Data Security and Cryptology VIII Other Symmetric Cryptoalgorithms































- Slides: 68

Data Security and Cryptology, VIII Other Symmetric Cryptoalgorithms (beyond AES) October 21 st, 2015 Valdo Praust mois@mois. ee Lecture Course in Estonian IT College Autumn 2015

Main Types of Cryptoalgorithms 1. Symmetric cryptoalgorithms or secret-key crypotoalgorithms are traditional (historical) cryptoalgorithms 2. Asymmetric cryptoalgorithms or public-key crypotoalgorithms are widely spread within last 30 years 3. Cryptographic message digests and similar constructions 4. Special-purpose algorithms for proofing, authentication etc

Secret-Key Cryptoalgorithm: Fields of Use • transmitting of confidential information using some (interceptable) networks • secure storing of confidential information (with an appropriate key management system) • secure erasing of confidential data • generating a secure white noise (keys of cryptoalgorithms’ etc. )

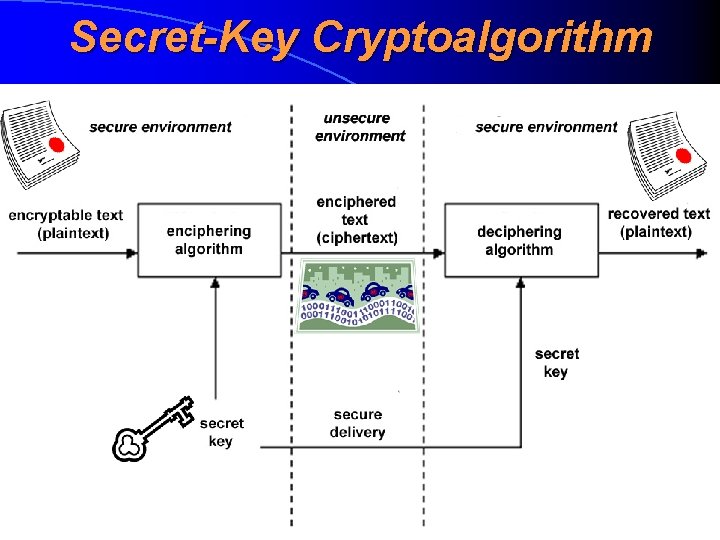
Secret-Key Cryptoalgorithm Secret-key cryptoalgorithm (salajase võtmega krüptoalgoritm) or symmetric cryptoalgorithm (sümmeetriline krüptoalgorithm) is such a cryptoalgorithm where the same secret key is used both for enciphering and deciphering purposes Is considered to be practically secure if the following two conditons are satisfied: • The key is at least 80 bit long (it’s considered to be infeasible to perform 280 operations in practice), for enhanced security cases at least 128 bits long • There aren’t known effective cryptoanalytic

Role of Key in Enciphering and Deciphering Process Encrypting or encipherment (krüpteerimine, šifreerimine) needs the using of certain key as a pre-defined queue of bits Opposite process is a decrypting or deciphering (dešifreerimine), which needs a same key in order to restore the initial data (plaintext) from the encrypted text (ciphertext) Without knowing the key the both processes are impossible to peform

Secret-Key Cryptoalgorithm

Secret-Key Cryptoalgorithm – Possibility to Break Secret-key cryptoalgorithm is considered to be practically enough secure when the keylength is at least 80 bits (for enhanced security cases 128 bits) DES is already considered insecure because its keylenght is only 56 bits (until 2005 it was allowed to use DES is triple mode as 3 DES) Additionally to sufficient keylenght the effective cryptoanalytic attacks must not be known

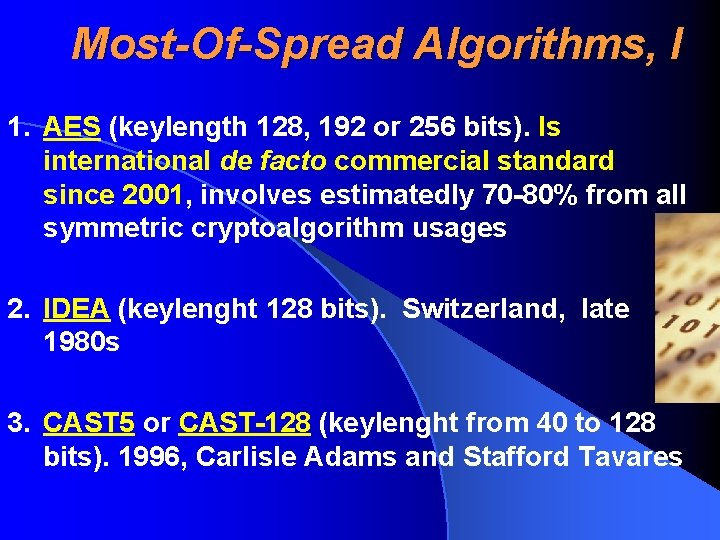
Most-Of-Spread Algorithms, I 1. AES (keylength 128, 192 or 256 bits). Is international de facto commercial standard since 2001, involves estimatedly 70 -80% from all symmetric cryptoalgorithm usages 2. IDEA (keylenght 128 bits). Switzerland, late 1980 s 3. CAST 5 or CAST-128 (keylenght from 40 to 128 bits). 1996, Carlisle Adams and Stafford Tavares

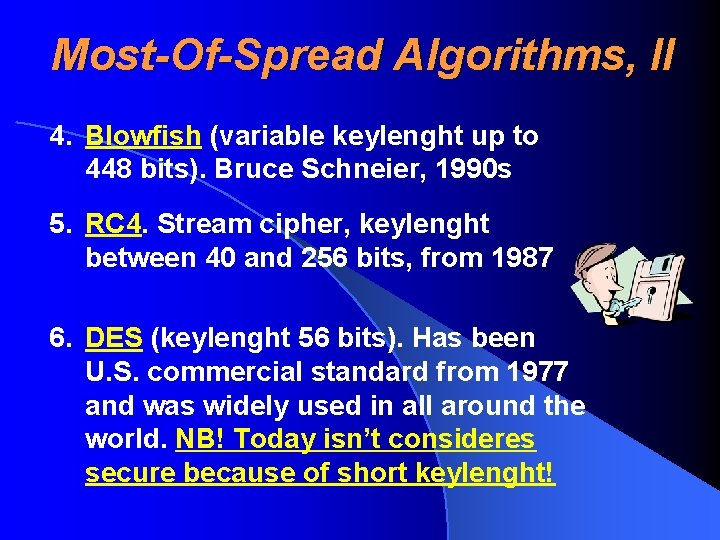
Most-Of-Spread Algorithms, II 4. Blowfish (variable keylenght up to 448 bits). Bruce Schneier, 1990 s 5. RC 4. Stream cipher, keylenght between 40 and 256 bits, from 1987 6. DES (keylenght 56 bits). Has been U. S. commercial standard from 1977 and was widely used in all around the world. NB! Today isn’t consideres secure because of short keylenght!

