Cybersecurity Services and Integration Division Code 710 Sergio

Cybersecurity Services and Integration Division – Code 710 Sergio Mc. Kenzie Chief Information Security Officer Goddard Space Flight Center 25 May, 2017 Cybersecurity Services and Integration Division 1

Agenda • • Cybersecurity History Cybersecurity Vision Division Set-Up What is New in 2017 IT Security Management Plans Resources/Escalations Questions Cybersecurity Services and Integration Division 2
Purpose • What this is not – – Security Brief – Statistical Road Map – Challenges Discussion • What it is – Cybersecurity Services and Integration Division 3

History • Day 0 – September 21, 2015 • Official re-org – May 1, 2016 • Official Name – Cybersecurity Services and Integration Division (CSID); Code 710 • New operating paradigm – from compliance to service • Location – Basement of building 8 • Mission – The Cybersecurity Services and Integration Division (CSID) is responsible for ensuring the confidentiality, integrity, and availability of Goddard’s critical data and IT assets. In accordance with Federal regulations and Agency IT policies and standards, CSID applies the technologies, policies, security concepts, security controls, training, processes and best practices necessary to protect Goddard’s networks, data and information systems from cyber threats and vulnerabilities. Code 710 4

Cybersecurity Services and Integration Division Vision: The Cybersecurity Services and Integration Division (CSID) aims to become a solution oriented, customer focused organization, offering cyber services that protect, enhance, and advance GSFC directives into the 21 st century and beyond. Major Goals: 1. Improve Cybersecurity 2. Transition from compliance to service delivery Cybersecurity Services and Integration Division 5

What Was New in FY 16 & FY 17 • Consolidation and Re-organization • Initiation of Information System Security Engineering capabilities • Implementation of customer facing Service Management Team & associated processes (e. g. ITSMP, CFRB, IT on Travel, etc. ) • In December 2016, NASA Administrator published a memorandum enforcing NASA-wide compliance with the Fed-wide Continuous Diagnostic and Mitigation (CDM) and Personal Identity Verification mandatory (PIV-M) deployment programs. The memo cited specific compliance dates which is a new approach to NASA. • Implementation of Threat Management Program with targeted alerts to the Center • Started a new agency-wide service in support of enterprise security requirements – IT Security Change Management Service Code 710 6
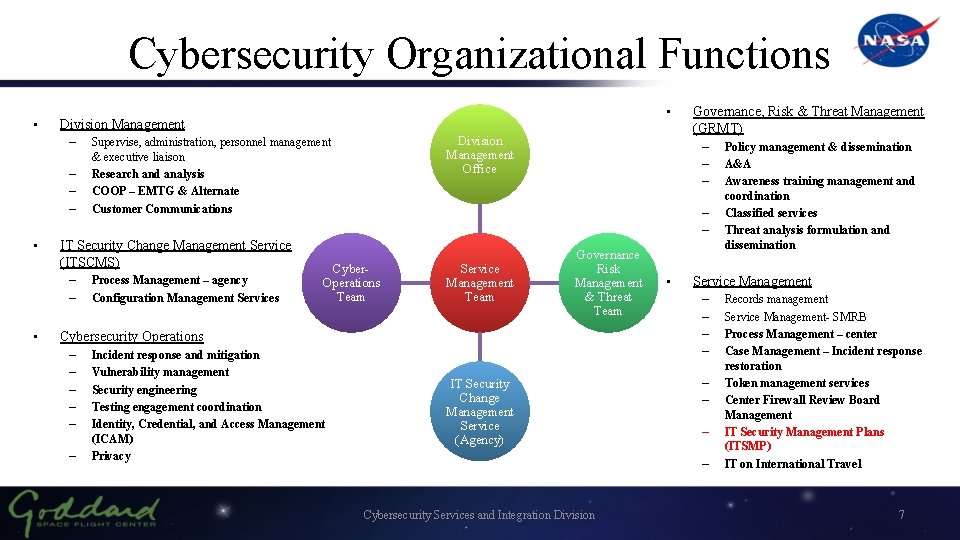
Cybersecurity Organizational Functions • – – • Division Management Office Supervise, administration, personnel management & executive liaison Research and analysis COOP – EMTG & Alternate Customer Communications IT Security Change Management Service (ITSCMS) – – • • Division Management Process Management – agency Configuration Management Services – – – Cyber. Operations Team Service Management Team Governance Risk Management & Threat Team Cybersecurity Operations – – – Incident response and mitigation Vulnerability management Security engineering Testing engagement coordination Identity, Credential, and Access Management (ICAM) Privacy Governance, Risk & Threat Management (GRMT) IT Security Change Management Service (Agency) • Service Management – – – – Cybersecurity Services and Integration Division Policy management & dissemination A&A Awareness training management and coordination Classified services Threat analysis formulation and dissemination Records management Service Management- SMRB Process Management – center Case Management – Incident response restoration Token management services Center Firewall Review Board Management IT Security Management Plans (ITSMP) IT on International Travel 7

IT Security Management Plan: Overview Cybersecurity Services and Integration Division 8

Code 710: IT Security Management Plan • Required Code 710 deliverable for any new contract Code 710 ITSMP fillable pdf template. – Sensitive But Unclassified: Always send encrypted to GSFC-IT-Security-Review@mail. nasa. gov – ITSMP is the formal plan that defines the plan of action to secure a computer or information system. Typically lists authorized personnel/users that can access the system, level of access, access control methods, system back up, how data is handled, etc. – Federal Information Security Management Act (FISMA) of 2002 driver Cybersecurity Services and Integration Division 9

