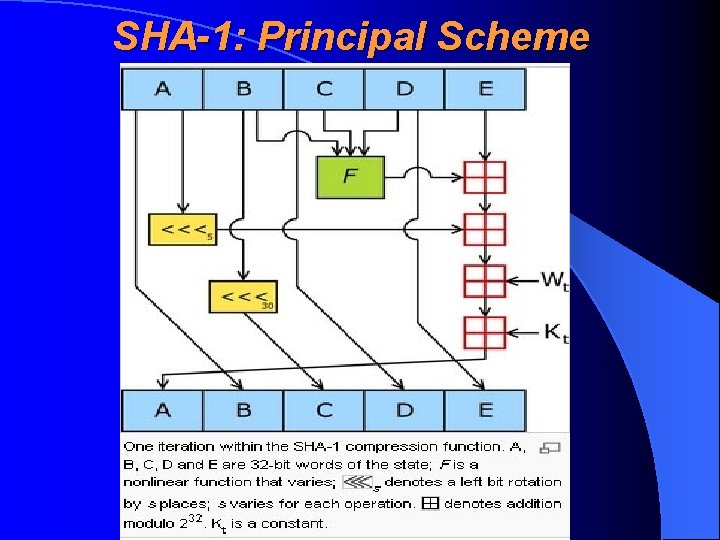
SHA-1: General Description • Is structurally similar to MD 5 • Was constructed in 1996 by modifying the MD 4 making its’ procedures longer and more secure • Lenght of hash (digest) is 160 bits or 20 bytes • Has four rounds. For each round there was taken the result of previous round and it was “mixed” to the next part of message using special functions

SHA-1: Principal Scheme

SHA-1: Security and Appliability • Is much more secure than MD 5 • Has very widely used (about 80% of all hash functions usages in AD 2013) • The Breaking Machine which costs some million euros, can calculate collision of SHA 1 within thousands of years • Is a part of ANSI X. 90 standard • Is mathematically almost identical with SHS (Secure Hash Standard), which has specified in U. S. standard FIPS PUB 180

SHA-1 Cryptanalysis Last result (Mac. Donald, Hawkes, Piperzyk 2009): SHA-1 collisions can be found by 251 variants, which is millions times less that by exhaustive search • However, the actual collisions have not yet found • If the collisions can be practically calculated, it doesn’t authomatically make SHA-1 practically breakable because it needs practical invertability • For enhanced security places is recommended longer and more secure versions of SHA: SHA 256, SHA-384 or SHA-512 (common name SHA-2)

Retrospectical View: MD 2 and MD 4 • Was construced by Ron Rivest correspondingly in 1989 and 1990 • Are similar with MD 5 both by the inner structure (rounds, periodical calulation) and by the hash length (128 bits) • Collisions are found already in 1994 -95 for both algorithms. For MD 4 collisions are computable by an ordinary PC within a couple of seconds Conclusion: MD 2 and MD 4 are unsuitable for a practical use

RIPEMD-160: An Overview • Is constructed in early 1990 s by Hans Dobbertin, Antoon Bosselaers and Bart Preneel • Computes a 160 -bit (20 -byte) hash (digest) • Inner structure is quite similar with MD 5 and SHA-1 (number of rounds is five, i. e. bigger) • There exist some modifications of RIPEMD family: RIPEMD-128 (precessor of RIPEMD 160 e), RIPEMD-160, RIPEMD-256 and RIPEMD 320, with a 128 -, 160 -, 256 - and 320 -bit hash correspondingly

RIPEMD: Security • RIPEMD-128 isn’t considered no more secure. In 1994 Paul van Oorschot and Mike Wiener offered a plan of a Breaking Machine which costed 10 millions ofeuros and which was able to break algorithm within one month • Today such a machine costs less than 300 000 euros (according to Moore’s rule) • In 2004 there was practically found a collision of RIPEMD-128 • RIPEMD-160 is considered to be secure at least next 5 years, higher versions of RIPEMD presumably much longer (10 -20 years)

Enhanced Security: RIPEMD-256 and SHA-2 • RIPEMD-256 is successor of RIPEMD-160 with a hash lenght of 256 bits (breaking is much more harder) • SHA-2 is a family of hash functions with longer than 160 -bit hash (224, 256, 384 or 512 bits) It’s reasonable to use RIPEMD-256 or SHA-2 in the following two cases: • for a long-term security (longer as 5 -10 years) • for an enhanced level of security (enhanced level of integrity)

Practical Usage of Hash Functions • Are used for ensuring of integrity both with and without public-key cryptoalgorithms • Are important components of digital signatures and time stamps Result: instead of ensuring of integrity of long files (messages) we can ensure integrity only of one short (160 -bit or 256 -bit) hash which is practically much more simple in many cases

