CYBERSECURITY Simple things we should be doing Aldo

CYBERSECURITY Simple things we should be doing Aldo Mayo


$445 billion GLOBAL COST OF CYBER-ATTACKS

CYBER ATTACKS 2014 “cybercrime is a growth industry. ”

Passwords • 8 -12 characters minimum • Complex combination of uppercase and lowercase letters, numbers and special characters • Use a passphrase to develop complex passwords, for example…I love Aruba can be changed to !l 0 v 3@r. Ub. A • Should be changed often, at a minimum every 90 days

www. passfault. com

Common sense points • Don’t share your password with anyone • Clean desk Policy (https: //www. sans. org/securityresources/policies/general/pdf/clean-desk-policy • Dictionary, Brute Force Attacks • Shoulder Surfing • Windows key + L key locks your PC, Automate via screensaver lock

Vulnerabilities • Keep all IT assets up to date • 90% of all vulnerabilities can be easily avoided by making sure your operating systems and common third party apps are kept up to date, with the latest security patches. • Vulnerability Scanning and Assessment • Allow you to see where your biggest risks are and begin to remediate those risks
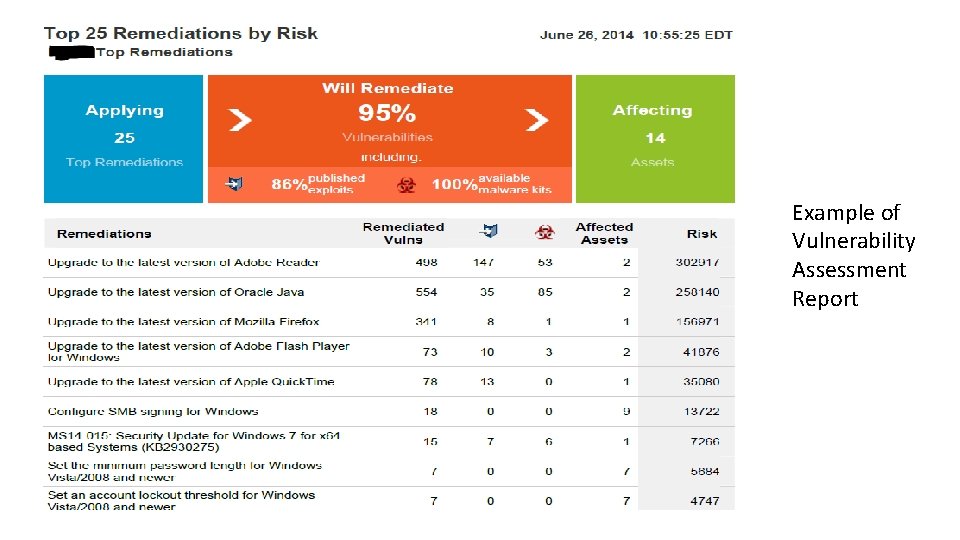
Example of Vulnerability Assessment Report

Documentation • Clear Network Documentation • Inventory of all the hardware and software on your network • SEC stresses these points at the beginning of their guideline • The better documentation you have the easier is it to recover from a breach or a disaster scenario.

Example of documentation

Backup, Disaster Recovery and Business Continuity • Make sure you back up the important data in at least 2 places (Onsite as well as offsite in the event of a real disaster situation • This can range anywhere from backing up to two USB drives, again onsite and offsite all the way to having the ability to virtualize your critical business servers onsite or in the cloud.
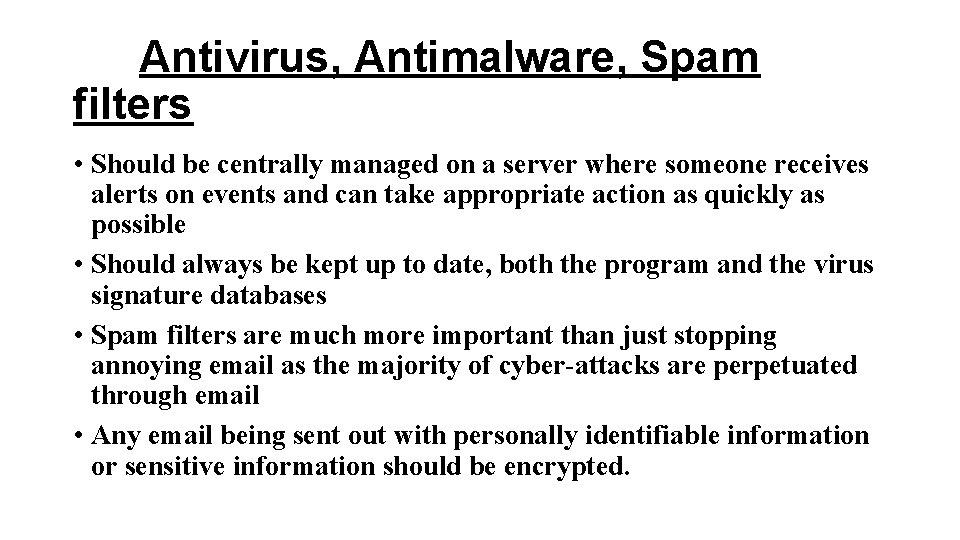
Antivirus, Antimalware, Spam filters • Should be centrally managed on a server where someone receives alerts on events and can take appropriate action as quickly as possible • Should always be kept up to date, both the program and the virus signature databases • Spam filters are much more important than just stopping annoying email as the majority of cyber-attacks are perpetuated through email • Any email being sent out with personally identifiable information or sensitive information should be encrypted.

