Cybersecurity in the Maritime Domain Maritime Cyber Team

Cybersecurity in the Maritime Domain Maritime Cyber Team Advisor: Dr. Barry Bunin Team Members: Nisil Patel, Grace Miguel, Sebastian Churion, Trey Robertson

This material is based upon work supported by the U. S. Department of Homeland Security under Cooperative Agreement No. 2014 -ST-061 -ML 0001. The views and conclusions contained in this document are those of the authors and should not be interpreted as necessarily representing the official policies, either expressed or implied, of the U. S. Department of Homeland Security.

Research Question and Goals ● What cyber attack vectors have been used to attack the maritime and other critical infrastructures, what can be learned from those attacks, and what can be done to mitigate the consequences of those attacks happening again? ● From our research and the work we created ○ ○ ○ A database containing all the incidents we discovered during our literary search Created a visual display for users to view data gathered Created a risk assessment and mitigation plan for both port facilities and vessels

Process Flow Cyber Attack Catalog Data Visualization Data Analysis/Risk Assessment Risk Priority and Mitigation Plan

Methodology ● Catalogued 67 cyber attacks across all critical infrastructures in Google Sheets. ● Categorized by: ○ Critical Infrastructure- water, power, transportation, etc. ○ Entry Attack- Phishing, Portable Devices, etc. ○ Main Attack- Ransomware, Trojan Horse, etc. ○ Date https: //www. pcmag. com/reviews/tableaudesktop
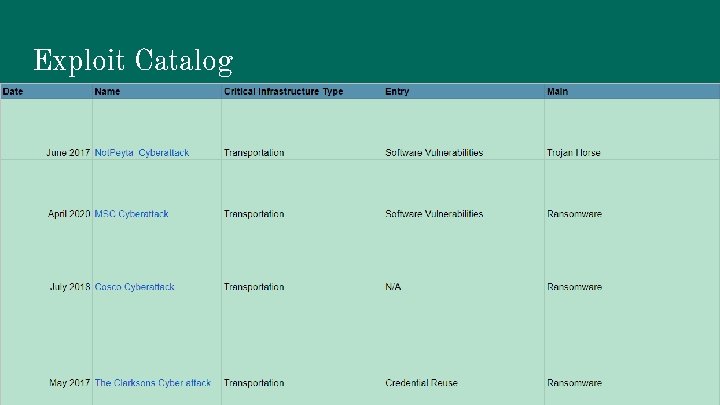
Exploit Catalog
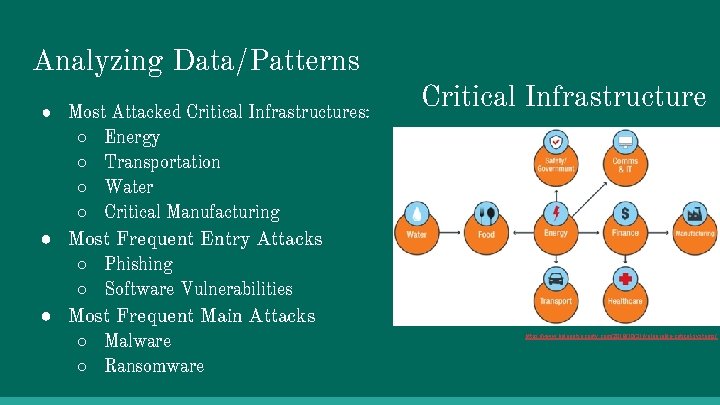
Analyzing Data/Patterns ● Most Attacked Critical Infrastructures: ○ Energy ○ Transportation ○ Water ○ Critical Manufacturing Critical Infrastructure ● Most Frequent Entry Attacks ○ Phishing ○ Software Vulnerabilities ● Most Frequent Main Attacks ○ Malware ○ Ransomware https: //www. helpnetsecurity. com/2018/10/31/vulnerable-critical-systems/
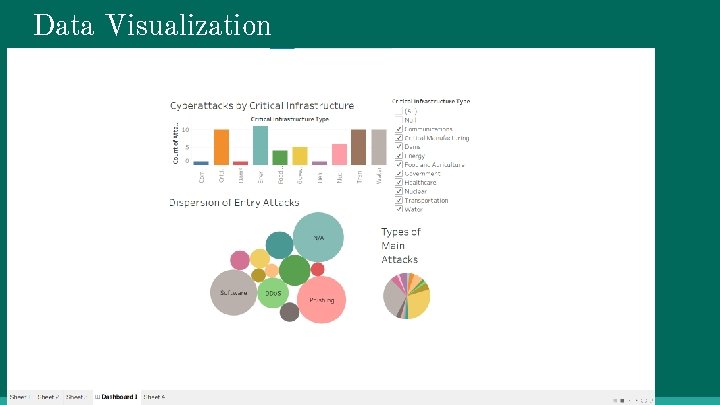
Data Visualization SV