Code 710: IT Security Management Plan • What is NIST? – National Institute of Standards and Technology under Dept. of Commerce established to promote and maintain measurement standards as it relates to a variety of fields. • Energy & Environment, Forensic Science, Health & Bioscience, Cybersecurity • NIST 800 -60 Publication: Provides guidelines for mapping types of information and information system to security categories. New tool Cybersecurity Services and Integration Division 10

Requirements For Approval • Prior to Code 710 approval the following must be completed. – Signatures (either hand signed or digitally signed) from: 1. Information System Security Officer (ISSO), or equivalent AND 2. Concurrence by Contracting Officer Representative (COR) SLA: 30 days from receiving a completed and signed ITSMP Cybersecurity Services and Integration Division 11

Escalations • Inquiries, suggestions, recommendations, or concerns: GSFC-IT-Security-Review@mail. nasa. gov • If you are having an issue with cyberservices, please reach out: – CISO/Division Chief: Sergio Mc. Kenzie • Email: Sergio. mckenzie@nasa. gov • Phone: 301. 286. 0877 – DCISO/Associate Chief: Roopalee Nesson • Email: Roopalee. d. nesson@nasa. gov • Phone: 301. 286. 0033 – Cybersecurity Service Manager: Tammy Tuttle • Email: Tammy. e. Tuttle@nasa. gov • Phone: 301. 286. 4883 Cybersecurity Services and Integration Division 12

Resources • All customer facing services that the Cybersecurity Division offers can be found here: Cybersecurity Services • The IT on Travel documents and process can be found here: IT On Travel Cybersecurity Services and Integration Division 13

What Do We Need From You? • Participation – It takes the voice of many to understand impacts and develop workable solutions • Patience – It takes 1 second to say “no” but time to develop solutions • Perseverance – We will keep at it, need you to just hang with us • Acceptance – At some point we will exhaust all alternatives. I promise you an honest effort! • Transparency – Please help! Security by obscurity doesn’t work. Cybersecurity Services and Integration Division 14

QUESTIONS Cybersecurity Services and Integration Division 15

BACKUP SLIDES Cybersecurity Services and Integration Division 16

Accomplishments 2017 (1 of 2) • • • Performed Security Control Assessments on 22 GSFC security boundaries Per NASA requirement, increased the scope of the FY 2017 Cybersecurity Awareness training to include all NASA badged employees. Trained the largest pool of GSFC users in over 5 years. Conducted classroom training for over 300 GSFC local and remote users. Integrated capability to host and participate in classified meetings and built a threat management program for distributing actionable intelligence. Completed the 4 -Cert-on-card roll-out Piloted an Information System Security Engineering capability expanding our engagement with an array of programs/projects. – Restore-L, Landsat-9, Space Test Program Satellite (STPSat)-6, Laser Communications Relay Demonstration (LCRD), Total and Spectral solar Irradiance Sensor (TSIS-1), GLOBE (Global Learning and Observations to Benefit the Environment) Data and Information System (DIS), and building close relationships with OCIO, DHS, IV&V BT-VAP, Space Asset Protection Program (SAPP), The Laboratory for Atmospheric and Space Physics (LASP), The Aerospace Corporation, GSFC Radio Frequency Spectrum Management Office, and other critical counter-intelligence services • Built formal and structured cybersecurity processes to support IT on International Travel, remote access Token distribution, DAR waivers, IT Security Management Plan reviews for new contracts, tracking of Center-wide Plan of Action and Milestones, firewall opening reviews/approval/execution/verification, and other critical service delivery functions Code 710 17

Accomplishments 2017 (2 of 2) • Expanded our communication capabilities by creating a Share. Point portal and blog to facilitate information exchange with our customers • Successfully sponsored the Cyber Security Awareness Day and Expo, represented by over 60 vendors and over 200 Center participants • Achieved 75% compliance with the Personal Identity Verification (PIV) mandate of machine based enforcement for workstations and servers • Achieved 95% compliance with the Continuous Diagnostic and Mitigation (CDM) program for all Corporate systems and environment. • Reached 100% compliance for all GSFC externally facing websites with the government mandate for HTTPS which secured our external connections. With the largest pool of websites in the agency (1150+) and close to the top in the Federal Government, this was a great accomplishment. • Supported the agency and built the agency-wide IT Security Change Management Service which included principles, structures, and processes Code 710 18

Goals in FY 18 • Continue to expand the Information System Security Engineering capability with capacity to integrate into the system development lifecycle for new and ongoing mission programs and projects managed by the Center. Also, establish clearly defined processes for adapting new systems into the NASA computing environment • Develop a Cybersecurity Professional training program focusing on helping security professionals, network/system managers/administrators, and system owners to achieve and maintain skills in cybersecurity. • Implement innovative cybersecurity systems and networks to meet identified gaps in the Center’s cybersecurity environment – especially establishing secure environments for our more sensitive applications • Complete deployment of agency tools and establish processes associated with information security risk management programs, concept of operations associated with enterprise border protections, network access controls, and incident management systems • Expand improve outreach and communication activities • Expand, mature, and modernize vulnerability management and incident response capabilities to better identify and manage risks to the computing environment Code 710 19

Current High Priority Activities • Agency or Above Driven – – – • Center or Below Driven CDM (Phase 1 – 3) PIV-M (user and machine) HTTPS Mandate ITSCMP EIB-NAC & EBPro Business Process Implementation – Threat Services – IT on International Travel – Restore-L, SAGE, IBEX – – – – A&A Modernization CFRB Modernization Awareness Training Enhancement Center Privacy Program Modernization Development of Risk Registry Incident Response Process Review Vulnerability Management Process Review – Improved Communication Strategy – Secure Enclave – Cloud Security Service Provisioning Cybersecurity Services and Integration Division 20
- Slides: 20