Data gathering in WSN Issues to consider Delay











- Slides: 38


Data gathering in WSN

Issues to consider • Delay: Some application require data gathering within specific timeframe • Energy: The total energy consumption needs to be minimized in order to increase the network lifetime Network Lifetime: Time until Ø First node dies Ø Network looses its connectivity Ø Network coverage falls under predefined threshold • Accuracy: Different applications require different level of accuracy • Network Coverage: All points within the network that the sensors are deployed need to be covered by at least one sensor node 3

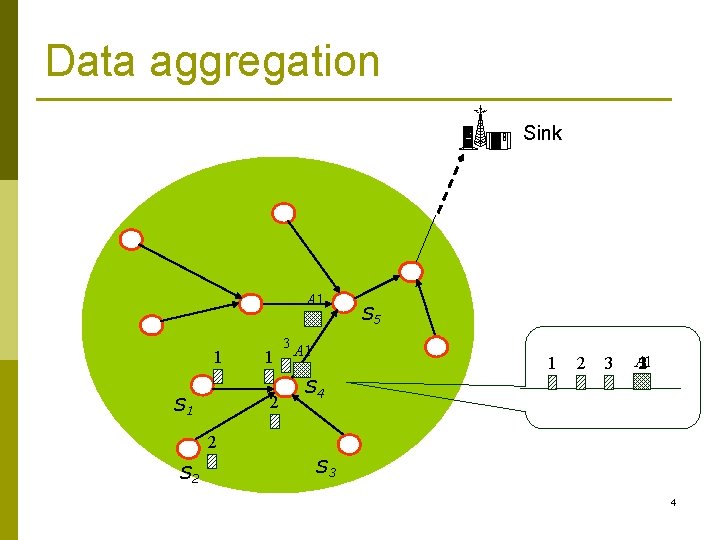
Data aggregation Sink A 1 1 1 2 S 1 3 A 1 S 5 1 2 3 A 1 123 S 4 2 S 3 4

Data gathering approaches • The data gathering approaches are classified based on their characteristics. Rely upon: Ø Ø Ø • Network structure Routing dependence Nature of sent data Frequency of data transmissions Network connectivity Simplest way to sent data: Direct communication to the sink 5

Hierarchical – no hierarchical approaches • Given the network structure the data gathering strategies are divided: Ø Ø • Hierarchical No Hierarchical are further divided to: Ø Ø Ø Cluster-based Chain-based Tree-based 6

Cluster based I • Sensor nodes are divided into groups –clusters- based on their relative position • A node takes the leader role in each group – cluster head • At each gathering round nodes send their data to cluster head • The cluster head sends the gathered data to the sink 7

Cluster based II • The cluster head consumes greater energy • Therefore, nodes take turns in becoming cluster heads are often • Delay is incurred because of the data gathering in the clusters • Low complexity in cluster creation • Significant energy benefits 8

Cluster based III • Representative protocols: § § § Low-Energy Adaptive Clustering Hierarchy (LEACH) (Heinzelman, Chandrakasan and Balakrishnan, 2000) LEACH-C, centralized version of LEACH (Heinzelman 2000) E-LEACH, enhanced version of LEACH (Pham, Kim and Moh, 2004) Δημιουργία ομάδων αισθητήρων σε συνδυασμό με ενδιάμεσα σημεία αναμετάδοσης (Choi, Shah and Das, 2004) Clustering-Based Maximum Lifetime Data Aggregation, CMLDA (Dasgupta, Kalpakis and Namjoshi 2003) 9

