Cybersecurity and Encryption Sergeant Paul Johnstone LLB MLitt

Cyber-security and Encryption Sergeant Paul Johnstone LLB MLitt © Garda Bureau of Fraud Investigation

What is Encryption? Encryption is an electronic method used to protect the integrity of devices, data and communications by scrambling the contents preventing its use by persons who don't have the decryption code needed to unscramble it again. Conversion of electronic data into another form (ciphertext) which is not readable without an appropriate key.
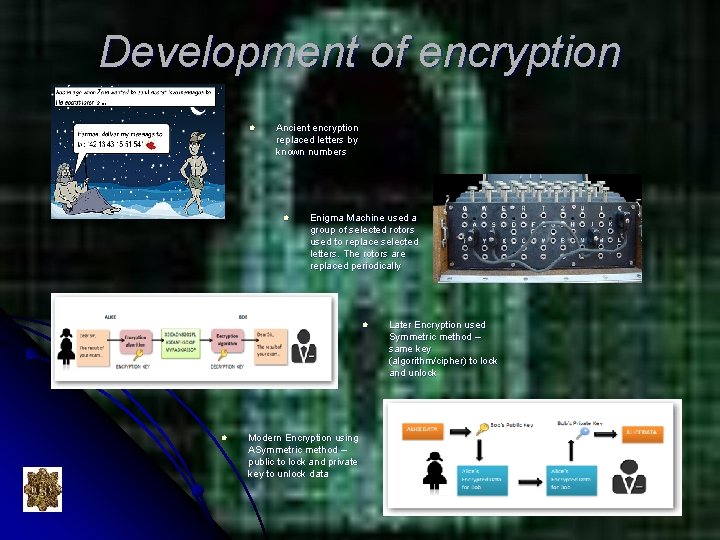
Development of encryption l Ancient encryption replaced letters by known numbers l Enigma Machine used a group of selected rotors used to replace selected letters. The rotors are replaced periodically l l Modern Encryption using ASymmetric method – public to lock and private key to unlock data Later Encryption used Symmetric method – same key (algorithm/cipher) to lock and unlock

Why is it important? l l l Secure data and information exchange – authorised use Prevents data loss or manipulation – internal and external* Enables secure browsing - Wi. Fi Enables secure access to emails and content Legal and ethical obligation to protect sensitive data Protects client and YOU Censure from Professional Bodies Censure from Political or Governmental Bodies – DPC etc Prevents Civil claim by clients Prevents reputational damage • Its available and relatively easy to use

Problems with Encryption some 1) 2) 3) 4) 5) 6) 7) Slows down browsing and file exchange as the file is transferred encrypted and then decrypted at the other end. If you forget the decryption key the data is lost. If you lose the device, the data is lost Which one to use – large number of suppliers Not secure from attack – SQL injection or Java Exploit Human Error – is it totally secure? * Applications with access to encrypted data can be infected with sniffing malware etc The can be cracked by reverse engineering or. . . Truecrypt
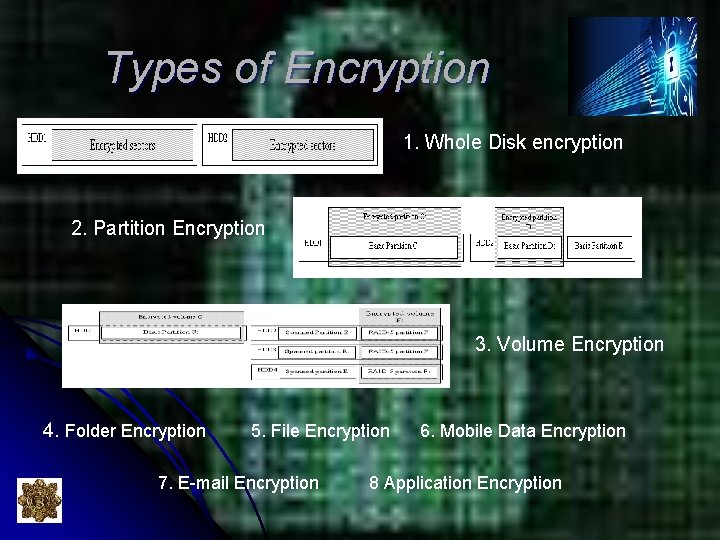
Types of Encryption 1. Whole Disk encryption 2. Partition Encryption 3. Volume Encryption 4. Folder Encryption 5. File Encryption 7. E-mail Encryption 6. Mobile Data Encryption 8 Application Encryption