Risk Assessment ● The risk assessment is based of attacks that had already happened. ● As a result, the risk assessment is for known vulnerabilities and not potential new vulnerabilities. ● This is still important as these known vulnerabilities are still exploited to this day. ● The attacks that were cataloged happened across many critical infrastructure types, and the same vulnerabilities can be exploited in the maritime domain.

Risk Assessment ● Created two separate security plans: one for a generic port facility and the other for a generic vessel. (only generic port facility is displayed) ● Vulnerability Scale is based on MARSEC Levels, the Coast Guard’s three-tiered threat security system. ● Consequence Scale self-created. ● Creation of a Vulnerability-Consequence Matrix with each risk identified through our literature review. ● Risk is the sum of the Vulnerability and Consequence

Risk Assessment of Generic Port Facility Threat Vulnerability Consequence Impact Mitigation Risk Score Software Vulnerability 3 4 Hackers gain access & implement malware, ransom ware, DDo. S Update software, test patches 7 Interception of radio/ telecommunica tions 2 2 Loss of communication, Stolen information Authentication access to radio channels 4 Man in the middle attack 2 2 The attacker alters communications between parties Encryption on access points 4 Phishing 3 3 Malware, ransomware Educate workforce on basic cybersecurity 6

Mitigation Plan ● Action Steps ○ Preventing entry attacks will mitigate main attacks. ○ Create and implement an employee cybersecurity education program to mitigate attacks. ○ Have a well-funded and staffed cybersecurity subdivision of the IT department.

Mitigation Plan: Employee Education Program ● Lesson 1: Phishing ○ Email ○ Pop-up ads ○ Personal Information ● Lesson 2: Hidden Vulnerabilities ○ Software updates ○ Password protection ○ Devices
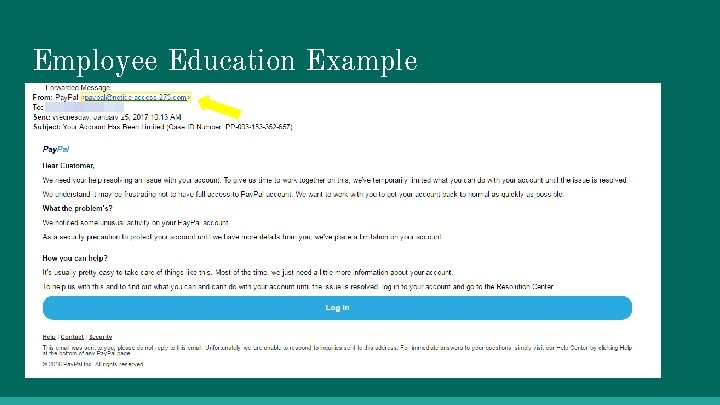
Employee Education Example
Mitigation Plan ● Firewalls ● Network Segmentation ● Encryption

Takeaways ● US critical infrastructures are most heavily targeted with phishing attacks and social engineering. ● An attack is often two-fold, when an entry attack is mitigated, so is the main attack. ● The Maritime domain has vulnerabilities in IT and OT. They are intertwined. ● An employee education plan, well-funded and experienced cybersecurity team will help mitigate these problems and lower the risk.

Questions?
- Slides: 17