Block and Stream Ciphers Symmetric cryptoalgorithm can be divided into block ciphers and stream ciphers. Block ciphers are much more spread than stream ciphers • Block cipher (plokkšiffer) is an enciphering method where plaintext is divided into the blocks of certain lenght and these blocks are encrypted separately. How and if the encryption result of one block is related from the prevoius blocks is determined by the block cipher mode, which is curtrently used • Stream cipher (jadašiffer) is a method where there is generated a key sequence (võtmejada) from a given secret key. Encryption process is an ordinary XOR operation between plaintext and key sequence

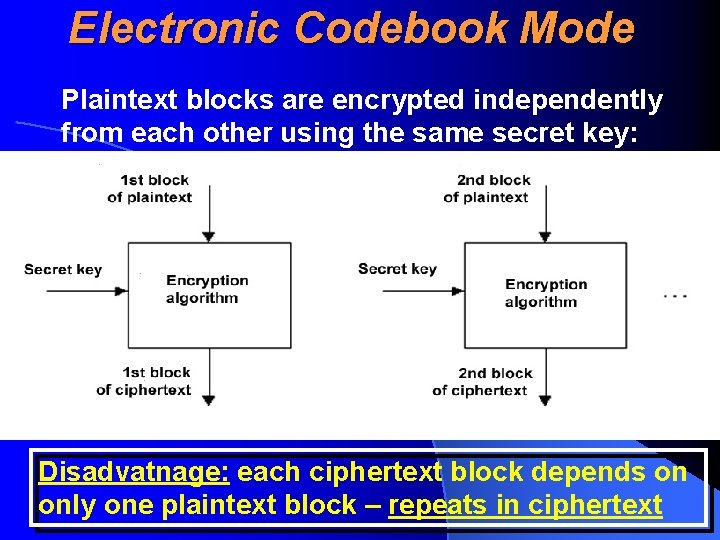
Electronic Codebook Mode Plaintext blocks are encrypted independently from each other using the same secret key: Disadvatnage: each ciphertext block depends on only one plaintext block – repeats in ciphertext

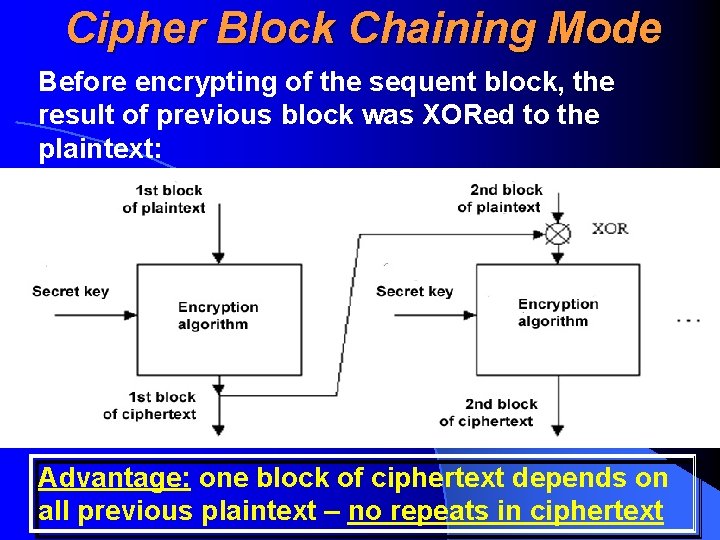
Cipher Block Chaining Mode Before encrypting of the sequent block, the result of previous block was XORed to the plaintext: Advantage: one block of ciphertext depends on all previous plaintext – no repeats in ciphertext

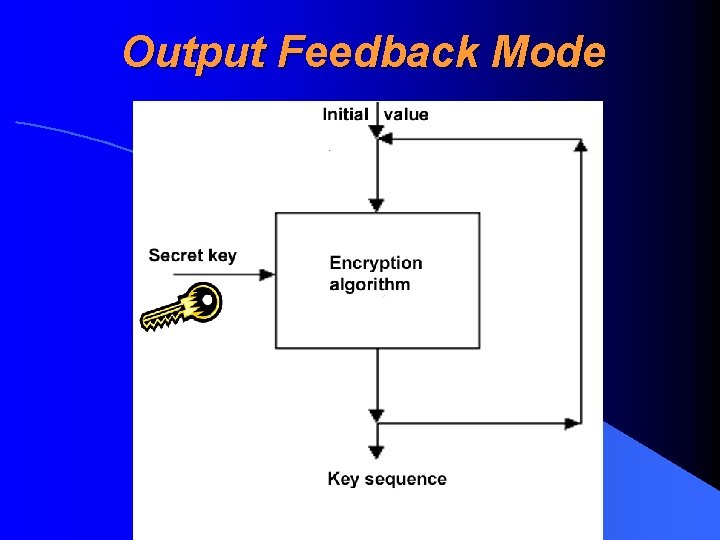
Output Feedback Mode

Using of Different Modes • The most convenient but not sufficiently secure for a long plaintexts is an electronic codebook mode – each bit of a ciphertext depends only on one plaintext block • The most-of-used and sufficently secure mode is a cipher block chaining mode – each bit of a ciphertext depends on all previous plaintext • Feedback modes are less frequently used but they allow to use a block cipher as a stream cipher in order to produce the key sequence. Main usage area of them is secure erasing of a data from any rewritable media (disks, flash memory etc).

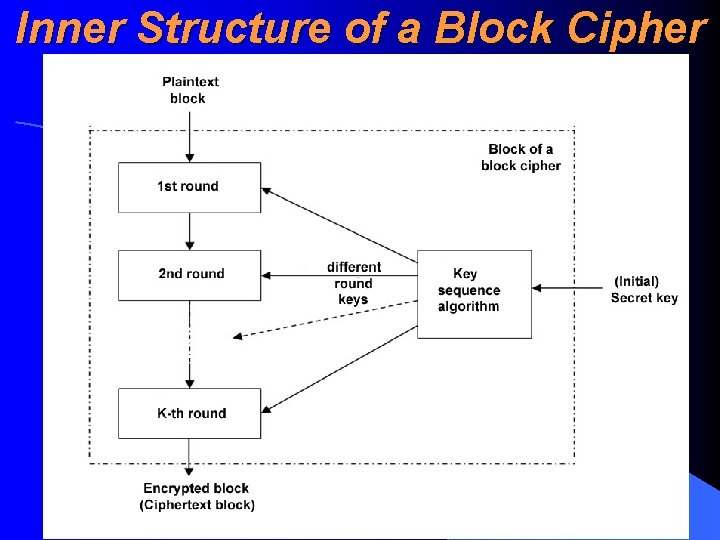
Inner Structure of a Block Cipher • Block cipher block usually involves a numerous subsequent similar standard transformations of a plaintext called rounds (raund). Output of a previous round is an input to the next round • How differents rounds use (generally different) keys is determined by a key sequence algorithm (võtmejaotusalgoritm). Key sequence algoroithm may also be missing, in these cases all rounds use straightly the original key • If such a key sequence algorithm exists, it comuptes from initial key the special round keys (raundivõtmed) for different rounds

