Data and Network Security I Lecture 1 Introduction































- Slides: 51

Data and Network Security I Lecture 1: Introduction to Security & Overview of current security incidents

Is there a security problem? n Web sites (amazon. com, yahoo, e-bay) down in 2002 n Hacking into corporate network – industrial espionage n Virus, worm spread on Internet n Online stock trading applications down n Theft – stealing from bank by modifying data in DB n Terrorism Slammer worm took down Bank of America’s ATM network, Seattle 911 service, Ohio's Davis-Besse nuclear power plant’s safety monitoring system, … Nachi worm invaded Diebold ATMs Real worries about e-voting validity n Internet Connection shut down in 2006 Mauritius n n n Mrs S. Armoogum Lecture 1 Security Concepts 2

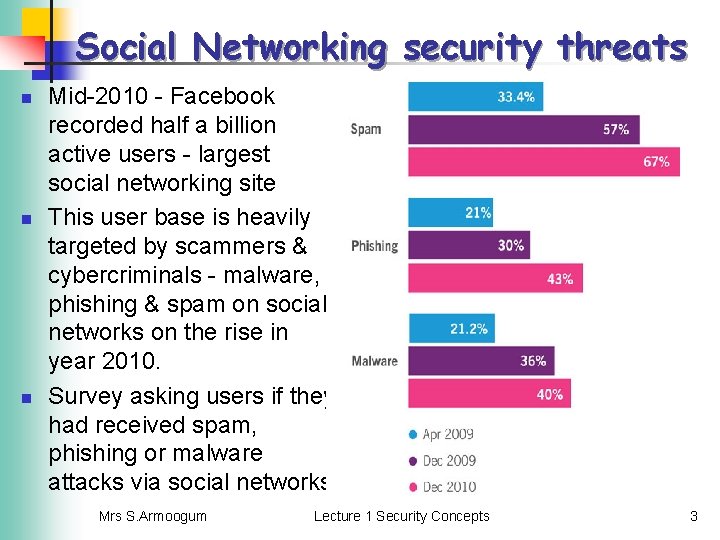
Social Networking security threats n n n Mid-2010 - Facebook recorded half a billion active users - largest social networking site This user base is heavily targeted by scammers & cybercriminals - malware, phishing & spam on social networks on the rise in year 2010. Survey asking users if they had received spam, phishing or malware attacks via social networks Mrs S. Armoogum Lecture 1 Security Concepts 3

On. Mouse. Over Twitter worm attack biggest social networking worm of 2010 n on. Mouse. Over Twitter worm hit the Twitter site in September 2010 & spread like wildfire. n The cross-site-scripting (XSS) attack demonstrated how quickly a vulnerability on a social network can affect a huge number of users. n Web profile pages were tampered (via XSS) such that on. Mouse. Over certain links or images etc user redirected to malicious web sites e. g. Phishing attacks. Mrs S. Armoogum Lecture 1 Security Concepts 4

Koobface n n Koobface – malware - spreads by delivering Facebook messages to people who are 'friends' of a Facebook (My. Space/Bebo/Hi 5, . . ) user whose computer has already been infected. Msg subject lines e. g. “You look so amazing funny on our new video” or “You look just awesome in this new movie” Offer recipients links to video sites – users follow link & attempt to play video get error msg saying they need to download a file to update Adobe Flash software. Downloaded software contains Koobface code that infect computer n Computer becomes a zombie, tamper with search engine to. Mrs direct user to contaminated websites, also attempts to 5 S. Armoogum Lecture 1 Security Concepts

Politics & cybercrime -Wiki. Leaks n n n Wiki. Leaks – an international non-profit organisation – publishes submissions of private, secret & classified media from anonymous news sources & news leaks – launched in 2006 – whistleblower website Julian Assange – australian internet activist – director. Nov 2010 – Wiki. Leaks under “mass distributed denial of service attack” just as its much-hyped release of secret embassy cables leaked early on Twitter. Site available intermittently (mirror sites) then completely out! E. g. disclose that Arab leaders are privately urging an air strike on Iran and that US officials have been instructed to spy on the UN leadership. Massive scale of attack exceeding 10 Gigabits a Mrs S. Armoogum Lecture 1 Security Concepts second 6