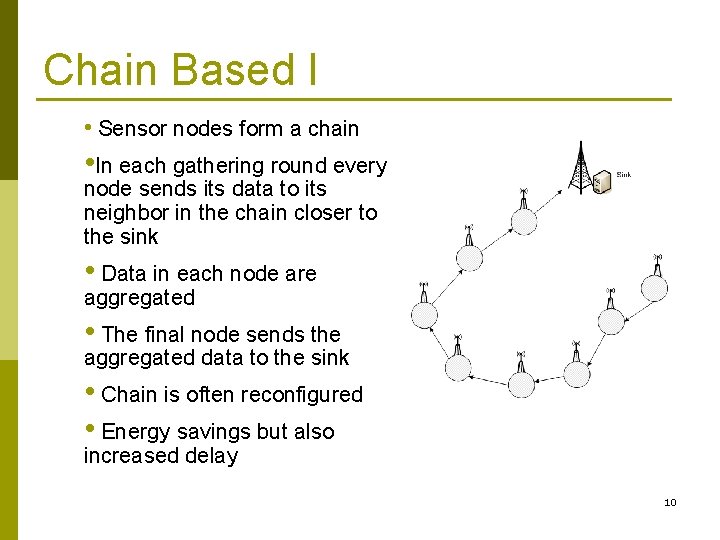
Chain Based I • Sensor nodes form a chain • In each gathering round every node sends its data to its neighbor in the chain closer to the sink • Data in each node are aggregated • The final node sends the aggregated data to the sink • Chain is often reconfigured • Energy savings but also increased delay 10

Chain Based II • Representative protocols: § Simplest protocol is the linear § Power-Efficient Gathering in Sensor Information Systems, PEGASIS (Lindsey, Raghavendra and Sivalingam, 2002) § Code Division Multiple Access, CDMA (Lindsey, Raghavendra and Sivalingam 2002) 11

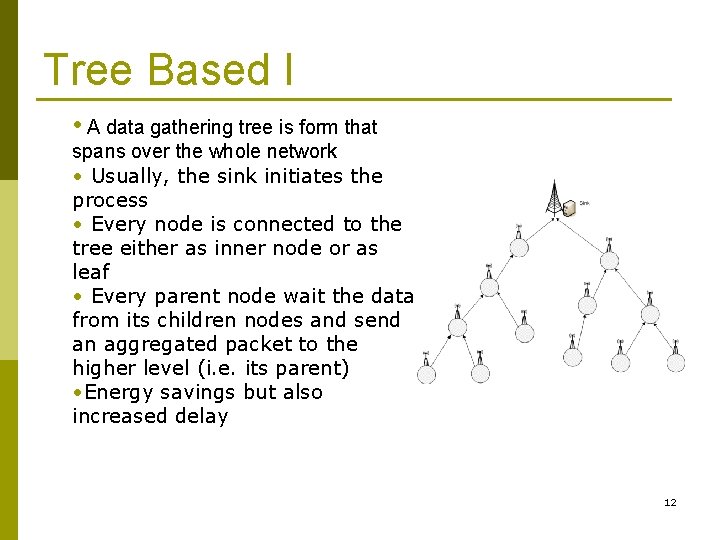
Tree Based I • A data gathering tree is form that spans over the whole network • Usually, the sink initiates the process • Every node is connected to the tree either as inner node or as leaf • Every parent node wait the data from its children nodes and send an aggregated packet to the higher level (i. e. its parent) • Energy savings but also increased delay 12

Tree Based II • Representative protocols: n Efficient Data Gath. Ering protocol, EDGE (Thepvilojanapong, Tobe and Sezaki 2005) n Power Efficient Data gathering and Aggregation Protocol, PEDAP (Tan and Körpeo 2003) 13

Non hierarchical approaches • Flooding: Every sensor node sends its packets to all of its neighbors • • • Gossiping: Every sensor node sends its packets to a group of its neighbors • • Great energy cost Excessive packet creation Solves the flooding drawbacks Directed diffusion (Intanagonwiwat, Govindan and Estrin (2000) • • • Sink asks for data Data packets are created More efficient paths are reinforced 14

Routing independent propabilistic methods I • Many strategies are routing dependent • However, some approaches are routing independent and can be combined with energy efficient routing for greater energy earnings • The decision for data aggregation is distributed and probabilistic 15