Inner Structure of a Block Cipher

Parameters of a Typical Block Cipher • Lenght of a key • Lenght of a block (sometimes is equal to keylenght, but sometimes it’s not) • Number of rounds (and sometimes also the number of different round types) • Presence of key sequence algorithm • Number of round keys (if key sequence algorithm exists, sometimes is equal to number of rounds sometimes it’s not) • Lenght of round keys (sometimes is equal to initial key, sometimes it’s not)

Main Basic Operations Inside the Rounds • substitution (substitutsioon) – replacing of original characters (letters) by another characters (letters) • transposition or permutation (transpositsioon, permutatsioon) – changing the order of characters (letters) Most of transformations inside the block cipher rounds are certain (usually complex) combinations of them

AES: Main Facts • Is the main commercial secret-key cryptoalgorithm (about 75 -85% from all use cases) • Has won in the AES Competition, before it was known as a Rijndael • Has three different versions with different strenght (with different key lenghts) • Is a block cipher with a block lenght of 128, 192 or 256 bits cosequently • Uses a key which lenght is equal to the block lenght - consequently 128, 192 or 256 bits • Authors are Joan Daemen and Vincent Rijmen

AES: Technical Description For a 128 -bit key involves 10 rounds, for a 192 bit key involves 12 rounds and for a 256 -bit key involves 14 rounds Key sequence algorithm is missing (all rounds use straightly initial key) Each round consists of four subsequent different type of transforms: • byte sub (asendusbaidi faas) • shift row (ridade nihutuse faas) • mix column (tulpade segamise faas) • add round key (raundivõtme lisamise faas)

AES: Cryptanalysis • Exhaustive search needs to performe a 2128 to 2256 operations – it is clearly infeasible • Effective cryptanalytic means are not known up to this time (the algorithm is practically secure) • Authors of AES (Rjindael) have itself shown it for a most of cryptanalytic methods known in these times (in 1999)

AES: Cryptanalysis • In October 2002 there was offered a new type of cryptanalysis, an algebraic cryotanalysis (Courtois, Piperszyk) which probably allows to break 128 -bit AESi with 287 operations • It needs the solving of a complex algebraic equation systems which is not yet realized. Therefore, the algrebraic cryptanalysis has remained a pure theoretical constuction • There has been a little succees in a field of related key attack (seotud võtmete rünne) in 2009 where there is used different keys which are mathematically related to each other. It is a pure theoretical construction and doesn’t affect practice • There has also been some success using a side channel attack (lisakanali rünne) which is again a pure theorectical approach and is based on getting some internal information from inside the block

AES: Realizations • There’s possible to realize fast AES both in hardware and software • Hardware realizations are hundreds of times faster (depends on chip-making techniques and used programming language) • Both hardware and software realizations of AES can be used as "background“ activities, for example, the data reading/writing background activities Both hardware and software realizations of AES are widely spread

IDEA: Main Facts • Is a block cipher with a block size 64 bits (8 bytes) • Keylenght is 128 bits (16 bytes) • Was constructed in Switzerland, was published in 1991 • Was patented by Media. Crypt, patent has expired in 2010 -11 • In 2005 there was published the successor of IDEA called IDEA NXT (FOX), but it hasn’t gained the popularity of IDEA

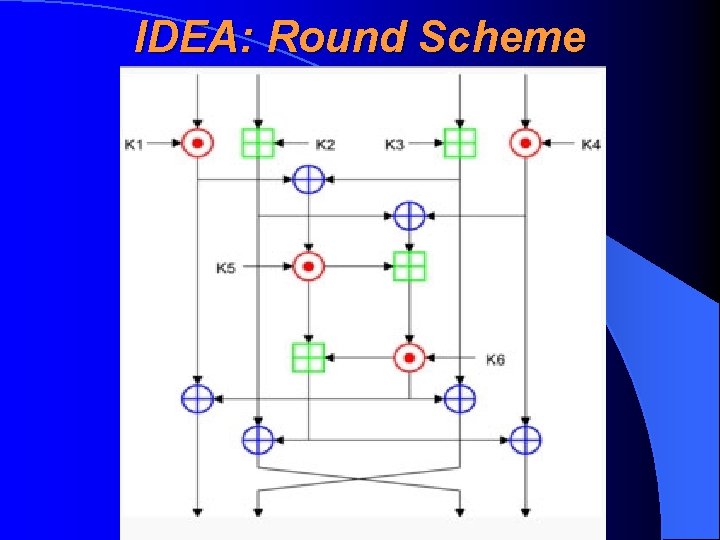
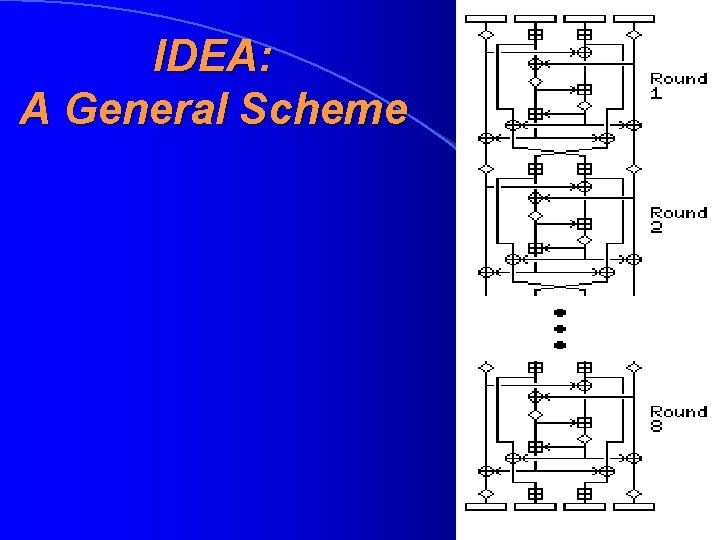
IDEA: Technical Description • Is designed, oppositely to DES, to gain also fast software realizations, not only fast hardware realisations • Uses one-way hash functions instead of typical for symmetric algorithms S-boxes • Includes a key sequence algorithm which generates 52 16 -bit subkeys (round keys) from 128 -bit general key • Consists of 8 rounds • Each round uses 6 subkeys, after thew rounds there were used 4 other subkeys • Considers 64 -bit plaintext as four 16 -bit parts

IDEA: Inside the Round Inside the round there a numerous functions with 16 -bit parts (quarters of result, subkeys) are realised: • Ordinary adding (by module 216 or mod 65536) • XOR • multiplying with module 216+1 (65537) These functions together will gain us a sufficiently non-linear function. One reason for this property is, that 65537 is a prime number

