Data and Computer Communications Chapter 2 Protocol Architecture










- Slides: 49

Data and Computer Communications Chapter 2 – Protocol Architecture, TCP/IP, and Internet-Based Applications

Protocol Architecture, TCP/IP, and Internet-Based Applications Ø To destroy communication completely, there must be no rules in common between transmitter and receiver—neither of alphabet nor of syntax —On Human Communication, Colin Cherry

Need For Protocol Architecture Ø data exchange can involve complex procedures, file transfer example Ø better if task broken into subtasks Ø implemented separately in layers in stack l l each layer provides functions needed to perform communications for layers above using functions provided by layers below Ø peer layers communicate with a protocol

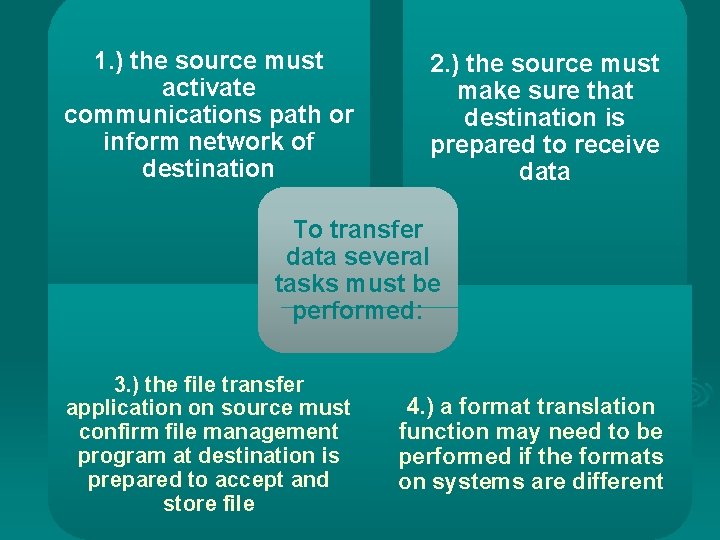
1. ) the source must activate communications path or inform network of destination 2. ) the source must make sure that destination is prepared to receive data To transfer data several tasks must be performed: 3. ) the file transfer application on source must confirm file management program at destination is prepared to accept and store file 4. ) a format translation function may need to be performed if the formats on systems are different

Functions of Protocol Architecture Ø breaks logic into subtask modules which are implemented separately Ø modules are arranged in a vertical stack each layer in the stack performs a subset of functions • relies on next lower layer for primitive functions • changes in one layer should not require changes in other layers •

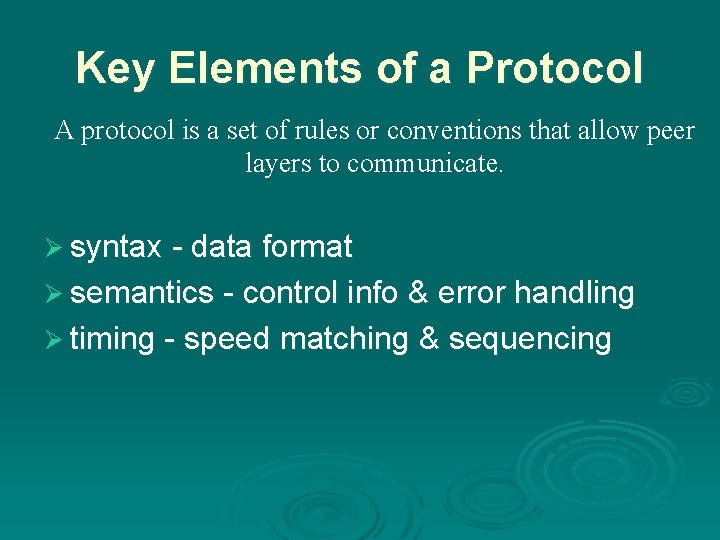
Key Elements of a Protocol A protocol is a set of rules or conventions that allow peer layers to communicate. Ø syntax - data format Ø semantics - control info & error handling Ø timing - speed matching & sequencing

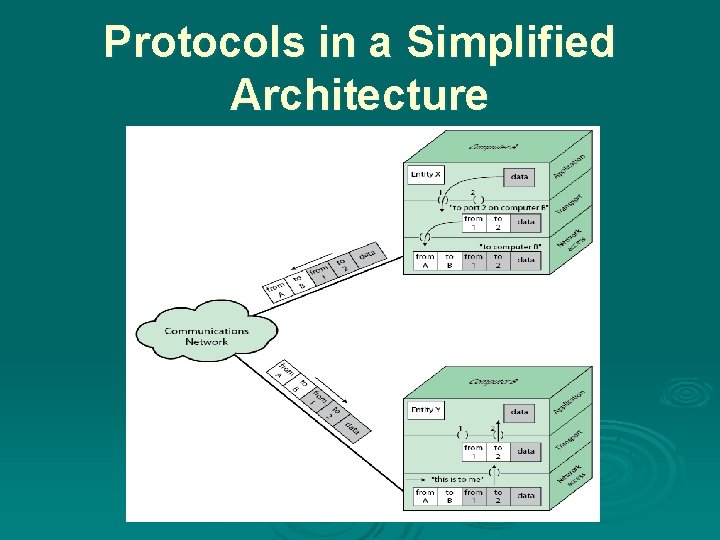
A Simple Protocol agents involved: • applications • computers • networks these execute on computers that support multiple simultaneous applications examples of applications include file transfer and electronic mail