Stuxnet in Iran n n Stuxnet - June 2010 - first weapon made entirely out of code Targeted specifically at critical infrastructure systems Power plants, traffic control systems, factories. One known target - centrifuges at Iran's Natanz uranium enrichment plant, that spin nuclear material – to purify uranium n reportedly shutdown 1, 000 centrifuges at Natanz – Iran main enrichment facility causing Iran to suspend work at nuclear facility! n Also attacked the Bushehr nuclear facility still under construction n Could lead to national blackout Iran – open call for hackers to be part of the iranian nd largest online army in the world revolutionary guard – 2 Mrs S. Armoogum Lecture 1 Security Concepts 7

How it works! n n n Stuxnet infects Windows computers - primarily spreads via USB sticks (allows infection of computers not connected to Internet) Once inside a network, it propagate to other machines & gain privilege. Windows computer not the real target. Stuxnet looks for a Programmable Logic Controller (PLC) made by Siemens (Siemens Simatic Step 7) – embedded industrial control systems – used in manufacturing plants, oil refineries, nuclear power plants etc. Written to attack Supervisory Control And Data Acquisition (SCADA) systems used to control & monitor industrial processes. Stuxnet includes capability to reprogram the PLCs – control many things e. g. turn on pressure inside nuclear reactors, Mrs S. Armoogum 8 switch-off oil pipelines Lecture 1 Security Concepts

How it works! n Stuxnet hide its changes (rootkit) tells OS everything is normal. n Stuxnet install its own driver on the victim computer. n n Drivers should be signed for them to work in Windows Stuxnet driver was signed with a real certificate stolen from Realtek Semiconductor Corp Stuxnet did not use forged security clearance like other viruses n Stolen certificate been revoked on 16 th July but a modified variant signed with a certificate stolen from JMicron Mrs S. Armoogum Lecture Concepts Technology Corporation was 1 Security found on 17 th July!! 9

About Stuxnet n Stuxnet 20 times more complex than other malware - Stuxnet is over 1. 5 MB in size. n It exploits 20 unknown vulnerabilities (zero day exploits) and drops its own driver to the system. n One Zero day exploit sold on market for like $100 000 n Some not yet patched up by Microsoft n E. . g LNK (MS 10 -046), Print Spooler (MS 10 -061), Server Service (MS 08 -067); Privilege escalation via Keyboard layout file; Privilege escalation via Task Scheduler Mrs S. Armoogum Lecture 1 Security Concepts 10

Who created Stuxnet? n Rumor Israel n Code contains references to Hebrew Bible - "Myrtus" (myrtle plant). n Not "hidden" in code artifact left inside program when it was compiled. tells us where author stored the source code in his system. n Specific path in Stuxnet is: myrtussrcobjfre_w 2 k_x 86i 386guava. pdb. n Author(s) called project “Myrtus” n Could also mean "My RTUs“ - RTU abbr for Remote Terminal Units, used in factory systems. n Stuxnet know it has already infected a machine as it sets Registry key with a value "19790509" as an infection marker. Mrs S. Armoogum Lecture 1 Security Concepts 11 n "1979050” is date. 9 th of May, 1979. birthday of the

Who created Stuxnet? n n n US also suspected for testing & development of Stuxnet Siemens also suspected In June 2012, The New York Times reports that the U. S. and Israel developed the worm. n President Obama, and his predecessor President Bush, had overseen the development of a secret and highly sophisticated U. S cyber campaign to disrupt and degrade Iranian nuclear capabilities. n codenamed "Olympic Games" by the Bush Administration Concern that other nations will retaliate! US being the target Stuxnet Open source weapon – people may redesign it!! Many offshoots since: Duqu, Flame, Wiper, Gauss Mrs S. Armoogum Lecture 1 Security Concepts 12

Stuxnet offspins n n n Duqu – Sep 2011 - shares a lot of code with Stuxnet but is designed for a different purpose: stealing data for surveillance or other intelligence efforts. Duqu exploits zeroday Windows kernel vulnerabilities, uses stolen digital certificates, installs a backdoor, & captures keystrokes and information that could be used to attack industrial control systems. Gauss – Sep 2011 - Gauss is capable of stealing browser passwords, online banking accounts, cookies, & system configurations. Mahdi – Feb 2012 - Mahdi records keystrokes, screenshots, and audio and steals text & image files. Its name comes from Mrs S. Armoogum Lecture 1 Security Concepts 13 references in the code to the word for the Islamic Messiah. It

