DAT 356 Hackers Paradise SQL Injection Attacks Doug









![MachineASPNET -- Windows 2000 / XP EXEC sp_grantlogin [Machine. NameASPNET] EXEC sp_grantdbaccess [Machine. NameASPNET], MachineASPNET -- Windows 2000 / XP EXEC sp_grantlogin [Machine. NameASPNET] EXEC sp_grantdbaccess [Machine. NameASPNET],](https://slidetodoc.com/presentation_image_h2/66e6489c3989cd8eadcd690df72bac19/image-12.jpg)









- Slides: 26

DAT 356 Hackers Paradise SQL Injection Attacks Doug Seven, Microsoft MVP Cofounder of Sql. Junkies. com dseven@dotnetjunkies. com

Session Agenda Introduction to SQL Injection How Do Attackers Do it? Advanced Attacks Solutions Least-privilege Access Parameterize DML Validating Input

What is a SQL Injection? SQL statement(s) “injected” into an existing SQL command Injection occurs through malformed application input: Text box. Query string. Manipulated values in HTML. A good SQL injection attack can cripple and even destroy your database!

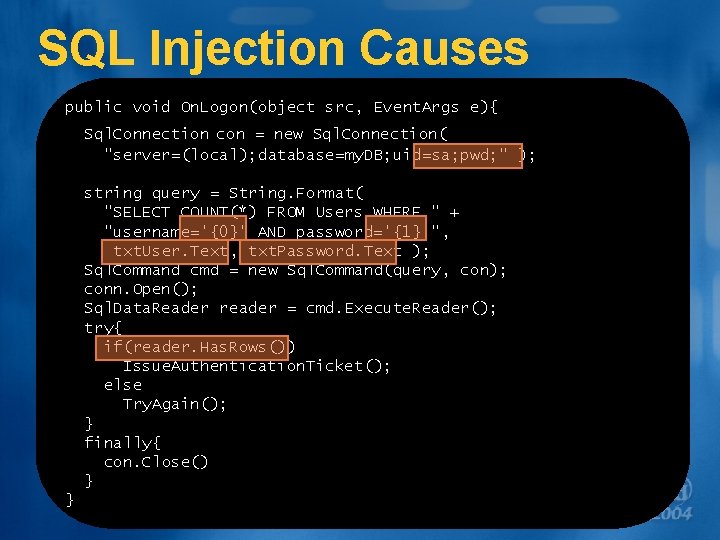
SQL Injection Causes public void On. Logon(object src, Event. Args e){ Sql. Connection con = new Sql. Connection( "server=(local); database=my. DB; uid=sa; pwd; " ); string query = String. Format( "SELECT COUNT(*) FROM Users WHERE " + "username='{0}' AND password='{1}'", txt. User. Text, txt. Password. Text ); Sql. Command cmd = new Sql. Command(query, con); conn. Open(); Sql. Data. Reader reader = cmd. Execute. Reader(); try{ if(reader. Has. Rows()) Issue. Authentication. Ticket(); else Try. Again(); } finally{ con. Close() } }

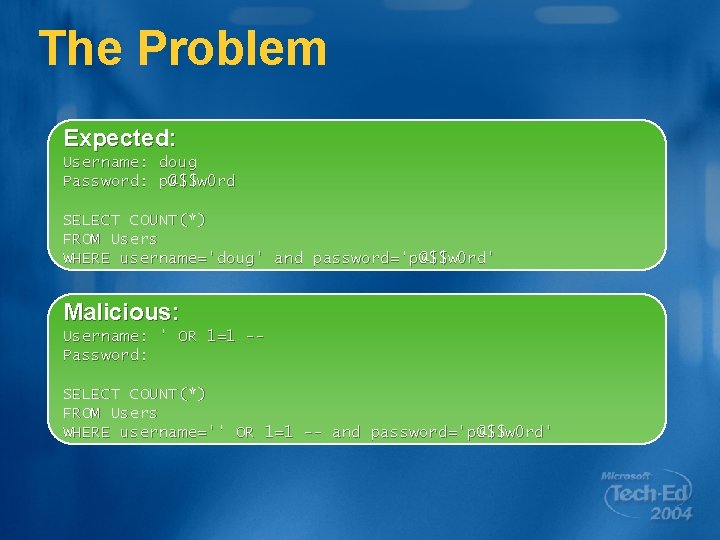
The Problem Expected: Username: doug Password: p@$$w 0 rd SELECT COUNT(*) FROM Users WHERE username='doug' and password='p@$$w 0 rd' Malicious: Username: ' OR 1=1 -Password: SELECT COUNT(*) FROM Users WHERE username='' OR 1=1 -- and password='p@$$w 0 rd'