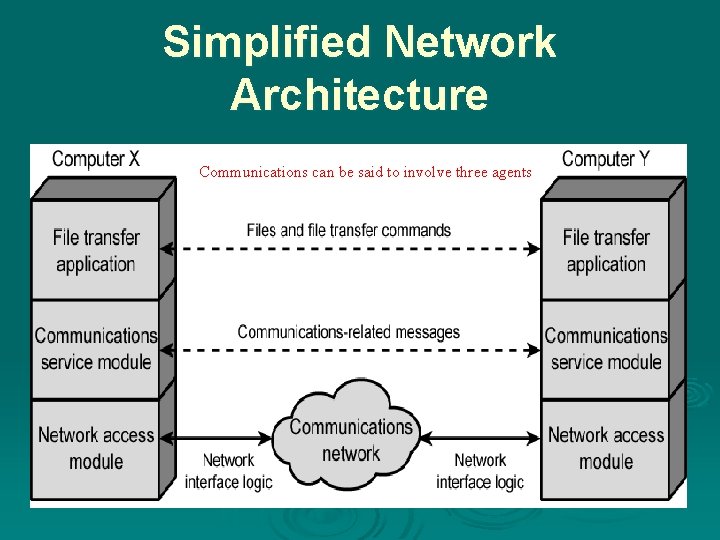
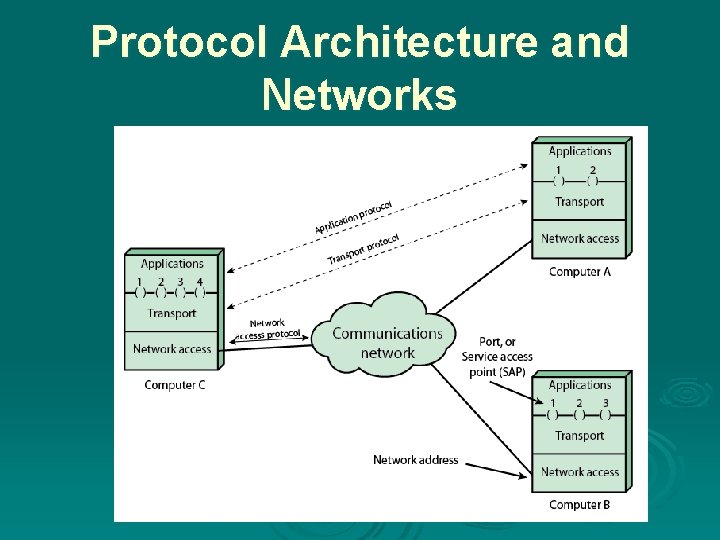
Simplified Network Architecture , Communications can be said to involve three agents

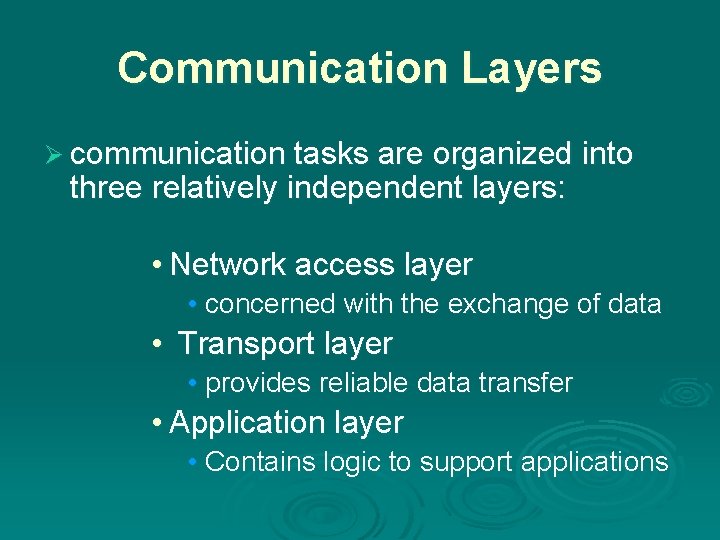
Communication Layers Ø communication tasks are organized into three relatively independent layers: • Network access layer • concerned with the exchange of data • Transport layer • provides reliable data transfer • Application layer • Contains logic to support applications

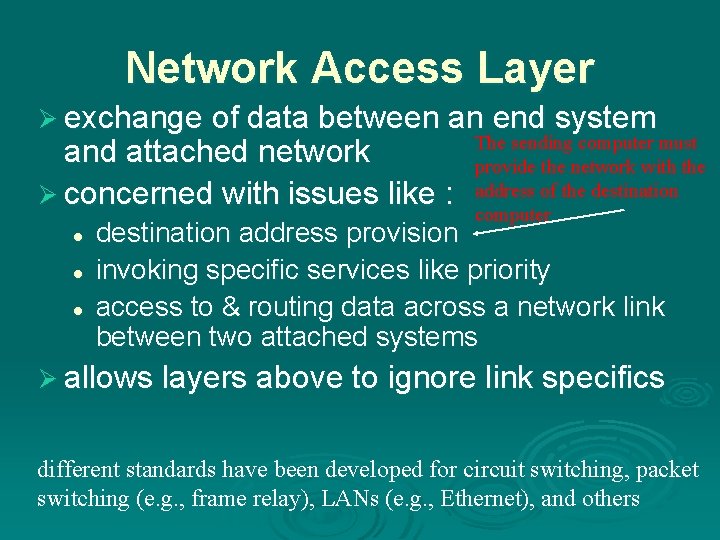
Network Access Layer Ø exchange of data between an end system and attached network Ø concerned with issues like : l l l The sending computer must provide the network with the address of the destination computer destination address provision invoking specific services like priority access to & routing data across a network link between two attached systems Ø allows layers above to ignore link specifics different standards have been developed for circuit switching, packet switching (e. g. , frame relay), LANs (e. g. , Ethernet), and others