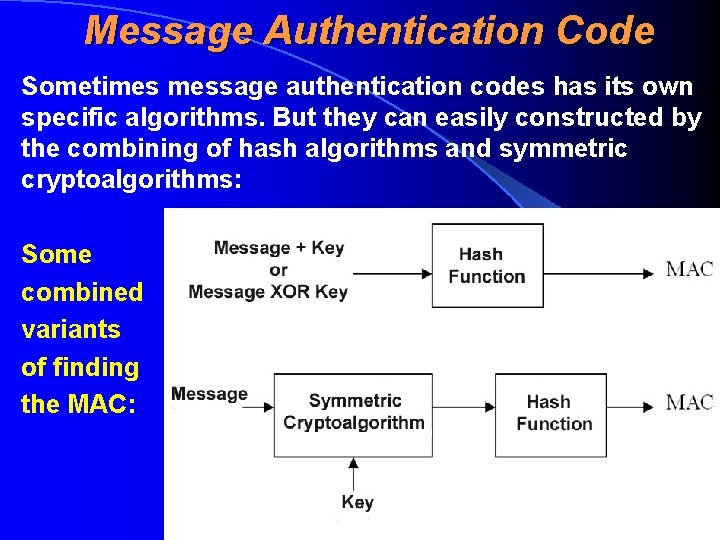
Message Authentication Code Message authentication code, (MAC, sõnumi autentimiskood) is so-called hash function with a key, where both computing and verifying of a hash needs beside the message also the knowing of a certain secret key • Is a necessary replacement of an hash function, when it’s needed to limit the subjects who can authenticate/verify the message by the owners of a key • Differs from public-key cryptoalgorithm by the fact, that the both computing and verfying processes for a MAC can be performed with the same key

Message Authentication Code Sometimes message authentication codes has its own specific algorithms. But they can easily constructed by the combining of hash algorithms and symmetric cryptoalgorithms: Some combined variants of finding the MAC:

Essence of a Cryptoprotcol • Protocol (protokoll) determines, which information moves between different subjects and who/how/when transforms it • Cryptoprotocol is a protocol where transformings include different cryptoalgorithms (symmetric, asymmetric, hash algorithms) and/oe key generations There a lot of different cryptoprotocols. The most-of-spread cryptoprotocol (in Internet) is TLS (Transport Layer Security)

TLS: Main Properties and Facts • Is constructed to work in Internet, i. e. in the network which bases on TCP/IP • Enables to autenticate different (both) parties • Enable to change the symmetric algorithm’s key for secure transfer of information and to transfer information securely • Includes to the higher-level protocols, adding the security to the basic functionality: ssh instead of telnet https instead of http secure ftp instead of ftp

TLS Channel TLS makes a secure channel (turvaline sidekanal) over a network which have following three properties: • Channel is a private. After the parties has changed the encryption keys, all transferrable data are encrypted • Channel is authenticated. It’s possible bothside authentication but also a single-side authentication • TLS enables to check the successful receiving of all packages (necessary property for a batch mode information transfer – TCP/IP protocol)

TLS: Main Principles Under TLS connection there can be distinguished two phases: • handshaking phase (autentimisfaas) • message transferring phase The connection is considered to perform between two unequal parties, a client and a server It’s mandatory to authenticate the server. Authentication of a client is voluntary (as it needed)

TLS Handshaking, I By a little simplified view it includes the following activities (client A starts to communicate with server B): • A says “Hello” to B and mentions which cryptoalgorithms he/she can use • A demands from B, that B proves that he is B amd sends a generated nonse to B • B writes a text “I am B” and makes from it a hash or message digest hash(“I am B” + nonse) • B signes hash with his/her private key sigb (hash(“I am B” + nonse))

TLS Handshaking, II • B sends to A his public key (certificate), a text “I am B” and a signature sigb (hash(“I am B” + nonse)) • A, receiving these data, verifies the signature, ensuring that his/her communication partner is realy B. A puts the public key of B to his directory • Therefore, client A has authenticated server B • If it’s necessary, B can authenticate A by a similar way (if the both-side authentication is needed)

TLS Handshaking, III • A generates a symmetric cryptoalgorithm’s key (primary key) K, and puts it in his directory. A encrypts K with public key of B and sends it in encryped form to B • B deciphers the primary key K with his private key and stores it into his directory • Therefore, handshaking phase is ended and a corresponding symmetric algorithm key is stored by the both parties

TLS: Communication Phase Presumption: A and B start to communicate and ensure that handshaking phase has already performed earlier and the corresponding primary key K is already stored into their’ directories. • A generates a session key S, encrypts it by a primary key K and sends the encrypted key to B • B deciphers the session key S by the stored primaty key K • All communication between A and B is performed by encrypted form using a session key S

SSL versus TLS (Transport Layer Security) is a successor of SSL, where numerous disadvantages are eliminated • Last version, TLS 1. 2, is specified in detail in RFC 5246 (August 2008) In comparison with SSL 3 some weaknesses are repaired • For SSL 1 and SSL 2 there are some serious disadvantages discovered – in practice their usage is refused •

TLS Security and Problems • If B has his private key and the signed message already sent to A, it’s impossible to masquerade B to A – it is protected by cryptographic algorithms • It’s impossible to eavesdrop the communication between A and B without knowing the secret keys • But there remains a problem: if instead of real B the communication with A was started by a “false B” it can’t be discovered by A This problem cannot be solved only by TLS – it needs some additional resources

TLS: Opportunities and Applicability SSL/TLS is able without the certificates and its’ infrastructure to ensure that the other party of transferring phase is the same that was other party for handshaking To prove some information about ohter party during handshaking there’s necessary to have some additional information – usually it is in a form of certificate (sertifikaat) of other party. A certificate is signed by a trusted third party (usaldatav kolmas osapool)

Other Cryptoprotocols • • • DNSSEC (Domain Name System Security Extensions) – replaces ordinary (unsecure) DNS IEEE 802. 11 – wireless local area protocol IPSec (IP Security Protocol) S/MIME (Secure MIME) – replaces ordinary (unsecure) mail service SSH (Secure Shell) – secure remote access. . . etc. . .