Cybersecurity for railways Protecting railway infrastructure Emanuele Di

Cyber-security for railways Protecting railway infrastructure • Emanuele Di Liberto • April 2018 1 © 2017 Nokia
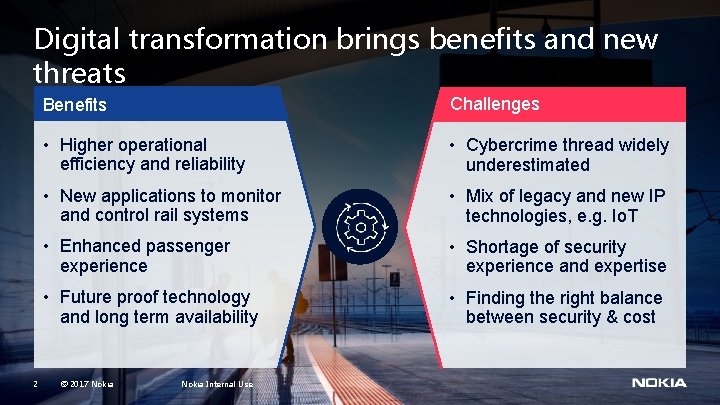
Digital transformation brings benefits and new threats 2 Benefits Challenges • Higher operational efficiency and reliability • Cybercrime thread widely underestimated • New applications to monitor and control rail systems • Mix of legacy and new IP technologies, e. g. Io. T • Enhanced passenger experience • Shortage of security experience and expertise • Future proof technology and long term availability • Finding the right balance between security & cost © 2017 Nokia Internal Use
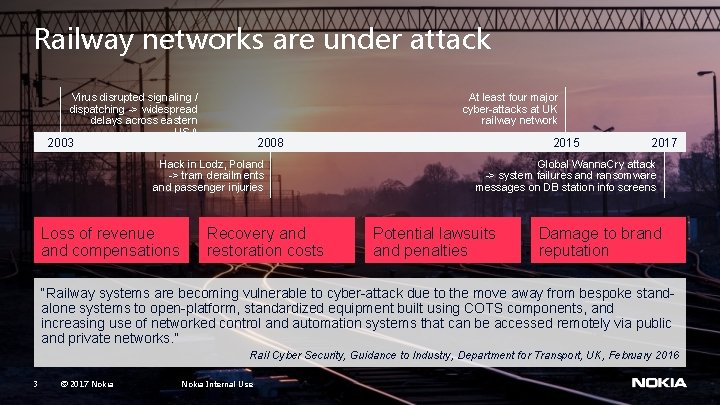
Railway networks are under attack Virus disrupted signaling / dispatching -> widespread delays across eastern USA At least four major cyber-attacks at UK railway network 2003 Hack in Lodz, Poland -> tram derailments and passenger injuries Loss of revenue and compensations 2015 2008 Recovery and restoration costs 2017 Global Wanna. Cry attack -> system failures and ransomware messages on DB station info screens Potential lawsuits and penalties Damage to brand reputation “Railway systems are becoming vulnerable to cyber-attack due to the move away from bespoke standalone systems to open-platform, standardized equipment built using COTS components, and increasing use of networked control and automation systems that can be accessed remotely via public and private networks. ” Rail Cyber Security, Guidance to Industry, Department for Transport, UK, February 2016 3 © 2017 Nokia Internal Use