Security of Devices l Offline devices – not on internal network
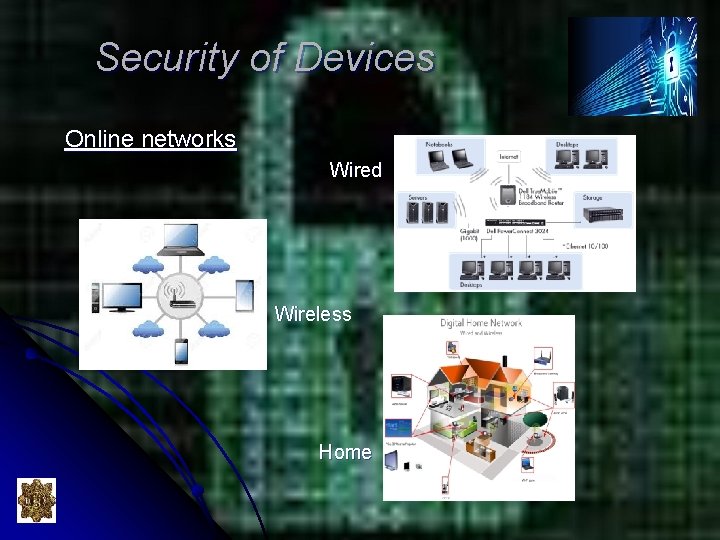
Security of Devices Online networks Wired Wireless Home

Encryption Examples PGP – Communications/files/email l File. Vault II – MAC Devices l Bit. Locker – Windows Devices l Vera. Crypt – Disks/volumes/files/systems l GPG (GNU Privacy Guard)- files/folders l Best. Crypt – Files/Folders l True. Crypt - now compromised l Encryption to 256 bit. ‘Unbreakable’. Can upgrade to 512 Military.

When needed? Devices Stolen l Network compromised or hacked l Insecure networks – open wifi etc l Media lost l BYOD l Email intrusion – malware l Data sent to wrong recipient l

Level Needed l No correct answer - Depends on a. The data b. Your needs c. The risks – real or perceived

Policies on Encryption i. iii. iv. v. viii. Law Society – Ireland & UK HSE – Ireland Bar Council UK NUI Galway An Garda Síochána – secure access and mobile devices Government Departments – mobile device data Etc. . . Your policy should be your policy

Security of Communications l l l l SMS and emails messages are susceptible to intercept Open Wi. Fi in cafe or hotel etc – phone seeks and connects Hacker uses laptop with WAP running and stronger signal that Wi. Fi in premises. My device will automatically seek the stronger signal and connect I send message over internet using phone and Wi. Fi Hacker sets his network to reject MMS (secure messaging) My network reverts to SMS plain text messaging Hacker has my messages and attachments and if he connects malware to phone – he has access to my account etc. . .

Home Networks Connected to home Wi. Fi network - secure l Previously connected to open Wi. Fi l Car outside war-driving with strong open Wi. Fi l Device connects to stronger open signal l Access to computer, malware injection, contents etc l Disable Wi. Fi scanning when at home and encrypt l