Application Layer contains the logic needed to support user applications separate module is needed for each type of application

Protocol Architecture and Networks

Protocols in a Simplified Architecture

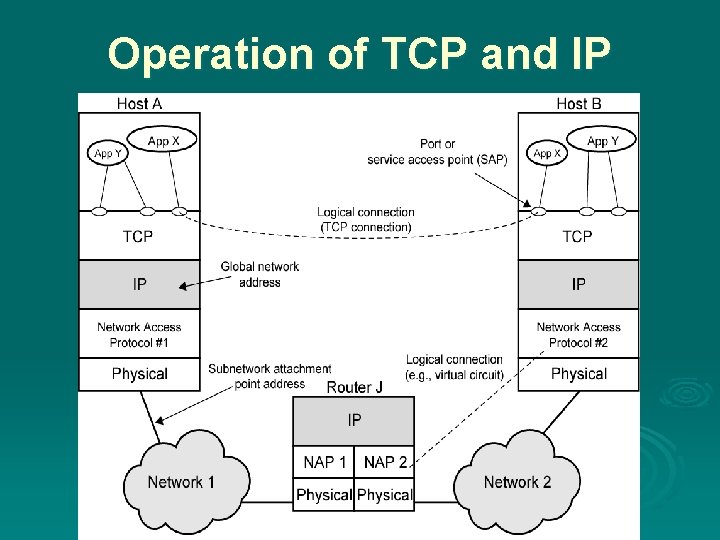
Addressing and addressing Requirements every entity in the overall system must have a unique address. Ø two levels of addressing required Ø each host on a subnet needs a unique global network address l its IP address Ø each application on a (multi-tasking) host needs a unique address within the host l known as a port or SAP(service acces point)

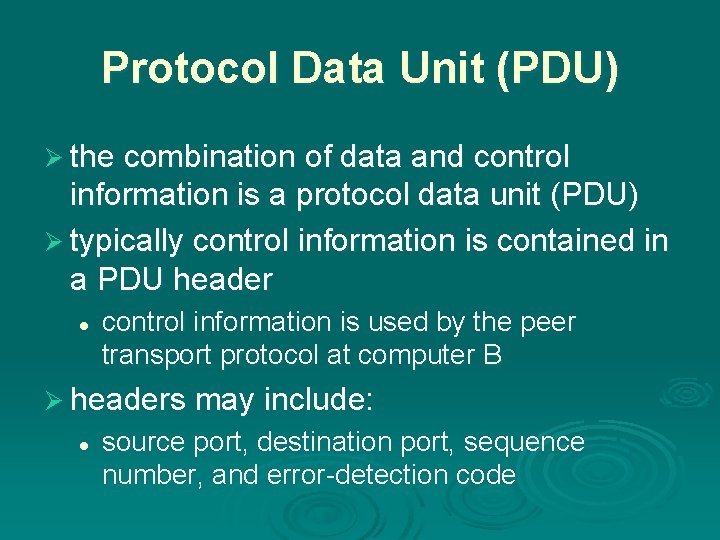
Protocol Data Unit (PDU) Ø the combination of data and control information is a protocol data unit (PDU) Ø typically control information is contained in a PDU header l control information is used by the peer transport protocol at computer B Ø headers may include: l source port, destination port, sequence number, and error-detection code

Network Access Protocol Ø after receiving segment from transport layer, the network access protocol must request transmission over the network l the network access protocol creates a network access PDU (packet) with control information Ø header includes: l l l source computer address destination computer address facilities requests

TCP/IP Protocol Architecture Ø developed by US Defense Advanced Research Project Agency (DARPA) Ø for ARPANET packet switched network Ø used by the global Internet Ø protocol suite comprises a large collection I S of standardized protocols O e h t uil he t n e s a bi o B Open System Interconnection Reference Model f o s t

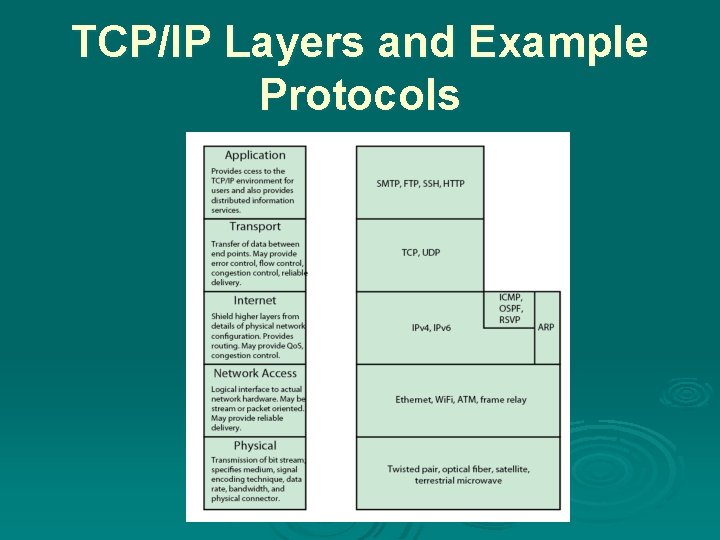
TCP/IP Layers Ø no official model but a working one l Application layer l Host-to-host, or transport layer l Internet layer l Network access layer l Physical layer

