DAIR Dense Array of Inexpensive Radios Managing Enterprise












- Slides: 23

DAIR: Dense Array of Inexpensive Radios Managing Enterprise Wireless Networks Using Desktop Infrastructure Victor Bahl†, Jitendra Padhye†, Lenin Ravnindranath†, Manpreet Singh‡, Alec Wolman†, Brian Zill† † Microsoft Research ‡ Cornell University 1

Observations • Outfitting a desktop PC with 802. 11 wireless is becoming very inexpensive – Wireless USB dongles are cheap $6. 99! – PC motherboards are starting to appear with 802. 11 radios built-in • Desktop PC’s with good wired connectivity are ubiquitous in enterprises 2

Key Insight • Combine to provide a dense deployment of wireless “sensors” • We can use this platform to realize the full potential of wireless networks – Enterprise wireless management tools – Enable new services where wireless is a key component 3

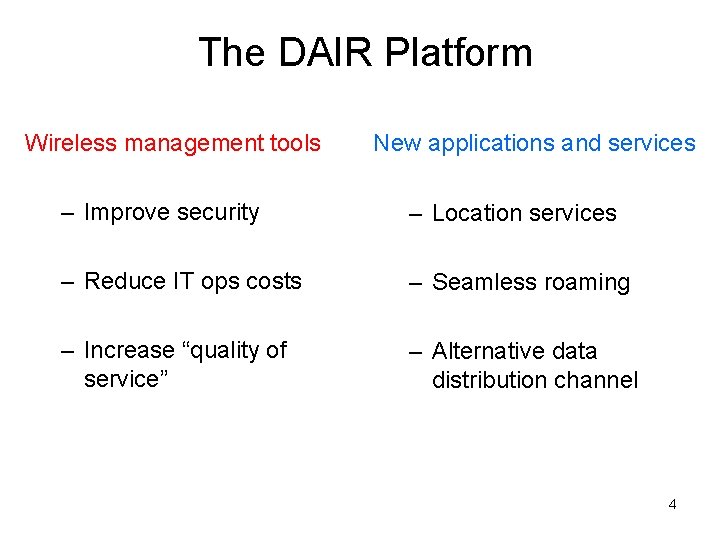
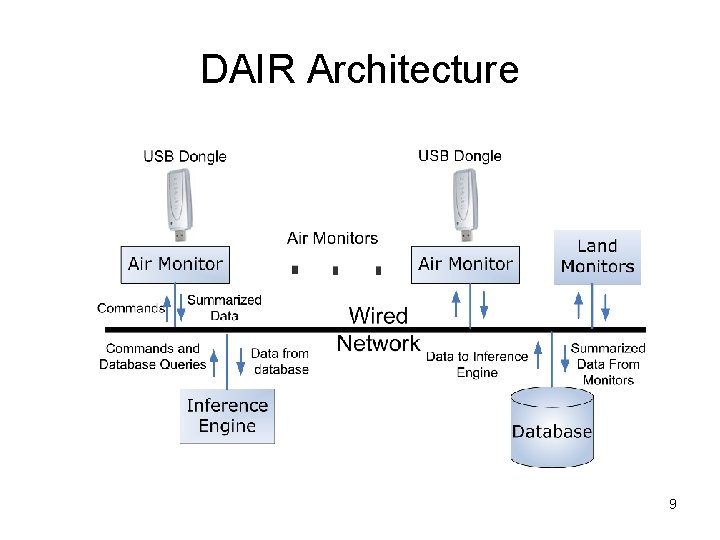
The DAIR Platform Wireless management tools New applications and services – Improve security – Location services – Reduce IT ops costs – Seamless roaming – Increase “quality of service” – Alternative data distribution channel 4

Outline • • Motivation DAIR architecture Management apps (& Rogue networks) Related work 5

Enterprise WLAN Management • Corporations spend a lot on WLAN infrastructure – Worldwide enterprise WLAN business expected to grow from $1. 1 billion this year to $3. 5 billion in 2009 – MS IT dept. – 72% of costs are people • Security and reliability are major concerns – Wireless networks are becoming a target for hackers – Reliability: • MS IT receives ~500 WLAN helpdesk requests per month • No easy way to measure cost of reliability problems 6

Advantages of the DAIR Approach – High density • Wireless propagation is highly variable in enterprise environments (many obstructions) • Lots of channels to cover: 11 for 802. 11 b/g, 13 for 802. 11 a • Improves fidelity of many management tasks • Enables accurate location (useful as a diagnosis tool) – Stationary sensing • Provides predictable coverage • Also helps enable location services • Allows meaningful historical analysis – Desktop resources • Spare CPU, disk, and memory • Good connectivity to wired network • Wall power 7

