Data Security and Cryptology IV Risk Management and


























- Slides: 35

Data Security and Cryptology, IV Risk Management and its Methods September 24 th, 2014 Valdo Praust mois@mois. ee Lecture Course in Estonian IT College Autumn 2014

Components of Information Security Infortmation security (infoturve) or data security (andmeturve) is a complex concept consisting of following three properties (security goals): • information availability (käideldavus) • information integrity (terviklus) • information confidentiality (konfidentsiaalsus) These three properties – called branches or goals of secrity – must be maintained for all information/data items we possess and process

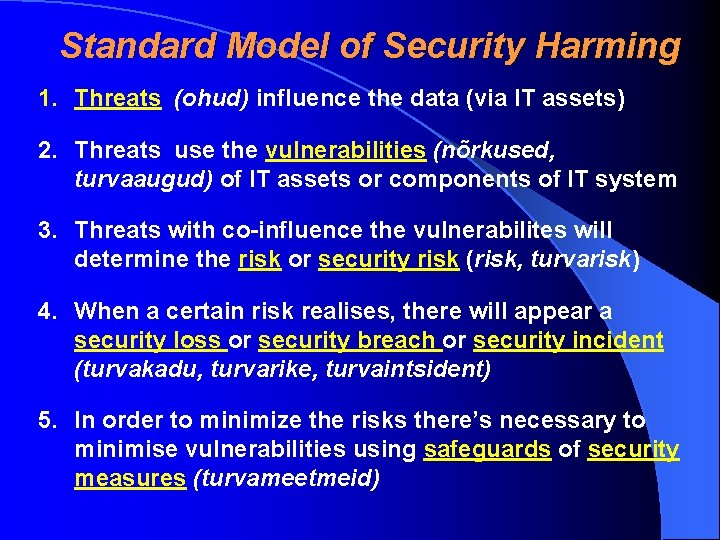
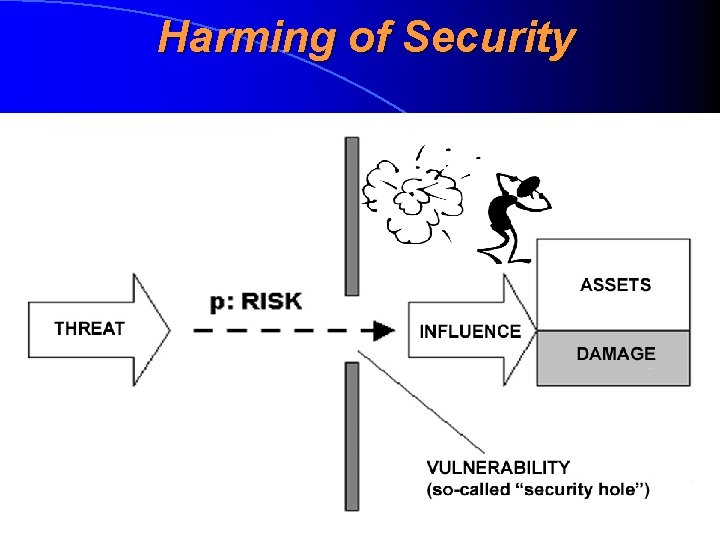
Standard Model of Security Harming 1. Threats (ohud) influence the data (via IT assets) 2. Threats use the vulnerabilities (nõrkused, turvaaugud) of IT assets or components of IT system 3. Threats with co-influence the vulnerabilites will determine the risk or security risk (risk, turvarisk) 4. When a certain risk realises, there will appear a security loss or security breach or security incident (turvakadu, turvarike, turvaintsident) 5. In order to minimize the risks there’s necessary to minimise vulnerabilities using safeguards of security measures (turvameetmeid)