TCP/IP Layers and Example Protocols

Physical Layer Ø concerned with physical interface between computer and network Ø concerned with issues like: l l characteristics of transmission medium signal levels data rates other related matters

Network Access Layer Ø covers the exchange of data between an end system and the network that it is attached to Ø concerned with issues like : l l l destination address provision invoking specific services like priority access to & routing data across a network for two end systems attached to the same network

Internet Layer (IP) This protocol is implemented not only in the end systems but also in routers Ø Covers routing functions across multiple networks Ø Used for systems attached to different networks Ø routers connect two networks and (main function) relays data between them

Host-to-Host (Transport) Layer • concerned with providing reliable delivery of data • common layer shared by all applications • most commonly used protocol is the Transmission Control Protocol (TCP)

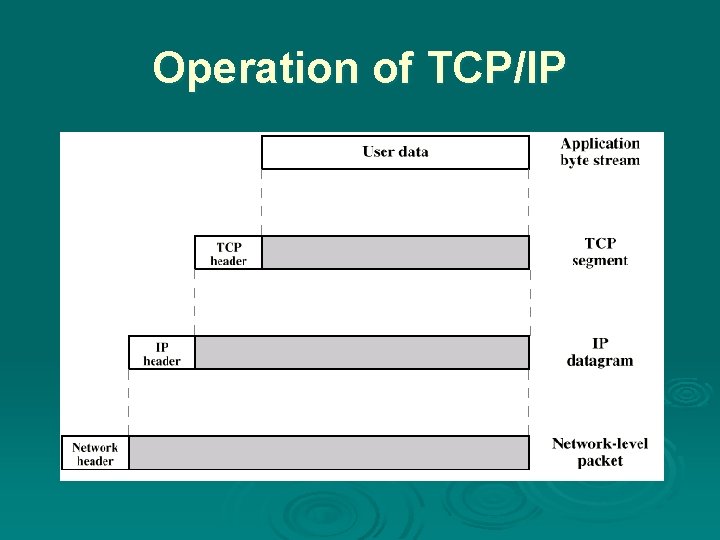
Operation of TCP and IP

TCP/IP Address Requirements Two levels of addressing are needed: each host on a subnetwork must have a unique global internet address each process with a host must have an address (known as a port) that is unique within the host

Operation of TCP/IP

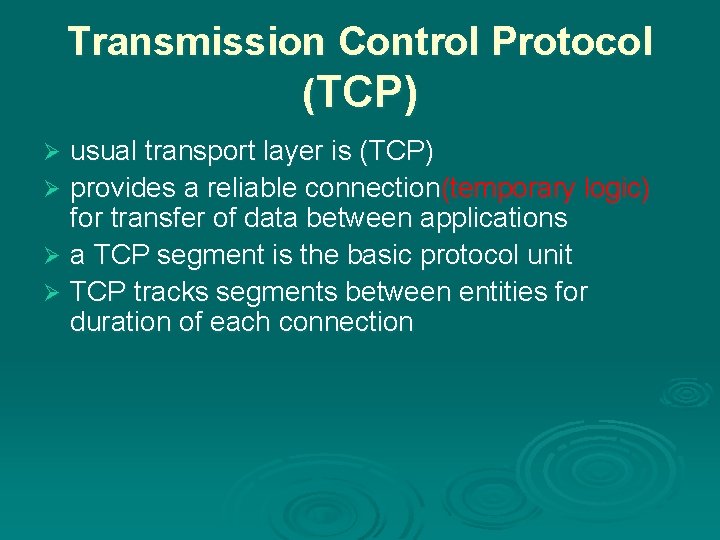
Transmission Control Protocol (TCP) usual transport layer is (TCP) Ø provides a reliable connection(temporary logic) for transfer of data between applications Ø a TCP segment is the basic protocol unit Ø TCP tracks segments between entities for duration of each connection Ø

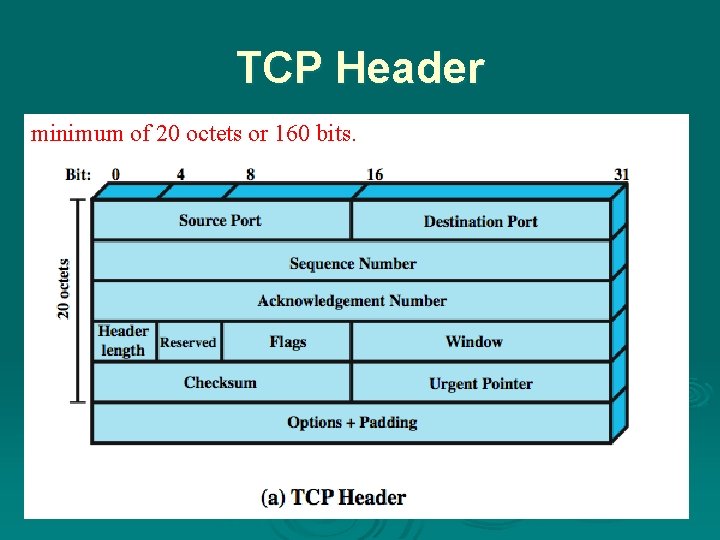
TCP Header minimum of 20 octets or 160 bits.