Outline • • Motivation DAIR architecture Management apps (& Rogue networks) Related work 8

DAIR Architecture 9

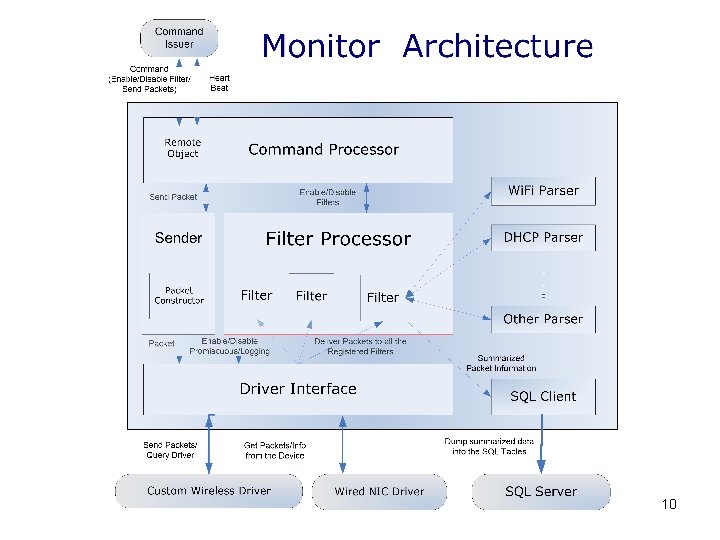
10

Outline • • Motivation DAIR architecture Management apps (& Rogue networks) Related work 11

Wireless Management Apps Performance and Reliability • Performance monitoring – Site planning: AP placement, frequency selection – AP Load balancing – Isolating performance problems • Helping disconnected clients – RF Holes – Misconfiguration, certificates, etc… • Reliability – Recovery from malfunctioning APs – Recovery from poor association policies 12

Wireless Management: Security Apps • Detecting Do. S attacks: – Spoofing Disassociation – Large NAV values – Jamming • Detecting Rogue Wireless Networks 13

Rogue Wireless Networks • Detecting rogue APs and rogue ad-hoc networks • An uninformed or careless employee who doesn’t understand (or chooses not to think about) the security implications – An employee brings in an AP from home, and attaches it to the corporate network, creating a rogue AP – It is trivial to configure a desktop PC with a wireless interface to create a rogue ad-hoc network 14

Risks • Attaching unauthorized AP to a corporate network – May allow unauthorized wireless clients to gain access • A wireless client unknowingly connects to unauthorized AP on unauthorized network – May expose corporate information on that network • Once rogue network is installed, physical proximity is no longer needed (esp. with directional antennas)… 15

A Simple Solution? • Build a database of known: – SSIDs (network names) – BSSIDs (access point MAC addresses) • Use DAIR infrastructure to scan – Whenever an unknown entity appears (either SSID or BSSID), raise an alarm • This is the level at which most previous work solves this problem 16

False Alarms • In many enterprise environments, one can hear other legitimate APs – E. g. shared office buildings • Is the unknown wireless network connected to your corporate wired network? 17