Key learnings from attacks on critical infrastructures Anatomy of the 2015 Ukrainian power system attack (250, 000 without electricity)… Step 1: Break-in Hackers target personnel through phishing emails with attached malware macros Step 2: Expand & Step 3: The attack prepare Hackers harvest credentials and Hackers disconnect circuit set up IPSec VPN connection directly into the network breakers and hinder recovery -> Visits to each substation to manually reset circuit breakers Credential protection, anomaly detection, IP/MPLS VPN and firewall Automated response solutions to prevent threats before they become breaches … and how to prevent it Endpoint security to detect command-control traffic, before malware is detonated 4 © 2017 Nokia Internal Use
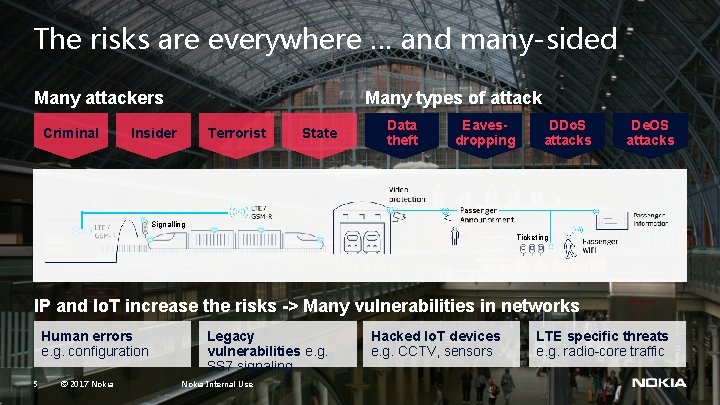
The risks are everywhere … and many-sided Many attackers Criminal Many types of attack Insider Terrorist State Data theft Eavesdropping DDo. S attacks De. OS attacks Signalling Ticketing IP and Io. T increase the risks -> Many vulnerabilities in networks Human errors e. g. configuration 5 © 2017 Nokia Legacy vulnerabilities e. g. SS 7 signaling Nokia Internal Use Hacked Io. T devices e. g. CCTV, sensors LTE specific threats e. g. radio-core traffic

Rising regulatory pressure – Examples EU Cybersecurity Strategy APTA Security Programs & Resources Roles, responsibilities and actions to protect citizens Help ensure that transit agencies are successful in maintaining and improving security General Data Protection Regulation Government legislation Substantial tightening of data privacy requirements 6 © 2017 Nokia Internal Use GDPR § Operators need to monitor compliance to security requirements and report security breaches to safeguard data privacy
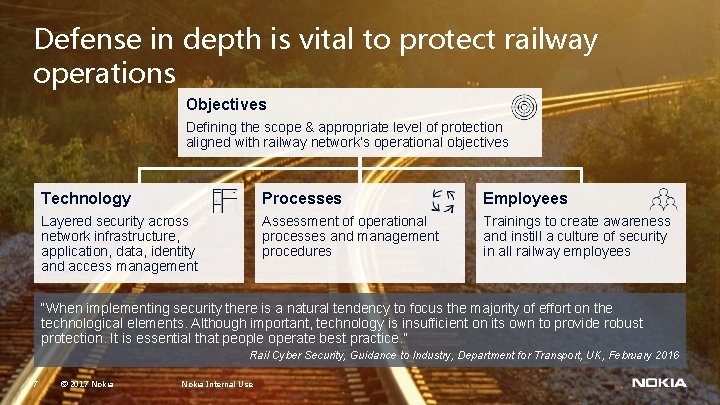
Defense in depth is vital to protect railway operations Objectives Defining the scope & appropriate level of protection aligned with railway network’s operational objectives Technology Processes Employees Layered security across network infrastructure, application, data, identity and access management Assessment of operational processes and management procedures Trainings to create awareness and instill a culture of security in all railway employees “When implementing security there is a natural tendency to focus the majority of effort on the technological elements. Although important, technology is insufficient on its own to provide robust protection. It is essential that people operate best practice. ” Rail Cyber Security, Guidance to Industry, Department for Transport, UK, February 2016 7 © 2017 Nokia Internal Use
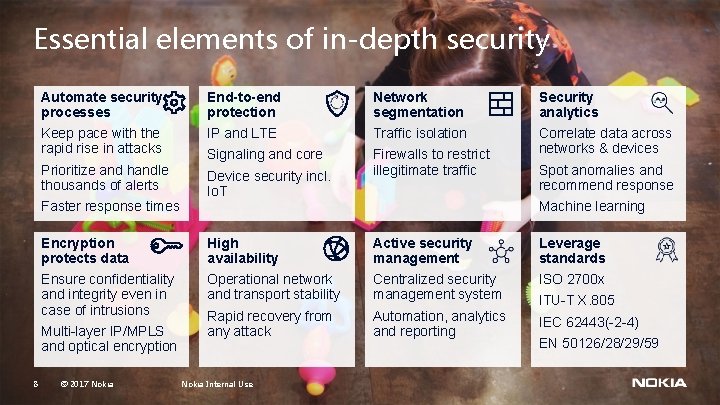
Essential elements of in-depth security Automate security processes End-to-end protection Network segmentation Security analytics Keep pace with the rapid rise in attacks IP and LTE Traffic isolation Prioritize and handle thousands of alerts Signaling and core Device security incl. Io. T Firewalls to restrict illegitimate traffic Correlate data across networks & devices Faster response times Machine learning Encryption protects data High availability Active security management Leverage standards Ensure confidentiality and integrity even in case of intrusions Operational network and transport stability Centralized security management system ISO 2700 x Rapid recovery from any attack Automation, analytics and reporting IEC 62443(-2 -4) Multi-layer IP/MPLS and optical encryption 8 Spot anomalies and recommend response © 2017 Nokia Internal Use ITU-T X. 805 EN 50126/28/29/59
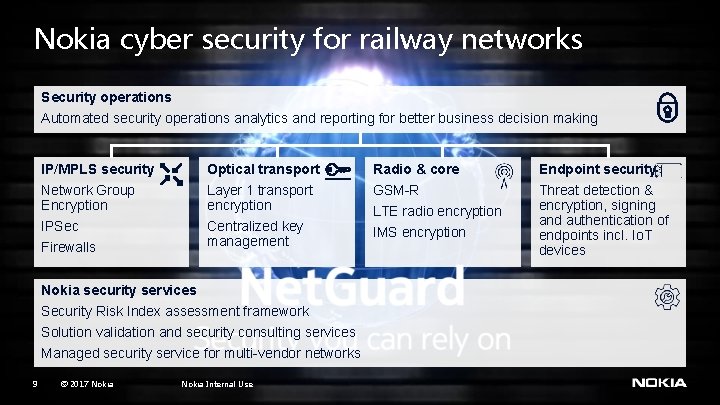
Nokia cyber security for railway networks Security operations Automated security operations analytics and reporting for better business decision making IP/MPLS security Optical transport Radio & core Endpoint security Network Group Encryption Layer 1 transport encryption GSM-R IPSec Centralized key management IMS encryption Threat detection & encryption, signing and authentication of endpoints incl. Io. T devices Firewalls Nokia security services Security Risk Index assessment framework Solution validation and security consulting services Managed security service for multi-vendor networks 9 © 2017 Nokia Internal Use LTE radio encryption