Routing independent propabilistic methods I • Representative protocols: n Quality Constrained Data Aggregation and Processing, Q-DAP, (Zhu, Papavassiliou & Yang, 2006) Ø Every node with probability γ waits defined time and aggregates all the packets gathered in the given time duration. • Adaptive Application-Independent Data Aggregation, AIDA, (He, Blum, Stankovic & Abdelzaher, 2004) Ø The aggregation is realized in a separate layer – between the data link layer and the network layer 16

Approaches based on the nature of the data I Distributed compression strategies • • • Use of source compression with combination of the correlation of data between neighboring nodes Less bits are transmitted less energy is consumed Loss in data accuracy Cost of compression and decompression should be small The approaches are divided: Ø Ø multi-input coding strategies single-input coding strategies Ø self coding Ø foreign coding 17

Approaches based on the nature of the data II • Representative protocols: n Minimum-Energy Gathering Algorithm, MEGA, foreign coding (Rickenbach & Wattenhofer, 2004) n Low-Energy Gathering Algorithm, LEGA, approximation algorithm for self-coding (Rickenbach & Wattenhofer, 2004) n Removal of correlation with the use of distributed compression algorithm (Chou, Petrovic & Ramchandran 2003) n Energy-Efficient Distributed Source Coding, EEADSC (Tang, Raghavendra & Prasanna 2003) 18

Approaches based on the nature of the data III Transmission of meta-data • Whenever a node has data to send, transmits first a packet that describes its data • Neighboring nodes wanting to receive the data, send a packet to declare their interest • Data packet transmission follows • Use of the described approach by the SPIN protocols (Heinzelman, Kulik, & Balakrishnan 1999) 19

Query based approaches I • Data are sent to the sink: § Periodically § Whenever a value exceeds a threshold § As a response to user request • • Users pose requests to the sink The sink inserts the question to the network and the sensor nodes send the requested data The requests may regard a specific group of sensor nodes Example: What is the temperature in the west side of the room? 20

Query based approaches II • Representative protocols: n The Cougar approach, (Yao & Gehrke, 2002) Ø Ø n At each node there is a query proxy layer that interacts with the network and application layer Synchronization is needed among the nodes Tiny AGregation, TAG, (Madden, Franklin, Hellerstein & Hong, 2002) Ø Ø The request is propagated to all the network nodes (distribution phase) The nodes that have data answering the question send it through a data collection tree rooted at the sink. In every intermediate node data aggregation is performed (data gathering phase) 21

Query based approaches III • Representative protocols: n Temporal coherency-aware in-Network Aggregation, Ti. NA, (Sharaf, Beaver, Labrinidis & Chrysanthis, 2004) Ø Ø § Enhancement of the above mentioned approaches with the tradeoff of loss in accuracy Use of tct value which represents the acceptable loss in accuracy – defined by the user Adaptive Periodic Threshold-sensitive Energy Efficient sensor network protocol, APTEEN, (Manjeshwar, Zeng & Agrawal, 2002) Ø Ø Network is partioned into groups Use of modified TDMA model 22

Selection of subset of sensors I • • In every gathering round a representative set of sensor nodes is selected that sends sensed data to the sink The chosen subset must cover the entire network Nodes that are not chosen are put either to sleep or idle mode Similar to the approaches used in the MAC layer 23

Selection of subset of sensors II p Energy Savings with Topology Control (TC) Two major ways to do TC: p 1. 2. Controlling the power at the node to create energy effective topologies Taking advantage of the network density for turning off the radio interface p p “Node sleep” saves a lot Only a (connected) fraction of the nodes stays up for performing network functions Another idea: p n backbone formation can also be used for the sake of topology control (only backbone nodes are awake, or better, nodes have different duty cycles depending on whether they belong to the backbone or are ordinary nodes) 24

Selection of subset of sensors IV • Representative protocols: n n n Selection of a connected correlated-dominating set, (Gupta, Navda, Das & Chowdhary, 2005) Use of data reporters for transmission of data (Choi & Das, 2005) Capability for data gathering with different level of accuracy (Chen, Guan & Pooch, 2004) The above approaches have great energy savings with the tradeoff of loss in covering the whole network 26