Stuxnet offspins n n n Flame – May 2012 - designed for intelligence gathering. Flame uses a fraudulent digital certificate and spreads via USB stick, local network, or shared printer spool vulnerability and leaves a backdoor on computers. It can sniff network traffic and record audio, screenshots, Skype conversations, and keystrokes, as well as download information from other devices via Bluetooth. Wiper – April 2012 - malware attack shutting down computer systems at companies in Iran, including the Oil Ministry. Malware wipes data from hard drives, placing high priority on those with a. pnf extension, which are the type of files Stuxnet and Duqu used. Shamoon – Aug 2012 - attacks Windows computers & designed for espionage. Shamoon – believed to be a Wiper copycat targeting oil companies. Amateurs Not nation-state 14 Mrs S. Armoogum Lecture 1 Security Concepts

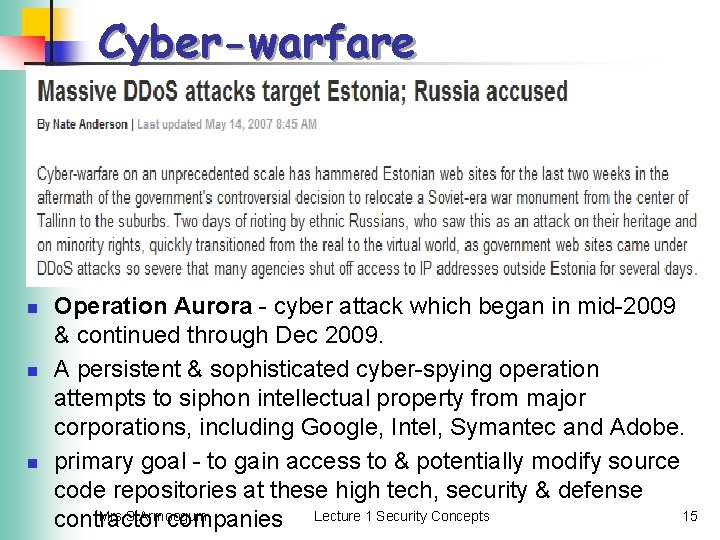
Cyber-warfare n n n Operation Aurora - cyber attack which began in mid-2009 & continued through Dec 2009. A persistent & sophisticated cyber-spying operation attempts to siphon intellectual property from major corporations, including Google, Intel, Symantec and Adobe. primary goal - to gain access to & potentially modify source code repositories at these high tech, security & defense Mrs S. Armoogum 15 contractor companies Lecture 1 Security Concepts

Sony’s nightmare n n n April 2011 - DDo. S attack on sony PSN (playstation network – online games center) by Anonymous collective - operation called #Op. Sony Revenge – because Sony sued hacker George Hotz (geohot) Jan 2011 who jailbreak PS 3 (remove limitations laid by Sony) The PSN servers were also hacked (not by Anonymous) & users data stolen - about 77 million Playstation accounts were jeopardised by a malicious intrusion between April 17 & 19 Data stolen includes – name, address (city, state, and zip), Country, E-mail address, Birthday, PSN password and login name and even credit card numbers. n Sony claims that credit cards numbers were stored as cryptographic hash values Mrs S. Armoogum Lecture 1 Security Concepts 16 These data may be used for identity theft attacks later

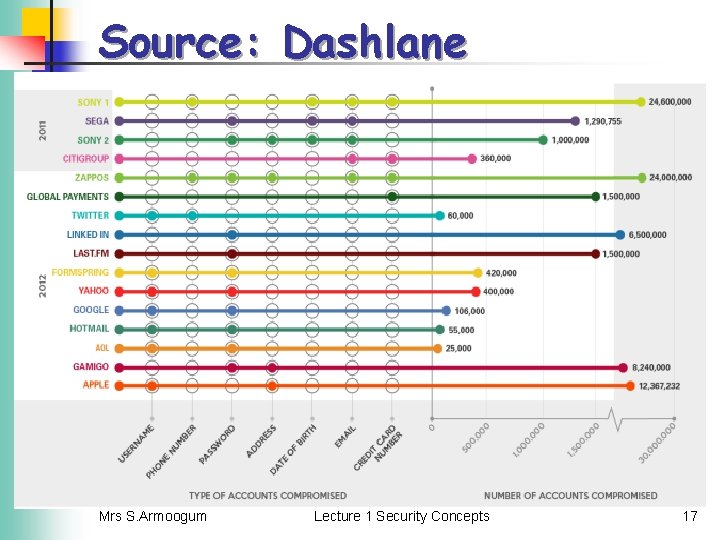
Source: Dashlane Mrs S. Armoogum Lecture 1 Security Concepts 17