Basic SQL Injection

How Do Attackers Know? Insider Information Trial and Error message often reveal too much Malicious user can force an error to discover information about the database

It Gets Worse Once a malicious user can access the database, they are likely to use: xp_cmdshell xp_grantlogin xp_regread With the right privileges the user can access ALL databases on the server

Extended Stored Procedures

Problem: Access Privileges Application is accessing database with: “sa” account ASP. NET worker process account (added as admin) High-privilege user account

Solution: Limit Privileges Application should have least necessary privileges to access database Grant ASP. NET account access to database using an alias Create an account that has minimal privileges (EXEC-only)
![MachineASPNET Windows 2000 XP EXEC spgrantlogin Machine NameASPNET EXEC spgrantdbaccess Machine NameASPNET MachineASPNET -- Windows 2000 / XP EXEC sp_grantlogin [Machine. NameASPNET] EXEC sp_grantdbaccess [Machine. NameASPNET],](https://slidetodoc.com/presentation_image_h2/66e6489c3989cd8eadcd690df72bac19/image-12.jpg)
MachineASPNET -- Windows 2000 / XP EXEC sp_grantlogin [Machine. NameASPNET] EXEC sp_grantdbaccess [Machine. NameASPNET], [Alias] GRANT EXECUTE ON [Procedure. Name] TO [Alias] GO -- Windows Server 2003 EXEC sp_grantlogin [NT AUTHORITYNETWORK SERVICE] EXEC sp_grantdbaccess [NT AUTHORITYNETWORK SERVICE] GRANT EXECUTE ON [Procedure. Name] TO [NT AUTHORITYNETWORK SERVICE] GO

Least Privilege

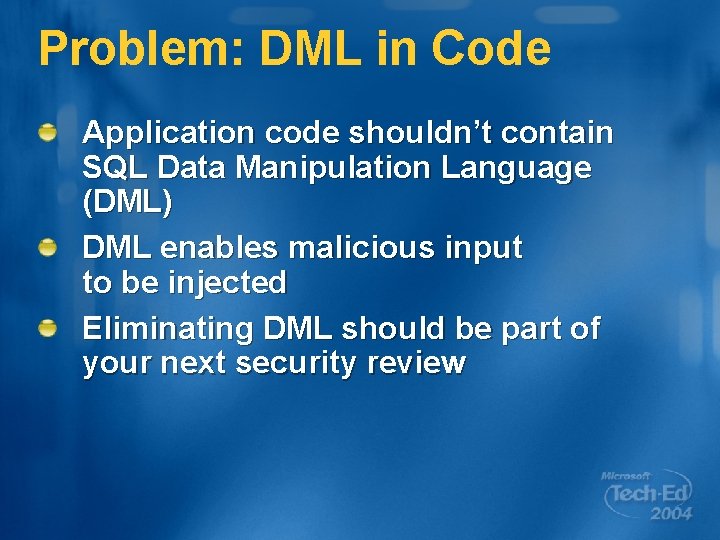
Problem: DML in Code Application code shouldn’t contain SQL Data Manipulation Language (DML) DML enables malicious input to be injected Eliminating DML should be part of your next security review