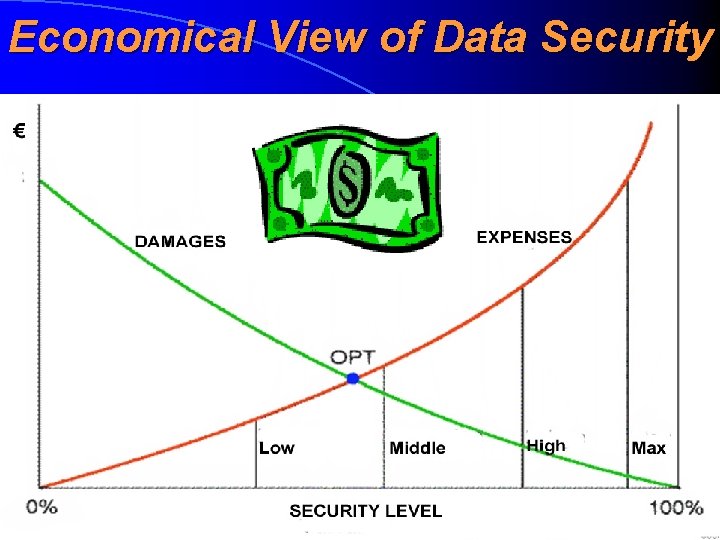
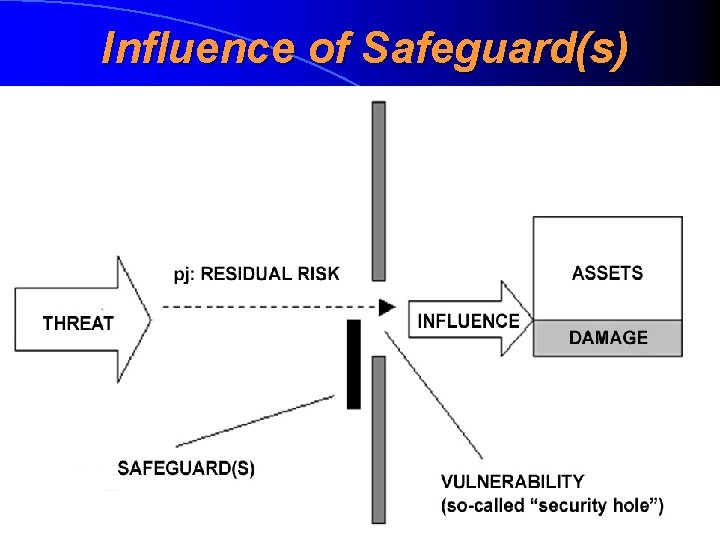
Security and Residual Risk NB! It does not matter how many safeguards we implement, we never achieve the absolute security. If we implement more safeguards we only minimise the probability that security (availability, integrity of confidentiality) will be harmed but it will never fall into zero Instead of absolute security usually the concept acceptable residual risk by the business process ((äriprotsessi jaoks) aktsepteeritav jääkrisk) is used An acceptable residual risk is a situation where the total price of all implemented safeguards is approximately equal to the forecasted total loss of security (measured by the amount of money)

Economical View of Data Security

Vulnerabilities (nõrkused ehk turvaaugud) are all such a properties of a protectable object through which (security) threats can be realised Can be divied to: • infrastructure vulnerabilities • IT vulnerabilities • personal-related vulnerabilities • organisational vulnerabilities

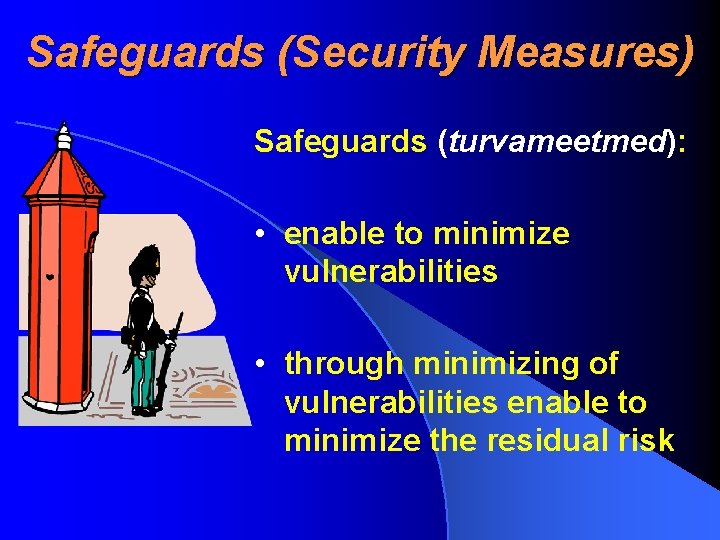
Safeguards (Security Measures) Safeguards (turvameetmed): • enable to minimize vulnerabilities • through minimizing of vulnerabilities enable to minimize the residual risk