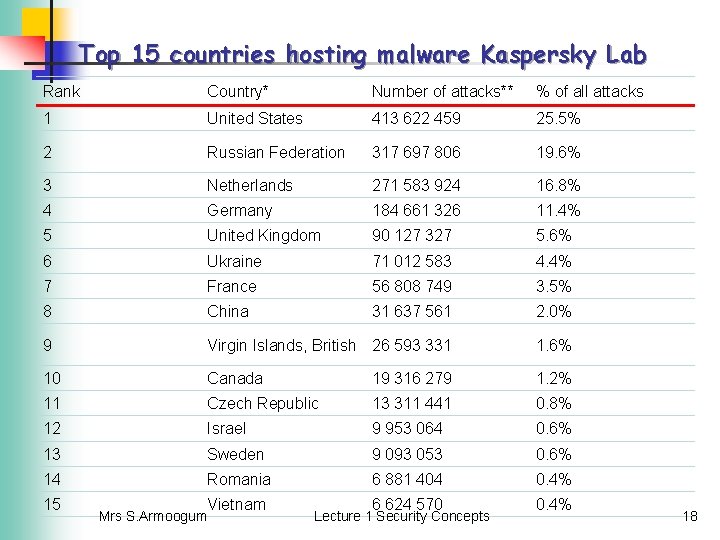
Top 15 countries hosting malware Kaspersky Lab Rank Country* Number of attacks** % of all attacks 1 United States 413 622 459 25. 5% 2 Russian Federation 317 697 806 19. 6% 3 Netherlands 271 583 924 16. 8% 4 Germany 184 661 326 11. 4% 5 United Kingdom 90 127 327 5. 6% 6 Ukraine 71 012 583 4. 4% 7 France 56 808 749 3. 5% 8 China 31 637 561 2. 0% 9 Virgin Islands, British 26 593 331 1. 6% 10 Canada 19 316 279 1. 2% 11 Czech Republic 13 311 441 0. 8% 12 Israel 9 953 064 0. 6% 13 Sweden 9 093 053 0. 6% 14 Romania 6 881 404 0. 4% 6 624 570 0. 4% 15 Vietnam Mrs S. Armoogum Lecture 1 Security Concepts 18

Theft of personal data n n n 10: Wyndham Hotels. credit card data was stored in plain text - cyber thieves broke in & stole some. Still no increase in security – lightning doesn’t strike twice - Wyndham got hit 3 times in 3 years. More than 600, 000 credit card nos stolen & some $10. 5 billion in fraudulent transactions reported. 9: July 11 th - More than 400, 000 plaintext Yahoo passwords posted on Internet. Focused on voice services – used SQL injection to collect data. D 33 Ds Company warning wakeup call as security holes exploited in Yahoo! Web servers caused far greater damage than this disclosure. 8: Hacktivist group "Anti. Sec" released an archive of more than a million Apple Unique Device Identifiers (UDIDs) stolen from an FBI computer using a Java vulnerability Sep. Mrs S. Armoogum 1 Security 19 Maybe to embarrass FBI, Lecture which was. Concepts in the midst of

Theft of personal data n n 7: March, transaction processor Global Payments confirmed a network penetration resulting in the data theft of approximately 1. 5 million credit cards including Track 2 data which can be used to clone credit cards. 6: Dec 10 - Hacktivist "Team Ghostshell" posted to Pastebin records from approximately 1. 6 million government & contractor accounts involving aerospace, defense industry, financial services & law enforcement. Stolen data names, email addr, passwords, phone nos etc. Project. White. Fox 5: June, social networking pioneer Linked. In was tapped for approximately 6. 5 million passwords, which were comprised of unsalted SHA-1 hashes. Bad guys published hash passwords in various places to get help cracking them! 4: Oct 3, An attack on a network used by both the Mrs S. Armoogum Lecture 1 Security Concepts 20 Nationwide Insurance Company and the Allied Insurance