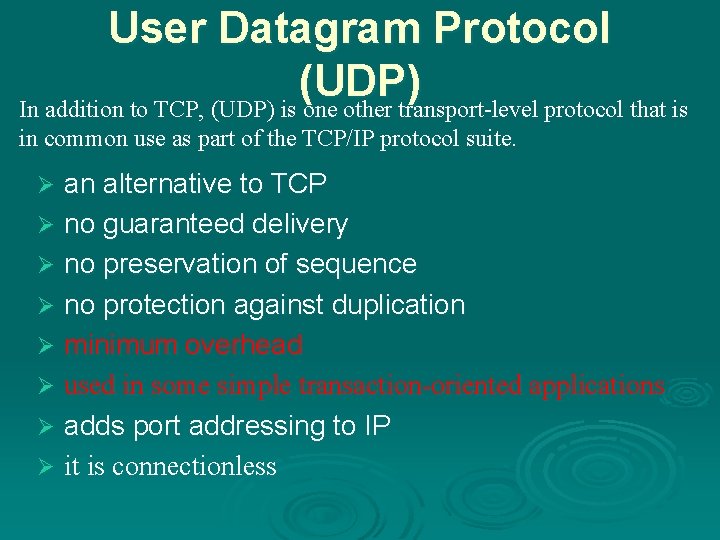
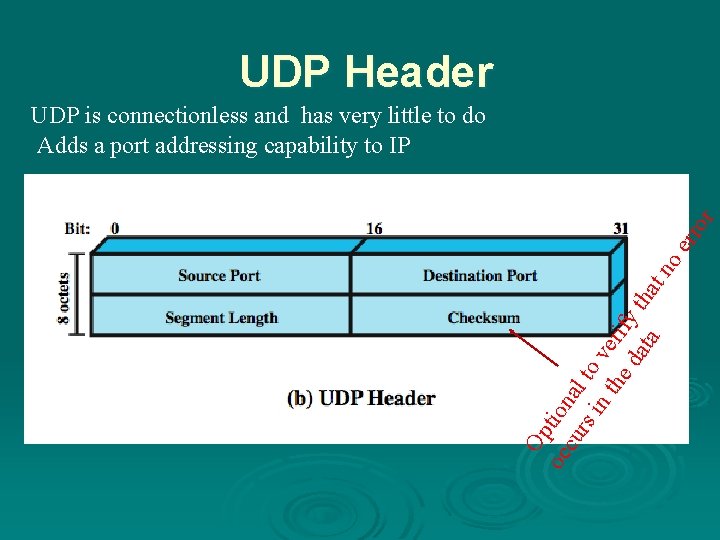
User Datagram Protocol (UDP) In addition to TCP, (UDP) is one other transport-level protocol that is in common use as part of the TCP/IP protocol suite. an alternative to TCP Ø no guaranteed delivery Ø no preservation of sequence Ø no protection against duplication Ø minimum overhead Ø used in some simple transaction-oriented applications Ø adds port addressing to IP Ø it is connectionless Ø

UDP Header Op oc tion cu al rs in to ve the ri da fy th ta at no err or UDP is connectionless and has very little to do Adds a port addressing capability to IP

IP and IP v 6 History Ø IP v 4 header format was the keystone for decades Ø In 1995 the Internet Engineering Task (develops standards and protocols) issued specs for the next generation IP (IP ng). Ø IP ng became IPv 6 in 1996. Ø IPv 6 provided a number of functional enhancement over existing IP

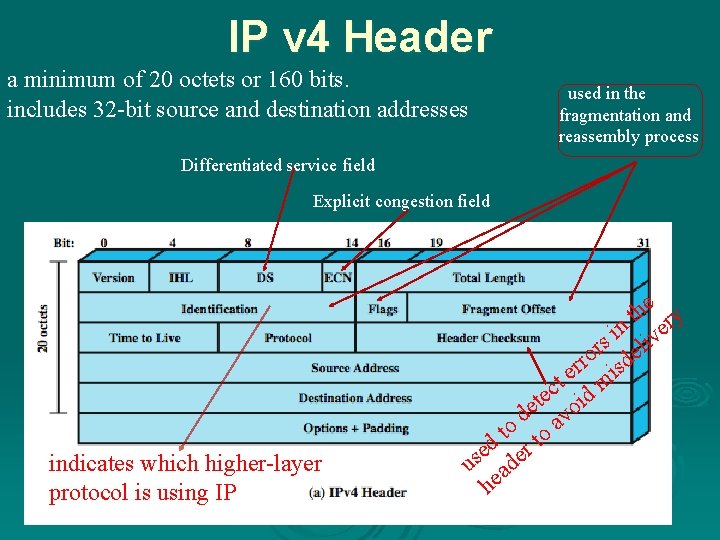
IP v 4 Header a minimum of 20 octets or 160 bits. includes 32 -bit source and destination addresses used in the fragmentation and reassembly process Differentiated service field Explicit congestion field indicates which higher-layer protocol is using IP e th ry n ve i rs eli o rr isd e t m c e t oid e d av o t to d e er s u ad he