IDEA: Round Scheme

IDEA: A General Scheme

IDEA: Key Sequence Algorithm • First 8 subkeys are received by dividing of general key into 8 parts • After it the bit circular shift by 25 bits is realised and next 8 subkeys were received againg by dividing the result into 8 parts • This procedure is repeated 7 times, as we have find 52 subkeys (last 4 keys will remain unused as 7 x 8 = 56) Consequently, subkeys are related together after each of eight key

IDEA: Cryptanalysis • Exhaustive search needs considering of 2128 variants • The effective cryptanalytic algorithms are not known – consequenlty the algorithm is considered to be practically secure • Best known result is a breaking of 5 round algoritm by the plaintext collision attack (De. Mirci 2003) Conclusion: IDEA is still a suitable algorithm for a practical use (despite of it long age)

IDEA: Advantages and Disadvantages Advantages: • Is well-realizable in software • Has used in many programs and standards during last 20 years • Is extremely small – C-source of IDEA is only some KBs long and executable file (file part) consists of only some hundreds of bytes Disadvantages: • AES is more effective and more secure (if to take into account the long-term security)

Skipjack: Main Facts • Is a block cipher with a block lenght 64 bits (8 bytes) • Keylenght is 80 bits (10 bytes) • Is constructed in U. S. by NSA (National Security Agency) in early 1990 s • Was initally planned to use in Clipper chip (but this project hasn’t realized) • As an exception, the technical description of an algorith, was kept secret until 1998

Skipjack: Technical Description • Is possible to realize both fast hardware and software realizations of Skipjack (don’t consist special bit operations) • Plaintext is considered as for 16 -bit quarters (parts) • Consists of 32 rounds • Each round changes only one quarter (16 bits) of message • There are A and B type rounds - after 8 A-rounds there were used 8 B-rounds (and the same combination is repeated) • 80 -bitine key is divided to 10 8 -bit round keys by a simple sharing

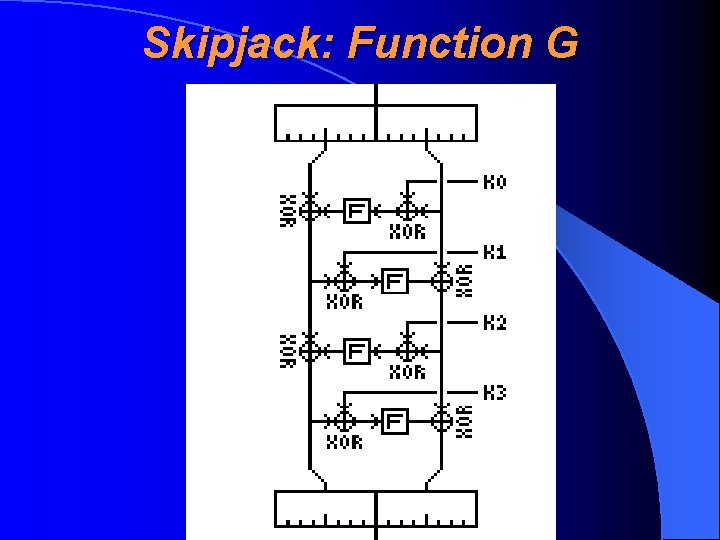
Skipjack: Description of Rounds • A- and B-type rounds differ only by a minor differencies of the place of XORing • Each round includes the same encryption function G or so-called Feistel structure, where 16 -bit text is transforming using 4 subkeys and a permutation F • Before implementing of G, the round number and previous quarter was XORed to the result

Skipjack: Function G

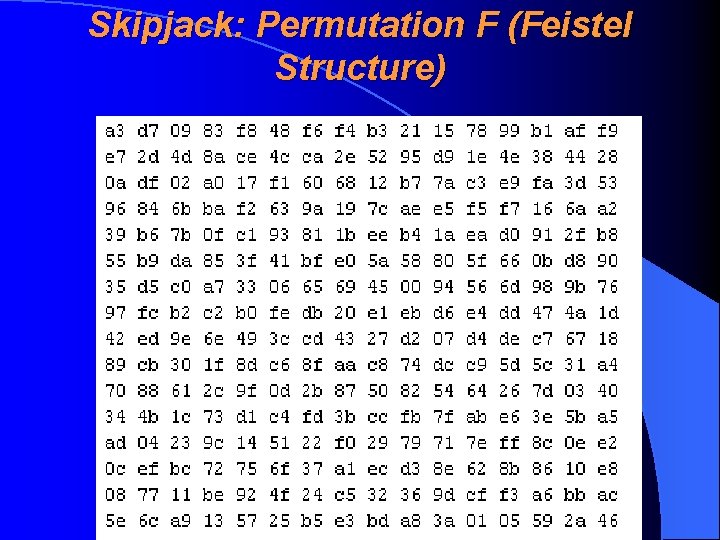
Skipjack: Permutation F (Feistel Structure)

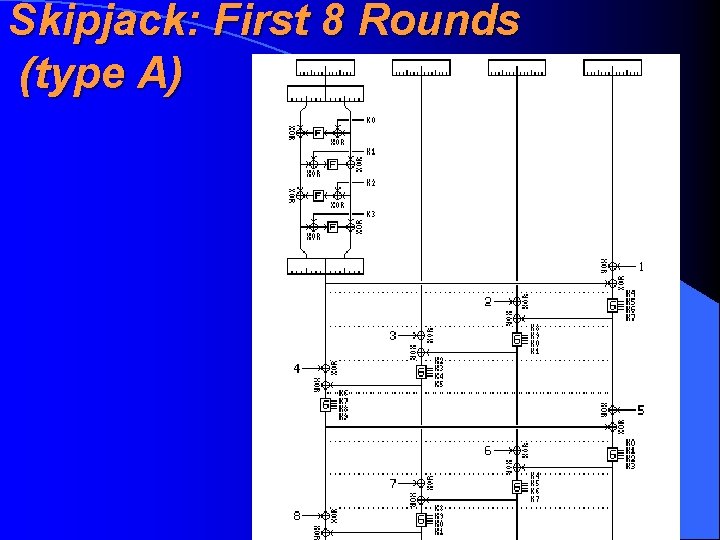
Skipjack: First 8 Rounds (type A)

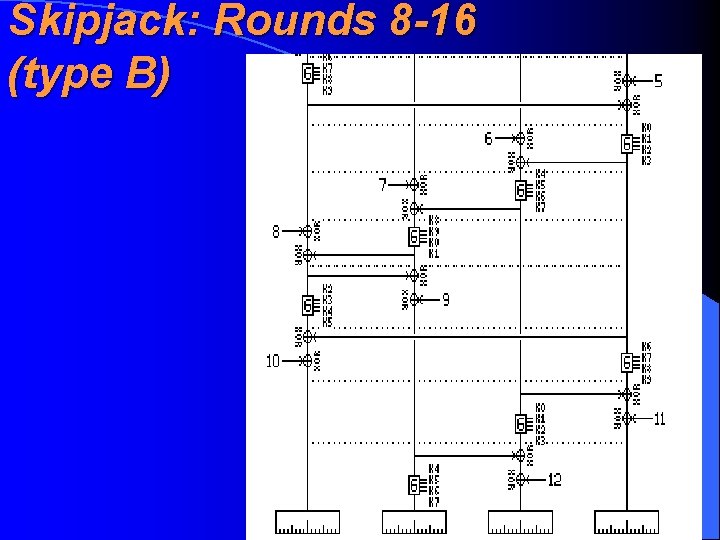
Skipjack: Rounds 8 -16 (type B)