Theft of personal data n n n 3: Approximately 3. 8 million tax records and nearly 400, 000 credit card numbers were stolen from the South Carolina Department of Revenue spearphishing exploit that stole employee usernames and passwords to gain access to the sensitive data. Improper password policies and failure to encrypt social security numbers were key enablers of the operation - largest data theft from a state government. 2: Jan - Zappos online shoe and clothing - Personal details on as many as 24 million people were hacked and stolen. Fortunately for the victims, however, passwords were at least encrypted. 1: Governments reportedly exposed more than 94 million records containing personally identifiable info. In addition to hacking incidents, the numbers include unintended disclosure, the loss or theft of 1 portable devices and physical 21 Mrs S. Armoogum Lecture Security Concepts

Lessons learnt! n User data in databases not being properly secured n Passwords should be salted & encrypted n Other sensitive data such as credit card numbers, social security number etc. should be encrypted. n Access to network resources should be properly secured. n Users tend to use same password in various web-based services to gain remote access to corporate networks n Weak passwords – hashed password easily broken! Mrs S. Armoogum Lecture 1 Security Concepts 22

Worm steals 45, 000 Facebook passwords n n n Jan 2012 - Data mainly from Facebook accounts in UK & France, according to security firm Seculert. malware - dubbed Ramnit - which has been around since April 2010 & previously stolen banking details. Attackers behind Ramnit - using stolen credentials to login to victims' Facebook accounts & to transmit malicious links to their friends spreading malware even further Also using facebook credentials to get access to other resources e. g. gmail, bank a/c, email servers etc as people tend to use same password! Ramnit - infects Windows executables, Microsoft Office & HTML files. n can steal user names, passwords, browser cookies, and allow hackers to do other malicious actions on an infected Mrs S. Armoogum Lecture 1 Security Concepts 23 computer.

Why is security difficult? n n Rapidly evolving threats. New hacker tools, techniques, methods, scripts, and automated hacking malware everyday. TOR – The onion routing anonymity online n Hackers are also using Tor!! n I 2 P is an anonymizing network, offering a simple layer that identity-sensitive applications can use to securely communicate n Freenet is a fully distributed, peer to peer anonymous publishing network, offering secure ways to store data & applications on top of it allows generic anonymous communication, such as static websites & message boards. “To catch a thief, you must think like a thief. ” Mrs S. Armoogum Lecture 1 Security Concepts 24

TOR anonymity online n n n http: //www. torproject. org/index. html. en Tor is free software and an open network that helps you defend against a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security known as traffic analysis. Tor is the second-generation low-latency anonymity network of onion routers that enables users to communicate anonymously across the Internet. Originally sponsored by the U. S. Naval Research Laboratory Became an Electronic Frontier Foundation (EFF) project in 2004 Mrs S. Armoogum Lecture 1 Security Concepts 25

Traffic analysis n Traffic analysis – gather info based on traffic pattern (header info). n source and destination of Internet traffic allows others to track your identity, location, behaviour & interests and even data being sent. n Internet data packets have 2 parts: data payload + header n Data payload content being sent e. g. email can be encrypted for protection n Headers – not encrypted as intermediate routers need to S. Armoogum read Mrs header info Lecture 1 Security Concepts 26

Who uses Tor? n Journalists, bloggers, activist groups , corporations (to protect sensitive procurement patterns – VPN reveal amt of traffic and time) n A branch of the U. S. Navy uses Tor for open source intelligence gathering, and one of its teams used Tor while deployed in the Middle East recently. n Law enforcement uses Tor for visiting or surveilling web sites without leaving government IP addresses in their web logs, and for security during sting operations. n Mrs S. Armoogum Attackers Lecture 1 Security Concepts 27

How it works n n n Volunteers operate an onion proxy server on their system that allows users of the Tor network to make anonymous outgoing connections via TCP. Users of Tor network must run an onion proxy on their system, which allows them to communicate to the Tor network & negotiate a virtual circuit. Tor employs advanced cryptography in a layered manner, thus the name “Onion” Router. Advantage – Tor application independence - works at TCP stream level. Supports instant messaging, Internet Relay Chat (IRC), and web browsing Not 100 percent foolproof or stable BUT advance in anonymous communications across the Internet Mrs S. Armoogum Lecture 1 Security Concepts 28

