Cybersecurity By Craig Watanabe and Jon Beyrer Overview

Cybersecurity By Craig Watanabe and Jon Beyrer

Overview • Why Cybersecurity Is A High Priority • Regulatory Guidance (? ) • Risk Management -Compliance, Business Perspectives • Practicality Drives Reality -Perimeter versus Interior • Identifying and Assessing Risk • The Human Element • Developing Your Program

Materials • SEC’s cybersecurity sweep exam letter • Summary from a firm examined under the cybersecurity sweep • Policy and procedure templates tie into the annotated sweep exam letter • Forms and checklists aid in program implementation • Memos- Interoffice Memorandum • Training Aids- Smarter than CCO game
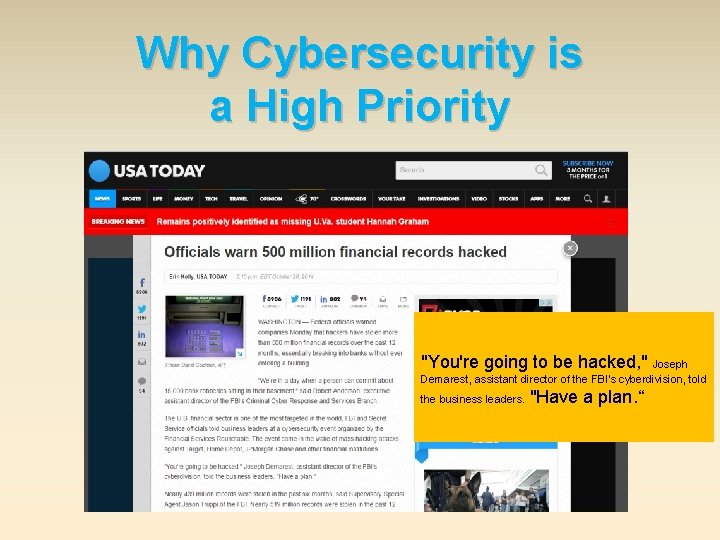
Why Cybersecurity is a High Priority "You're going to be hacked, " Joseph Demarest, assistant director of the FBI's cyberdivision, told the business leaders. "Have a plan. “

Regulatory Guidance? • Federal Guidance: – Much on “What, little on “How” – OCIE Risk Alert, Initiative, Sweep Exams for 50 firms – What is SEC looking for? • States: – Some have specific requirements, more may follow. – California: Disclosure of and response to Breaches.

Risk Management • Risk and Compliance Decisions – SEC requires a risk-based program – Risk generally measured by: Frequency and Severity. • Frequency of cyber risk is growing rapidly. May be more frequent than you know! • Severity can be high. Attacks are becoming more sophisticated and targeted. • Risk and Business Decisions – Business decisions often drive compliance decisions – Prevention: Choice of vendors, suppliers, equipment, allocation of resources – Transfer: Cyber insurance transfers risk to an insurance company. – Response to and containment of Breaches
Perimeter vs. Interior Security • Perimeter security – Think of your home. If a skilled burglar wants to get into your home, do you think they will be successful? – What if you installed bars on the windows, security doors and a robust alarm system? – The reality is if a skilled person really wants to get in, there is little you could do to stop them. – Think of your privacy. Of all the precautions you could take, do you think you could prevent a determined identity thief from obtaining your personal information?
Perimeter vs. Interior Security • Interior security – In the home security example, you could place valuables in a bank safe deposit box. Although inconvenient, this is the best way to protect those valuables. – In the privacy example, you could freeze your credit This would make it difficult for an identity thief to abuse your information.

Practicality Drives Reality • Interior security is more effective than perimeter security. • The two most important cybersecurity policies relate to interior security – Encryption If breached, encrypted data would make it difficult for a hacker to abuse the data – Data Backup If breached, a hacker could maliciously destroy data so robust data backups are essential
Identifying Risks • Vulnerability assessment – Identify and quantify vulnerabilities. – Provide appropriate mitigation procedures to eliminate or reduce them • Penetration test – Simulates the actions of an attacker aiming to breach the system. – Attempts to exploit critical systems and gain access to sensitive data. – A vulnerability assessment will yield more value than a penetration test.

Human Element • In reality there is a human element to cybersecurity and many breaches emanate from compromised users • User awareness training -a good place to start because it is not highly technical.

Developing Your Program Policies and Procedures – Should cover all facets: • Risk identification and assessment • Network configuration (Perimeter Security) • Controls (i. e. Encryption, destruction, passwords, physical security, etc. ) • Training and education • Supervision and Testing • Due Diligence

Developing Your Program • Key Elements: – Perimeter: Network, Access, Physical Security – Interior: Data Backup, Encryption, Passwords, Destruction – Transmission: Internet, E-mail, Mobile Devices – Human: Training, Supervision, Discipline – Incident Management • Tools and Templates: – Checklists for Supervision, Testing, Controls and Policy implementation – Memos, Communications, Training – “Action Templates” Templates Increase compliance, not state in P&Ps

Conclusion • Questions? • Craig Watanabe craig@advisorsolutionsgroup. com • Jon Beyrer beyrer@bfadvisers. com
- Slides: 14