Skipjack: Appliability • Exhaustive search needs a considening of 280 variants – it’s infeasible for contemporary computers • The effective cryptoanalytic means are not known • There has realized the impossible differential cryptanalysis (võimatute erinevuste krüptoanalüüs) in 1998 for a reduced number of rounds (Biham, Shamir, Birjukov) Conclusion: Skipjack can still considered as a parctically secure algorithm (although not suitable for a long-term security)

RC 4: Main Facts • Paralleel Names: ARC 4, ARCFOUR • Is a stream cipher (the most popular stream cipher in all the world) • Uses a variable lenght key, from 40 to 128 bits • Was constructed by Bruce Schneier in 1987 • Has widely spread with the Wi. Fi-related protocols WEP and WPA • There a full familty of RC (RC-2, RC-5, RC-6)

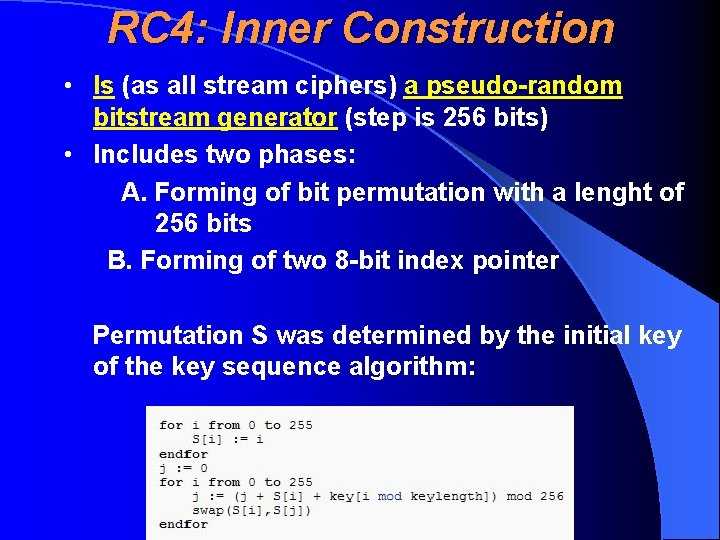
RC 4: Inner Construction • Is (as all stream ciphers) a pseudo-random bitstream generator (step is 256 bits) • Includes two phases: A. Forming of bit permutation with a lenght of 256 bits B. Forming of two 8 -bit index pointer Permutation S was determined by the initial key of the key sequence algorithm:

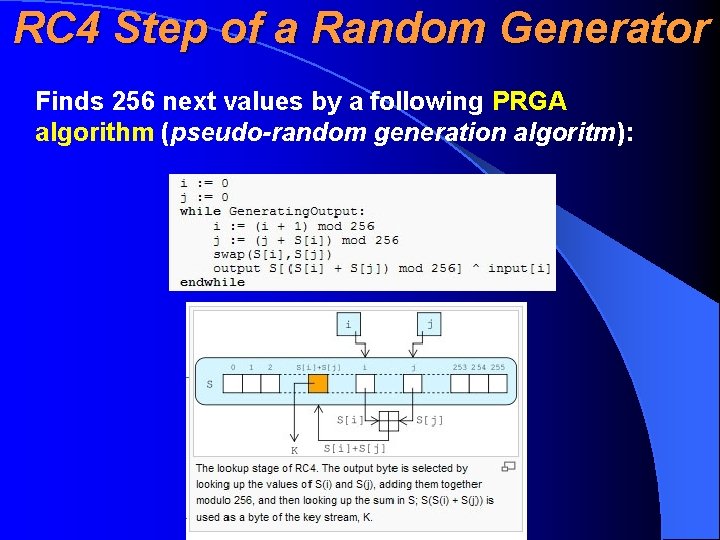
RC 4 Step of a Random Generator Finds 256 next values by a following PRGA algorithm (pseudo-random generation algoritm):

RC 4: Usage in Practice • For a stream ciphers the crytptoanalytic means’ effectiveness can’t be expressed in the form of 2 N as for block ciphers • Attack of Flucher, Martin and Shamir (2001): first bits of key sequence (768 or 3072) are not reliable and they shouldn’t be used • Klein’s attack: 104 -bit RC 4 can be broken for a minute (128 -bit RC 4 is probably not yet broken) Because of these facts RC 4 was used very seldom and is usually replaced by other more secure algorithms (AES in a stream cipher mode)

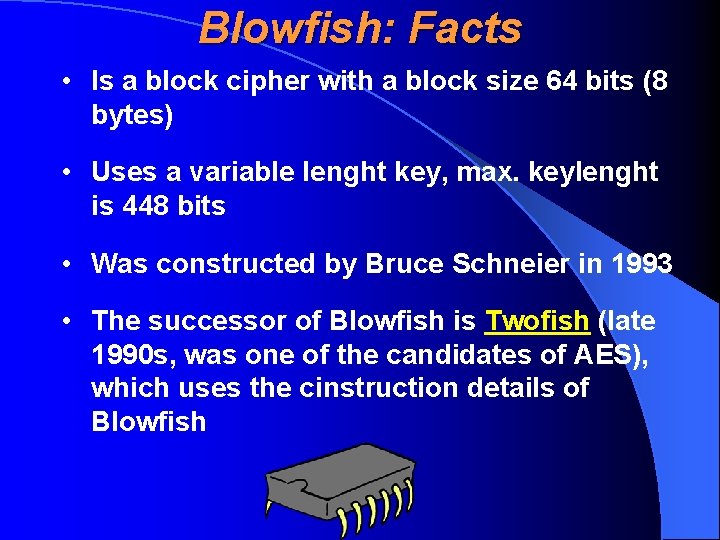
Blowfish: Facts • Is a block cipher with a block size 64 bits (8 bytes) • Uses a variable lenght key, max. keylenght is 448 bits • Was constructed by Bruce Schneier in 1993 • The successor of Blowfish is Twofish (late 1990 s, was one of the candidates of AES), which uses the cinstruction details of Blowfish