Harming of Security

Influence of Safeguard(s)

Classification of Safeguards (turvameetmed) can by classified using different approaches: • by purpose (prevents threat, frightens attask, repairs defect etc) • by influented security component/goal (availability, integrity, confidentiality) • by type of (harmable) IT asset • mean of implementation or realisation (procedure, technical equipment, program, building construction etc) • by strength of security

Purpose of Safeguards By purpose the safeguards are divided to: • preventive safeguards (profülaktilised meetmed) • identifying safeguards (tuvastusmeetmed) • reconstructive safeguards (taastemeetmed) Several safeguards are polyfunctional (for example error correcting codes)

Preventive Safeguards Preventive safeguards (profülaktilised turvameetmed) enable to prevent security incidents: • to minimize vulnerabilities • to prevent attacks • to minimize security risk probabilities • to decrease the influence of security incidents to IT assets • to facilitate site (object) restoration Can be divided into three categories: • reinforcable safeguards (tugevdusmeetmed) • scaring safeguards (peletusmeetmed) • separative safeguards (eraldusmeetmed)

Identifying Safeguards By the minimization of security loss we tend towards the following queue of goals: • to avoid the security incident • to identify operatively the incident • to registrate the incident (and identifying it later) • to prove the incident later Identifying safeguards (avastavad turvameetmed) can be divided to: • operative identification (operatiivtuvastus) • post-identification (järeltuvastus) • evidence-based identification (tõendtuvastus)

Reconstructive Safeguards After a security incident realizes it’s always necessary to restore the normal operability of a harmed object. It can be done as fast and to a greater extent as the more importance the object (IT asset) has for us Main branches of reconstructive safeguards (taastavad turvameetmed) are: • backuping (varundamine) • renovation (ennistamine) • replacing (asendamine)

Classification of Safeguards by Realization • organisational safeguards • physical safeguards • IT-related sefaguards The most essential branch is organisational safeguards – without them any physical or ITrelated safeguards hasn’t any real influence

Essence of Risk Management Main goal of risk management: to implement exactly such a set of safeguards, which lead a security risk (the significance of theats + and its realising probability through vulnerabilities) to the level of the accepted residual risk • all kind of risks - risk of availability loss, risk of integrity loss and risk of confidentiality loss - must be taken into account • these acceptable risks are typically determined by the business process and given to IT specialists (IT security specialists) as existing values

Main Alternatives of Risk Management 1. Detailed risk analysis (detailne riskianalüüs). An ideal case 2. Baseline approach (etalonturve metoodika). A convenient way in a lot of practical cases 3. Mixed approach (segametoodika). Takes the best elements from both baseline and detailed risk analysis combining them 4. Informal approach (mitteformaalne metoodika). A real practical alternative to systematic (formal) approaches

Detailed Risk Analysis 1. Residual risk evaluating with the using of either qualitative or quantitative risk analysis methodology 2. Founding areas where it’s necessary to reduce the residual risk 3. Implementing appropriate safeguards in these areas 4. Finding new residual risks with comparing them to accepted residual risk 5. Repeating the above-mentioned procedure until we fit to the accepted residual risk limits

Quantitative and Qualitative Risk Analysis There are two main possibilities to perform the detailed risk analysis: a quantitative risk analysis (kvantitatiivne riskianalüüs) or a qualitative risk analysis (kvalitatiivne riskianalüüs) • Quantitative risk analysis is based on the calculation of quantitative values (often measured by the amount of money, other units are often reduced to money • Qualitative risk analysis is based in the calculation of some pre-agreed relative values (scales)

Quantitative Risk Analysis Typically involves: • the detailed specification of all IT assets • the specification of all threats and their’ realizing frequency • the evaluating of all vulnerabilities of all IT assets by the amount of money necessary for a performing a successful attack (successful realisation of accidential threat) • the calculation of co-influences of all vulnerabilities and threats in the probability units for all IT assets • the actual risk calculations, reduced to security risk (availability, integrity and confidentiality risk) of all data and other essential assets Often, the special questionnaire and/or software is used for it