Data gathering in mobile WSNs I • All the above presented approaches work for static deployed WSNs • Not efficient use in mobile environments • Different parameters need to be taken into consideration, ex. The motion pattern of the nodes 27

Data gathering in mobile WSNs II • Representative protocols: § Liu and Lee, 2004. Creation of clusters based on the LEACH protocol Ø Ø § For the cluster head selection each node sends a packet containing information about the location, speed and direction Each node based on its data decides in which cluster will become member of Chae, Han, Lim, Seo and Wo, 2000. Creation of sensor groups with 2 kinds of nodes: sensors & transmitters § Nodes operate in defined intervals and then are put to idle mode 28

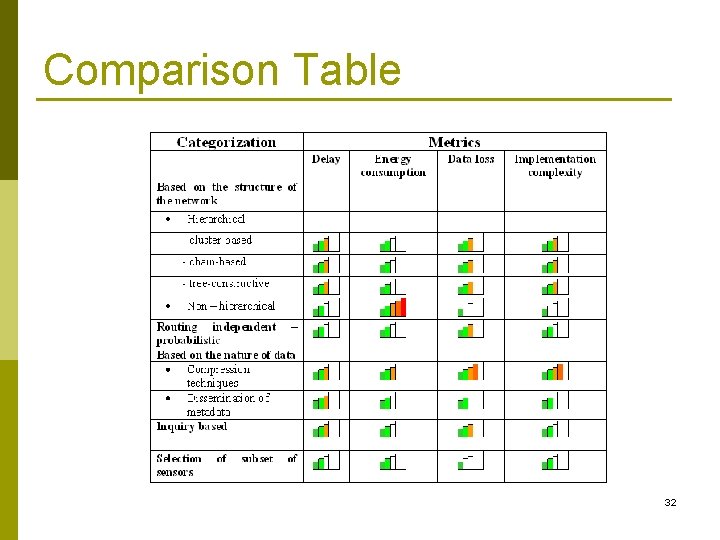
Data gathering approaches comparison I Hierarchical • • Great energy savings Delay in data gathering Initialization and maintance cost Data accuracy depends on the aggregation function used Non - Hierarchical • • Sensor nodes consume great amount of energy Simple in operation and maintance Increase in network load because of vast amount of data Small delay & good throughput at first but as the load increase in delay and decrease in throughput 29

Data gathering approaches comparison II Routing independent – probabilistic approaches • • Increase in network lifetime Delay and throughput depend on the aggregation decision taken in a distributed manner at every node Approaches based on the nature of data • Energy savings • Cost in compressing and decompressing the data • Delay and throughput depend on the type of coding 30

Data gathering approaches comparison III Querry based approaches • • Not all nodes send data to the sink less energy consumed in each data gathering round Data accuracy depend on the type of aggregation function • • Many nodes do not send data similar to previous sent Delay because of data aggregation Selection of subset of sensor • • • Since some nodes are put in sleep mode in predefined rounds Network lifetime increases Reduced network coverage 31

Comparison Table 32

Security

Security I p What is different ? n n n p Security has never been more important! n p Unfriendly, unattended environments Severe resource constraints render most of the cryptographic mechanisms impossible PKI is infeasible for sensor networks and have to rely on symmetric key cryptography Applications in battlefield management, emergency response systems and so on Key management is the most critical issue n Focus of majority of the research 34

Security II SPINS p p Complete suite of security protocols for sensor networks SNEP (Secure Network Encryption Protocol) n n n p Data Confidentiality Data Integrity Data Freshness μTESLA n Lightweight version of TESLA for authenticated broadcast 35

Security III p Authenticated Routing n n n p Base station can be authenticated using μTESLA For each time interval, the first packet heard is chosen as parent, which is authenticated later Prevents spurious routing Node-to-Node Key Agreement n n n A sends B a request with a nonce B asks the sink for a session key using SNEP Sink distributes shared session keys securely to A and B using SNEP with strong freshness 36