CSI/FBI Computer crime & Security survey n n n Computer Security Institute (San Francisco, California) in cooperation with the FBI produces a yearly report called the CSI/FBI Computer Crime and Security Survey: more than 600 individuals from all over US representing all types of business organizations in terms of size and operation most representative source of assessment of the security status of businesses. Some of the key findings from the 2008 survey were: n Virus attacks continue to be the source of the greatest financial losses. n Unauthorized access continues to be the second-greatest source of financial loss. n Financial losses related to laptops (or mobile hardware) and theft of proprietary information (i. e. , intellectual Mrs S. Armoogum 1 Security Concepts 29 property) are third and. Lecture fourth. These four categories

Why is security important? n Typically driven by legal, finance, or operations within a large company, today security risk management is now a mainstream concept. n To protect company assets n To gain a competitive advantage - arena of Internet financial services and e-commerce. n To comply with regulatory requirements & fiduciary responsibilities - ensure the safety and soundness of organization & employee. n Continuity of operations and correct functioning of information systems is important to most businesses Mrs S. Armoogum Lecture 1 Security Concepts 30

Regulatory Expectations n Health Information Portability and Accountability Act (HIPAA). Regulations regarding treatment of patient healthcare information - health-care industry n Gramm-Leach-Bliley Act (GLBA) - Financial institutions protecting clients information & rights. n Sarbanes-Oxley Act came into force in July 2002 and introduced major changes to the regulation of corporate governance and financial practice. n Family Educational Rights and Privacy Act (FERPA). n 1974 Privacy Act - Guidelines on keeping individual's records & on individual rights to review such documents. Mrs S. Armoogum Lecture 1 Security Concepts 31

Where to get help? n Several organizations ready to provide expert assistance in case of attack: n The Computer Emergency Response Team (CERT) at Carnegie Mellon University created to provide info & support against any Internet crises, cyber attacks, accidents, or failures. n Funded by DARPA. n Now officially named the CERT Coordination Center (mother-of-all-CERTs), n Regional and corporate incident response centers are springing up to handle crises locally e. g. Aus. CERT (Australian CERT), Can. CERT (Canada), CERT Polska, Sing. CERT (Singapore CERT), SI-CERT (Slovenia), National Infrastructure Security Co-ordination Centre Mrs S. Armoogum Lecture 1 in Security Concepts 32 (NISCC) in UK, CERT-MU 2008

Others - SANS n http: //isc. sans. edu/diary. html Mrs S. Armoogum Lecture 1 Security Concepts 33

Computer Security n Before computers - security enforced by physical & administrative means (filing cabinets with locks) n computer networking – Nowadays very few computers are standalone. With the advent of computer networking almost all computers are interconnected. There is a need for sophisticated & automated tools to protect resources. n Collection of tool designed to protect data and to thwart attackers is computer security. Mrs S. Armoogum Lecture 1 Security Concepts 34

Understanding Security n Security - protecting valuable assets of computer system: n Hardware (including communication devices), n Software, Software and storage media n Data (stored or in transit) n People , Intangible assets: assets reputation (e-commerce) n Network Security: To be Connected or not to be? n Security – subjective – security level. n n General law of security - No solution is perfect. Given time, money, & motivation, any security system can be compromised. "Security is a process, not a product. " Security - is the Mrs S. Armoogum Lecture 1 Security Concepts culmination of interaction between people, process, and 35

Security Infrastructure n n n No-out-of box, plug-n-play security solution Policies form the foundation of your security infrastructure. n Policies define how a company approaches security, how employees should handle security, & how certain situations will be addressed - broad statement of principle. People are the next most important security component. n People - weakest link. Corporate security relies on password a user chooses – easy to crack. Security-Aware users. Surprisingly, technology - least important component. n Technology only provides the means to implement policies. Security must be pervasive Every aspect of a company should security conscious. Mrs be S. Armoogum Lecture 1 Security Concepts 36