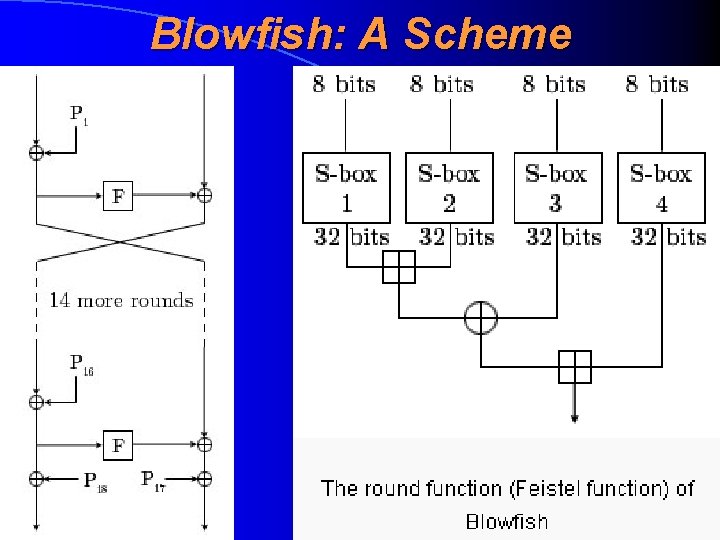
Blowfish: Technical Description • Coinsists of 16 rounds, their’ main component is F as a Feistel structure • Uses 18 32 -bit subkeys, which are generated from the initial key • Uses four 32 -bit S-boxes • Inside the rounds the 64 -bit block is divided into two halves (each round changes only one half)

Blowfish: A Scheme

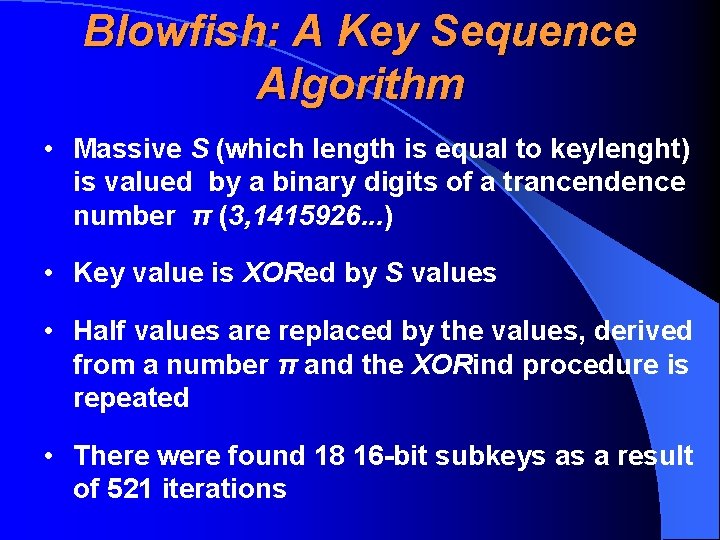
Blowfish: A Key Sequence Algorithm • Massive S (which length is equal to keylenght) is valued by a binary digits of a trancendence number π (3, 1415926. . . ) • Key value is XORed by S values • Half values are replaced by the values, derived from a number π and the XORind procedure is repeated • There were found 18 16 -bit subkeys as a result of 521 iterations

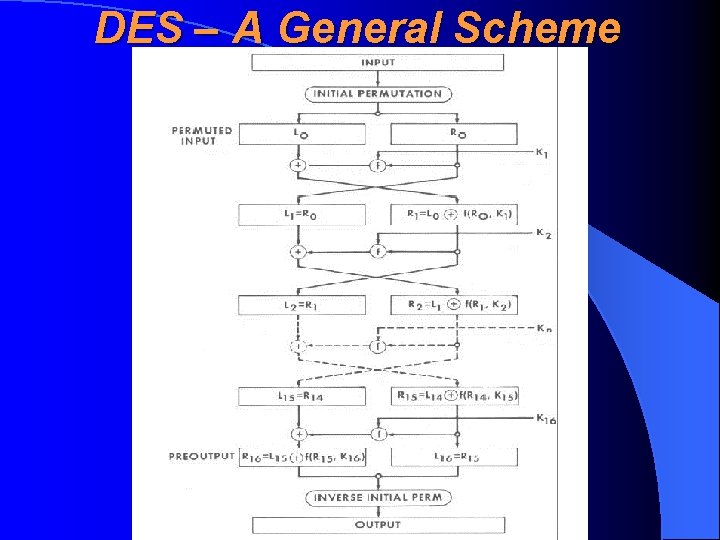
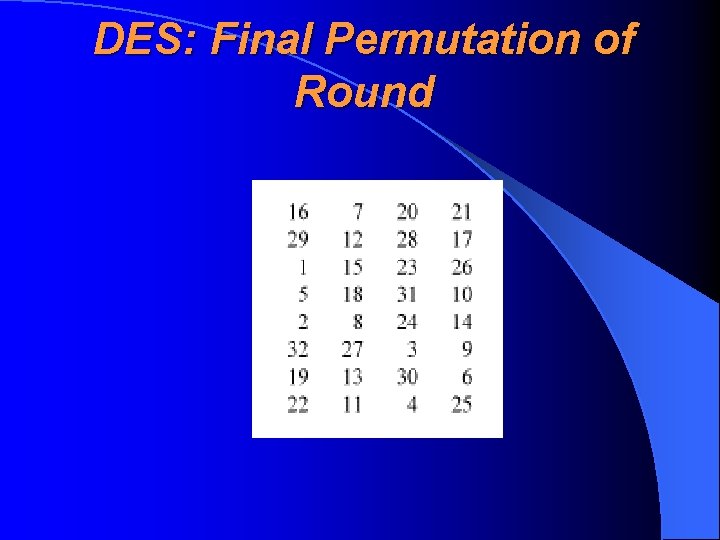
Retrospective View — DES is a typical iterative block cipher, consisting of the following parts: • key schedule calculation (võtmejaotusarvutus), which founds 16 48 -bit subkeys (alamvõtmed) from 56 -bit initial key • initial permutation (algpermutatsioon) • 16 rounds (raund), each of them using one subkey • final permutation (lõpp-permutatsioon)

DES – A General Scheme

DES: Initial Permutation

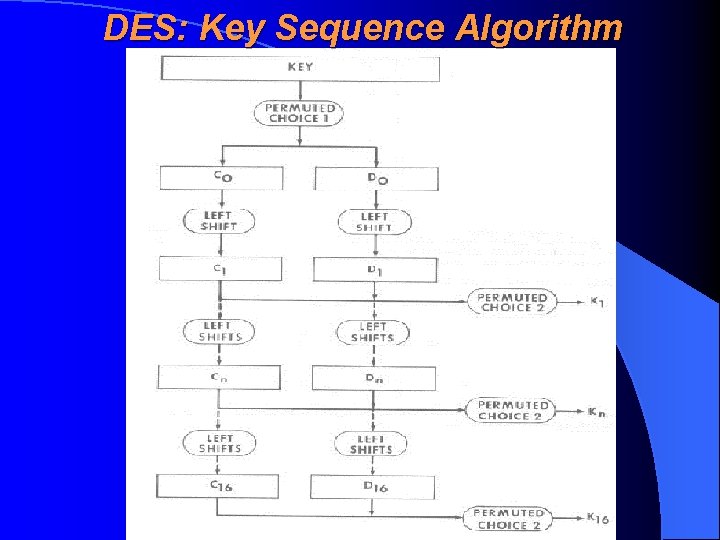
DES: Finding Subkeys 16 subkeys (round keys), 48 bits long, are found from 56 -bit initial key by a special key sequence algorithm. Each subkey is used exactly in one round There are following typical construction elements of DES: • substitution - replacing of bit combinations by an another bit combinations • permutation – changing of bits order