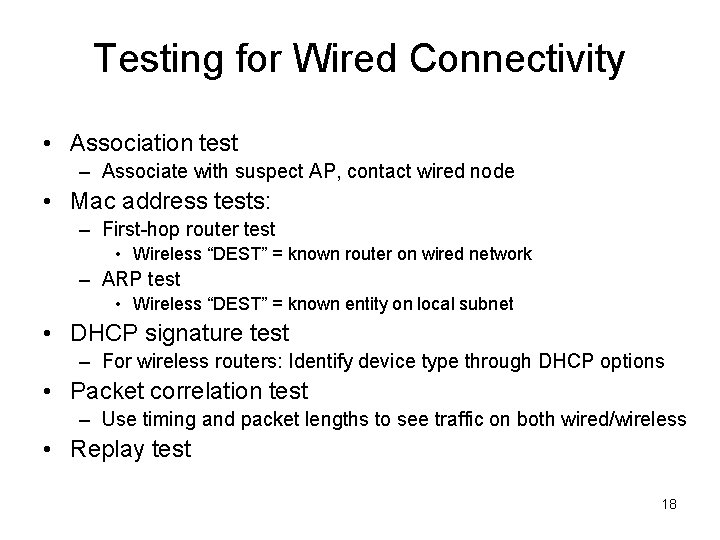
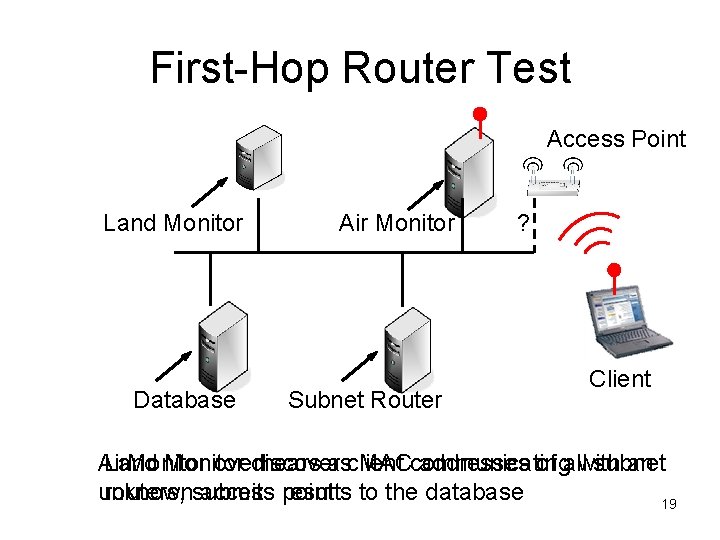
Testing for Wired Connectivity • Association test – Associate with suspect AP, contact wired node • Mac address tests: – First-hop router test • Wireless “DEST” = known router on wired network – ARP test • Wireless “DEST” = known entity on local subnet • DHCP signature test – For wireless routers: Identify device type through DHCP options • Packet correlation test – Use timing and packet lengths to see traffic on both wired/wireless • Replay test 18

First-Hop Router Test Access Point Land Monitor Database Air Monitor Subnet Router ? Client Air. Monitor Land Monitor overhears discovers a client MACcommunicating addresses of allwith subnet an unknown routers, submits access results point to the database 19

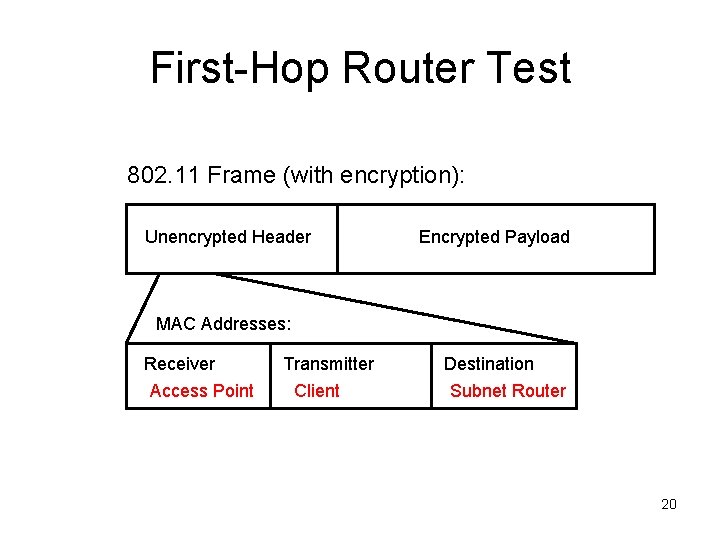
First-Hop Router Test 802. 11 Frame (with encryption): Unencrypted Header Encrypted Payload MAC Addresses: Receiver Access Point Transmitter Client Destination Subnet Router 20

Outline • • Motivation DAIR architecture Management apps (& Rogue networks) Related work 21

Current Approaches & Related Research • Many commercial offerings in this space • Leverage existing access points (APs) – Air. Wave, Manage. Engine, … – AP’s primary goal is to provide service to clients, limited time listening on other channels • Specialized sensors – Aruba (MS IT choice), Air. Defense, Air. Tight … – Expensive limited density • [Adya et al. Mobicom 04] – use assistance of mobile clients – Difficult to provide predictable coverage – Less proactive due to energy constraints • Other wireless monitoring 22

Wrapping Up… – Status • Built much of the “plumbing”: Air. Monitors, Inferencing Service, Management Console (GUI) • Built set of wireless security apps, ongoing evaluation • Deployed ~22 Air. Monitors on one floor of our building – Next 6 months: • Performance & reliability apps • Provide location services • Larger scale deployment – Longer Term: going beyond management tools • Seamless roaming • Self-configuring complete replacement for existing wireless infrastructure 23