Nokia – protecting railway communication networks 1 2 3 Secure evolution towards future-proof LTE and IP/MPLS technology to support new services & efficient operations Robust network defense through automation, data analytics, machine learning and end-to-end encryption Advanced approach built on long, in-depth expertise in security and mission critical networks and operations 10 © 2017 Nokia Internal Use
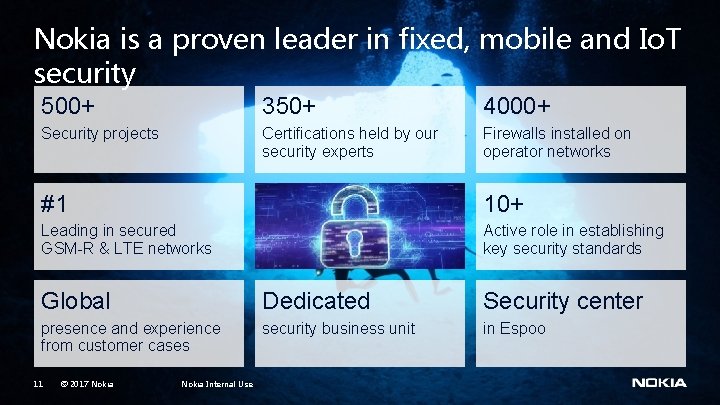
Nokia is a proven leader in fixed, mobile and Io. T security 500+ 350+ 4000+ Security projects Certifications held by our security experts Firewalls installed on operator networks #1 10+ Leading in secured GSM-R & LTE networks Active role in establishing key security standards Global Dedicated Security center presence and experience from customer cases security business unit in Espoo 11 © 2017 Nokia Internal Use

- Slides: 12