Computer Security Policy n n n A computer security policy defines the goals & elements of an organization's computer systems protection. No security policy confidentiality, Integrity & availability of network can be compromised. n 1. Assess risk to network & build a team to respond. Risk Analysis n 2. Implement a security change management practice & monitor the network for security violations. n 3. Review process modifies the existing policy and adapts to lessons learned. Security policies are enforced by organizational policies or security mechanisms. n Organisational policy – e. g. Not allowed to eat/drink in server room. Mrs S. Armoogum Lecture 1 Security Concepts 37

Ex of Policy: User Policies n Define what users can & must do to use organisation’s network – e. g. whether user can install programs on their workstations n Password Policies - keep user accounts secure. how often users must change their passwords, how long they must be, complexity of password n Proprietary Info Use – who can access, where it can be stored & where it may be taken, how & where it can be transmitted. n Internet Usage – Use of internet mail, Use of programs with passwords or unencrypted data sent over the internet. n System Use - Program installation, No Instant Messaging, No file sharing such as Kazaa. Restrictions on use of account or password (not to be given away). Mrs S. Armoogum Lecture 1 Security Concepts 38 n Acceptable use of hardware such as modems - No use of

Ex of Policy: IT Policies n These policies include general policies for the IT department which are intended to keep the network secure and stable. n Virus incident & security incident - Intrusion detection, containment, & removal. n Backup policy - what to back up, who backs it up, where it is stored, how long it is stored, how to test backups, what s/w used to backup. n Client update policies - how often & using what means or tools. n Server configuration, patch update, and modification policies (security) - Remove unneeded services (harden server). What servers should have IDS. How is it determined to do an update? What is done when someone works on the server? Mrs S. Armoogum Lecture 1 Security Concepts 39 n Firewall policies - What ports to block or allow, how to

Ex of Policy: General Policies n n High level program policy - Defines who owns other policies, who is responsible for them, scope and purpose of policies, any policy exceptions, related documents or policies. Business continuity plan - Includes the following plans: n Crisis Management - What to do during the (any) crisis which may threaten the organization. n Disaster Recovery - Subfunctions: n Server recovery n Data recovery n End-user recovery n Phone system recovery n Emergency response plan n Workplace recovery Mrs S. Armoogum Lecture 1 Security Concepts 40

Policies for UTM n Write down some security policies for UTM computer network. n n Check user identity before giving access Access to authorised users: outsiders not allowed any access, students allowed in labs but not to computers elsewhere, only financial dept staff allowed access to financial info/db, all administrative staff not allowed access to student info, etc. Some files should only be read and written to by some privileged users, etc Technology allows us to implement policies Mrs S. Armoogum Lecture 1 Security Concepts 41

How much to spend on security? n n More money more secure network. Don’t want to spend more money on security than the cost of what you are protecting. n n cost to replace compromised data is $200, 000, do not want to spend $1 million to protect that data. Also even if unlimited money spent on security - never completely secure network! Risk analysis is a technique for quantitative assessment of the relative value of protective measures Approach - methodical, more precise, but can be slow and have high initial costs. Mrs S. Armoogum Lecture 1 Security Concepts 42

More on Risk Analysis n Why Should a Risk Analysis Be Conducted? n n When Should a Risk Analysis Be Conducted? n n With an effective risk analysis process in place, only those controls and safeguards that are actually needed will be implemented. Before starting a task, project, or development cycle, an enterprise should conduct an analysis of the need for the project. Understanding the concepts of risk analysis and applying them to the business needs of the enterprise will ensure that only necessary spending is done. Who Should Conduct the Risk Analysis? n A process such as the Facilitated Risk Analysis Process (FRAP) takes advantage of 1 the internal Mrs S. Armoogum Lecture Security Concepts experts. No one 43

Assessing Risk n Risk - probability of a threat taking advantage of a vulnerability. n When a threat has a chance to exploit a vulnerability - risk needs to be addressed. n E. g. On-site storage of backups coupled with a catastrophic fire creates a risk that seriously affects availability of data. n When a company suffers losses from a threat an exposure. n Prevent exposures by implementing countermeasures. Mrs S. Armoogum Lecture 1 Security Concepts 44

Vulnerability n Vulnerability – inherent weakness in design, configuration, implementation, or management of a network or system that renders it susceptible to a threat - might be exploited to cause loss or harm n Unlocked doors to server rooms; n unnecessary services running on a server, n flaws in program or the security protecting the program, n Data backups that are not regularly performed, and not stored in secure locations, n Easy-to-guess passwords, hard-to-remember passwords user writes password, n system not verifying a user’s identity before giving access - unauthorized data manipulation. Mrs S. Armoogum Lecture 1 Security Concepts 45