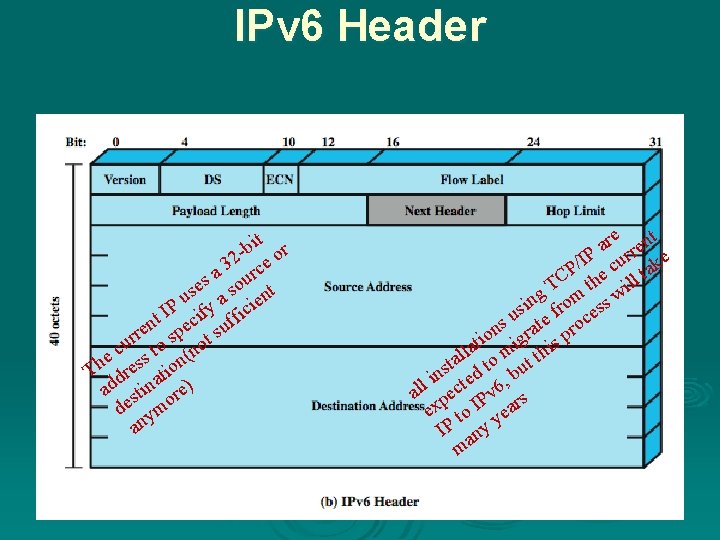
IPv 6 Ø Provides enhancements over existing IP Ø Designed to accommodate higher speeds and the mix of graphic and video data Ø Driving force was the need for more addresses due to growth of the Internet Ø IPv 6 includes 128 -bit source and destination address fields

IPv 6 Header bit or 32 rce a es sou nt s u a ie P I cify fic t f n e u e s p r ur to s not c e ss on( h T dre ati ad stin re) de ymo an re ent a IP curr ke / CP the ill ta T ing from ess w s s u ate roc n o igr s p i t la m thi l a t to but s n d i e , all pect Pv 6 rs ex to I yea IP any m

TCP/IP Applications Ø have a number of standard TCP/IP applications such as (common ones) l l l Simple Mail Transfer Protocol (SMTP) File Transfer Protocol (FTP) Telnet (provides a remote logon capability)

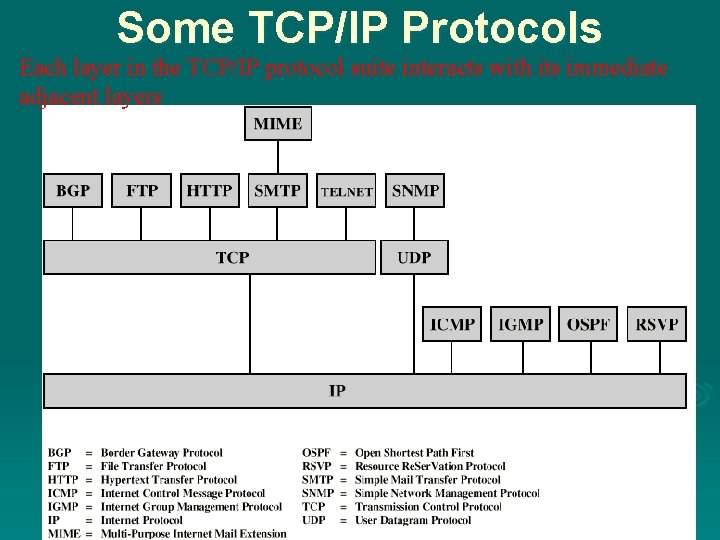
Some TCP/IP Protocols Each layer in the TCP/IP protocol suite interacts with its immediate adjacent layers

The Open Systems Interconnection OSI Ø Open Systems Interconnection Ø developed by the International Organization for Standardization (ISO) Ø has seven layers Ø is a theoretical system delivered too late! Ø TCP/IP is the de facto standard

OSI Standardization Ø framework for standardization was motivator Ø lower layers are concerned with greater levels of details Ø each layer provides services to the next higher layer Ø three key elements: Protocol specification Service definition Addressing