Properties of Quantitative Risk Analysis Advantage: if we have actual data for both the vulnerabilities’ utilisability by threats and the threats’ frequency, there’s always possible to calculate the actual residual risks correctly in the money and probability units Disadvantages: • a very huge amount of work (hundreds of different IT assets, threats and vulnerabilities) • the actual information about threats and vulnerabilities is usually missing or incorrect (unusable) which rigidly excludes the usage of quantitative risk analysis

Qualitative Risk Analysis Instead of precise probabilities and money values we use several notional values and the coarse gradients and scales. Usually 3 -4 steps are used (such as a high-average-low) Also the known exact monetary values will be transferred to such a relative gradient/scale form Difficultly measurable values are usually replaced by the empirical and subjective (expertbased) evaluations of them

Part of Qualitative Risk Analysis – the Evaluation of Threat’s Influence As a rule, the following factors are taking into account (using some subjective scale): • enticement of an asset - for a case of an attack) • easyness of transforming of an asset into amenity (money) - for a case of an attack • technical possibilities of a typical attacker • the rate of utilization of (different) vulnerabilities • frequency of threat actual realization

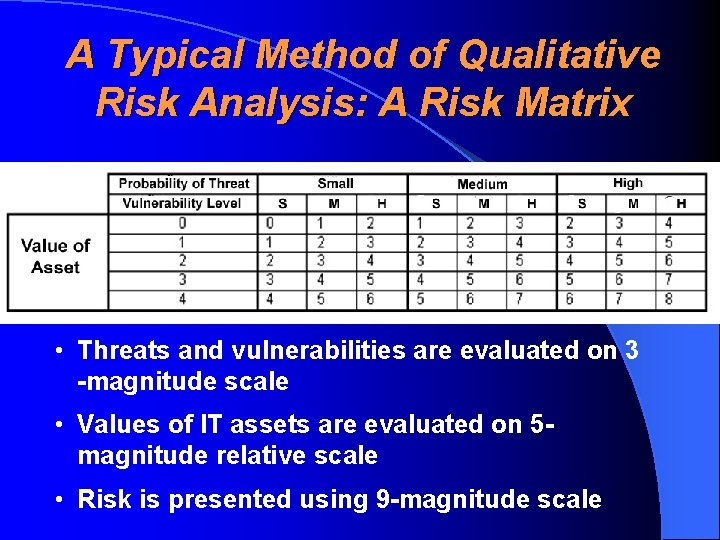
A Typical Method of Qualitative Risk Analysis: A Risk Matrix • Threats and vulnerabilities are evaluated on 3 -magnitude scale • Values of IT assets are evaluated on 5 magnitude relative scale • Risk is presented using 9 -magnitude scale

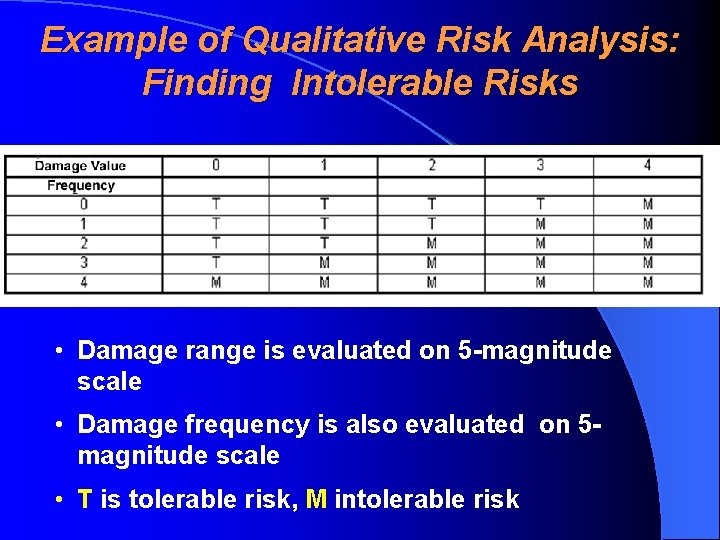
Example of Qualitative Risk Analysis: Finding Intolerable Risks • Damage range is evaluated on 5 -magnitude scale • Damage frequency is also evaluated on 5 magnitude scale • T is tolerable risk, M intolerable risk