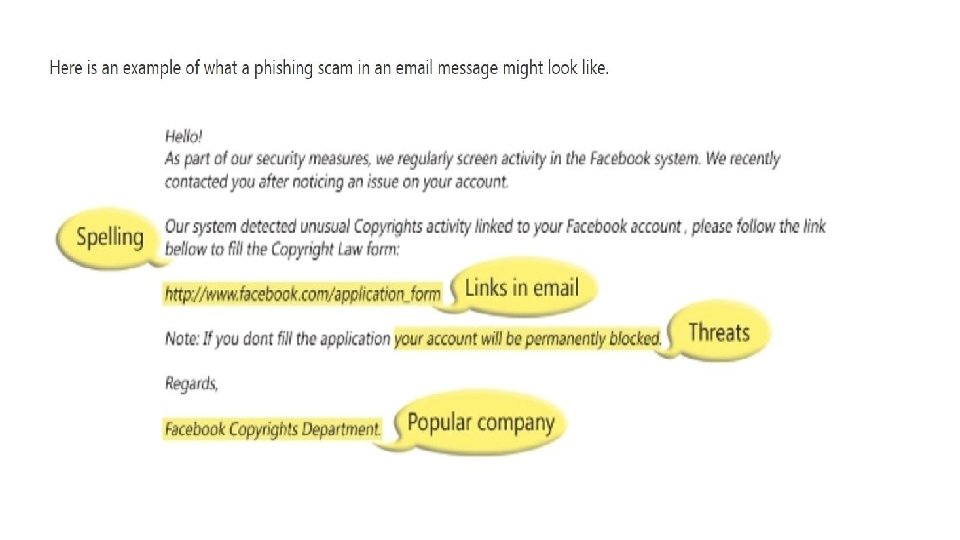
• Phishing-an email sent by a cyber-criminal pretending to be a well-known organization. The email is very professional looking, including the firm’s logo.
Test your Phishing IQ www. sonicwall. com/furl/phishing/index. php

• Spear phishing- highly customized attack where only a few emails are sent to specific individuals within your organization. These emails appear very realistic, often with a subject that is relevant to the victim’s job or appear to come from individuals that the victim highly trusts. Again a lot of information can be gathered from social media sites for this purpose.
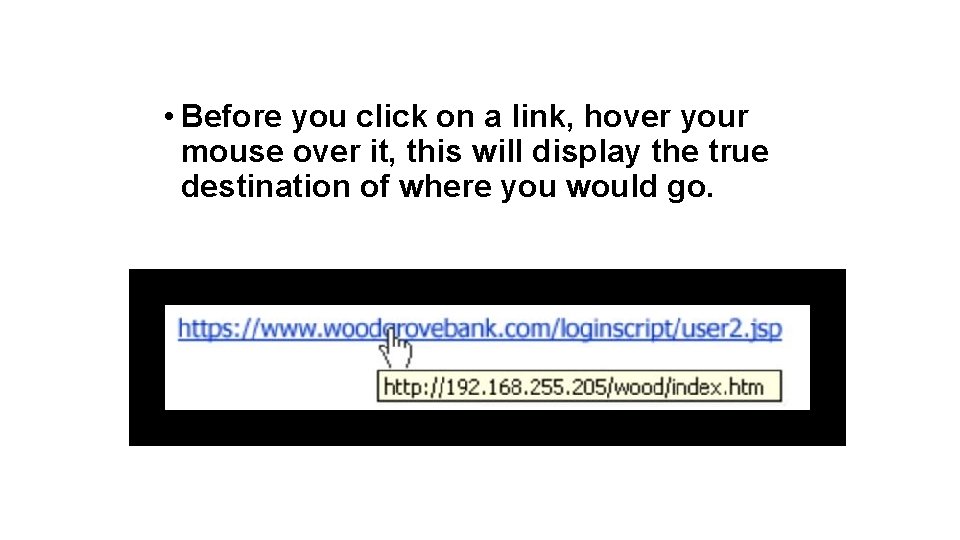
• Before you click on a link, hover your mouse over it, this will display the true destination of where you would go.