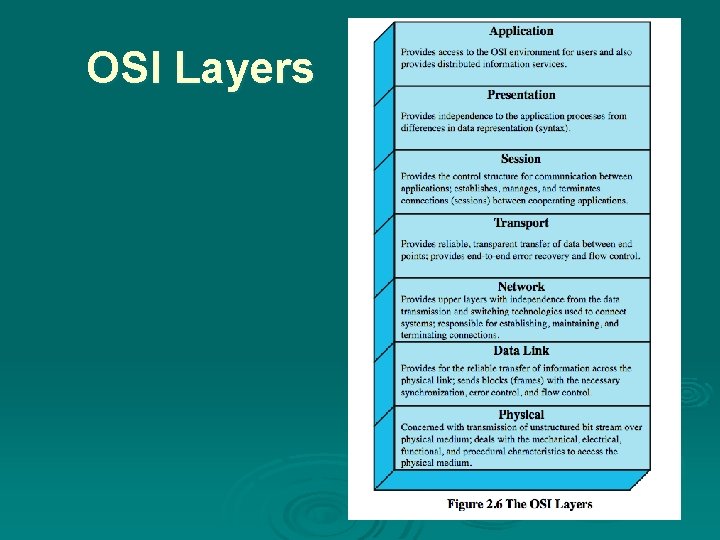
OSI Layers

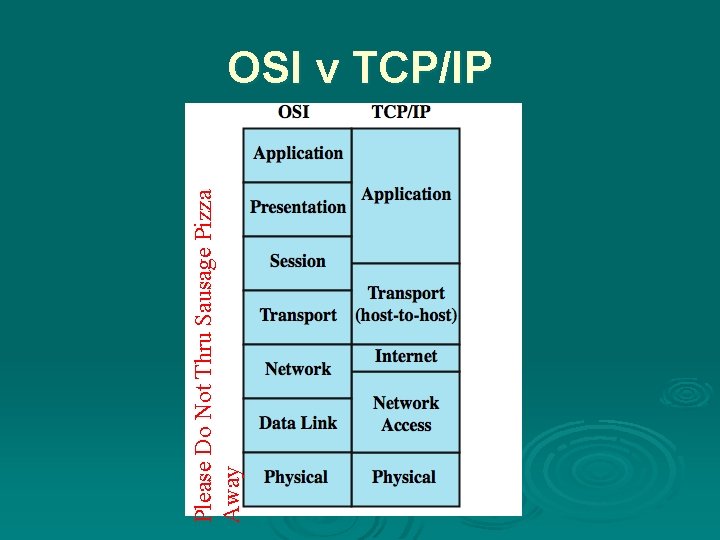
Please Do Not Thru Sausage Pizza Away OSI v TCP/IP

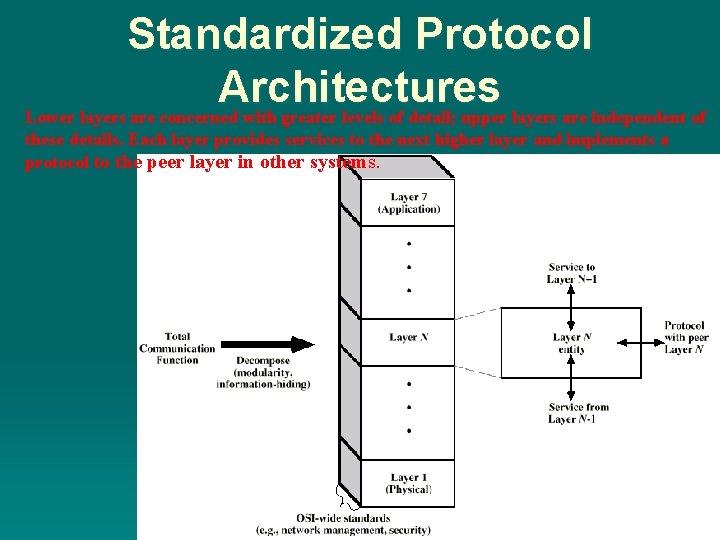
Standardized Protocol Architectures Lower layers are concerned with greater levels of detail; upper layers are independent of these details. Each layer provides services to the next higher layer and implements a protocol to the peer layer in other systems.

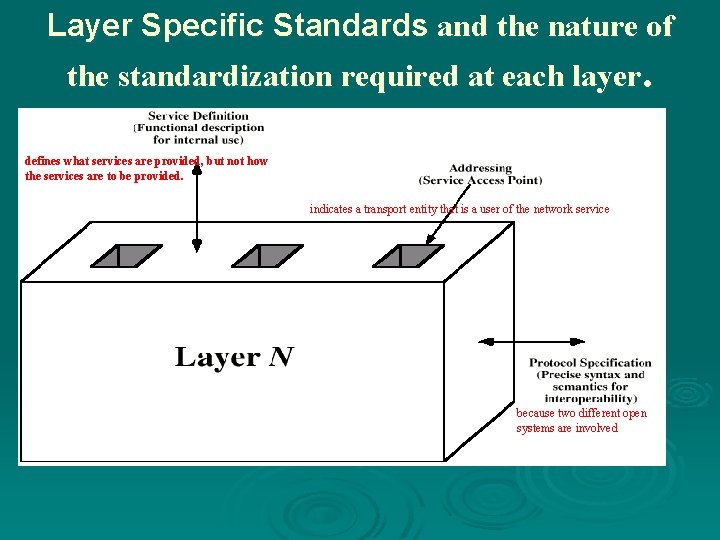
Layer Specific Standards and the nature of the standardization required at each layer. defines what services are provided, but not how the services are to be provided. indicates a transport entity that is a user of the network service . because two different open systems are involved