Properties of Detailed Risk Analysis (in general) Advantages: • we got a realistic overview of situation • a calculated residual risk is very likely the actual residual risk • systematic methodology takes into account all possible vulnerabilities and threats (“we do not miss them”) A serious disadvantage: detailed risk analysis is an extremly resourceconsuming process (work, time, money, specialists)

Detailed Risk Analysis in Practice Conclusion: Detailed risk analysis is usuallyimplemented only in a few critical information systems when we have sufficient resources to perfom it (less than 1% of real systems) In the case of limited resources the detailed risk analysis is always an unsuitable method Therefore, we must implement other alternative risk management methods

Essence of Baseline Approach In the case of baseline methodology (etalonturbe metoodika) we have a given (fixed) set of mandatory safeguards for a certain (early determined) security level. We assume that implementing of these safeguards is sufficient to reach the mentioned security level (to reach to the limits of accepted residual risk) Baseline approach is a main alternative of detailed security analysis for the cases of limited resources (used for 99% practical systems)

Main Idea of Baseline Approach 1. All typical components of the typical information system (buildings, office, servers, hardware, software, communications, users, organization, access control, etc. ) was taken into account as an hypothetical system 2. The certain level of security was predefined 3. The detailed risk analysis was implemented (once!) for above-mentioned circumstances. The result is a certain set of safeguards 4. It is assumed that for any other information system the reaching of the same security level needs the implementing of same set of safeguards. Therefore, these safeguards can be considered as a baseline safeguards (etalonturvameetmed)

Properties of Baseline Approach Advantages: • in comparison with detailed risk analysis we need dozens, hundreds or even thousands of times less resources (people, time, money, work) • same set of baseline safeguards is applicable to the different information systems Disadvantages: • for a high reference security level we are forced to implement more safeguards than necessary • for a low reference security level it gains too high (unacceptable for us) residual risks • information system components with an unique architecture may cause an enormous security risks that we can’t take into the account

Essence of Mixed Approach Overtakes the advantages from both, detailed risk analysis and baseline approach combining them in order to find a reasonable compromize Two main branches of mixed approach (segametoodika) : 1. Sets of baseline safeguards are prepared not only for a certain (single) security level but for different security levels (for different pre-defined availability, integrity and confidentiality levels) 2. In mission-critcal and/or unique architecture components the detailed risk analysis was implemented (for other components we use widelyspread baseline approach)

Properties of Mixed Approach Advantages: • in comparison with detailed risk analysis it is less resouce-consuming • in comparison with baseline approach it enables to take into account the specific security goals (levels) determined by the protectable IT assets (protectable data) Disadvantages: • in comparison with detailed risk analysis it gives the less realistic result • in comparison with baseline approach it is a little more expensive

Informal Apporoach Informal approach (mitteformaalne riskihaldusmetoodika) is based on risk assessment by a non-abstract methods using the existing experience of specialists (own employees, external consultants) It is a useful method when: • risk analysis must to be performed very fast • we havn’t any suitable abstract risk assessment approaches or we can’t use them for some reasons • existing risk management methods are too resource -consumable for us • we have suitable experienced (IT) professionals

Properties of Informal Approach Advantages: • there’s no necessity to learn new skills and techniques (we need only good experts) • risk management process can be implemented by a smaller amout of resources (cheaper) than in the case of detailed risk analysis Serious disadvantages: • if we disregard systemicness, there’s always a great risk to leave some serious vulnerabilities or risks unnoticed • experience of internal/external experts both is always subjective and often absent (unsatisfiable) for some areas • expenses of safeguards isn’t sufficiently justified by us for company’s management • major problems will arise when some of experts terminate his/her duty

Examples of Risk Management Methods: BSI and ISKE • BSI Baseline Security Method (in German: IT Grundschutz) is a German National baseline security method which assumes that we operate on basic level of security (basic levels of availability, integrity and confidentiality) • ISKE is an Estonian public sector IT security standard where baseline safeguards are prepared for different security levels (regarding different availability, integrity and confidentiality levels determined by business process). It is a typical mixed approach. ISKE uses the classification and safeguards prepared by the BSI Baseline Security Method