DES: Key Sequence Algorithm

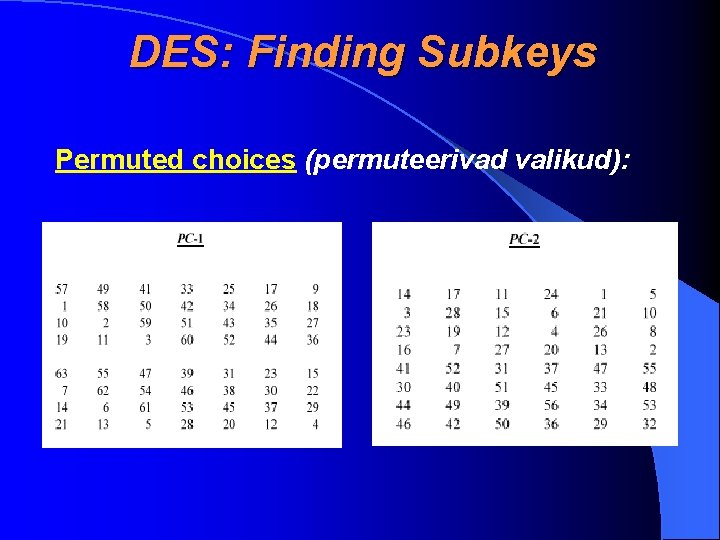
DES: Finding Subkeys Permuted choices (permuteerivad valikud):

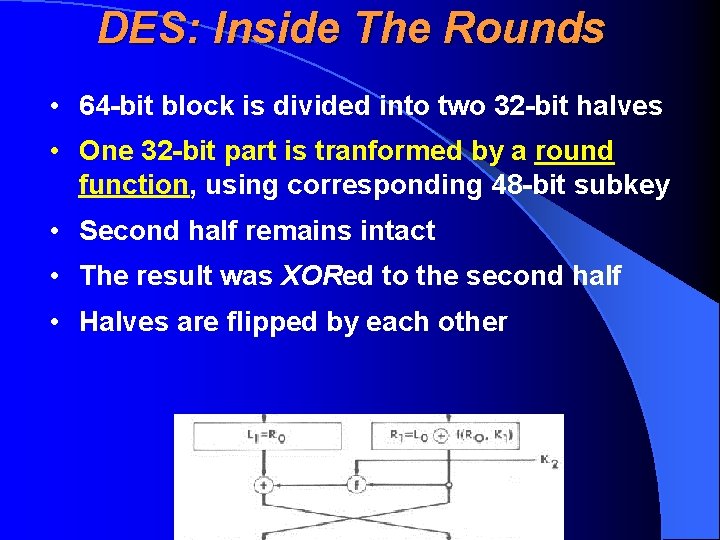
DES: Inside The Rounds • 64 -bit block is divided into two 32 -bit halves • One 32 -bit part is tranformed by a round function, using corresponding 48 -bit subkey • Second half remains intact • The result was XORed to the second half • Halves are flipped by each other

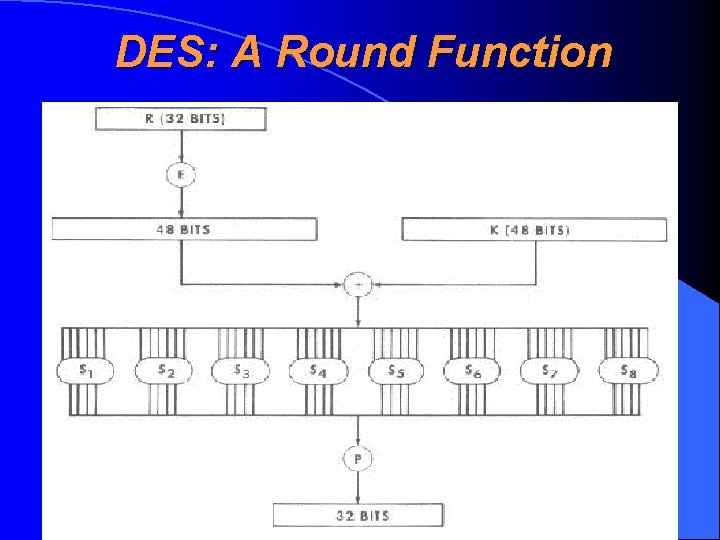
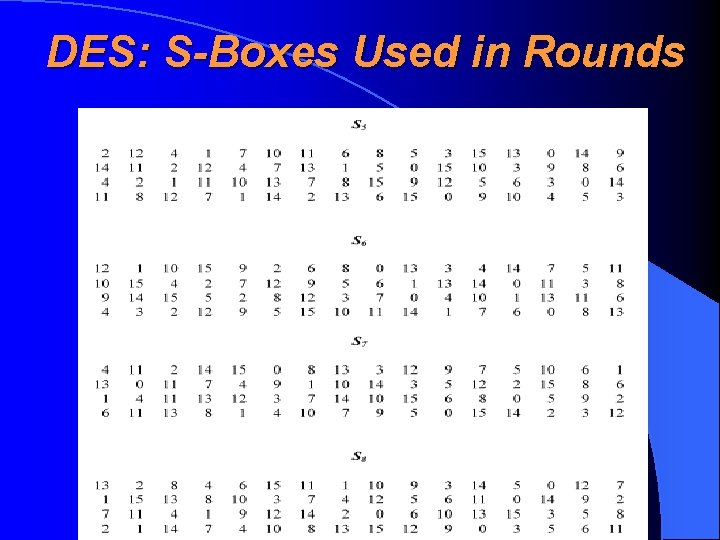
DES: Round Function • 32 -bit text is expanded to 48 -bit • 48 -bit subkey was XORed • The result is transformed back to 32 -bit 48 -bit result was transformed into 32 -bit using S-boxes (S-boksid). S-boxes form mathematically a most critical part of the whole DES algorithm