Threat, Attack, Control n Threat - anything that can disrupt the operation, functioning, integrity, or availability of a network or system – potential dangers of any type n Malevolent, Accidental, or simply an act of nature (flood). n An attack is a specific technique used to exploit a vulnerability. n E. g. threat - denial of service, system unavailable. Vulnerability limited buffer space n A control/countermeasure is an action, device, procedure, or technique that removes or reduces a vulnerability/threat. Mrs S. Armoogum Lecture 1 Security Concepts 46

Threat – 4 types n n Interception: unauthorized party (person, program, system) gain access to an asset. Ex. Illicit copying of program/data files, or wiretapping. Attack on confidentiality. Interruption (Denial Of Service - Do. S): asset lost, unavailable, or unusable. Ex. Malicious destruction of a hardware device, erasure of program/data, or cutting communication wire. Attack on availability. Modification: unauthorized party not only access but tampers with asset. Ex. Change values in DB, alter program so that it performs additional computation, modify data being transmitted. Attack on integrity. Fabrication: Intruder inserts spurious messages to a Mrs S. Armoogum Lecture 1 Security Concepts communication or add records to a database. Attack on 47

Risk Analysis & Management n Risk analysis allows to sort risk exposure and, based on the possible damage from an exposure, justify the cost of security. n Once risks identified & possible loss from exposure is defined - begin the process of risk management. n Risk management is the process of reducing risk to an acceptable level, transferring the risk to another entity such as an insurance company, rejecting the risk outright, or accepting the risk. Mrs S. Armoogum Lecture 1 Security Concepts 48

Top Down Approach 1. Asset Analysis: What needs to be protected? The measures taken to protect assets should correspond to the value of assets. 2. Threat Analysis: What the system is to be protected against i. e. what threats are to be countered - (employee vengeance, crackers, espionage, technical failures etc. ). Identify vulnerabilities. Potential ways in which threats can be realised? 3. Impact Analysis: What is the probability of a vulnerability being exploited? What is the impact or consequence (harm to business - financial) if a threat, or a combination of threats is realised? 4. Constraints Analysis: Examine requirements outside of your control (national & international laws, corporate requirements, corporate culture, budget). 5. Identify potential protective measures - cost effective Mrs S. Armoogum Lecture 1 Security Concepts 49 control mechanism.

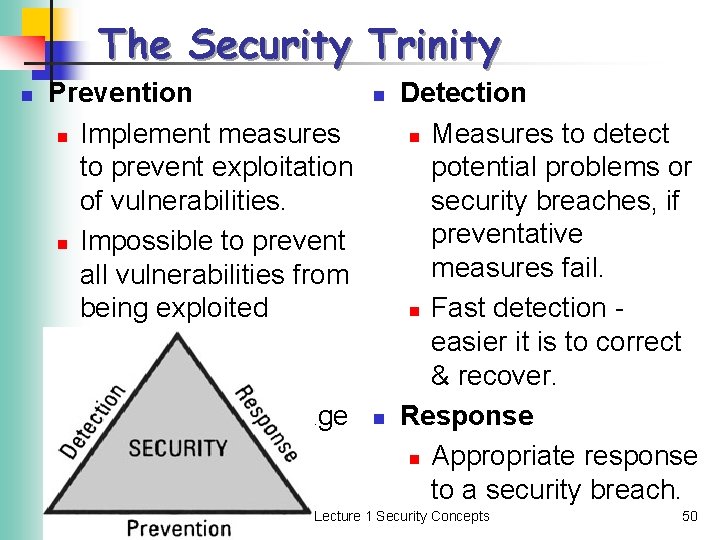
The Security Trinity n Prevention n Implement measures to prevent exploitation of vulnerabilities. n Impossible to prevent all vulnerabilities from being exploited n Preventative measures strong enough to discourage potential attackers Mrs S. Armoogum n n Detection n Measures to detect potential problems or security breaches, if preventative measures fail. n Fast detection easier it is to correct & recover. Response n Appropriate response to a security breach. Lecture 1 Security Concepts 50

Mrs S. Armoogum 51