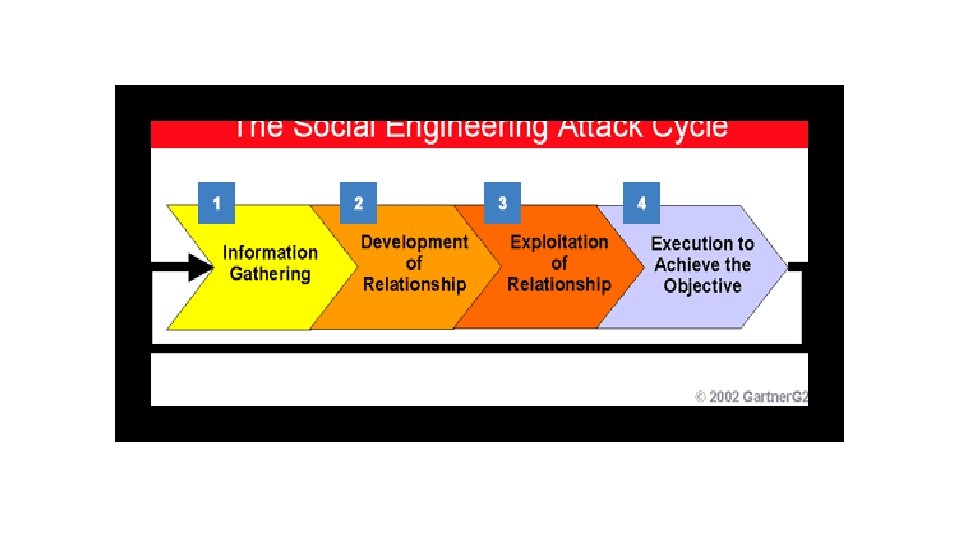

Social Engineering • Predictable human behavior • Dumpster diving • Candy drop -USB sticks with malicious code • Information gathering from Social media sites like Linked. In, Facebook, Twitter etc. Pay attention to your privacy controls on each respective website • Security Awareness training for your staff

Wireless Networks • Pervasive throughout • Should always be encrypted with a minimum of WPA 2, older routers used WEP which has been cracked and is no longer a secure protocol. DO NOT USE WEP.

Firewalls • Should be configured to only open the ports necessary for business requirements • Content filter (such as pornography or known malicious websites) • Intrusion detection and prevention

Security away from the office • Laptop security • Mobile devices (phones, tablets etc. ) • Should always be password protected and encrypted • Remote wipe capability is widely available • Take extra care when using public computers as there may be malicious software waiting to capture confidential information. Things like key loggers

Additional Reference 1. 2. 3. 4. 5. 6. 7. 8. 9. http: //phys. org/news/2014 -06 -cybercrime-deep-global-economy. html%20 -%20 j. Cp/ http: //www. welivesecurity. com/2014/08/06/cybervor-hacking-gang/ http: //www. latimes. com/business/la-fi-pf-changs-breach-33 -restaurants-20140804 -story. html http: //time. com/3086359/target-data-breach-loss/ http: //www. sec. gov/ocie/announcement/Cybersecurity+Risk+Alert++%2526+Appendix+-+4. 15. 14. pdf http: //online. wsj. com/news/articles/SB 10001424052702303409004579565703558096872 http: //www. fcc. gov/cyberplanner https: //apps. fcc. gov/edocs_public/attachmatch/DOC-306595 A 1. pdf http: //isalliance. org/publications/1 A. %20 The%20 Financial%20 Impact%20 of%20 Cyber%20 Risk%2050%20 Questions%20 Every%20 CFO%20 Should%20 Ask%20 -%20 ISA-ANSI%202008. pdf 10. http: //www. searchenginegenie. com/101 -articles/phishing. html 11. http: //www. thinkadvisor. com/2014/03/14/5 -linkedin-privacy-tips-every-financial-advisor-sh 12. http: //www. mcafee. com/us/resources/reports/rp-economic-impact-cybercrime 2. pdf 13. http: //www. sans. org/security-resources/policies/general/pdf/password-protection-policy

For additional information contact us at 561 -989 -4653. We offer a full suite of IT managed services. Check out our facebook page at https: //www. facebook. com/infinitytechnologypartners Our website address http: //www. infinitytechnologypartners. com/
- Slides: 26