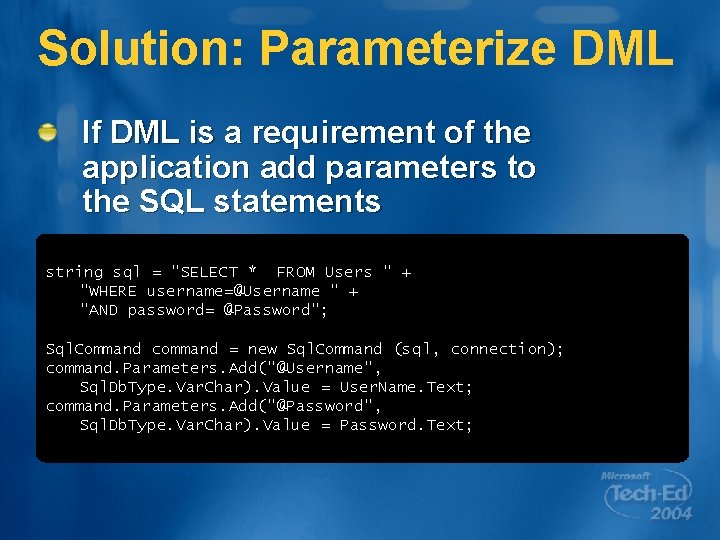
Solution: Parameterize DML If DML is a requirement of the application add parameters to the SQL statements string sql = "SELECT * FROM Users " + "WHERE username=@Username " + "AND password= @Password"; Sql. Command command = new Sql. Command (sql, connection); command. Parameters. Add("@Username", Sql. Db. Type. Var. Char). Value = User. Name. Text; command. Parameters. Add("@Password", Sql. Db. Type. Var. Char). Value = Password. Text;

Solution: Stored Procedures Less vulnerable to SQL injection attacks Added security via EXECUTE permission Sql. Command command = new Sql. Command ("Users_Get. User", connection); command. Command. Type = Command. Type. Stored. Procedure; Sql. Command command = new Sql. Command (sql, connection); command. Parameters. Add("@Username", Sql. Db. Type. Var. Char). Value = User. Name. Text; command. Parameters. Add("@Password", Sql. Db. Type. Var. Char). Value = Password. Text;

Stored Procedures

Problem: User Input All user input is inherently evil Malicious input can: Inject SQL statements Execute arbitrary SQL Damage limited only by privilege of data account Alter application flow Attack other users (cross-site scripting) Read/write cookies Execute script, etc.

Solution: Input Validation All user input should be cleansed ASP. NET validation controls Reg. Ex class Reject invalid input Encode any input that is echoed to the browser Http. Ulitity. Html. Encode() Always use parameterized SQL queries Parameterized commands (good) Parameterized stored procedures (better)

ASP. NET Request Validation Validates query string, form data, cookies Developers still have responsibility to secure inputs Can be disabled at page-, application-, or machine-level

Input and Request Validation

Sql. Junkies. com Online resource for DEVELOPERS using SQL Server Dot. Net. Junkies. com Online resource for developers working with the. NET Framework Web Application Disassembly with ODBC Error Messages by David Litchfield http: //www. nextgenss. com/papers/webappdis. doc

Writing Secure Code (Second Edition) Michael Howard & David Le. Blanc Microsoft Press, December 2002 Required reading at Microsoft!

Improving Web Application Security http: //msdn. microsoft. com/security/default. aspx? pull= /library/en-us/dnnetsec/html/threatcounter. asp Building Secure ASP. NET Applications http: //msdn. microsoft. com/security/default. aspx? pull= /library/en-us/dnnetsec/html/secnetlpmsdn. asp

Please fill out a session evaluation on Comm. Net Q 1: Overall satisfaction with the session Q 2: Usefulness of the information Q 3: Presenter’s knowledge of the subject Q 4: Presenter’s presentation skills Q 5: Effectiveness of the presentation

© 2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.