References p p p W. Ye, J. Heidemann, D. Estrin, “Medium Access Control With Coordinated Adaptive Sleeping for Wireless Sensor Networks”, IEEE/ACM Transactions on Networking, Vol: 12, Issue: 3, pp: 493 - 506, June 2004 A. El-Hoiydi, “Spatial TDMA and CSMA with preamble sampling for low power ad hoc wireless sensor networks”, Proc. ISCC 2002, 7 th International Symposium on Computers and Communications, pp: 685 - 692, 1 -4 July 2002. V. Rajendran, K. Obraczka, J. J. Garcia-Luna-Aceves, “Energy-Efficient, Collision-Free Medium Access Control for Wireless Sensor Networks”, Proc. ACM Sen. Sys 03, pp: 181 - 192, Los Angeles, California, 5 -7 November 2003 G. Lu, B. Krishnamachari, C. S. Raghavendra, “An adaptive energy efficient and low-latency MAC for data gathering in wireless sensor networks”, Proc. of 18 th International Parallel and Distributed Processing Symposium, pp: 224, 26 -30 April 2004. T. van Dam and K. Langendoen, “An adaptive energy-efficient Mac protocol for wireless sensor networks, ” in Proc. ACM Sen. Sys, New York, 2003, pp. 171– 180. Rhee, I. , Warrier, A. , Aia, M. , Min, J. : Z-MAC: A Hybrid MAC for Wireless 37 Sensor Networks. In: Proc. of the ACM Sen. Sys Conf. , San Diego, CA (2005) 90– 101

References p p p Heinzelmann, W. (2000). Application-Specific protocol architectures for wireless sensor networks. Ph. P Thesis, Massachusetts Institute of Technology, June 2000. Heinzelman, W. R. , Kulik, J. and Balakrishnan H. (1999). Adaptive protocols for information dissemination in wireless sensor networks. In Proc. of the 5 th annual ACM/IEEE International Coference on Mobile Computeing and networking, 174 -185. Heinzelman, W. R , Chandrakasan, A. , and Balakrishnan, H. (2000). Energy efficient communication protocol for wireless microsensor networks. In Proc. IEEE of the 33 rd Annual Hawaii International Conference on System Sciences, 2, 10. Intanagonwiwat, C. , Govindan, R. , and Estrin, D. (2000). Directed Diffusion: A scalable and robust communication paradigm for sensor networks. In Proc. Of the 6 th Annual International Conference on Mobile Computing and Networking, 56 -67. Lindsey, S. , Raghavendra, C. , and Sivalingam, K. M. (2002). Data gathering algorithms in sensor networks using energy metrics. IEEE Transactions on Parallel and Distributed Systems, 13, 924 – 935. 38

References p p p Madden, S. R. , Franklin, M. J. , Hellerstein, J. M. , and Hong, W. (2002). TAG: A tiny aggregation service for ad-hoc sensor networks. In Proc. The 5 th Symposium on Operating Systems Design and Implementation, 36, 131– 146. Manjeshwar, A. , Zeng, Q. A. , and Agrawal, D. P. (2002). An analytical model for information retrieval in wireless sensor networks using enhanced APTEEN protocol. IEEE Transactions on Parallel and Distributed Systems, 13, 1290– 1302. Tang, C. , Raghavendra, C. S. , and Prasanna, V. K. (2003). An energy efficient adaptive distributed source coding scheme in wireless sensor networks, IEEE Internation Coference on Communications, 1, 732 -737. Yao, Y. , and Gehrke, J. (2002). The cougar approach to in-network query processing in sensor networks. ACM SIGMOD Record, 31, 9– 18. Meguerdichian, S. , Koushanfar, F. , Potkonjak, M. , and Srivastava, M. B. (2001). Coverage problems in wireless ad-hoc sensor networks. In Proceedings of 20 th Annual Joint Conf. IEEE Computer and Communication Societies, 3, 1380 -1387. Tutorial: Wireless Sensor Networks, Krishna M. Sivalingam, University of 39 Maryland, Baltimore County, USA