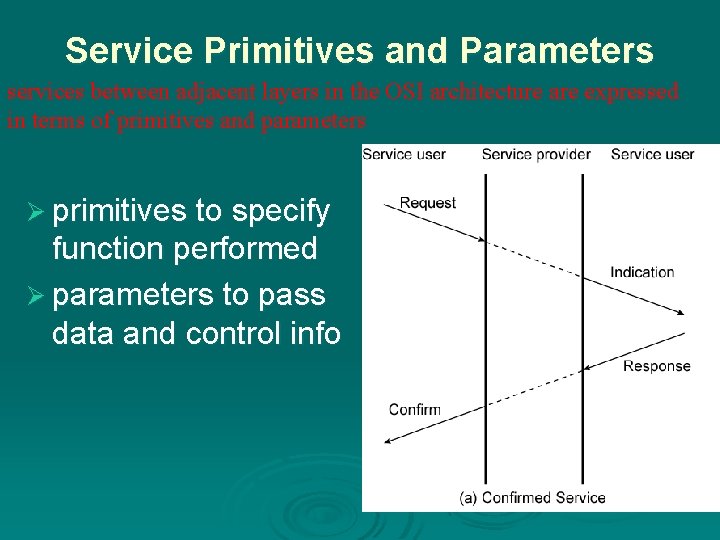
Service Primitives and Parameters services between adjacent layers in the OSI architecture are expressed in terms of primitives and parameters Ø primitives to specify function performed Ø parameters to pass data and control info

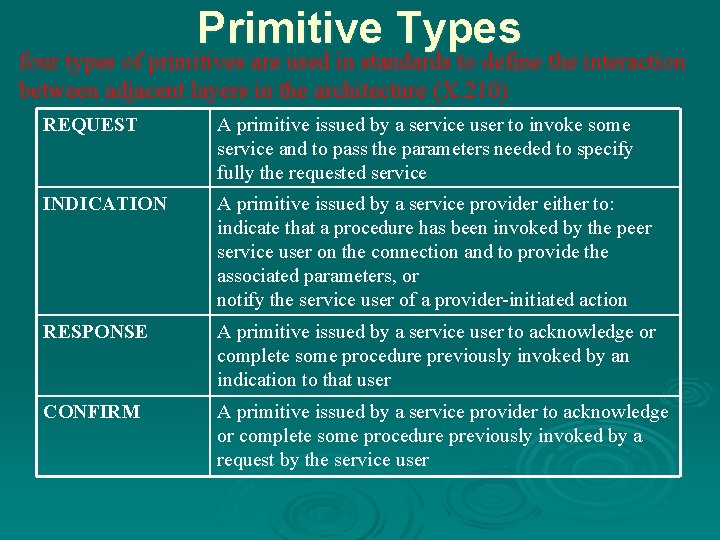
Primitive Types four types of primitives are used in standards to define the interaction between adjacent layers in the architecture (X. 210) REQUEST A primitive issued by a service user to invoke some service and to pass the parameters needed to specify fully the requested service INDICATION A primitive issued by a service provider either to: indicate that a procedure has been invoked by the peer service user on the connection and to provide the associated parameters, or notify the service user of a provider-initiated action RESPONSE A primitive issued by a service user to acknowledge or complete some procedure previously invoked by an indication to that user CONFIRM A primitive issued by a service provider to acknowledge or complete some procedure previously invoked by a request by the service user

Traditional vs Multimedia Applications Ø traditionally Internet dominated by info retrieval applications l l typically using text and image transfer eg. email, file transfer, web Ø see increasing growth in multimedia applications l l involving massive amounts of data such as streaming audio and video

Elastic and Inelastic Traffic Ø Traffic on a network or internet can be divided into two broad categories: elastic and inelastic. Ø elastic traffic l l can adjust to delay & throughput changes over a wide range eg. traditional “data” style TCP/IP traffic. common Internet-based applications, such as file transfer, electronic mail, remote logon, network management, and Web access some applications more sensitive though

Elastic and Inelastic Traffic Ø inelastic traffic l does not adapt to such changes l eg. “real-time” voice & video traffic l The requirements for inelastic traffic may include the following: • minimum throughput. • may be delay-sensitive • may require a reasonable upper bound on delay variation, may vary in the amount of packet loss l These requirements are difficult to meet in an environment with variable queuing delays and congestion losses.

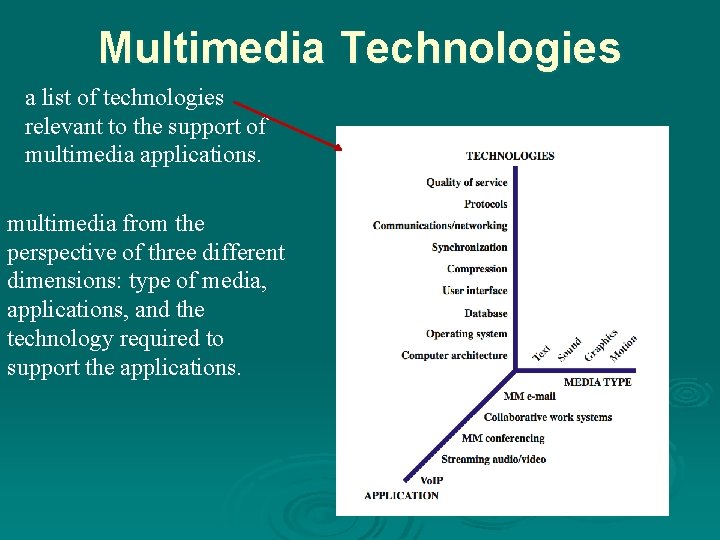
Multimedia Technologies a list of technologies relevant to the support of multimedia applications. multimedia from the perspective of three different dimensions: type of media, applications, and the technology required to support the applications.

Summary Ø introduced need for protocol architecture Ø TCP/IP protocol architecture Ø OSI Model & protocol architecture standardization Ø traditional vs multimedia application needs