DES: A Round Function

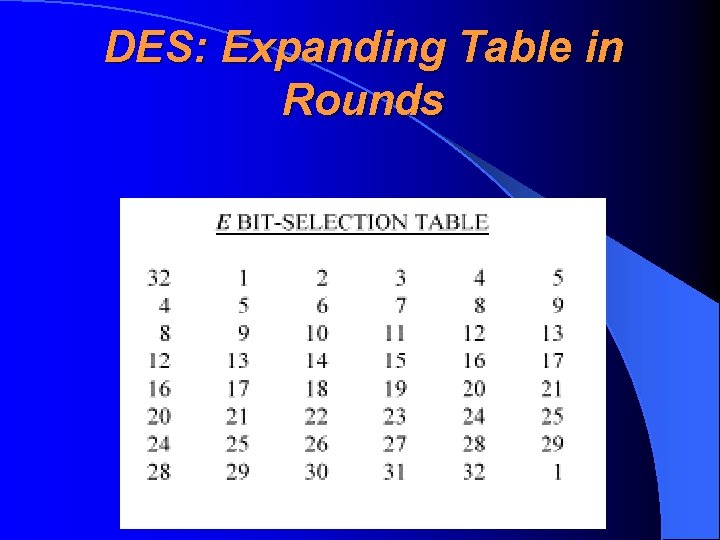
DES: Expanding Table in Rounds

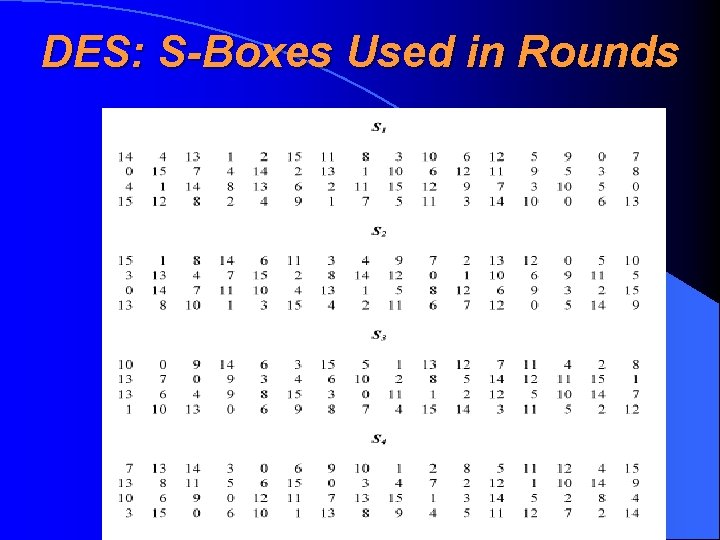
DES: S-Boxes Used in Rounds

DES: S-Boxes Used in Rounds

DES: Final Permutation of Round

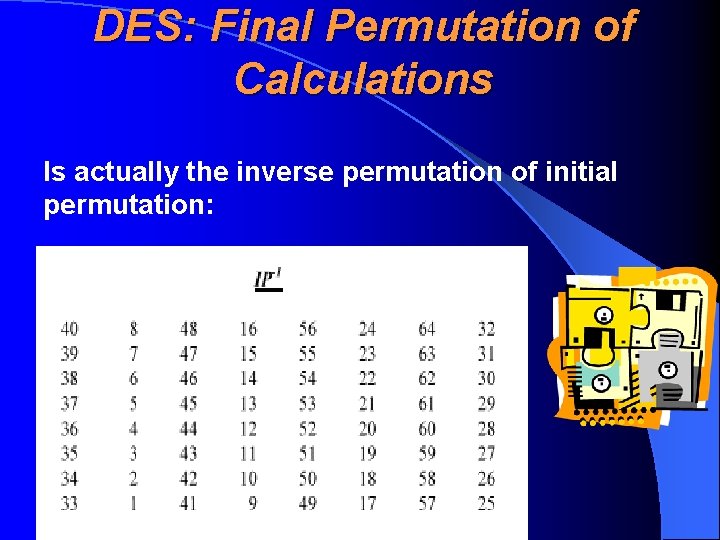
DES: Final Permutation of Calculations Is actually the inverse permutation of initial permutation:

DES: Realisations • Because there are used some complex (special) bit operations, the software realisations are much more (thousands times) slower than hardware realisations (Modern algorithms are different) • Because of the huge speed of contemporary computers there’s possibility to use DES as a backgound operations also in software already during last 15 years • DES has integrated in a numerous standards and devices (especially during 1990 s) which are sometimes still somewhere in operation

DES – Exhaustive Search • Can be performed by 256 operations – is is already feasible for contemporary computers (mainframe computers) • There’s possible to construct a special parallel “breaking machine” consisting of a lot of chips, which cost (AD 2015) is about 100 000 EUR and is able to break DES about within one second • The cost and breaking time are related together (more expensive machine is able to break faster)

DES - Cryptoanalysis • There also some effective cryptoanalytic means found • Differential cryptanalysis (erinevuste krüptoanalüüs, Biham, Shamir, 1991) allows for a adaptive chosen plaintext attack to break algorithm using 247 variants instead of 256 • Linear cryptanalysis allows to break DES only by 243 variants (Junod 2001) Sad conclusion : DES is unsuitable for practical use already for last 15 years

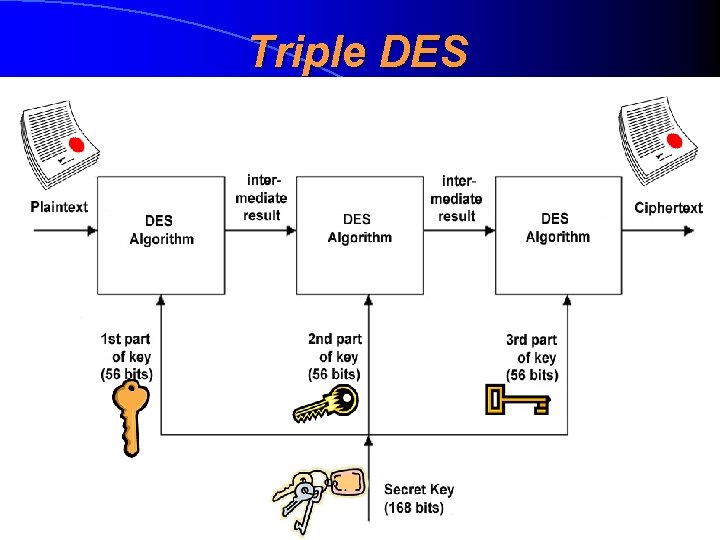
DES - Recommendations for Practice • Alternative 1 (highly recommended): to use other symmetric algorithm, especially AES • Alternative 2 (unrecommended, only use as emergency option): to use triple DES or 3 DES (kolmekordne DES), with a keylenght of 168 bits and which is not yet broken in practice Last version of DES standad FIPS PUB 46 -3 (October 1999) determines only usage of triple DES, but the standard was valid only until 2005

Triple DES

Conclusions All the presented algorithms (excepted DES) can be used in practice because they are still practically secure Since 2001 AES is better from other algorithms and it’s recommended to use AES if it is possible

Other Symmetric Algorithms? There also other symmetric algorithms which are not considered here (both older and newer algorithms) If it’s necessary to use them, it must be taken account: • If the effective keylenght is not less than 80 (128) bits • If there aren’t known effective cryptanalytic means • If the algorithms is published at least 3 -4 years ago