People One of the most significant risks of data loss
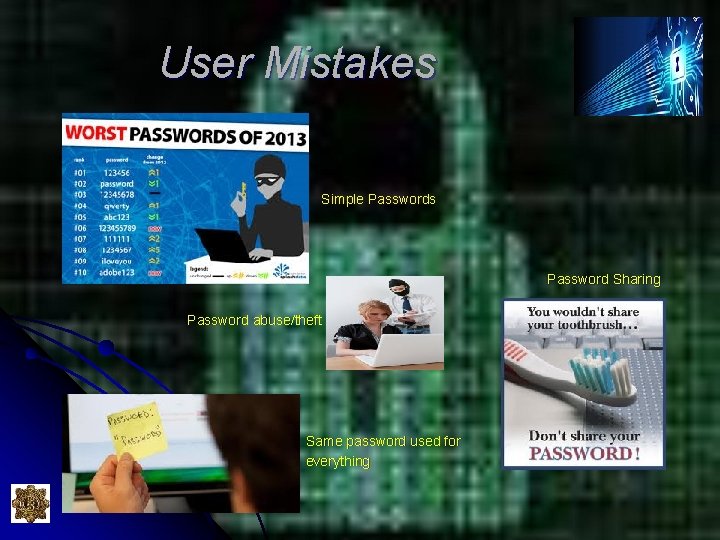
User Mistakes Simple Passwords Password Sharing Password abuse/theft Same password used for everything
Network/Data Intrusions Memory stick manipulation l Stick dropped outside l Connected to network l Second pin removed l Windows machines = keyboard l Malware = full access l BYOD – not good policy l
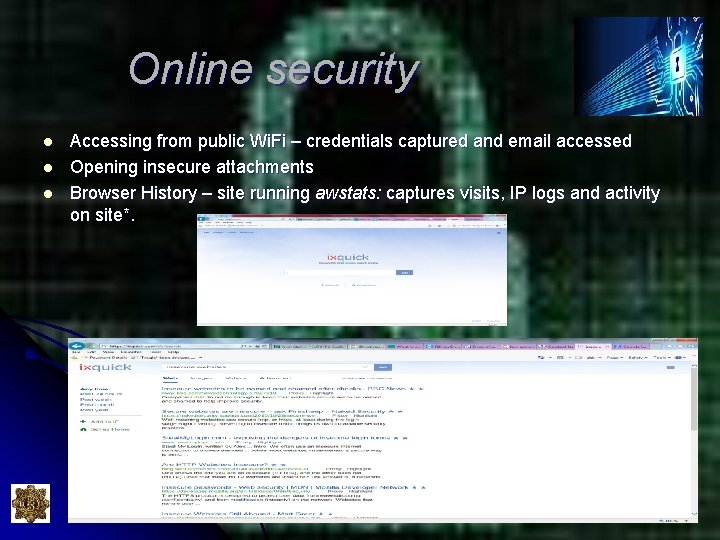
Online security l l l Accessing from public Wi. Fi – credentials captured and email accessed Opening insecure attachments Browser History – site running awstats: captures visits, IP logs and activity on site*.
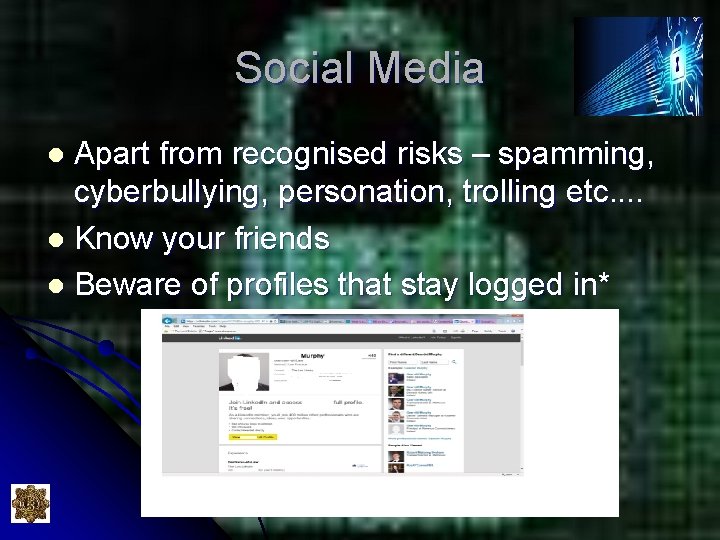
Social Media Apart from recognised risks – spamming, cyberbullying, personation, trolling etc. . l Know your friends l Beware of profiles that stay logged in* l
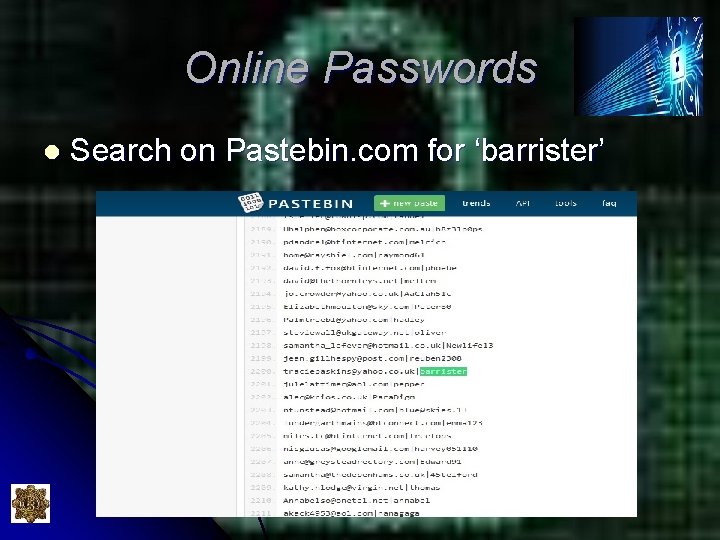
Online Passwords l Search on Pastebin. com for ‘barrister’
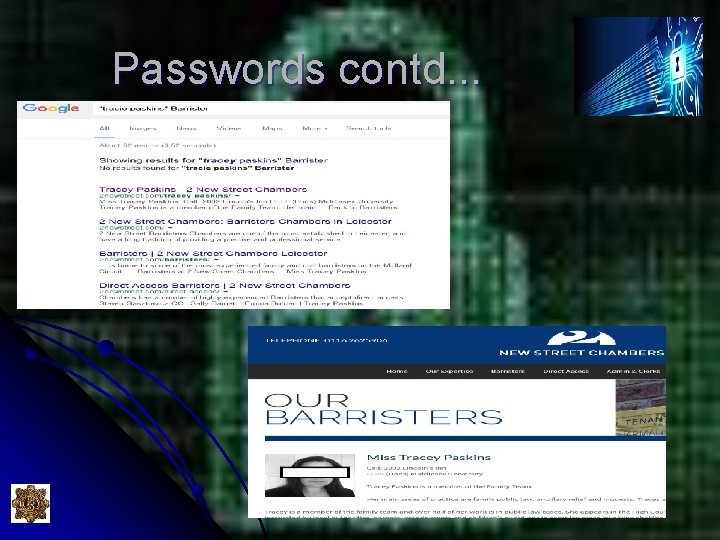
Passwords contd. . .

Identifying threats Know your system l Know your users l Know your devices l Use encryption l Use secure email l Vary and change passwords l Unknown source – DELETE l Disable Wi. Fi scanning after connection l

Security is your concern – its your data l Its as secure as you make it l Antivirus, malware protection, passwords l System intrusion testing and updates l Intrusion detection software l If in doubt consult IT specialists Grant Thornton – Ritz - Critical Data – Mazars - Mandiant – RMS – l Espion – Ward Solutions – e. Sentire – Digicore - etc
Homework • If you have a website run the following Google tests against it at home ‘filetype: docs site: pauljohnstone. ie’ ‘info: pauljohnstone. ie’ • • • Is there access to a private members area on a publically accessible system? – subject to interception. Is your internal network and internet access through same machine? – subject to interception Is your Wi. Fi open – www. wigle. net maps open wireless networks

Sgt Paul Johnstone Computer Crime Investigation Unit An Garda Síochána Harcourt Street Dublin 2 D 02 PT 89 Tel: +353 1 6663796 Mob: +363 86 8281889 Email: paul. j. johnstone@garda. ie
- Slides: 25